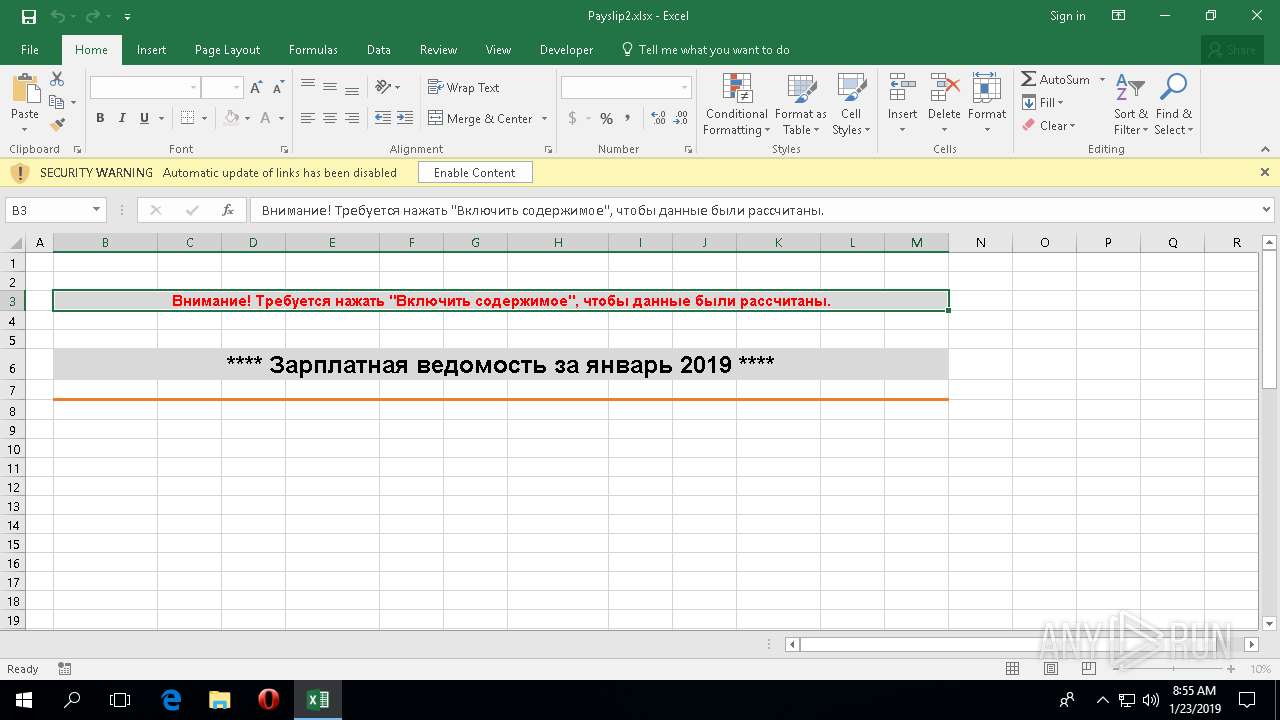
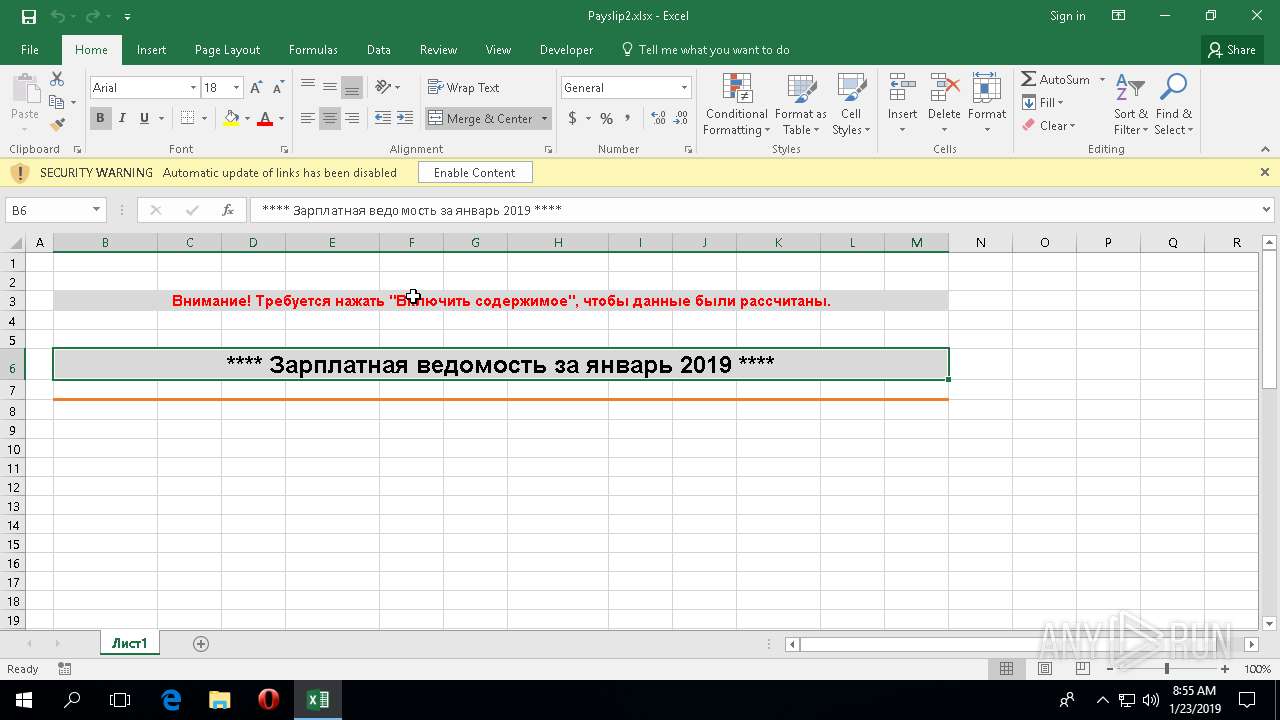
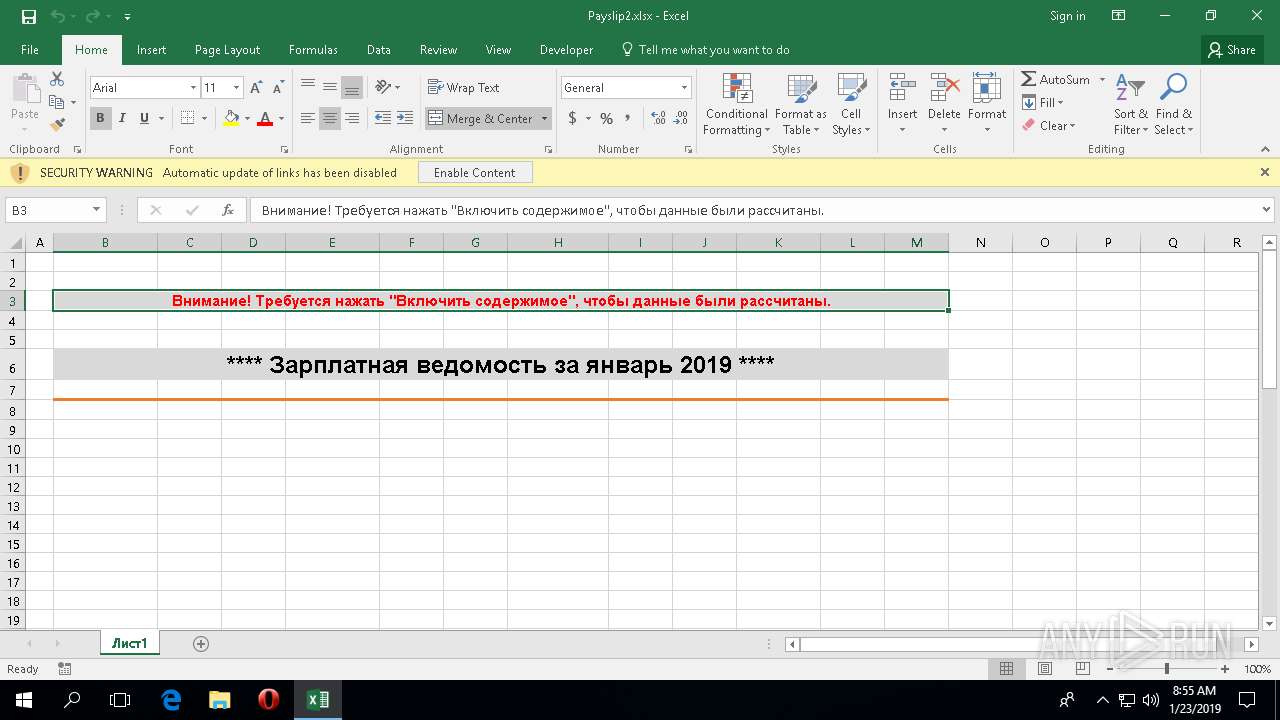
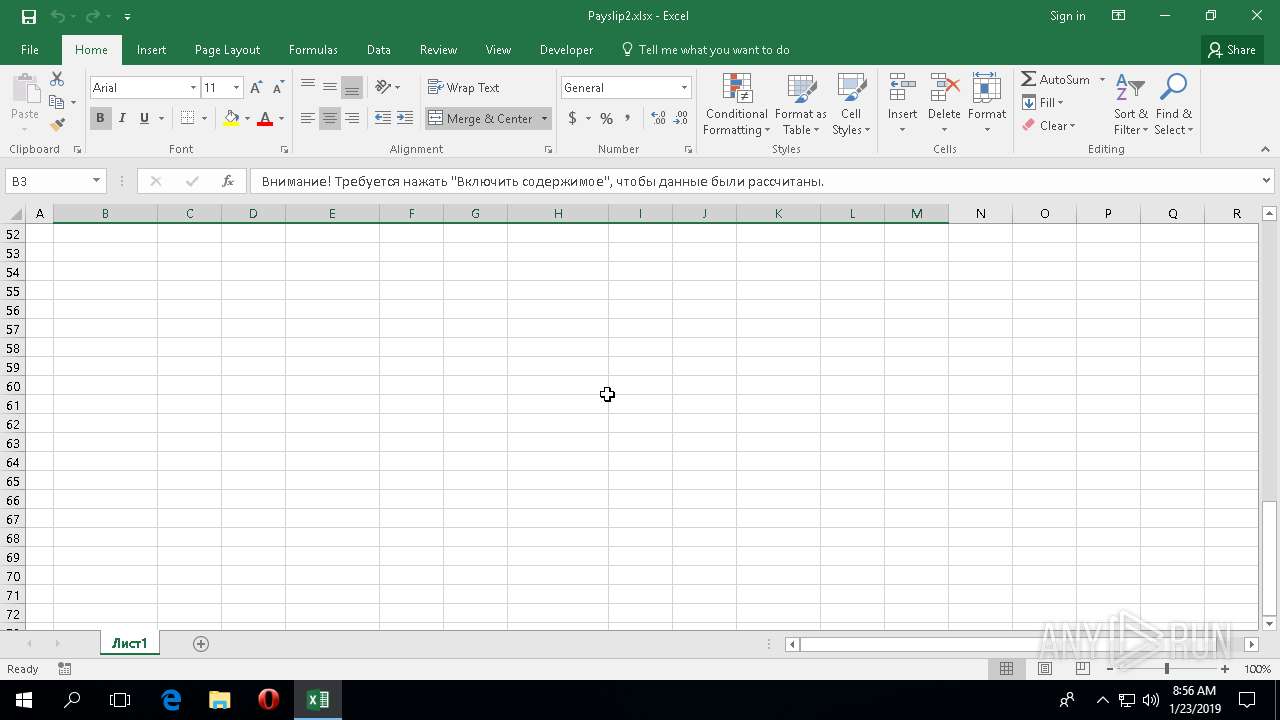
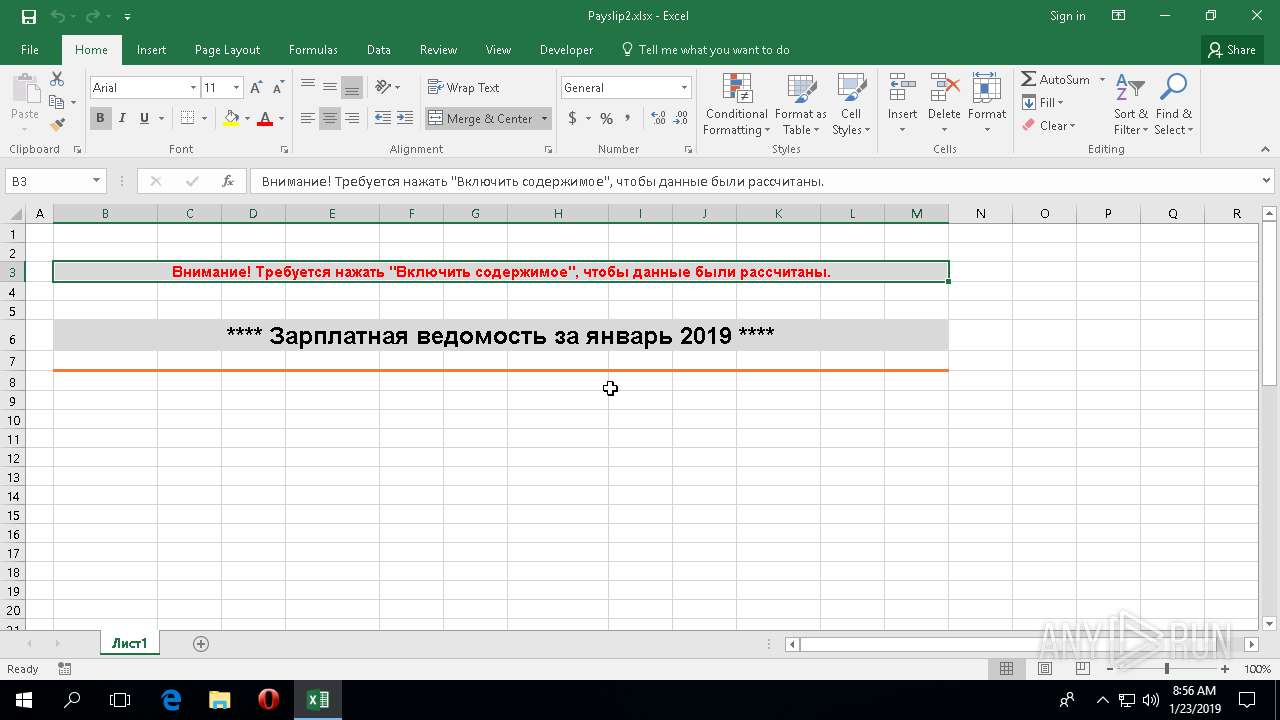
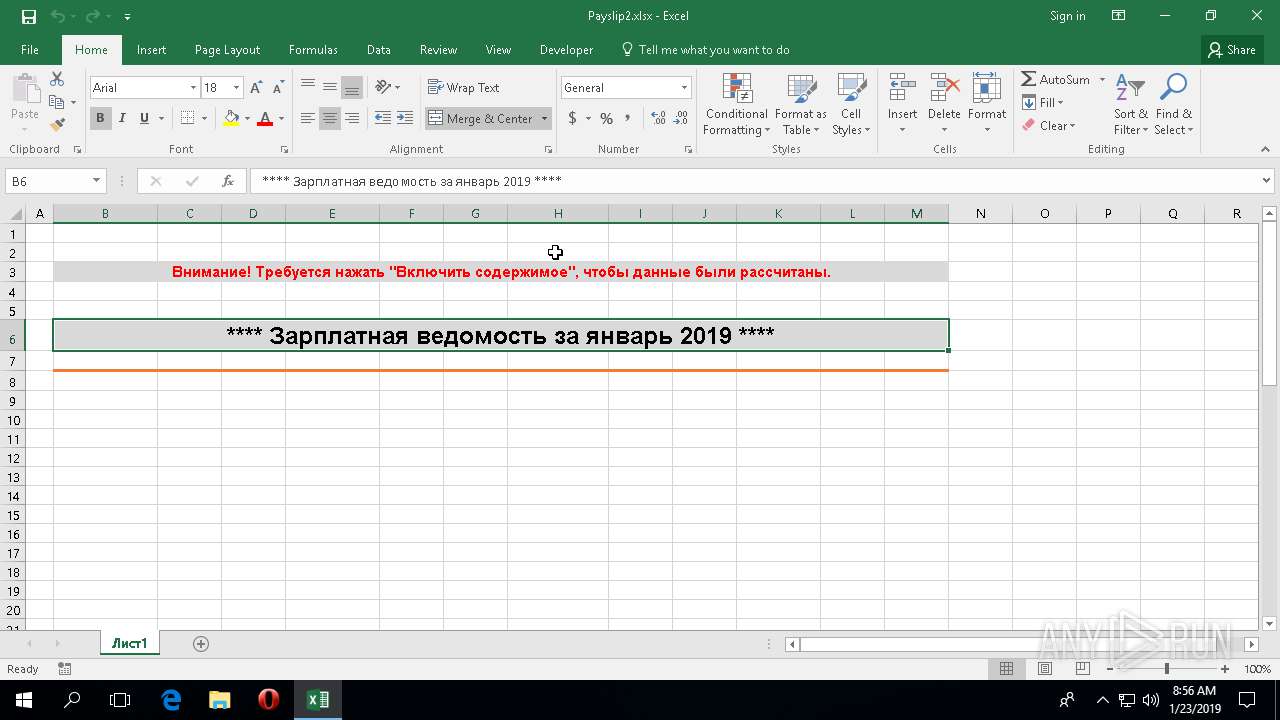
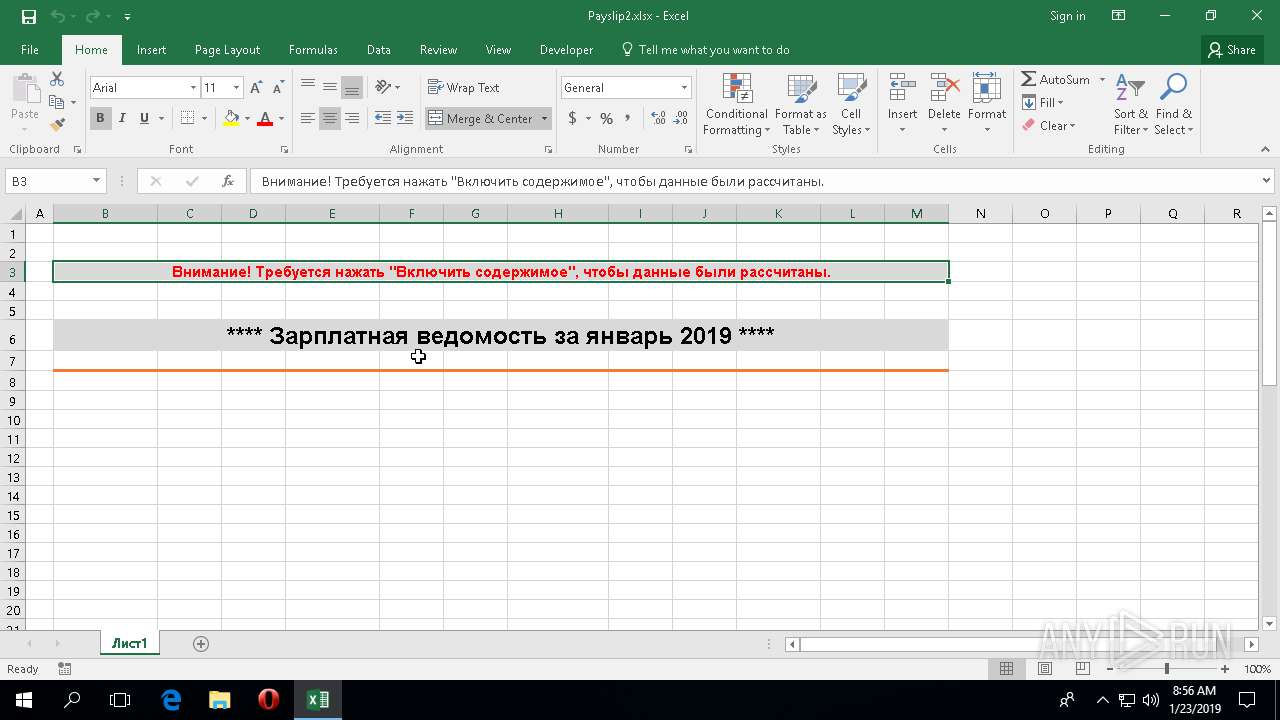
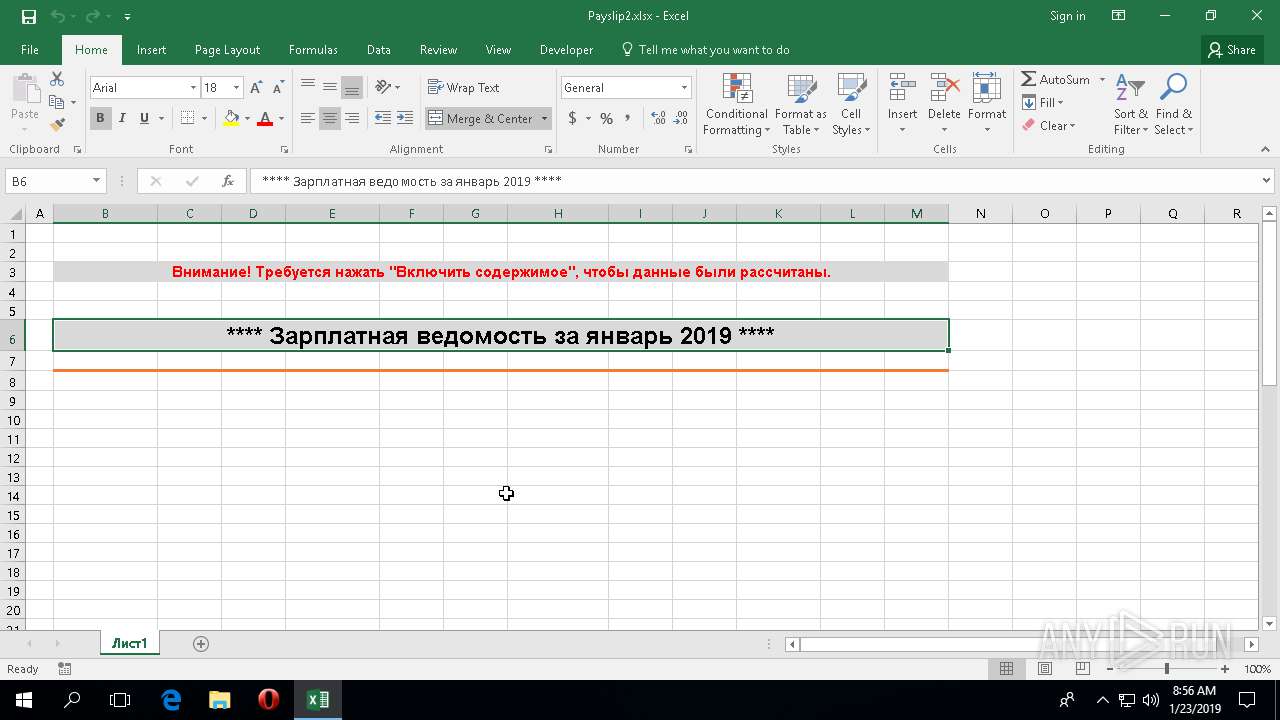
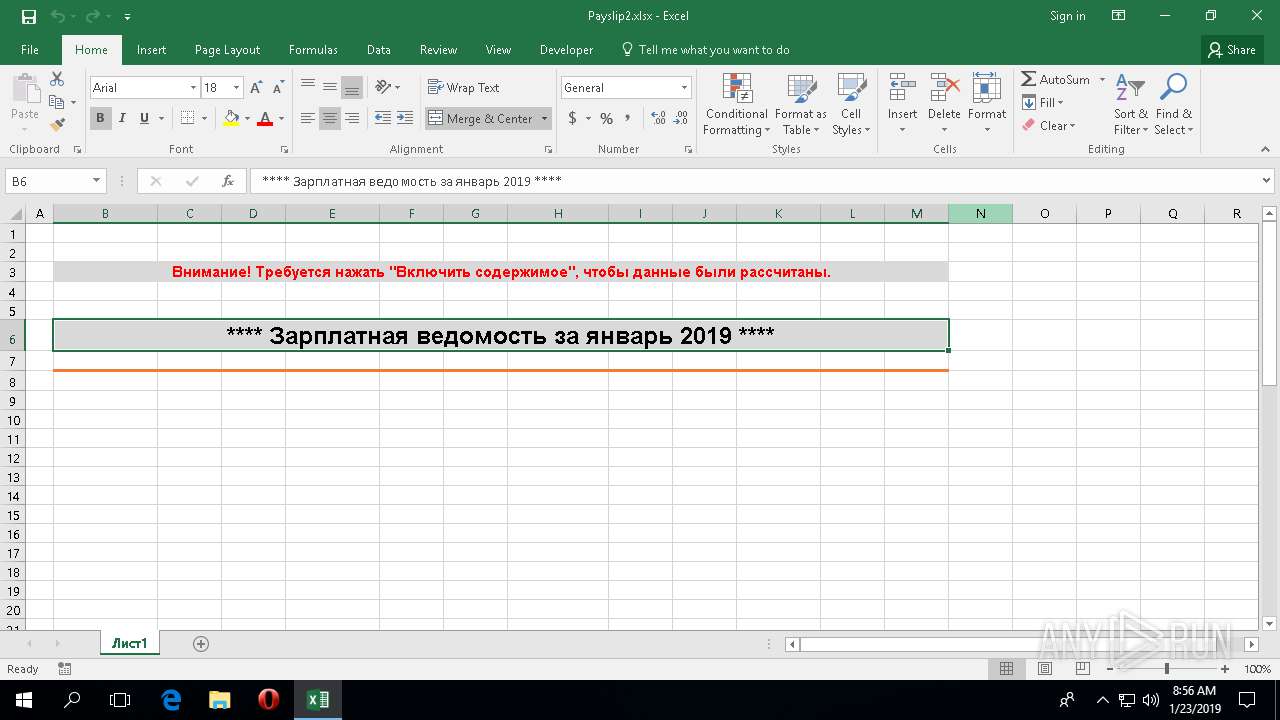
| File name: | Payslip2.xlsx |
| Full analysis: | https://app.any.run/tasks/fd693026-5f72-4162-a847-05b46278ab4c |
| Verdict: | Malicious activity |
| Analysis date: | January 23, 2019, 08:54:41 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | DB3539E70754686200DCD5D462F43439 |
| SHA1: | 60A7EBD3C3E0C1395005D0C1E1C4D84E9FAA886C |
| SHA256: | 6FFE642E17FBF6D81837A98FE1A43C0549F9FBE3D8D14819874ABF63710473ED |
| SSDEEP: | 96:FmzZ0lRLYi2mzE69pKr5JxGO1PND4JU1L1/l28kJQ408TViCE2:FC0lRLYi2mY692xGO9ND4e1Lhl2lJQ4N |
MALICIOUS
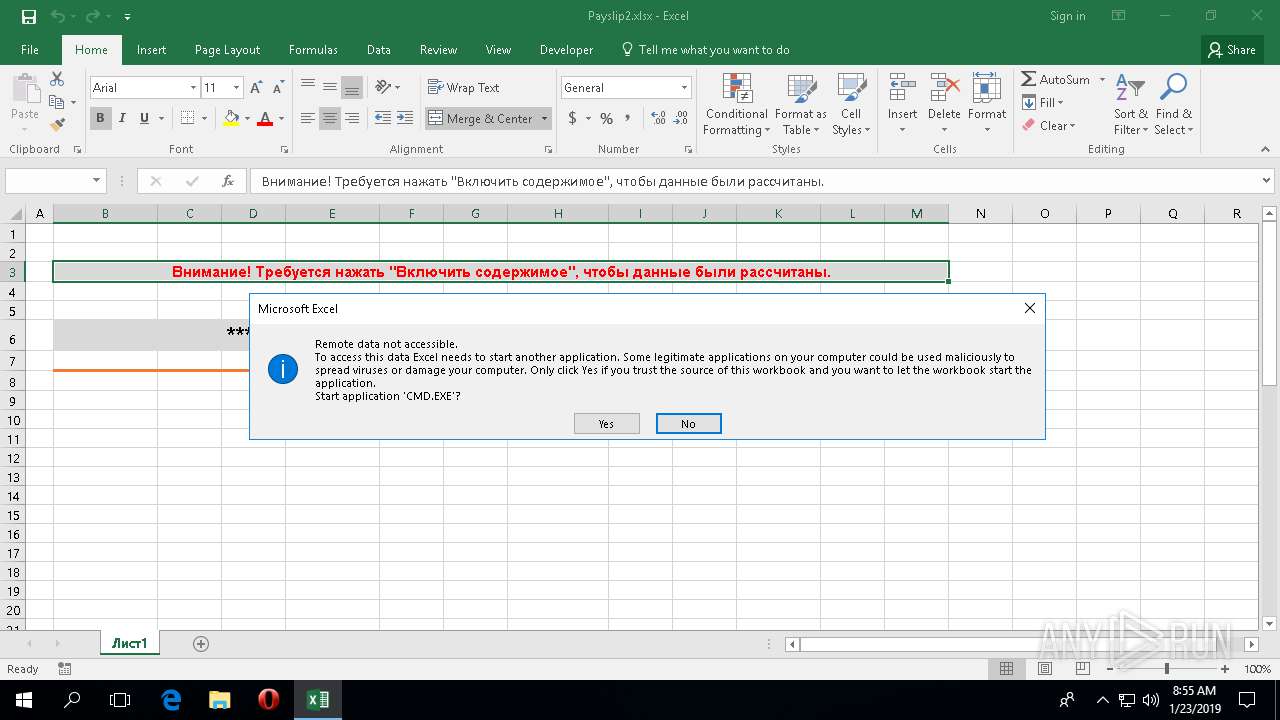
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2644)
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 2644)
SUSPICIOUS
Unusual connect from Microsoft Office
- EXCEL.EXE (PID: 2644)
INFO
Reads the machine GUID from the registry
- EXCEL.EXE (PID: 2644)
Creates files in the user directory
- EXCEL.EXE (PID: 2644)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlsx | | | Excel Microsoft Office Open XML Format document (61.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (31.5) |
| .zip | | | ZIP compressed archive (7.2) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:01:22 21:07:25 |
| ZipCRC: | 0x03cf231f |
| ZipCompressedSize: | 192 |
| ZipUncompressedSize: | 531 |
| ZipFileName: | _rels/.rels |
XML
| Application: | Microsoft Excel |
|---|---|
| AppVersion: | 2.5 |
| CreateDate: | 2015:06:05 18:19:34Z |
| ModifyDate: | 2019:01:22 17:51:49Z |
| LastModifiedBy: | Пользователь Microsoft Office |
XMP
| Creator: | openpyxl |
|---|
Total processes
90
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1868 | CMD.EXE /c REM.&&@p^o^w^e^r^s^h^e^l^l^|^|c:/*/*2/?al?.?x?" | C:\WINDOWS\SYSTEM32\CMD.EXE | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2644 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\Desktop\Payslip2.xlsx" | C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 16.0.6741.2048 Modules
| |||||||||||||||
| 5548 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\WINDOWS\system32\conhost.exe | CMD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 655
Read events
1 294
Write events
293
Delete events
68
Modification events
| (PID) Process: | (2644) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (2644) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 1 | |||
| (PID) Process: | (2644) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | +yo |
Value: 2B796F00540A00000100000000000000D4D5285CF9B2D40100000000 | |||
| (PID) Process: | (2644) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | :yo |
Value: 3A796F00540A000000000440010000005D382B5CF9B2D4013A0000001E8EDB854433A544A3A4051BFA11AB085D382B5CF9B2D40100000000000010000008551A00000000030000000000000002000000000000000000 | |||
| (PID) Process: | (2644) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | :yo |
Value: 3A796F00540A000000000440010000005D382B5CF9B2D4013C0000001E8EDB854433A544A3A4051BFA11AB085D382B5CF9B2D40100000000000010000008551A000000000300000000000000040000000000000000000000 | |||
| (PID) Process: | (2644) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2644) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2644) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2644) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2644) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\excel.exe\ETWMonitor\{02FD33DF-F746-4A10-93A0-2BC6273BC8E4} |
| Operation: | delete key | Name: | |
Value: | |||
Executable files
0
Suspicious files
2
Text files
3
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2644 | EXCEL.EXE | C:\Users\admin\Desktop\~$Payslip2.xlsx | — | |
MD5:— | SHA256:— | |||
| 2644 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_88614FFAD35D353421B8A7E1FE18FCE4 | der | |
MD5:— | SHA256:— | |||
| 2644 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\Payslip2.xlsx.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2644 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_88614FFAD35D353421B8A7E1FE18FCE4 | binary | |
MD5:— | SHA256:— | |||
| 2644 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 2644 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\OTele\{85DB8E1E-3344-44A5-A3A4-051BFA11AB08} (0) - 2644 - excel.exe - OTele.dat | pgc | |
MD5:— | SHA256:— | |||
| 2644 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\excel.exe_Rules.xml | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
11
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2328 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?16f570c0217bf5f6 | US | — | — | whitelisted |
2328 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?ec1013f96dba2e9b | US | — | — | whitelisted |
2644 | EXCEL.EXE | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAi4elAbvpzaLRZNPjlRv1U%3D | US | der | 471 b | whitelisted |
2328 | svchost.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAtqs7A%2Bsan2xGCSaqjN%2FrM%3D | US | der | 471 b | whitelisted |
2328 | svchost.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAiIzVJfGSRETRSlgpHeuVI%3D | US | der | 471 b | whitelisted |
2328 | svchost.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 471 b | whitelisted |
2328 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?986b7c10856ac7b0 | US | compressed | 55.2 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2644 | EXCEL.EXE | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2644 | EXCEL.EXE | 52.109.32.23:443 | roaming.officeapps.live.com | Microsoft Corporation | GB | whitelisted |
2328 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2644 | EXCEL.EXE | 52.109.8.19:443 | nexusrules.officeapps.live.com | Microsoft Corporation | US | whitelisted |
— | — | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2644 | EXCEL.EXE | 52.109.76.5:443 | odc.officeapps.live.com | Microsoft Corporation | IE | whitelisted |
2644 | EXCEL.EXE | 52.109.88.40:443 | nexus.officeapps.live.com | Microsoft Corporation | NL | whitelisted |
2328 | svchost.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2644 | EXCEL.EXE | 13.107.5.88:443 | ocos-office365-s2s.msedge.net | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ocos-office365-s2s.msedge.net |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
odc.officeapps.live.com |
| whitelisted |
nexus.officeapps.live.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
Process | Message |
|---|---|
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |