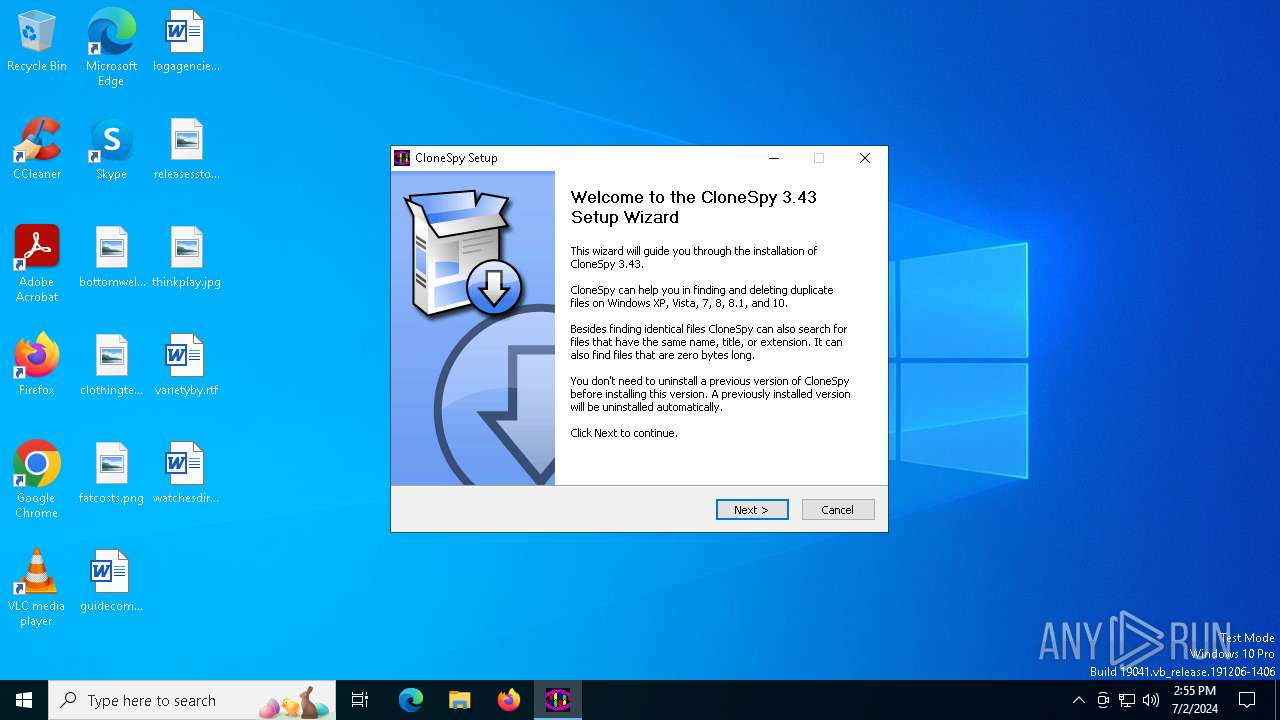
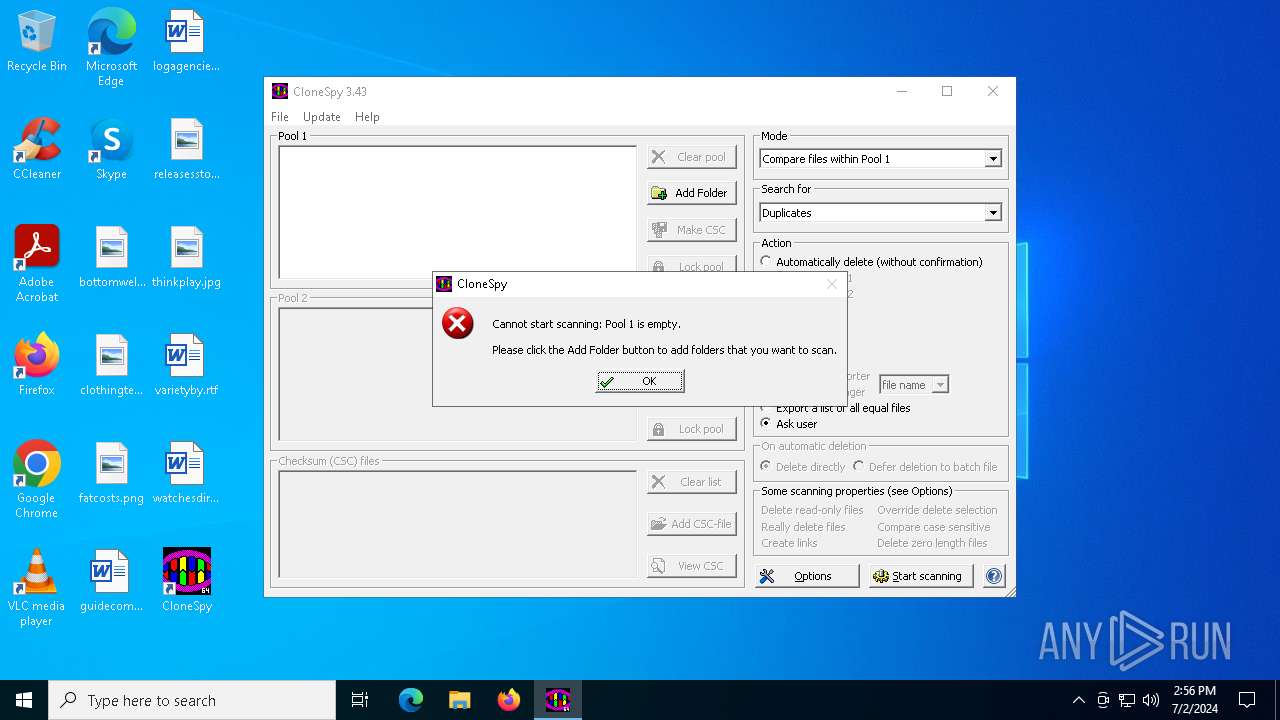
| File name: | cspy343.exe |
| Full analysis: | https://app.any.run/tasks/ce81c162-3857-47cb-a07a-2c2580773c4c |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2024, 14:55:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | F200BC324AE1C57EDE1476AEC22A9089 |
| SHA1: | 7E6E48325A7BDA96245010811E65D93C25D4A3AD |
| SHA256: | 6F1C39F521D7CCDC2C0CFB8A69D456C57B6094E95AFC9D9294D85F35EB116A45 |
| SSDEEP: | 98304:8b7O4WwEuG0ndnJXE3dV7uFKQulFadJ7mVKt9fh4ijLJW85ZO0+VP/upm7ge1xTk:IBJbqGrEG |
MALICIOUS
Drops the executable file immediately after the start
- cspy343.exe (PID: 732)
SUSPICIOUS
Executable content was dropped or overwritten
- cspy343.exe (PID: 732)
Malware-specific behavior (creating "System.dll" in Temp)
- cspy343.exe (PID: 732)
Creates a software uninstall entry
- cspy343.exe (PID: 732)
The process creates files with name similar to system file names
- cspy343.exe (PID: 732)
Reads security settings of Internet Explorer
- cspy343.exe (PID: 732)
- CloneSpy64.exe (PID: 4860)
INFO
Create files in a temporary directory
- cspy343.exe (PID: 732)
Creates files in the program directory
- cspy343.exe (PID: 732)
Checks supported languages
- cspy343.exe (PID: 732)
- CloneSpy64.exe (PID: 4860)
Reads the computer name
- cspy343.exe (PID: 732)
- CloneSpy64.exe (PID: 4860)
Reads Microsoft Office registry keys
- cspy343.exe (PID: 732)
Checks proxy server information
- CloneSpy64.exe (PID: 4860)
Creates files or folders in the user directory
- cspy343.exe (PID: 732)
- CloneSpy64.exe (PID: 4860)
Manual execution by a user
- CloneSpy64.exe (PID: 4860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:15 22:24:32+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25088 |
| InitializedDataSize: | 118784 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x3328 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.4.3.0 |
| ProductVersionNumber: | 3.4.3.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | Duplicate file removal tool |
| CompanyName: | Marcus Kleinehagenbrock |
| FileDescription: | CloneSpy Installer |
| FileVersion: | 3.43 |
| InternalName: | CloneSpy |
| LegalCopyright: | © 2001 - 2019 Marcus Kleinehagenbrock |
| OriginalFileName: | cspy343.exe |
| ProductName: | CloneSpy |
| ProductVersion: | 3.43 |
| WWW: | http://www.clonespy.com |
Total processes
133
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 732 | "C:\Users\admin\AppData\Local\Temp\cspy343.exe" | C:\Users\admin\AppData\Local\Temp\cspy343.exe | explorer.exe | ||||||||||||
User: admin Company: Marcus Kleinehagenbrock Integrity Level: HIGH Description: CloneSpy Installer Exit code: 0 Version: 3.43 Modules
| |||||||||||||||
| 2440 | "C:\Users\admin\AppData\Local\Temp\cspy343.exe" | C:\Users\admin\AppData\Local\Temp\cspy343.exe | — | explorer.exe | |||||||||||
User: admin Company: Marcus Kleinehagenbrock Integrity Level: MEDIUM Description: CloneSpy Installer Exit code: 3221226540 Version: 3.43 Modules
| |||||||||||||||
| 4860 | "C:\Program Files\CloneSpy\CloneSpy64.exe" | C:\Program Files\CloneSpy\CloneSpy64.exe | explorer.exe | ||||||||||||
User: admin Company: Marcus Kleinehagenbrock Integrity Level: MEDIUM Description: CloneSpy Application Version: 3.43 Modules
| |||||||||||||||
Total events
6 877
Read events
6 843
Write events
34
Delete events
0
Modification events
| (PID) Process: | (732) cspy343.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\CloneSpy64.exe |
| Operation: | write | Name: | Path |
Value: C:\Program Files\CloneSpy | |||
| (PID) Process: | (732) cspy343.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CloneSpy |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\CloneSpy\CloneSpy64.exe,0 | |||
| (PID) Process: | (732) cspy343.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CloneSpy |
| Operation: | write | Name: | DisplayName |
Value: CloneSpy 3.43 - 64 bit | |||
| (PID) Process: | (732) cspy343.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CloneSpy |
| Operation: | write | Name: | DisplayVersion |
Value: 3.43 | |||
| (PID) Process: | (732) cspy343.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CloneSpy |
| Operation: | write | Name: | EstimatedSize |
Value: 7520 | |||
| (PID) Process: | (732) cspy343.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CloneSpy |
| Operation: | write | Name: | HelpLink |
Value: http://www.clonespy.com | |||
| (PID) Process: | (732) cspy343.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CloneSpy |
| Operation: | write | Name: | InstallLocation |
Value: {C:\Program Files\CloneSpy} | |||
| (PID) Process: | (732) cspy343.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CloneSpy |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (732) cspy343.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CloneSpy |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
| (PID) Process: | (732) cspy343.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CloneSpy |
| Operation: | write | Name: | Publisher |
Value: The CloneSpy Team | |||
Executable files
6
Suspicious files
9
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 732 | cspy343.exe | C:\Users\admin\AppData\Local\Temp\nsuE06F.tmp | — | |
MD5:— | SHA256:— | |||
| 732 | cspy343.exe | C:\Users\admin\AppData\Local\Temp\nsr2598.tmp | text | |
MD5:9904D3F19A1668FD7536A3043681EEEE | SHA256:8E731CAB878B4CEA6D4AAF9F1432B52595A812C3FF52DF2C153D04189F2A5C63 | |||
| 732 | cspy343.exe | C:\Program Files\CloneSpy\CloneSpy64.exe | executable | |
MD5:D05BB94F0F09A0A90CC0F9E40D87E97F | SHA256:CA30738F63F1FAA851DEB020A39689678A8DC9497366DA95FB469715C5CE7E0C | |||
| 732 | cspy343.exe | C:\Users\admin\Desktop\CloneSpy.lnk | binary | |
MD5:AEB1E6559E657CC031165D45EBEA3298 | SHA256:EB16976A0BFE41E68E08577DC538D92E174609CB2702F03EEA61B5724812BDB9 | |||
| 732 | cspy343.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\CloneSpy\CloneSpy.lnk | binary | |
MD5:0EBC764B133D8084060C4234BEDF54C5 | SHA256:1C923F6D67CC1FD16B7AA26CE06187F7DBF90B26F2B164050EF609F4F3520E65 | |||
| 732 | cspy343.exe | C:\Program Files\CloneSpy\CSUninstall64.exe | executable | |
MD5:54DB18E00D12CFBA4A0A2C73FC2F9638 | SHA256:48C236404F978821A35A0F56A1A18E27523003BE1AD954115EBB4A66F8901D17 | |||
| 732 | cspy343.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\CloneSpy\Help.lnk | binary | |
MD5:3BE31CA7E00B09AD08DC0679012EA66E | SHA256:9D31FEC28F30C9884215AEAA1B5F8A44270DC66E162C3FF222E1247BA1F24F35 | |||
| 732 | cspy343.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\CloneSpy\Readme.lnk | binary | |
MD5:C4B2DAC9D4BB88EDCBDCACF60CF6060F | SHA256:923C97682B7DEB21CE43D4FC5B03355A43B362D6A7F68BA9BBB98D6225E71C17 | |||
| 732 | cspy343.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\CloneSpy\Uninstall.lnk | binary | |
MD5:7D00F4D446B388CA4AD8A11498963D53 | SHA256:774C4CF1993DDF35B232DC32381A218B63257922511E80506B2E4D3444108222 | |||
| 732 | cspy343.exe | C:\Users\admin\AppData\Local\Temp\nsuE070.tmp\modern-header.bmp | image | |
MD5:732BEDF95585DFC1023573F0FA4F6E60 | SHA256:670ABB7576D8A890A7D4B480FA2F26FABACD873E11DA23C5D4D55720E0791DC6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
55
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4276 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
4276 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
5968 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
4860 | CloneSpy64.exe | GET | 200 | 85.13.129.201:80 | http://www.clonespy.info/iupdate/update_eng.txt | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
3624 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4656 | SearchApp.exe | 92.123.104.34:443 | www.bing.com | Akamai International B.V. | DE | unknown |
1544 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
1544 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4656 | SearchApp.exe | 13.107.21.200:443 | r.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1060 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
3040 | OfficeClickToRun.exe | 20.189.173.26:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3040 | OfficeClickToRun.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msftauth .net) |
Process | Message |
|---|---|
cspy343.exe | ExecShellAsUser: DLL_PROCESS_ATTACH |
cspy343.exe | ExecShellAsUser: got desktop |
cspy343.exe | ExecShellAsUser: elevated process detected |
cspy343.exe | ExecShellAsUser: NSPIM_UNLOAD wait... |
cspy343.exe | ExecShellAsUser: thread finished |
cspy343.exe | ExecShellAsUser: NSPIM_UNLOAD |
cspy343.exe | ExecShellAsUser: DLL_PROCESS_DETACH |