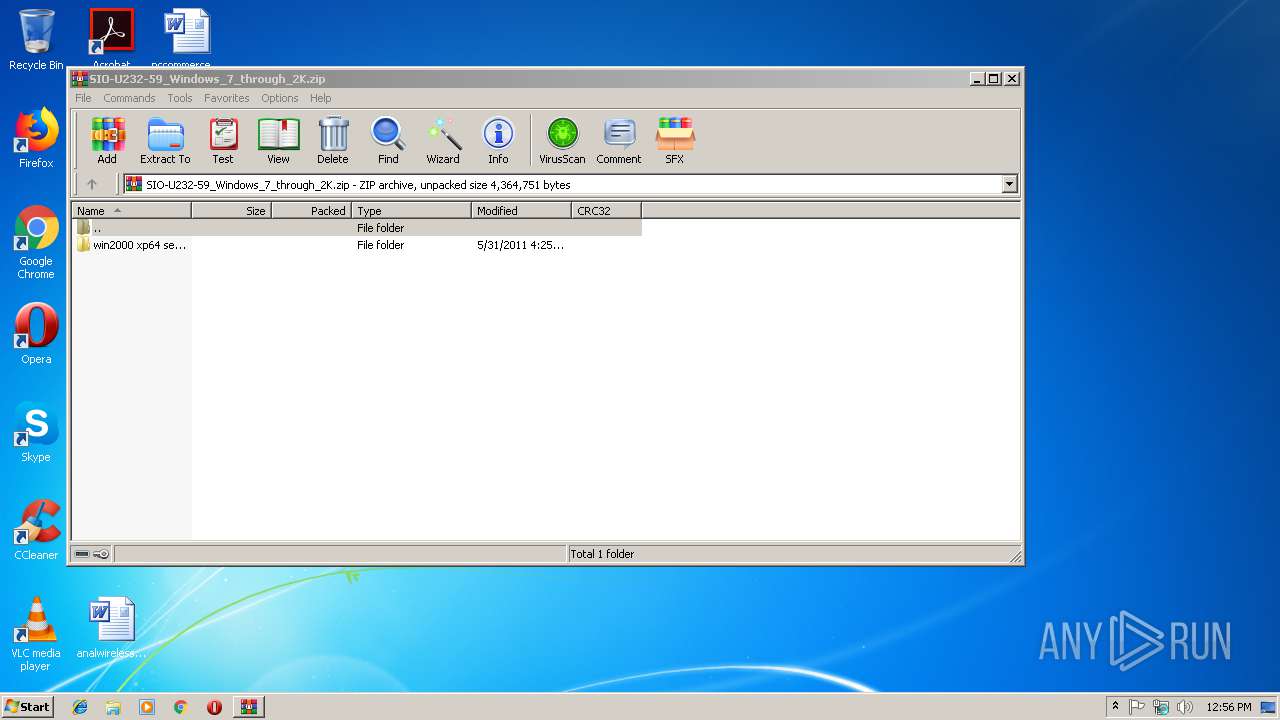
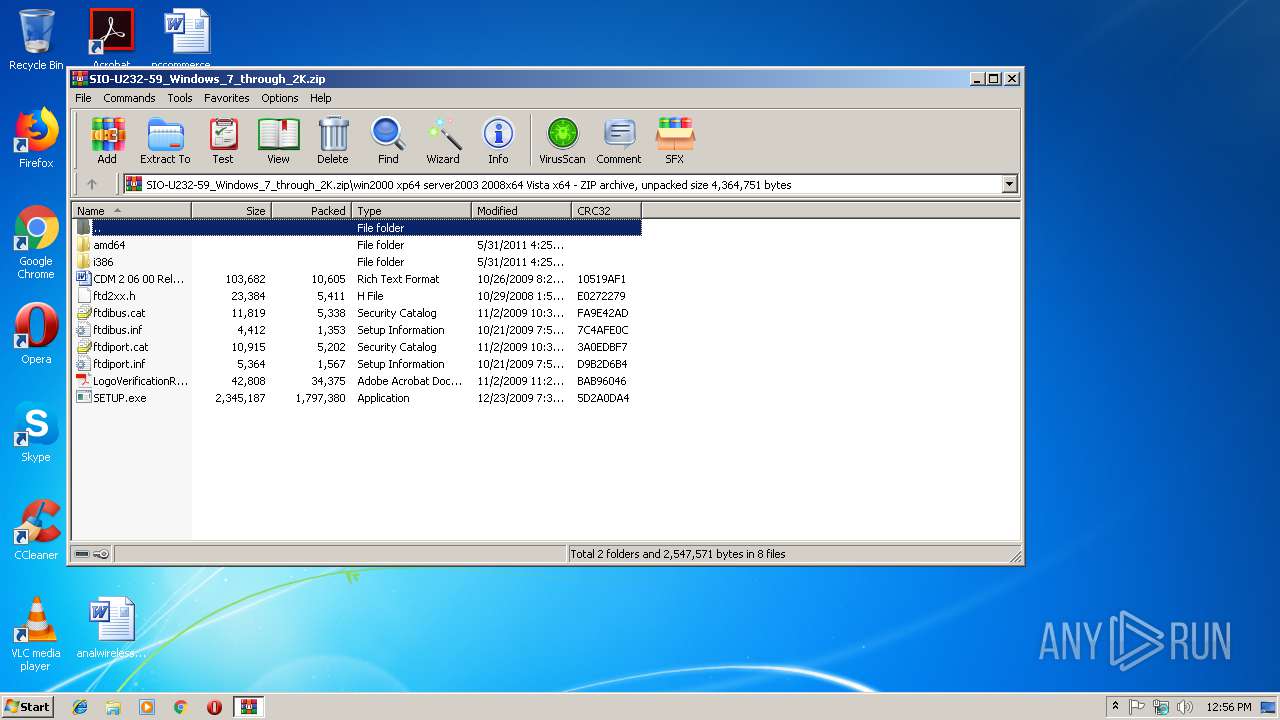
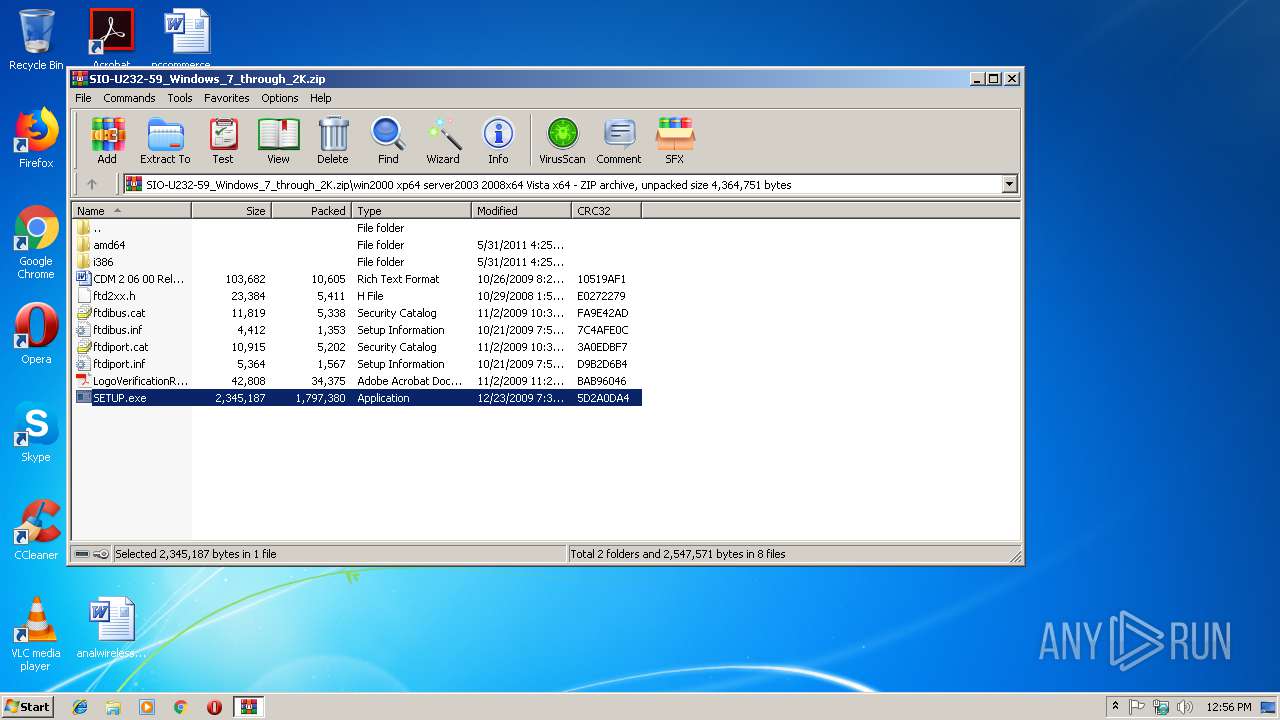
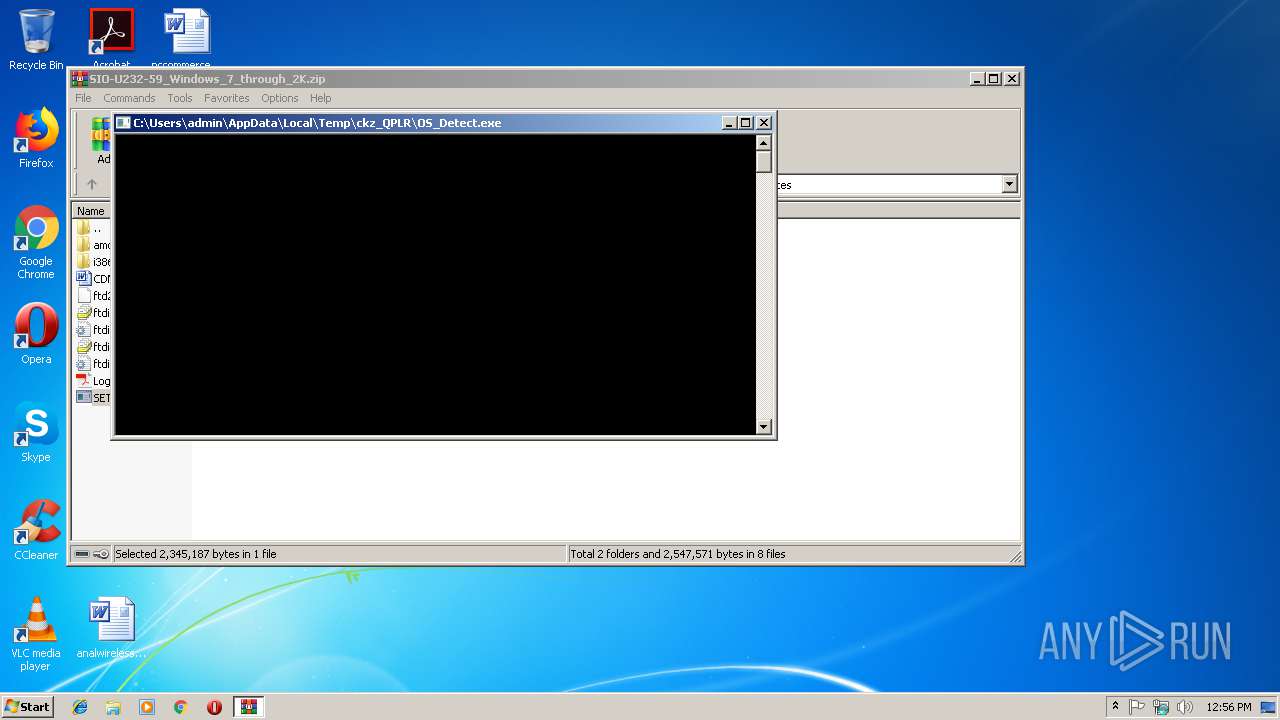
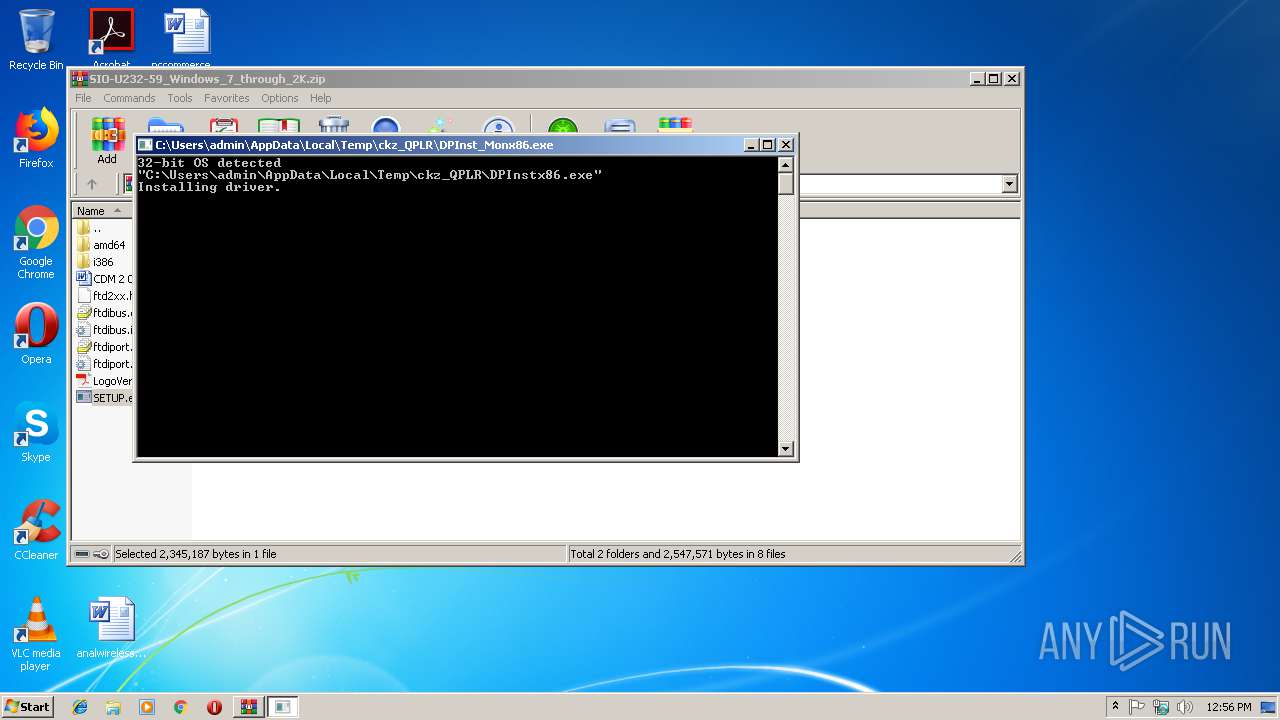
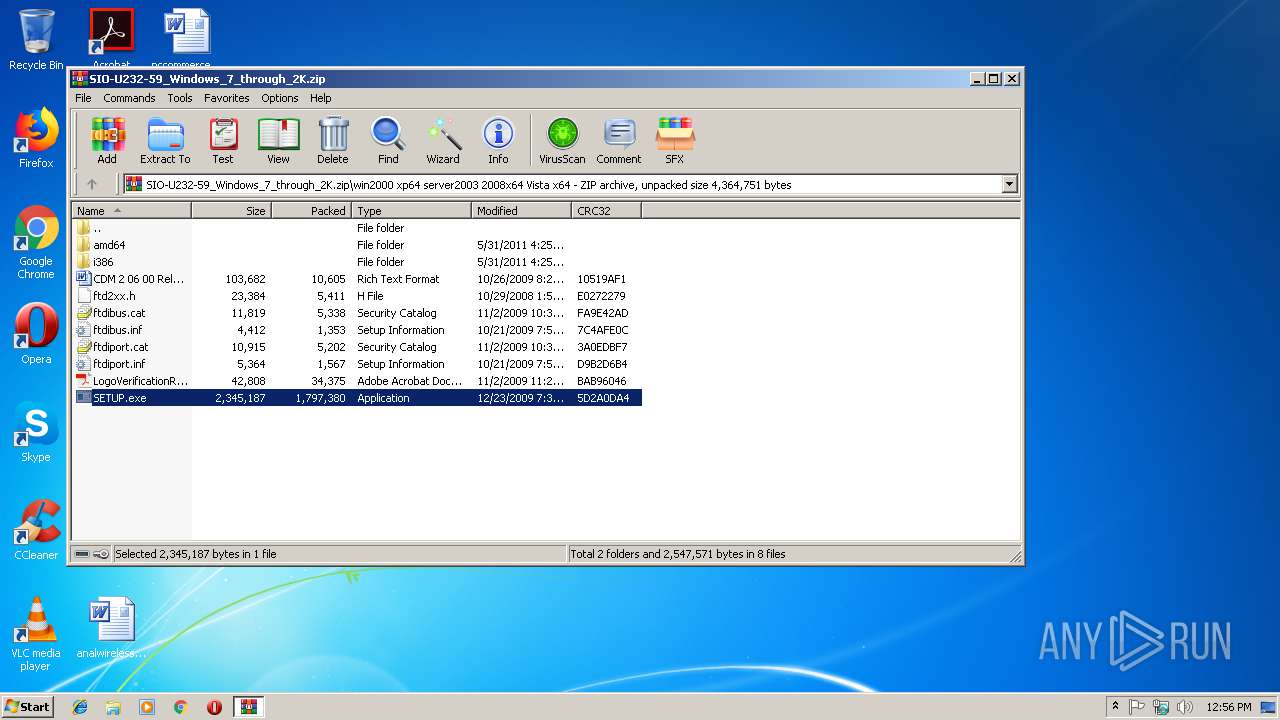
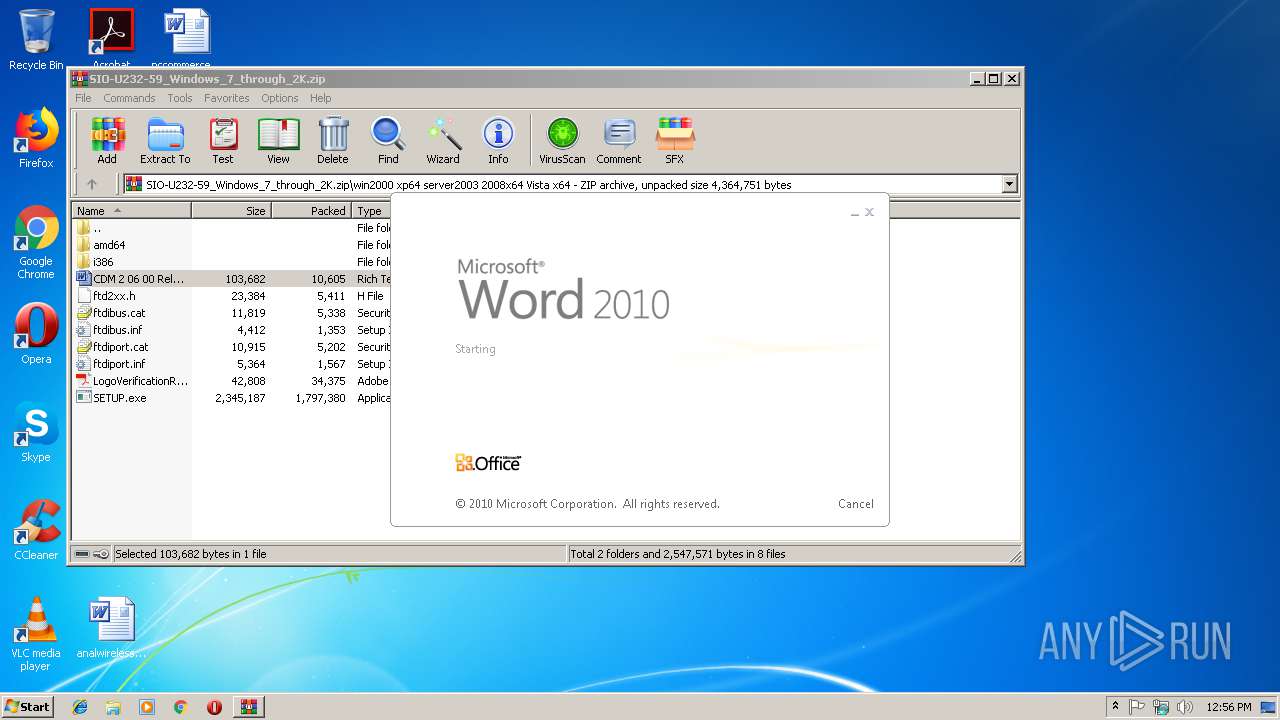
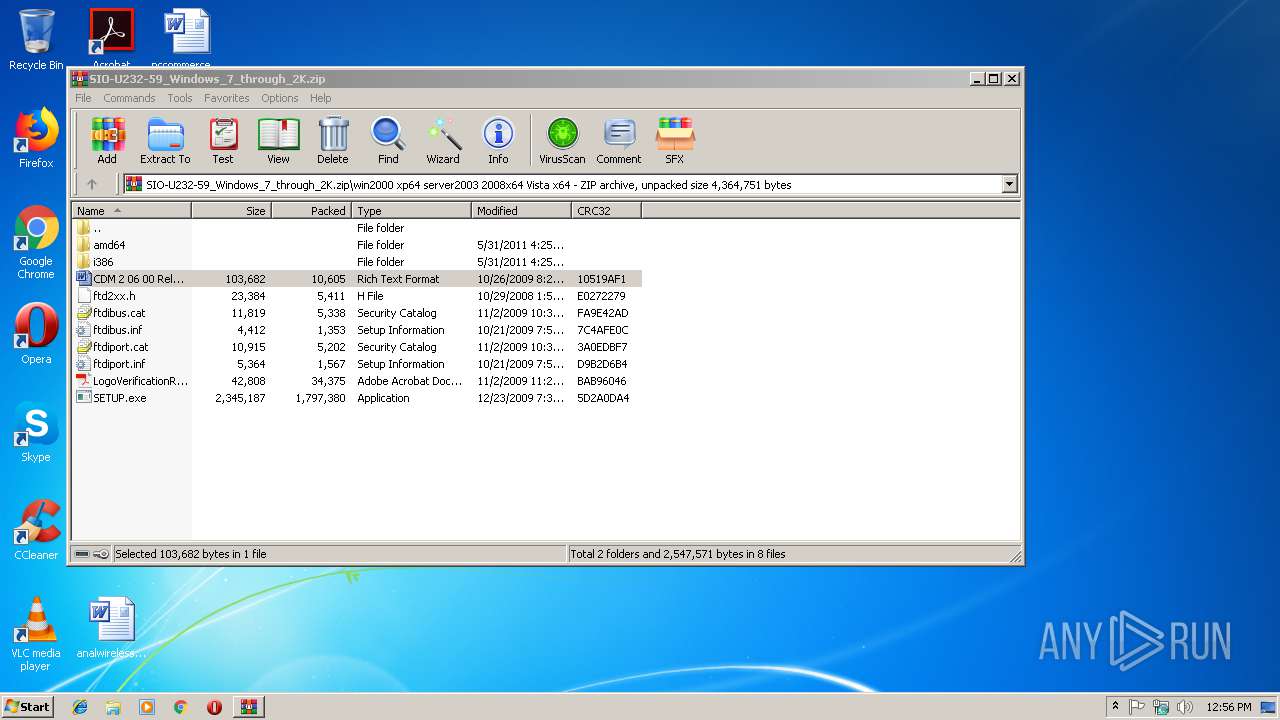
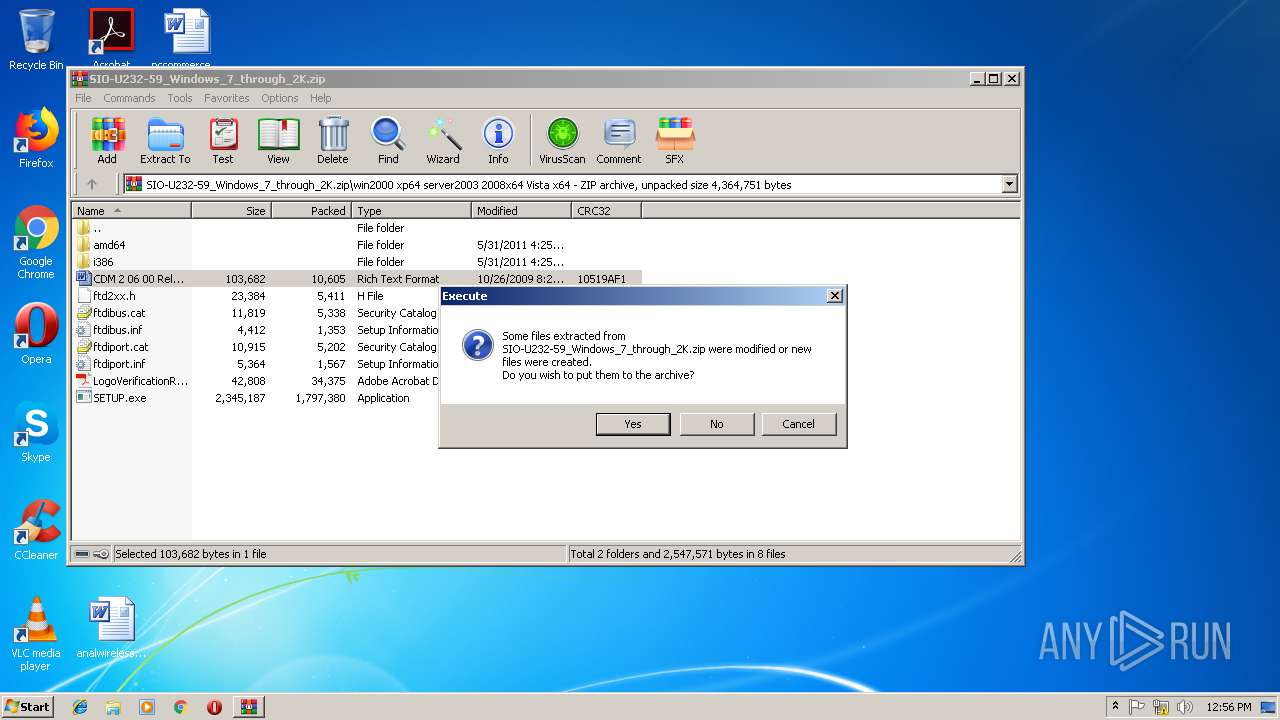
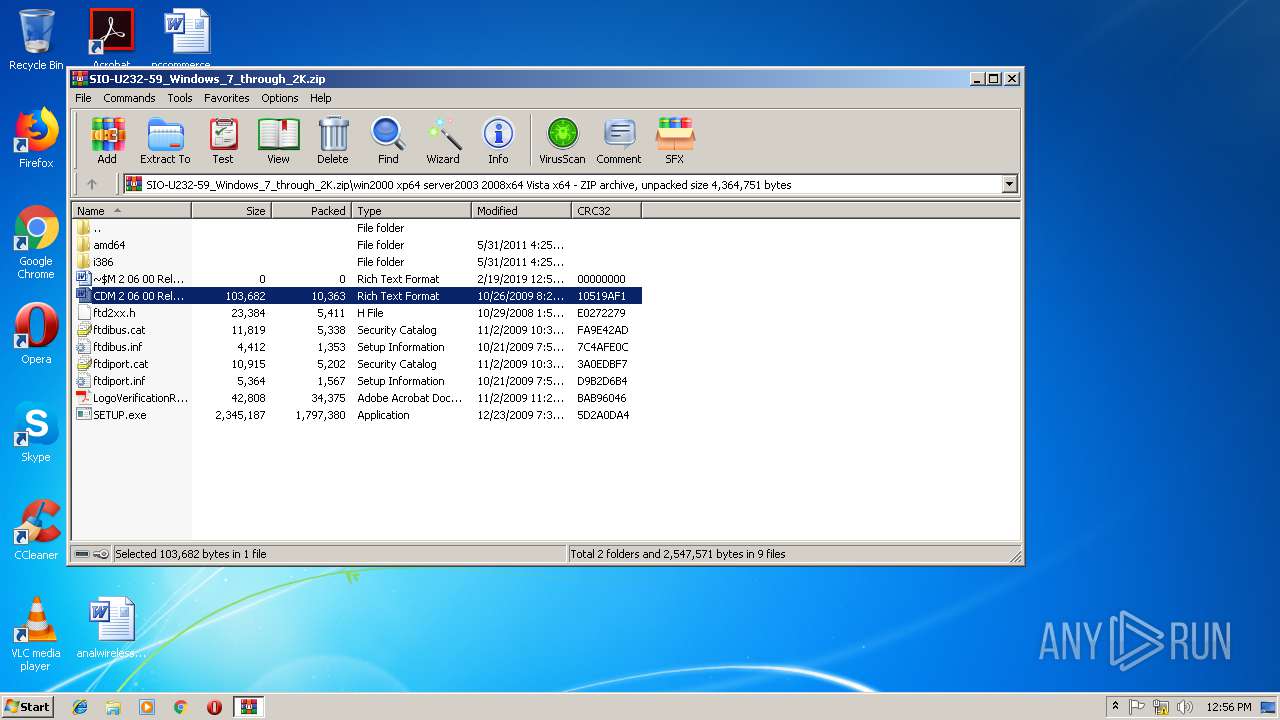
| download: | SIO-U232-59_Windows_7_through_2K.zip |
| Full analysis: | https://app.any.run/tasks/31b37d6d-1bf6-4cd5-8d4f-a0cd36858c15 |
| Verdict: | Malicious activity |
| Analysis date: | February 19, 2019, 12:55:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 1BC5A19C28D55CDB4B7E26CF817B8612 |
| SHA1: | 37E0441A0132B3BF8DA273AB42477017BC9F15D9 |
| SHA256: | 6F8A6EFAB1CD875461A2D06837C669D737ECCB711086B3543DB920511EBF097D |
| SSDEEP: | 49152:J32fKzwoOTT4Fz+DoS9WSsm3Pr63V+JmrmVx0T70F+Ta+T9nTeozRCXi5oS:J32fyhFniWpw63YErm70TY+Tx9TeotCM |
MALICIOUS
Application was dropped or rewritten from another process
- SETUP.exe (PID: 2148)
- DPInst_Monx86.exe (PID: 3172)
- SETUP.exe (PID: 2844)
- DPInstx86.exe (PID: 3492)
- OS_Detect.exe (PID: 3348)
SUSPICIOUS
Executable content was dropped or overwritten
- SETUP.exe (PID: 2148)
- WinRAR.exe (PID: 3008)
- DPInstx86.exe (PID: 3492)
Creates files in the Windows directory
- DPInstx86.exe (PID: 3492)
- DrvInst.exe (PID: 3268)
- DrvInst.exe (PID: 928)
Removes files from Windows directory
- DrvInst.exe (PID: 3268)
- DrvInst.exe (PID: 928)
Creates files in the driver directory
- DrvInst.exe (PID: 3268)
- DrvInst.exe (PID: 928)
Creates files in the program directory
- DPInstx86.exe (PID: 3492)
Creates a software uninstall entry
- DPInstx86.exe (PID: 3492)
Starts Microsoft Office Application
- WinRAR.exe (PID: 3008)
INFO
Application launched itself
- AcroRd32.exe (PID: 3876)
Creates files in the user directory
- WINWORD.EXE (PID: 3660)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2011:05:31 16:25:02 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | win2000 xp64 server2003 2008x64 Vista x64/ |
Total processes
50
Monitored processes
12
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 928 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{10123aaf-e44a-5fc7-8eff-866b7f35a730}\ftdiport.inf" "0" "624cb962b" "0000048C" "WinSta0\Default" "000005BC" "208" "c:\users\admin\appdata\local\temp\ckz_qplr" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2148 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3008.48819\win2000 xp64 server2003 2008x64 Vista x64\SETUP.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3008.48819\win2000 xp64 server2003 2008x64 Vista x64\SETUP.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 2844 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3008.48819\win2000 xp64 server2003 2008x64 Vista x64\SETUP.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3008.48819\win2000 xp64 server2003 2008x64 Vista x64\SETUP.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3008 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SIO-U232-59_Windows_7_through_2K.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
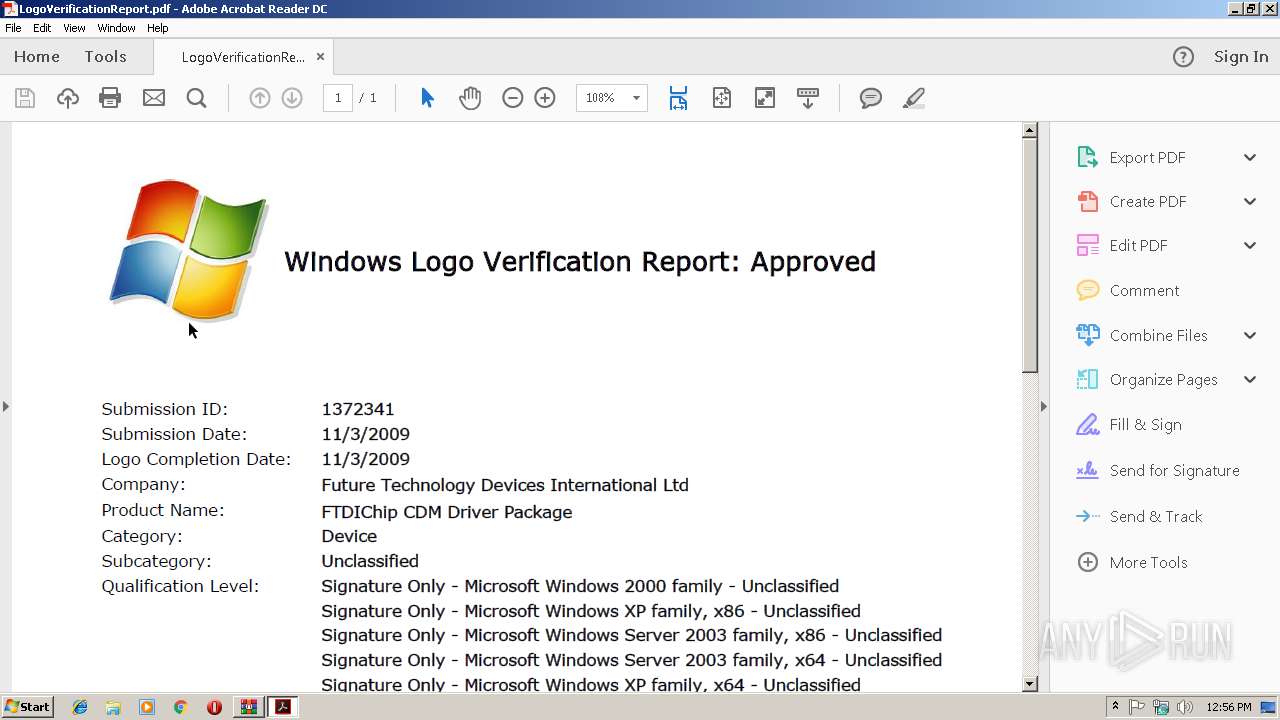
| 3096 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Temp\Rar$DIa3008.49506\LogoVerificationReport.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 3172 | "C:\Users\admin\AppData\Local\Temp\ckz_QPLR\DPInst_Monx86.exe" | C:\Users\admin\AppData\Local\Temp\ckz_QPLR\DPInst_Monx86.exe | — | OS_Detect.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3268 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{10123aaf-eeeb-4496-5147-3b1cf24e554a}\ftdibus.inf" "0" "6271cb14b" "000002A0" "WinSta0\Default" "0000048C" "208" "c:\users\admin\appdata\local\temp\ckz_qplr" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3348 | "C:\Users\admin\AppData\Local\Temp\ckz_QPLR\OS_Detect.exe" | C:\Users\admin\AppData\Local\Temp\ckz_QPLR\OS_Detect.exe | — | SETUP.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3492 | "C:\Users\admin\AppData\Local\Temp\ckz_QPLR\DPInstx86.exe" | C:\Users\admin\AppData\Local\Temp\ckz_QPLR\DPInstx86.exe | DPInst_Monx86.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 512 Version: 2.1 Modules
| |||||||||||||||
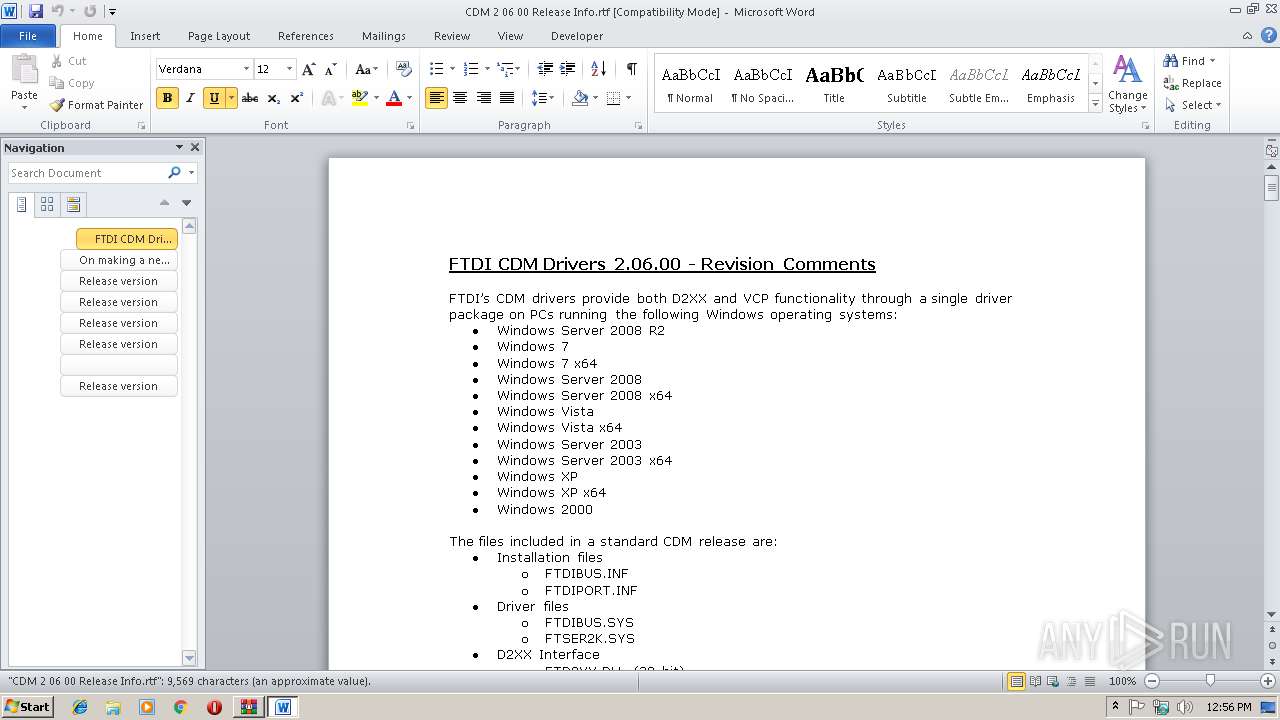
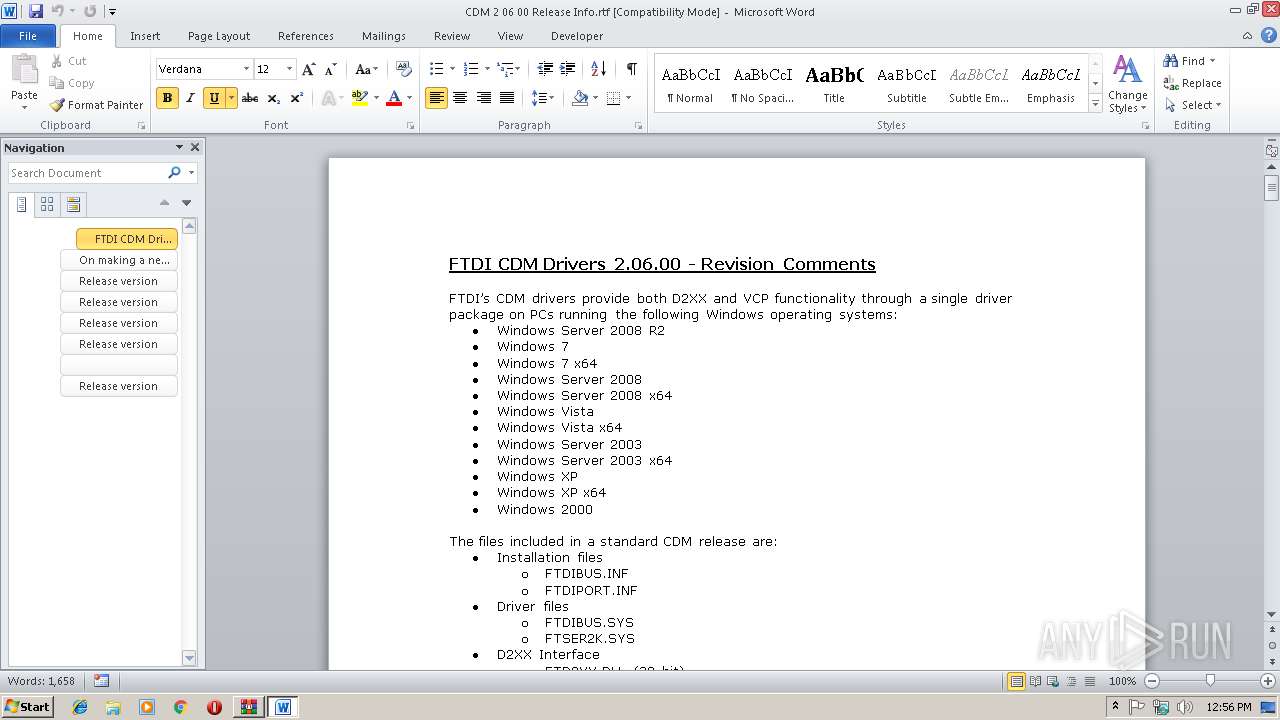
| 3660 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIa3008.036\CDM 2 06 00 Release Info.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 691
Read events
2 439
Write events
241
Delete events
11
Modification events
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SIO-U232-59_Windows_7_through_2K.zip | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @cryptext.dll,-6145 |
Value: Security Catalog | |||
| (PID) Process: | (3008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
42
Suspicious files
21
Text files
41
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3008.48819\win2000 xp64 server2003 2008x64 Vista x64\amd64\ftbusui.dll | executable | |
MD5:49424524EC55EDCB9F448239DCAC04F5 | SHA256:B4C5A11AC96F61F04A1AF46BBC7507FA9E356EE928D5662E5303B23A0EDDA834 | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3008.48819\win2000 xp64 server2003 2008x64 Vista x64\i386\ftlang.dll | executable | |
MD5:A7BD75938F91C815EA0BDC991A207C68 | SHA256:43D220695201DC92BA818C7BC998BDE201DC7676D26388261AEFA8A75E8A71F0 | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3008.48819\win2000 xp64 server2003 2008x64 Vista x64\amd64\ftd2xx64.dll | executable | |
MD5:BC0FD46D9E9D8578053D02511CEBDF2A | SHA256:CE1FF346E4BB51A605A99AE6E51FB7929D176A31A24EE536FB95C08BEE037FD0 | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3008.48819\win2000 xp64 server2003 2008x64 Vista x64\amd64\ftdibus.sys | executable | |
MD5:7442BCA60ED46CC31C2F39728BBDD9AD | SHA256:0218349E24AC059C502009432A0EC51086E1F9A895E7367CAC1FC6A6C8187B2B | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3008.48819\win2000 xp64 server2003 2008x64 Vista x64\ftdiport.cat | cat | |
MD5:3A52D058A5203C5EFD4E0027017E3E58 | SHA256:661CE147A903A951E217B177A9BA793E50EC1073E0660412B671E81D652E8131 | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3008.48819\win2000 xp64 server2003 2008x64 Vista x64\CDM 2 06 00 Release Info.rtf | text | |
MD5:65430128D59CBD56C181F462E264201E | SHA256:558DC38A7C7E76678B60688575A97EF1289993B66E9EB48CC42BCEA6738DF19D | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3008.48819\win2000 xp64 server2003 2008x64 Vista x64\amd64\ftd2xx.lib | obj | |
MD5:96A2C1BF6B37246255E112265DA84602 | SHA256:76439BF5EFF1A3C372799C9DF924D64E84E31D9C272CCFE48C0BEC453801F6DA | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3008.48819\win2000 xp64 server2003 2008x64 Vista x64\ftdibus.cat | cat | |
MD5:719C0C5A7CB6312F13A9BAE4B3110152 | SHA256:B2508E8AB1ABC297DF0881F60C40AB495749E7F6C4C76D0DA4AA72CB071453C3 | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3008.48819\win2000 xp64 server2003 2008x64 Vista x64\ftd2xx.h | text | |
MD5:3B584F7365B32F928C1A8924D0E1B402 | SHA256:C1E81B4B9BE73BB1AAF7BBF2D086377C45EA590024417BA0EE60D0F6BB8D46C0 | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3008.48819\win2000 xp64 server2003 2008x64 Vista x64\ftdiport.inf | binary | |
MD5:C94170EC43E861C43831537029789380 | SHA256:714EF681C28A88AA90EBEBAE3CAFCA58A743D191FC872FBCA169B79A7AFE18A6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report