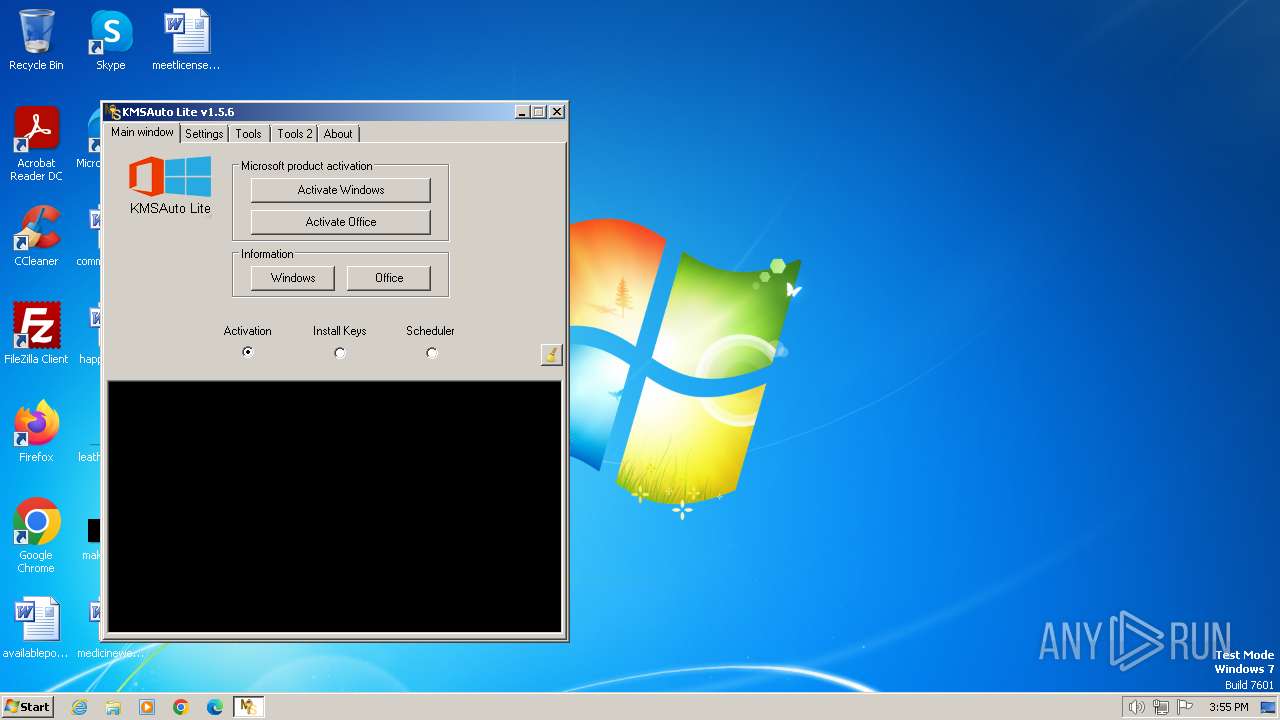
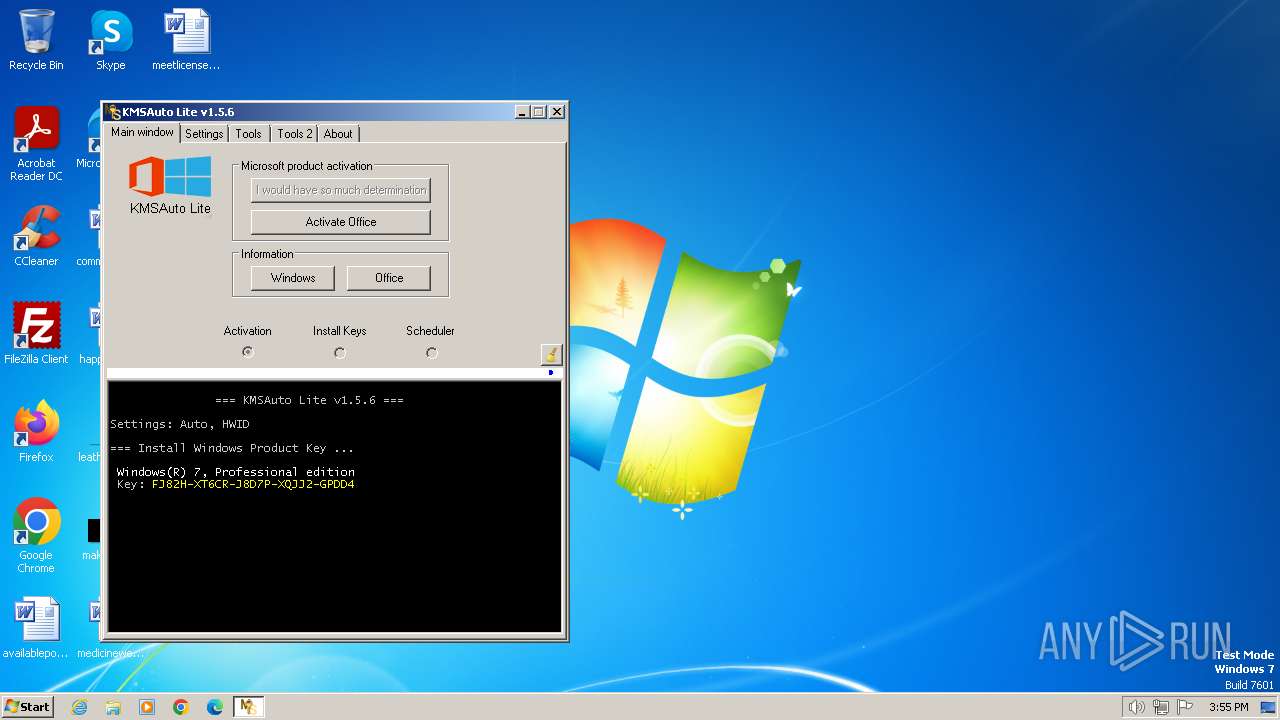
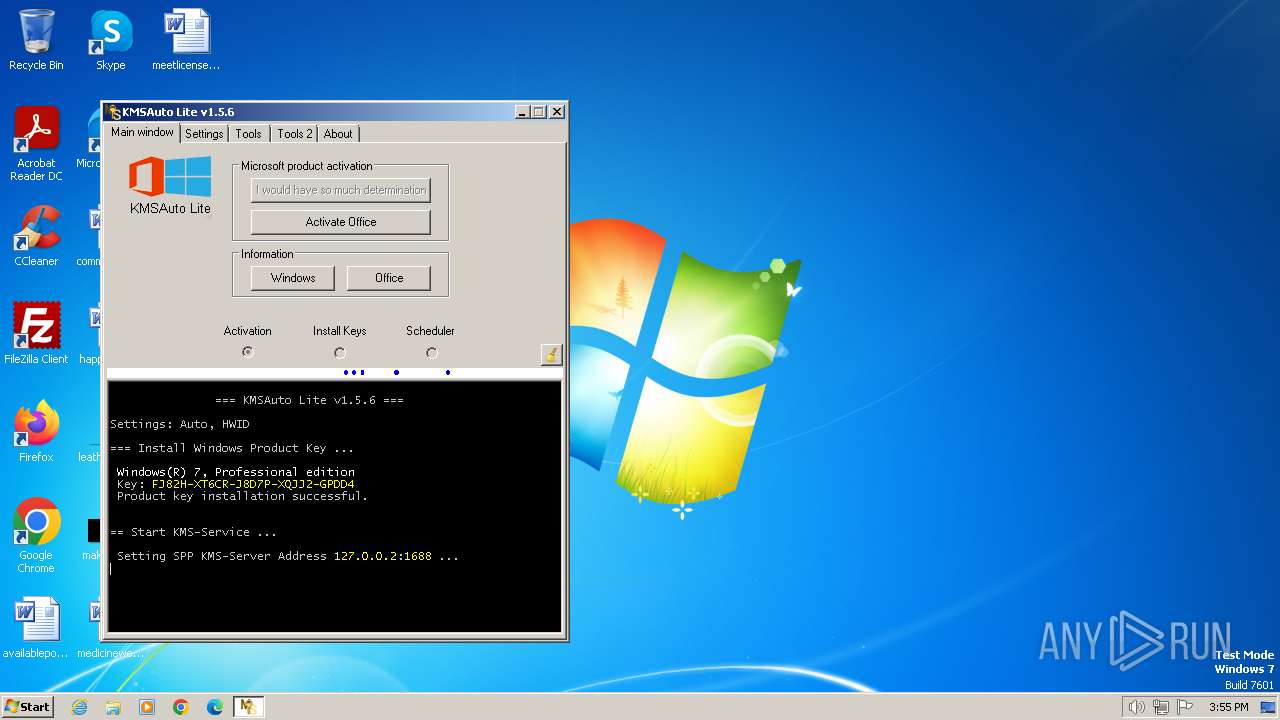
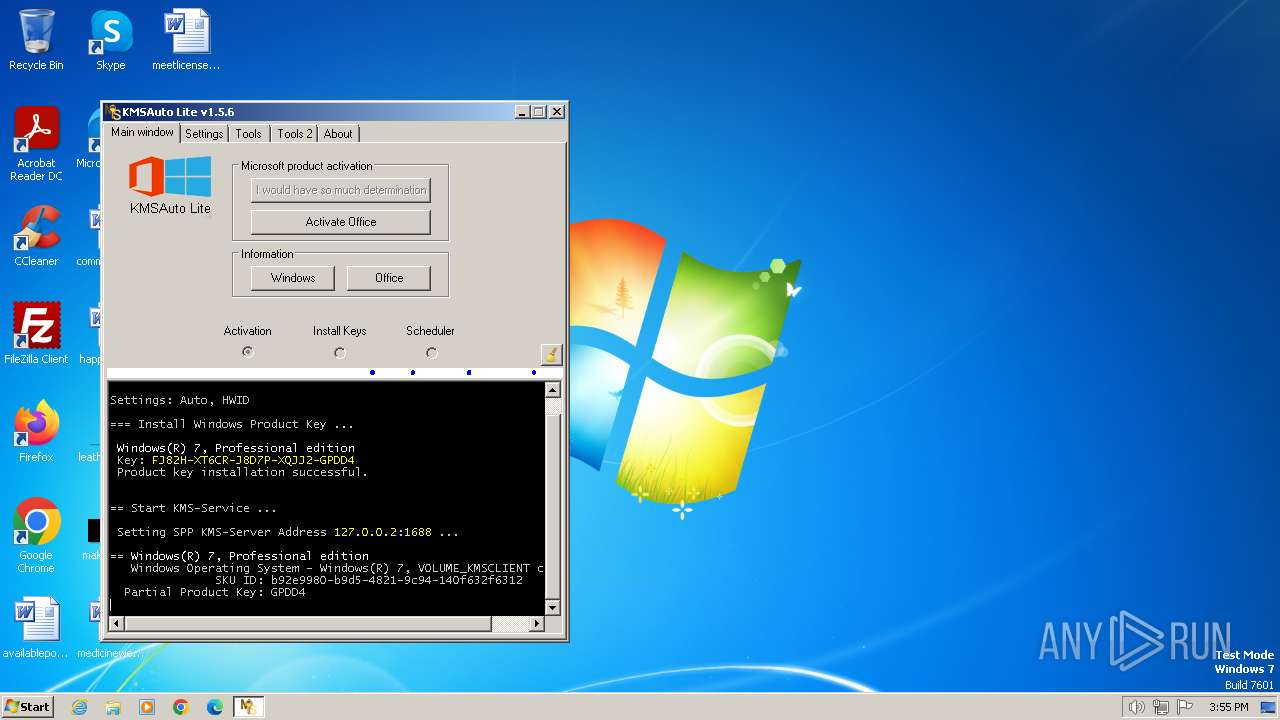
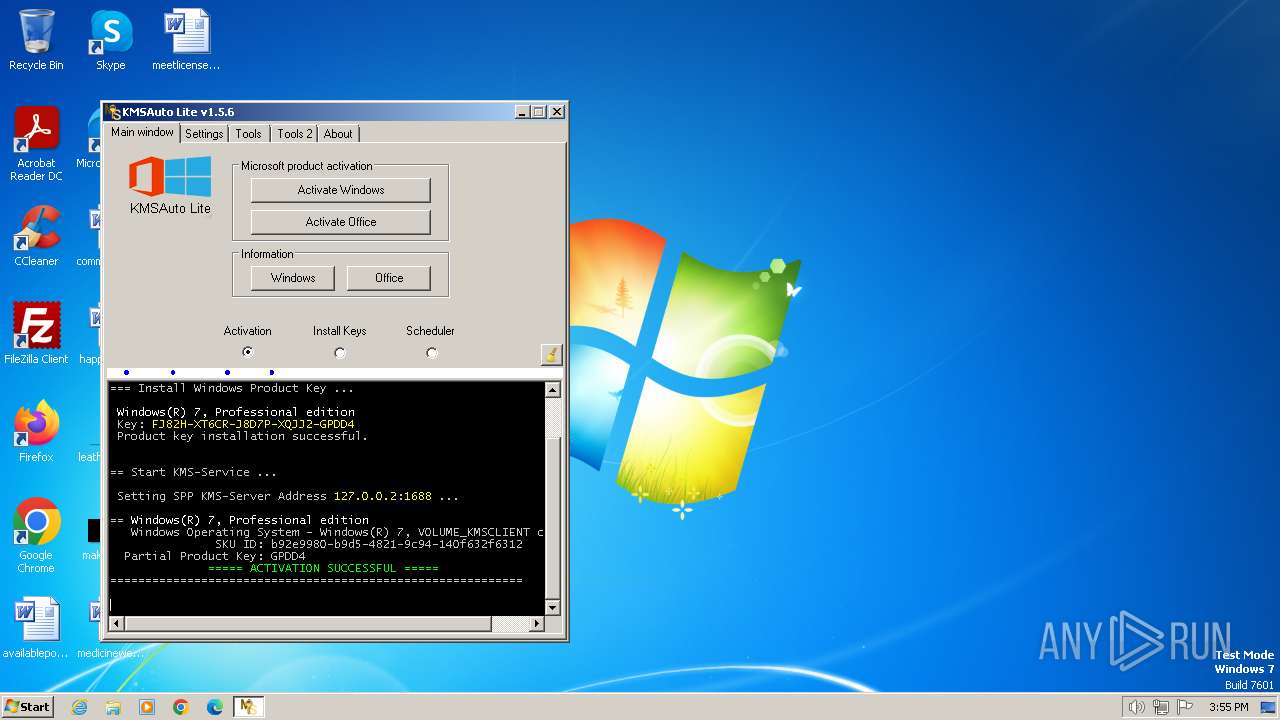
| File name: | KMSAuto.exe |
| Full analysis: | https://app.any.run/tasks/feea4e75-76ef-4245-87e2-834ed176a4f8 |
| Verdict: | Malicious activity |
| Analysis date: | December 26, 2023, 15:55:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | DBFB5E6381185DD6AE408A9E9E972FB4 |
| SHA1: | E4A333AFE159AE73F751FEB5CDC3E2957396A2D5 |
| SHA256: | 6FCE8010511D2B513D5589A148B52F0CE33083DEC68EE23463300AD15CC6DD7E |
| SSDEEP: | 98304:eFB6kaAoFRjuJpuJtY1Gd4a+VlOVZxQpuafa3sKkqQ9hE3xEUYVnMnSH5hXiJ/3o:xsSaf1olqCZfv8JusnZbiJEd |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- KMSAuto.exe (PID: 2416)
Uses WMIC.EXE
- KMSAuto.exe (PID: 2416)
Reads the Internet Settings
- WMIC.exe (PID: 572)
- signtool.exe (PID: 1504)
- WMIC.exe (PID: 1540)
- WMIC.exe (PID: 1880)
- WMIC.exe (PID: 796)
- WMIC.exe (PID: 2664)
Reads security settings of Internet Explorer
- signtool.exe (PID: 1504)
Reads settings of System Certificates
- signtool.exe (PID: 1504)
Checks Windows Trust Settings
- signtool.exe (PID: 1504)
Starts SC.EXE for service management
- cmd.exe (PID: 2900)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 3232)
- cmd.exe (PID: 3300)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 2468)
- cmd.exe (PID: 3636)
- cmd.exe (PID: 3428)
- cmd.exe (PID: 2484)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 552)
- cmd.exe (PID: 2756)
Uses WMIC.EXE to obtain Windows Installer data
- KMSAuto.exe (PID: 2416)
Uses WMIC.EXE to obtain service application data
- KMSAuto.exe (PID: 2416)
Adds/modifies Windows certificates
- signtool.exe (PID: 1504)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2544)
- cmd.exe (PID: 3068)
- cmd.exe (PID: 3064)
- cmd.exe (PID: 2972)
The process downloads a VBScript from the remote host
- cmd.exe (PID: 3052)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 2944)
- cscript.exe (PID: 3124)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 2944)
- cscript.exe (PID: 3124)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 2944)
- cscript.exe (PID: 3124)
The process executes VB scripts
- cmd.exe (PID: 3052)
- cmd.exe (PID: 3140)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 2944)
- cscript.exe (PID: 3124)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 2944)
- cscript.exe (PID: 3124)
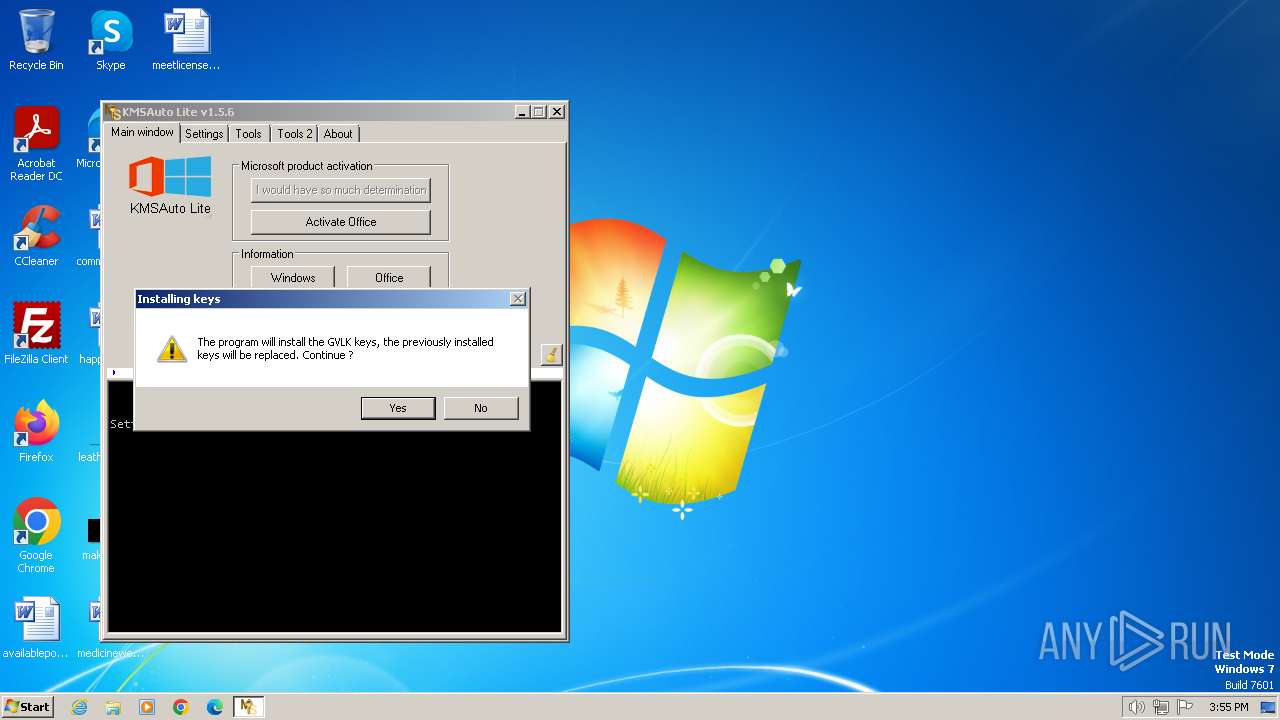
Creates or modifies Windows services
- KMSAuto.exe (PID: 2416)
INFO
Reads product name
- KMSAuto.exe (PID: 2416)
Checks supported languages
- KMSAuto.exe (PID: 2416)
- signtool.exe (PID: 1504)
- KMSSS.exe (PID: 908)
Process drops legitimate windows executable
- KMSAuto.exe (PID: 2416)
Reads Environment values
- KMSAuto.exe (PID: 2416)
Drops the executable file immediately after the start
- KMSAuto.exe (PID: 2416)
Reads the machine GUID from the registry
- signtool.exe (PID: 1504)
- KMSSS.exe (PID: 908)
Create files in a temporary directory
- KMSAuto.exe (PID: 2416)
- signtool.exe (PID: 1504)
- KMSSS.exe (PID: 908)
Reads the computer name
- signtool.exe (PID: 1504)
- KMSSS.exe (PID: 908)
- KMSAuto.exe (PID: 2416)
Executes as Windows Service
- KMSSS.exe (PID: 908)
Reads security settings of Internet Explorer
- cscript.exe (PID: 2944)
- cscript.exe (PID: 3124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (64.1) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.5) |
| .exe | | | Win32 Executable (generic) (10.6) |
| .exe | | | Generic Win/DOS Executable (4.7) |
| .exe | | | DOS Executable Generic (4.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:04:18 11:17:22+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 5070848 |
| InitializedDataSize: | 49152 |
| UninitializedDataSize: | 1314816 |
| EntryPoint: | 0x617280 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.5.6.0 |
| ProductVersionNumber: | 1.5.6.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
Total processes
105
Monitored processes
43
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Users\admin\AppData\Local\Temp\KMSAuto.exe" | C:\Users\admin\AppData\Local\Temp\KMSAuto.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 240 | Netsh.exe Advfirewall Firewall add rule name=0pen_Port_KMS2 dir=out action=allow protocol=TCP localport=1688 | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 548 | "C:\Windows\System32\cmd.exe" /c copy C:\Windows\system32\Tasks\KMSAuto "C:\Users\admin\AppData\Local\Temp\KMSAuto.tmp" /Y | C:\Windows\System32\cmd.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 552 | "C:\Windows\System32\cmd.exe" /c Netsh.exe Advfirewall Firewall add rule name=0pen_Port_KMS dir=in action=allow protocol=TCP localport=1688 | C:\Windows\System32\cmd.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 572 | "wmic.exe" path Win32_NetworkAdapter get ServiceName /value /FORMAT:List | C:\Windows\System32\wbem\WMIC.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 796 | "wmic.exe" path SoftwareLicensingService get Version /value /FORMAT:List | C:\Windows\System32\wbem\WMIC.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 908 | "C:\Users\admin\AppData\Local\Temp\KMSAuto_Files\bin\KMSSS.exe" -Port 1688 -PWin RandomKMSPID -PO14 RandomKMSPID -PO15 RandomKMSPID -PO16 RandomKMSPID -AI 43200 -RI 43200 KillProcessOnPort -Log -IP | C:\Users\admin\AppData\Local\Temp\KMSAuto_Files\bin\KMSSS.exe | — | services.exe | |||||||||||
User: SYSTEM Company: MSFree Inc. Integrity Level: SYSTEM Description: KMS emulator by Ratiborus. Exit code: 0 Version: 2.0.7.0 Modules
| |||||||||||||||
| 984 | Netsh.exe Advfirewall Firewall add rule name=0pen_Port_KMS dir=in action=allow protocol=TCP localport=1688 | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1000 | sc.exe create KMSEmulator binpath= temp.exe type= own start= auto | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1504 | "C:\Users\admin\AppData\Local\Temp\signtool.exe" verify /v /ph /sha1 648384a4dee53d4c1c87e10d67cc99307ccc9c98 "C:\Users\admin\AppData\Local\Temp\KMSAuto.exe" | C:\Users\admin\AppData\Local\Temp\signtool.exe | KMSAuto.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Authenticode(R) - signing and verifying tool Exit code: 1 Version: 4.00 (rs1_release_sec.170105-1850) Modules
| |||||||||||||||
Total events
8 166
Read events
7 870
Write events
296
Delete events
0
Modification events
| (PID) Process: | (1504) signtool.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1504) signtool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\E12DFB4B41D7D9C32B30514BAC1D81D8385E2D46 |
| Operation: | write | Name: | Blob |
Value: 68000000010000000800000000409120D035D901090000000100000022000000302006082B06010505070303060A2B0601040182370A030406082B060105050703080F0000000100000014000000F45A0858C9CD920E647BAD539AB9F1CFC77F24CB030000000100000014000000E12DFB4B41D7D9C32B30514BAC1D81D8385E2D461D0000000100000010000000F919B9CCCE1E59C2E785F7DC2CCF6708140000000100000014000000DAED6474149C143CABDD99A9BD5B284D8B3CC9D86200000001000000200000006FFF78E400A70C11011CD85977C459FB5AF96A3DF0540820D0F4B8607875E58F0B000000010000002A0000005300650063007400690067006F0020002800550054004E0020004F0062006A0065006300740029000000190000000100000010000000E843AC3B52EC8C297FA948C9B1FB28197E0000000100000008000000000063F58926D70120000000010000006A040000308204663082034EA003020102021044BE0C8B500024B411D3362DE0B35F1B300D06092A864886F70D0101050500308195310B3009060355040613025553310B3009060355040813025554311730150603550407130E53616C74204C616B652043697479311E301C060355040A131554686520555345525452555354204E6574776F726B3121301F060355040B1318687474703A2F2F7777772E7573657274727573742E636F6D311D301B0603550403131455544E2D5553455246697273742D4F626A656374301E170D3939303730393138333132305A170D3139303730393138343033365A308195310B3009060355040613025553310B3009060355040813025554311730150603550407130E53616C74204C616B652043697479311E301C060355040A131554686520555345525452555354204E6574776F726B3121301F060355040B1318687474703A2F2F7777772E7573657274727573742E636F6D311D301B0603550403131455544E2D5553455246697273742D4F626A65637430820122300D06092A864886F70D01010105000382010F003082010A0282010100CEAA813FA3A36178AA31005595119E270F1F1CDF3A9B826830C04A611DF12F0EFABE79F7A523EF55519684CDDBE3B96E3E31D80A2067C7F4D9BF94EB47043E02CE2AA25D870409F6309D188A97B2AA1CFC41D2A136CBFB3D91BAE7D97035FAE4E790C39BA39BD33CF5129977B1B709E068E61CB8F39463886A6AFE0B76C9BEF422E467B9AB1A5E77C18507DD0D6CBFEE06C7776A419EA70FD7FBEE9417B7FC85BEA4ABC41C31DDD7B6D1E4F0EFDF168FB25293D7A1D489A1072EBFE10112421E1AE1D89534DB647928FFBA2E11C2E5E85B9248FB470BC26CDAAD328341F3A5E54170FD65906DFAFA51C4F9BD962B19042CD36DA7DCF07F6F8365E26AAB8786750203010001A381AF3081AC300B0603551D0F0404030201C6300F0603551D130101FF040530030101FF301D0603551D0E04160414DAED6474149C143CABDD99A9BD5B284D8B3CC9D830420603551D1F043B30393037A035A0338631687474703A2F2F63726C2E7573657274727573742E636F6D2F55544E2D5553455246697273742D4F626A6563742E63726C30290603551D250422302006082B0601050507030306082B06010505070308060A2B0601040182370A0304300D06092A864886F70D01010505000382010100081F52B1374478DBFDCEB9DA959698AA556480B55A40DD21A5C5C1F35F2C4CC8475A69EAE8F03535F4D025F3C8A6A4874ABD1BB17308BDD4C3CAB635BB59867731CDA78014AE13EFFCB148F96B25252D51B62C6D45C198C88A565D3EEE434E3E6B278ED03A4B850B5FD3ED6AA775CBD15A872F3975135A72B002819FBEF00F845420626C69D4E14DC60D9943010D12968C789DBF50A2B144AA6ACF177ACF6F0FD4F824555FF0341649663E5046C96371383162B862B9F353AD6CB52BA212AA194F09DA5EE793C68E1408FEF0308018A086854DC87DD78B03FE6ED5F79D16AC922CA023E59C91521F94DF179473C3B3C1C17105200078BD13521DA83ECD001FC8 | |||
| (PID) Process: | (1504) signtool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\E12DFB4B41D7D9C32B30514BAC1D81D8385E2D46 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000A7F2E41606411150306B9CE3B49CB0C97E0000000100000008000000000063F58926D701190000000100000010000000E843AC3B52EC8C297FA948C9B1FB28190B000000010000002A0000005300650063007400690067006F0020002800550054004E0020004F0062006A00650063007400290000006200000001000000200000006FFF78E400A70C11011CD85977C459FB5AF96A3DF0540820D0F4B8607875E58F140000000100000014000000DAED6474149C143CABDD99A9BD5B284D8B3CC9D81D0000000100000010000000F919B9CCCE1E59C2E785F7DC2CCF6708030000000100000014000000E12DFB4B41D7D9C32B30514BAC1D81D8385E2D460F0000000100000014000000F45A0858C9CD920E647BAD539AB9F1CFC77F24CB090000000100000022000000302006082B06010505070303060A2B0601040182370A030406082B0601050507030868000000010000000800000000409120D035D90120000000010000006A040000308204663082034EA003020102021044BE0C8B500024B411D3362DE0B35F1B300D06092A864886F70D0101050500308195310B3009060355040613025553310B3009060355040813025554311730150603550407130E53616C74204C616B652043697479311E301C060355040A131554686520555345525452555354204E6574776F726B3121301F060355040B1318687474703A2F2F7777772E7573657274727573742E636F6D311D301B0603550403131455544E2D5553455246697273742D4F626A656374301E170D3939303730393138333132305A170D3139303730393138343033365A308195310B3009060355040613025553310B3009060355040813025554311730150603550407130E53616C74204C616B652043697479311E301C060355040A131554686520555345525452555354204E6574776F726B3121301F060355040B1318687474703A2F2F7777772E7573657274727573742E636F6D311D301B0603550403131455544E2D5553455246697273742D4F626A65637430820122300D06092A864886F70D01010105000382010F003082010A0282010100CEAA813FA3A36178AA31005595119E270F1F1CDF3A9B826830C04A611DF12F0EFABE79F7A523EF55519684CDDBE3B96E3E31D80A2067C7F4D9BF94EB47043E02CE2AA25D870409F6309D188A97B2AA1CFC41D2A136CBFB3D91BAE7D97035FAE4E790C39BA39BD33CF5129977B1B709E068E61CB8F39463886A6AFE0B76C9BEF422E467B9AB1A5E77C18507DD0D6CBFEE06C7776A419EA70FD7FBEE9417B7FC85BEA4ABC41C31DDD7B6D1E4F0EFDF168FB25293D7A1D489A1072EBFE10112421E1AE1D89534DB647928FFBA2E11C2E5E85B9248FB470BC26CDAAD328341F3A5E54170FD65906DFAFA51C4F9BD962B19042CD36DA7DCF07F6F8365E26AAB8786750203010001A381AF3081AC300B0603551D0F0404030201C6300F0603551D130101FF040530030101FF301D0603551D0E04160414DAED6474149C143CABDD99A9BD5B284D8B3CC9D830420603551D1F043B30393037A035A0338631687474703A2F2F63726C2E7573657274727573742E636F6D2F55544E2D5553455246697273742D4F626A6563742E63726C30290603551D250422302006082B0601050507030306082B06010505070308060A2B0601040182370A0304300D06092A864886F70D01010505000382010100081F52B1374478DBFDCEB9DA959698AA556480B55A40DD21A5C5C1F35F2C4CC8475A69EAE8F03535F4D025F3C8A6A4874ABD1BB17308BDD4C3CAB635BB59867731CDA78014AE13EFFCB148F96B25252D51B62C6D45C198C88A565D3EEE434E3E6B278ED03A4B850B5FD3ED6AA775CBD15A872F3975135A72B002819FBEF00F845420626C69D4E14DC60D9943010D12968C789DBF50A2B144AA6ACF177ACF6F0FD4F824555FF0341649663E5046C96371383162B862B9F353AD6CB52BA212AA194F09DA5EE793C68E1408FEF0308018A086854DC87DD78B03FE6ED5F79D16AC922CA023E59C91521F94DF179473C3B3C1C17105200078BD13521DA83ECD001FC8 | |||
| (PID) Process: | (1600) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (984) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2324) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (240) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2416) KMSAuto.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\KMSEmulator |
| Operation: | write | Name: | ImagePath |
Value: temp.exe | |||
| (PID) Process: | (2880) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform |
| Operation: | write | Name: | KeyManagementServiceName |
Value: 127.0.0.2 | |||
| (PID) Process: | (2940) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform |
| Operation: | write | Name: | KeyManagementServicePort |
Value: 1688 | |||
Executable files
2
Suspicious files
4
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2416 | KMSAuto.exe | C:\Users\admin\AppData\Local\Temp\signtool.exe | executable | |
MD5:05624E6D27EAEF0DB0673AE627BD6027 | SHA256:962A92821F54A1E706AA989973130FDC1072C7BD8B9E6D11EA1050B46EB9D313 | |||
| 2416 | KMSAuto.exe | C:\Users\admin\AppData\Local\Temp\KMSAuto_Files\bin\KMSSS.exe | executable | |
MD5:01A80AAD5DABED1C1580F7E00213CF9D | SHA256:FD7499214ABAA13BF56D006AB7DE78EB8D6ADF17926C24ACE024D067049BC81D | |||
| 1504 | signtool.exe | C:\Users\admin\AppData\Local\Temp\Cab357.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 2416 | KMSAuto.exe | C:\Users\admin\AppData\Local\Temp\slmgr.vbs | text | |
MD5:38482A5013D8AB40DF0FB15EAE022C57 | SHA256:AC5C46B97345465A96E9AE1EDAFF44B191A39BF3D03DC1128090B8FFA92A16F8 | |||
| 908 | KMSSS.exe | C:\Users\admin\AppData\Local\Temp\KMSAuto_Files\bin\KMSSS.log | text | |
MD5:81051BCC2CF1BEDF378224B0A93E2877 | SHA256:7EB70257593DA06F682A3DDDA54A9D260D4FC514F645237F5CA74B08F8DA61A6 | |||
| 1504 | signtool.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:B8373B7F6D63982609F7950A85DD303F | SHA256:20A4F15C877A561EC24724EC6F0A26119BA216BB63DEBF3673949E3CD80DF2FC | |||
| 2416 | KMSAuto.exe | C:\Users\admin\AppData\Local\Temp\KMSAutoLite.ini | text | |
MD5:5FA08448CA529C31FD26E4597875FD77 | SHA256:D1AC2BF66F452CD5878E4547896D54B8F56B455E4E83F80290E14E2580BEA36A | |||
| 1504 | signtool.exe | C:\Users\admin\AppData\Local\Temp\Tar358.tmp | binary | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 1504 | signtool.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1504 | signtool.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?bcb3af3000b88b06 | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1504 | signtool.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |