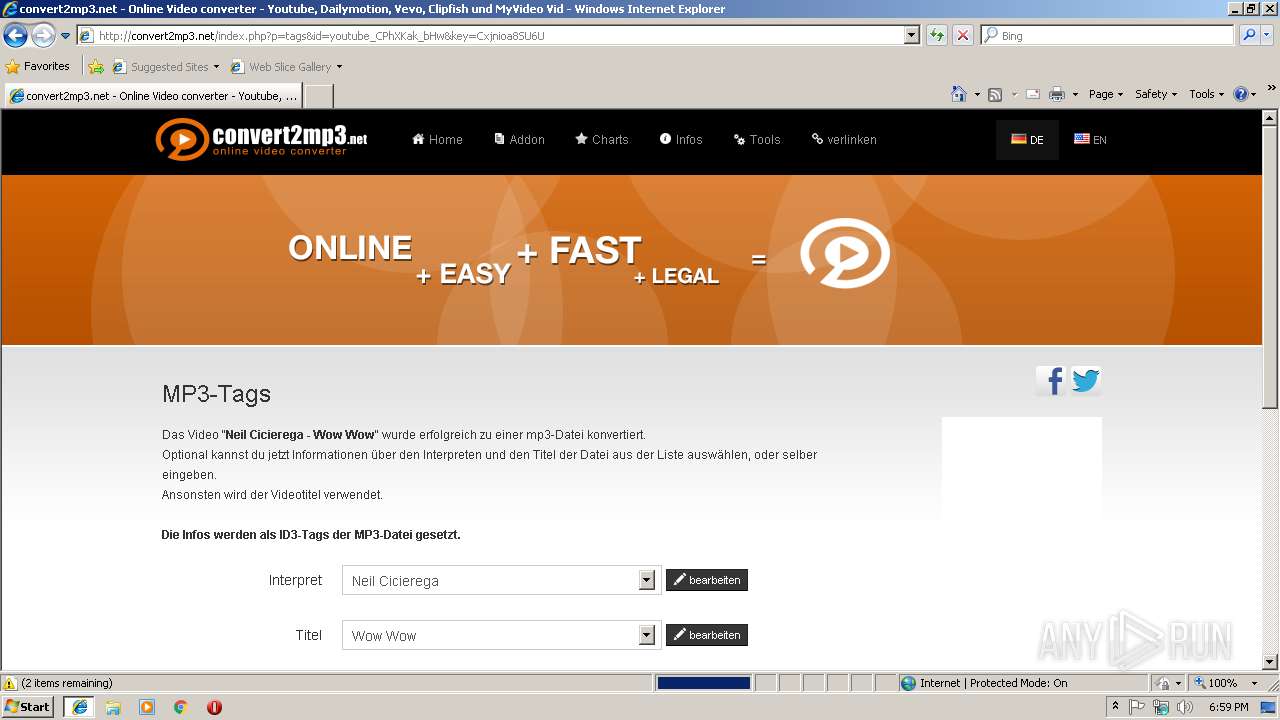
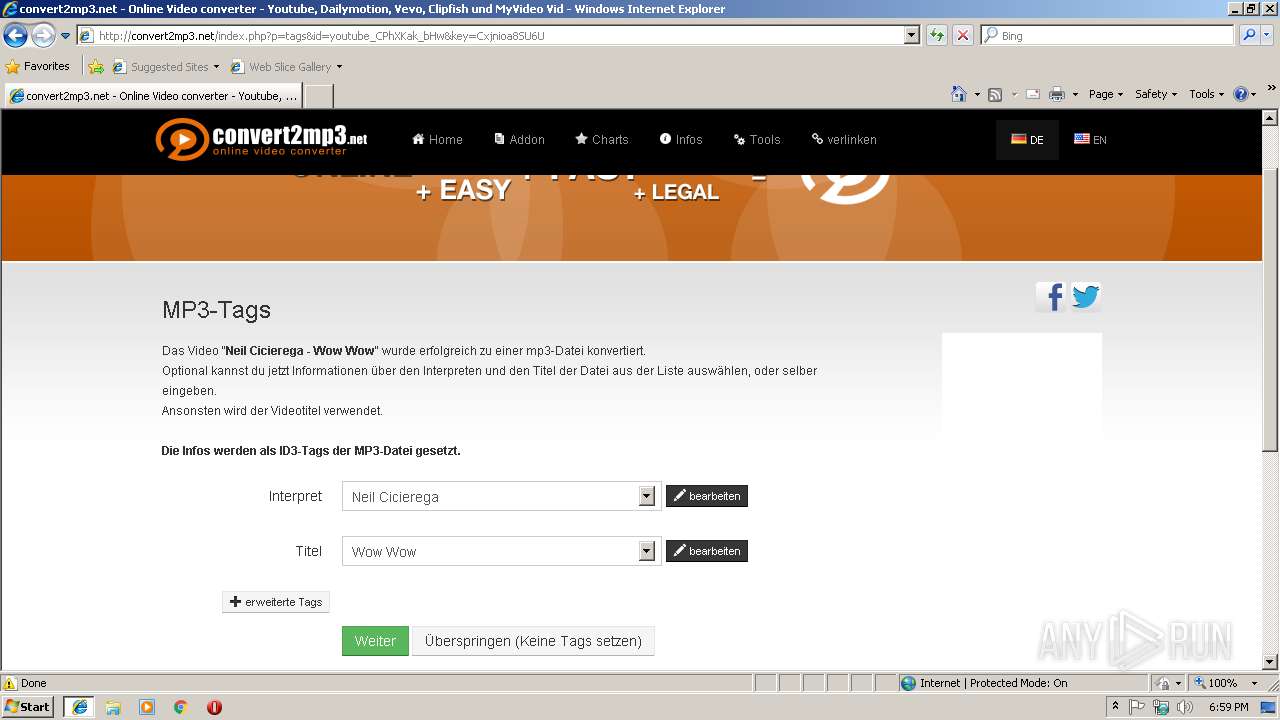
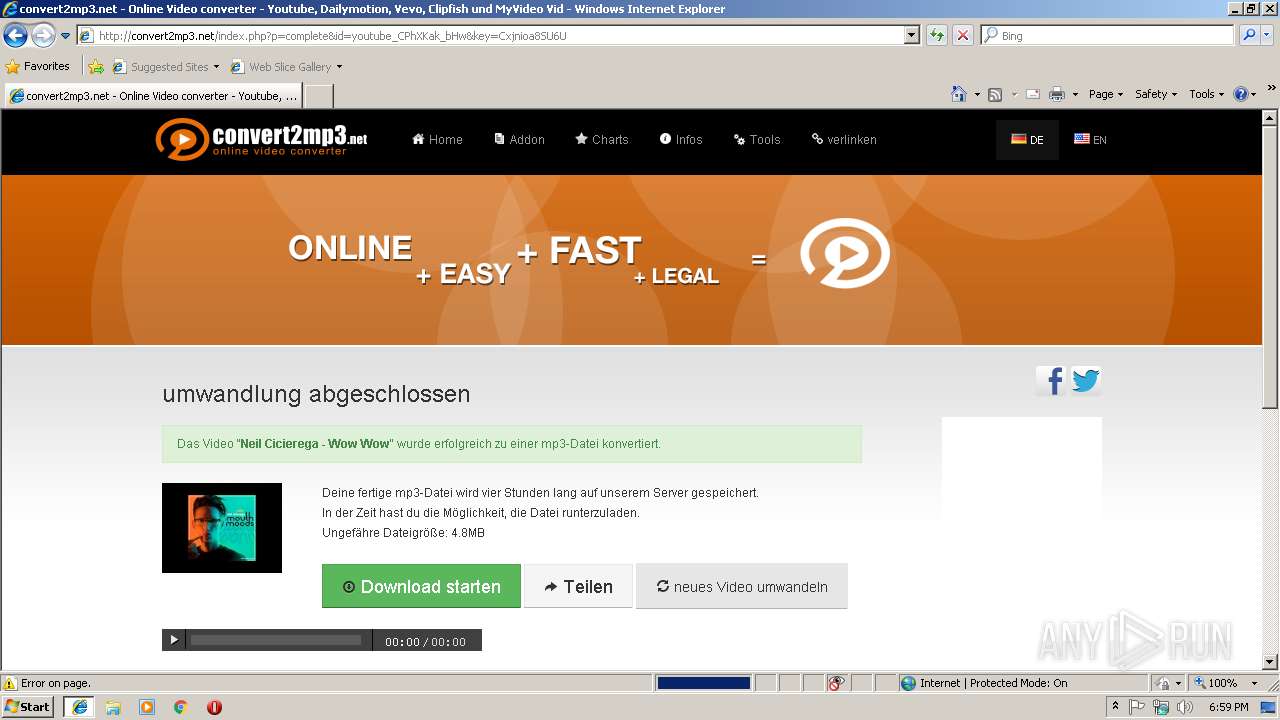
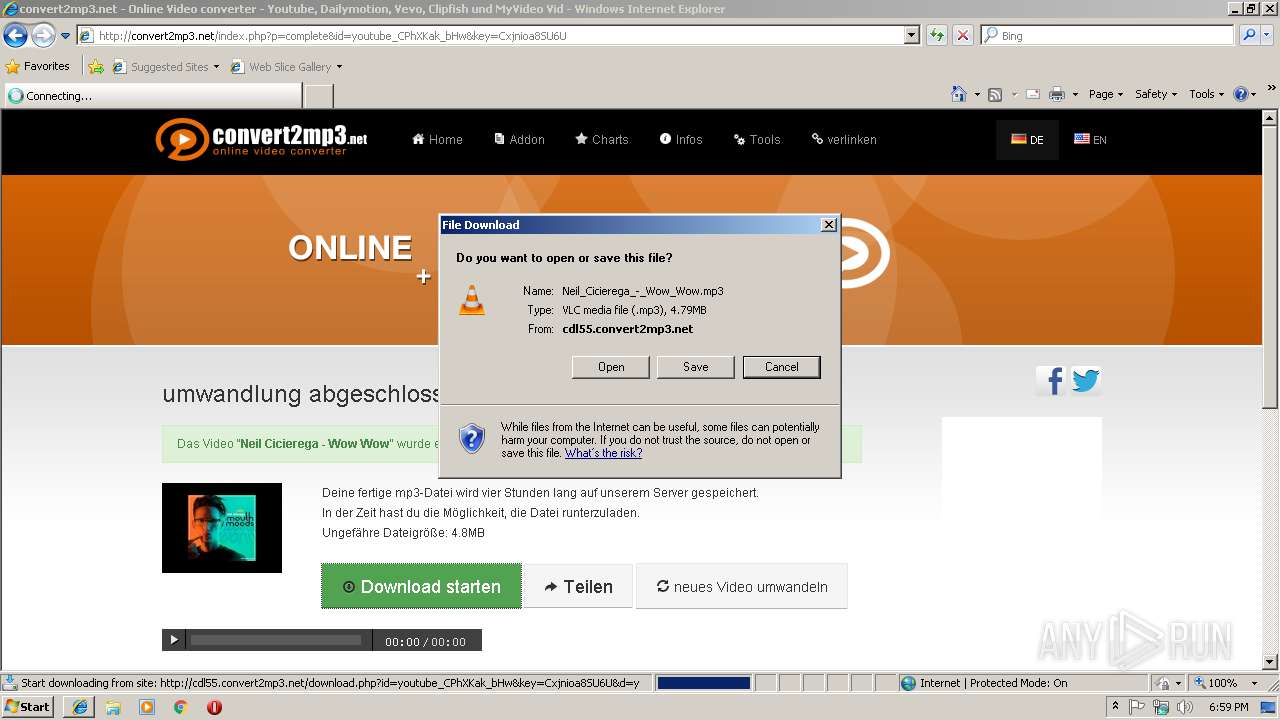
| URL: | http://convert2mp3.net/index.php?p=complete&id=youtube_CPhXKak_bHw&key=3H1xxd1q6m38 |
| Full analysis: | https://app.any.run/tasks/ac66f628-5caf-49f4-afda-d2961b2ea87e |
| Verdict: | No threats detected |
| Analysis date: | January 28, 2019, 18:58:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 17DCC2BC19A6EB561C6A148DFE95B5EB |
| SHA1: | 182E698064FA0CB656747AB6A61E18FB863A762B |
| SHA256: | 707090F1825A5E230E61B9C5C8354D868FF2AFA35A857A7B4140179C994EFCE9 |
| SSDEEP: | 3:N1KdKLMea0sLbHer3A0AMQgGJ7Acp4UW:CIAelaHerwLCGCgZW |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- vlc.exe (PID: 2604)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2992)
Reads settings of System Certificates
- iexplore.exe (PID: 3292)
- chrome.exe (PID: 3012)
Application launched itself
- iexplore.exe (PID: 2992)
- chrome.exe (PID: 3012)
Reads Internet Cache Settings
- iexplore.exe (PID: 3292)
Dropped object may contain TOR URL's
- iexplore.exe (PID: 3292)
Creates files in the user directory
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3844)
- iexplore.exe (PID: 3292)
- iexplore.exe (PID: 2992)
Reads internet explorer settings
- iexplore.exe (PID: 3292)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
51
Monitored processes
14
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
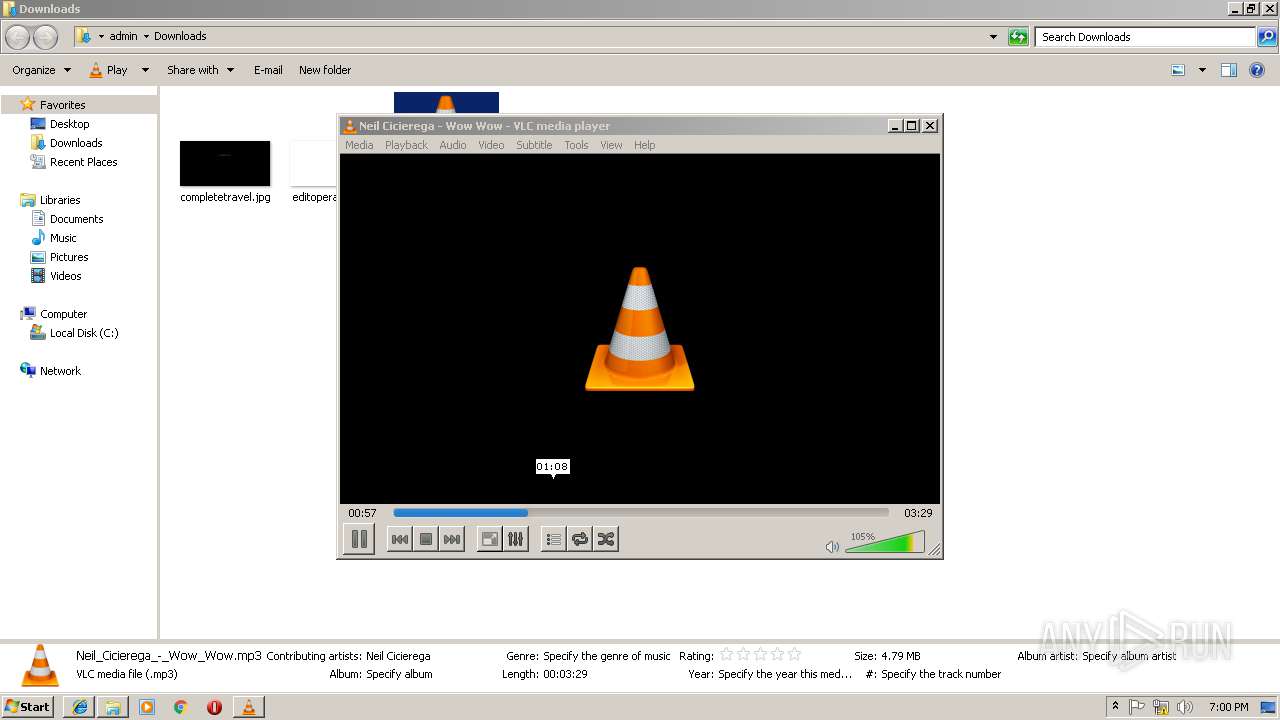
| 1044 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\Downloads\Neil_Cicierega_-_Wow_Wow.mp3" | C:\Program Files\VideoLAN\VLC\vlc.exe | explorer.exe | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 2.2.6 Modules
| |||||||||||||||
| 1060 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x666000b0,0x666000c0,0x666000cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2508 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\Downloads\Neil_Cicierega_-_Wow_Wow.mp3" | C:\Program Files\VideoLAN\VLC\vlc.exe | explorer.exe | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 2.2.6 Modules
| |||||||||||||||
| 2592 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=956,6812000922785881392,15921776202332794240,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=3FF7C9E8E616390E379F6CAF2F058308 --mojo-platform-channel-handle=976 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2604 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\Downloads\Neil_Cicierega_-_Wow_Wow.mp3" | C:\Program Files\VideoLAN\VLC\vlc.exe | explorer.exe | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 2.2.6 Modules
| |||||||||||||||
| 2880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=956,6812000922785881392,15921776202332794240,131072 --enable-features=PasswordImport --service-pipe-token=747BD4CBB661B153E6C0D1BF90BCD9A8 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=747BD4CBB661B153E6C0D1BF90BCD9A8 --renderer-client-id=3 --mojo-platform-channel-handle=2088 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2992 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3012 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3108 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=956,6812000922785881392,15921776202332794240,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=582965789B13FC8AE8E650224DB94608 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=582965789B13FC8AE8E650224DB94608 --renderer-client-id=6 --mojo-platform-channel-handle=2704 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=956,6812000922785881392,15921776202332794240,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=EF0A4B95F81013C8733383EF37BA30DD --mojo-platform-channel-handle=3744 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
1 632
Read events
1 432
Write events
191
Delete events
9
Modification events
| (PID) Process: | (2992) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2992) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2992) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2992) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2992) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2992) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2992) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {C2BFAC83-232E-11E9-AA93-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2992) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2992) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2992) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307010001001C0012003A003800C902 | |||
Executable files
0
Suspicious files
53
Text files
148
Unknown types
33
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2992 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2992 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3292 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@convert2mp3[1].txt | — | |
MD5:— | SHA256:— | |||
| 3292 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\index[1].php | — | |
MD5:— | SHA256:— | |||
| 3292 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@pushgaga[1].txt | — | |
MD5:— | SHA256:— | |||
| 3292 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@cobalten[2].txt | — | |
MD5:— | SHA256:— | |||
| 3292 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\index[1].htm | html | |
MD5:— | SHA256:— | |||
| 3292 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@convert2mp3[2].txt | text | |
MD5:— | SHA256:— | |||
| 3292 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\bootstrap.min[1].css | text | |
MD5:— | SHA256:— | |||
| 3292 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\main.min[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
65
TCP/UDP connections
44
DNS requests
27
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3292 | iexplore.exe | GET | 302 | 104.27.120.50:80 | http://convert2mp3.net/index.php?p=complete&id=youtube_CPhXKak_bHw&key=3H1xxd1q6m38 | US | html | 7.90 Kb | whitelisted |
3292 | iexplore.exe | GET | 200 | 104.27.120.50:80 | http://convert2mp3.net/index.php?url=http%3A%2F%2Fwww.youtube.com%2Fwatch%3Fv%3DCPhXKak_bHw | US | html | 5.40 Kb | whitelisted |
3292 | iexplore.exe | GET | 200 | 104.27.120.50:80 | http://convert2mp3.net/main.min.css | US | text | 1.79 Kb | whitelisted |
3292 | iexplore.exe | GET | 200 | 104.27.120.50:80 | http://convert2mp3.net/bootstrap.min.css | US | text | 20.4 Kb | whitelisted |
3292 | iexplore.exe | GET | 200 | 104.27.120.50:80 | http://convert2mp3.net/assets/js/main.min.js | US | text | 2.33 Kb | whitelisted |
3292 | iexplore.exe | GET | 200 | 188.72.213.234:80 | http://pushgaga.com/ntfc.php?p=1747878 | NL | text | 568 b | suspicious |
3292 | iexplore.exe | GET | 200 | 188.72.213.176:80 | http://cobalten.com/apu.php?zoneid=813021 | NL | text | 27.6 Kb | malicious |
3292 | iexplore.exe | GET | 200 | 104.27.120.50:80 | http://convert2mp3.net/assets/js/push.js | US | text | 14.5 Kb | whitelisted |
3292 | iexplore.exe | GET | 200 | 104.27.120.50:80 | http://convert2mp3.net/assets/img/addon.png | US | image | 1.15 Kb | whitelisted |
3292 | iexplore.exe | GET | 200 | 104.27.120.50:80 | http://convert2mp3.net/assets/img/home.png | US | image | 1.21 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3292 | iexplore.exe | 172.217.16.205:443 | accounts.google.com | Google Inc. | US | whitelisted |
3292 | iexplore.exe | 172.217.22.67:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3292 | iexplore.exe | 185.60.216.19:443 | static.xx.fbcdn.net | Facebook, Inc. | IE | whitelisted |
3292 | iexplore.exe | 104.27.121.50:80 | convert2mp3.net | Cloudflare Inc | US | shared |
2992 | iexplore.exe | 104.27.121.50:80 | convert2mp3.net | Cloudflare Inc | US | shared |
3292 | iexplore.exe | 188.72.213.106:80 | native.propellerads.com | Webzilla B.V. | NL | unknown |
3292 | iexplore.exe | 188.165.236.222:80 | cdl55.convert2mp3.net | OVH SAS | FR | unknown |
3292 | iexplore.exe | 162.125.66.1:443 | www.dropbox.com | Dropbox, Inc. | DE | shared |
3012 | chrome.exe | 172.217.22.99:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2992 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
convert2mp3.net |
| whitelisted |
pushgaga.com |
| suspicious |
go.oclasrv.com |
| malicious |
cobalten.com |
| malicious |
platform.twitter.com |
| whitelisted |
www.facebook.com |
| whitelisted |
apis.google.com |
| whitelisted |
static.xx.fbcdn.net |
| whitelisted |
accounts.google.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3292 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY Outdated Flash Version M1 |
Process | Message |
|---|---|
vlc.exe | core libvlc: one instance mode ENABLED
|
vlc.exe | core libvlc: Running vlc with the default interface. Use 'cvlc' to use vlc without interface.
|
vlc.exe | mpgatofixed32 audio converter error: libmad error: bad main_data_begin pointer
|
vlc.exe | core libvlc: one instance mode ENABLED
|
vlc.exe | core libvlc: one instance mode ENABLED
|
vlc.exe | mpgatofixed32 audio converter error: libmad error: Huffman data overrun
|