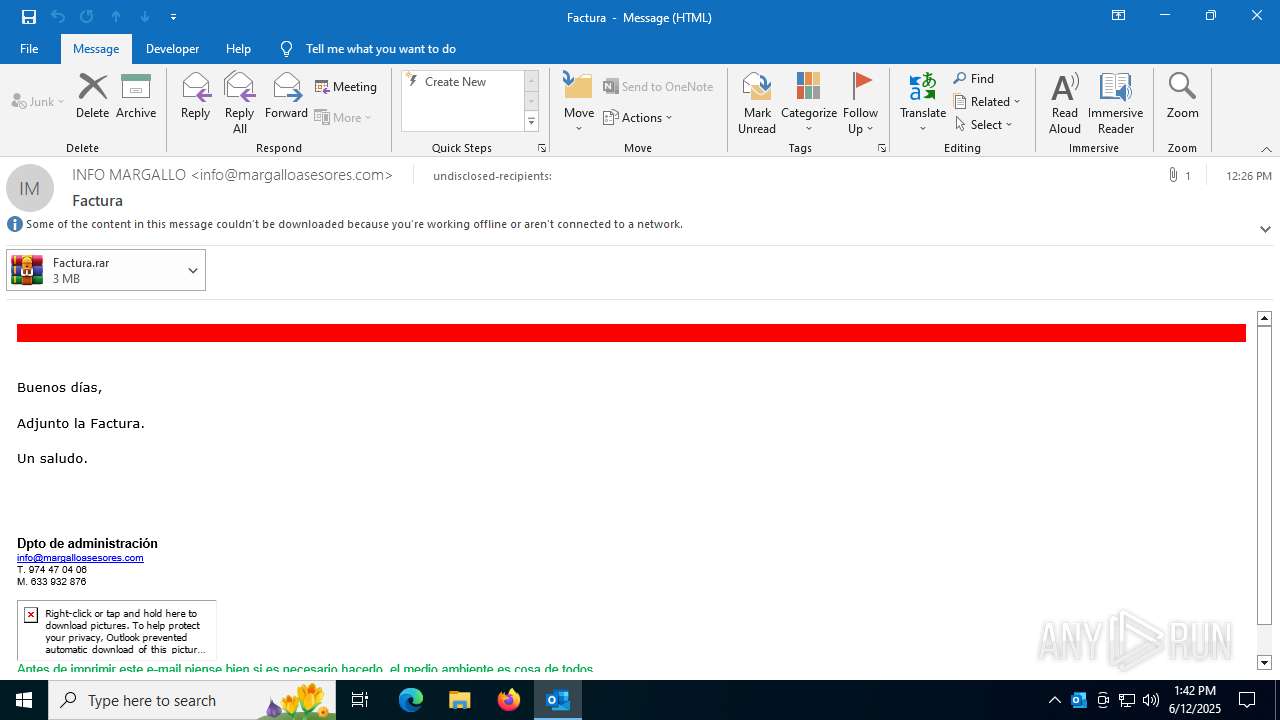
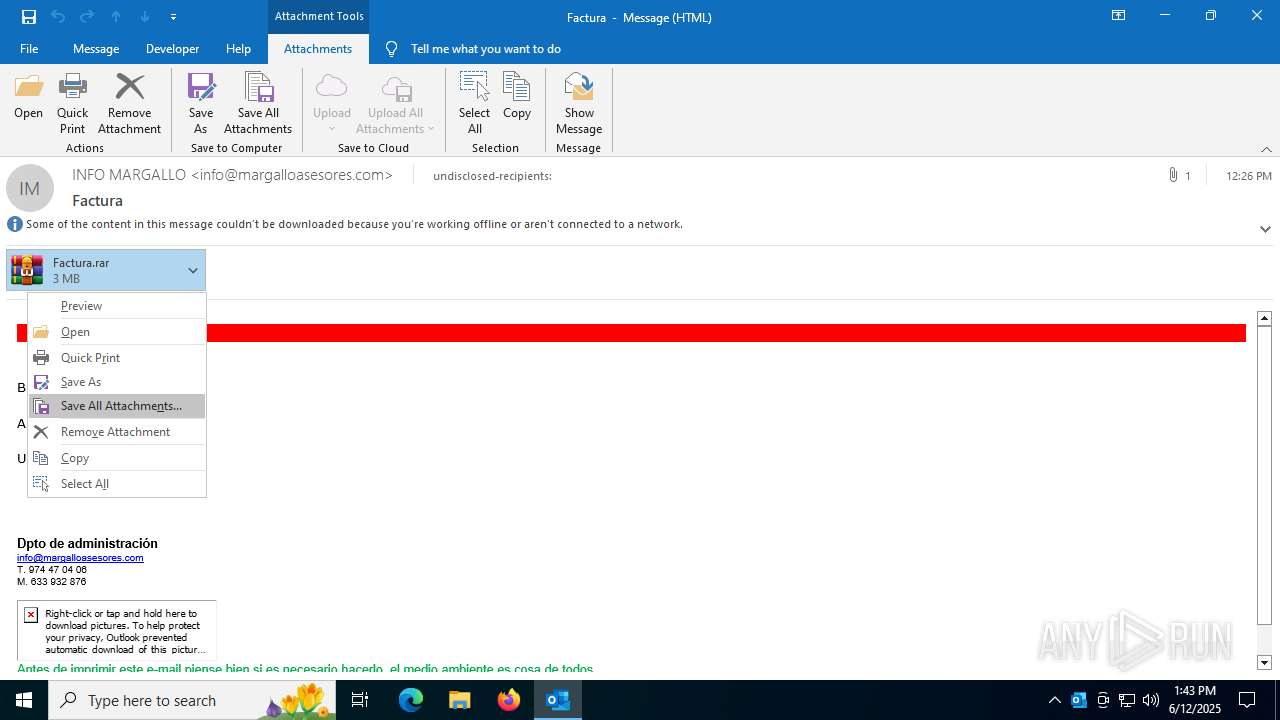
| File name: | 531418e9-36a3-4581-5b44-59364d85a0ca.eml |
| Full analysis: | https://app.any.run/tasks/61e01084-e442-4bb7-a725-1667128573ce |
| Verdict: | Malicious activity |
| Analysis date: | June 12, 2025, 13:42:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, Unicode text, UTF-8 text, with CRLF line terminators |
| MD5: | CD11E9D7B11E5FC5E69B04791E814E97 |
| SHA1: | 3125670E23C0F8DD0E1825CB8869B2AA9D0E669D |
| SHA256: | 7040AC3FCBB2E9641BF6779974AB779F39004D01312826999EB87C354A0F9686 |
| SSDEEP: | 49152:b20G/L4CCFzIcbCrBtVeQh8JZqXM8jxrZRvv12wtZEX:J |
MALICIOUS
Generic archive extractor
- OUTLOOK.EXE (PID: 3820)
Starts NET.EXE for service management
- msiexec.exe (PID: 7160)
- net.exe (PID: 6840)
Bypass execution policy to execute commands
- powershell.exe (PID: 6004)
Changes powershell execution policy (Bypass)
- AgentPackageAgentInformation.exe (PID: 5012)
SUSPICIOUS
Process drops legitimate windows executable
- OUTLOOK.EXE (PID: 3820)
- WinRAR.exe (PID: 5348)
- msiexec.exe (PID: 3668)
- AteraAgent.exe (PID: 1380)
Executes as Windows Service
- VSSVC.exe (PID: 3756)
- AteraAgent.exe (PID: 1380)
- AteraAgent.exe (PID: 6220)
Executable content was dropped or overwritten
- rundll32.exe (PID: 420)
- rundll32.exe (PID: 3832)
- rundll32.exe (PID: 5008)
- rundll32.exe (PID: 4680)
- AteraAgent.exe (PID: 1380)
- SplashtopStreamer.exe (PID: 7524)
- csc.exe (PID: 7564)
- PreVerCheck.exe (PID: 7704)
Potential Corporate Privacy Violation
- rundll32.exe (PID: 3832)
- AteraAgent.exe (PID: 1380)
- AgentPackageAgentInformation.exe (PID: 2596)
- AgentPackageAgentInformation.exe (PID: 1964)
- AteraAgent.exe (PID: 6220)
- AgentPackageMonitoring.exe (PID: 7272)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 7160)
Restarts service on failure
- sc.exe (PID: 3644)
- sc.exe (PID: 4828)
ATERAAGENT has been detected
- AteraAgent.exe (PID: 5012)
- AteraAgent.exe (PID: 1380)
- AteraAgent.exe (PID: 6220)
Starts SC.EXE for service management
- AteraAgent.exe (PID: 1380)
- AteraAgent.exe (PID: 6220)
The process hides Powershell's copyright startup banner
- AgentPackageAgentInformation.exe (PID: 5012)
Starts POWERSHELL.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 5012)
The process bypasses the loading of PowerShell profile settings
- AgentPackageAgentInformation.exe (PID: 5012)
CSC.EXE is used to compile C# code
- csc.exe (PID: 7564)
The process executes VB scripts
- cmd.exe (PID: 7660)
Starts CMD.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 5012)
The process executes Powershell scripts
- AgentPackageAgentInformation.exe (PID: 5012)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5348)
- msiexec.exe (PID: 3668)
Manual execution by a user
- WinRAR.exe (PID: 5348)
- msiexec.exe (PID: 7072)
- notepad++.exe (PID: 5480)
Checks proxy server information
- msiexec.exe (PID: 7072)
Creates files or folders in the user directory
- msiexec.exe (PID: 7072)
Reads the software policy settings
- msiexec.exe (PID: 7072)
Reads the computer name
- msiexec.exe (PID: 3668)
Checks supported languages
- msiexec.exe (PID: 3668)
Manages system restore points
- SrTasks.exe (PID: 3460)
The sample compiled with english language support
- rundll32.exe (PID: 420)
- rundll32.exe (PID: 3832)
- rundll32.exe (PID: 5008)
- rundll32.exe (PID: 4680)
- SplashtopStreamer.exe (PID: 7524)
- AteraAgent.exe (PID: 1380)
- PreVerCheck.exe (PID: 7704)
- msiexec.exe (PID: 3668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
194
Monitored processes
52
Malicious processes
3
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | rundll32.exe "C:\WINDOWS\Installer\MSI30DF.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1585468 2 AlphaControlAgentInstallation!AlphaControlAgentInstallation.CustomActions.GenerateAgentId | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageSTRemote\AgentPackageSTRemote.exe" b723f852-a37b-42c8-98a7-3f64dcd8c553 "4ce42ce1-010a-4a61-9e27-47fd2954f3f2" agent-api.atera.com/Production 443 or8ixLi90Mf "install eyJSbW1Db2RlIjoiaFpDREZQaEs3NW1KIiwiUmVxdWVzdFBlcm1pc3Npb25PcHRpb24iOjMsIlJlcXVpcmVQYXNzd29yZE9wdGlvbiI6bnVsbCwiUGFzc3dvcmQiOm51bGx9" 001Q300000TdQzlIAF | C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageSTRemote\AgentPackageSTRemote.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Company: Atera Networks Integrity Level: SYSTEM Description: AgentPackageSTRemote Version: 25.1.0.0 Modules
| |||||||||||||||
| 1380 | "C:\Program Files (x86)\ATERA Networks\AteraAgent\AteraAgent.exe" | C:\Program Files (x86)\ATERA Networks\AteraAgent\AteraAgent.exe | services.exe | ||||||||||||
User: SYSTEM Company: ATERA Networks Ltd. Integrity Level: SYSTEM Description: AteraAgent Version: 1.8.7.2 Modules
| |||||||||||||||
| 1800 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1816 | "TaskKill.exe" /f /im AteraAgent.exe | C:\Windows\SysWOW64\taskkill.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1964 | "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageAgentInformation\AgentPackageAgentInformation.exe" b723f852-a37b-42c8-98a7-3f64dcd8c553 "b08687d2-0359-4356-b30b-c325af4ae525" agent-api.atera.com/Production 443 or8ixLi90Mf "minimalIdentification" 001Q300000TdQzlIAF | C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageAgentInformation\AgentPackageAgentInformation.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Company: Atera Networks Integrity Level: SYSTEM Description: AgentPackageAgentInformation Exit code: 0 Version: 40.5.0.0 Modules
| |||||||||||||||
| 2272 | C:\WINDOWS\system32\net1 STOP AteraAgent | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2596 | "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageAgentInformation\AgentPackageAgentInformation.exe" b723f852-a37b-42c8-98a7-3f64dcd8c553 "4e8474ff-d415-4d77-ae90-9c683faa6580" agent-api.atera.com/Production 443 or8ixLi90Mf "minimalIdentification" 001Q300000TdQzlIAF | C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageAgentInformation\AgentPackageAgentInformation.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Company: Atera Networks Integrity Level: SYSTEM Description: AgentPackageAgentInformation Exit code: 0 Version: 40.5.0.0 Modules
| |||||||||||||||
| 3196 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AgentPackageSTRemote.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3460 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
52 919
Read events
51 201
Write events
1 560
Delete events
158
Modification events
| (PID) Process: | (3820) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\3820 |
| Operation: | write | Name: | 0 |
Value: 0B0E10DDCA016F208D6648B00B024D3BB6ED5F230046BA8285AEFEF3F6ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511EC1DD2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (3820) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (3820) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (3820) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (3820) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (3820) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (3820) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (3820) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (3820) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (3820) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
80
Suspicious files
40
Text files
45
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3820 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 3820 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olk6011.tmp | ini | |
MD5:7D52F2A2E5719CC0C231D71F19CBA372 | SHA256:F6897F1F3BE3E7C19280259A76141A880FA4B57C90D6931018D7EAF280075E3D | |||
| 3820 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:A1C8813AE4D08F36043D0344BA1F237A | SHA256:72F5CA4721BB0ABEFF2FCA24E7DF81867A054BB6647C4D102855199A0BA88A44 | |||
| 3820 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:E7EA5D463CFB45AC5EA9D59B73793886 | SHA256:6C617FB3E692722E1812E25F2ABD5169186585997F8134E2D21B14BF6049AE03 | |||
| 3668 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3820 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | der | |
MD5:B04055911AE289E29FAA3D5511A6A3EF | SHA256:B72FDE954D02891648C07090D70EE7E4847E643665AC3625F76C2380C063420C | |||
| 3820 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_892E423CC71AFF408967DD42E9E44D47.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 3820 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:C65AF9EDD36652ED9C25E92A2112E7E0 | SHA256:06A6A6F974E678132458E1663AC8FE42C2D747DD91555BD27C072A5AAF2B49A8 | |||
| 3820 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:BB4F9FD6C6EDE859EFF0F51E2A25769D | SHA256:873DEEF6C4ACAEF1B645AC4CCC24B06F1D26AFF0A0EDC15B4E01504DB127BF5A | |||
| 3820 | OUTLOOK.EXE | C:\Users\admin\Downloads\Factura.rar:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
63
DNS requests
31
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1200 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3820 | OUTLOOK.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
4808 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4808 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7072 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
7072 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
7072 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAnTy%2FhDMohv9omwS69%2Fdow%3D | unknown | — | — | whitelisted |
5012 | AteraAgent.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2468 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3820 | OUTLOOK.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3820 | OUTLOOK.EXE | 2.16.168.119:443 | omex.cdn.office.net | Akamai International B.V. | RU | whitelisted |
3820 | OUTLOOK.EXE | 52.111.231.8:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2336 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1200 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3832 | rundll32.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
1380 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
1380 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
1380 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
1380 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
2596 | AgentPackageAgentInformation.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
2596 | AgentPackageAgentInformation.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
1964 | AgentPackageAgentInformation.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
1380 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
6220 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
AgentPackageMonitoring.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\x64\SQLite.Interop.dll"...
|
SplashtopStreamer.exe | [7524]2025-06-12 13:44:06 [CUnPack::UnPackFiles] FreeSpace:232954384384 FileSize:60981760 (Last=0) |
SplashtopStreamer.exe | [7524]2025-06-12 13:44:06 [CUtility::OSInfo] OS 10.0(19045) x64:1 (Last=0) |
SplashtopStreamer.exe | [7524]2025-06-12 13:44:06 [CUnPack::FindHeader] Name:C:\WINDOWS\TEMP\SplashtopStreamer.exe (Last=0) |