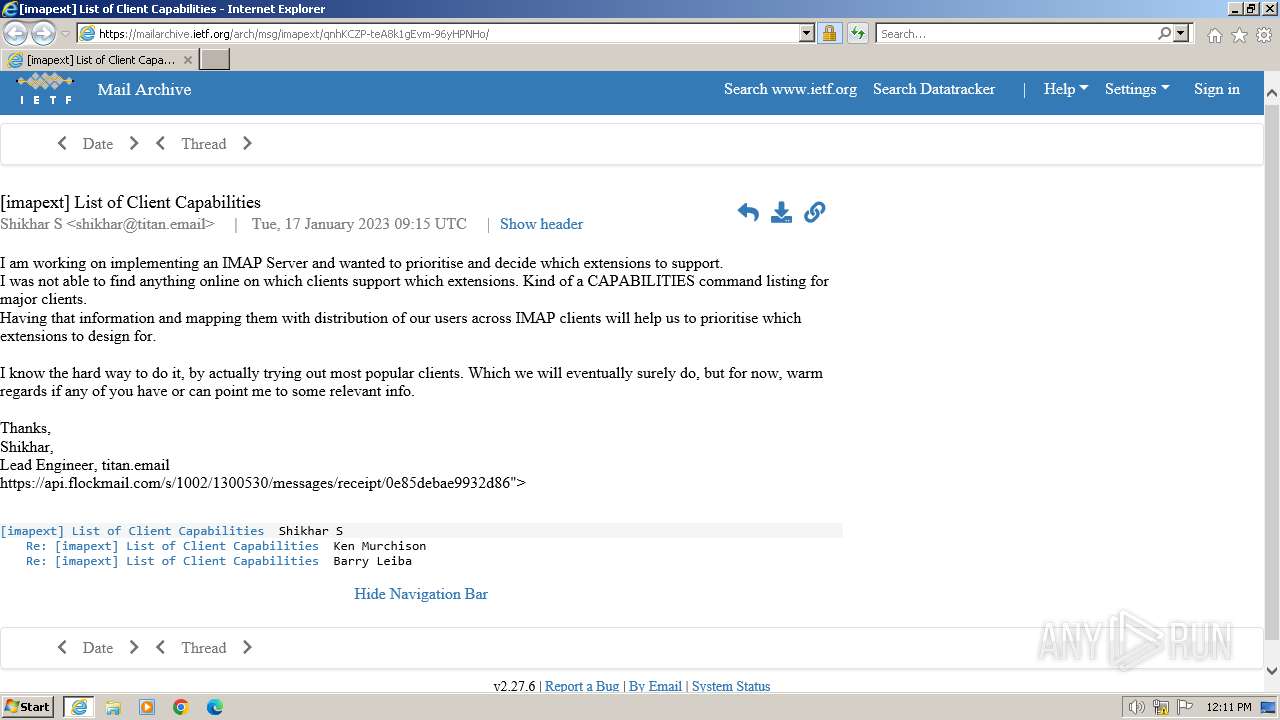
| URL: | https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&cad=rja&uact=8&ved=2ahUKEwjtnO37iuCIAxUA1gIHHWZLNNQ4ChAWegQIERAB&url=https%3A%2F%2Fmailarchive.ietf.org%2Farch%2Fmsg%2Fimapext%2FqnhKCZP-teA8k1gEvm-96yHPNHo%2F&usg=AOvVaw2krUV2wwrhoEHlrk8LrmdU&opi=89978449 |
| Full analysis: | https://app.any.run/tasks/dcfbaa6e-2772-458a-beef-16f224186166 |
| Verdict: | Malicious activity |
| Analysis date: | September 26, 2024, 11:11:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 5336850278A4F457DE239D735C1C8BBD |
| SHA1: | 88D3758B7615F30B6E891A1FDEA95057081DEA17 |
| SHA256: | 704C9D57C641D88FA91F486A94B57506A48B13E34663F3B338654B4C711D1B8F |
| SSDEEP: | 6:2OLI2sq+wp1w4pNPQDrbBkWKRR3zSMaMBI7maTBPhBShfwhSga:2V2JnNPQDzKnetSkm6BpBWkQ |
MALICIOUS
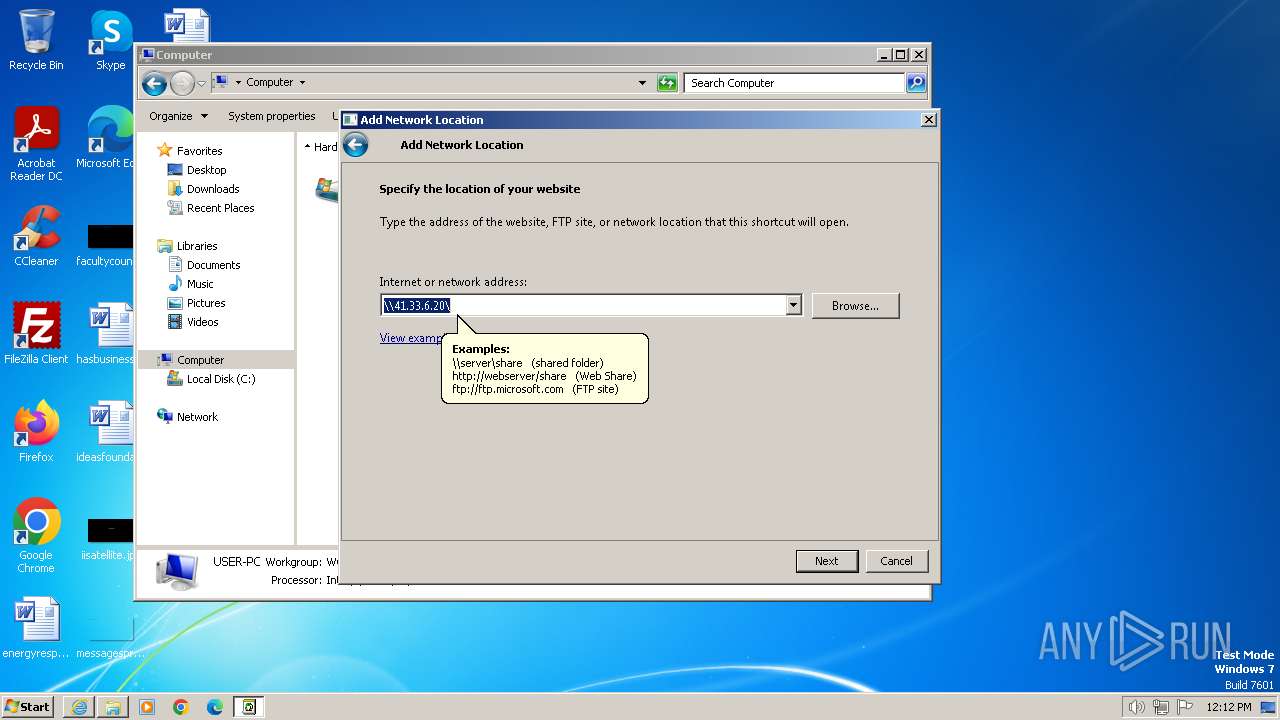
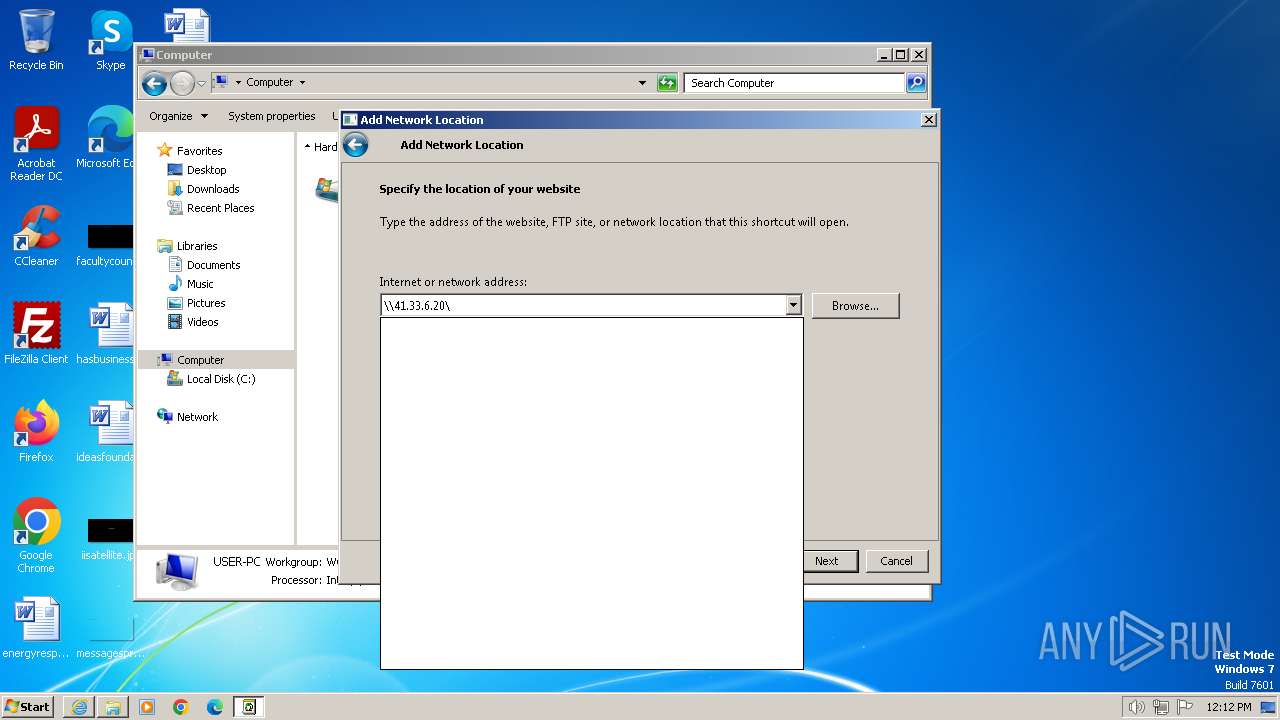
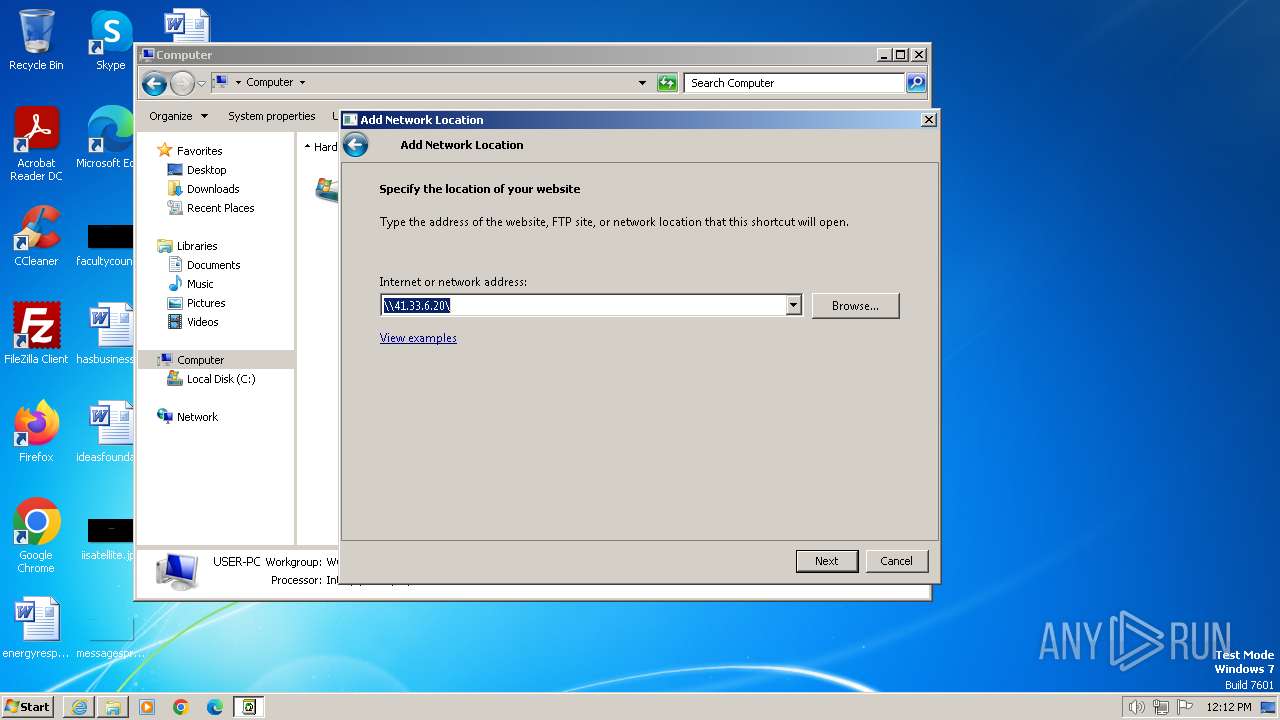
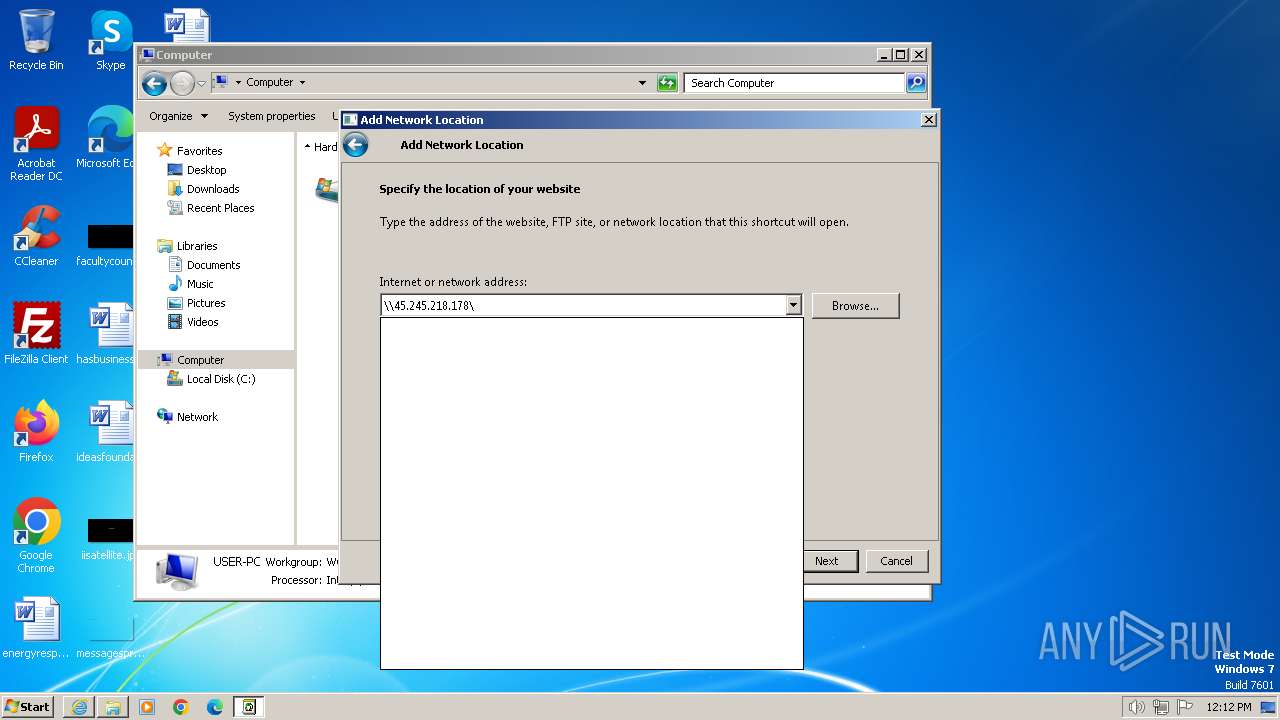
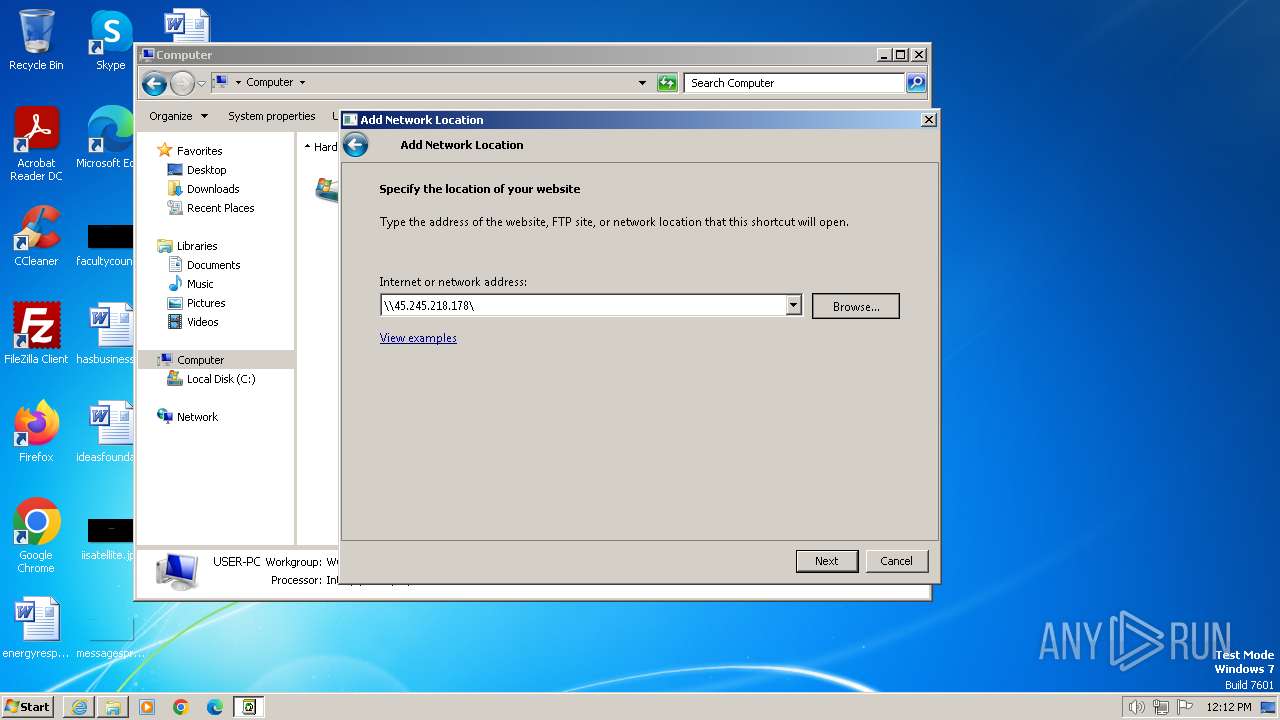
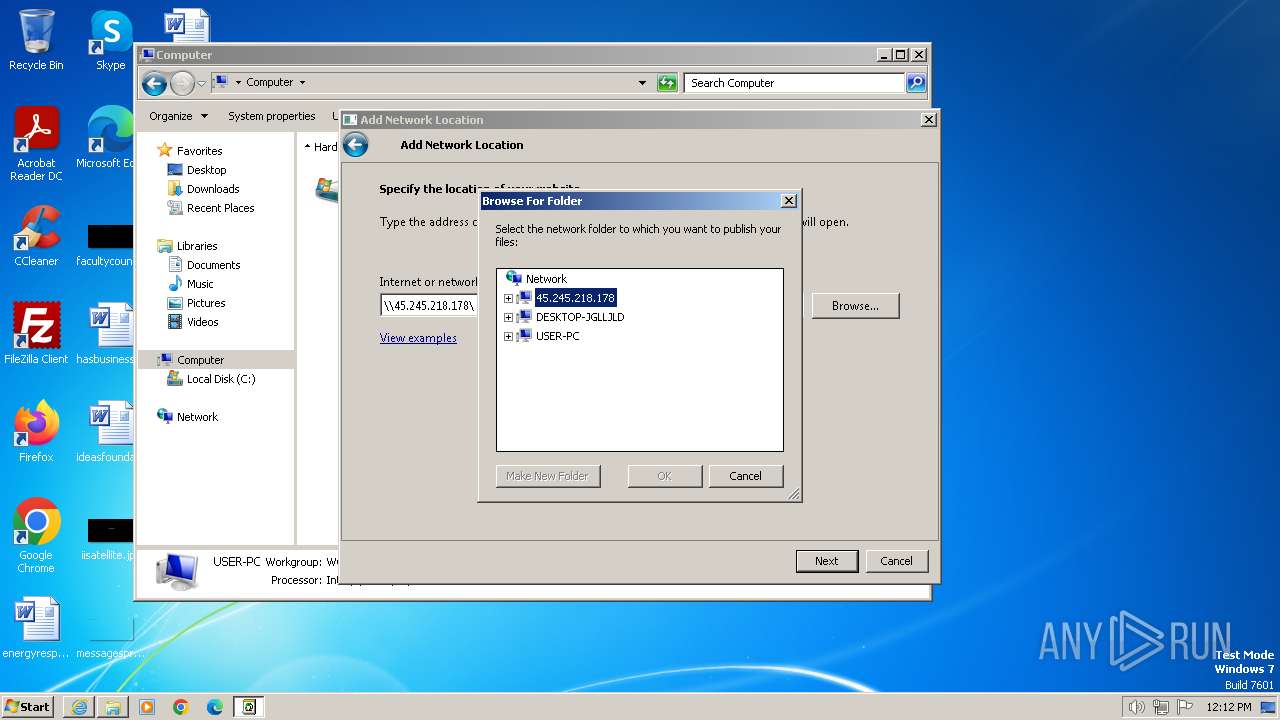
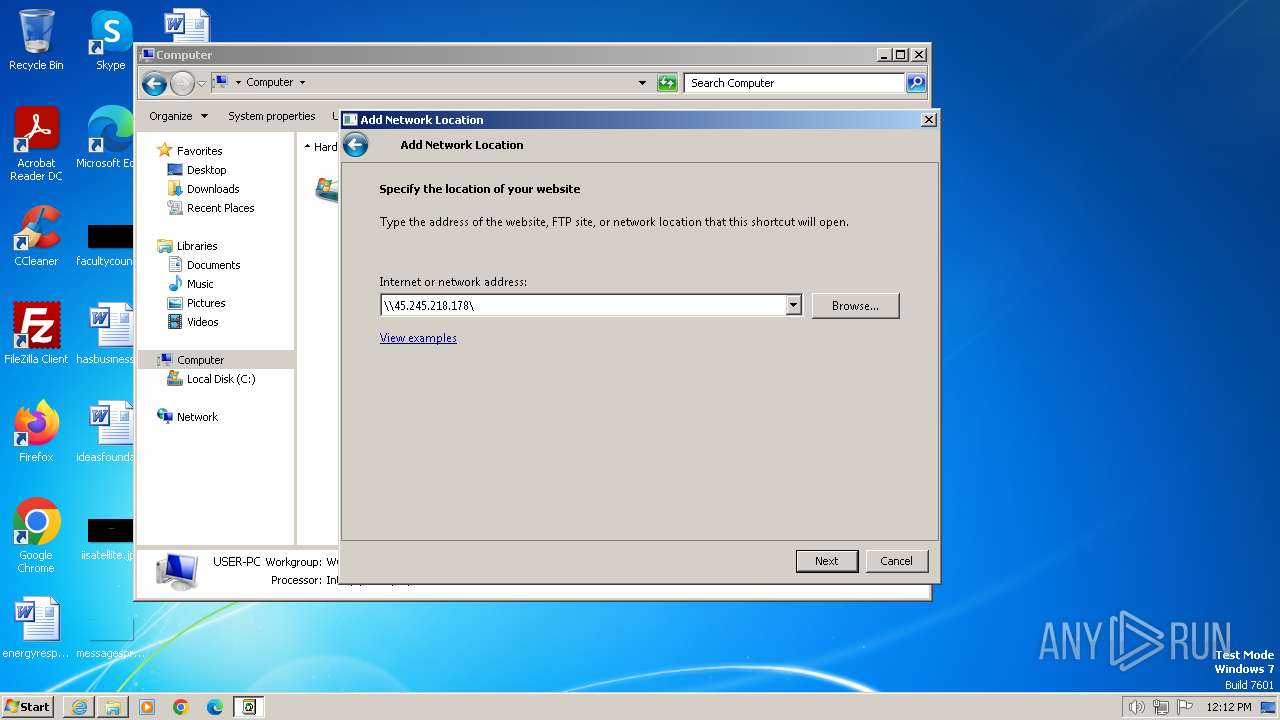
Attempt to connect to SMB server
- System (PID: 4)
SUSPICIOUS
Potential Corporate Privacy Violation
- System (PID: 4)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 1016)
- wmpnscfg.exe (PID: 4052)
Manual execution by a user
- wmpnscfg.exe (PID: 1016)
- wmpnscfg.exe (PID: 4052)
- explorer.exe (PID: 3552)
- rundll32.exe (PID: 1164)
Application launched itself
- iexplore.exe (PID: 4076)
Reads the computer name
- wmpnscfg.exe (PID: 4052)
- wmpnscfg.exe (PID: 1016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4 | System | [System Process] | |||||||||||||
User: SYSTEM Integrity Level: SYSTEM | |||||||||||||||
| 1016 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1164 | "C:\Windows\System32\rundll32.exe" shwebsvc.dll,AddNetPlaceRunDll | C:\Windows\System32\rundll32.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3240 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:4076 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3552 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4052 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4076 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&cad=rja&uact=8&ved=2ahUKEwjtnO37iuCIAxUA1gIHHWZLNNQ4ChAWegQIERAB&url=https%3A%2F%2Fmailarchive.ietf.org%2Farch%2Fmsg%2Fimapext%2FqnhKCZP-teA8k1gEvm-96yHPNHo%2F&usg=AOvVaw2krUV2wwrhoEHlrk8LrmdU&opi=89978449" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
15 748
Read events
15 616
Write events
109
Delete events
23
Modification events
| (PID) Process: | (4076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (4076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (4076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31133700 | |||
| (PID) Process: | (4076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (4076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31133700 | |||
| (PID) Process: | (4076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (4076) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
30
Text files
28
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3240 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\05DDC6AA91765AACACDB0A5F96DF8199 | der | |
MD5:E935BC5762068CAF3E24A2683B1B8A88 | SHA256:A8ACCFCFEB51BD73DF23B91F4D89FF1A9EB7438EF5B12E8AFDA1A6FF1769E89D | |||
| 3240 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:951D351A8E7FAA6258FA5A930A111AAB | SHA256:681B4474467B70341072D56AA4CFB15F43397513D87C7336C0BC1A91B74F0C58 | |||
| 3240 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:4AEEECC932F2362936242C0A087C5171 | SHA256:79E174BF9A296EC8FF95FB3340B8B81B9F7145ADA4FB5911691A1DC971F668ED | |||
| 3240 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\url[1].htm | html | |
MD5:5B43B6942D73782FDB8537FD6794E55C | SHA256:D3CF0C8B207DD19AF2FBA9B900B70835DFAA4A4A101208033ED9EF2599B78DBB | |||
| 3240 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\7EDJZ7US.txt | text | |
MD5:AE6DD4983A1DB27DE51026C6A64FD155 | SHA256:E7CA8A47CF05DD912378A6CD66B52E6C24B18EE3361AD1421F08C9DD07BF7E6B | |||
| 3240 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\bootstrap.bundle.min[1].js | binary | |
MD5:9BA32250DA070FA7FF78F67F67E35552 | SHA256:E5A12B84F9543D5BA3231837C2F2467563405AA66A582B6FC400985F85DF49AD | |||
| 3240 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 3240 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\DDE8B1B7E253A9758EC380BD648952AF_71D00F0D3698C81F2158FA9703C4EFA3 | der | |
MD5:591CA9EDC4038E988B14F4BA01B2AB03 | SHA256:DBB109F379EBD2DA408F5580F8C5574CBE9A8DB39D0A68F079EB46E4FC4B4B41 | |||
| 3240 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:4769C0BF4A5DE4B64E48A88AE6D8B4EC | SHA256:298ECF5D522AD229D70EC650BFA6F096EB5DDE648E0A4A7906811FB1B64A16A4 | |||
| 3240 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:9AAE88934BB14E9F45477722417D990F | SHA256:A65E016468B014325190EFED811BE6E21E62F2F9F61BB37A2DCC2615265B4753 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
66
DNS requests
21
Threats
100
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3240 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
3240 | iexplore.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?669e2a4197a86f29 | unknown | — | — | whitelisted |
3240 | iexplore.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b8207b9ed6f4c065 | unknown | — | — | whitelisted |
3240 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
3240 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEAZxo4%2FaPl1aEI0G7vMpnjs%3D | unknown | — | — | whitelisted |
3240 | iexplore.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
3240 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
3240 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
4076 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4076 | iexplore.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?71ad38700476eb67 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3240 | iexplore.exe | 142.250.184.196:443 | www.google.com | GOOGLE | US | whitelisted |
3240 | iexplore.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
3240 | iexplore.exe | 142.250.184.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3240 | iexplore.exe | 142.250.186.67:80 | c.pki.goog | GOOGLE | US | whitelisted |
3240 | iexplore.exe | 142.250.186.163:80 | o.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.google.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
c.pki.goog |
| whitelisted |
o.pki.goog |
| whitelisted |
mailarchive.ietf.org |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
static.ietf.org |
| whitelisted |
api.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] NTLM Over SMB (NTLMSSP_NEGOTIATE) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] NTLM Over SMB (NTLMSSP_NEGOTIATE) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible NTLM Hash leak over SMB (NTLMSSP_AUTH) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an external SMB server |