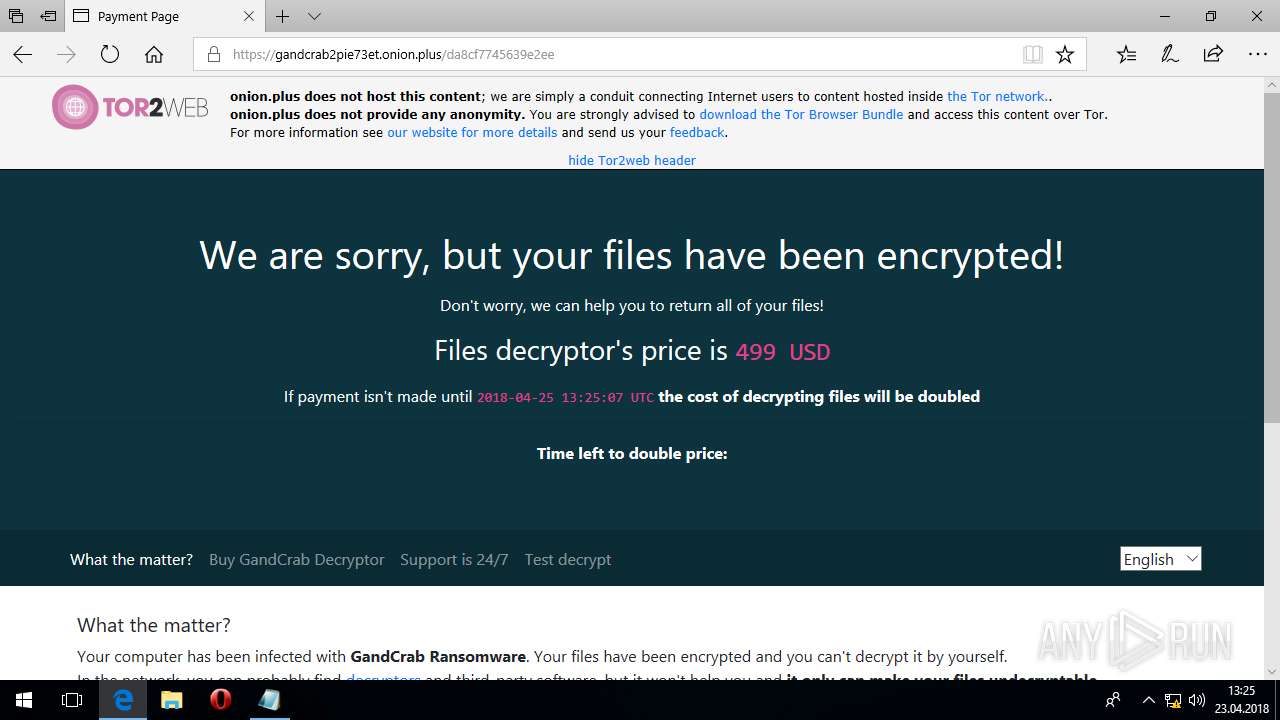
| File name: | grounded.exe |
| Full analysis: | https://app.any.run/tasks/a6febcff-3db9-4a49-a174-3217c94e1e31 |
| Verdict: | Malicious activity |
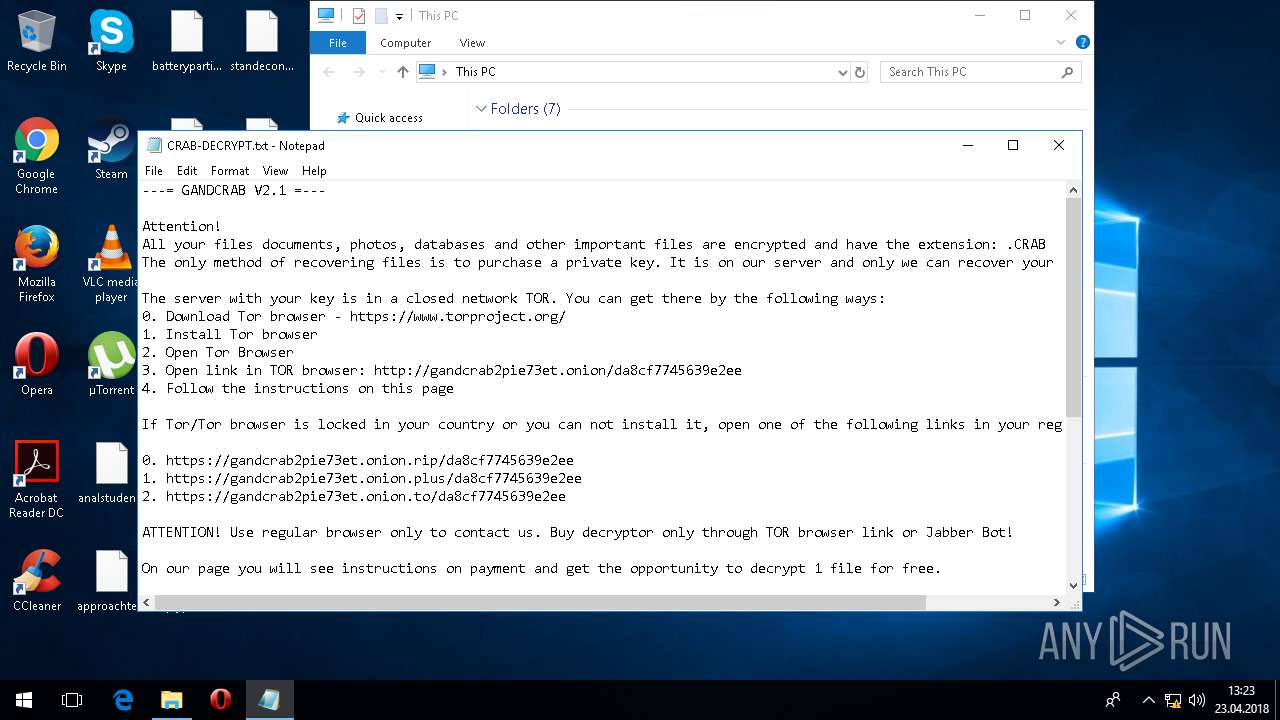
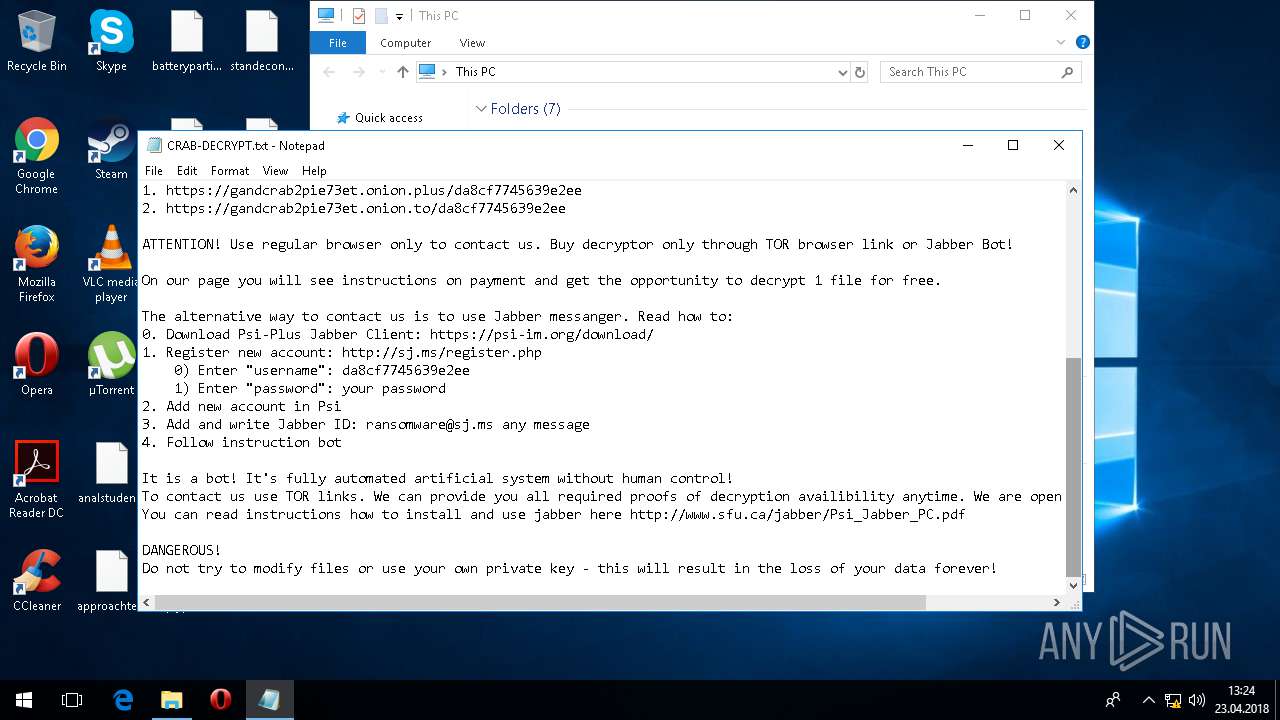
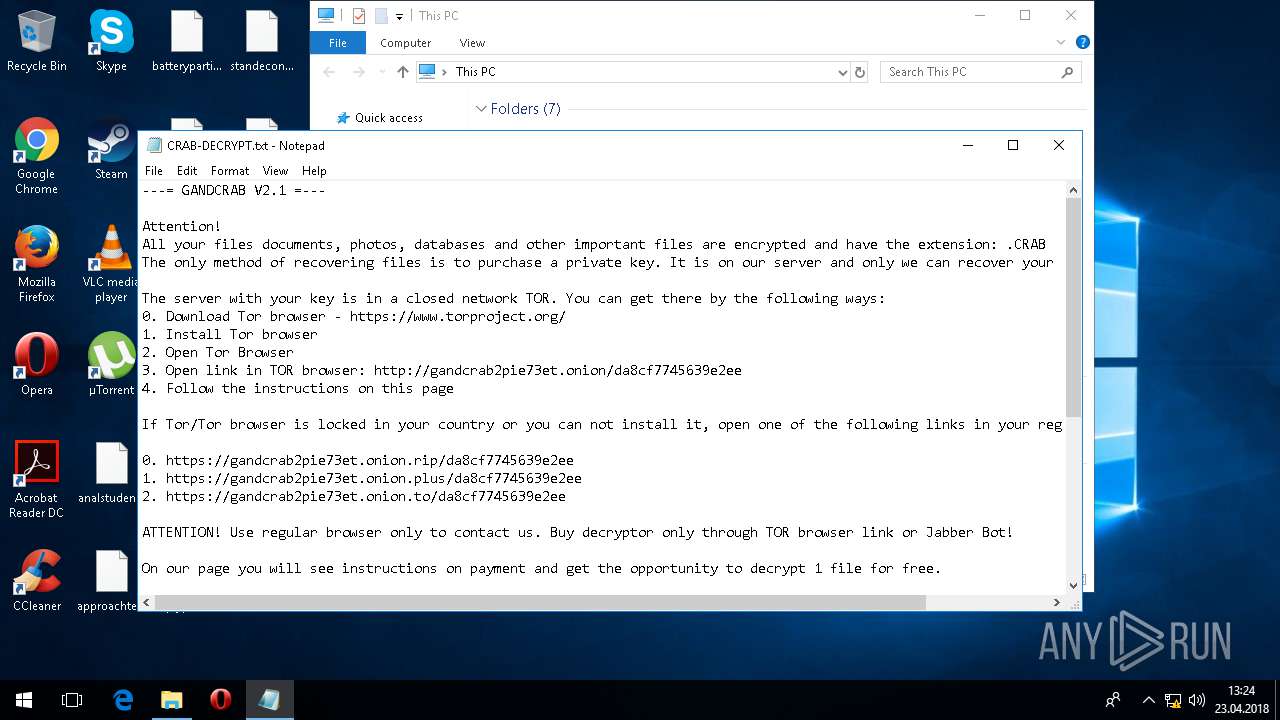
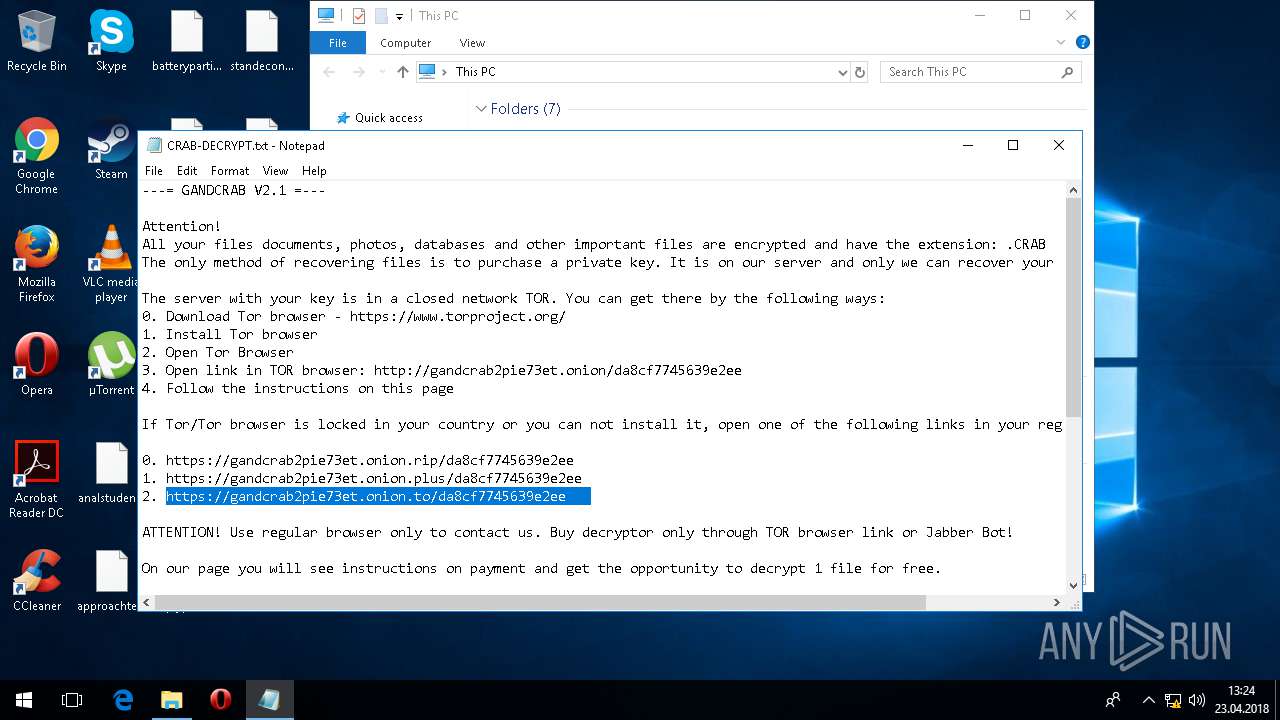
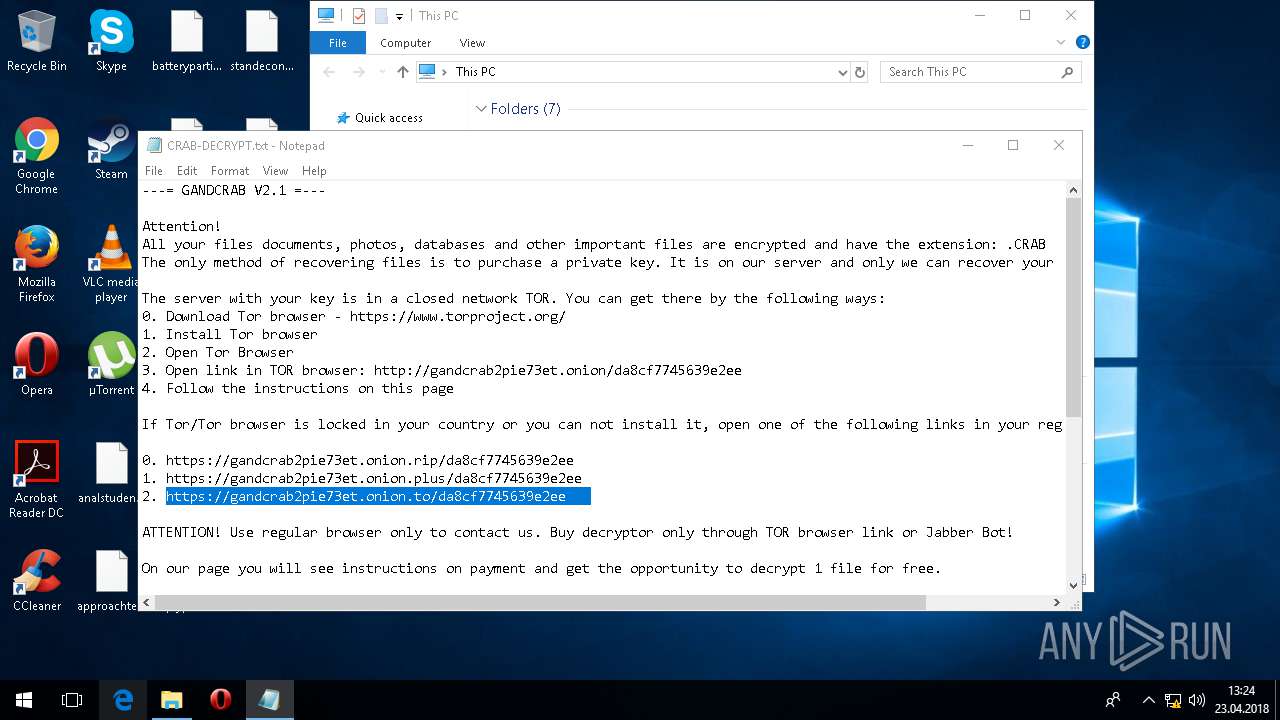
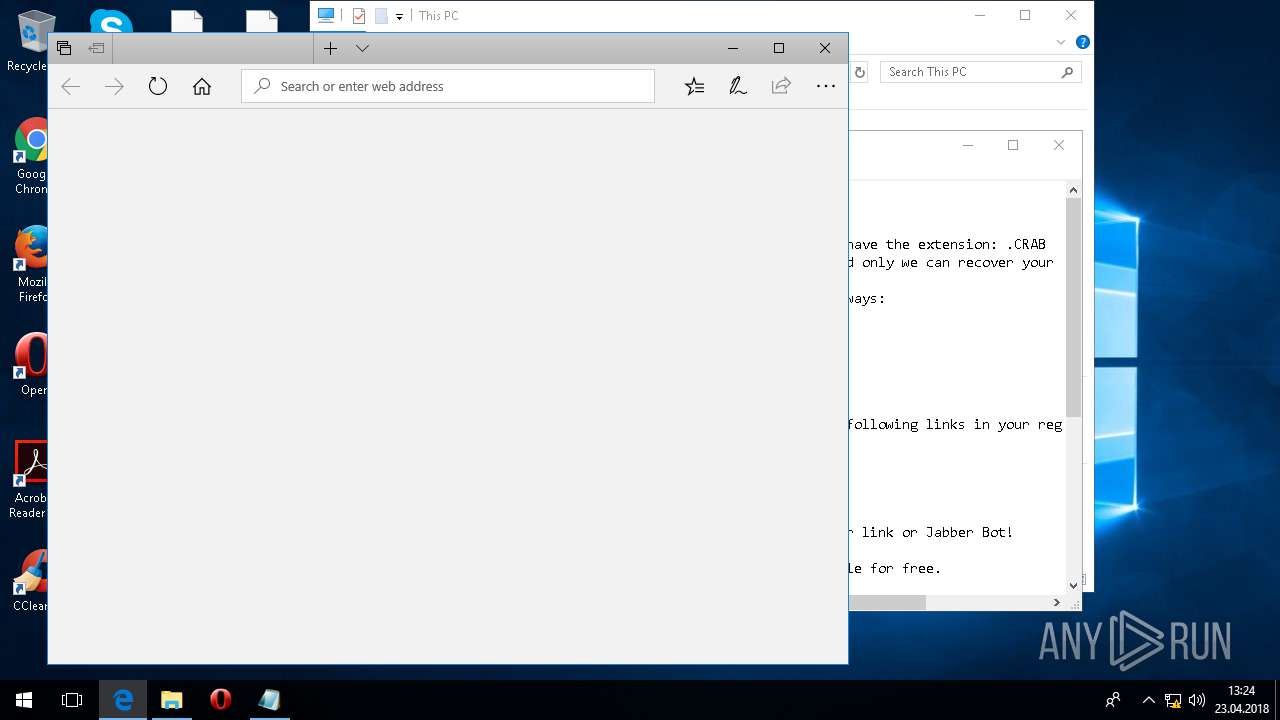
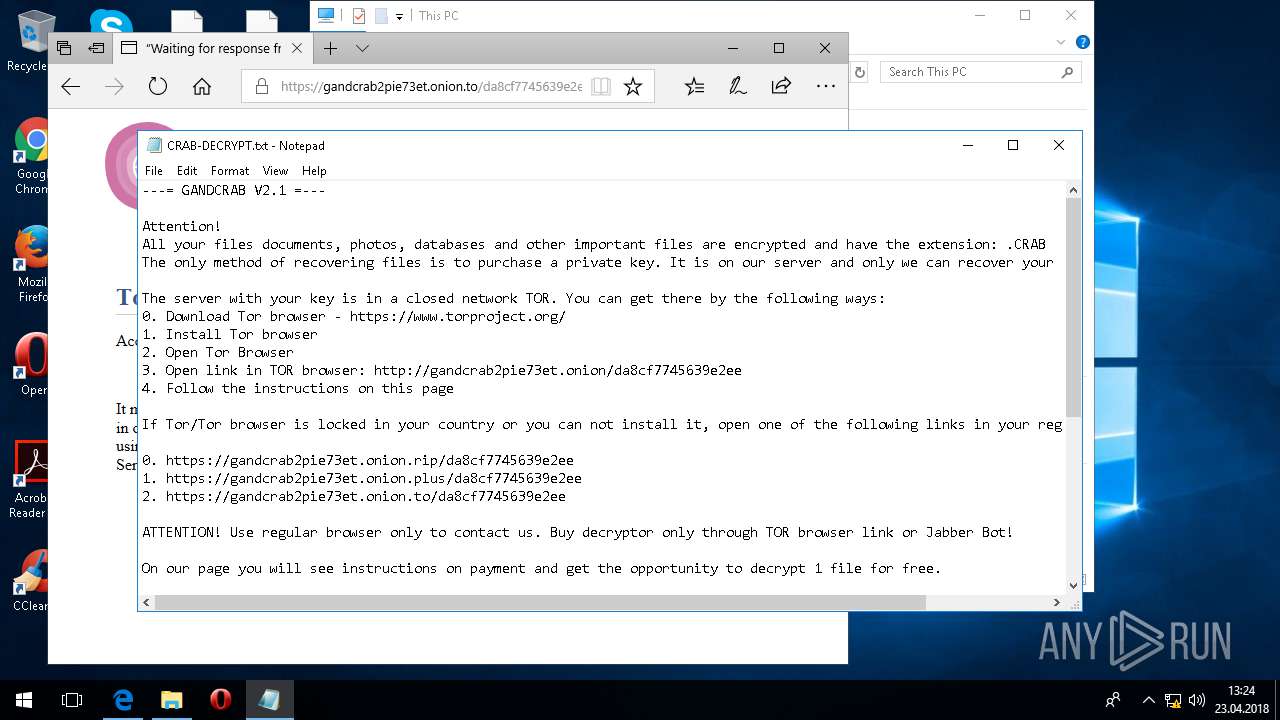
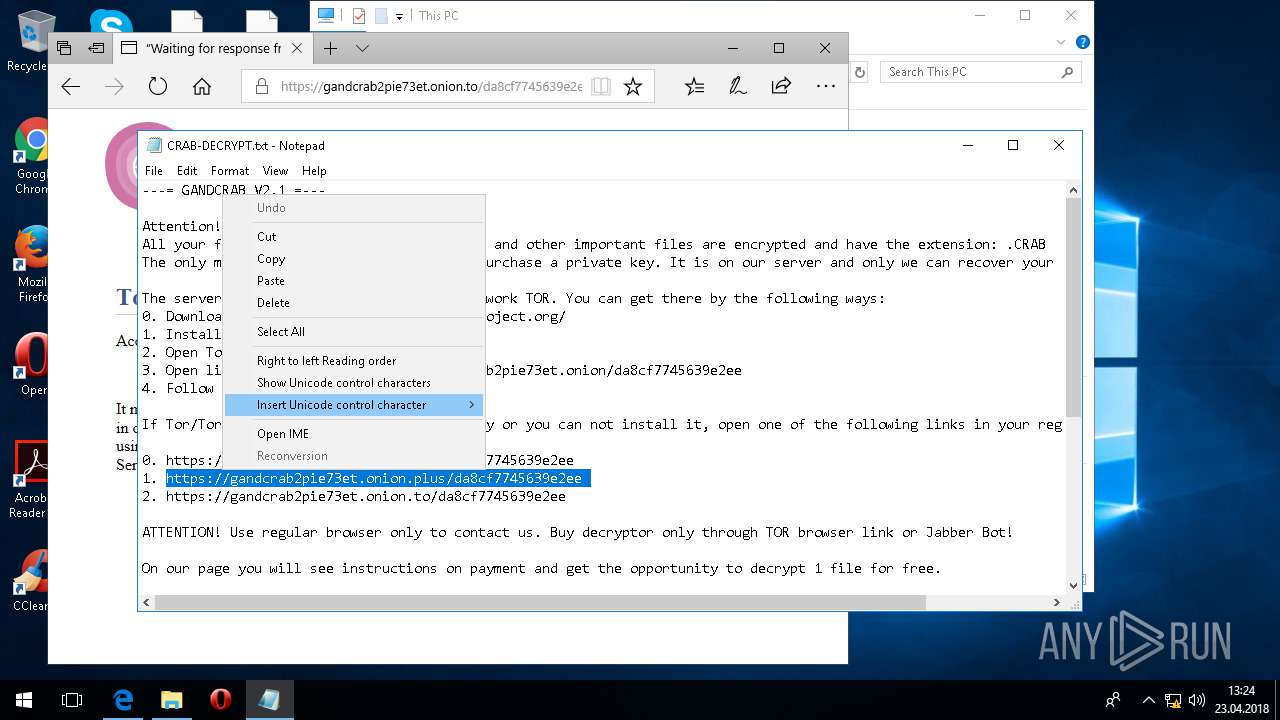
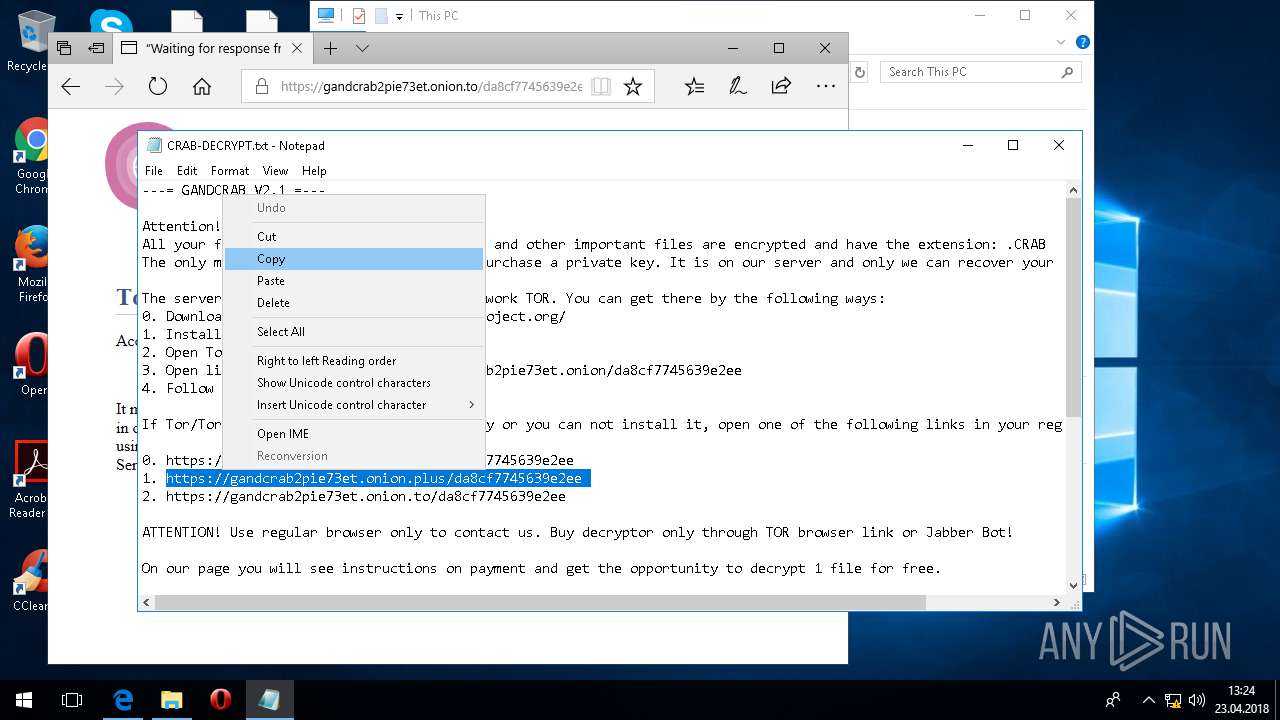
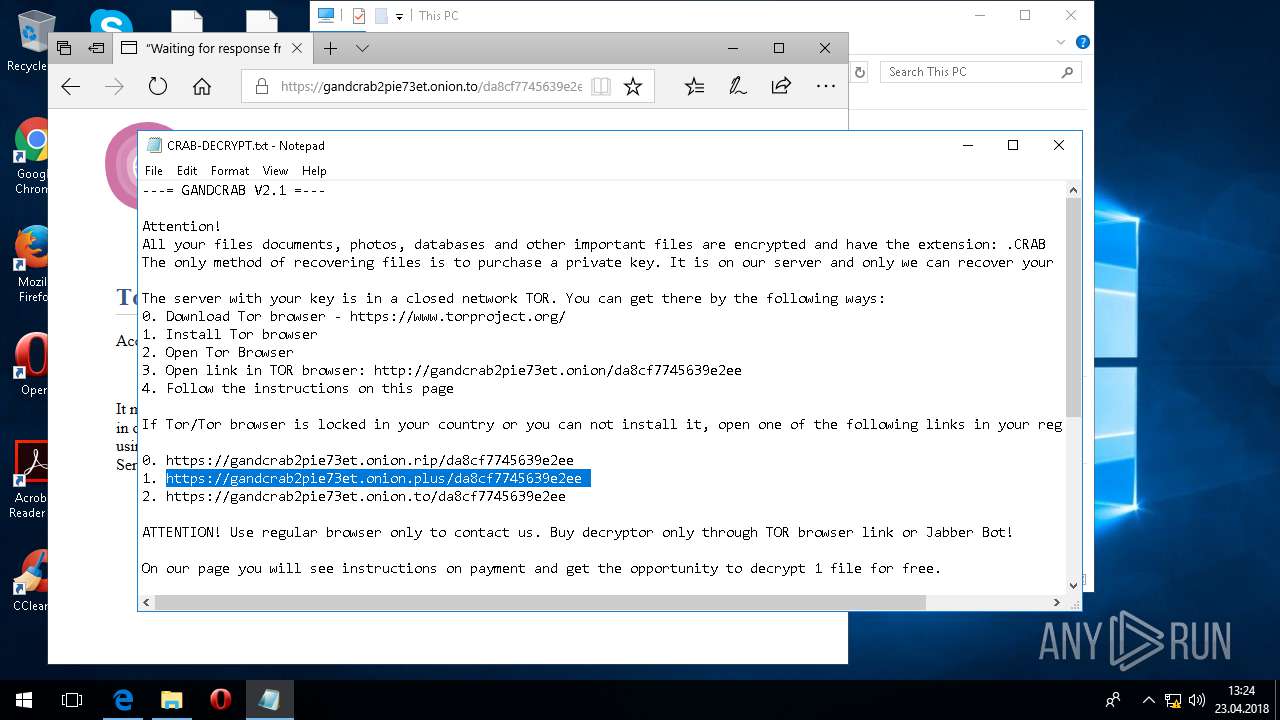
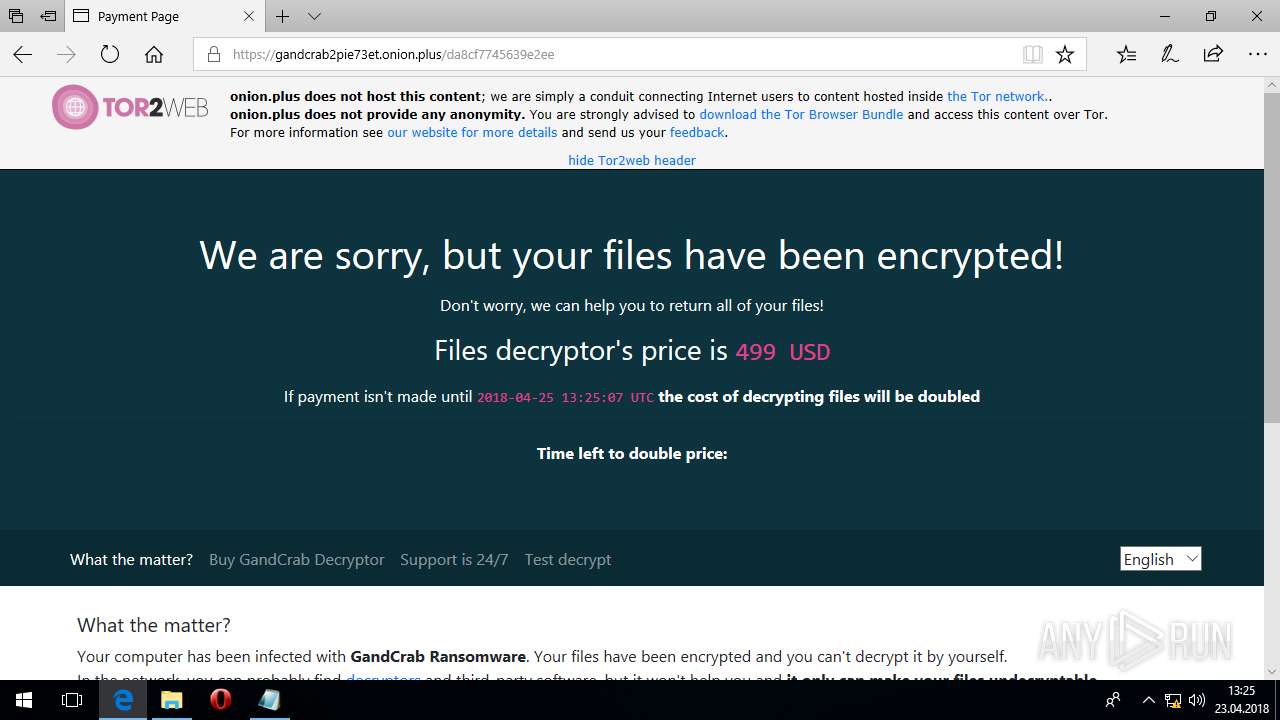
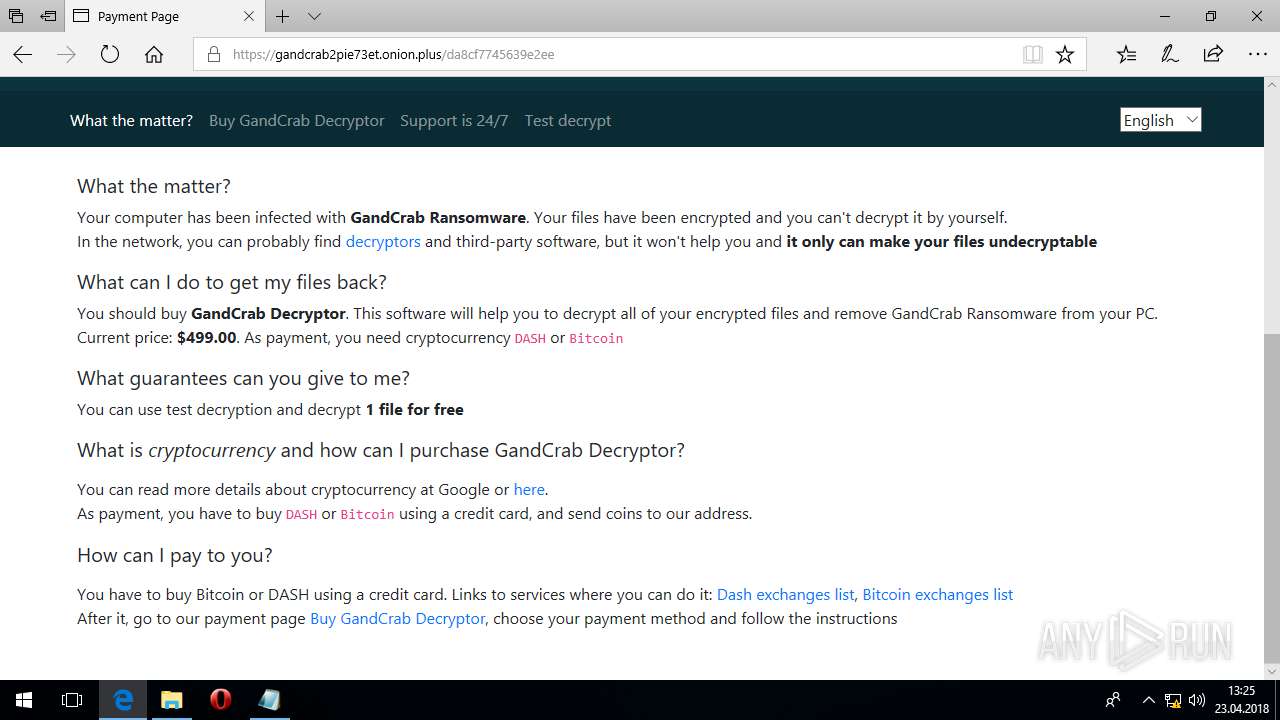
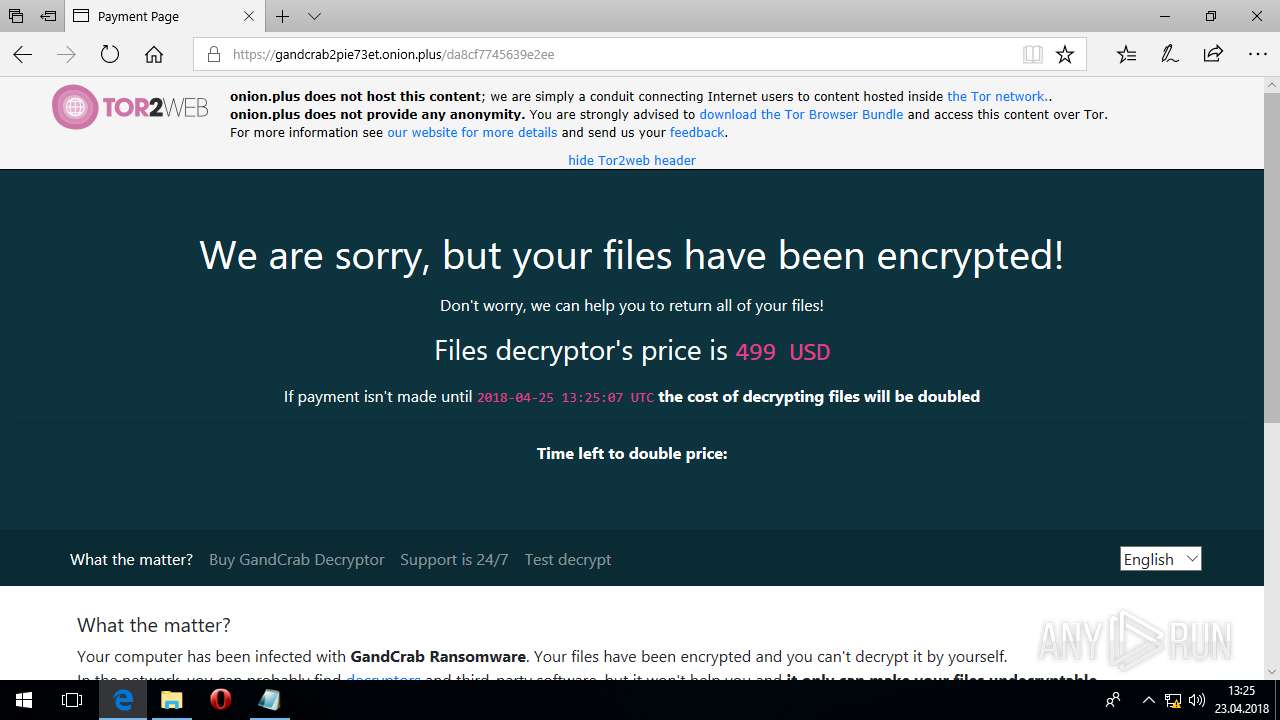
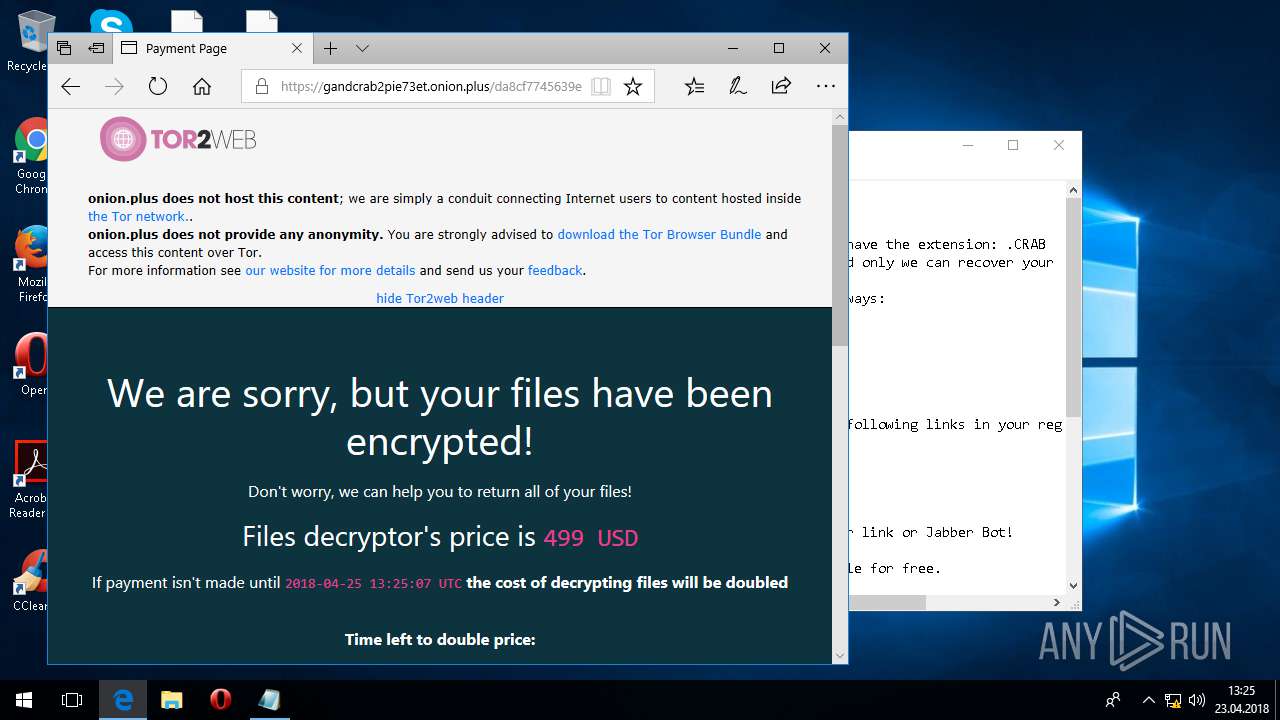
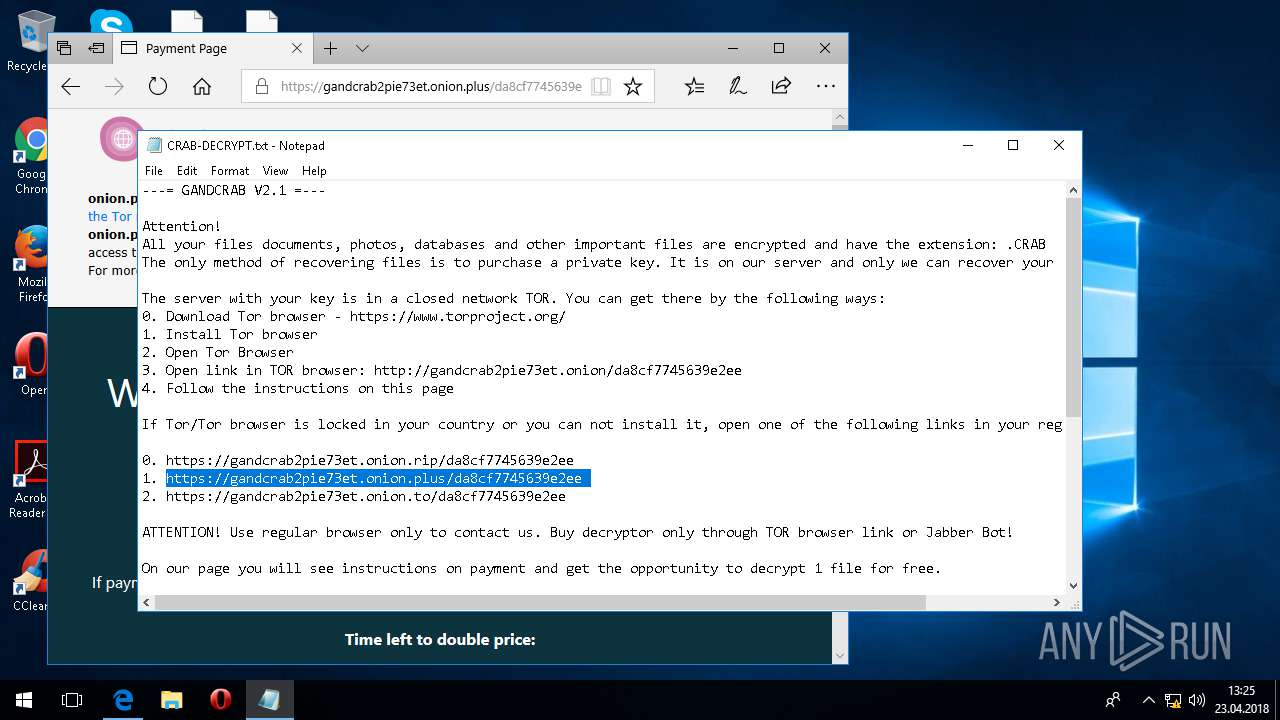
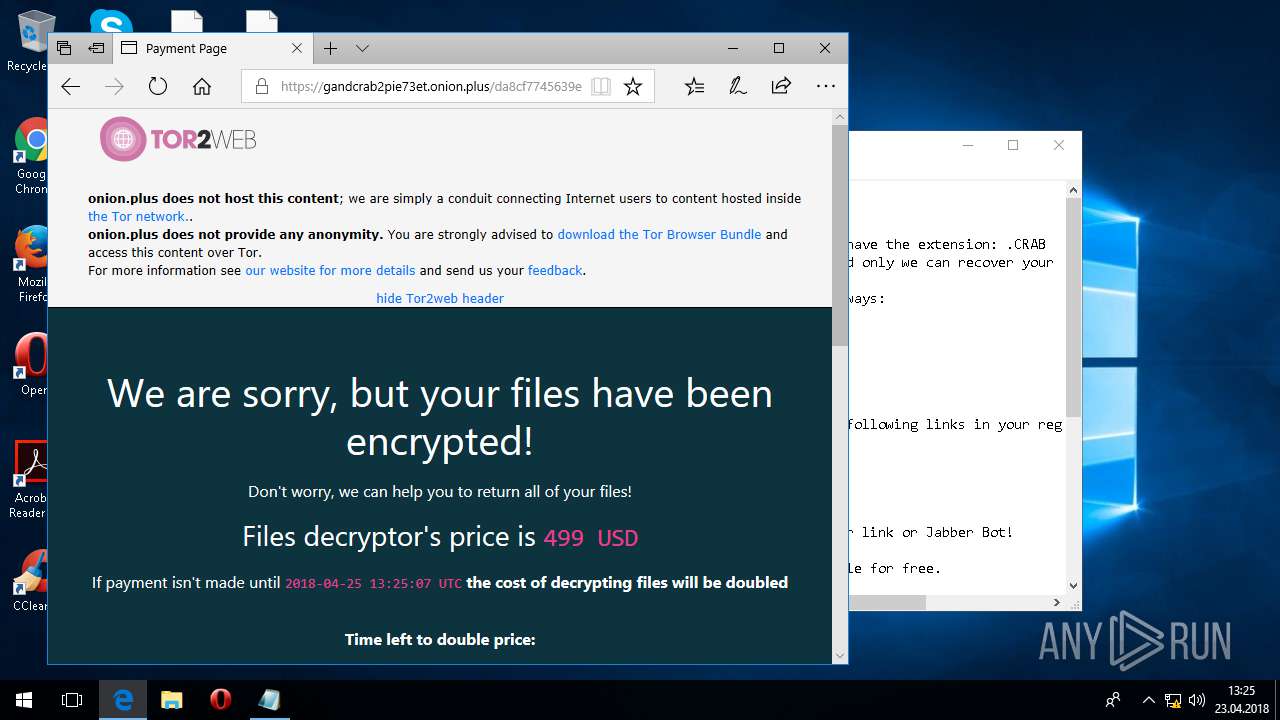
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | April 23, 2018, 13:22:28 |
| OS: | Windows 10 Professional (build: 16299, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | EF5353B4B40EDB06AC7250AEFB6B7000 |
| SHA1: | 76FA9AB30DB12DA4E325C90C3405092D5F1A4E4E |
| SHA256: | 6FAFE7BB56FD2696F2243FC305FE0C38F550DFFCFC5FCA04F70398880570FFFF |
| SSDEEP: | 6144:ItINzDJCd5QfI6RtlENOmpmPyAkp/H6QFVt60cEVwH:JNzPHoTQFa/1FVc0cE |
MALICIOUS
Uses SVCHOST.EXE for hidden code execution
- grounded.exe (PID: 2444)
Writes file to Word startup folder
- svchost.exe (PID: 5836)
Dropped file may contain instructions of ransomware
- svchost.exe (PID: 5836)
SUSPICIOUS
Creates files like Ransomware instruction
- svchost.exe (PID: 5836)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 5836)
Creates files in the user directory
- svchost.exe (PID: 5836)
INFO
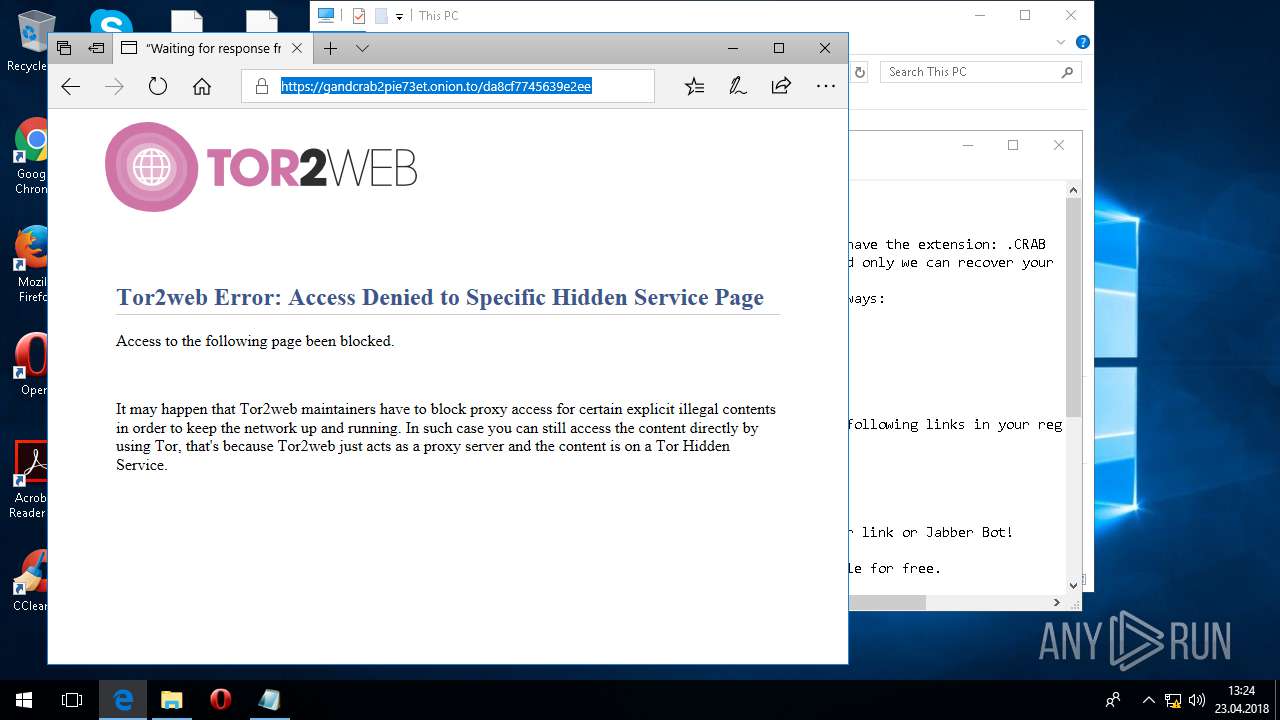
Dropped object may contain TOR URL's
- svchost.exe (PID: 5836)
Dropped object may contain URL's
- svchost.exe (PID: 5836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:04:23 11:21:19+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 115712 |
| InitializedDataSize: | 1298432 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x99e1 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 23-Apr-2018 09:21:19 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 23-Apr-2018 09:21:19 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0001C281 | 0x0001C400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.5777 |
.rdata | 0x0001E000 | 0x00004D6C | 0x00004E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.1107 |
.data | 0x00023000 | 0x00118988 | 0x00004400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.75304 |
.rsrc | 0x0013C000 | 0x0001D854 | 0x0001DA00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.90411 |
.reloc | 0x0015A000 | 0x00002A50 | 0x00002C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 4.08504 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 6.89454 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
11 | 2.78311 | 214 | UNKNOWN | UNKNOWN | RT_STRING |
12 | 2.5115 | 128 | UNKNOWN | UNKNOWN | RT_STRING |
14 | 2.26226 | 92 | UNKNOWN | UNKNOWN | RT_STRING |
18 | 2.82421 | 230 | UNKNOWN | UNKNOWN | RT_STRING |
25 | 1.43775 | 52 | UNKNOWN | UNKNOWN | RT_STRING |
29 | 2.70815 | 166 | UNKNOWN | UNKNOWN | RT_STRING |
30 | 1.19151 | 48 | UNKNOWN | UNKNOWN | RT_STRING |
33 | 1.29057 | 48 | UNKNOWN | UNKNOWN | RT_STRING |
45 | 1.53362 | 56 | UNKNOWN | UNKNOWN | RT_STRING |
Imports
KERNEL32.dll |
ole32.dll |
Total processes
155
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2444 | "C:\Users\admin\Desktop\grounded.exe" | C:\Users\admin\Desktop\grounded.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1073807364 Modules
| |||||||||||||||
| 3240 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Roaming\Microsoft\Windows\Network Shortcuts\CRAB-DECRYPT.txt | C:\WINDOWS\system32\NOTEPAD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4192 | "C:\Windows\System32\cmd.exe" /c shutdown -r -t 1 -f | C:\Windows\System32\cmd.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\WINDOWS\system32\conhost.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5836 | C:\WINDOWS\system32\svchost.exe | C:\WINDOWS\system32\svchost.exe | grounded.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 3221225786 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6040 | shutdown -r -t 1 -f | C:\WINDOWS\system32\shutdown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
177
Read events
166
Write events
11
Delete events
0
Modification events
| (PID) Process: | (5836) svchost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (5836) svchost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (5836) svchost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (5836) svchost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (5836) svchost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5836) svchost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5836) svchost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
195
Text files
175
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5836 | svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-3775154099-3075979740-599700546-1001\0f5007522459c86e95ffcc62f32308f1_a5a43bce-52d4-40cd-b07e-dea4b2ef1ca3 | — | |
MD5:— | SHA256:— | |||
| 5836 | svchost.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\B713ULK5\BYMIU9X1.htm | — | |
MD5:— | SHA256:— | |||
| 5836 | svchost.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\B713ULK5\ssiesei[1].htm | — | |
MD5:— | SHA256:— | |||
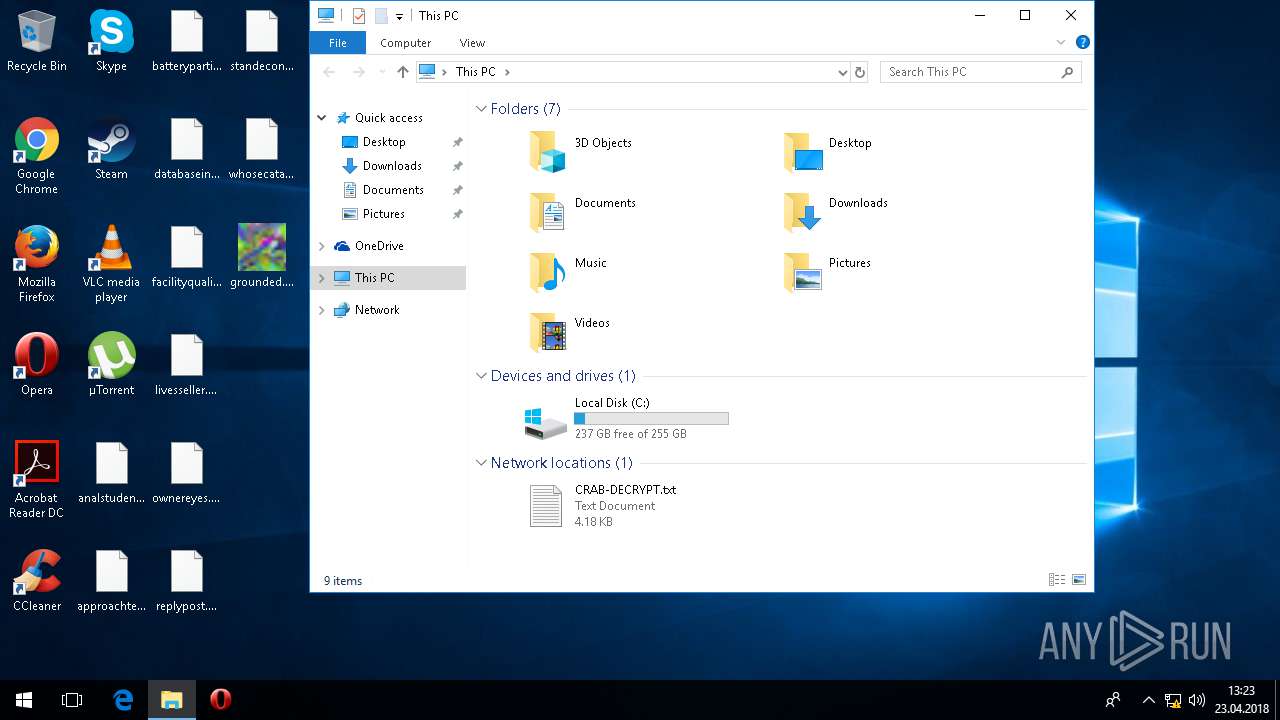
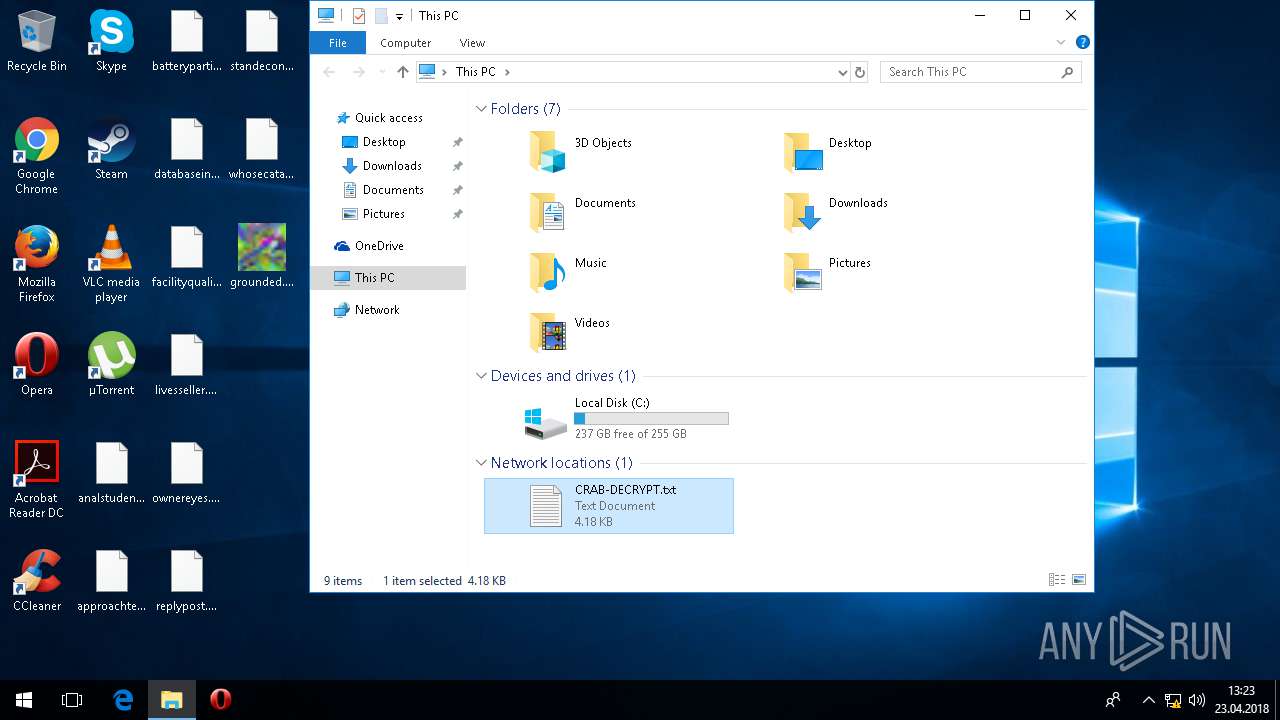
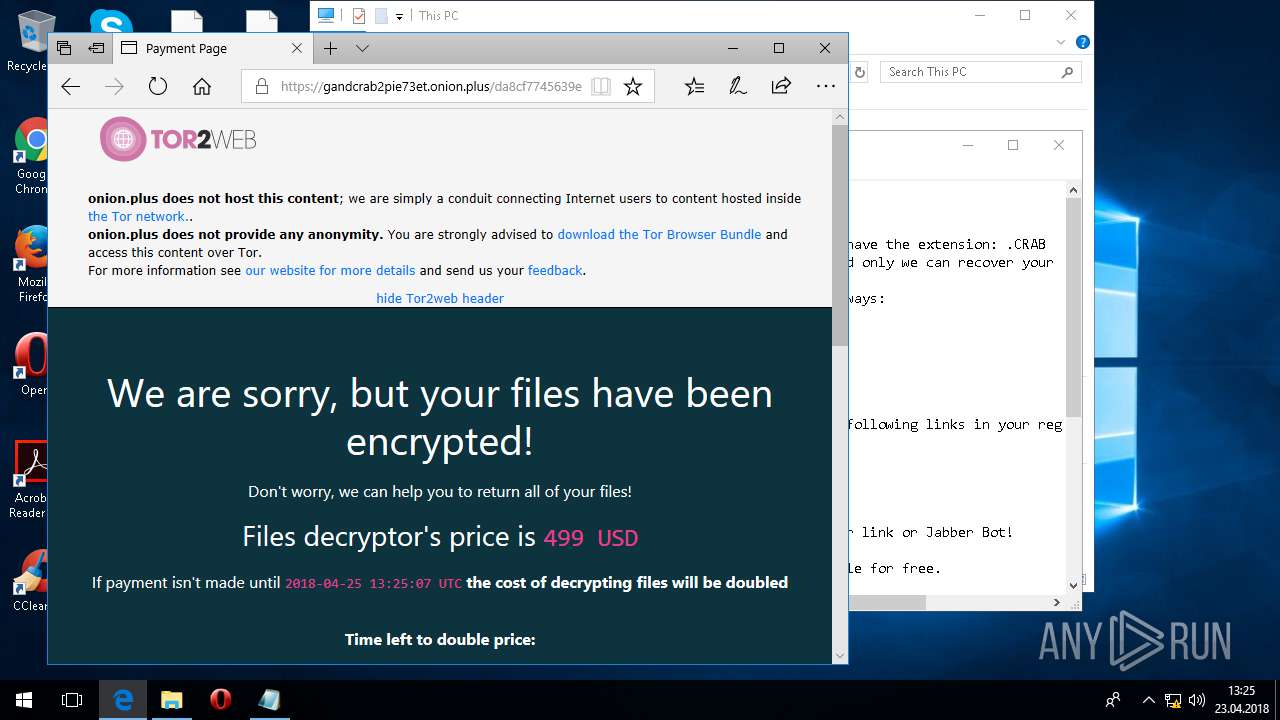
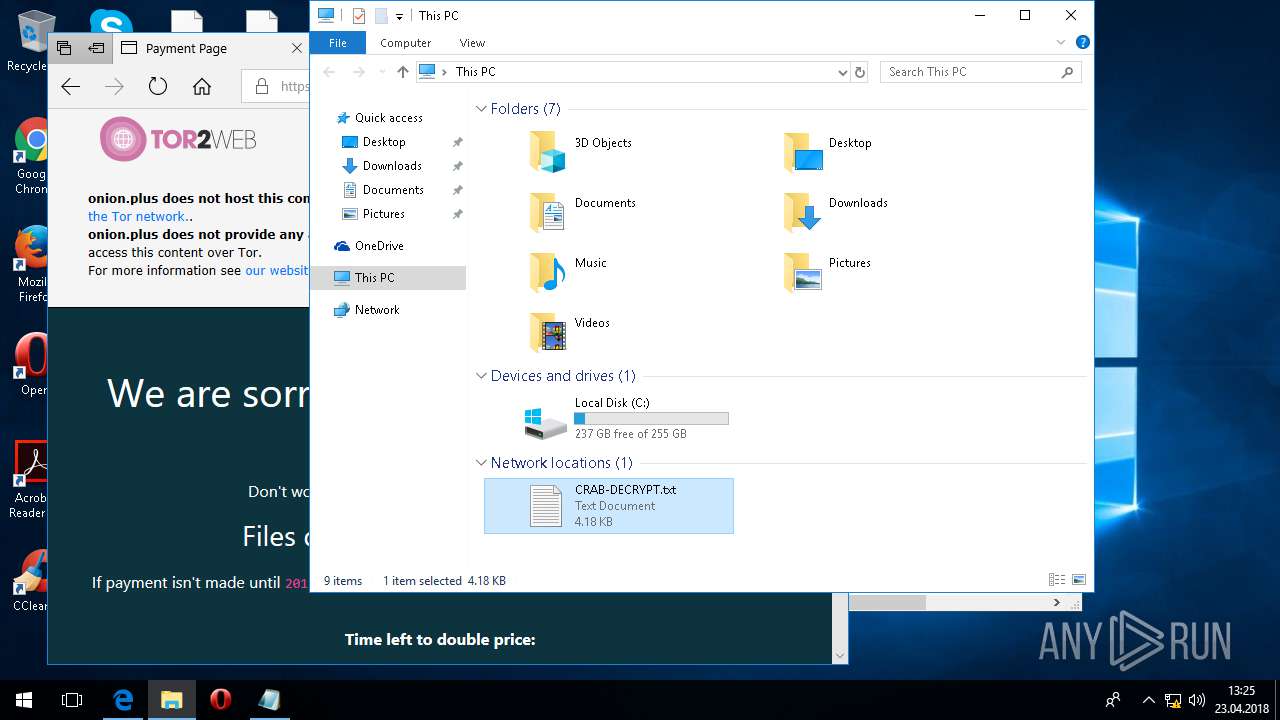
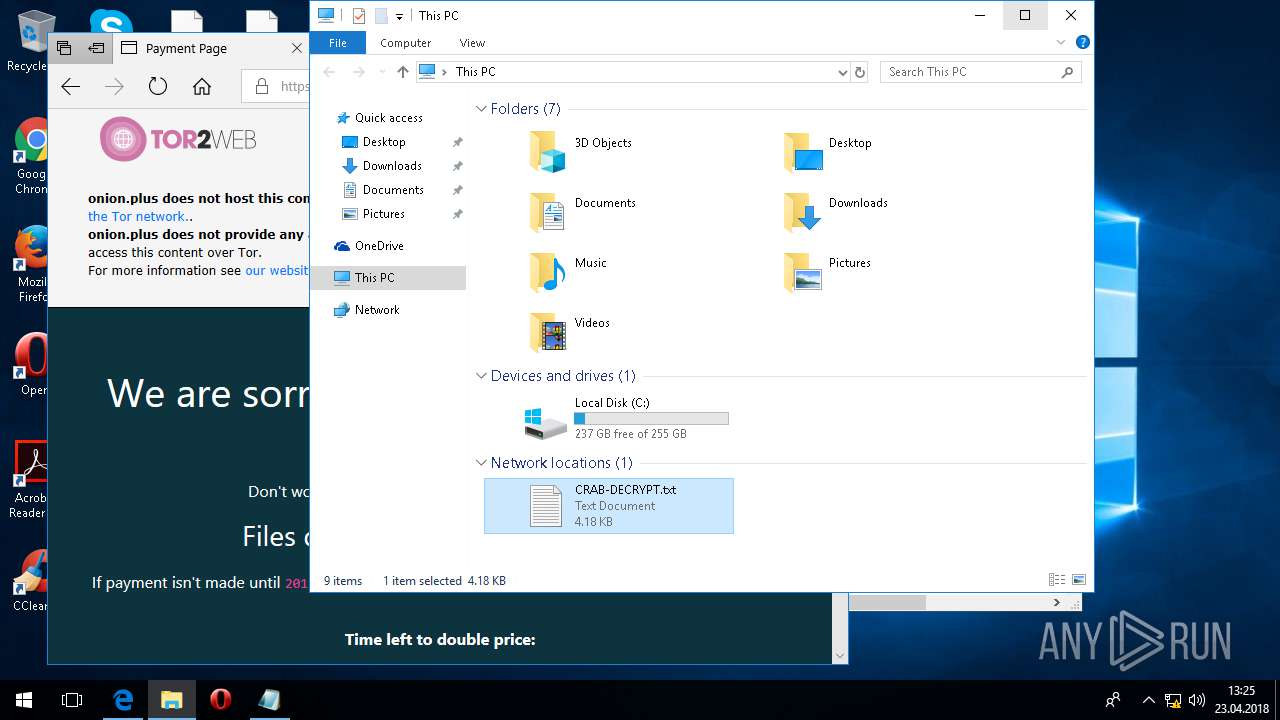
| 5836 | svchost.exe | C:\Users\admin\CRAB-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 5836 | svchost.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp.CRAB | gpg | |
MD5:— | SHA256:— | |||
| 5836 | svchost.exe | C:\Users\admin\AppData\Roaming\CRAB-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 5836 | svchost.exe | C:\Users\admin\AppData\CRAB-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 5836 | svchost.exe | C:\Users\admin\.oracle_jre_usage\CRAB-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 5836 | svchost.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\CRAB-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 5836 | svchost.exe | C:\Users\admin\AppData\Roaming\Adobe\Linguistics\CRAB-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
73
DNS requests
31
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 66.171.248.178:80 | http://ahnlab.com/ | US | text | 14 b | whitelisted |
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAi4elAbvpzaLRZNPjlRv1U%3D | US | der | 471 b | whitelisted |
— | — | POST | 200 | 185.183.98.202:80 | http://ahnlab.com/ssiesei?eepl=uiscea | NL | text | 552 b | malicious |
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAiIzVJfGSRETRSlgpHeuVI%3D | US | der | 471 b | whitelisted |
— | — | GET | 200 | 178.255.83.1:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCECdm7lbrSfOOq9dwovyE3iI%3D | GB | der | 471 b | whitelisted |
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 471 b | whitelisted |
— | — | GET | 200 | 23.211.9.92:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Secure%20Server%20CA%202.1.crl | NL | der | 820 b | whitelisted |
— | — | GET | 200 | 178.255.83.1:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCECsuburZdTZsFIpu26N8jAc%3D | GB | der | 727 b | whitelisted |
— | — | GET | 200 | 104.31.75.124:80 | http://ocsp.globalsign.com/rootr1/MEwwSjBIMEYwRDAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCCwQAAAAAAURO8DYx | US | der | 1.48 Kb | whitelisted |
— | — | GET | 200 | 2.16.186.17:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrJdiQ%2Ficg9B19asFe73bPYs%2BreAQUdXGnGUgZvJ2d6kFH35TESHeZ03kCEFslzmkHxCZVZtM5DJmpVK0%3D | unknown | der | 313 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.79.65.237:443 | geo-prod.do.dsp.mp.microsoft.com | Microsoft Corporation | US | whitelisted |
— | — | 104.109.75.4:443 | kv601-prod.do.dsp.mp.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.186.42:443 | static-spartan-neu-s-msn-com.akamaized.net | Akamai International B.V. | — | whitelisted |
— | — | 131.253.33.203:443 | www.msn.com | Microsoft Corporation | US | malicious |
— | — | 13.107.21.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 23.211.9.92:80 | www.microsoft.com | Akamai Technologies, Inc. | NL | whitelisted |
— | — | 151.101.2.2:443 | images.taboola.com | Fastly | US | shared |
— | — | 131.253.61.70:443 | login.live.com | Microsoft Corporation | US | whitelisted |
— | — | 104.31.75.124:80 | ocsp.globalsign.com | Cloudflare Inc | US | shared |
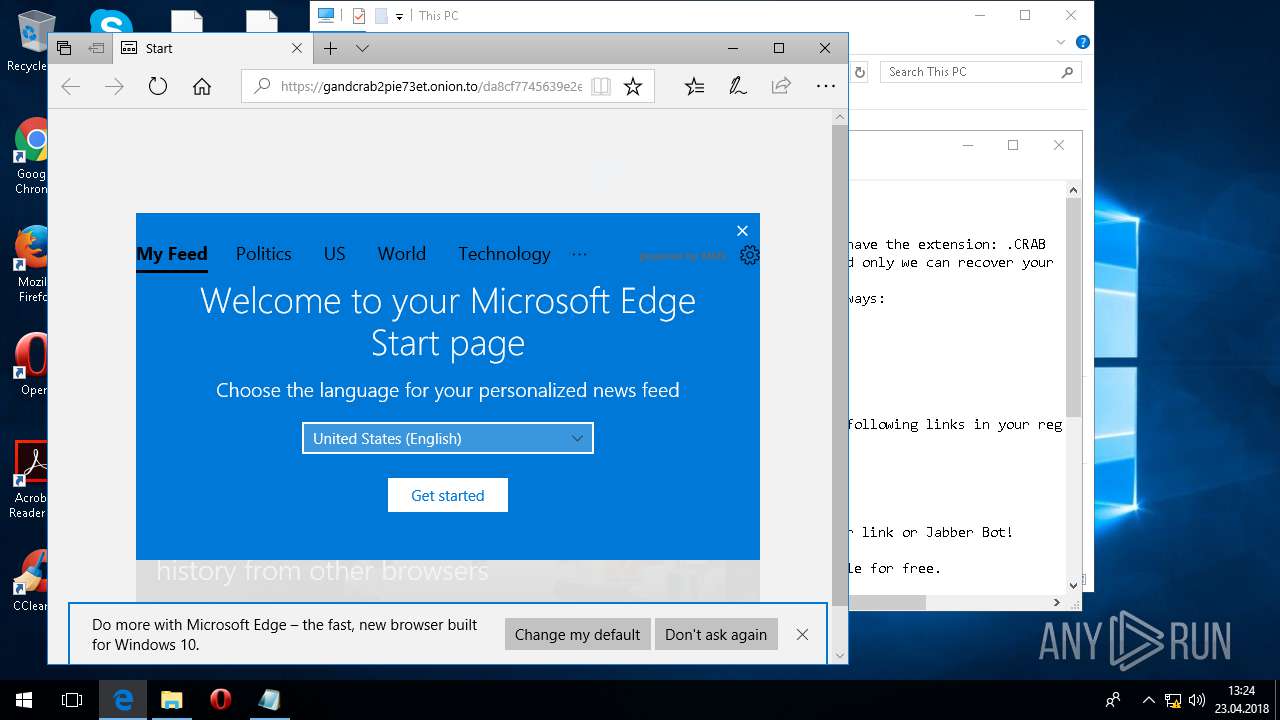
— | — | 185.100.85.150:443 | gandcrab2pie73et.onion.to | Flokinet Ltd | RO | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ipv4bot.whatismyipaddress.com |
| shared |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| malicious |
geo-prod.do.dsp.mp.microsoft.com |
| whitelisted |
kv601-prod.do.dsp.mp.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
static-spartan-neu-s-msn-com.akamaized.net |
| whitelisted |
img-s-msn-com.akamaized.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET POLICY DNS Query to .onion proxy Domain (onion.to) |
— | — | A Network Trojan was detected | ET CNC Ransomware Tracker Reported CnC Server group 22 |
— | — | A Network Trojan was detected | ET CURRENT_EVENTS Tor2Web .onion Proxy Service SSL Cert (2) |
— | — | A Network Trojan was detected | ET CURRENT_EVENTS Tor2Web .onion Proxy Service SSL Cert (2) |
— | — | A Network Trojan was detected | ET CURRENT_EVENTS Tor2Web .onion Proxy Service SSL Cert (2) |
— | — | A Network Trojan was detected | ET POLICY .onion proxy Domain (onion .plus in DNS Lookup) |
Process | Message |
|---|---|
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |