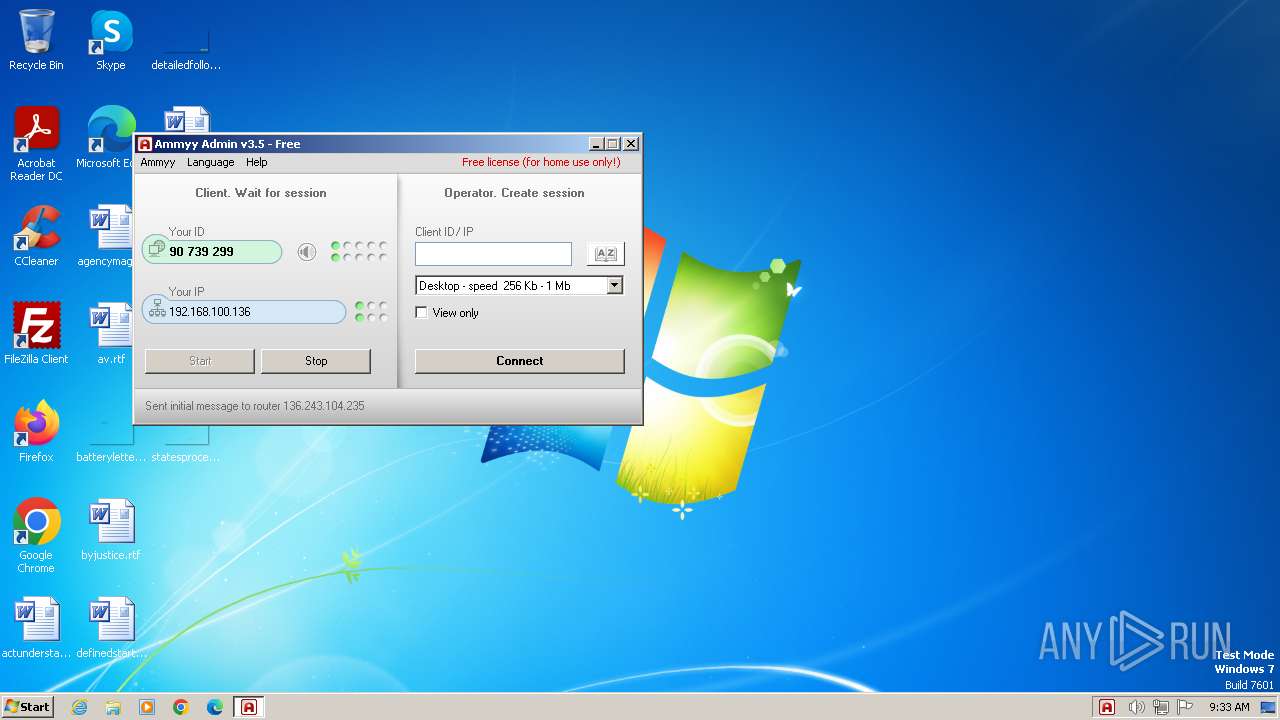
| File name: | AA_v3.5.exe |
| Full analysis: | https://app.any.run/tasks/f6b07ddb-3ed0-451c-b43e-d6c81f222c84 |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2024, 09:33:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F8CD52B70A11A1FB3F29C6F89FF971EC |
| SHA1: | 6A0C46818A6A10C2C5A98A0CCE65FBAF95CAA344 |
| SHA256: | 6F2258383B92BFAF425F49FC7A5901BFA97A334DE49CE015CF65396125C13D20 |
| SSDEEP: | 12288:Z3PYGkUF/lwVZWjgdzWUrcN18HTPDEOxFHw4lrJo5p:Z3ZkUF/+ldzWUrcNSHT7E2xw4lrJo5p |
MALICIOUS
Drops the executable file immediately after the start
- AA_v3.5.exe (PID: 3956)
Deletes the SafeBoot registry key
- AA_v3.5.exe (PID: 3180)
Connects to the CnC server
- AA_v3.5.exe (PID: 2688)
AMMYY has been detected (SURICATA)
- AA_v3.5.exe (PID: 2688)
SUSPICIOUS
Reads the Internet Settings
- AA_v3.5.exe (PID: 3956)
Application launched itself
- AA_v3.5.exe (PID: 1824)
- AA_v3.5.exe (PID: 3956)
Checks for external IP
- AA_v3.5.exe (PID: 2688)
Reads security settings of Internet Explorer
- AA_v3.5.exe (PID: 3956)
Executes as Windows Service
- AA_v3.5.exe (PID: 1824)
INFO
Checks supported languages
- AA_v3.5.exe (PID: 3956)
- AA_v3.5.exe (PID: 1824)
- AA_v3.5.exe (PID: 2688)
Reads the computer name
- AA_v3.5.exe (PID: 3956)
- AA_v3.5.exe (PID: 2688)
- AA_v3.5.exe (PID: 1824)
Checks proxy server information
- AA_v3.5.exe (PID: 3956)
- AA_v3.5.exe (PID: 2688)
Creates files in the program directory
- AA_v3.5.exe (PID: 3956)
Process checks computer location settings
- AA_v3.5.exe (PID: 2688)
Manual execution by a user
- explorer.exe (PID: 2100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:07:02 22:56:03+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 532480 |
| InitializedDataSize: | 253952 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x7c3ae |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.5.0.0 |
| ProductVersionNumber: | 3.5.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Ammyy LLC |
| FileDescription: | Ammyy Admin |
| FileVersion: | 3.5 |
| InternalName: | Ammyy Admin |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| PrivateBuild: | - |
| ProductName: | Ammyy Admin |
| ProductVersion: | 3.5 |
| SpecialBuild: | - |
Total processes
43
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1824 | "C:\Users\admin\AppData\Local\Temp\AA_v3.5.exe" -service -lunch | C:\Users\admin\AppData\Local\Temp\AA_v3.5.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Ammyy LLC Integrity Level: SYSTEM Description: Ammyy Admin Exit code: 0 Version: 3.5 Modules
| |||||||||||||||
| 2100 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2688 | "C:\Users\admin\AppData\Local\Temp\AA_v3.5.exe" -elevated | C:\Users\admin\AppData\Local\Temp\AA_v3.5.exe | AA_v3.5.exe | ||||||||||||
User: SYSTEM Company: Ammyy LLC Integrity Level: SYSTEM Description: Ammyy Admin Version: 3.5 Modules
| |||||||||||||||
| 3180 | "C:\Users\admin\AppData\Local\Temp\AA_v3.5.exe" -elevated | C:\Users\admin\AppData\Local\Temp\AA_v3.5.exe | AA_v3.5.exe | ||||||||||||
User: admin Company: Ammyy LLC Integrity Level: HIGH Description: Ammyy Admin Exit code: 0 Version: 3.5 | |||||||||||||||
| 3956 | "C:\Users\admin\AppData\Local\Temp\AA_v3.5.exe" | C:\Users\admin\AppData\Local\Temp\AA_v3.5.exe | — | explorer.exe | |||||||||||
User: admin Company: Ammyy LLC Integrity Level: MEDIUM Description: Ammyy Admin Version: 3.5 Modules
| |||||||||||||||
Total events
3 090
Read events
3 067
Write events
18
Delete events
5
Modification events
| (PID) Process: | (3956) AA_v3.5.exe | Key: | HKEY_CURRENT_USER\Software\Ammyy\Admin |
| Operation: | write | Name: | hr |
Value: 537D56736631765DC3FAEE5FBB52 | |||
| (PID) Process: | (3956) AA_v3.5.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Ammyy\Admin |
| Operation: | write | Name: | hr |
Value: 537D56736631765DC3FAEE5FBB52 | |||
| (PID) Process: | (3956) AA_v3.5.exe | Key: | HKEY_CURRENT_USER\Software\Ammyy\Admin |
| Operation: | write | Name: | hr3 |
Value: F80289DAD50E2FCE5A6E109F1BB0616048AEEE3B766CD604625A3B8B42667A5A5288C7E6B69FC30A690AD69C966EB5E12BFD944B13BA2EFBEE45DB | |||
| (PID) Process: | (3956) AA_v3.5.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Ammyy\Admin |
| Operation: | write | Name: | hr3 |
Value: F80289DAD50E2FCE5A6E109F1BB0616048AEEE3B766CD604625A3B8B42667A5A5288C7E6B69FC30A690AD69C966EB5E12BFD944B13BA2EFBEE45DB | |||
| (PID) Process: | (3956) AA_v3.5.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3956) AA_v3.5.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3956) AA_v3.5.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3956) AA_v3.5.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3180) AA_v3.5.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SafeBoot\Network\AmmyyAdmin_C6C |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2688) AA_v3.5.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
0
Suspicious files
2
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3956 | AA_v3.5.exe | C:\ProgramData\AMMYY\hr | text | |
MD5:A5A6DCF051EA002E84FF1ECCBE5A86F1 | SHA256:9F1D196F3717B8005841F599B9F040859554DAED22913AAA414D1BE28FD95703 | |||
| 3956 | AA_v3.5.exe | C:\ProgramData\AMMYY\hr3 | binary | |
MD5:F34FA8D99EFB03DCF92121B79A7C0593 | SHA256:8EAA05DC16692DEC2EE06DDED335089657B605153027443F6F93C3D3C907FE5E | |||
| 3956 | AA_v3.5.exe | C:\ProgramData\AMMYY\settings3.bin | binary | |
MD5:714F2508D4227F74B6ADACFEF73815D8 | SHA256:A5579945F23747541C0E80B79E79375D4CA44FEAFCD425EE9BD9302E35312480 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
1
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2688 | AA_v3.5.exe | POST | 200 | 188.42.129.148:80 | http://rl.ammyy.com/ | unknown | text | 138 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
2688 | AA_v3.5.exe | 188.42.129.148:80 | rl.ammyy.com | SERVERS-COM | LU | unknown |
2688 | AA_v3.5.exe | 136.243.104.235:443 | — | Hetzner Online GmbH | DE | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
rl.ammyy.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2688 | AA_v3.5.exe | Potential Corporate Privacy Violation | ET POLICY IP Check (rl. ammyy. com) |
2 ETPRO signatures available at the full report