| File name: | BSOD.bat |
| Full analysis: | https://app.any.run/tasks/7d6732a6-e725-4c0a-ba6e-8fe0767e430b |
| Verdict: | Malicious activity |
| Analysis date: | August 02, 2025, 02:33:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text |
| MD5: | 8ECF12DDF752A339440CFC46A49F16CD |
| SHA1: | 15A79DC05270705D6462C524CFB65326DF702CCF |
| SHA256: | 6F1123FB13CA072836E8BB67D2B6E2882EF7FAA376143E36AF41D6513206BC69 |
| SSDEEP: | 3:mKDDUFcTwi9ufyM1K/RFofD6tRQpohLQ0+jnNCG85JSYsdL0in:hzTN9uH1MUmt2psQ0aQ/cYKLJn |
MALICIOUS
Create files in the Startup directory
- cmd.exe (PID: 3576)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 3576)
Probably uses Microsoft diagnostics tool to execute malicious payload
- rundll32.exe (PID: 4172)
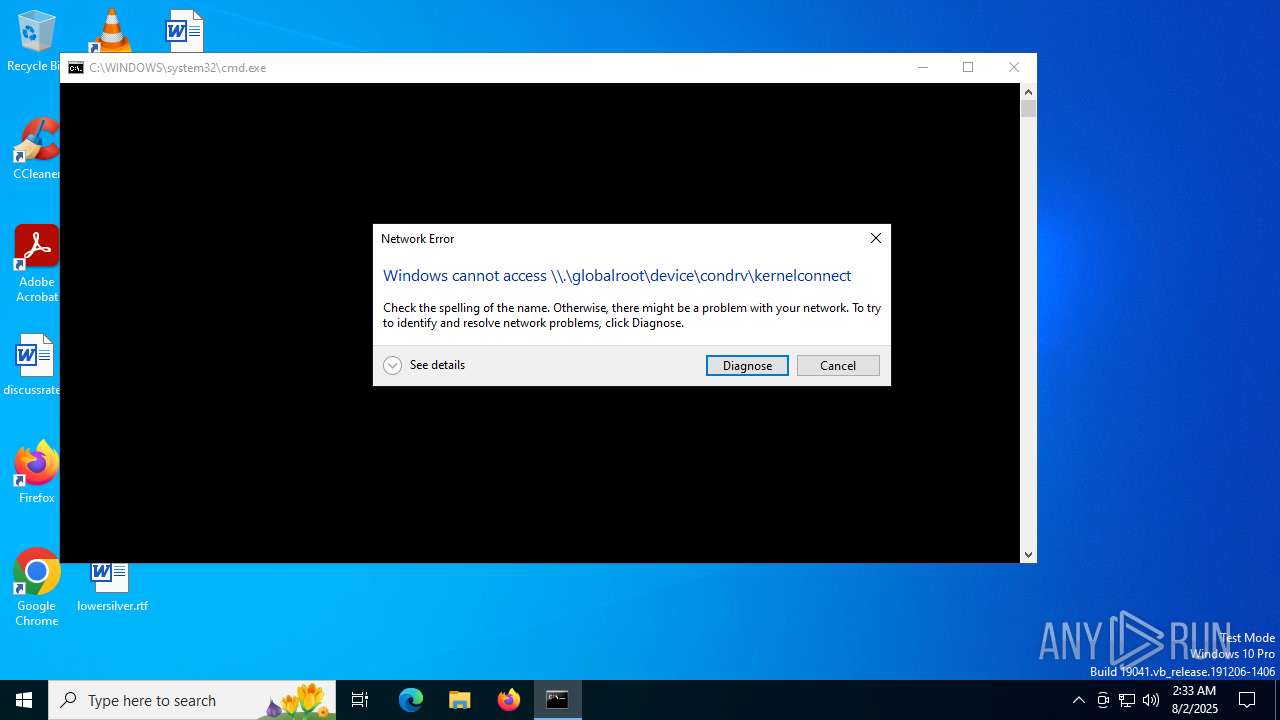
Uses NETSH.EXE to trace traffic
- sdiagnhost.exe (PID: 4072)
Checks a user's role membership (POWERSHELL)
- sdiagnhost.exe (PID: 4072)
INFO
Launching a file from the Startup directory
- cmd.exe (PID: 3576)
The sample compiled with english language support
- msdt.exe (PID: 3504)
Reads security settings of Internet Explorer
- msdt.exe (PID: 3504)
- sdiagnhost.exe (PID: 4072)
Create files in a temporary directory
- sdiagnhost.exe (PID: 4072)
- msdt.exe (PID: 3504)
Reads the software policy settings
- msdt.exe (PID: 3504)
Gets data length (POWERSHELL)
- sdiagnhost.exe (PID: 4072)
Creates files or folders in the user directory
- msdt.exe (PID: 3504)
Creates files in the program directory
- msdt.exe (PID: 3504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
142
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3504 | -skip TRUE -path "C:\WINDOWS\diagnostics\system\networking" -af "C:\Users\admin\AppData\Local\Temp\NDFF567.tmp" -ep "NetworkDiagnosticsSharing" | C:\Windows\System32\msdt.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3576 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\BSOD.bat" " | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3844 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4072 | C:\WINDOWS\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4172 | "C:\WINDOWS\system32\rundll32.exe" ndfapi.dll,NdfRunDllDiagnoseWithAnswerFile NetworkDiagnosticsSharing C:\Users\admin\AppData\Local\Temp\NDFF567.tmp | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5460 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6684 | "C:\WINDOWS\system32\netsh.exe" trace diagnose Scenario=NetworkSnapshot Mode=NetTroubleshooter | C:\Windows\System32\netsh.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 142
Read events
7 142
Write events
0
Delete events
0
Modification events
Executable files
3
Suspicious files
14
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3504 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_1e82808e-cdd2-4066-8520-4c4aba3e0381\DiagPackage.dll | executable | |
MD5:1203827613D81E3B3E1CDA9EF405BCE3 | SHA256:5B855529D414ECE27A6B31280BCEB568BBE0F97D0A326C43B9573EE919AC932E | |||
| 3504 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_1e82808e-cdd2-4066-8520-4c4aba3e0381\InteractiveRes.ps1 | text | |
MD5:25B8543DBF571F040118423BC3C7A75E | SHA256:D78E6291D6F27AC6FEBDCF0A4D5A34521E7F033AF8875E026DF21BA7513AB64A | |||
| 3576 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\bsod.bat | text | |
MD5:8ECF12DDF752A339440CFC46A49F16CD | SHA256:6F1123FB13CA072836E8BB67D2B6E2882EF7FAA376143E36AF41D6513206BC69 | |||
| 3504 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_1e82808e-cdd2-4066-8520-4c4aba3e0381\NetworkDiagnosticsResolve.ps1 | text | |
MD5:D213491A2D74B38A9535D616B9161217 | SHA256:4662C3C94E0340A243C2A39CA8A88FD9F65C74FB197644A11D4FFCAE6B191211 | |||
| 3504 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_1e82808e-cdd2-4066-8520-4c4aba3e0381\DiagPackage.diagpkg | xml | |
MD5:0606098A37089BDC9D644DEE1CC1CD78 | SHA256:284A7A8525B1777BDBC194FA38D28CD9EE91C2CBC7856F5968E79667C6B62A9D | |||
| 3504 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_1e82808e-cdd2-4066-8520-4c4aba3e0381\NetworkDiagnosticSnapIn.dll | executable | |
MD5:1E0DC9D0AC324AABC64E7D3FA479C1A1 | SHA256:61406D54859D92DCC8A34F929444D2A3F021EC789C4D9BDAB84E256C8AD042C1 | |||
| 3504 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_1e82808e-cdd2-4066-8520-4c4aba3e0381\HTInteractiveRes.ps1 | text | |
MD5:C25ED2111C6EE9299E6D9BF51012F2F5 | SHA256:8E326EE0475208D4C943D885035058FAD7146BBA02B66305F7C9F31F6A57E81B | |||
| 3504 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_1e82808e-cdd2-4066-8520-4c4aba3e0381\StartDPSService.ps1 | text | |
MD5:A660422059D953C6D681B53A6977100E | SHA256:D19677234127C38A52AEC23686775A8EB3F4E3A406F4A11804D97602D6C31813 | |||
| 3504 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_1e82808e-cdd2-4066-8520-4c4aba3e0381\UtilityFunctions.ps1 | text | |
MD5:C912FAA190464CE7DEC867464C35A8DC | SHA256:3891846307AA9E83BCA66B13198455AF72AF45BF721A2FBD41840D47E2A91201 | |||
| 3504 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_1e82808e-cdd2-4066-8520-4c4aba3e0381\result\results.xsl | xml | |
MD5:310E1DA2344BA6CA96666FB639840EA9 | SHA256:67401342192BABC27E62D4C1E0940409CC3F2BD28F77399E71D245EAE8D3F63C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
17
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.55.110.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1380 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7124 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 20.72.205.209:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1268 | svchost.exe | 23.55.110.211:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1380 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1380 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |