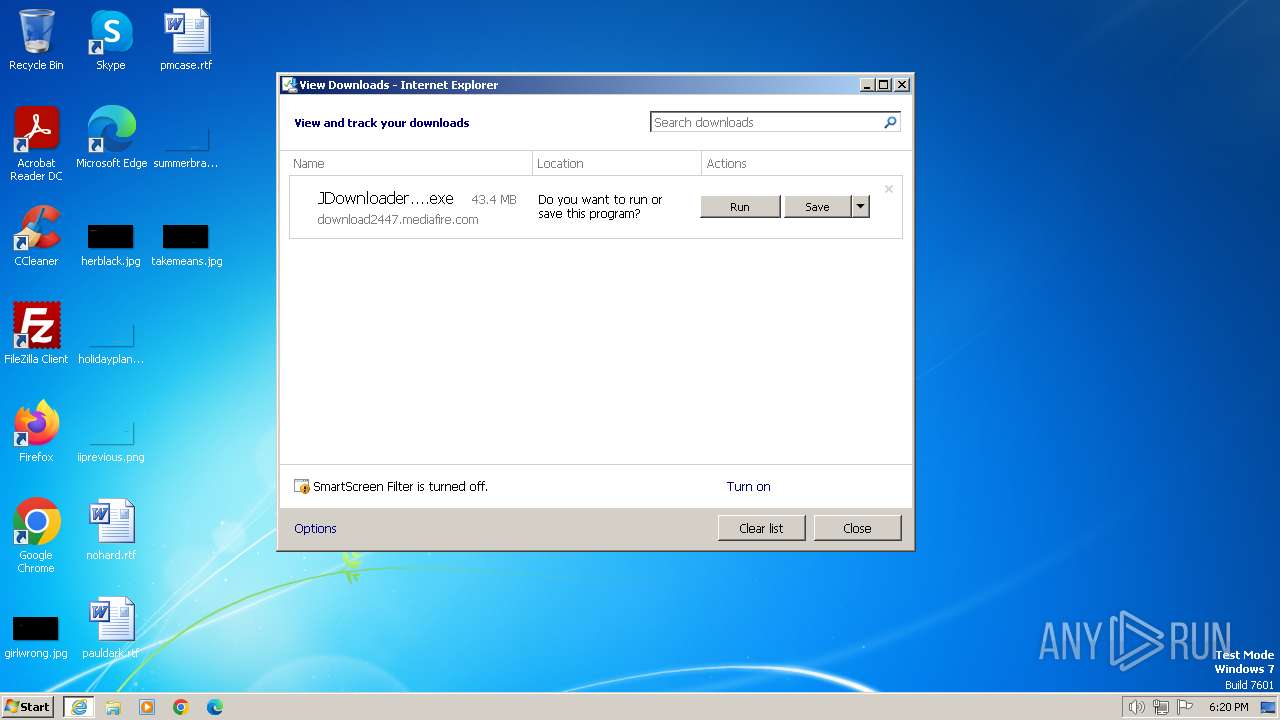
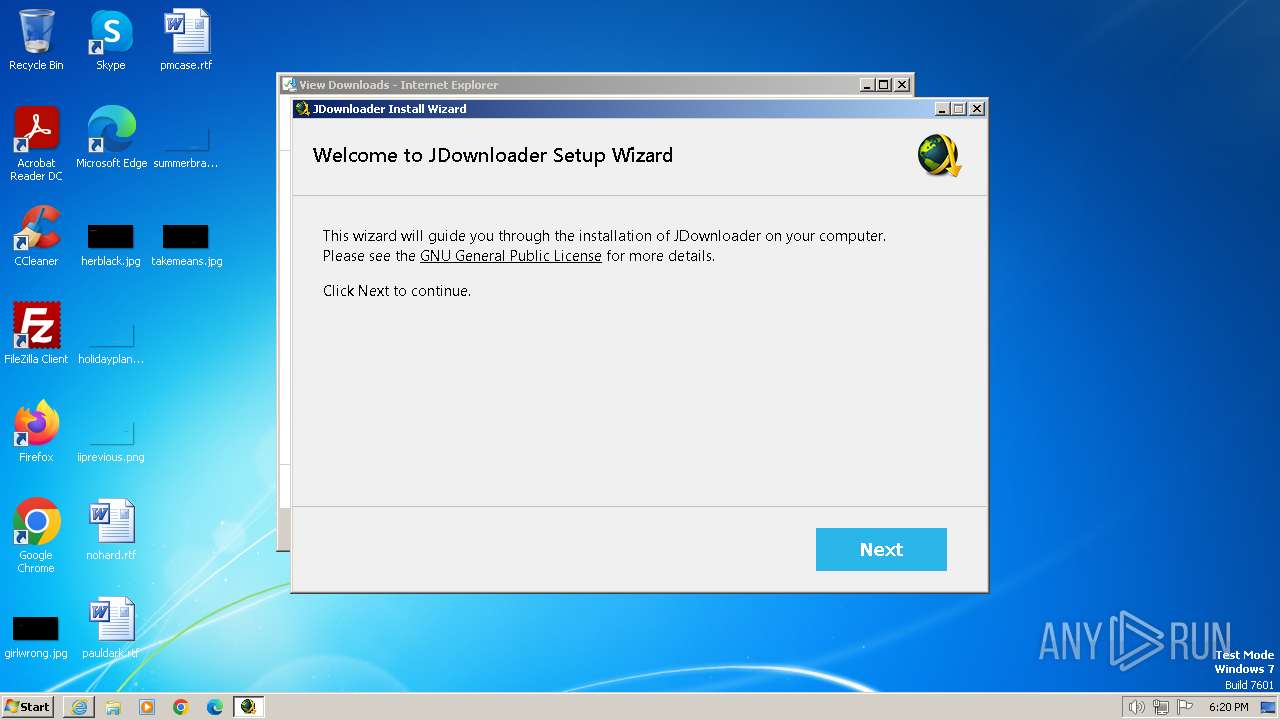
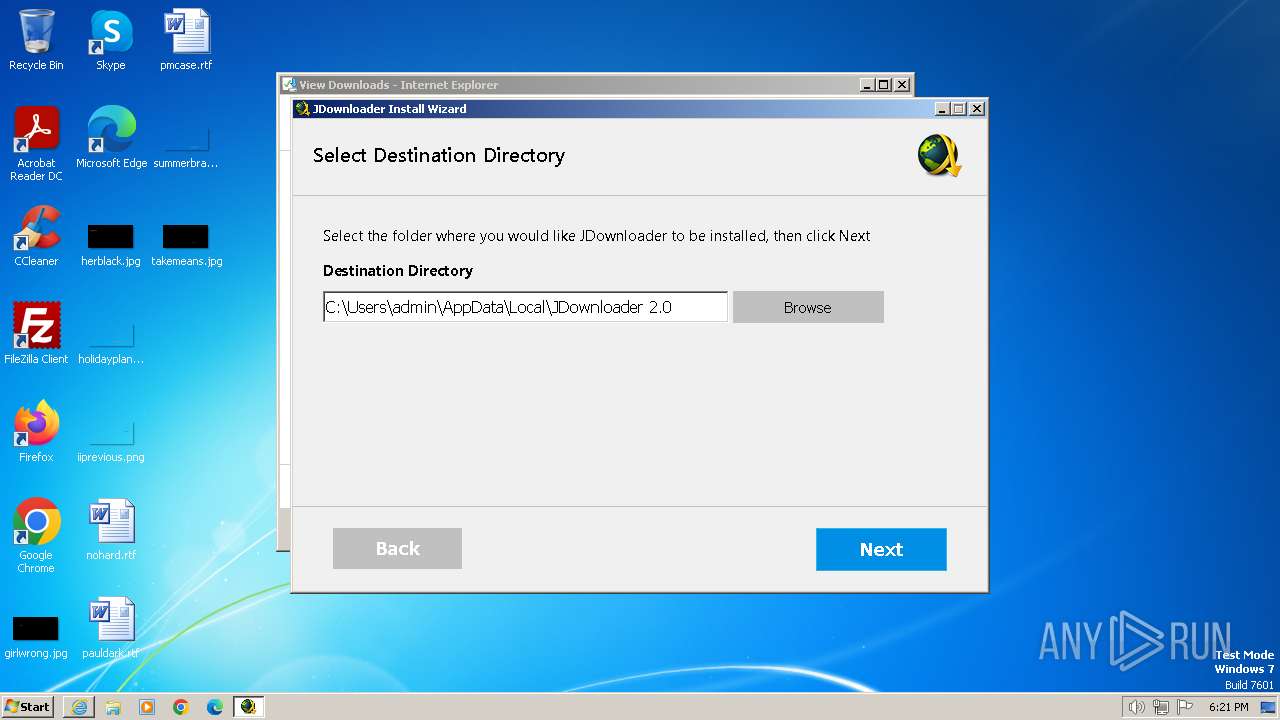
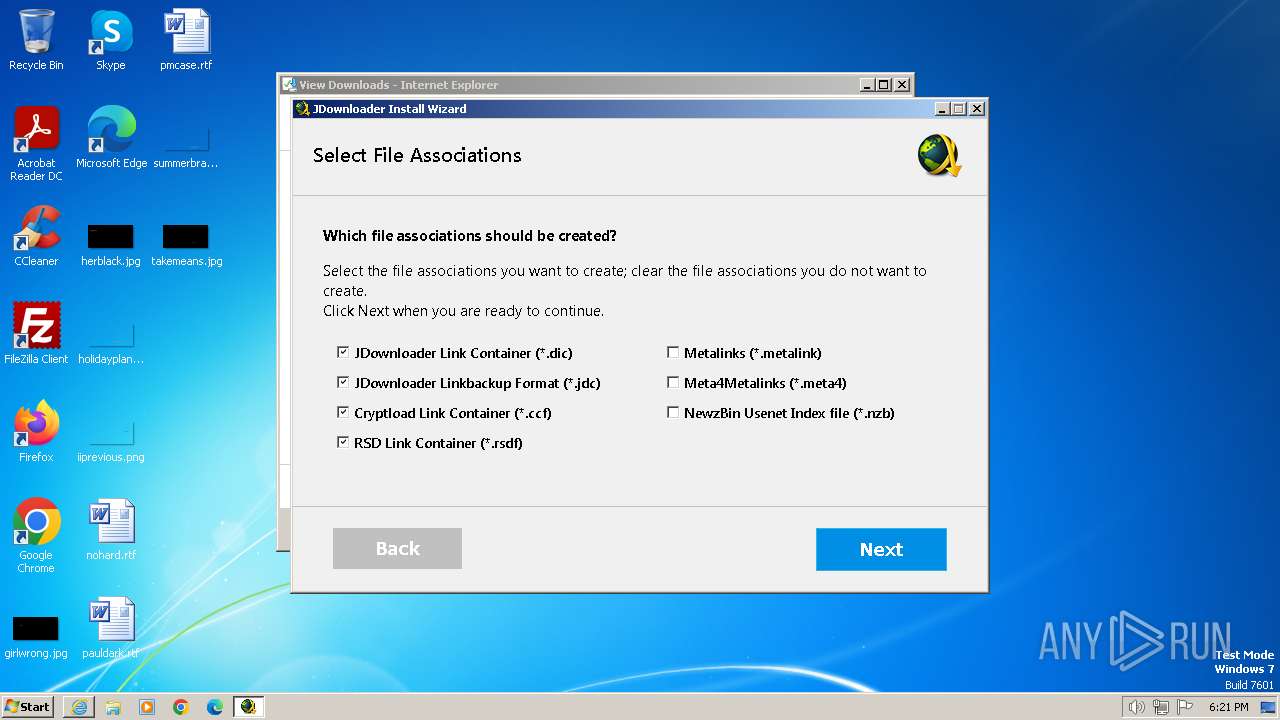
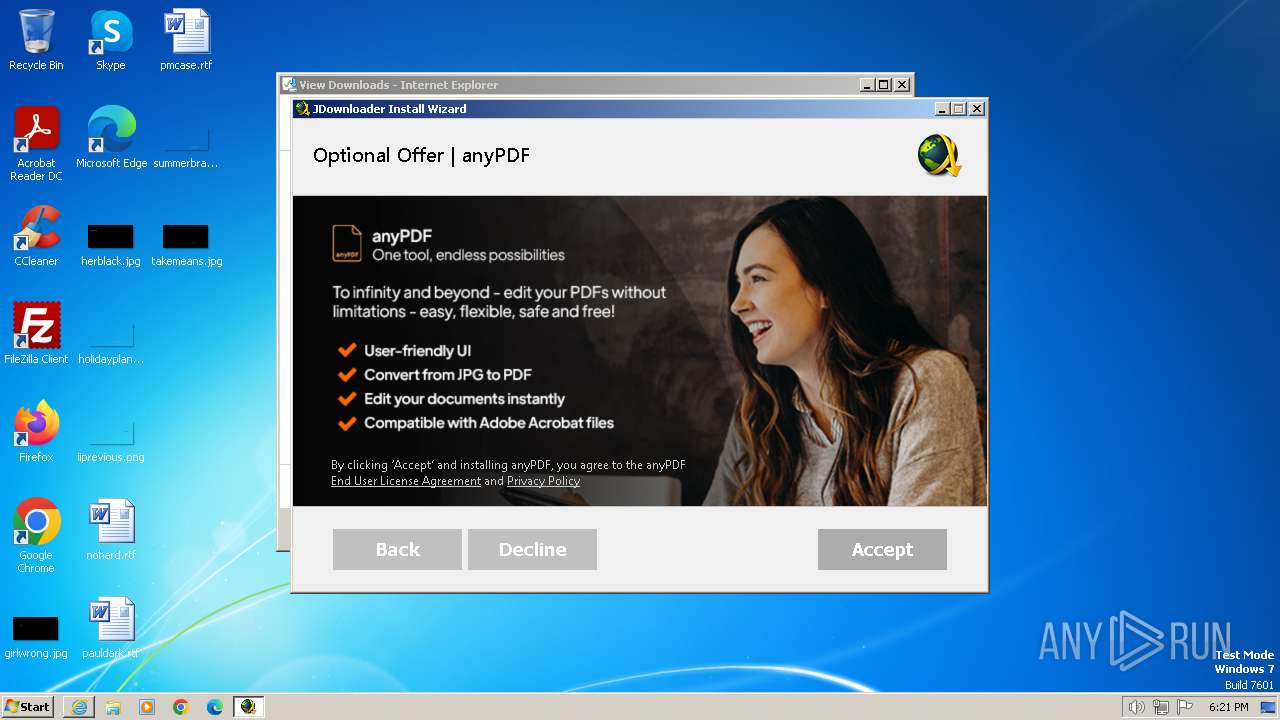
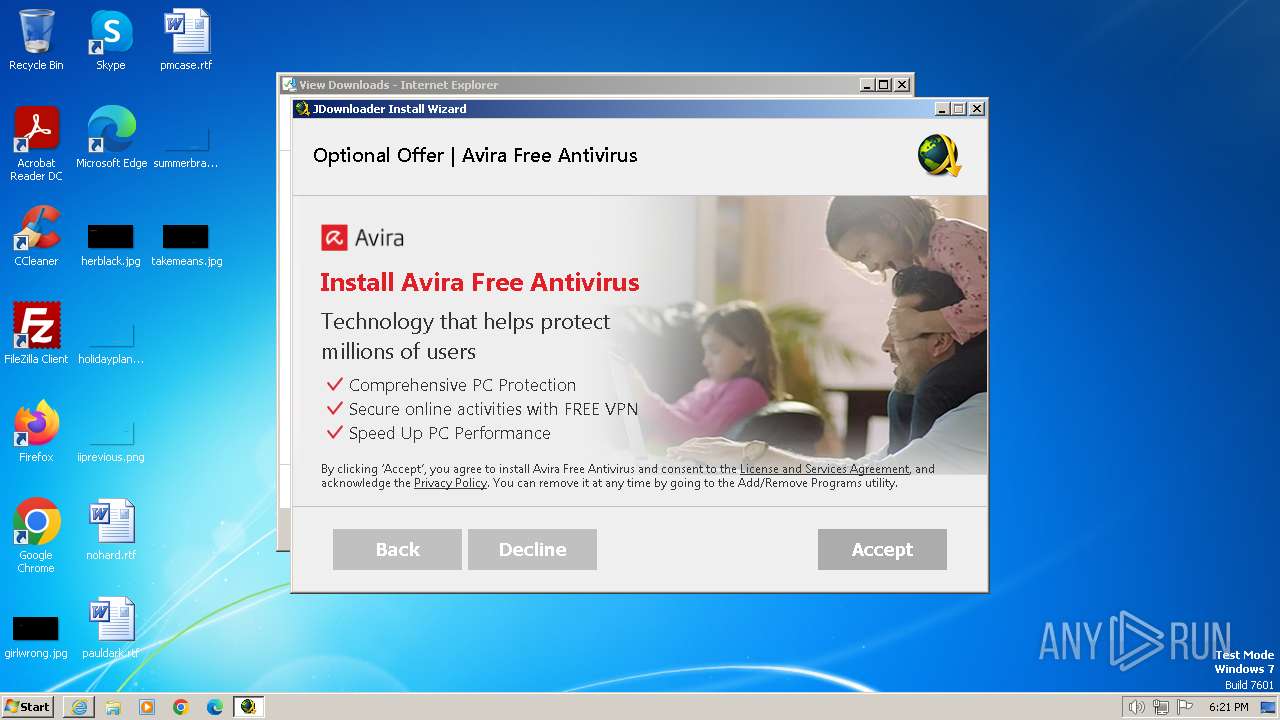
| URL: | https://download2447.mediafire.com/zm21nnk7aujg2JM70Ikl3C5_Na_jQ1lihcVm28yRVWJaSaEftzg0m3ps-j4bS194hYAx7iVUl1hhSiO3GsvFKIyjE0vD3Nya9WlTCginEvtHRegd5NblkC6gc3ftl8nTn8sj3xNtQNg5y94Ysrk8an6mha8o89ik0GyhDNwyOYRA6Q/2akwfxzvwowoigt/JDownloaderSetup.exe |
| Full analysis: | https://app.any.run/tasks/e5ce86a3-fc98-4cc3-8353-f8a29b0ae0a9 |
| Verdict: | Malicious activity |
| Analysis date: | February 17, 2024, 18:19:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 73E261F415A928D23806A99FFCB44434 |
| SHA1: | 5896627594D7203B952A52C217EA27F9BAFCB6B2 |
| SHA256: | 703027A0AC4F776D2379EBFE63EDF3E7F09D9D7C5FB68A724DF83B15CDBC8A5A |
| SSDEEP: | 6:2SWo2eGddZk2jzceRzB4gMWILPkxFfbrBeJvK7EHLMnzsA:2t3eQdZkgLB4gMWILPkt4K7k8 |
MALICIOUS
Drops the executable file immediately after the start
- JDownloaderSetup.exe (PID: 1972)
- avira__sptl1___lavasoft.exe (PID: 3484)
- Carrier.exe (PID: 1892)
SUSPICIOUS
The process creates files with name similar to system file names
- JDownloaderSetup.exe (PID: 1972)
- avira__sptl1___lavasoft.exe (PID: 3484)
Executable content was dropped or overwritten
- JDownloaderSetup.exe (PID: 1972)
- Carrier.exe (PID: 1892)
- avira__sptl1___lavasoft.exe (PID: 3484)
Reads the Internet Settings
- installer.exe (PID: 2960)
- GenericSetup.exe (PID: 2644)
- cmd.exe (PID: 840)
- Avira.Spotlight.Bootstrapper.exe (PID: 548)
- reg.exe (PID: 3936)
- Carrier.exe (PID: 1892)
- reg.exe (PID: 3344)
- reg.exe (PID: 2292)
- reg.exe (PID: 2064)
Reads security settings of Internet Explorer
- GenericSetup.exe (PID: 2644)
- installer.exe (PID: 2960)
- Avira.Spotlight.Bootstrapper.exe (PID: 548)
Reads the Windows owner or organization settings
- GenericSetup.exe (PID: 2644)
Searches for installed software
- GenericSetup.exe (PID: 2644)
- Avira.Spotlight.Bootstrapper.exe (PID: 548)
Reads settings of System Certificates
- GenericSetup.exe (PID: 2644)
- Avira.Spotlight.Bootstrapper.exe (PID: 548)
Starts CMD.EXE for commands execution
- GenericSetup.exe (PID: 2644)
Checks Windows Trust Settings
- GenericSetup.exe (PID: 2644)
The executable file from the user directory is run by the CMD process
- Carrier.exe (PID: 1892)
- avira__sptl1___lavasoft.exe (PID: 3484)
Adds/modifies Windows certificates
- GenericSetup.exe (PID: 2644)
Process drops legitimate windows executable
- Carrier.exe (PID: 1892)
The process drops C-runtime libraries
- Carrier.exe (PID: 1892)
Process requests binary or script from the Internet
- Carrier.exe (PID: 1892)
INFO
Application launched itself
- iexplore.exe (PID: 3864)
Executable content was dropped or overwritten
- iexplore.exe (PID: 3952)
Create files in a temporary directory
- JDownloaderSetup.exe (PID: 1972)
- installer.exe (PID: 2960)
- GenericSetup.exe (PID: 2644)
- Carrier.exe (PID: 1892)
- unpack200.exe (PID: 1608)
- unpack200.exe (PID: 3036)
- unpack200.exe (PID: 1840)
- unpack200.exe (PID: 124)
- unpack200.exe (PID: 2808)
- unpack200.exe (PID: 948)
- unpack200.exe (PID: 920)
- unpack200.exe (PID: 3292)
- unpack200.exe (PID: 3232)
- unpack200.exe (PID: 3900)
- unpack200.exe (PID: 2828)
- unpack200.exe (PID: 1652)
- avira__sptl1___lavasoft.exe (PID: 3484)
- Avira.Spotlight.Bootstrapper.exe (PID: 548)
- unpack200.exe (PID: 2104)
- unpack200.exe (PID: 3436)
- unpack200.exe (PID: 3572)
- unpack200.exe (PID: 3756)
- unpack200.exe (PID: 3360)
- java.exe (PID: 3388)
- unpack200.exe (PID: 3672)
- unpack200.exe (PID: 2032)
- unpack200.exe (PID: 864)
- unpack200.exe (PID: 3428)
- javaw.exe (PID: 2908)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3952)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3864)
Checks supported languages
- JDownloaderSetup.exe (PID: 1972)
- installer.exe (PID: 2960)
- GenericSetup.exe (PID: 2644)
- Carrier.exe (PID: 1892)
- unpack200.exe (PID: 1608)
- unpack200.exe (PID: 2808)
- unpack200.exe (PID: 3036)
- unpack200.exe (PID: 1840)
- unpack200.exe (PID: 3232)
- unpack200.exe (PID: 124)
- unpack200.exe (PID: 920)
- unpack200.exe (PID: 948)
- unpack200.exe (PID: 3292)
- unpack200.exe (PID: 3900)
- unpack200.exe (PID: 1652)
- Avira.Spotlight.Bootstrapper.exe (PID: 548)
- avira__sptl1___lavasoft.exe (PID: 3484)
- unpack200.exe (PID: 2104)
- unpack200.exe (PID: 2828)
- unpack200.exe (PID: 2032)
- unpack200.exe (PID: 3436)
- unpack200.exe (PID: 3756)
- unpack200.exe (PID: 3572)
- java.exe (PID: 3388)
- unpack200.exe (PID: 3360)
- unpack200.exe (PID: 3672)
- unpack200.exe (PID: 864)
- unpack200.exe (PID: 3428)
- javaw.exe (PID: 2908)
The process uses the downloaded file
- iexplore.exe (PID: 3864)
Reads the computer name
- installer.exe (PID: 2960)
- GenericSetup.exe (PID: 2644)
- Avira.Spotlight.Bootstrapper.exe (PID: 548)
- Carrier.exe (PID: 1892)
Reads the machine GUID from the registry
- installer.exe (PID: 2960)
- GenericSetup.exe (PID: 2644)
- Avira.Spotlight.Bootstrapper.exe (PID: 548)
- Carrier.exe (PID: 1892)
Reads the software policy settings
- GenericSetup.exe (PID: 2644)
- Avira.Spotlight.Bootstrapper.exe (PID: 548)
Reads Environment values
- GenericSetup.exe (PID: 2644)
- Avira.Spotlight.Bootstrapper.exe (PID: 548)
Reads product name
- GenericSetup.exe (PID: 2644)
Creates files in the program directory
- java.exe (PID: 3388)
- Avira.Spotlight.Bootstrapper.exe (PID: 548)
- Carrier.exe (PID: 1892)
Checks proxy server information
- reg.exe (PID: 3936)
- reg.exe (PID: 3344)
- reg.exe (PID: 2292)
- reg.exe (PID: 2064)
Creates files or folders in the user directory
- Carrier.exe (PID: 1892)
- javaw.exe (PID: 2908)
Drops a (possible) Coronavirus decoy
- Carrier.exe (PID: 1892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
113
Monitored processes
42
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | -r "jre\lib\jsse.jar.pack" "jre\lib\jsse.jar" | C:\Users\admin\AppData\Local\Temp\e4j3E76.tmp_dir1708194085\jre\bin\unpack200.exe | — | Carrier.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1620.12 Modules
| |||||||||||||||
| 548 | "C:\Users\admin\AppData\Local\Temp\.CR.6493\Avira.Spotlight.Bootstrapper.exe" "C:\Users\admin\AppData\Local\Temp\.CR.6493\Avira.Spotlight.Bootstrapper.exe" OriginalFileName=avira__sptl1___lavasoft.exe Silent=true AcceptEula=true LaunchUi=true | C:\Users\admin\AppData\Local\Temp\.CR.6493\Avira.Spotlight.Bootstrapper.exe | avira__sptl1___lavasoft.exe | ||||||||||||
User: admin Company: Avira Operations GmbH Integrity Level: HIGH Description: Avira Security Exit code: 0 Version: 1.0.47.529 Modules
| |||||||||||||||
| 840 | "C:\Windows\system32\cmd.exe" /C ""anyPDF-h20-5.msi" /quiet" | C:\Windows\System32\cmd.exe | — | GenericSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1620 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 864 | -r "C:\Users\admin\AppData\Local\Temp\e4j3E76.tmp_dir1708194085\user\JDownloader.jar.pack" "C:\Users\admin\AppData\Local\Temp\e4j3E76.tmp_dir1708194085\user\JDownloader.jar" | C:\Users\admin\AppData\Local\Temp\e4j3E76.tmp_dir1708194085\jre\bin\unpack200.exe | — | Carrier.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1620.12 Modules
| |||||||||||||||
| 920 | -r "jre\lib\management-agent.jar.pack" "jre\lib\management-agent.jar" | C:\Users\admin\AppData\Local\Temp\e4j3E76.tmp_dir1708194085\jre\bin\unpack200.exe | — | Carrier.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1620.12 Modules
| |||||||||||||||
| 948 | -r "jre\lib\plugin.jar.pack" "jre\lib\plugin.jar" | C:\Users\admin\AppData\Local\Temp\e4j3E76.tmp_dir1708194085\jre\bin\unpack200.exe | — | Carrier.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1620.12 Modules
| |||||||||||||||
| 1608 | -r "jre\lib\charsets.jar.pack" "jre\lib\charsets.jar" | C:\Users\admin\AppData\Local\Temp\e4j3E76.tmp_dir1708194085\jre\bin\unpack200.exe | — | Carrier.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1620.12 Modules
| |||||||||||||||
| 1652 | -r "jre\lib\ext\cldrdata.jar.pack" "jre\lib\ext\cldrdata.jar" | C:\Users\admin\AppData\Local\Temp\e4j3E76.tmp_dir1708194085\jre\bin\unpack200.exe | — | Carrier.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1620.12 Modules
| |||||||||||||||
| 1840 | -r "jre\lib\jfr.jar.pack" "jre\lib\jfr.jar" | C:\Users\admin\AppData\Local\Temp\e4j3E76.tmp_dir1708194085\jre\bin\unpack200.exe | — | Carrier.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1620.12 Modules
| |||||||||||||||
| 1892 | "C:\Users\admin\AppData\Local\Temp\7zS4B7E6C98\Carrier.exe" "-Dregistry=true" -DinstallationDir="C:\Users\admin\AppData\Local\JDownloader 2.0" -q "-Dfilelinks=dlc,jdc,ccf,rsdf" "-Ddesktoplink=true" "-Dquicklaunch=false" | C:\Users\admin\AppData\Local\Temp\7zS4B7E6C98\Carrier.exe | cmd.exe | ||||||||||||
User: admin Company: AppWork GmbH Integrity Level: HIGH Description: JDownloader Exit code: 0 Version: 2.0 Modules
| |||||||||||||||
Total events
264 133
Read events
204 579
Write events
59 506
Delete events
48
Modification events
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31089101 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31089101 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
544
Suspicious files
2 041
Text files
387
Unknown types
86
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\JDownloaderSetup.exe.uednp5o.partial | — | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\JDownloaderSetup.exe | — | |
MD5:— | SHA256:— | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_BACC6CD2B29F18349081C9FD2343833B | binary | |
MD5:B8AFEC44772040692071A1A9DD0320F7 | SHA256:8D73CDE76EABF51FF9199F0FE9EDD8B92B7D9A8D1B0526AEA9238BA7223B4ED2 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:DBF565618B82F979C417E8B582DBA856 | SHA256:2D96D4B6E5BA12FAC19B790132D069F49716A5D228E995AF4054F02123ED50E6 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\JDownloaderSetup[1].exe | executable | |
MD5:BFA028BBFB6CDCF3240BC2BF14FDF1BE | SHA256:D78417B5E36A69B3670BC2AD9EFDE1247475AF1CDAB4338C411C8D603F90E549 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_BACC6CD2B29F18349081C9FD2343833B | binary | |
MD5:C3D3DAC113DF3B4072E4935C159F7E2C | SHA256:8B720BABEC7332A69A4ED320AAE2CD6D0D9D3DE078BE33DA771E3B2E678AD438 | |||
| 1972 | JDownloaderSetup.exe | C:\Users\admin\AppData\Local\Temp\7zS4B7E6C98\Resources\FinishPage.html | html | |
MD5:709B1627517AEE4AC94FB0A358BBAB99 | SHA256:134EDAC6561E6712B7988AD502928FD1423D57F31926F6A172E5EF423318C024 | |||
| 1972 | JDownloaderSetup.exe | C:\Users\admin\AppData\Local\Temp\7zS4B7E6C98\Resources\FolderPage.html | html | |
MD5:4D3CA1CBABA4C266FF26548578C8072A | SHA256:3D4A6BAAA9E8ADD6FB8A90CAE59BA0A3F994046CCA7410AC59F4D90EF34BD04E | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:E4877DBE9F7E0ED1752F023913F0A3B6 | SHA256:23F3F01C529C28C066F42CA9D99EA015FA981E5DAB96DBA004B34E3DAB4CA2EF | |||
| 1972 | JDownloaderSetup.exe | C:\Users\admin\AppData\Local\Temp\7zS4B7E6C98\app.ico | image | |
MD5:1F0FA25C629E147A347578677EF48C43 | SHA256:CA4422F74242954350DE35EFA9DB4F92FF748AD278B56CECF02C0CA9192460F2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
48
DNS requests
23
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3952 | iexplore.exe | GET | 304 | 173.222.108.243:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?545e1839169dd0e6 | unknown | — | — | unknown |
3952 | iexplore.exe | GET | 304 | 173.222.108.243:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f78d505714a595e3 | unknown | — | — | unknown |
3952 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEBN9U5yqfDGppDNwGWiEeo0%3D | unknown | binary | 2.18 Kb | unknown |
3952 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQh80WaEMqmyEvaHjlisSfVM4p8SAQUF9nWJSdn%2BTHCSUPZMDZEjGypT%2BsCED%2B0KeRQ8NP60VP53TIby3A%3D | unknown | binary | 471 b | unknown |
3864 | iexplore.exe | GET | 304 | 2.19.198.41:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?18014fff35250a83 | unknown | — | — | unknown |
1080 | svchost.exe | GET | 200 | 2.19.198.41:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?3e412f7b4eff0943 | unknown | compressed | 65.2 Kb | unknown |
3864 | iexplore.exe | GET | 304 | 2.19.198.41:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?76ad697231f9b13b | unknown | — | — | unknown |
3864 | iexplore.exe | GET | 304 | 2.19.198.41:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9aee5c2adfb08fdb | unknown | — | — | unknown |
3864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 304 | 2.19.198.41:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e2ddf83a2417bb20 | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3952 | iexplore.exe | 199.91.155.188:443 | download2447.mediafire.com | MEDIAFIRE | US | unknown |
3952 | iexplore.exe | 173.222.108.243:80 | ctldl.windowsupdate.com | Akamai International B.V. | CH | unknown |
3952 | iexplore.exe | 104.18.38.233:80 | ocsp.usertrust.com | CLOUDFLARENET | — | shared |
3952 | iexplore.exe | 172.64.149.23:80 | ocsp.usertrust.com | CLOUDFLARENET | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3864 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 2.19.198.41:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3864 | iexplore.exe | 2.19.198.41:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download2447.mediafire.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
flow.lavasoft.com |
| whitelisted |
sos.adaware.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
2960 | installer.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Lavasoft PUA/Adware Client Install |
12 ETPRO signatures available at the full report
Process | Message |
|---|---|
GenericSetup.exe | Error: File not found - h2osciter:console.tis
|
GenericSetup.exe | at sciter:init-script.tis
|
GenericSetup.exe | |
GenericSetup.exe | |
GenericSetup.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|
GenericSetup.exe | Error: File not found - h2osciter:console.tis
|
GenericSetup.exe | at sciter:init-script.tis
|
GenericSetup.exe | |
GenericSetup.exe | |
GenericSetup.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|