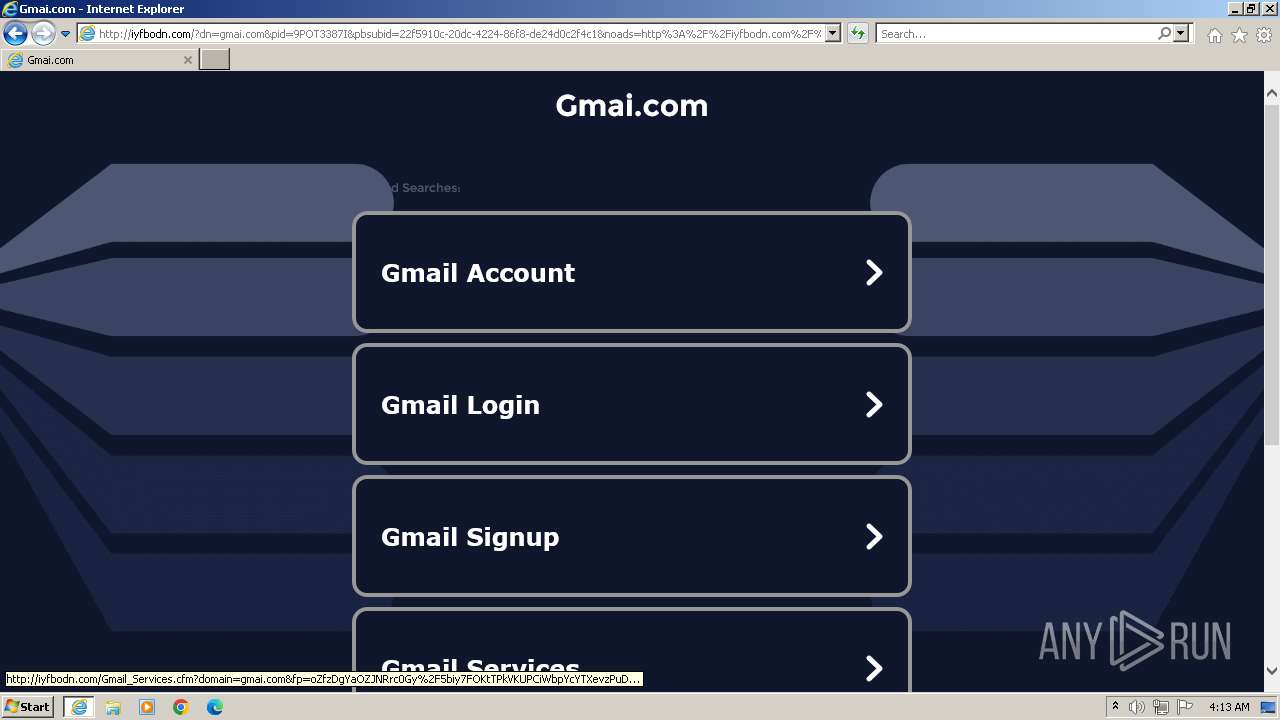
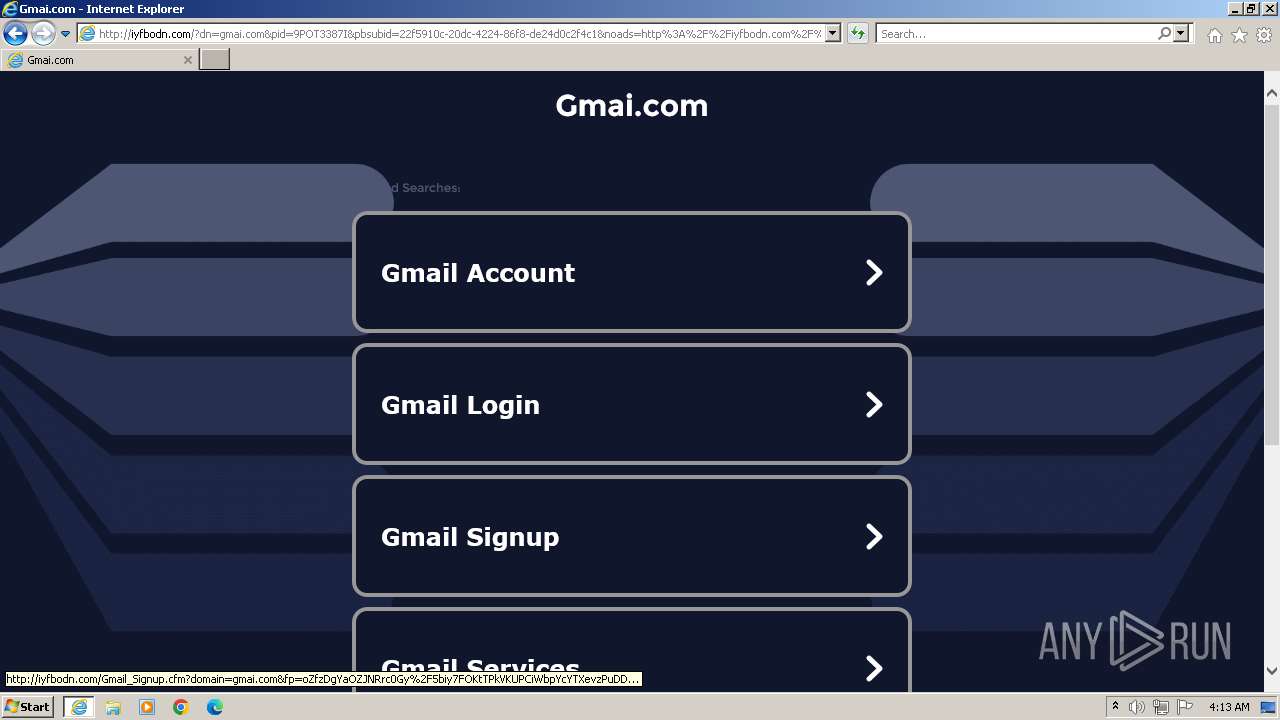
| URL: | gmai.com |
| Full analysis: | https://app.any.run/tasks/9e7fc3e8-52e0-43fb-8cc9-64ae86b3b3c5 |
| Verdict: | Malicious activity |
| Analysis date: | October 06, 2023, 03:12:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B5CB62647CCD822D6F8E50F923074CCA |
| SHA1: | 03F84F343C5D27F8DF25C8D67A06C678C6862D9B |
| SHA256: | 6F833158032A69B89BFF249CEA1EC97CA9702684D14FD40F619F9D1118B97D02 |
| SSDEEP: | 3:5ZIn:52n |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 612 | "C:\Program Files\Internet Explorer\iexplore.exe" "gmai.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3460 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:612 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
21 416
Read events
21 354
Write events
62
Delete events
0
Modification events
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (612) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
30
Text files
35
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3460 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\P8C0PPNC.txt | text | |
MD5:FE67F54A498E268070DD9DBA5E595B8A | SHA256:266D08B572D6D3F98C045D2D45A34787C1C823E2395D8AC03E166F28636483FD | |||
| 3460 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\OS0ZSV8R.txt | text | |
MD5:196920095FD62F393E95E3582F0D80CF | SHA256:839D42806A8B855000D9635C3082D3FFE732E5511D28EE391A1E2760F94B85B0 | |||
| 3460 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:25766C8E29903C5C4A6BF7F48BF32F59 | SHA256:0E053761C5620127012D18B4476EFFA94ADC6CFBEC34C9404E791772D7038780 | |||
| 3460 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E87CE99F124623F95572A696C80EFCAF_BBCE07F0D1D3591F7AACC4D200BCC3F0 | binary | |
MD5:BC488E5B16E6CA885CA0FBFD1F851A48 | SHA256:7F71B7B292A9633C8B22AD324F572865D75F20B35B7C1577414FA9B802D79B6E | |||
| 3460 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\PSYNJOPW.txt | text | |
MD5:F6CEDA06618371FC12865C0028F13F97 | SHA256:8E4B7452E3C7591D84CF25EA107848D017A53A49FA331B01241422D52CAC14FE | |||
| 3460 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E87CE99F124623F95572A696C80EFCAF_BBCE07F0D1D3591F7AACC4D200BCC3F0 | binary | |
MD5:AE5D71AA0E438260F532D2F999674D79 | SHA256:6FB92509611D81F6238D7F25DADF34A1C49D3C0EA86CE8E1EB982EE67264D841 | |||
| 3460 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:B63828AC5CA1DAE906229E0CF911EDDD | SHA256:16BAC58A4612E5448EE320ACE402C919162FFD048BB4B0E12CFAC627564317DB | |||
| 3460 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\D7B1I2M2.txt | text | |
MD5:F0F07C9455DCBEBE1D6F54B7D9756F02 | SHA256:40E814B296D56F36CFED66DA466D93A73D5DAC34E8078660C3117AF1273C067D | |||
| 3460 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A16C6C16D94F76E0808C087DFC657D99_42DEC485767232C8B99FDCA35BF678E8 | binary | |
MD5:709C54022790FC68487E9EC19D60CBDB | SHA256:8420E4B249E15043B4727A378F66CA6E9B983936A9746A28481F56029EE499E1 | |||
| 3460 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
38
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3460 | iexplore.exe | POST | 200 | 199.59.243.225:80 | http://ww1.gmai.com/_fd | unknown | compressed | 1.98 Kb | unknown |
3460 | iexplore.exe | GET | 200 | 199.59.243.225:80 | http://ww1.gmai.com/ | unknown | html | 1009 b | unknown |
3460 | iexplore.exe | GET | 200 | 199.59.243.225:80 | http://ww1.gmai.com/aQxparBlG.js | unknown | html | 67.5 Kb | unknown |
3460 | iexplore.exe | GET | 200 | 199.59.243.225:80 | http://ww1.gmai.com/px.gif?ch=1&rn=8.473729736487918 | unknown | image | 42 b | unknown |
3460 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?842b3e01a16ab432 | unknown | compressed | 4.66 Kb | unknown |
612 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | unknown | binary | 1.47 Kb | unknown |
3460 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDT17UIkLKbfRLCBYCPDA60 | unknown | binary | 472 b | unknown |
3460 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEBM9NSid4pOvCr35n90pfXk%3D | unknown | binary | 471 b | unknown |
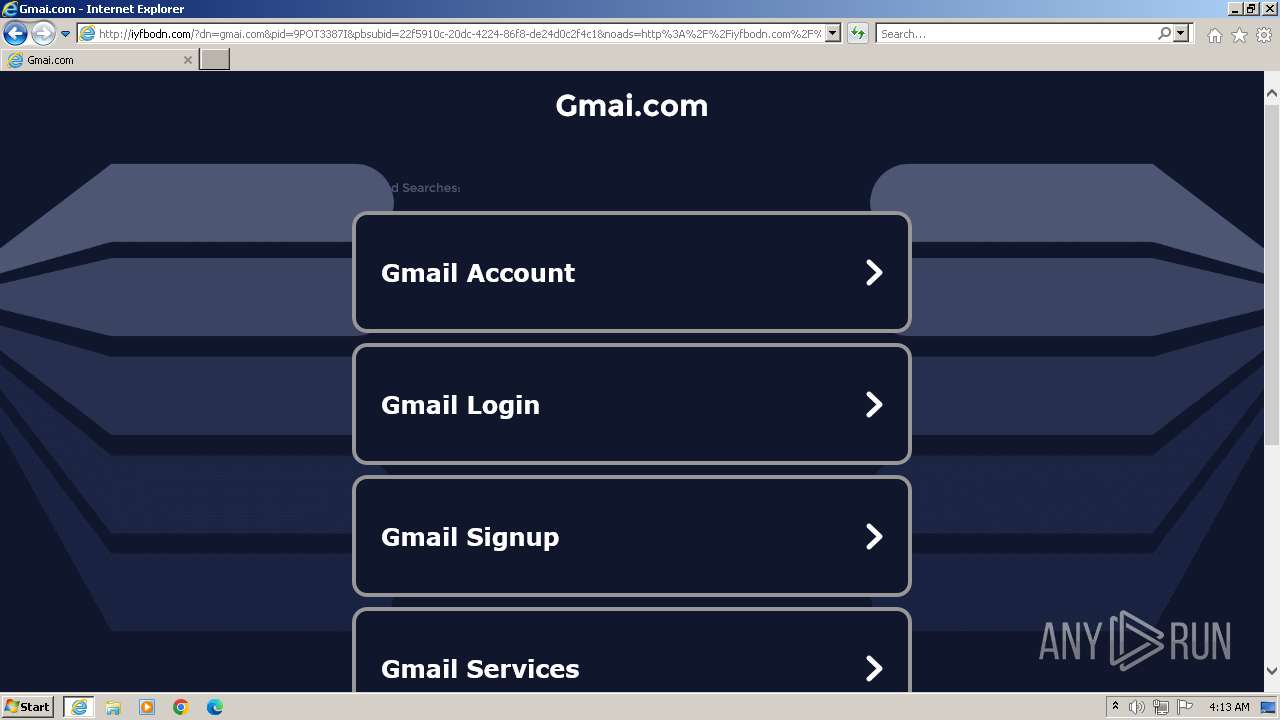
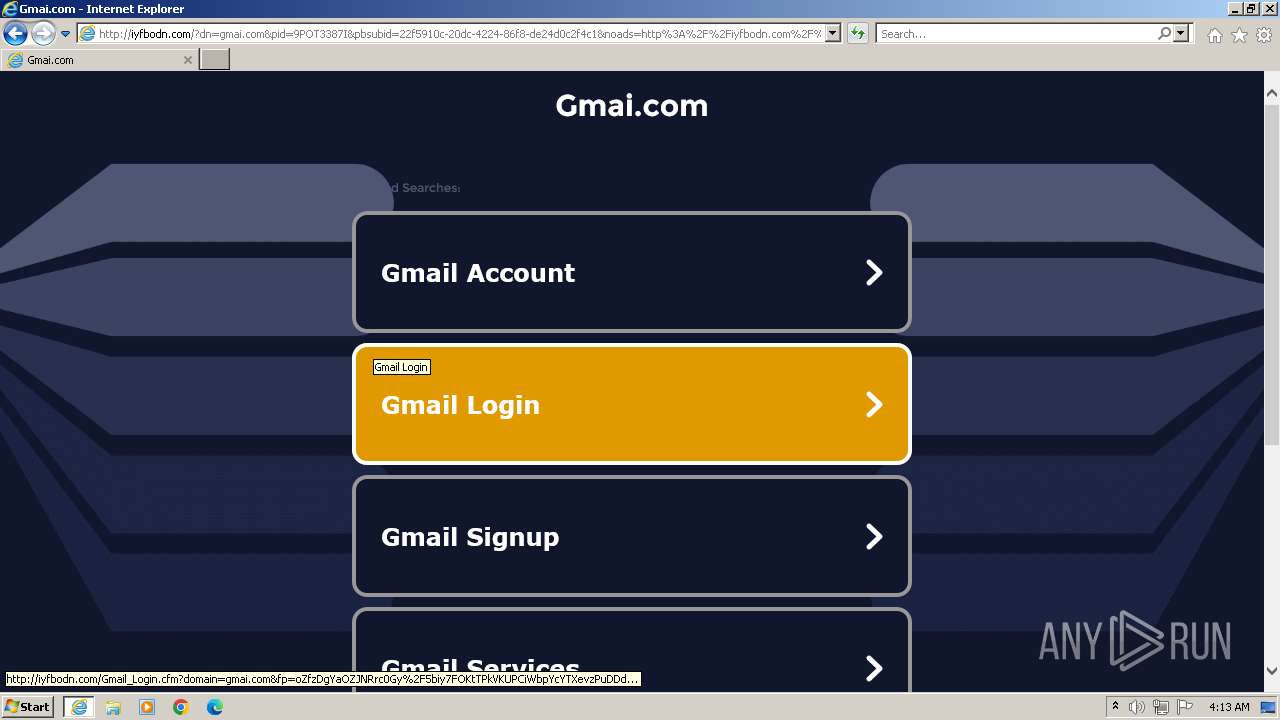
3460 | iexplore.exe | GET | 200 | 208.91.196.46:80 | http://iyfbodn.com/px.js?ch=1 | unknown | text | 346 b | unknown |
3460 | iexplore.exe | GET | 200 | 208.91.196.46:80 | http://iyfbodn.com/?dn=gmai.com&pid=9POT3387I&pbsubid=22f5910c-20dc-4224-86f8-de24d0c2f4c1&noads=http%3A%2F%2Fiyfbodn.com%2F%3Fdn%3Dgmai.com%26skipskenzo%3Dtrue | unknown | html | 28.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3460 | iexplore.exe | 78.41.204.39:80 | gmai.com | Snel.com B.V. | NL | unknown |
3460 | iexplore.exe | 199.59.243.225:80 | ww1.gmai.com | AMAZON-02 | US | unknown |
3460 | iexplore.exe | 142.250.74.196:443 | www.google.com | GOOGLE | US | whitelisted |
3460 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
3460 | iexplore.exe | 142.250.181.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3460 | iexplore.exe | 142.250.184.226:443 | partner.googleadservices.com | GOOGLE | US | whitelisted |
3460 | iexplore.exe | 172.217.16.195:443 | www.gstatic.com | GOOGLE | US | whitelisted |
3460 | iexplore.exe | 142.250.185.99:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
612 | iexplore.exe | 92.123.104.59:443 | www.bing.com | Akamai International B.V. | DE | unknown |
612 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
gmai.com |
| whitelisted |
ww1.gmai.com |
| unknown |
www.google.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
partner.googleadservices.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |