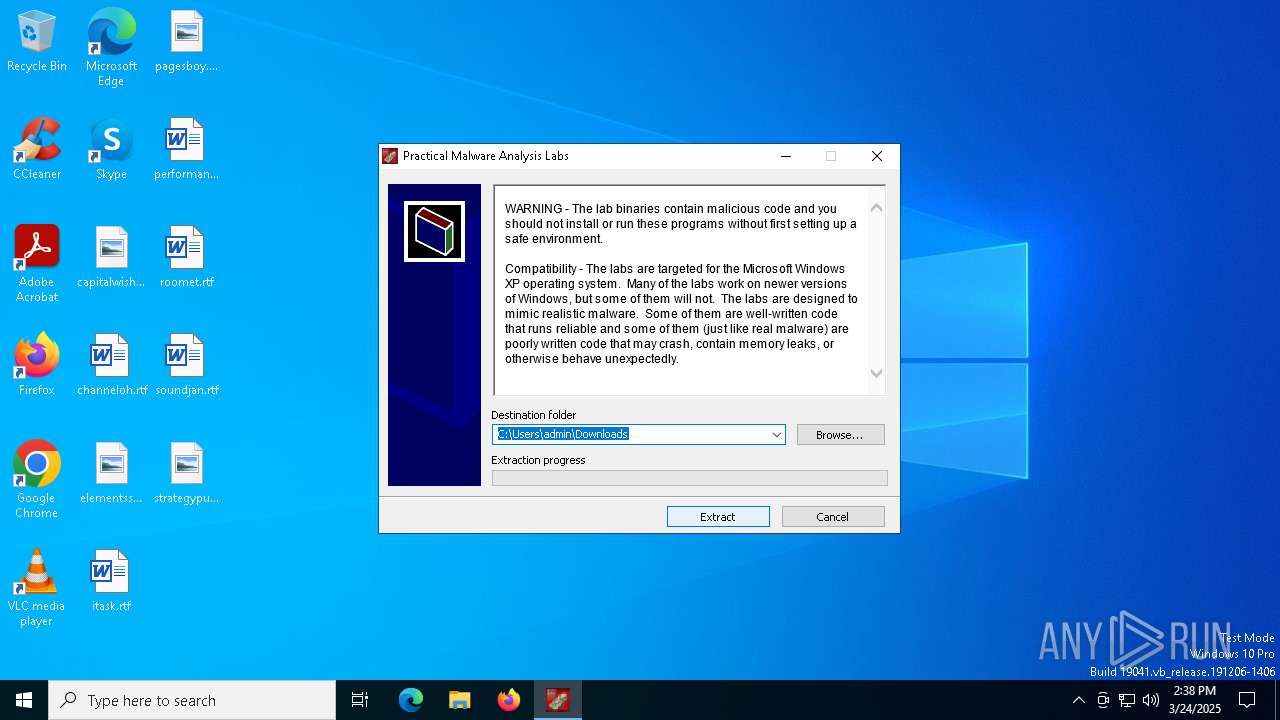
| download: | /Brandon-Everhart/Practical-Malware-Analysis/raw/refs/heads/master/PracticalMalwareAnalysis-Labs.exe |
| Full analysis: | https://app.any.run/tasks/c2d7474c-a7a1-47b0-a53d-8302125a16f9 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 14:38:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive, 5 sections |
| MD5: | 9D9C90870BC46AD65BAF0F3977E7590F |
| SHA1: | DEC5842D07BBD00EDF564FE27C14118EC9ECC77F |
| SHA256: | 704138BEC89CF9E7F00FBCE100DBC09CF133D16DC0203806392F0E153C43C68C |
| SSDEEP: | 24576:uxaVxr53s2QByK9VHFsZ+Ykyxm7g8LVYD/rh6m6er9wgwGe66hXS:u6QXHFsrxKY70neru/66dS |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 6036)
- cmd.exe (PID: 3192)
SUSPICIOUS
Reads Microsoft Outlook installation path
- PracticalMalwareAnalysis-Labs.exe (PID: 5332)
Reads security settings of Internet Explorer
- PracticalMalwareAnalysis-Labs.exe (PID: 5332)
There is functionality for taking screenshot (YARA)
- PracticalMalwareAnalysis-Labs.exe (PID: 5332)
Reads Internet Explorer settings
- PracticalMalwareAnalysis-Labs.exe (PID: 5332)
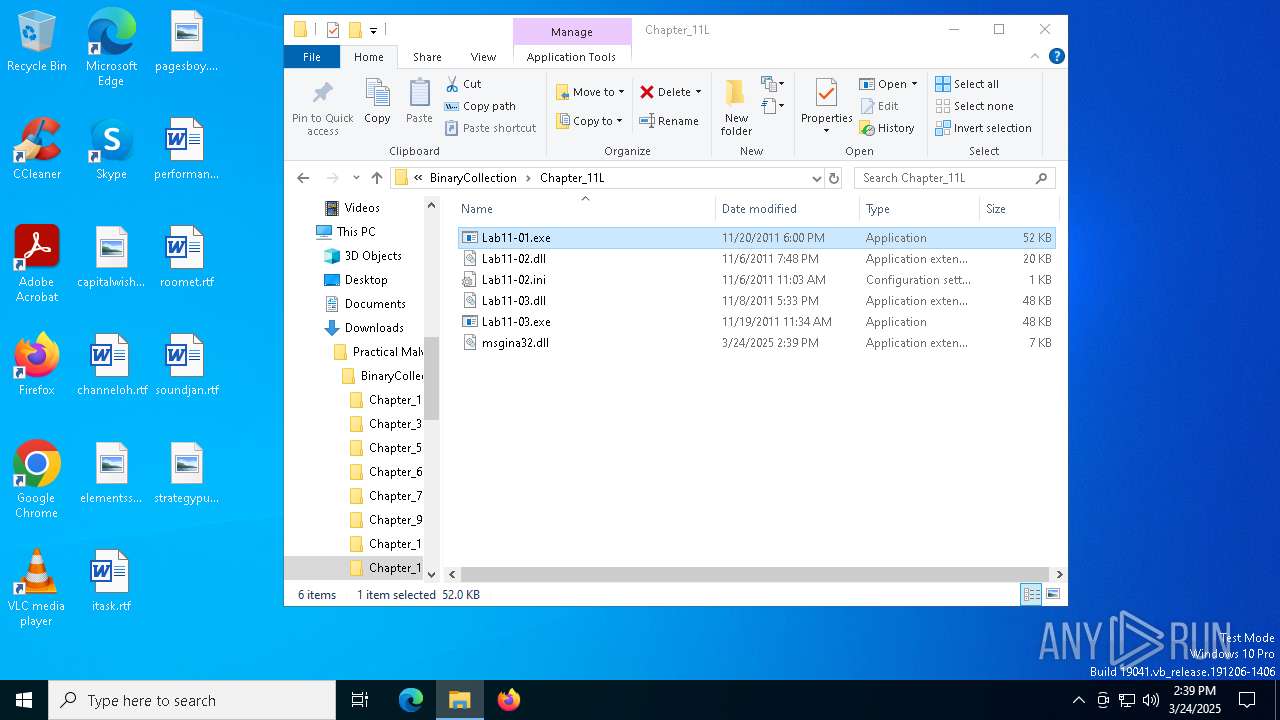
Process drops legitimate windows executable
- PracticalMalwareAnalysis-Labs.exe (PID: 5332)
Executable content was dropped or overwritten
- PracticalMalwareAnalysis-Labs.exe (PID: 5332)
- Lab11-01.exe (PID: 8164)
Drops a system driver (possible attempt to evade defenses)
- PracticalMalwareAnalysis-Labs.exe (PID: 5332)
Starts CMD.EXE for commands execution
- Lab11-03.exe (PID: 8000)
INFO
Reads the computer name
- PracticalMalwareAnalysis-Labs.exe (PID: 5332)
Checks supported languages
- PracticalMalwareAnalysis-Labs.exe (PID: 5332)
The sample compiled with english language support
- PracticalMalwareAnalysis-Labs.exe (PID: 5332)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 456)
- BackgroundTransferHost.exe (PID: 7624)
Manual execution by a user
- Lab12-04.exe (PID: 7052)
- Lab11-01.exe (PID: 8164)
- Lab11-03.exe (PID: 8000)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 456)
Checks proxy server information
- PracticalMalwareAnalysis-Labs.exe (PID: 5332)
The sample compiled with chinese language support
- PracticalMalwareAnalysis-Labs.exe (PID: 5332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:01:09 13:44:06+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 72704 |
| InitializedDataSize: | 25600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb3c1 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
155
Monitored processes
19
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3192 | C:\WINDOWS\system32\cmd.exe /c net start cisvc | C:\Windows\SysWOW64\cmd.exe | — | Lab11-03.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4448 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Lab11-03.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5332 | "C:\Users\admin\Downloads\PracticalMalwareAnalysis-Labs.exe" | C:\Users\admin\Downloads\PracticalMalwareAnalysis-Labs.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5720 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6036 | net start cisvc | C:\Windows\SysWOW64\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6048 | C:\WINDOWS\system32\net1 start cisvc | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6800 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7052 | "C:\Users\admin\Downloads\Practical Malware Analysis Labs\BinaryCollection\Chapter_12L\Lab12-04.exe" | C:\Users\admin\Downloads\Practical Malware Analysis Labs\BinaryCollection\Chapter_12L\Lab12-04.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
Total events
2 682
Read events
2 661
Write events
21
Delete events
0
Modification events
| (PID) Process: | (5332) PracticalMalwareAnalysis-Labs.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5332) PracticalMalwareAnalysis-Labs.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5332) PracticalMalwareAnalysis-Labs.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (8016) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8016) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (8016) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (456) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (456) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (456) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6800) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
66
Suspicious files
10
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5332 | PracticalMalwareAnalysis-Labs.exe | C:\Users\admin\Downloads\Practical Malware Analysis Labs\BinaryCollection\Chapter_11L\Lab11-02.dll | executable | |
MD5:BE4F4B9E88F2E1B1C38E0A0858EB3DD9 | SHA256:DF899256C4A9FC0E550C62B84AB9CB8ACD8D18683F0A41C98BA83F0487D4766E | |||
| 5332 | PracticalMalwareAnalysis-Labs.exe | C:\Users\admin\Downloads\Practical Malware Analysis Labs\BinaryCollection\Chapter_10L\Lab10-03.exe | executable | |
MD5:F72D773F13CEB6B842A9D29C56F8880F | SHA256:D66E15EEA51EBD4BFD13F8C97646253740B1E6A99328D22232FD01AE13EF5D05 | |||
| 5332 | PracticalMalwareAnalysis-Labs.exe | C:\Users\admin\Downloads\Practical Malware Analysis Labs\BinaryCollection\Chapter_11L\Lab11-03.exe | executable | |
MD5:18EC5BECFA3991FB654E105BAFBD5A4B | SHA256:BF023FF344EFE2DB0E0A963869368F0EF352764666BC368AD61B7A4C1D9F5975 | |||
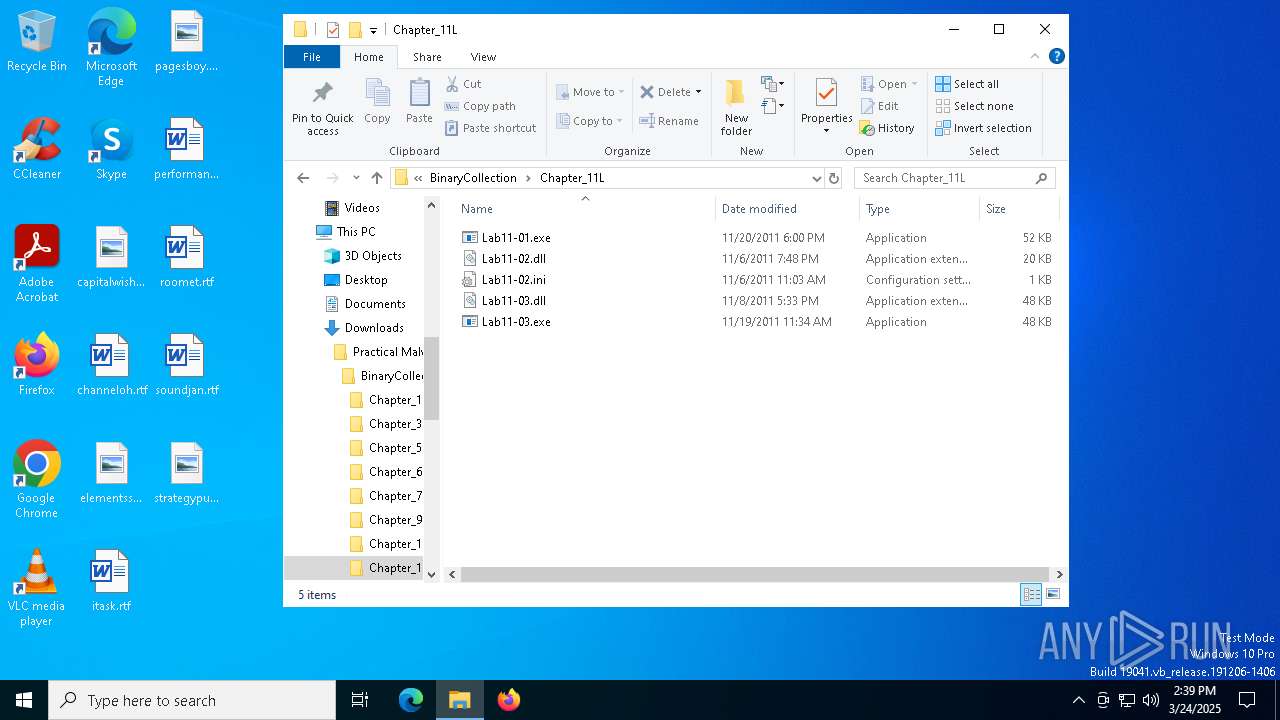
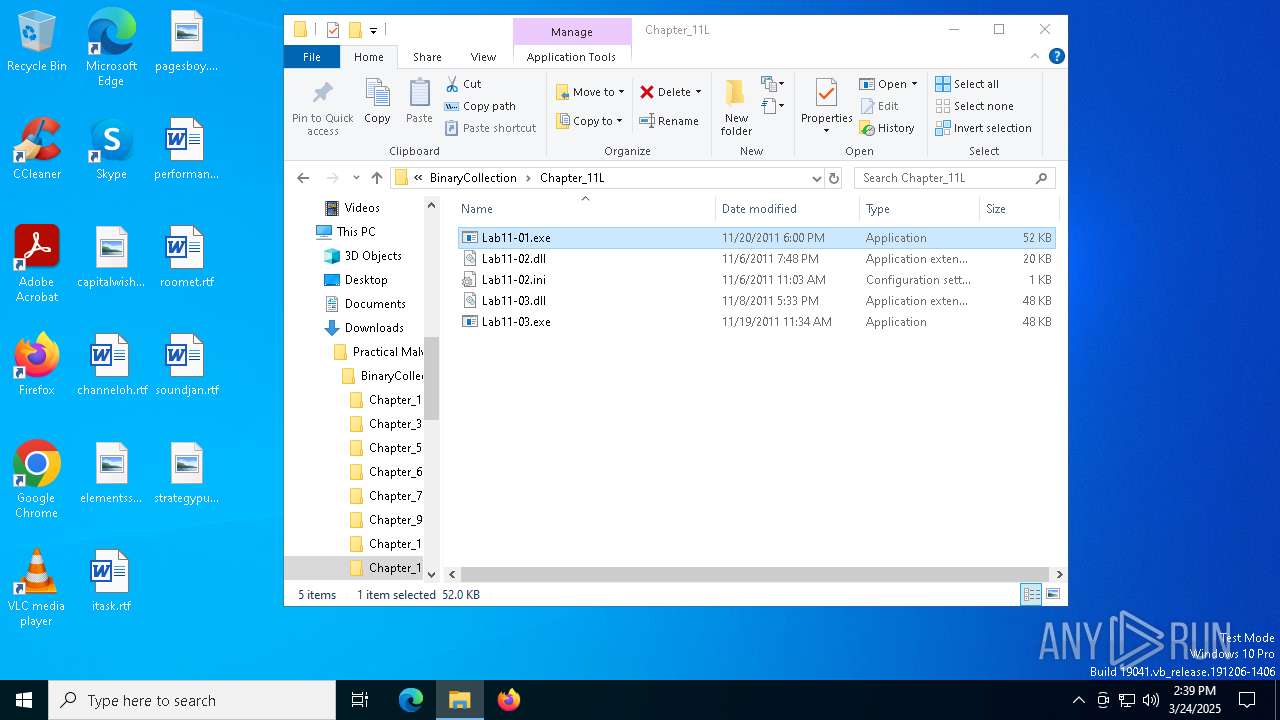
| 5332 | PracticalMalwareAnalysis-Labs.exe | C:\Users\admin\Downloads\Practical Malware Analysis Labs\BinaryCollection\Chapter_11L\Lab11-01.exe | executable | |
MD5:A9C55BB87A7C5C3C923C4FA12940E719 | SHA256:57D8D248A8741176348B5D12DCF29F34C8F48EDE0CA13C30D12E5BA0384056D7 | |||
| 5332 | PracticalMalwareAnalysis-Labs.exe | C:\Users\admin\Downloads\Practical Malware Analysis Labs\BinaryCollection\Chapter_10L\Lab10-01.sys | executable | |
MD5:3D3D1A8145E3237183984FAED04E052E | SHA256:D12A2C116A12993CFCF2F432A4FE53F8F6B3686E33ED8F7E8FF4628A37BD616E | |||
| 5332 | PracticalMalwareAnalysis-Labs.exe | C:\Users\admin\Downloads\Practical Malware Analysis Labs\BinaryCollection\Chapter_11L\Lab11-03.dll | executable | |
MD5:BBD65FCAD68E5A3CD1457E2EE05D1F2E | SHA256:F11FA868AC3DEE1E5FBD985FE15BA6D34C7EC0ABB47BABE0D34A35514C49C86A | |||
| 5332 | PracticalMalwareAnalysis-Labs.exe | C:\Users\admin\Downloads\Practical Malware Analysis Labs\BinaryCollection\Chapter_10L\Lab10-03.sys | executable | |
MD5:CF91A08F3D7A2875D6120C16B7C55398 | SHA256:59D09B747441ED35E0FC0B5B352B4C66532F1FDD4646457A5EA972F067A55B30 | |||
| 5332 | PracticalMalwareAnalysis-Labs.exe | C:\Users\admin\Downloads\Practical Malware Analysis Labs\BinaryCollection\Chapter_11L\Lab11-02.ini | binary | |
MD5:B61964305851A7AB4179067C231B4D97 | SHA256:0493C7167AE07704ED41FE4D43333165F3167ACA8547B6F1D2C67592ECCC6FA2 | |||
| 5332 | PracticalMalwareAnalysis-Labs.exe | C:\Users\admin\Downloads\Practical Malware Analysis Labs\BinaryCollection\Chapter_10L\Lab10-01.exe | executable | |
MD5:795F093A536F118FB4C34FCEDFA42165 | SHA256:E55CFA92ACC2FAC8B3B41002EBBEF343BFDB61ABF876E9C713F323E143D5E451 | |||
| 5332 | PracticalMalwareAnalysis-Labs.exe | C:\Users\admin\Downloads\Practical Malware Analysis Labs\BinaryCollection\Chapter_12L\Lab12-01.dll | executable | |
MD5:A6FB0D8FDEA1C15AFBA7A5DDB3D2867B | SHA256:0EA89A83B84B8D20E259BACB6B0D1B176C8327F097C54749AE832981F2A0095A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7280 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
456 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7228 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7228 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4220 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
7280 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7280 | backgroundTaskHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
456 | BackgroundTransferHost.exe | 92.123.104.37:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
456 | BackgroundTransferHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |