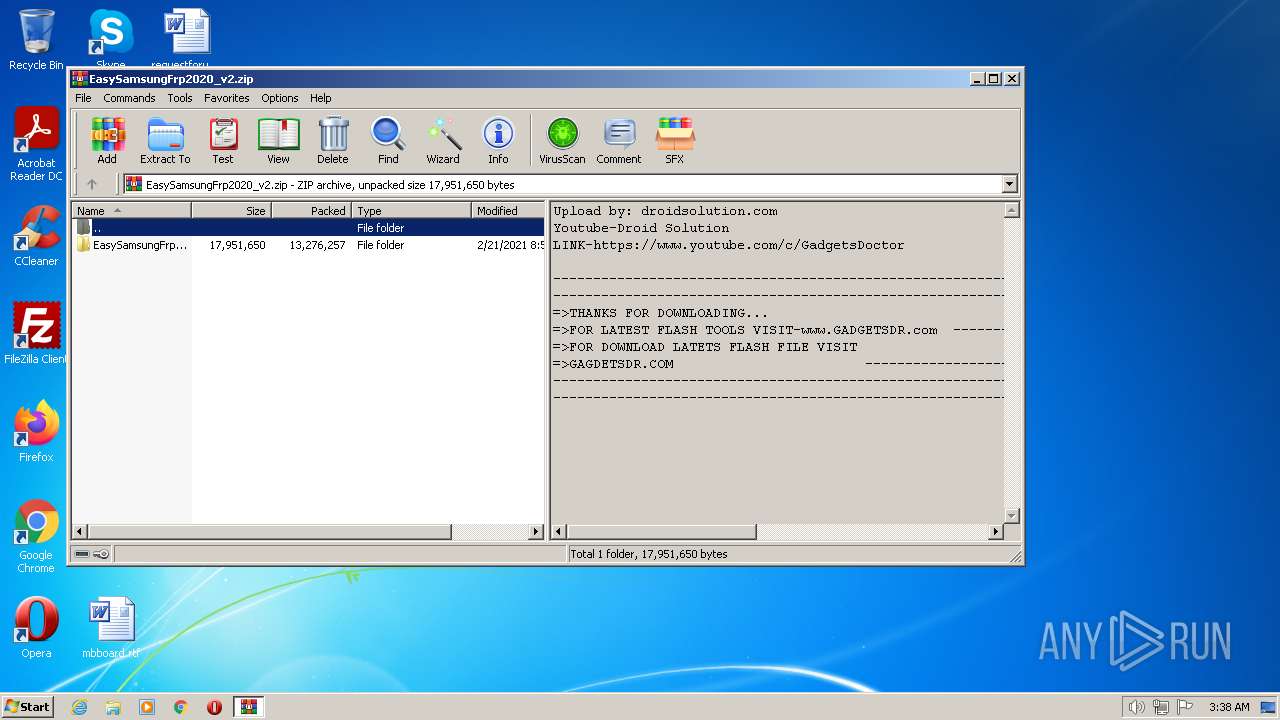
| File name: | EasySamsungFrp2020_v2.zip |
| Full analysis: | https://app.any.run/tasks/ca61f8b8-0587-4552-a4ec-2ed8a0c79003 |
| Verdict: | Malicious activity |
| Analysis date: | February 09, 2023, 03:38:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 9EEBB0D86EEDEF8796E2FAF213893DCB |
| SHA1: | F2197E6D8FF54F79810D71C7A54FFBB052708AAB |
| SHA256: | 70470295B0248D72C5F7ED96A396A4866349DA951105245F15F351F13449FE94 |
| SSDEEP: | 393216:FS6Knvu0BjIKZ2qXDmTLayXz8BgoBOCna:g6Knvw02dLpXfAOua |
MALICIOUS
Detects Cygwin installation
- WinRAR.exe (PID: 3616)
Application was dropped or rewritten from another process
- SamsungFrp2021.exe (PID: 2948)
- SamsungFrp2021.exe (PID: 3644)
SUSPICIOUS
Reads settings of System Certificates
- SamsungFrp2021.exe (PID: 2948)
Reads the Internet Settings
- SamsungFrp2021.exe (PID: 2948)
INFO
Checks supported languages
- SamsungFrp2021.exe (PID: 2948)
The process checks LSA protection
- SamsungFrp2021.exe (PID: 2948)
- iexplore.exe (PID: 3288)
- iexplore.exe (PID: 3268)
Reads the computer name
- SamsungFrp2021.exe (PID: 2948)
Create files in a temporary directory
- iexplore.exe (PID: 3288)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3616)
Reads the machine GUID from the registry
- SamsungFrp2021.exe (PID: 2948)
Application launched itself
- iexplore.exe (PID: 3288)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3616)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
Total processes
46
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
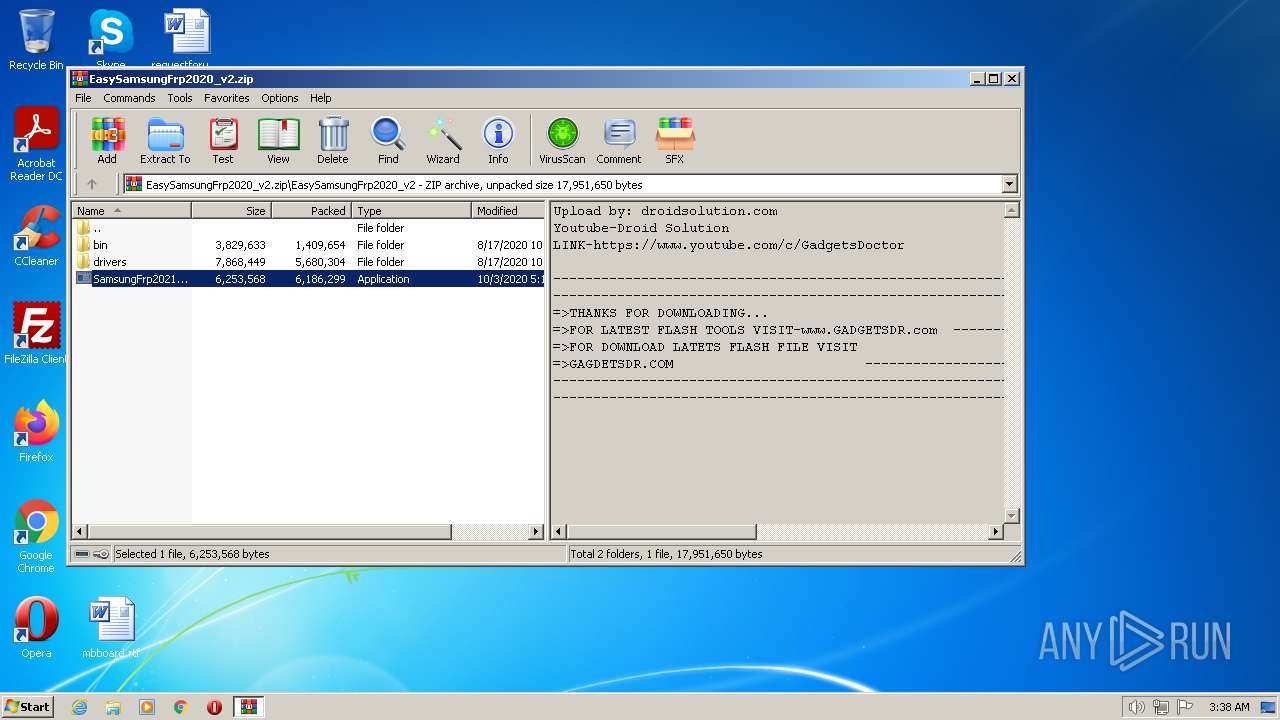
| 2948 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3616.40742\EasySamsungFrp2020_v2\SamsungFrp2021.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3616.40742\EasySamsungFrp2020_v2\SamsungFrp2021.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3268 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3288 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
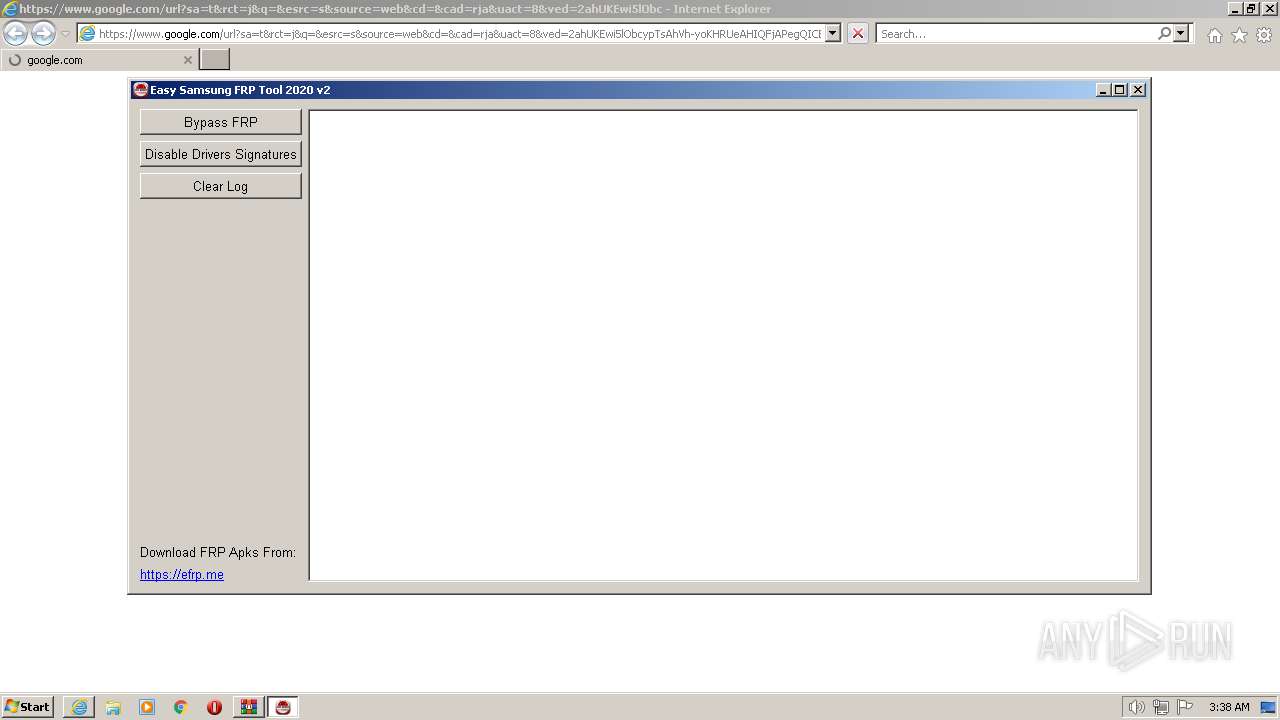
| 3288 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&cad=rja&uact=8&ved=2ahUKEwi5lObcypTsAhVh-yoKHRUeAHIQFjAPegQICBAC&url=https%3A%2F%2Feasy-firmware.com%2Findex.php%3Fa%3Ddownloads%26b%3Dfolder%26id%3D5691&usg=AOvVaw1nTDxuCisH83j8a8AgvYGa | C:\Program Files\Internet Explorer\iexplore.exe | SamsungFrp2021.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3616 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\EasySamsungFrp2020_v2.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3644 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3616.40742\EasySamsungFrp2020_v2\SamsungFrp2021.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3616.40742\EasySamsungFrp2020_v2\SamsungFrp2021.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
42 732
Read events
42 390
Write events
342
Delete events
0
Modification events
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\EasySamsungFrp2020_v2.zip | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
46
Suspicious files
56
Text files
170
Unknown types
64
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3616.40742\EasySamsungFrp2020_v2\bin\cyggcc_s-1.dll | executable | |
MD5:D6C813D4571C2957BA9E5BC652F80966 | SHA256:6E928DF3452D150DF15308977FE24F7C004E49F9D73070313029EC330C06F51C | |||
| 3616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3616.40742\EasySamsungFrp2020_v2\bin\cygusb-1.0.dll | executable | |
MD5:DB1EA9F7283B51EDB4414D123003B5F5 | SHA256:B455CECB7BADB3238647B93E8EA8E6EEA839A525E1E88A88C78E6AAD5E17DF47 | |||
| 3616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3616.40742\EasySamsungFrp2020_v2\drivers\amd64\libusb0_x86.dll | executable | |
MD5:8574627D4A5415C36176BF4AB9058183 | SHA256:3B8C37DB1AF7F30A2BAFF39B587ECF7EDD30027EE3E91D5E596E39DD0F0E3908 | |||
| 3616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3616.40742\EasySamsungFrp2020_v2\drivers\amd64\winusbcoinstaller2.dll | executable | |
MD5:246900CE6474718730ECD4F873234CF5 | SHA256:981A17EFFDDBC20377512DDAEC9F22C2B7067E17A3E2A8CCF82BB7BB7B2420B6 | |||
| 3616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3616.40742\EasySamsungFrp2020_v2\drivers\amd64\WdfCoInstaller01009.dll | executable | |
MD5:4DA5DA193E0E4F86F6F8FD43EF25329A | SHA256:18487B4FF94EDCCC98ED59D9FCA662D4A1331C5F1E14DF8DB3093256DD9F1C3E | |||
| 3616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3616.40742\EasySamsungFrp2020_v2\bin\linux-adk.exe | executable | |
MD5:1C08BD098CA2DA6B5C8BD0FD3BF8D37A | SHA256:7818468C19DBD4746E43B9DF2F4D25F571FFCBF45A8B0202351DD4969AF4C29C | |||
| 3616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3616.40742\EasySamsungFrp2020_v2\drivers\amd64\libusb0.dll | executable | |
MD5:F6A47E2A46C778B7AB915DFADF2C6E06 | SHA256:535B9A18D18E6C15F7B2D9E183A274A52B6ED13E87ECA963C501FBAC445E22F0 | |||
| 3616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3616.40742\EasySamsungFrp2020_v2\drivers\amd64\libusbK_x86.dll | executable | |
MD5:3935EC3158D0E488DA1929B77EDD1633 | SHA256:87CBD1F3BF5AB72089A879DF110263784602A574C0AE83F428DF57AE2F8115DB | |||
| 3616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3616.40742\EasySamsungFrp2020_v2\drivers\amd64\libusbK.sys | executable | |
MD5:ADA2D34031C8981D8A31089733EBFF0D | SHA256:0F86090E2493B77EF3C2169C6B573306685606341519FE3F99EE09BFA12BDF5D | |||
| 3616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3616.40742\EasySamsungFrp2020_v2\drivers\SAMSUNG_Android.cat | cat | |
MD5:C2D76F7BE6872F7EB5F3E8A6B6722589 | SHA256:85BA931146C43FA69AA9F07C49997397763F3F77B64F127220291821730ADBF3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
64
DNS requests
34
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3268 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3268 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEDvaL6%2FDDgY7Ci0DArJ6lpQ%3D | US | der | 471 b | whitelisted |
3268 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEAn%2Fs3f%2Bel%2BsIXMjy8Kdr2g%3D | US | der | 278 b | whitelisted |
3268 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQC%2ByQ3HCGjSjxK2rAEAFE8%2F | US | der | 472 b | whitelisted |
3268 | iexplore.exe | GET | 200 | 13.225.84.175:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
3268 | iexplore.exe | GET | 200 | 13.225.84.175:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
3268 | iexplore.exe | GET | 200 | 13.225.84.142:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEA6PbU42YSuqEUZapH%2Bu0cs%3D | US | der | 471 b | whitelisted |
3268 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3268 | iexplore.exe | GET | 200 | 104.18.32.68:80 | http://crl.comodoca.com/AAACertificateServices.crl | US | der | 506 b | whitelisted |
3268 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCvudpJRmxHQBIx2po2dhGU | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2948 | SamsungFrp2021.exe | 104.26.3.235:443 | code.eftp-server.com | CLOUDFLARENET | US | unknown |
3268 | iexplore.exe | 95.140.236.128:80 | ctldl.windowsupdate.com | LLNW | US | malicious |
3268 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
3268 | iexplore.exe | 142.250.185.68:443 | www.google.com | GOOGLE | US | whitelisted |
3268 | iexplore.exe | 172.217.16.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
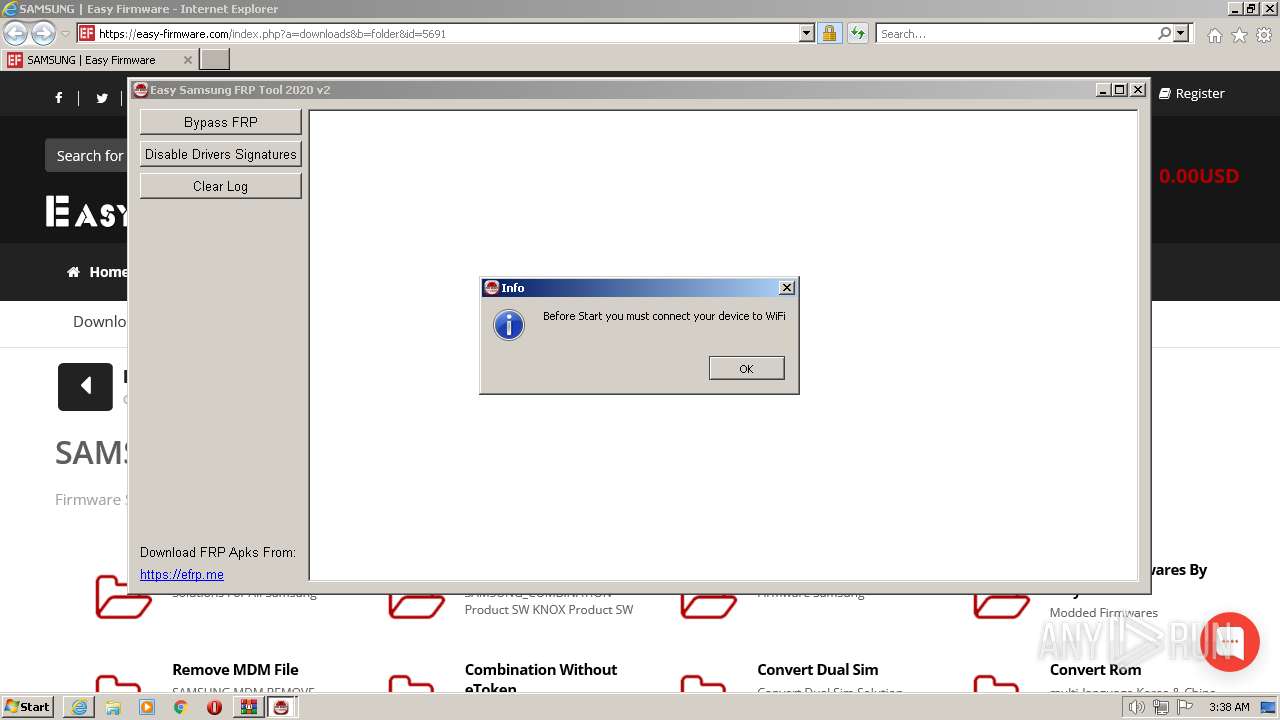
3268 | iexplore.exe | 104.26.14.4:443 | easy-firmware.com | CLOUDFLARENET | US | unknown |
3288 | iexplore.exe | 204.79.197.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3268 | iexplore.exe | 142.250.185.136:443 | www.googletagmanager.com | GOOGLE | US | suspicious |
3268 | iexplore.exe | 172.217.18.10:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
3288 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
code.eftp-server.com |
| unknown |
www.google.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
easy-firmware.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |