| File name: | blackbox.exe |
| Full analysis: | https://app.any.run/tasks/547b1410-b54c-4839-80e6-d5aa1d62fa32 |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2019, 00:24:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | A3B45CA464654717CC3C7D1046FB6165 |
| SHA1: | 4806533A559655B6AD14474AB63EB94A39189438 |
| SHA256: | 6F28A3B3B193AB0A3D94C3F0E7FB845988F2D01AA7BF29256B124BBAE867D6C4 |
| SSDEEP: | 98304:RcSt3M4lx2NB0IeVi1hxe8FvJ53ipCxo9e2qZLd5rdT4CdkTVK85sIIzXEba6M:KQMgxDJ07g8ND35xyILd1qsIIbUi |
MALICIOUS
Loads dropped or rewritten executable
- blackbox.exe (PID: 2596)
- blackbox.exe (PID: 2412)
SUSPICIOUS
Executable content was dropped or overwritten
- blackbox.exe (PID: 2596)
- blackbox.exe (PID: 2412)
Reads CPU info
- blackbox.exe (PID: 2596)
- blackbox.exe (PID: 2412)
Reads the BIOS version
- blackbox.exe (PID: 2596)
- blackbox.exe (PID: 2412)
Creates files in the user directory
- blackbox.exe (PID: 2596)
Reads the machine GUID from the registry
- blackbox.exe (PID: 2596)
- blackbox.exe (PID: 2412)
INFO
Manual execution by user
- blackbox.exe (PID: 2412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (42.6) |
|---|---|---|
| .exe | | | Win16/32 Executable Delphi generic (19.5) |
| .exe | | | Generic Win/DOS Executable (18.9) |
| .exe | | | DOS Executable Generic (18.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:05:03 11:04:06+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 3482624 |
| InitializedDataSize: | 2740736 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x103eaac |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.1.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 0.1.0.0 |
| ProductVersion: | 1.0.0.0 |
| ProgramID: | com.embarcadero.blackbox |
| FileDescription: | blackbox |
| ProductName: | blackbox |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 03-May-2019 09:04:06 |
| Detected languages: |
|
| FileVersion: | 0.1.0.0 |
| ProductVersion: | 1.0.0.0 |
| ProgramID: | com.embarcadero.blackbox |
| FileDescription: | blackbox |
| ProductName: | blackbox |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 14 |
| Time date stamp: | 03-May-2019 09:04:06 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
0x00702000 | 0x00711000 | 0x0002F400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99905 | |
.rsrc | 0x006E8000 | 0x0001A000 | 0x00019400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 6.30495 |
.bb | 0x00E13000 | 0x00231000 | 0x00230600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.98528 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.8622 | 725 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 4.50939 | 9640 | UNKNOWN | English - United States | RT_ICON |
3 | 4.64425 | 4264 | UNKNOWN | English - United States | RT_ICON |
4 | 5.06106 | 1128 | UNKNOWN | English - United States | RT_ICON |
5 | 7.32216 | 308 | UNKNOWN | English - United States | RT_CURSOR |
6 | 7.25555 | 308 | UNKNOWN | English - United States | RT_CURSOR |
7 | 7.25819 | 308 | UNKNOWN | English - United States | RT_CURSOR |
8 | 7.28715 | 308 | UNKNOWN | English - United States | RT_CURSOR |
4065 | 3.15103 | 844 | UNKNOWN | UNKNOWN | RT_STRING |
4066 | 3.34084 | 1524 | UNKNOWN | UNKNOWN | RT_STRING |
Imports
SHFolder.dll |
advapi32.dll |
comctl32.dll |
comdlg32.dll |
gdi32.dll |
kernel32.dll |
msvcrt.dll |
netapi32.dll |
ole32.dll |
oleaut32.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
dbkFCallWrapperAddr | 1 | 0x0037E63C |
__dbk_fcall_wrapper | 2 | 0x0000F688 |
madTraceProcess | 3 | 0x000A3FDC |
TMethodImplementationIntercept | 4 | 0x000CCE1C |
Total processes
43
Monitored processes
3
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2412 | "C:\Users\admin\Desktop\blackbox.exe" | C:\Users\admin\Desktop\blackbox.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: blackbox Exit code: 0 Version: 0.1.0.0 Modules
| |||||||||||||||
| 2596 | "C:\Users\admin\Desktop\blackbox.exe" | C:\Users\admin\Desktop\blackbox.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: blackbox Exit code: 0 Version: 0.1.0.0 Modules
| |||||||||||||||
| 3764 | "C:\Users\admin\Desktop\blackbox.exe" | C:\Users\admin\Desktop\blackbox.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: blackbox Exit code: 3221226540 Version: 0.1.0.0 Modules
| |||||||||||||||
Total events
201
Read events
156
Write events
45
Delete events
0
Modification events
| (PID) Process: | (2596) blackbox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2596) blackbox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2596) blackbox.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\blackbox_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2596) blackbox.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\blackbox_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2596) blackbox.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\blackbox_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2596) blackbox.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\blackbox_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2596) blackbox.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\blackbox_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2596) blackbox.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\blackbox_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2596) blackbox.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\blackbox_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2596) blackbox.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\blackbox_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
8
Suspicious files
0
Text files
7
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2596 | blackbox.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@blackbox[1].txt | — | |
MD5:— | SHA256:— | |||
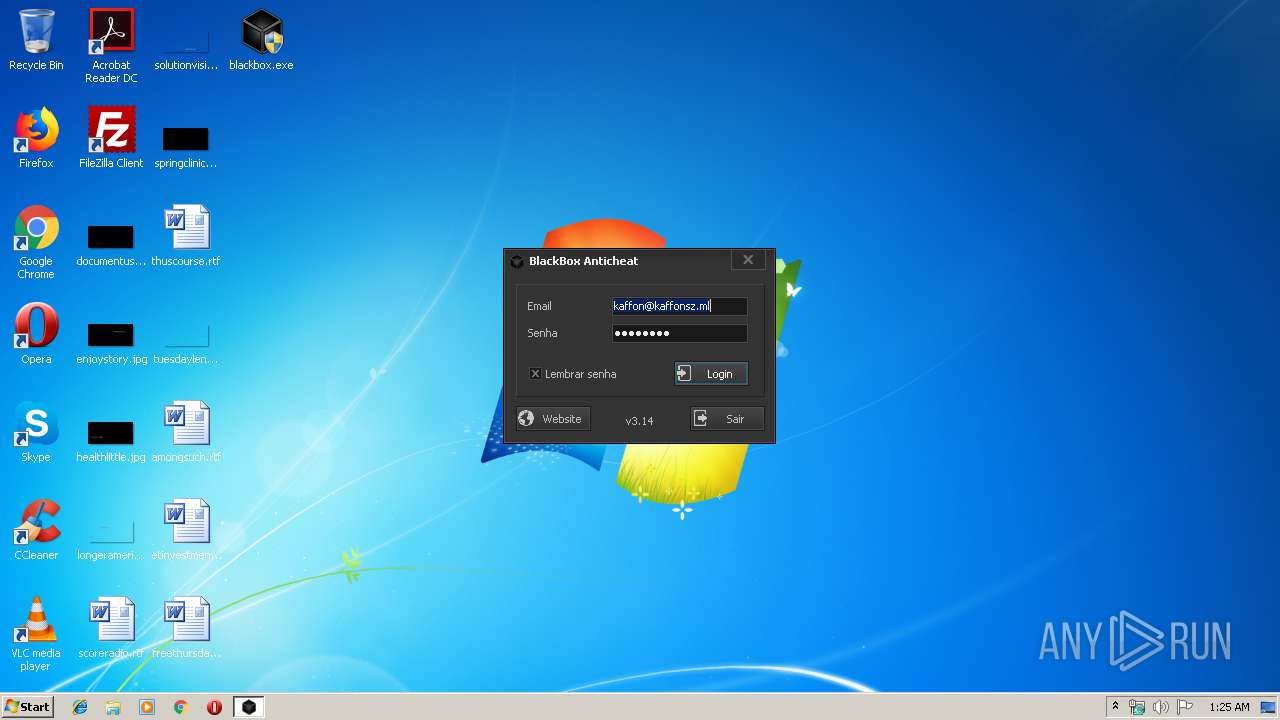
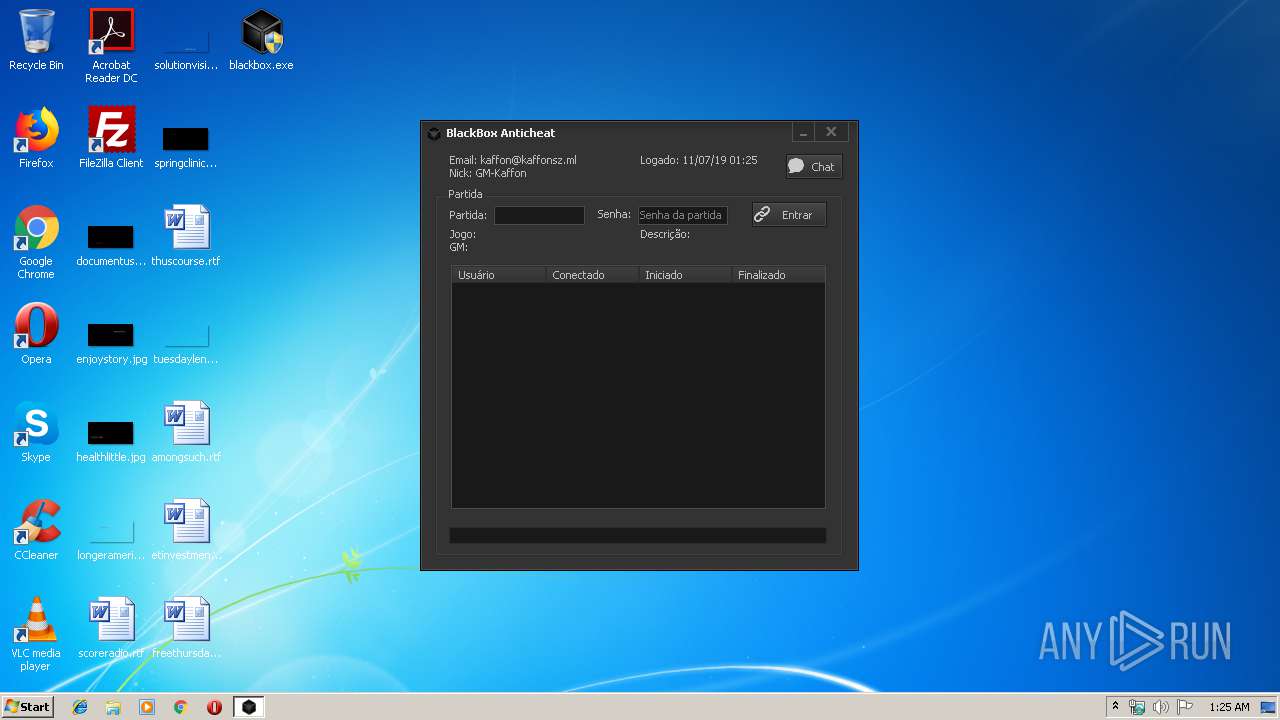
| 2596 | blackbox.exe | C:\Users\admin\AppData\Roaming\BlackBox Anticheat\login.ini | text | |
MD5:— | SHA256:— | |||
| 2412 | blackbox.exe | C:\Users\admin\AppData\Roaming\BlackBox Anticheat\login.ini | text | |
MD5:— | SHA256:— | |||
| 2596 | blackbox.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@blackbox[2].txt | text | |
MD5:— | SHA256:— | |||
| 2596 | blackbox.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\IETldCache\index.dat | dat | |
MD5:D7A950FEFD60DBAA01DF2D85FEFB3862 | SHA256:75D0B1743F61B76A35B1FEDD32378837805DE58D79FA950CB6E8164BFA72073A | |||
| 2412 | blackbox.exe | C:\Users\admin\AppData\Local\Temp\bbossl102q-1435671\ssleay32.dll | executable | |
MD5:284E004B654306F8DB1A63CFF0E73D91 | SHA256:2D11228520402EF49443AADC5D0F02C9544A795A4AFC89FB0434B3B81EBDD28C | |||
| 2412 | blackbox.exe | C:\Users\admin\AppData\Local\Temp\tmpE818.tmp | executable | |
MD5:86FEDF3C7B32B121AA72E171185699D5 | SHA256:E00F727BDFBF07C0AFF400F79B7B509F46FE8FD882154CF029B59FEDFC1BAC7C | |||
| 2596 | blackbox.exe | C:\Users\admin\AppData\Local\Temp\bbossl102q-1394000\ssleay32.dll | executable | |
MD5:284E004B654306F8DB1A63CFF0E73D91 | SHA256:2D11228520402EF49443AADC5D0F02C9544A795A4AFC89FB0434B3B81EBDD28C | |||
| 2412 | blackbox.exe | C:\Users\admin\AppData\Local\Temp\tmpE817.tmp | executable | |
MD5:75848ACD43300F5C5BC6E84192C9D9E3 | SHA256:C1114E4E476EDEEE26F20C17E6405E647415B3DD61A8288A505C164D3CC889BC | |||
| 2596 | blackbox.exe | C:\Users\admin\AppData\Local\Temp\tmp4551.tmp | executable | |
MD5:86FEDF3C7B32B121AA72E171185699D5 | SHA256:E00F727BDFBF07C0AFF400F79B7B509F46FE8FD882154CF029B59FEDFC1BAC7C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
10
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2596 | blackbox.exe | GET | 200 | 188.166.87.218:80 | http://direct.blackbox.ac/update | NL | text | 70 b | unknown |
2412 | blackbox.exe | GET | 200 | 188.166.87.218:80 | http://direct.blackbox.ac/update | NL | text | 70 b | unknown |
2596 | blackbox.exe | POST | 200 | 188.166.87.218:80 | http://direct.blackbox.ac/backend | NL | binary | 131 b | unknown |
2412 | blackbox.exe | POST | 200 | 188.166.87.218:80 | http://direct.blackbox.ac/backend | NL | binary | 131 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2596 | blackbox.exe | 188.166.87.218:80 | direct.blackbox.ac | Digital Ocean, Inc. | NL | unknown |
2596 | blackbox.exe | 104.27.157.50:443 | blackbox.ac | Cloudflare Inc | US | shared |
2596 | blackbox.exe | 52.51.253.140:10000 | data.logentries.com | Amazon.com, Inc. | IE | unknown |
2412 | blackbox.exe | 188.166.87.218:80 | direct.blackbox.ac | Digital Ocean, Inc. | NL | unknown |
2412 | blackbox.exe | 104.27.157.50:443 | blackbox.ac | Cloudflare Inc | US | shared |
2412 | blackbox.exe | 52.51.253.140:10000 | data.logentries.com | Amazon.com, Inc. | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
direct.blackbox.ac |
| unknown |
blackbox.ac |
| whitelisted |
data.logentries.com |
| unknown |