| File name: | WEXTRACT.EXE .MUI |
| Full analysis: | https://app.any.run/tasks/00a8ad17-6ae1-4dd7-a2e0-f8524cd33b15 |
| Verdict: | Malicious activity |
| Analysis date: | March 16, 2025, 13:44:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | E08DFB47C3E3D12845983EA61C810F10 |
| SHA1: | 330204E74F47A7CE0A0C4AE1FF2B259EC3D2284D |
| SHA256: | 6FE37A5615B3C47E4C6F7EB7ECA0BDCAB9E05DB9A39A1B6EC83917EED7BB72BA |
| SSDEEP: | 393216:RYkeNu9+t8QSKwdvnibZ0YlhWsJ9sTvFWlDqr33D9DQh4Ce36Y:RYkWM+pTwdvny7HYoZIz9DcY |
MALICIOUS
Executing a file with an untrusted certificate
- WEXTRACT.EXE .MUI.exe (PID: 2100)
- INSTAL~1.EXE (PID: 516)
- INSTAL~1.EXE (PID: 6468)
- INSTAL~1.EXE (PID: 1128)
- INSTAL~1.EXE (PID: 5756)
Changes Windows Defender settings
- INSTAL~1.EXE (PID: 5756)
Adds extension to the Windows Defender exclusion list
- INSTAL~1.EXE (PID: 5756)
Run PowerShell with an invisible window
- powershell.exe (PID: 2552)
- powershell.exe (PID: 1040)
- powershell.exe (PID: 7320)
- powershell.exe (PID: 6476)
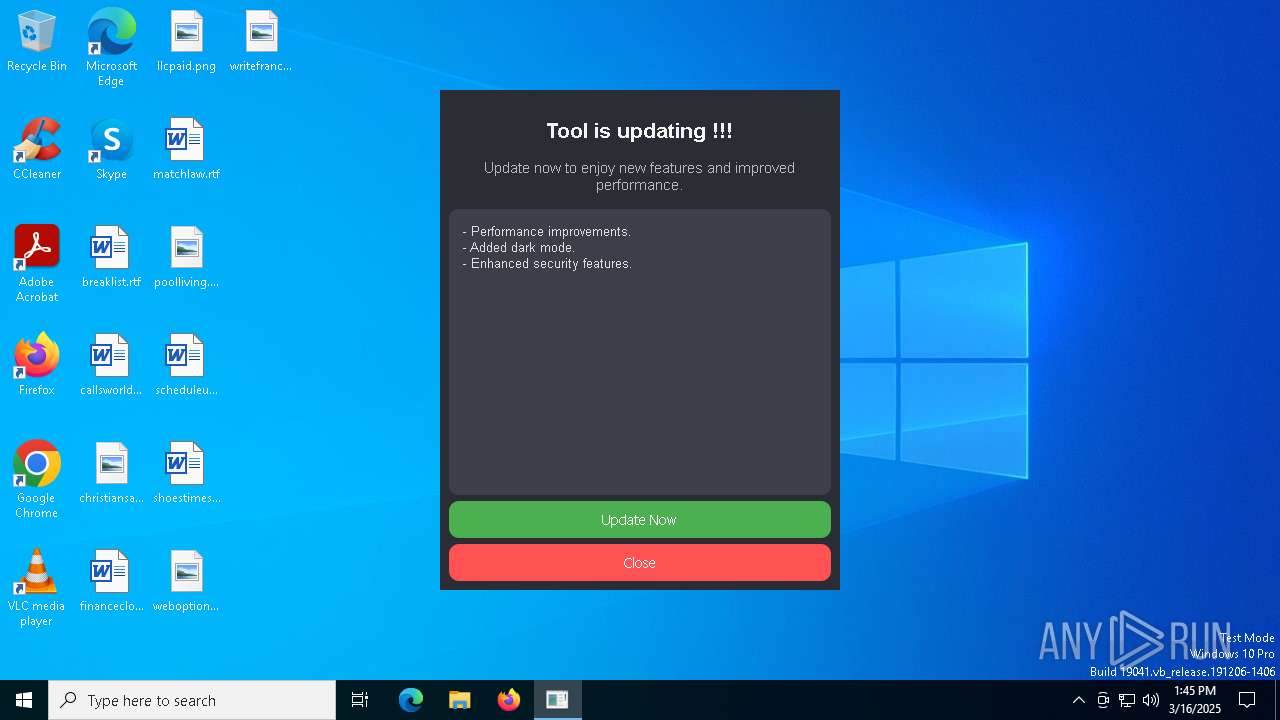
Script downloads file (POWERSHELL)
- powershell.exe (PID: 6476)
SUSPICIOUS
Process drops legitimate windows executable
- WEXTRACT.EXE .MUI.exe (PID: 2100)
- INSTAL~1.EXE (PID: 516)
- INSTAL~1.EXE (PID: 1128)
- powershell.exe (PID: 7320)
Executable content was dropped or overwritten
- WEXTRACT.EXE .MUI.exe (PID: 2100)
- INSTAL~1.EXE (PID: 516)
- INSTAL~1.EXE (PID: 1128)
- powershell.exe (PID: 7320)
Starts a Microsoft application from unusual location
- WEXTRACT.EXE .MUI.exe (PID: 2100)
Process drops python dynamic module
- INSTAL~1.EXE (PID: 516)
- INSTAL~1.EXE (PID: 1128)
- powershell.exe (PID: 7320)
The process drops C-runtime libraries
- INSTAL~1.EXE (PID: 516)
- INSTAL~1.EXE (PID: 1128)
- powershell.exe (PID: 7320)
Application launched itself
- INSTAL~1.EXE (PID: 516)
- INSTAL~1.EXE (PID: 6468)
- INSTAL~1.EXE (PID: 1128)
Loads Python modules
- INSTAL~1.EXE (PID: 6468)
- INSTAL~1.EXE (PID: 5756)
Reads security settings of Internet Explorer
- INSTAL~1.EXE (PID: 6468)
Reads the date of Windows installation
- INSTAL~1.EXE (PID: 6468)
Script adds exclusion extension to Windows Defender
- INSTAL~1.EXE (PID: 5756)
Starts POWERSHELL.EXE for commands execution
- INSTAL~1.EXE (PID: 5756)
- cmd.exe (PID: 736)
Executing commands from a ".bat" file
- INSTAL~1.EXE (PID: 5756)
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 736)
- powershell.exe (PID: 7320)
- powershell.exe (PID: 6476)
Starts CMD.EXE for commands execution
- INSTAL~1.EXE (PID: 5756)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 736)
- net.exe (PID: 5776)
Probably download files using WebClient
- cmd.exe (PID: 736)
INFO
The sample compiled with english language support
- WEXTRACT.EXE .MUI.exe (PID: 2100)
- INSTAL~1.EXE (PID: 516)
- INSTAL~1.EXE (PID: 1128)
- powershell.exe (PID: 7320)
Checks supported languages
- WEXTRACT.EXE .MUI.exe (PID: 2100)
- INSTAL~1.EXE (PID: 516)
- INSTAL~1.EXE (PID: 6468)
- INSTAL~1.EXE (PID: 1128)
- INSTAL~1.EXE (PID: 5756)
Reads the computer name
- INSTAL~1.EXE (PID: 516)
- INSTAL~1.EXE (PID: 6468)
- INSTAL~1.EXE (PID: 1128)
- INSTAL~1.EXE (PID: 5756)
Create files in a temporary directory
- WEXTRACT.EXE .MUI.exe (PID: 2100)
- INSTAL~1.EXE (PID: 516)
- INSTAL~1.EXE (PID: 1128)
- INSTAL~1.EXE (PID: 6468)
- INSTAL~1.EXE (PID: 5756)
Reads the machine GUID from the registry
- INSTAL~1.EXE (PID: 6468)
- INSTAL~1.EXE (PID: 5756)
Process checks computer location settings
- INSTAL~1.EXE (PID: 6468)
Disables trace logs
- powershell.exe (PID: 6476)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1040)
- powershell.exe (PID: 2552)
Checks proxy server information
- powershell.exe (PID: 6476)
- slui.exe (PID: 7672)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1040)
- powershell.exe (PID: 2552)
Reads the software policy settings
- slui.exe (PID: 7672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (91.4) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (4.2) |
| .exe | | | DOS Executable Generic (4.2) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2064:11:15 23:53:33+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.38 |
| CodeSize: | 40960 |
| InitializedDataSize: | 41406464 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1140 |
| OSVersion: | 10 |
| ImageVersion: | 10 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.26100.1 |
| ProductVersionNumber: | 11.0.26100.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Win32 Cabinet Self-Extractor |
| FileVersion: | 11.00.26100.1 (WinBuild.160101.0800) |
| InternalName: | Wextract |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | WEXTRACT.EXE .MUI |
| ProductName: | Internet Explorer |
| ProductVersion: | 11.00.26100.1 |
Total processes
146
Monitored processes
16
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\INSTAL~1.EXE | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\INSTAL~1.EXE | WEXTRACT.EXE .MUI.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 736 | C:\WINDOWS\system32\cmd.exe /c "C:\Users\Public\setup.bat" | C:\Windows\System32\cmd.exe | — | INSTAL~1.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | powershell -WindowStyle Hidden -Command "Add-MpPreference -ExclusionExtension '.bat'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | INSTAL~1.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\INSTAL~1.EXE" C:\Users\admin\AppData\Local\Temp\IXP000.TMP\INSTAL~1.EXE | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\INSTAL~1.EXE | INSTAL~1.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2100 | "C:\Users\admin\AppData\Local\Temp\WEXTRACT.EXE .MUI.exe" | C:\Users\admin\AppData\Local\Temp\WEXTRACT.EXE .MUI.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 11.00.26100.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2552 | powershell -WindowStyle Hidden -Command "Add-MpPreference -ExclusionExtension '.exe'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | INSTAL~1.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2984 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5244 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5756 | "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\INSTAL~1.EXE" C:\Users\admin\AppData\Local\Temp\IXP000.TMP\INSTAL~1.EXE | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\INSTAL~1.EXE | — | INSTAL~1.EXE | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
23 503
Read events
23 503
Write events
0
Delete events
0
Modification events
Executable files
214
Suspicious files
500
Text files
1 381
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2100 | WEXTRACT.EXE .MUI.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\INSTAL~1.EXE | — | |
MD5:— | SHA256:— | |||
| 516 | INSTAL~1.EXE | C:\Users\admin\AppData\Local\Temp\_MEI5162\PySide2\QtCore.pyd | executable | |
MD5:FD7831D4694005479AB5282266D41587 | SHA256:11C4B8859D2E1FD1BB315EDB21112662C674D739992ABC545AFAB894D3848CEF | |||
| 516 | INSTAL~1.EXE | C:\Users\admin\AppData\Local\Temp\_MEI5162\MSVCP140_1.dll | executable | |
MD5:A0B595F95BE9CCE12BFF7EF199F874C4 | SHA256:B05F3DFD4E999C3E110219FB59151CBAA322757F4F3CE52B64DDDC853E5C105C | |||
| 2100 | WEXTRACT.EXE .MUI.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\API-MS~1.DLL | executable | |
MD5:07EBE4D5CEF3301CCF07430F4C3E32D8 | SHA256:8F8B79150E850ACC92FD6AAB614F6E3759BEA875134A62087D5DD65581E3001F | |||
| 2100 | WEXTRACT.EXE .MUI.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\API-MS~3.DLL | executable | |
MD5:624401F31A706B1AE2245EB19264DC7F | SHA256:58A8D69DF60ECBEE776CD9A74B2A32B14BF2B0BD92D527EC5F19502A0D3EB8E9 | |||
| 2100 | WEXTRACT.EXE .MUI.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\APDEA0~1.DLL | executable | |
MD5:5A72A803DF2B425D5AAFF21F0F064011 | SHA256:629E52BA4E2DCA91B10EF7729A1722888E01284EED7DDA6030D0A1EC46C94086 | |||
| 2100 | WEXTRACT.EXE .MUI.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\AP87F4~1.DLL | executable | |
MD5:0F7D418C05128246AFA335A1FB400CB9 | SHA256:5C9BC70586AD538B0DF1FCF5D6F1F3527450AE16935AA34BD7EB494B4F1B2DB9 | |||
| 2100 | WEXTRACT.EXE .MUI.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\APC7B0~1.DLL | executable | |
MD5:721B60B85094851C06D572F0BD5D88CD | SHA256:DAC867476CAA42FF8DF8F5DFE869FFD56A18DADEE17D47889AFB69ED6519AFBF | |||
| 516 | INSTAL~1.EXE | C:\Users\admin\AppData\Local\Temp\_MEI5162\MSVCP140.dll | executable | |
MD5:6DA7F4530EDB350CF9D967D969CCECF8 | SHA256:9FEE6F36547D6F6EA7CA0338655555DBA6BB0F798BC60334D29B94D1547DA4DA | |||
| 516 | INSTAL~1.EXE | C:\Users\admin\AppData\Local\Temp\_MEI5162\PySide2\QtGui.pyd | executable | |
MD5:98B780F010162FD6824E343C5E6B8D4A | SHA256:BEC878849CBA1D0FC79E6D313E5B28E1DA9B5CA903673A6634768F52DF33BC4F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
29
DNS requests
18
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1228 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2644 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2644 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1228 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1228 | backgroundTaskHost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
github.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |