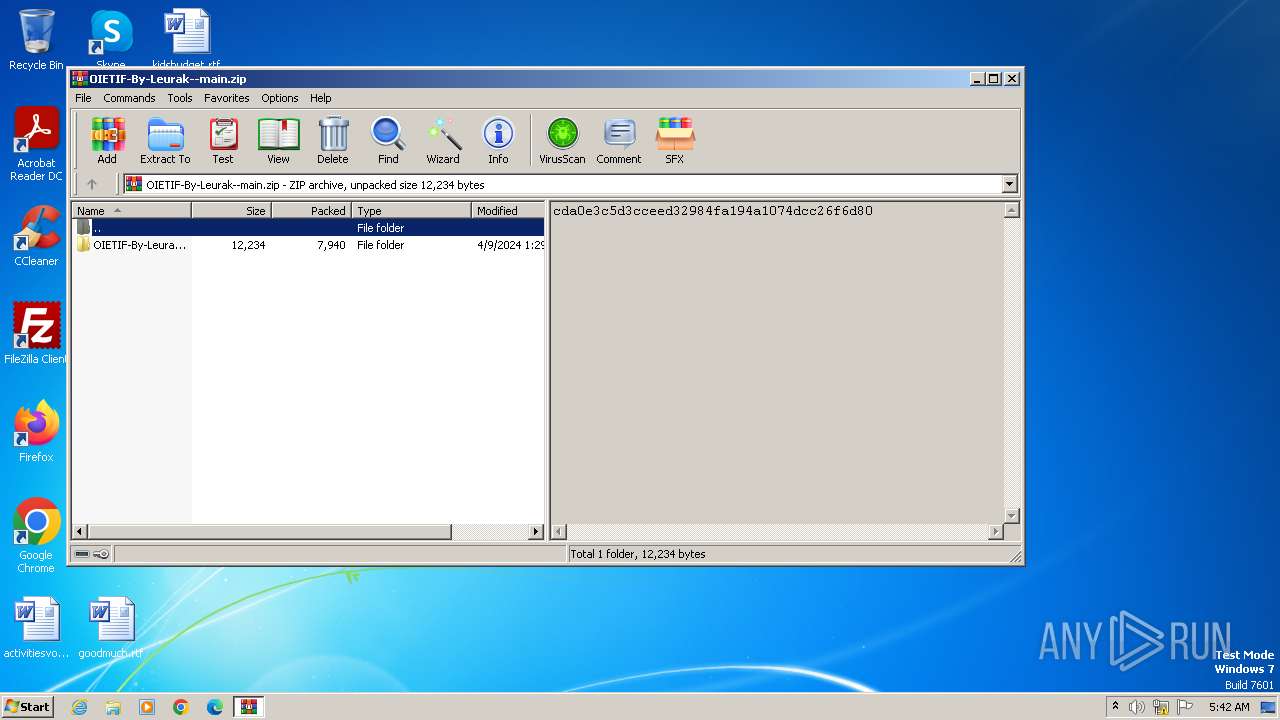
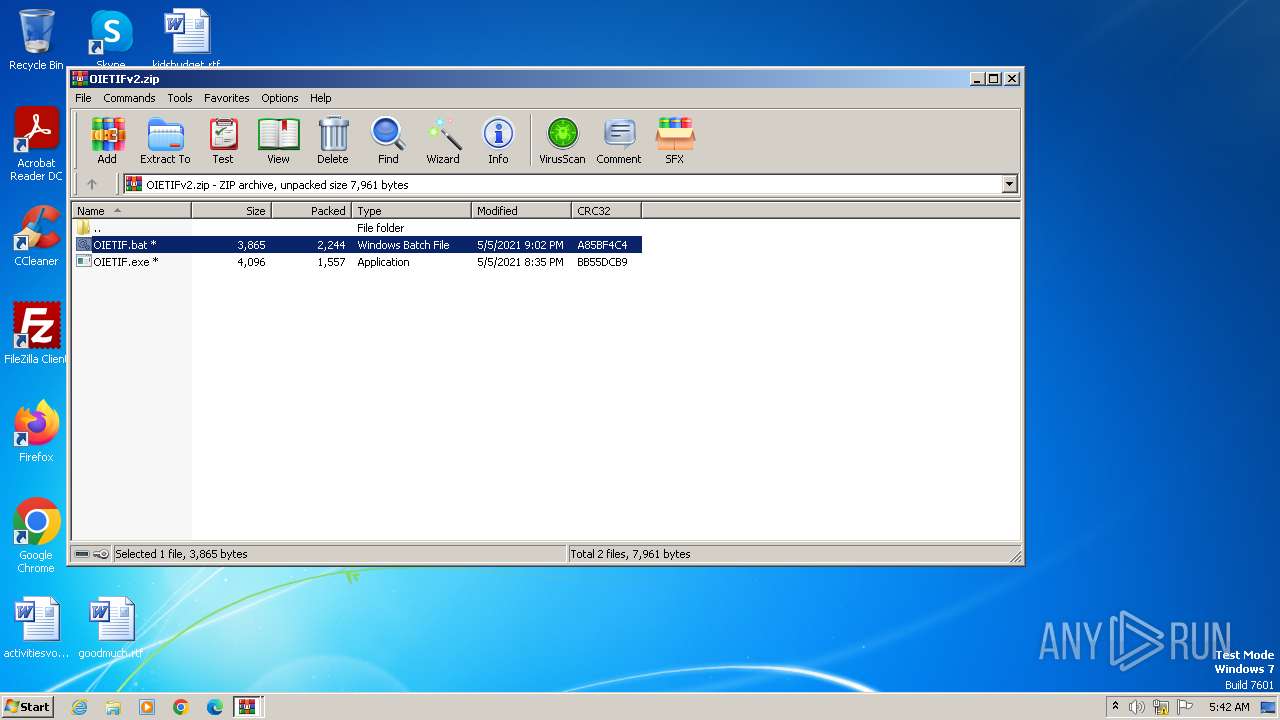
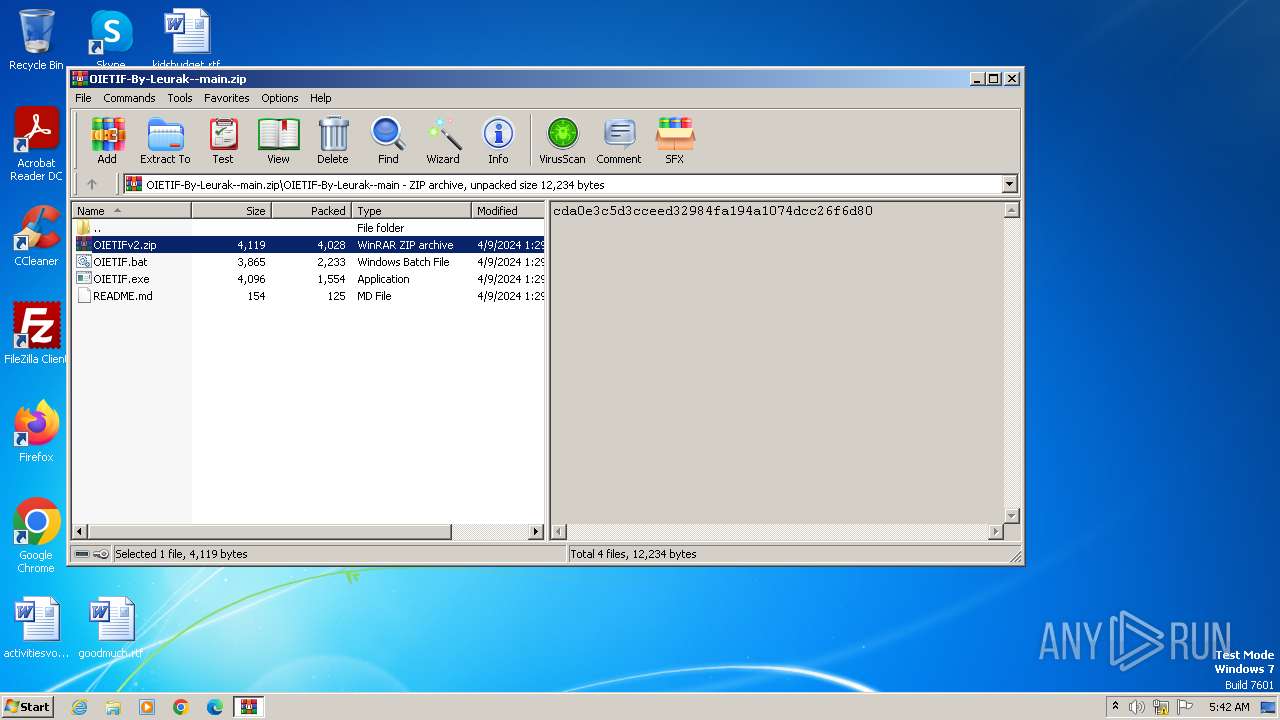
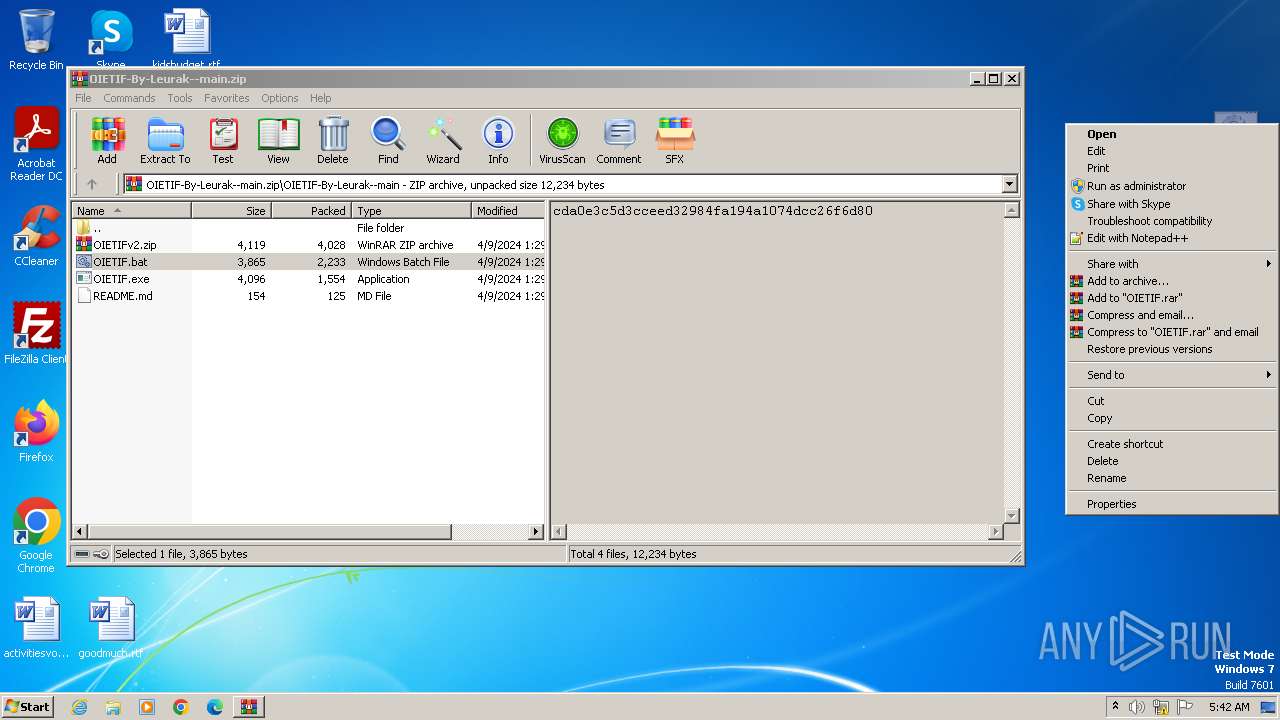
| File name: | OIETIF-By-Leurak--main.zip |
| Full analysis: | https://app.any.run/tasks/ed1139be-44f3-433f-bebd-55904423f604 |
| Verdict: | Malicious activity |
| Analysis date: | May 07, 2024, 04:41:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | BAF78928EEFB4FC9703CC4ECC050792D |
| SHA1: | 7FECA27B70ABEDB757BAD2ED70CA41852762751F |
| SHA256: | 703704EE82AF4F2AE94045447E5FFF226897CEA836632599F86D6229756052A7 |
| SSDEEP: | 192:56/kAmUfHGMUvrmHErhBy/+HY58F/n3fAqEPDp7IUdy5j3a/naq01ArnuuZ8PpFO:om6HGiOBy0nI/97byRqteo |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3984)
Uses base64 encoding (SCRIPT)
- cscript.exe (PID: 728)
Gets a file object corresponding to the file in a specified path (SCRIPT)
- cscript.exe (PID: 728)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3984)
The process executes JS scripts
- cmd.exe (PID: 308)
Creates XML DOM element (SCRIPT)
- cscript.exe (PID: 728)
Sets XML DOM element text (SCRIPT)
- cscript.exe (PID: 728)
Script creates XML DOM node (SCRIPT)
- cscript.exe (PID: 728)
Application launched itself
- WinRAR.exe (PID: 3984)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 728)
Saves data to a binary file (SCRIPT)
- cscript.exe (PID: 728)
Writes binary data to a Stream object (SCRIPT)
- cscript.exe (PID: 728)
Creates a Folder object (SCRIPT)
- cscript.exe (PID: 728)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 728)
Executable content was dropped or overwritten
- cscript.exe (PID: 728)
Reads the Internet Settings
- cscript.exe (PID: 728)
INFO
Reads security settings of Internet Explorer
- cscript.exe (PID: 728)
Manual execution by a user
- cmd.exe (PID: 308)
Creates files or folders in the user directory
- cscript.exe (PID: 728)
Drops the executable file immediately after the start
- cscript.exe (PID: 728)
Checks supported languages
- s.exe (PID: 1592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:04:08 17:29:36 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | OIETIF-By-Leurak--main/ |
Total processes
43
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | "C:\Windows\System32\cmd.exe" /C "C:\Users\admin\Desktop\OIETIF.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 728 | cscript x.js | C:\Windows\System32\cscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1592 | "C:\Users\admin\AppData\Roaming\s.exe" | C:\Users\admin\AppData\Roaming\s.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 3984 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\OIETIF-By-Leurak--main.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4072 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa3984.24287\OIETIFv2.zip | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
9 320
Read events
9 259
Write events
61
Delete events
0
Modification events
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\OIETIF-By-Leurak--main.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
2
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1592 | s.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
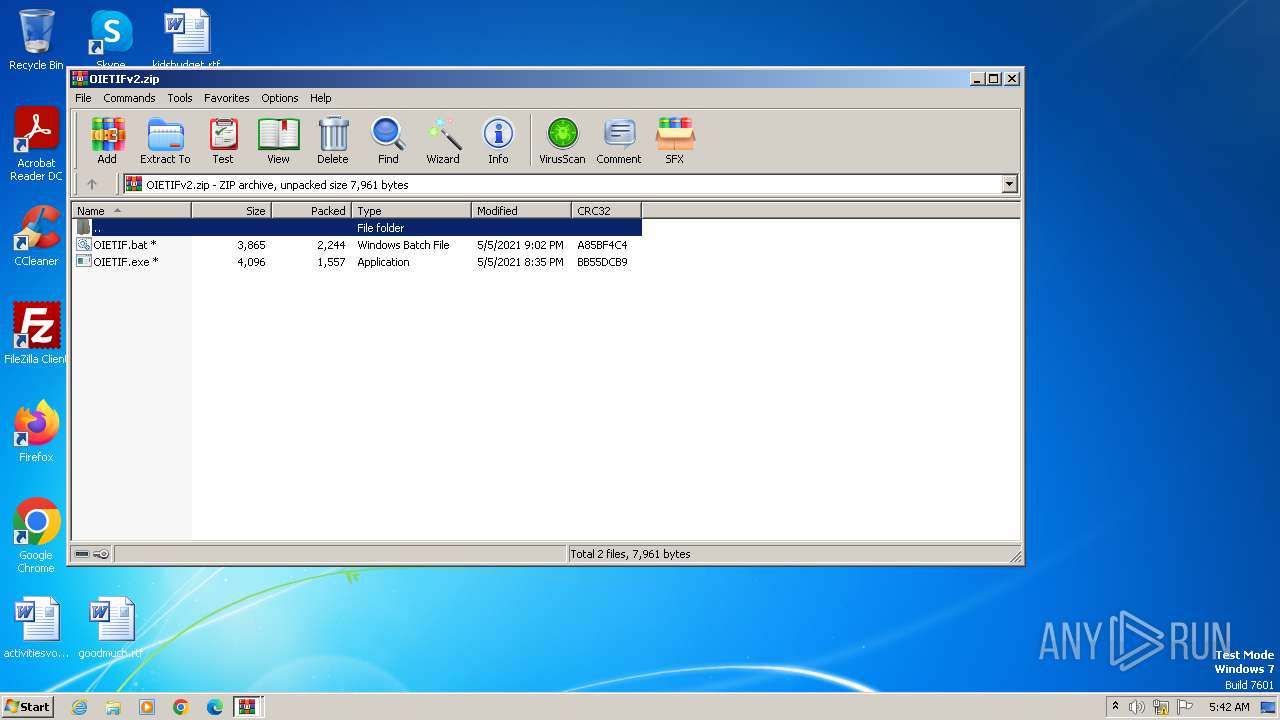
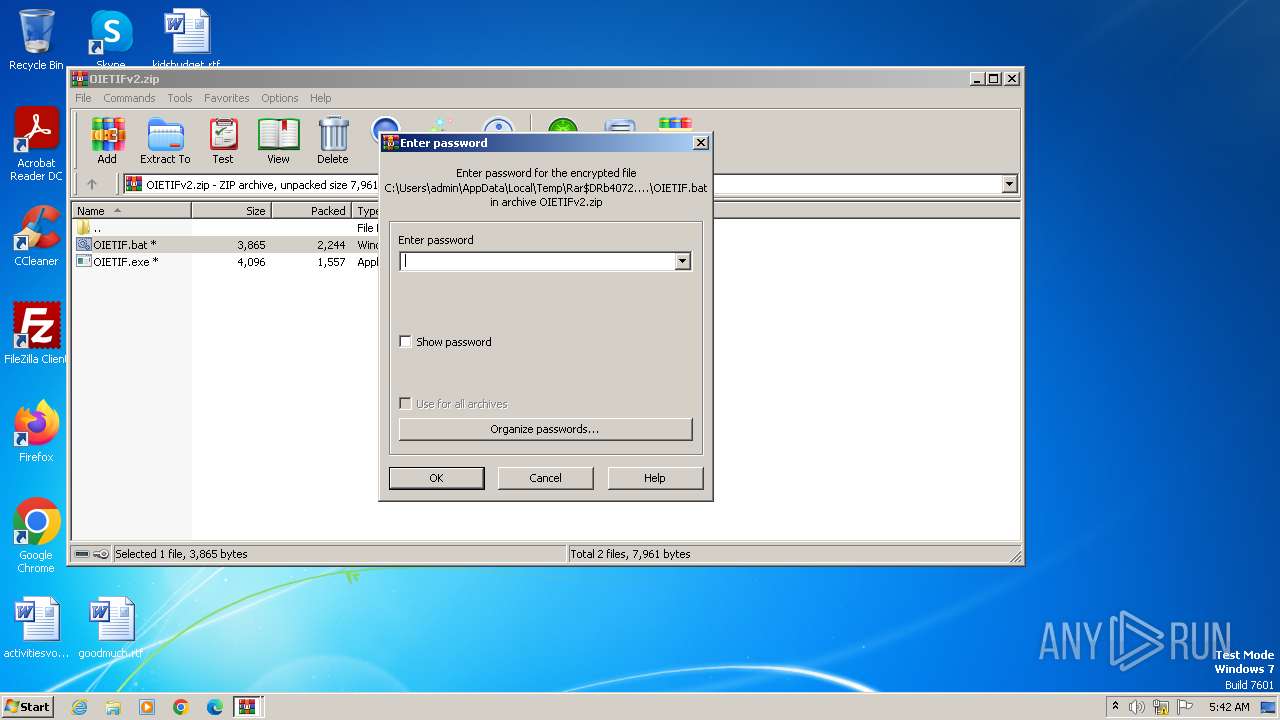
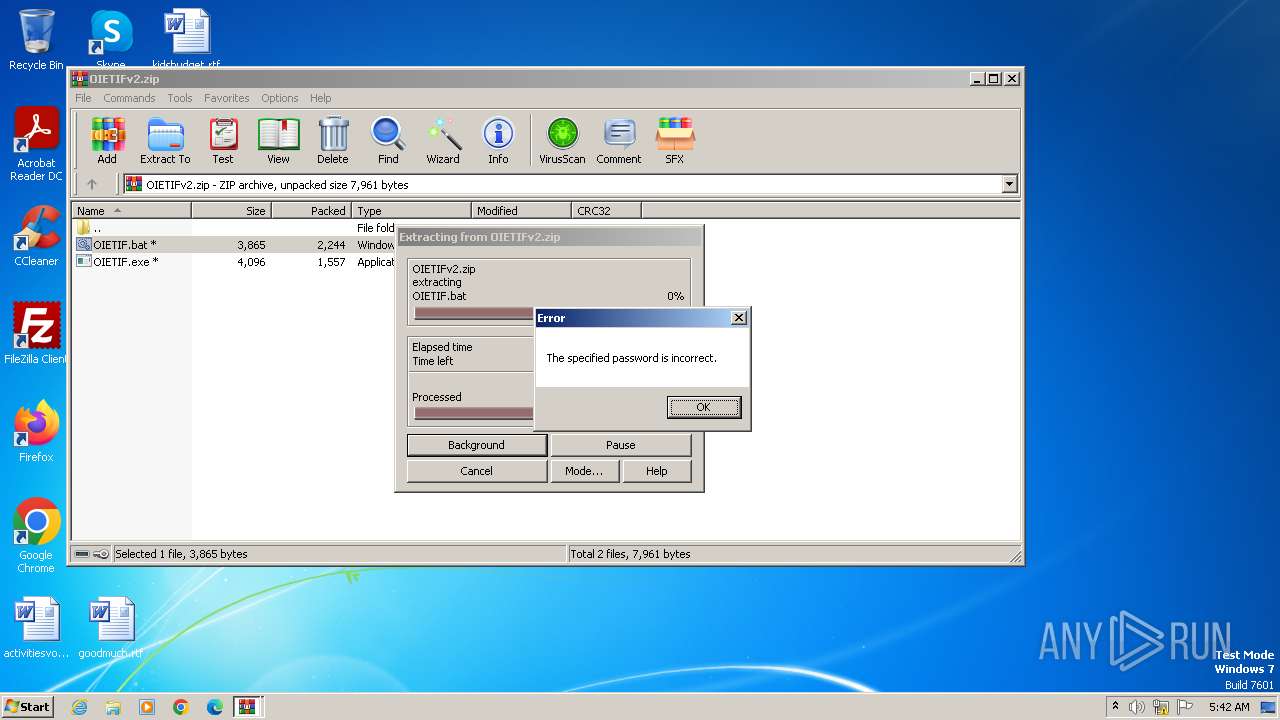
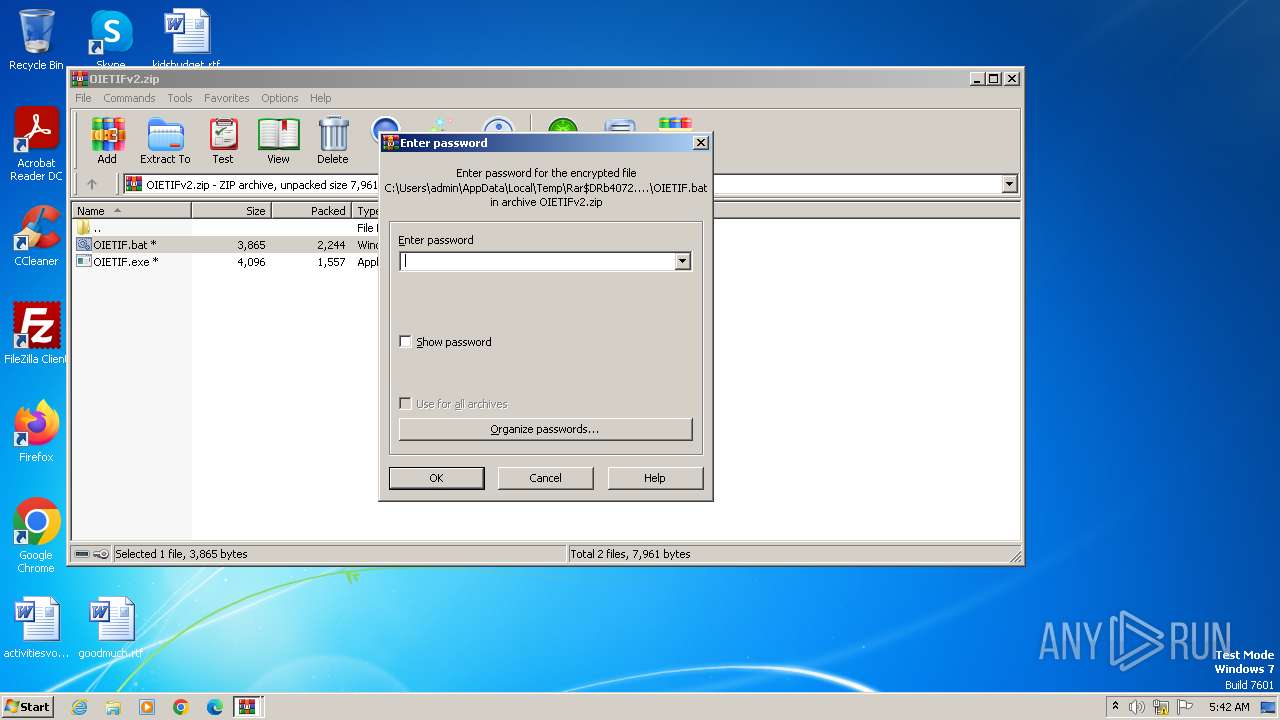
| 3984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3984.24287\OIETIFv2.zip | compressed | |
MD5:CDB001ED6E57EEB0AC36ED05EEE0B3E4 | SHA256:DADB4A3CD5ECB43FFB48A1D9AE29679993EBD408587D8D46EBA1D5A785AC40FB | |||
| 728 | cscript.exe | C:\Users\admin\AppData\Roaming\z.zip | compressed | |
MD5:A30962E7F10FA5A6F791B2D9AB453561 | SHA256:0C0A7F2E8EC916DC1E00110B6028E4EBABDBB3643838A073A8576DAACA475C4C | |||
| 308 | cmd.exe | C:\Users\admin\AppData\Roaming\x.js | text | |
MD5:D94C93F882CF030ED9D66CC35796731D | SHA256:F7941E6BE49D757B46B9D6FB5ECB15392EC36A64E8906692D2EEB2BA9FC67CB6 | |||
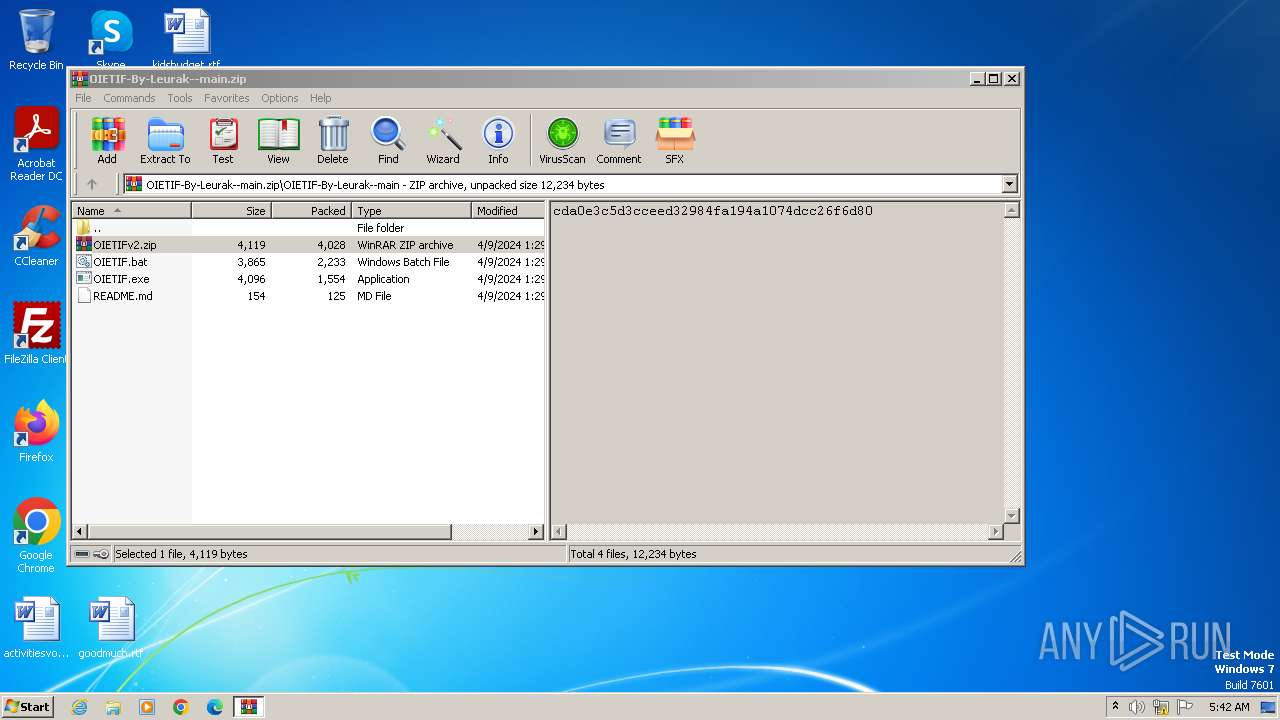
| 3984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3984.27059\OIETIF-By-Leurak--main\OIETIF.bat | text | |
MD5:C2852FB55116AC0B829DF7E9C0E3E04B | SHA256:4540A0AF78874DACE7BF6D3C69E6E6E033D3CD65BE718BC1516A687916433662 | |||
| 728 | cscript.exe | C:\Users\admin\AppData\Roaming\s.exe | executable | |
MD5:358666B4D8C4D306651F4B0F8FCE89E5 | SHA256:856CA1A7C06A7E385170B70334113C9729B28E4090A0C961CD2B3F8758B81704 | |||
| 308 | cmd.exe | C:\Users\admin\AppData\Roaming\x | text | |
MD5:4B1389A9F78BF5D94E7EB81D1506CA47 | SHA256:BFADC1FA9A0D4D0809EA1EEBEE1DDEDC64C2680275D175EC3830176499775199 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report