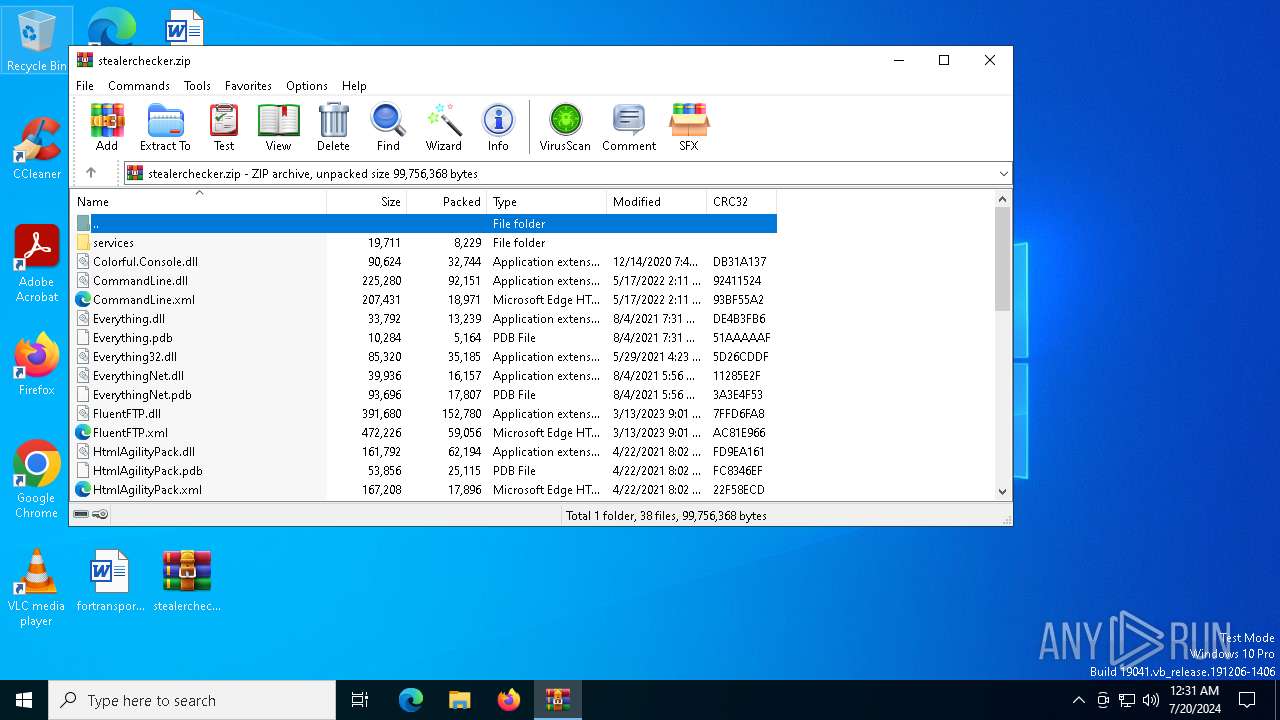
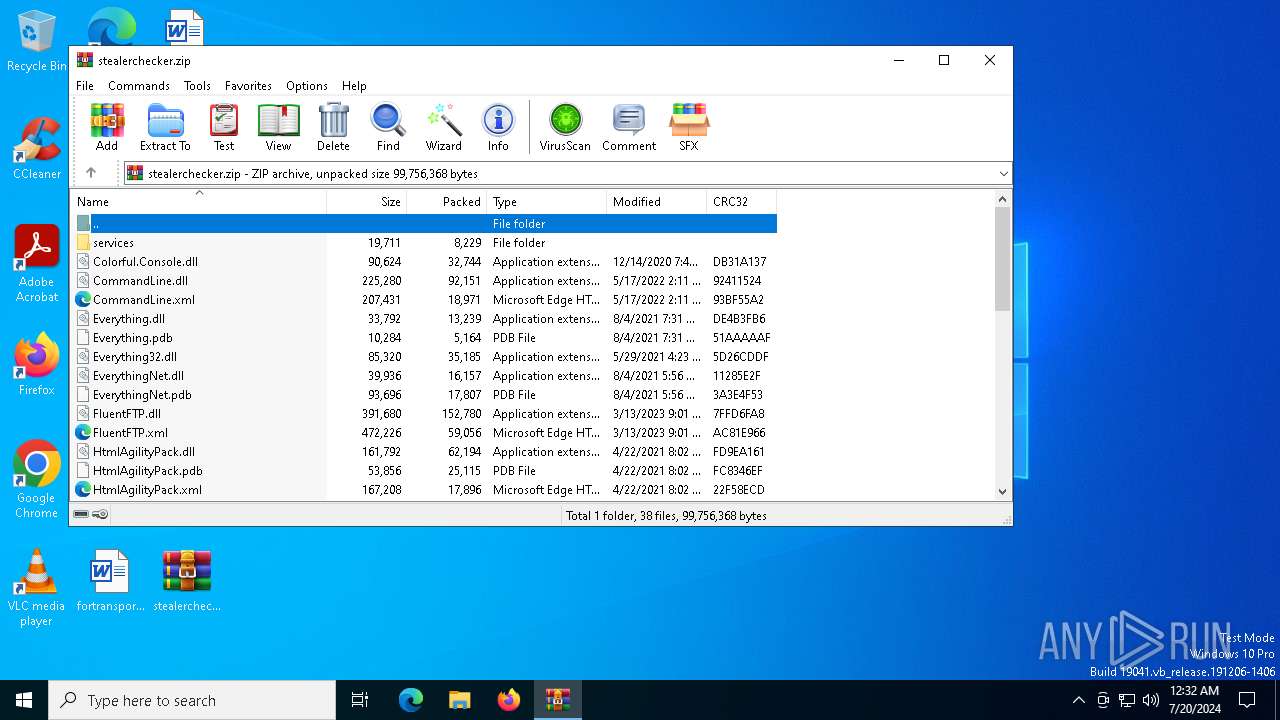
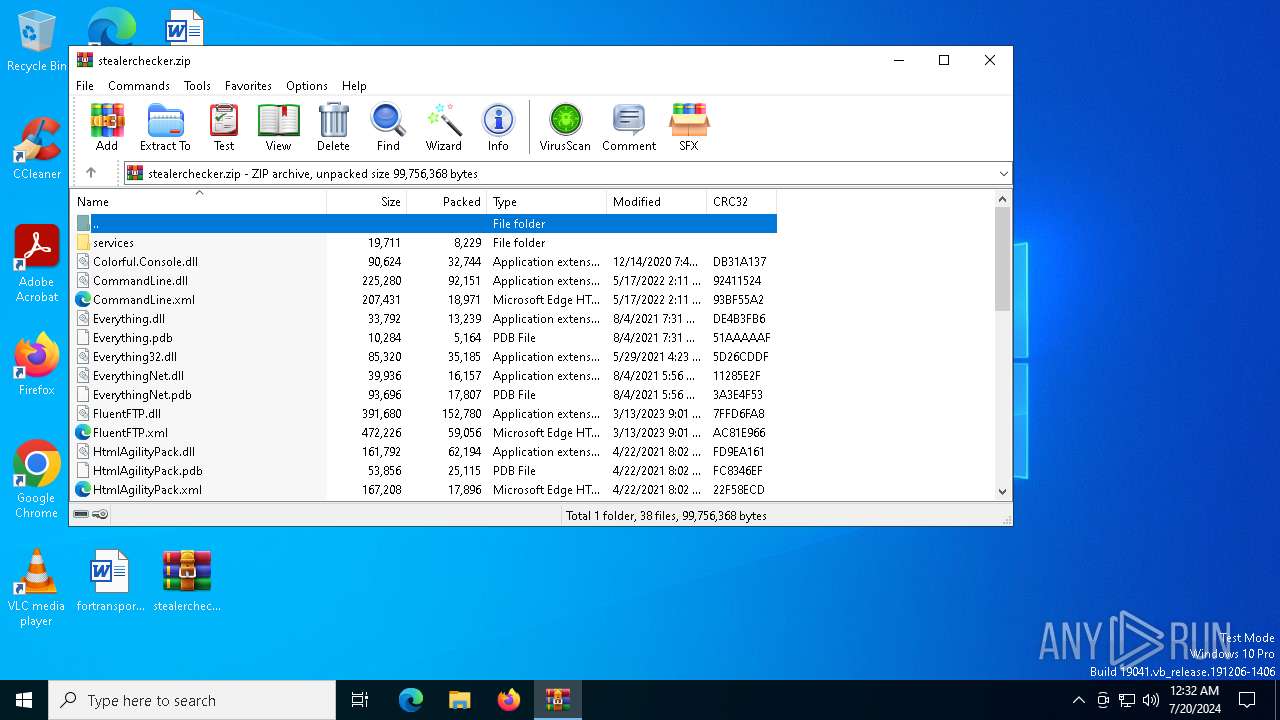
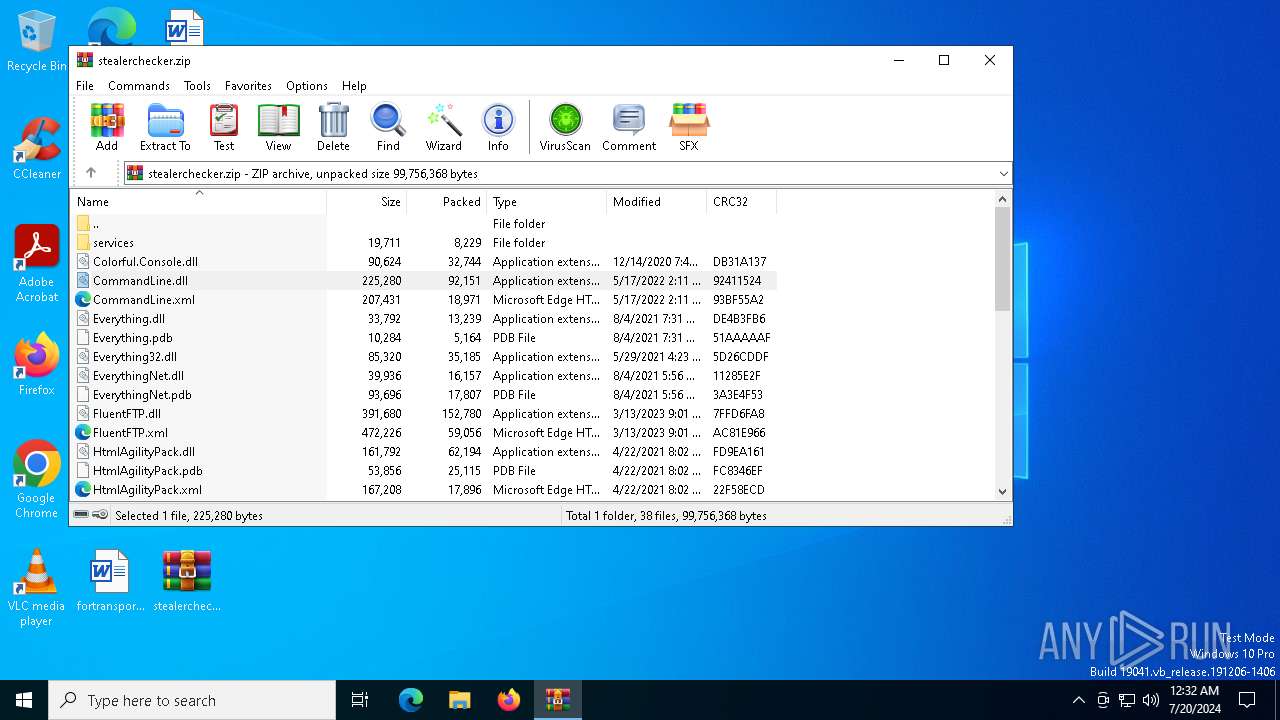
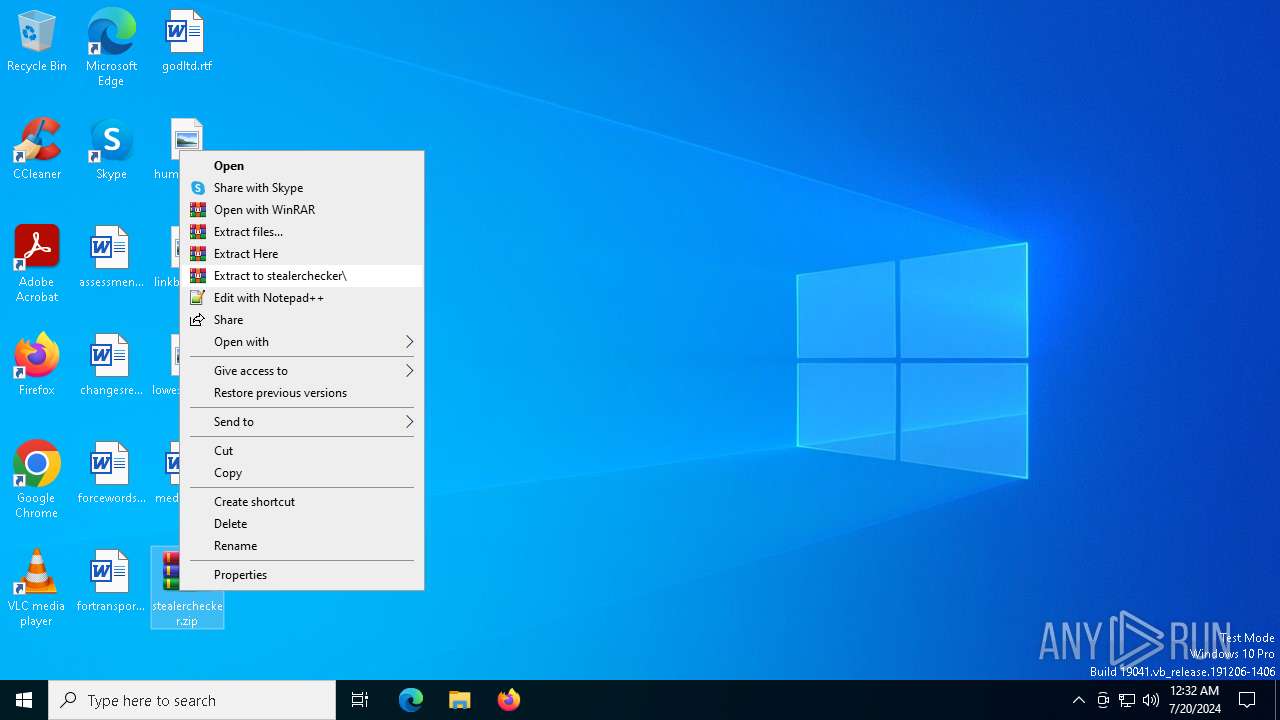
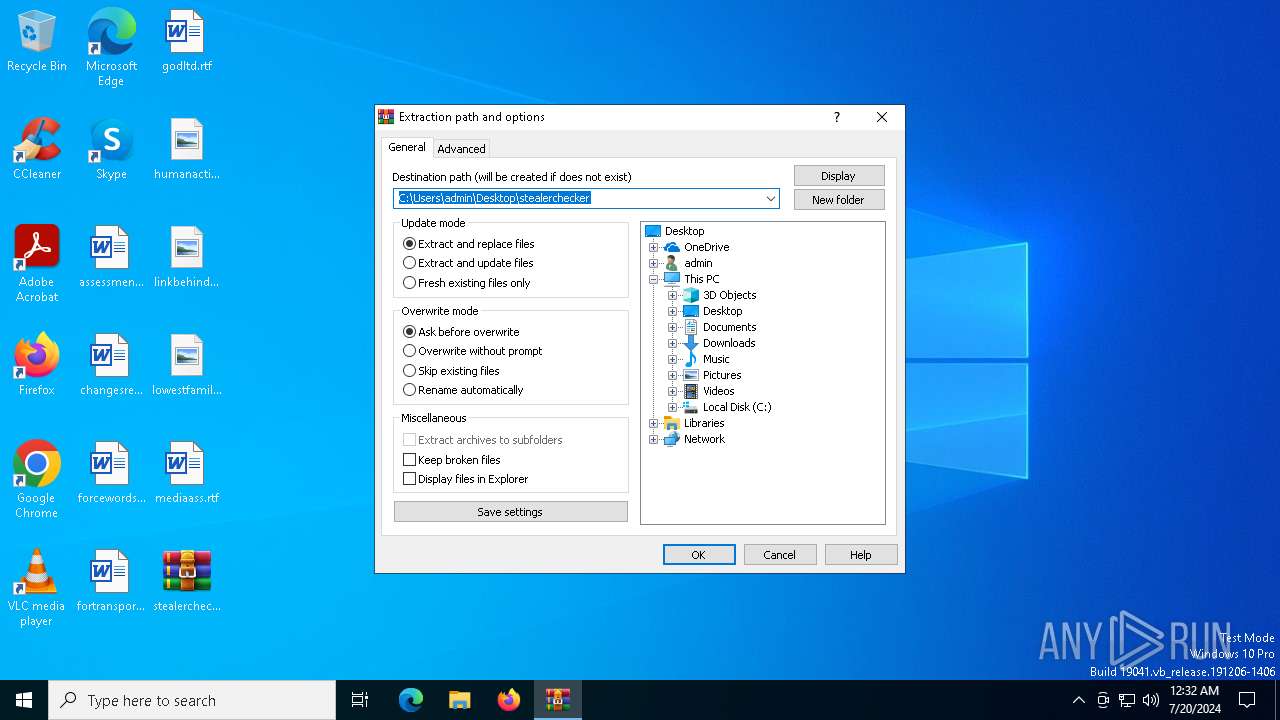
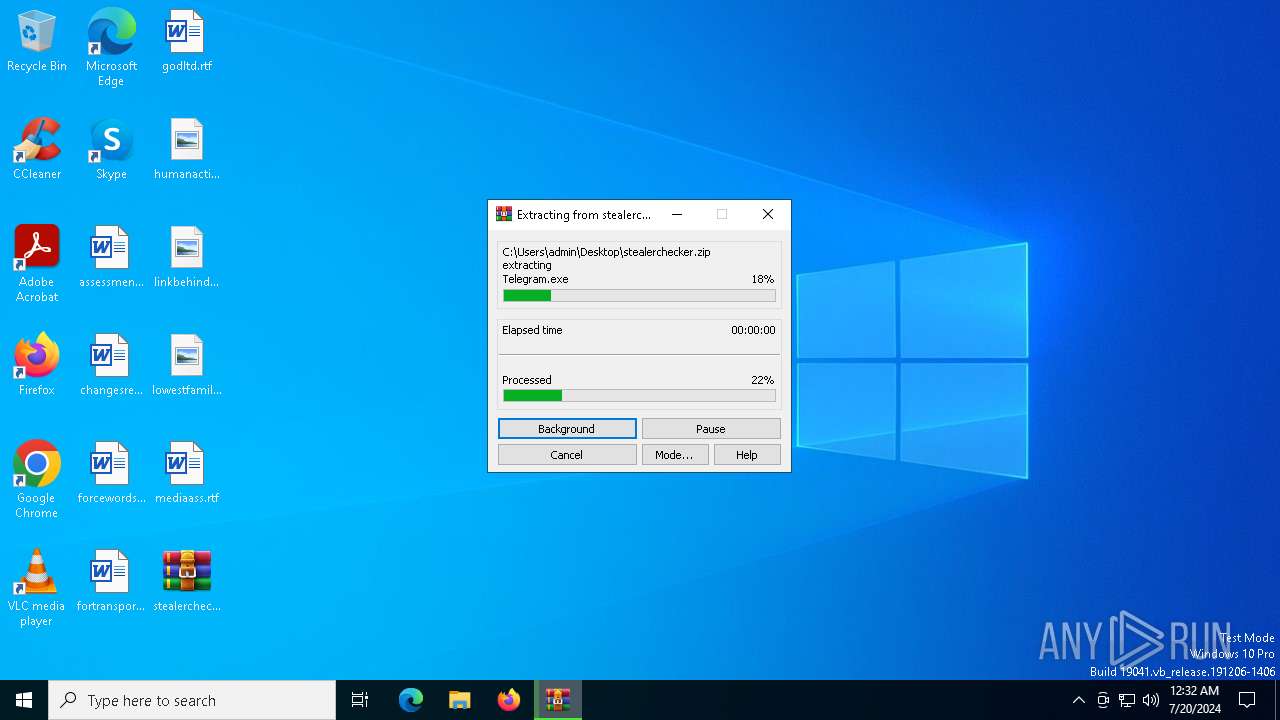
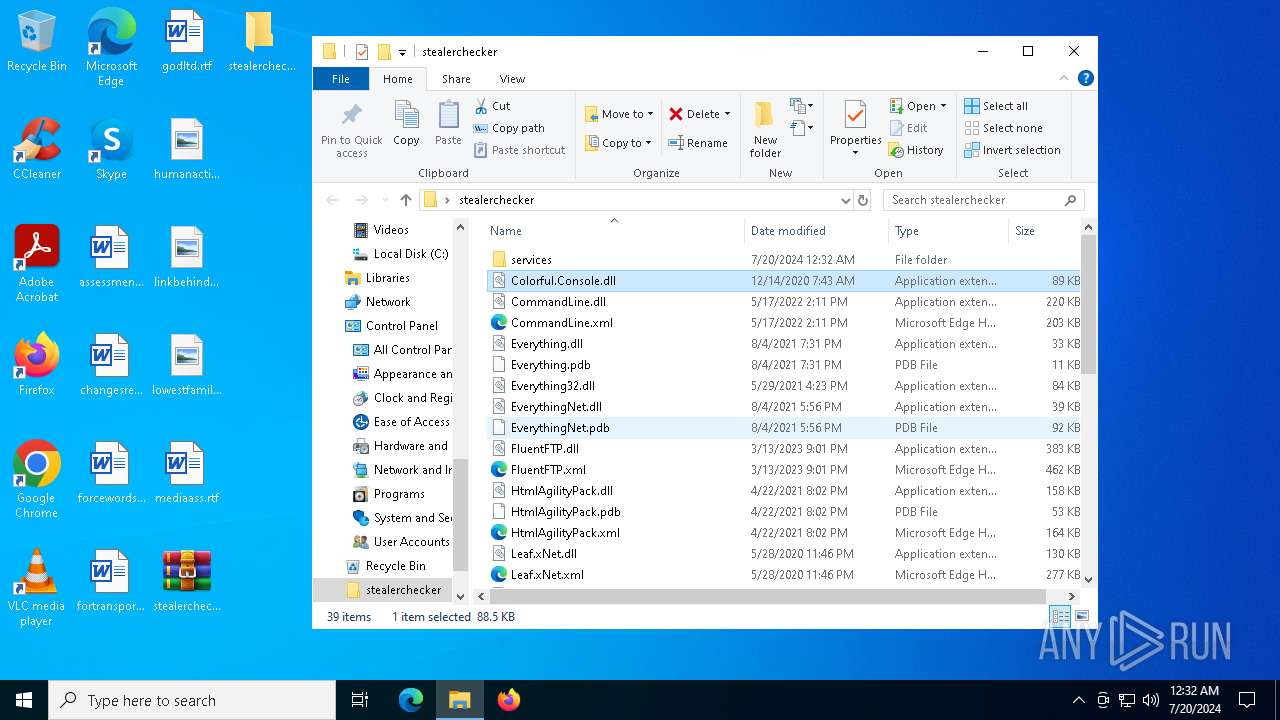
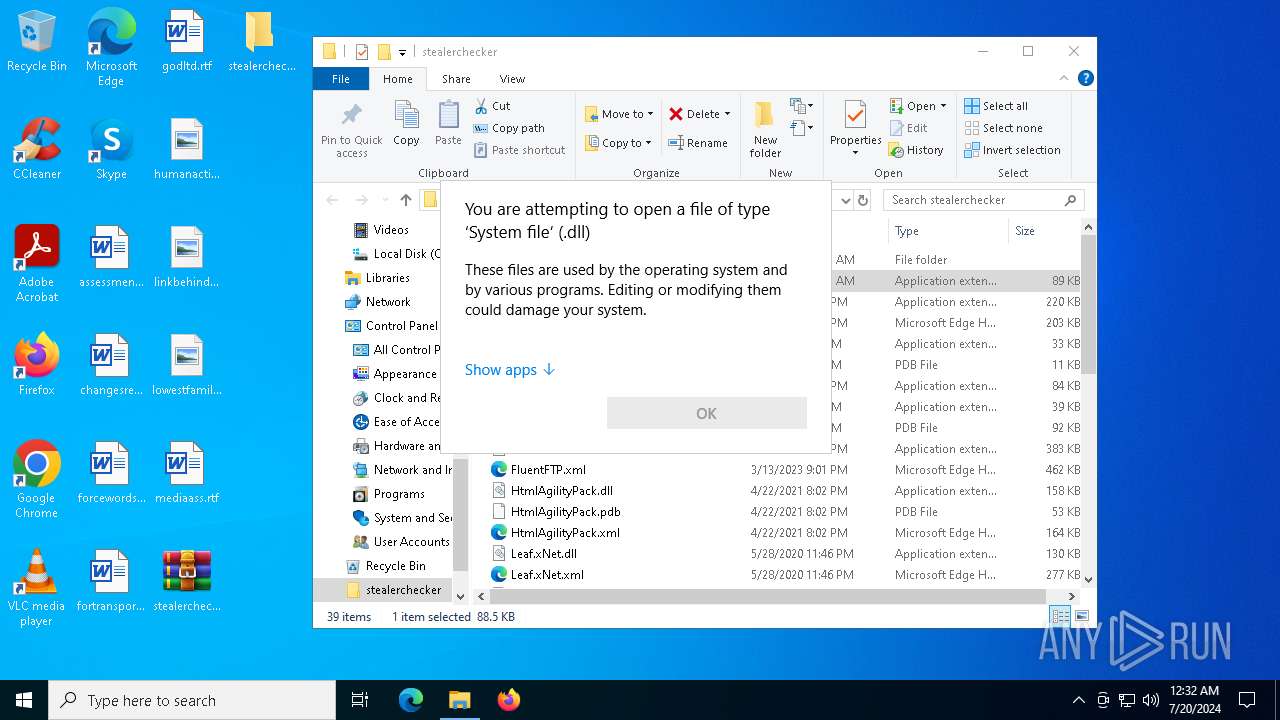
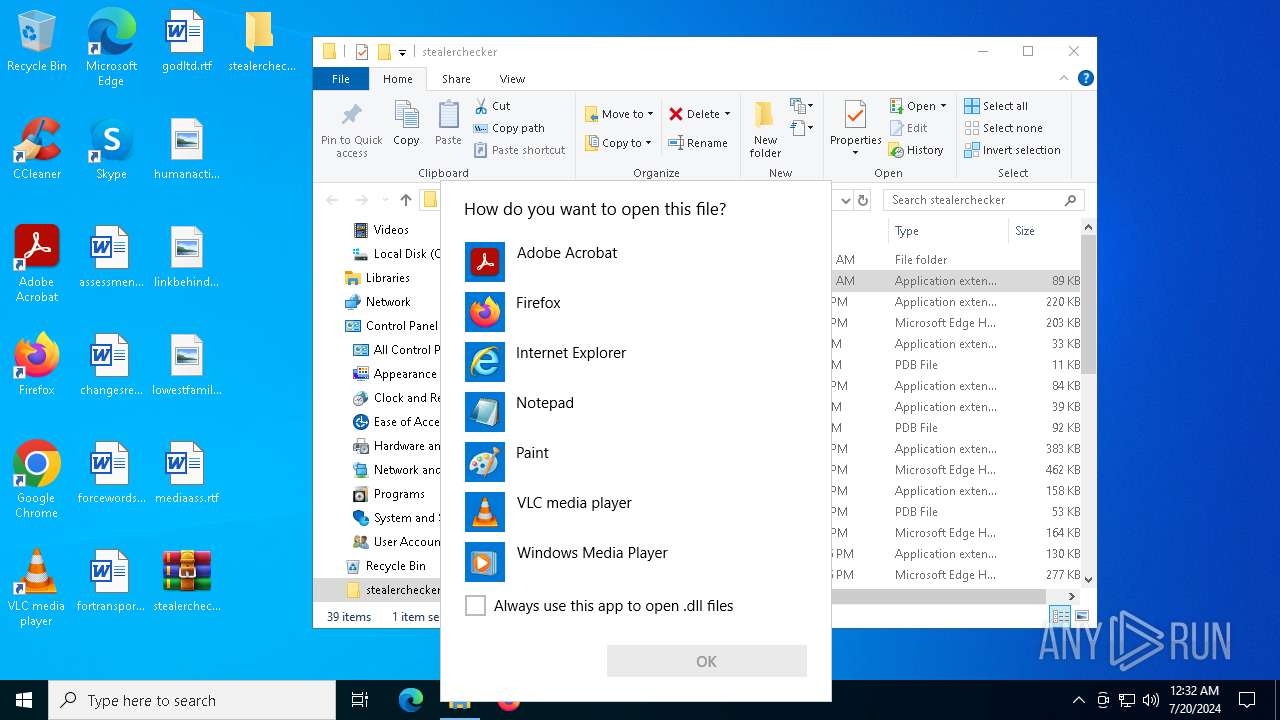
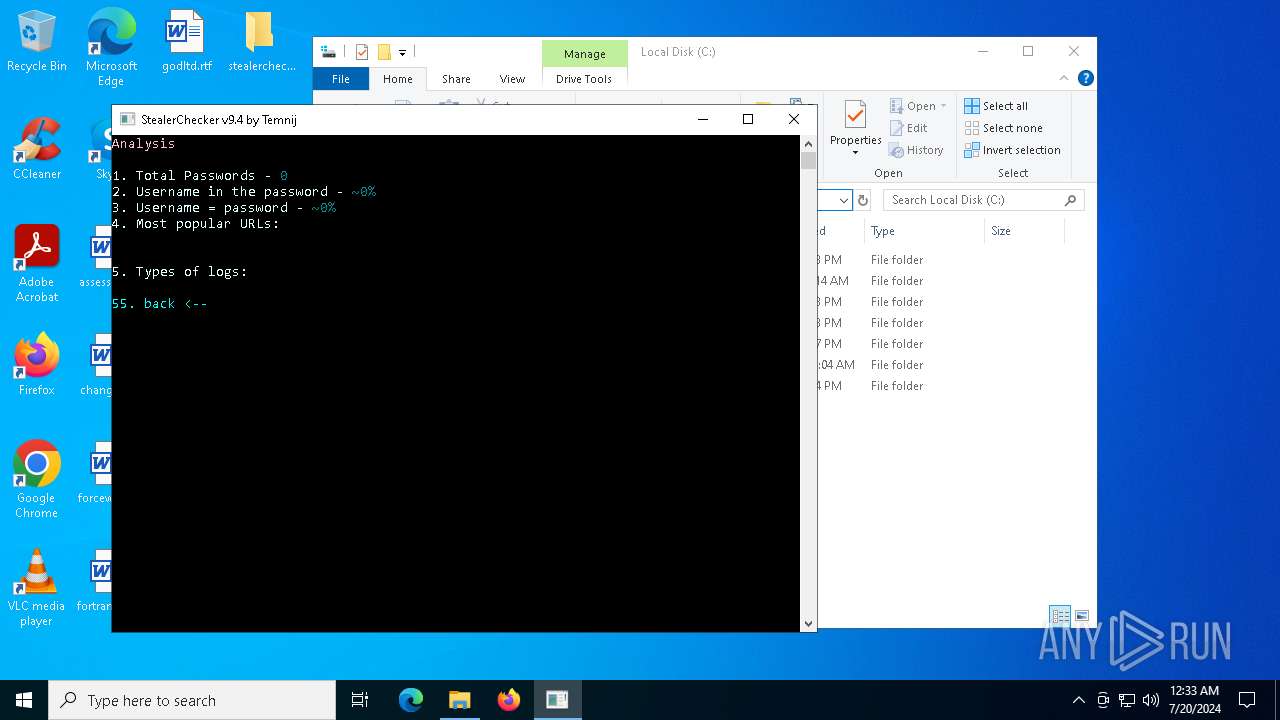
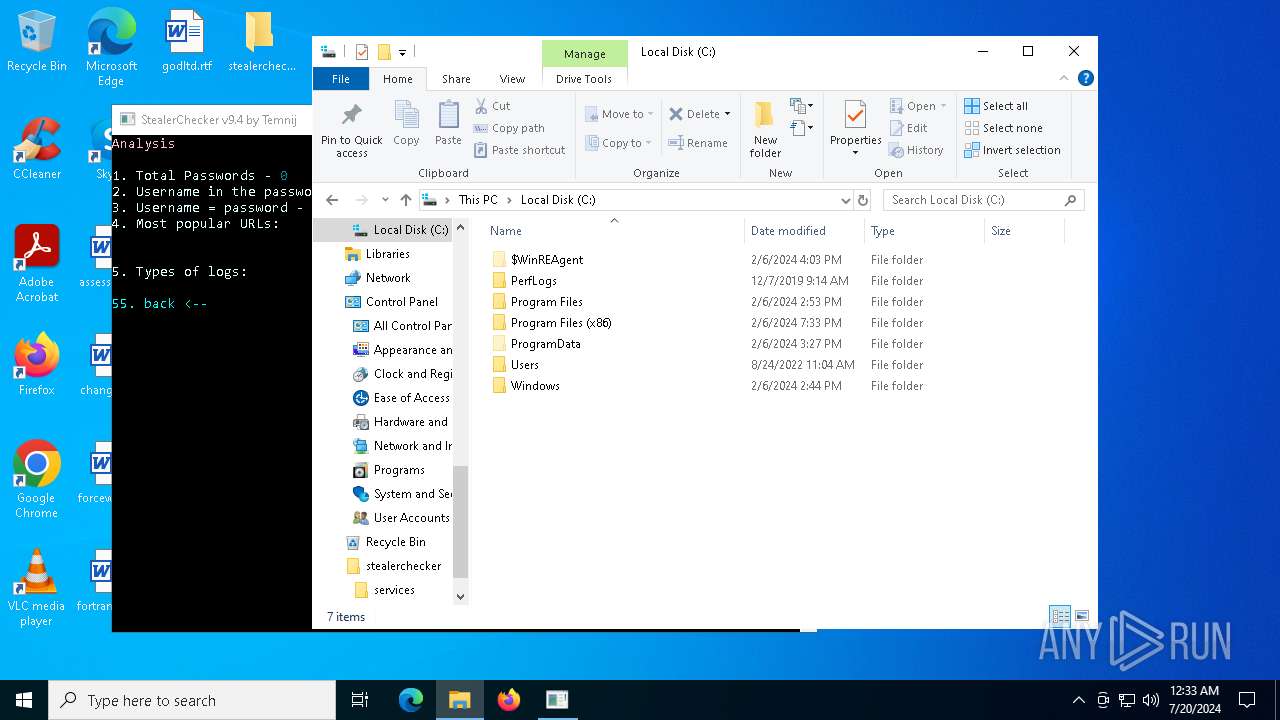
| File name: | stealerchecker.zip |
| Full analysis: | https://app.any.run/tasks/82e54f3a-655a-4262-a3d4-4f63eaea2b8b |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | July 20, 2024, 00:31:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 5792F2E296D98C0B9846CF29CF3840E4 |
| SHA1: | 906C210B3813EA776C46AEEF704DAA7F9CFD26BF |
| SHA256: | 6F35CEABE14F3AB8BA5C644B8486BACBF8AF2E71094098A18F4A6FEFBCF099F0 |
| SSDEEP: | 393216:XxMCz9Mi3j3hjfV7xw9DEK+5OG1E3xEKO1X7ld5OIvgYY:qK3D1V7xwCK+L1EhG1XAIv/Y |
MALICIOUS
DCRAT has been detected (YARA)
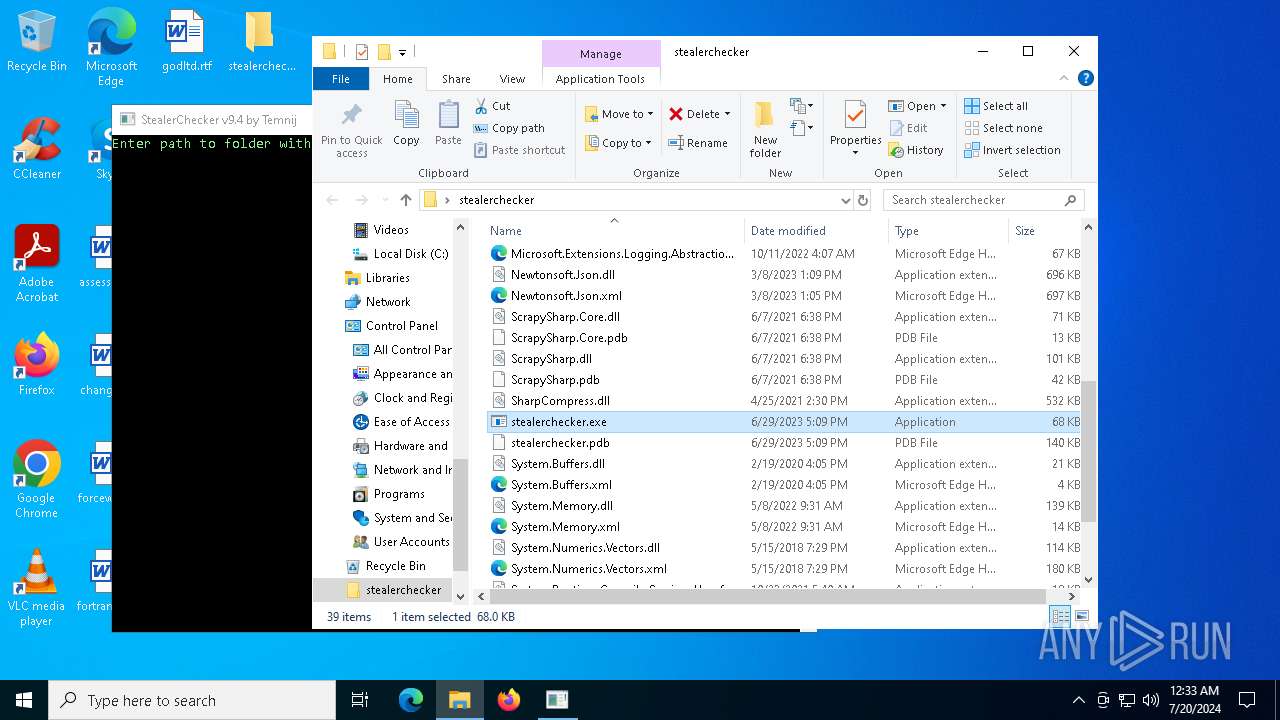
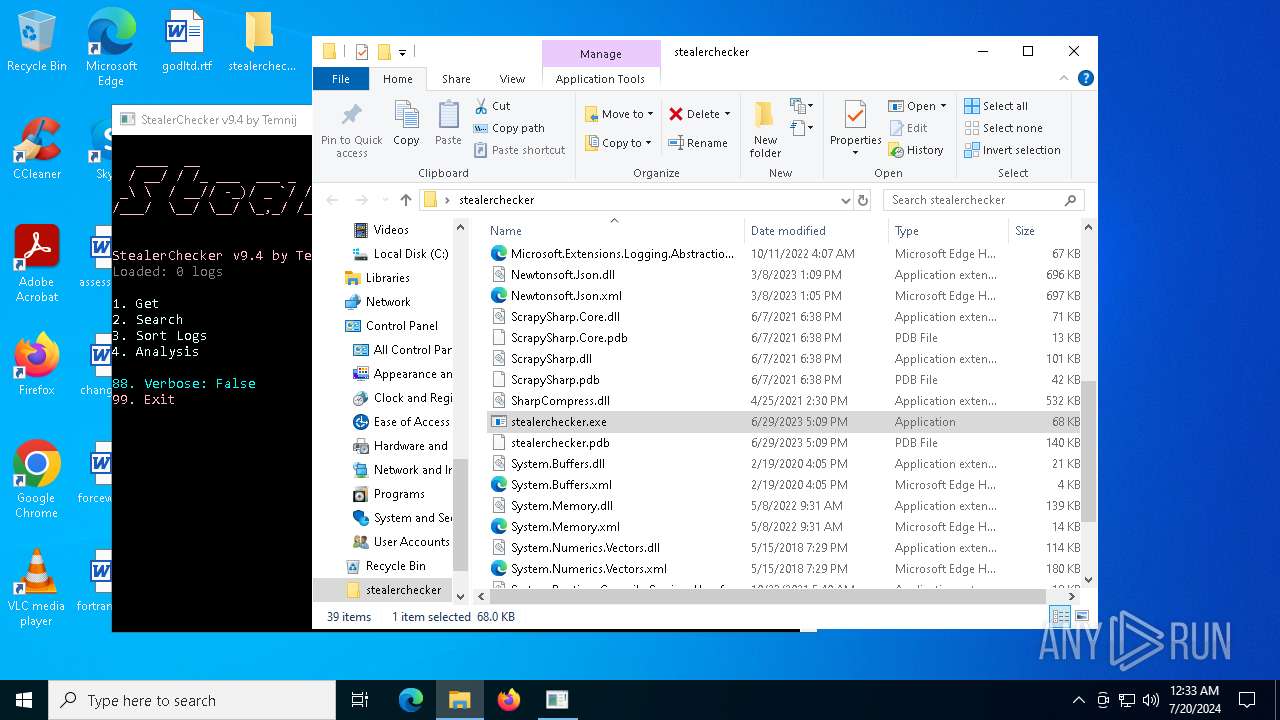
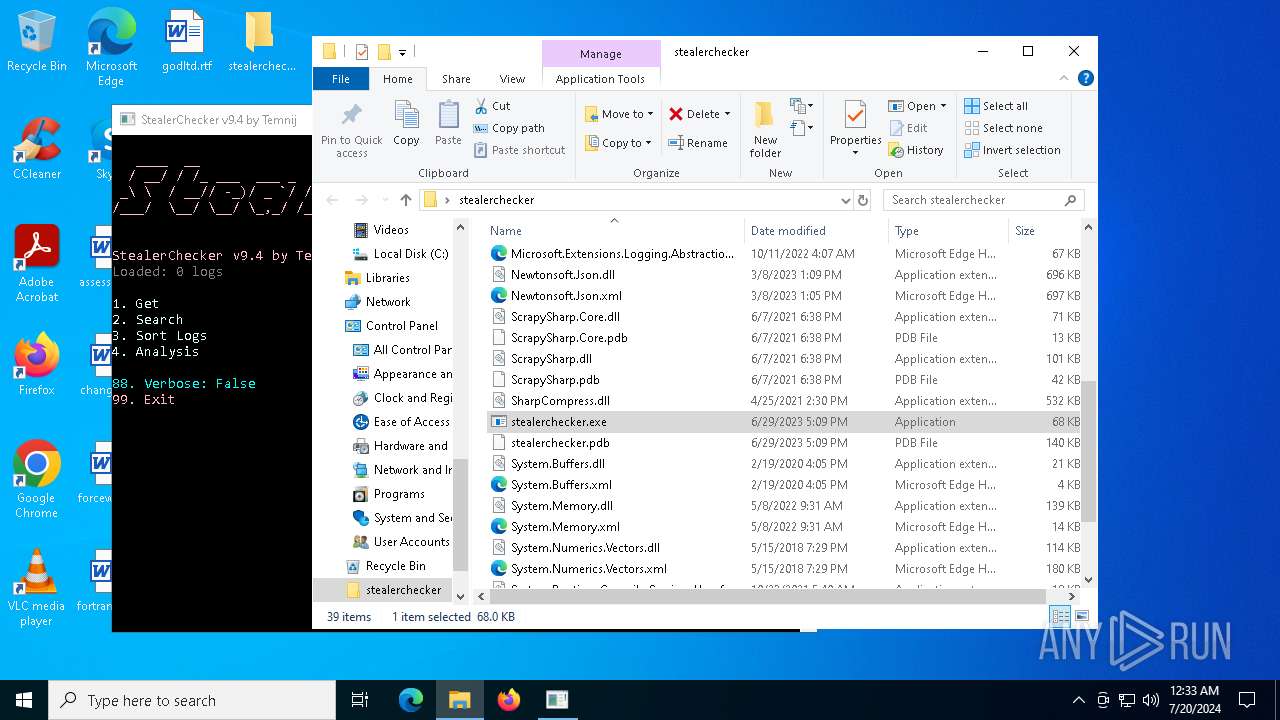
- stealerchecker.exe (PID: 4288)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6364)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 1940)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1940)
- WinRAR.exe (PID: 6364)
Manual execution by a user
- WinRAR.exe (PID: 1940)
- stealerchecker.exe (PID: 4288)
- WinRAR.exe (PID: 4076)
Checks supported languages
- stealerchecker.exe (PID: 4288)
Reads the computer name
- stealerchecker.exe (PID: 4288)
Checks proxy server information
- stealerchecker.exe (PID: 4288)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 3628)
- OpenWith.exe (PID: 6668)
Reads Environment values
- stealerchecker.exe (PID: 4288)
Reads the software policy settings
- stealerchecker.exe (PID: 4288)
Reads the machine GUID from the registry
- stealerchecker.exe (PID: 4288)
Disables trace logs
- stealerchecker.exe (PID: 4288)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1940)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:12:14 07:43:46 |
| ZipCRC: | 0xdb31a137 |
| ZipCompressedSize: | 32744 |
| ZipUncompressedSize: | 90624 |
| ZipFileName: | Colorful.Console.dll |
Total processes
132
Monitored processes
8
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1940 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\stealerchecker.zip" "?\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3220 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3628 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4076 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\stealerchecker.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
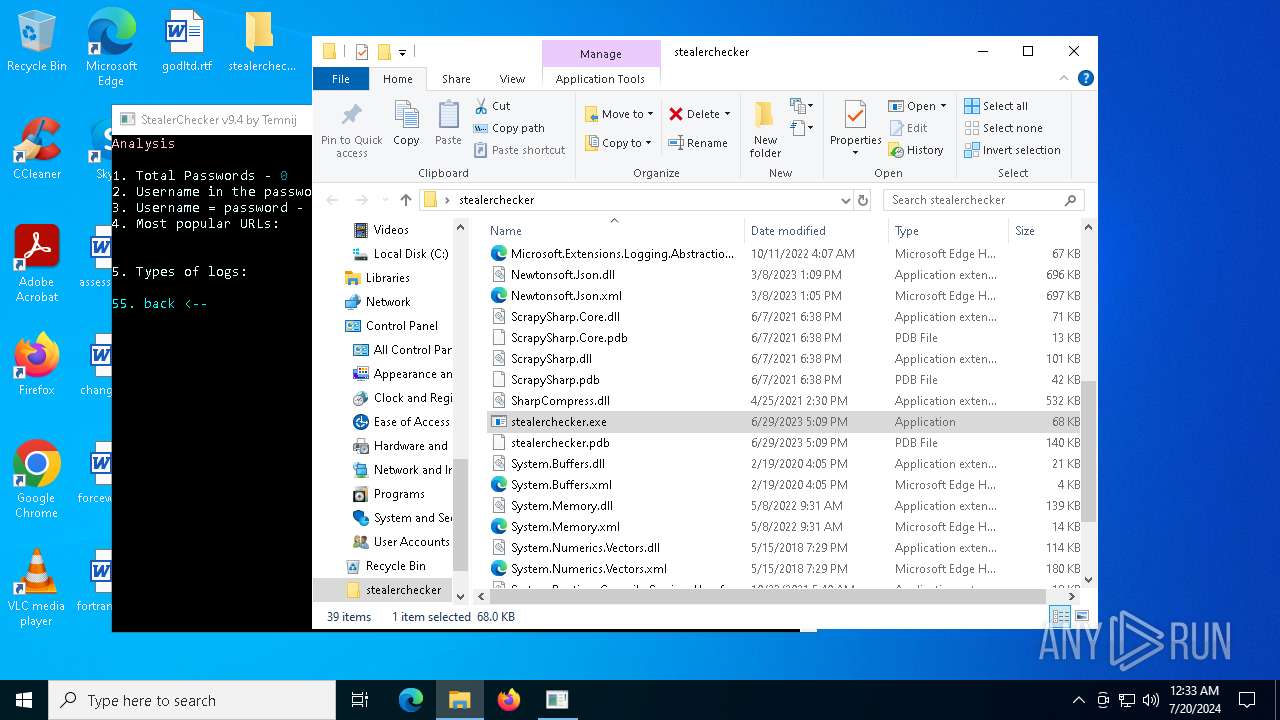
| 4288 | "C:\Users\admin\Desktop\stealerchecker\stealerchecker.exe" | C:\Users\admin\Desktop\stealerchecker\stealerchecker.exe | explorer.exe | ||||||||||||
User: admin Company: Temnij Integrity Level: MEDIUM Description: StealerChecker Version: 9.2.0.0 Modules
| |||||||||||||||
| 6364 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\stealerchecker.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6668 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7400 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | stealerchecker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 795
Read events
17 707
Write events
88
Delete events
0
Modification events
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\stealerchecker.zip | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
20
Suspicious files
7
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1940 | WinRAR.exe | C:\Users\admin\Desktop\stealerchecker\FluentFTP.xml | xml | |
MD5:AA6D45CAEFD55FFB3F9B6BE7F21C9EC2 | SHA256:2E80E3E37E898C2C10075EFCE02A7E9F4DC77B13D8CFA5FDBAA7A40B762275A6 | |||
| 1940 | WinRAR.exe | C:\Users\admin\Desktop\stealerchecker\HtmlAgilityPack.dll | executable | |
MD5:055397FD48839C9799F5286B4389D318 | SHA256:11B1A0C9B44CD484758DA9E23B55ADC95222F87E96DE985EF7CD976BF87CAAD7 | |||
| 1940 | WinRAR.exe | C:\Users\admin\Desktop\stealerchecker\HtmlAgilityPack.pdb | binary | |
MD5:00DEA0A4F8EA137A56A3DB06884ECEA2 | SHA256:6CE028297D4A029A21FD0D867A8DE67A47A8B7CD58D46400CE2F66C24161E1E3 | |||
| 1940 | WinRAR.exe | C:\Users\admin\Desktop\stealerchecker\Microsoft.Extensions.Logging.Abstractions.xml | xml | |
MD5:71FCAD21AEC8A8ED130F7939FF8F70C5 | SHA256:92A9DBECE8DA48BEE21C457229928D74C7300A3F00596717D959EB8A152C0983 | |||
| 1940 | WinRAR.exe | C:\Users\admin\Desktop\stealerchecker\Microsoft.Extensions.Logging.Abstractions.dll | executable | |
MD5:1A5BFF28FB38234646951AA48DA14620 | SHA256:5BBE7C1D06585CAB5482B50B87A0DF3476A7617C5D849A75D6D91E013F2BC877 | |||
| 6364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6364.35113\CommandLine.dll | executable | |
MD5:2F345B6D207489E52DB3F85C2E4E617D | SHA256:2135B40FA819E58CF1942453E4409BFDEA2BE631077A354B878DE8402BE7E026 | |||
| 1940 | WinRAR.exe | C:\Users\admin\Desktop\stealerchecker\Everything.pdb | binary | |
MD5:5BF86321410026383694295106A11E3A | SHA256:CE348E62D74117AEC74744084A354F55CD1177B63DA2C0E3E56FACB15AE940D9 | |||
| 1940 | WinRAR.exe | C:\Users\admin\Desktop\stealerchecker\Colorful.Console.dll | executable | |
MD5:9F6CE7FF934FB2E786CED3516705EFAD | SHA256:59A3696950AC3525E31CDD26727DABD9FECD2E1BDC1C47C370D4B04420592436 | |||
| 1940 | WinRAR.exe | C:\Users\admin\Desktop\stealerchecker\FluentFTP.dll | executable | |
MD5:A02A1FAD8AAE1C292014D9EA1FAC2B53 | SHA256:DEB3324F7D7AFD517FC2366F69032FAC120158A4B04E6EF987865466D9088F7B | |||
| 1940 | WinRAR.exe | C:\Users\admin\Desktop\stealerchecker\Leaf.xNet.xml | xml | |
MD5:B033607C30C9E7A25BA3E478B0A00E18 | SHA256:52631A555C91918BF0922474667DC6BB3576F1EAECE34480AE8ADDABCC7D0F08 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
54
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 20.3.187.198:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
— | — | POST | — | 20.190.159.75:443 | https://login.live.com/RST2.srf | unknown | — | — | unknown |
— | — | GET | 200 | 184.86.251.22:443 | https://www.bing.com/client/config?cc=US&setlang=en-US | unknown | binary | 2.15 Kb | unknown |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | unknown |
— | — | GET | 200 | 20.199.58.43:443 | https://fd.api.iris.microsoft.com/v4/api/selection?&asid=52B503DE342043A68D0A80B2E5577BFE&nct=1&placement=88000677&bcnt=30&country=US&locale=en-US&poptin=0&fmt=json&arch=AMD64&chassis=1&concp=0&d3dfl=D3D_FEATURE_LEVEL_12_1&devfam=Windows.Desktop&devosver=10.0.19045.4046&dinst=1661339444&dmret=0&flightbranch=&flightring=Retail&icluc=0&localid=w%3AAC7699B0-48EA-FD22-C8DC-06A02098A0F0&oem=DELL&osbranch=vb_release&oslocale=en-US&osret=1&ossku=Professional&osskuid=48&prccn=4&prccs=3094&prcmf=AuthenticAMD&procm=Intel%28R%29%20Core%28TM%29%20i5-6400%20CPU%20%40%202.70GHz&ram=4096&tinst=Client&tl=1&pat=0&smc=0&sac=0&disphorzres=1280&dispsize=15.3&dispvertres=720&ldisphorzres=1280&ldispvertres=720&moncnt=1&cpdsk=260281&frdsk=218542&lo=3611071&tsu=1001601 | unknown | binary | 102 b | unknown |
— | — | GET | 200 | 140.82.121.5:443 | https://api.github.com/repos/kzorin52/stealerchecker/releases/latest | unknown | binary | 3.84 Kb | unknown |
— | — | POST | 200 | 20.103.156.88:443 | https://arc.msn.com/v4/api/register?asid=543E7852DDF149A4B809D5CAC10DF60C&placement=cdmdevreg&country=US&locale=en-US&poptin=0&fmt=json&arch=AMD64&chassis=1&concp=0&d3dfl=D3D_FEATURE_LEVEL_12_1&devfam=Windows.Desktop&devosver=10.0.19045.4046&dinst=1661339444&dmret=0&flightbranch=&flightring=Retail&icluc=0&localid=w%3AAC7699B0-48EA-FD22-C8DC-06A02098A0F0&oem=DELL&osbranch=vb_release&oslocale=en-US&osret=1&ossku=Professional&osskuid=48&prccn=4&prccs=3094&prcmf=AuthenticAMD&procm=Intel%28R%29%20Core%28TM%29%20i5-6400%20CPU%20%40%202.70GHz&ram=4096&tinst=Client&tl=1&pat=0&smc=0&sac=0&disphorzres=1280&dispsize=15.3&dispvertres=720&ldisphorzres=1280&ldispvertres=720&moncnt=1&cpdsk=260281&frdsk=218542&lo=3611071&tsu=1001600 | unknown | — | — | unknown |
— | — | GET | 200 | 20.12.23.50:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
— | — | GET | 304 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7BE7A50285-D08D-499D-9FF8-180FDC2332BC%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7BE7A50285-D08D-499D-9FF8-180FDC2332BC%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | compressed | 24.8 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 4.208.221.206:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 40.115.3.253:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6592 | backgroundTaskHost.exe | 184.86.251.7:443 | www.bing.com | Akamai International B.V. | DE | unknown |
6556 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
api.github.com |
| whitelisted |