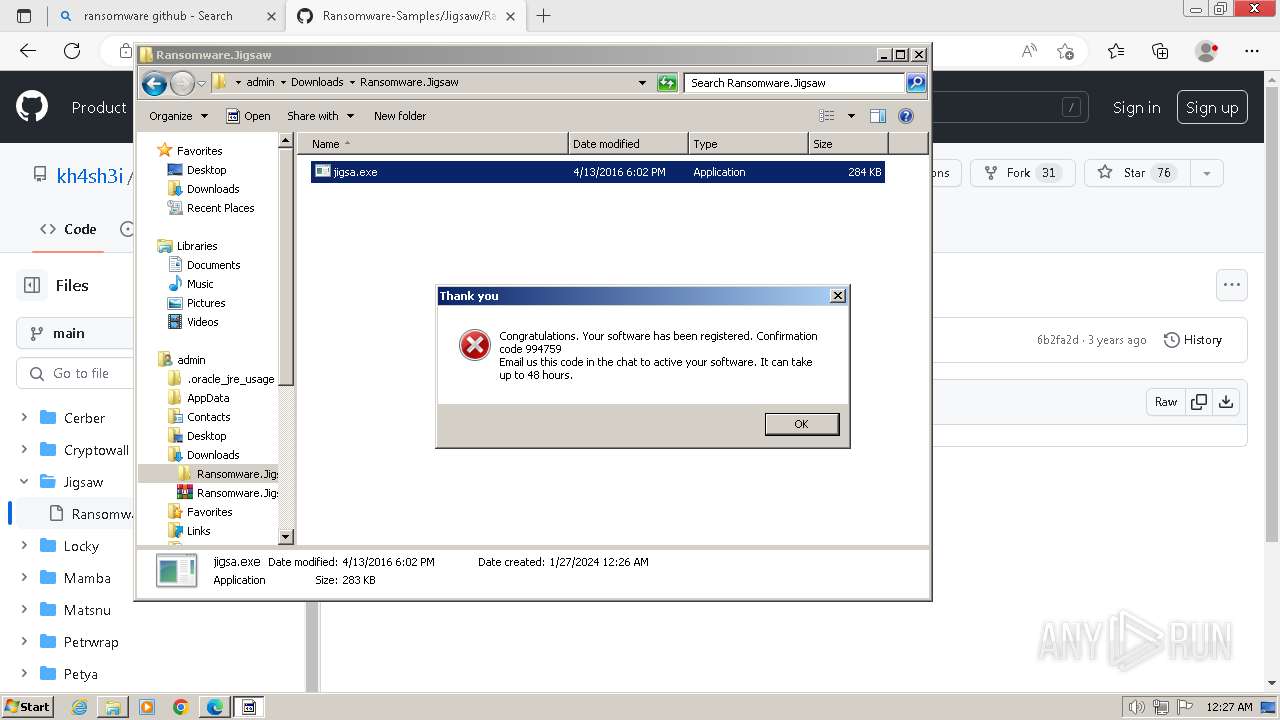
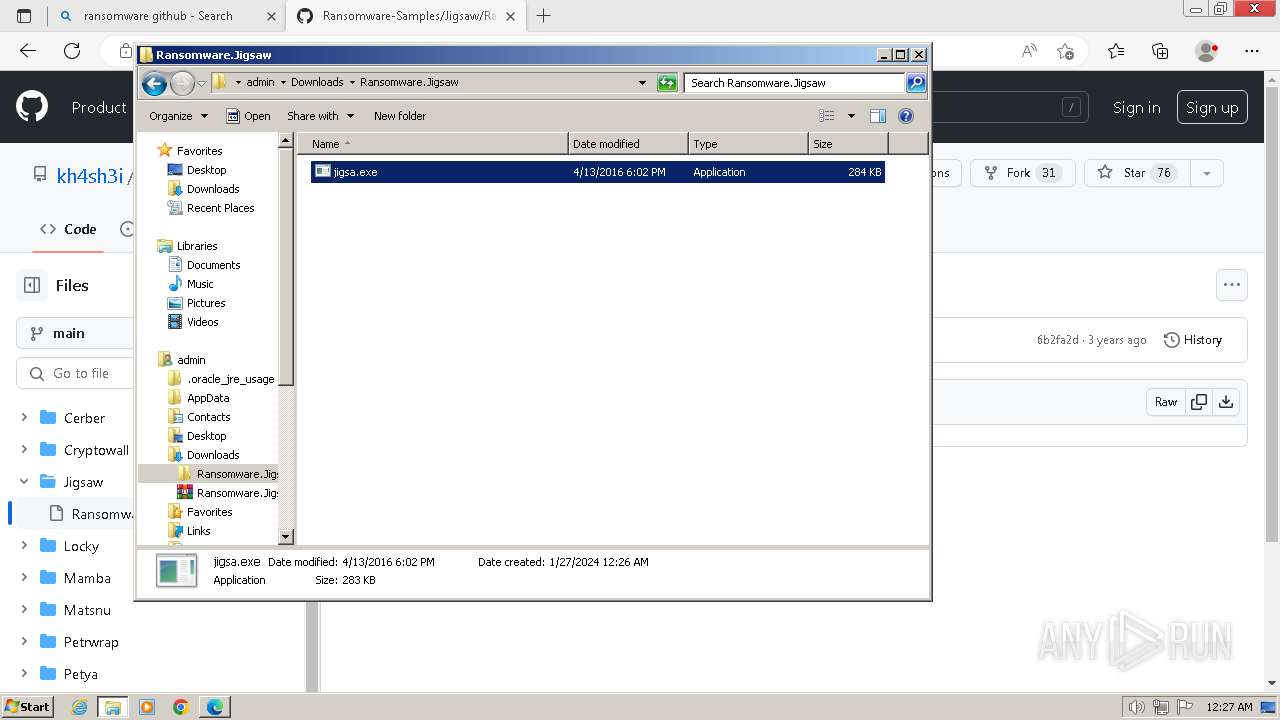
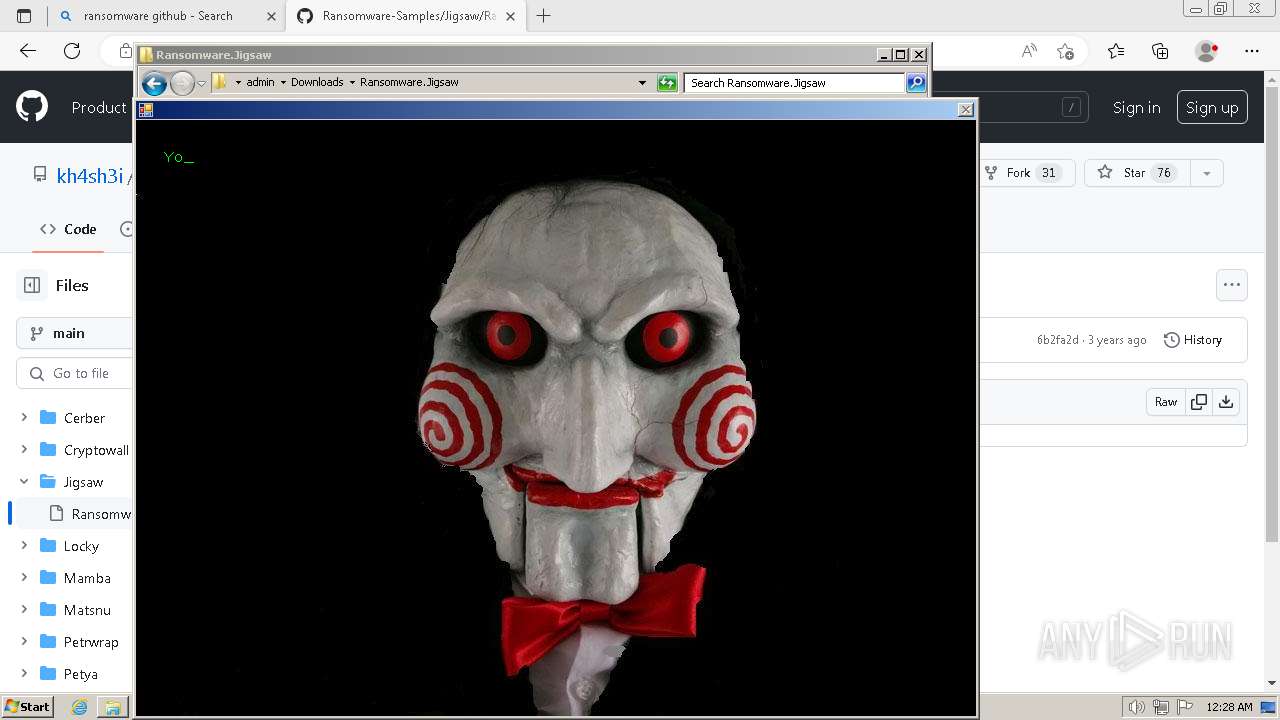
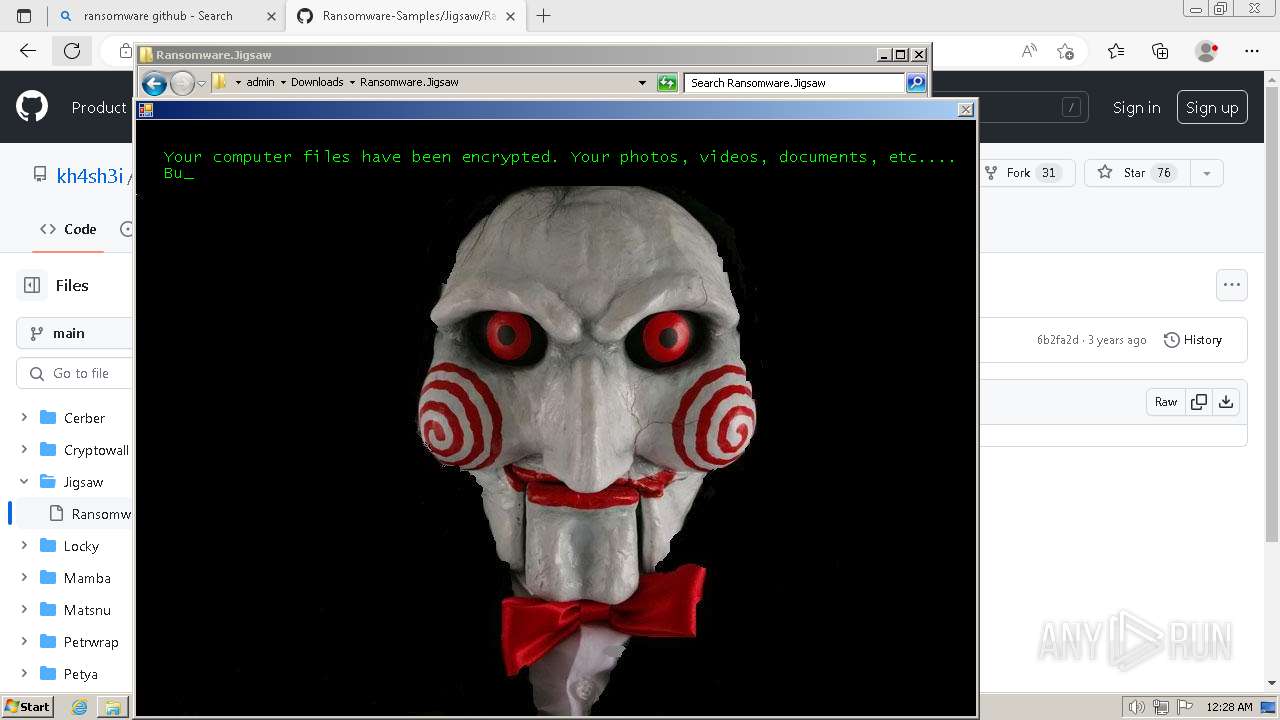
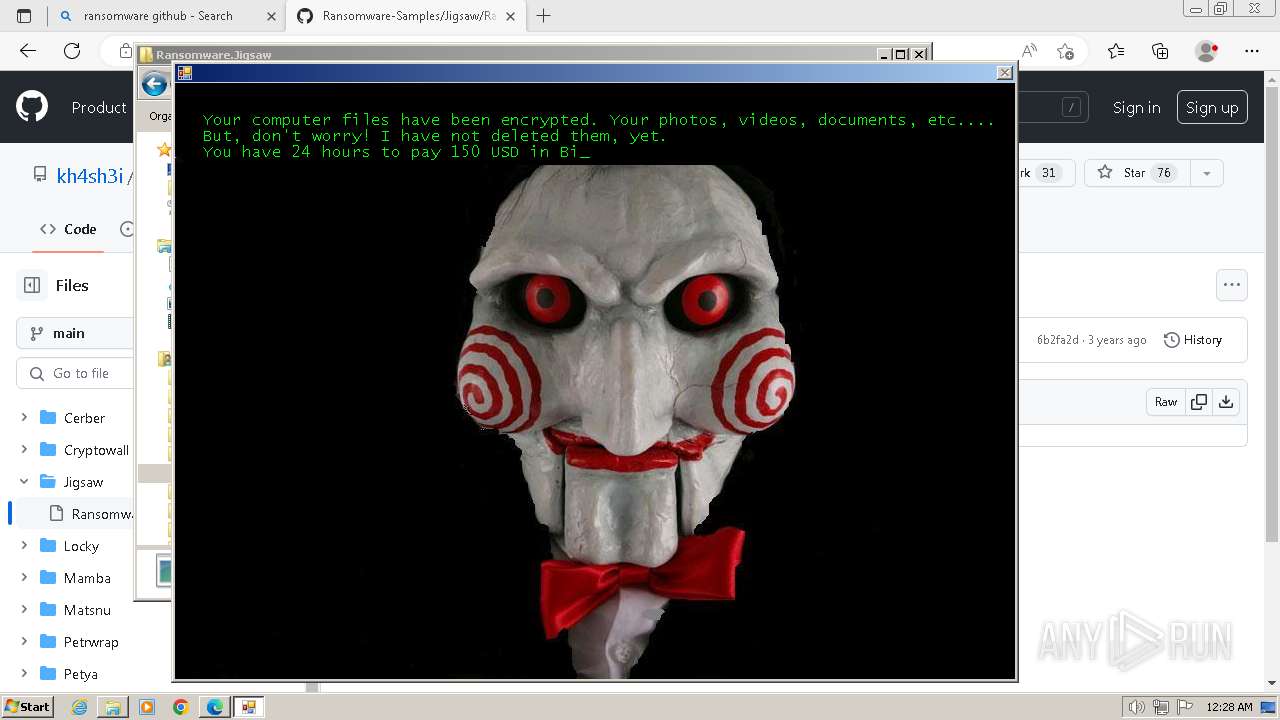
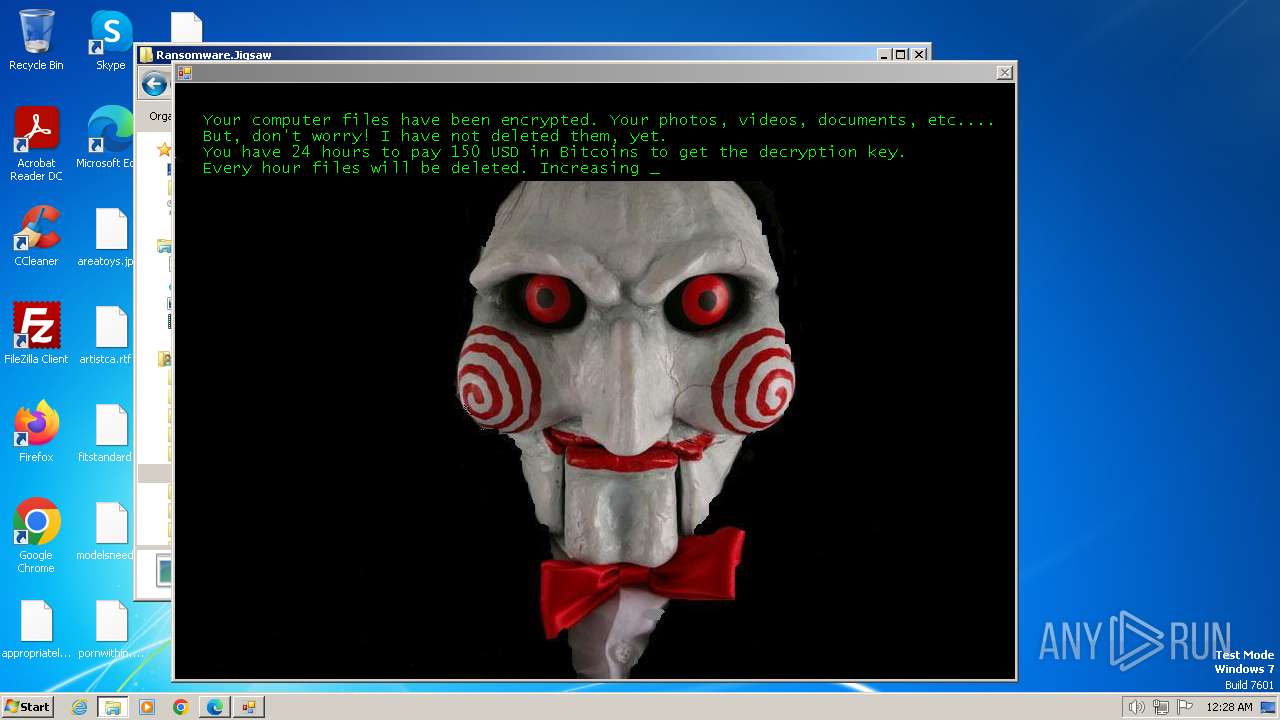
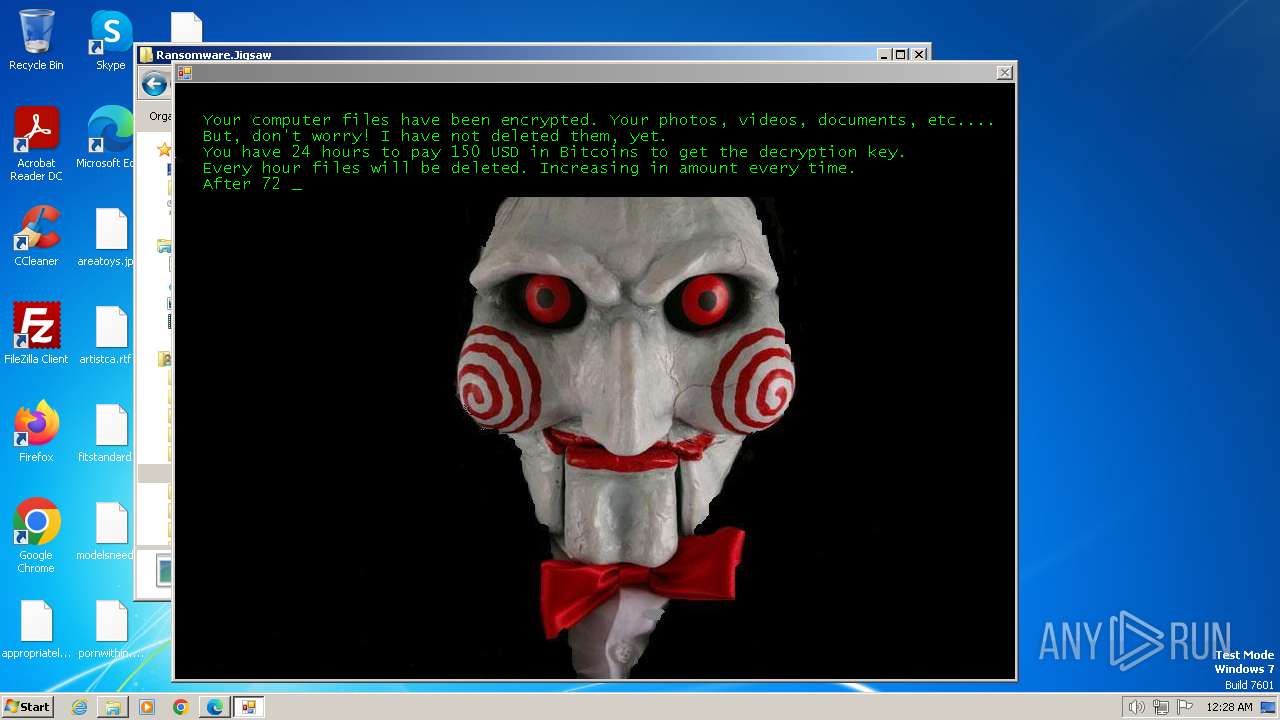
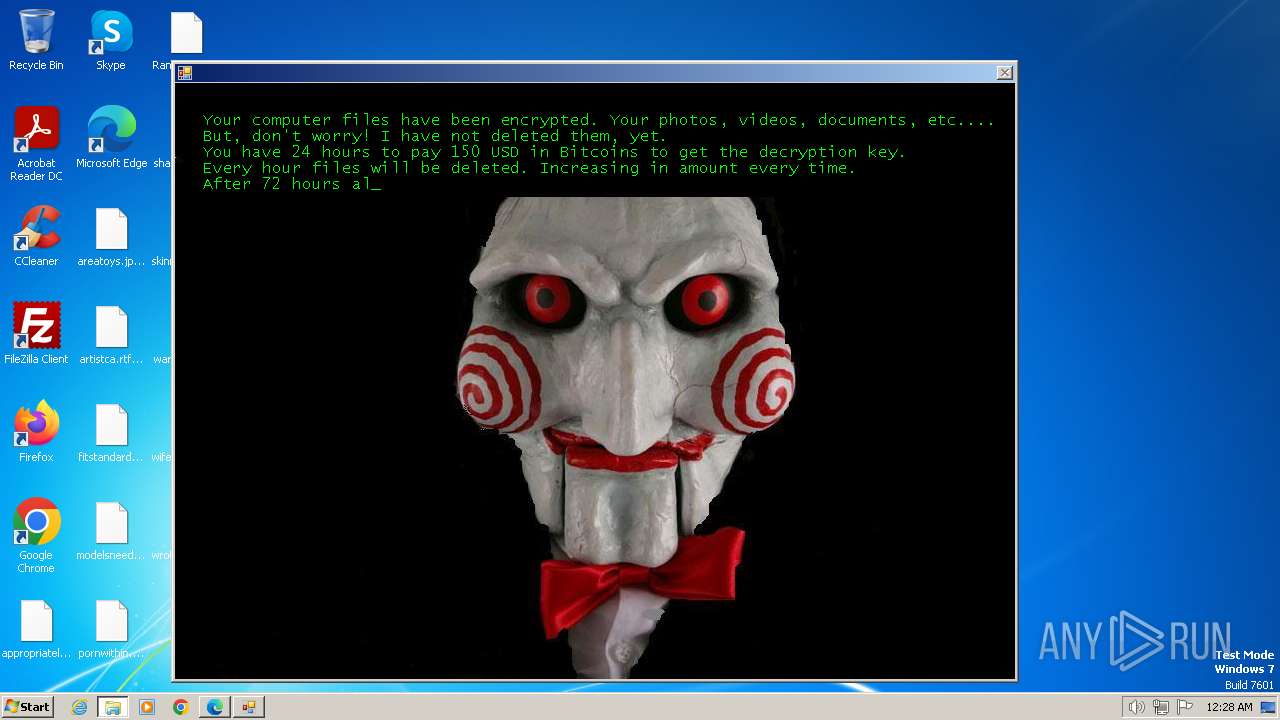
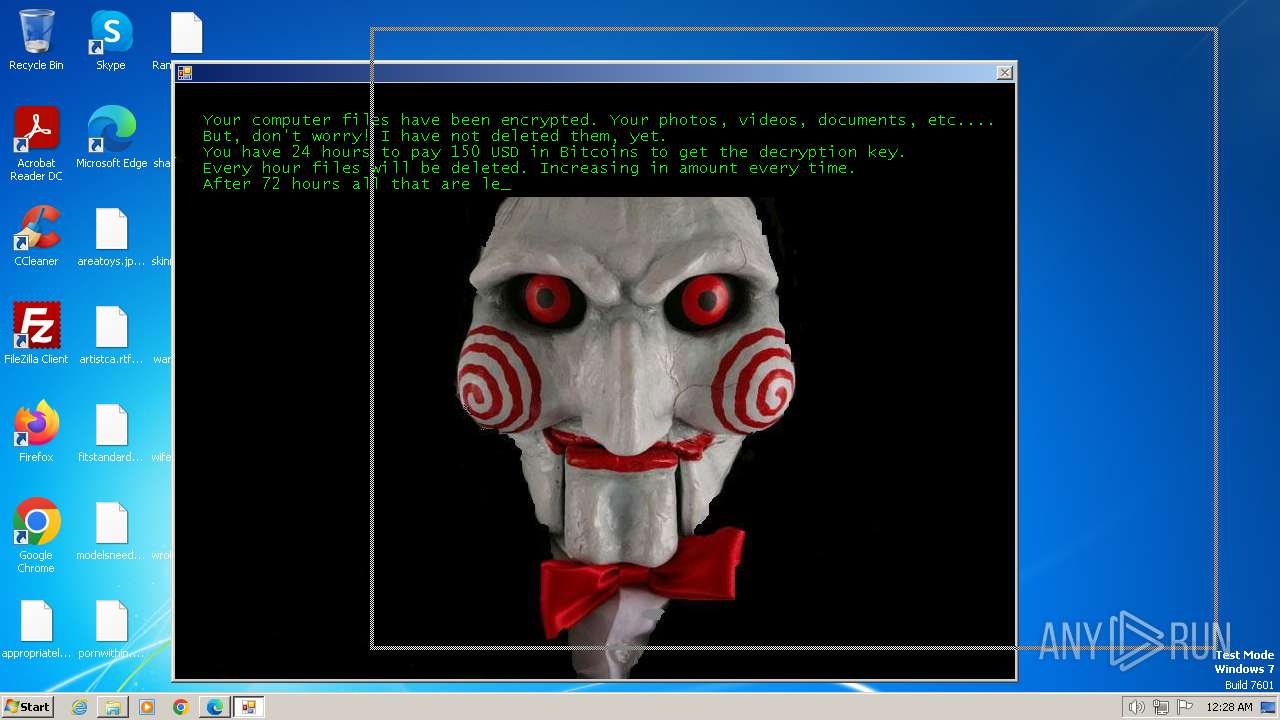
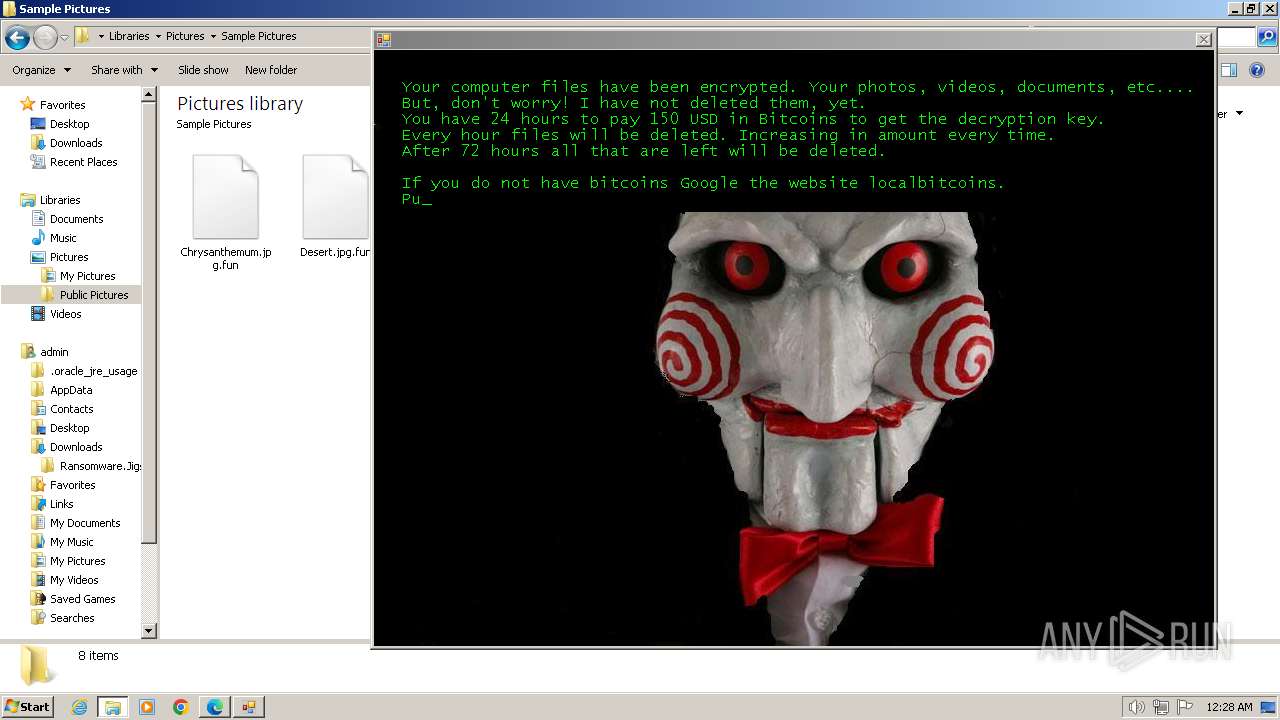
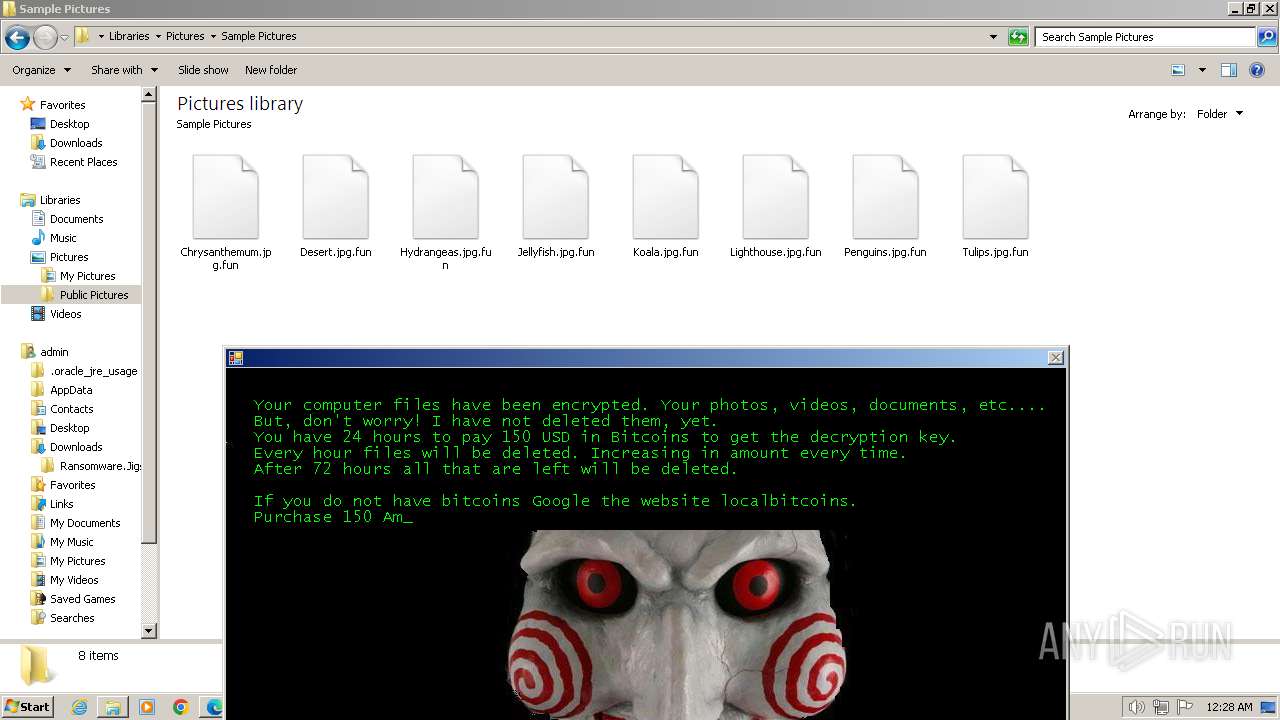
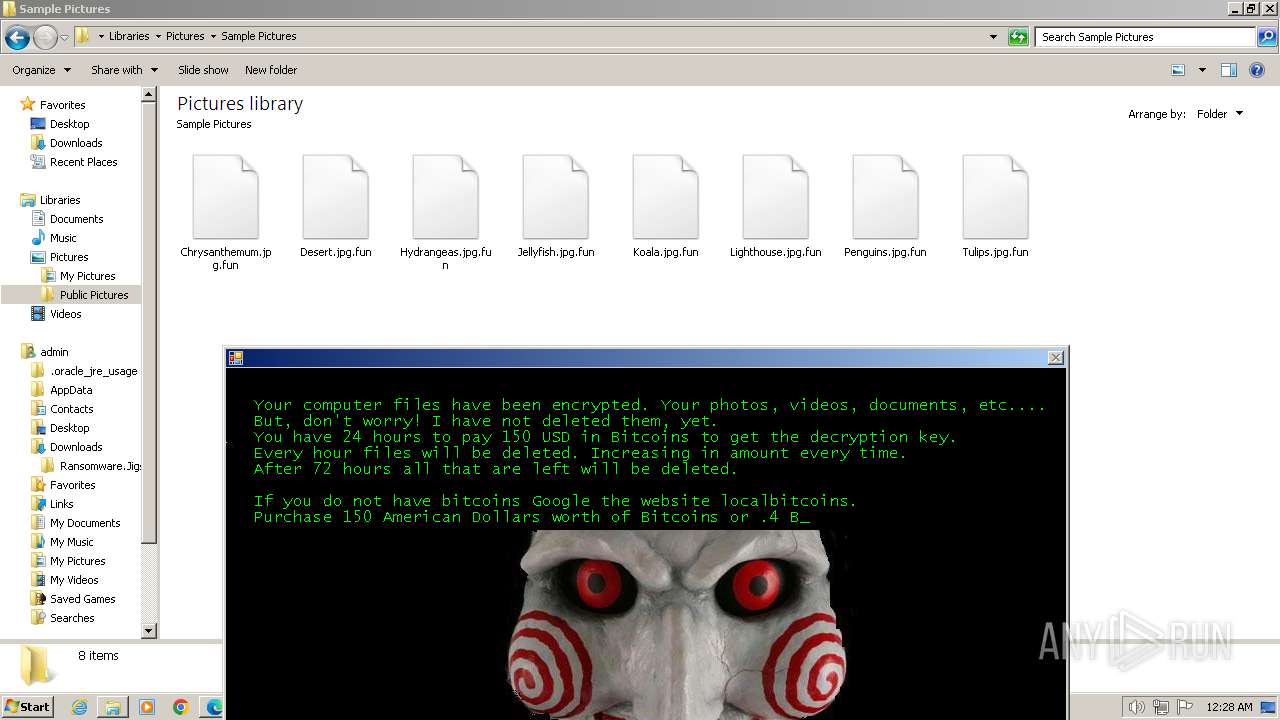
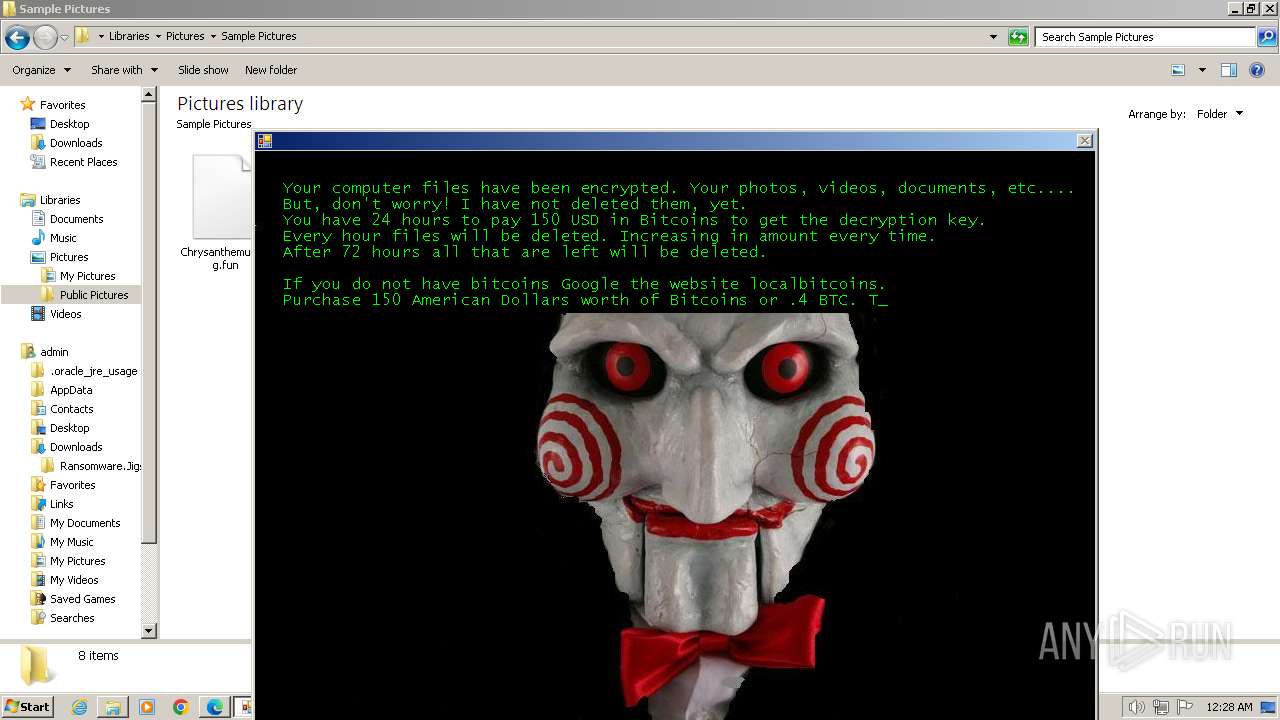
| download: | /kh4sh3i/Ransomware-Samples/blob/main/Jigsaw/Ransomware.Jigsaw.zip |
| Full analysis: | https://app.any.run/tasks/dd1bcdad-d8ac-4afe-a5c1-887cf0bf4367 |
| Verdict: | Malicious activity |
| Analysis date: | January 27, 2024, 00:23:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/json |
| File info: | JSON data |
| MD5: | E5465A34C8FDB3E63F7617C6B209B69E |
| SHA1: | B051F966A26D0A76E9CC92FEC76A2CEB0B44D5F8 |
| SHA256: | 6EE59E613C88EF4A27F207A232C272E092CEDBEBF52B013D56845EC13ABEBC01 |
| SSDEEP: | 96:WG9dfPVtXrRCkb11B5VbltZLbkrkSDOSDMwTh9uH2xJ1vHHMu+t4V:WG9dfPVJVCkb11B5VbltZLbkQSLMc9uI |
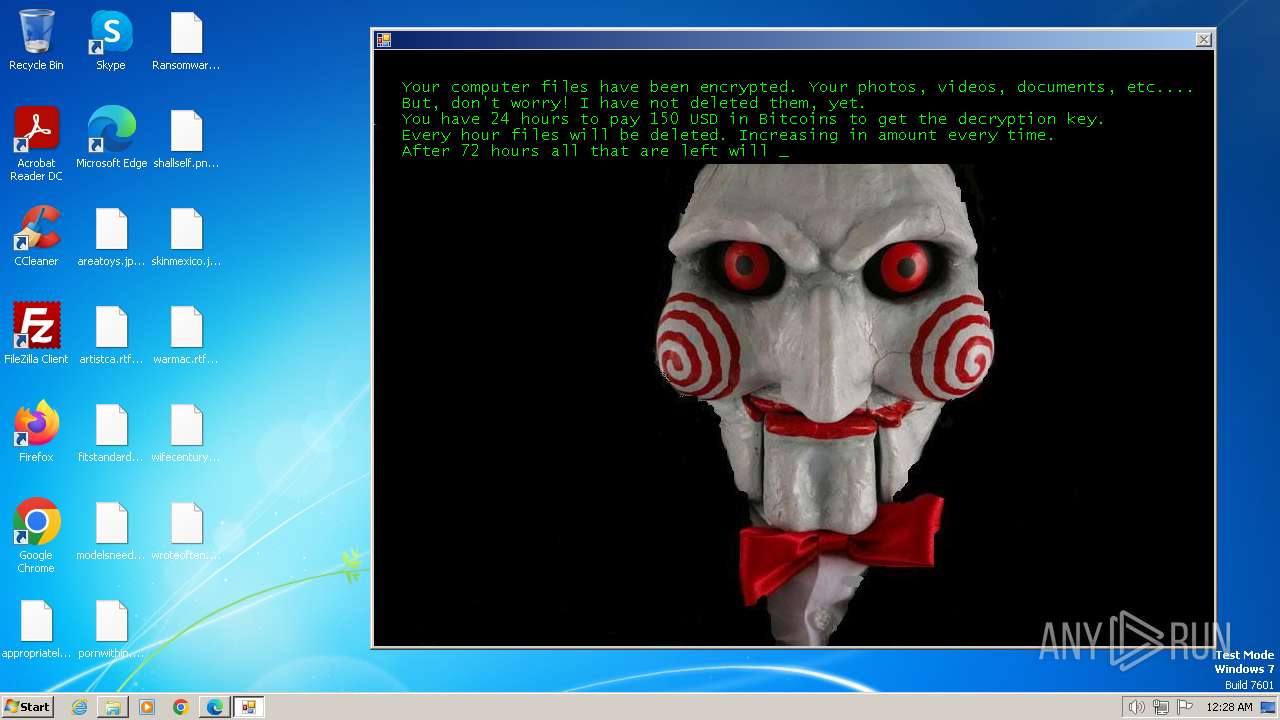
MALICIOUS
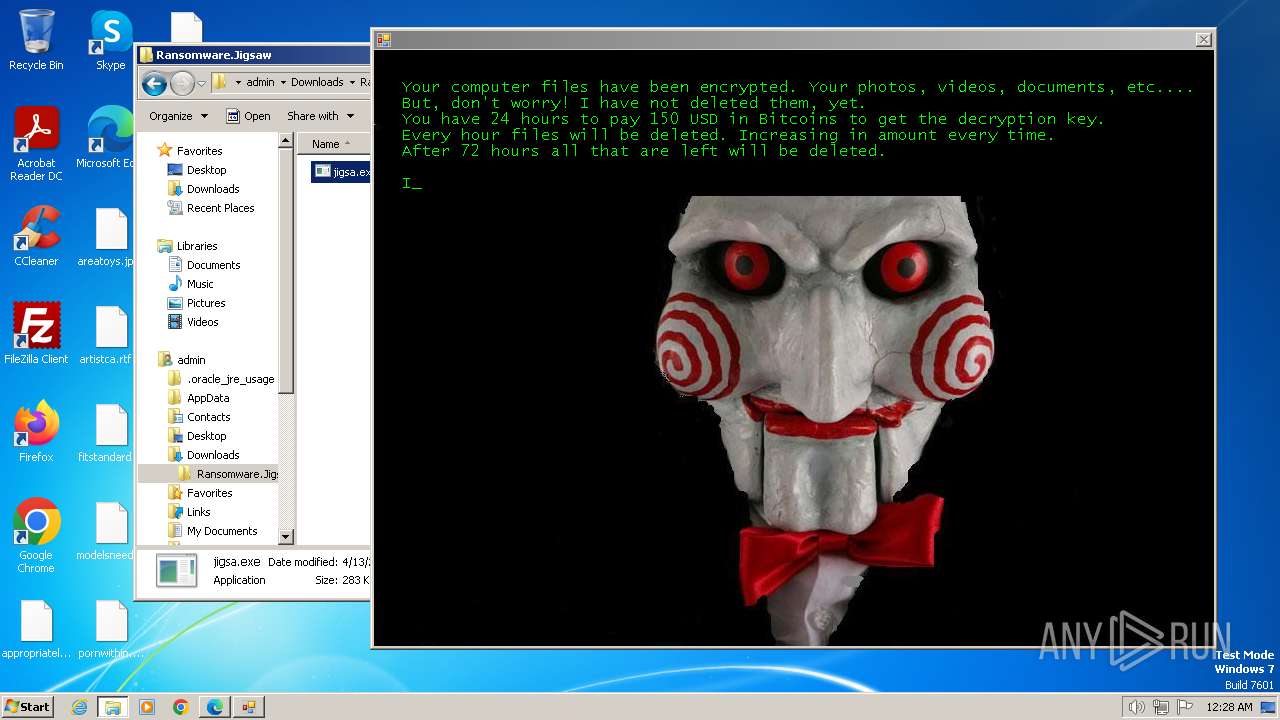
Drops the executable file immediately after the start
- jigsa.exe (PID: 1848)
- drpbx.exe (PID: 1776)
Changes the autorun value in the registry
- jigsa.exe (PID: 2480)
- jigsa.exe (PID: 2312)
Modifies files in the Chrome extension folder
- drpbx.exe (PID: 1776)
Steals credentials from Web Browsers
- drpbx.exe (PID: 1776)
Actions looks like stealing of personal data
- drpbx.exe (PID: 1776)
SUSPICIOUS
Starts itself from another location
- jigsa.exe (PID: 1848)
Executable content was dropped or overwritten
- jigsa.exe (PID: 1848)
Reads the Internet Settings
- jigsa.exe (PID: 1848)
INFO
Manual execution by a user
- WinRAR.exe (PID: 452)
- msedge.exe (PID: 2672)
- jigsa.exe (PID: 1848)
- WinRAR.exe (PID: 3368)
- WinRAR.exe (PID: 2316)
- WinRAR.exe (PID: 2484)
- jigsa.exe (PID: 2480)
- jigsa.exe (PID: 2312)
Application launched itself
- msedge.exe (PID: 2672)
Checks supported languages
- jigsa.exe (PID: 1848)
- jigsa.exe (PID: 2480)
- drpbx.exe (PID: 1776)
- jigsa.exe (PID: 2312)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3368)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3368)
Reads the computer name
- jigsa.exe (PID: 1848)
- jigsa.exe (PID: 2480)
- jigsa.exe (PID: 2312)
Reads the machine GUID from the registry
- jigsa.exe (PID: 1848)
- jigsa.exe (PID: 2480)
- jigsa.exe (PID: 2312)
- drpbx.exe (PID: 1776)
The process uses the downloaded file
- msedge.exe (PID: 2020)
- WinRAR.exe (PID: 3368)
Creates files or folders in the user directory
- jigsa.exe (PID: 1848)
- drpbx.exe (PID: 1776)
Creates files in the program directory
- drpbx.exe (PID: 1776)
Create files in a temporary directory
- drpbx.exe (PID: 1776)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
JSON
| PayloadAllShortcutsEnabled: | - |
|---|---|
| PayloadBlobCsv: | null |
| PayloadBlobCsvError: | null |
| PayloadBlobDependabotInfoConfigFilePath: | null |
| PayloadBlobDependabotInfoConfigurationNoticeDismissed: | null |
| PayloadBlobDependabotInfoCurrentUserCanAdminRepo: | - |
| PayloadBlobDependabotInfoDismissConfigurationNoticePath: | /settings/dismiss-notice/dependabot_configuration_notice |
| PayloadBlobDependabotInfoNetworkDependabotPath: | /kh4sh3i/Ransomware-Samples/network/updates |
| PayloadBlobDependabotInfoRepoAlertsPath: | /kh4sh3i/Ransomware-Samples/security/dependabot |
| PayloadBlobDependabotInfoRepoOwnerIsOrg: | - |
| PayloadBlobDependabotInfoRepoSecurityAndAnalysisPath: | /kh4sh3i/Ransomware-Samples/settings/security_analysis |
| PayloadBlobDependabotInfoShowConfigurationBanner: | - |
| PayloadBlobDiscussionTemplate: | null |
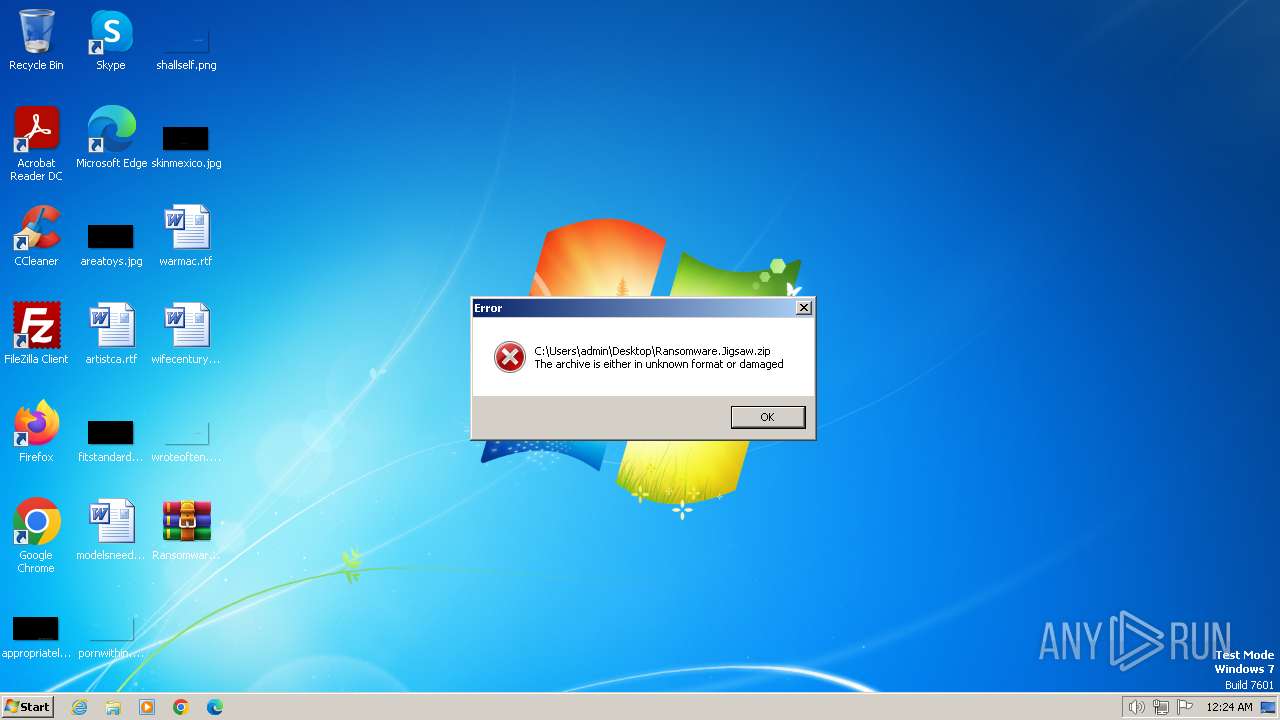
| PayloadBlobDisplayName: | Ransomware.Jigsaw.zip |
| PayloadBlobDisplayUrl: | https://github.com/kh4sh3i/Ransomware-Samples/blob/main/Jigsaw/Ransomware.Jigsaw.zip?raw=true |
| PayloadBlobHeaderInfoBlobSize: | 240 KB |
| PayloadBlobHeaderInfoDeleteInfoDeleteTooltip: | You must be signed in to make or propose changes |
| PayloadBlobHeaderInfoEditInfoEditTooltip: | You must be signed in to make or propose changes |
| PayloadBlobHeaderInfoGhDesktopPath: | https://desktop.github.com |
| PayloadBlobHeaderInfoGitLfsPath: | null |
| PayloadBlobHeaderInfoIsCSV: | - |
| PayloadBlobHeaderInfoIsRichtext: | - |
| PayloadBlobHeaderInfoLineInfoTruncatedLoc: | null |
| PayloadBlobHeaderInfoLineInfoTruncatedSloc: | null |
| PayloadBlobHeaderInfoMode: | file |
| PayloadBlobHeaderInfoOnBranch: | |
| PayloadBlobHeaderInfoShortPath: | e912ba0 |
| PayloadBlobHeaderInfoSiteNavLoginPath: | /login?return_to=https%3A%2F%2Fgithub.com%2Fkh4sh3i%2FRansomware-Samples%2Fblob%2Fmain%2FJigsaw%2FRansomware.Jigsaw.zip |
| PayloadBlobHeaderInfoToc: | null |
| PayloadBlobImage: | - |
| PayloadBlobIsCodeownersFile: | null |
| PayloadBlobIsPlain: | - |
| PayloadBlobIsValidLegacyIssueTemplate: | - |
| PayloadBlobIssueTemplate: | null |
| PayloadBlobIssueTemplateHelpUrl: | https://docs.github.com/articles/about-issue-and-pull-request-templates |
| PayloadBlobLanguage: | null |
| PayloadBlobLanguageID: | null |
| PayloadBlobLarge: | - |
| PayloadBlobLoggedIn: | - |
| PayloadBlobNewDiscussionPath: | /kh4sh3i/Ransomware-Samples/discussions/new |
| PayloadBlobNewIssuePath: | /kh4sh3i/Ransomware-Samples/issues/new |
| PayloadBlobPlanSupportInfoRepoIsFork: | null |
| PayloadBlobPlanSupportInfoRepoOwnedByCurrentUser: | null |
| PayloadBlobPlanSupportInfoRequestFullPath: | /kh4sh3i/Ransomware-Samples/blob/main/Jigsaw/Ransomware.Jigsaw.zip |
| PayloadBlobPlanSupportInfoShowFreeOrgGatedFeatureMessage: | null |
| PayloadBlobPlanSupportInfoShowPlanSupportBanner: | null |
| PayloadBlobPlanSupportInfoUpgradeDataAttributes: | null |
| PayloadBlobPlanSupportInfoUpgradePath: | null |
| PayloadBlobPublishBannersInfoDismissActionNoticePath: | /settings/dismiss-notice/publish_action_from_dockerfile |
| PayloadBlobPublishBannersInfoDismissStackNoticePath: | /settings/dismiss-notice/publish_stack_from_file |
| PayloadBlobPublishBannersInfoReleasePath: | /kh4sh3i/Ransomware-Samples/releases/new?marketplace=true |
| PayloadBlobPublishBannersInfoShowPublishActionBanner: | - |
| PayloadBlobPublishBannersInfoShowPublishStackBanner: | - |
| PayloadBlobRawBlobUrl: | https://github.com/kh4sh3i/Ransomware-Samples/raw/main/Jigsaw/Ransomware.Jigsaw.zip |
| PayloadBlobRawLines: | null |
| PayloadBlobRenderImageOrRaw: | |
| PayloadBlobRenderedFileInfo: | null |
| PayloadBlobRichText: | null |
| PayloadBlobShortPath: | null |
| PayloadBlobStylingDirectives: | null |
| PayloadBlobSymbols: | null |
| PayloadBlobTabSize: | 8 |
| PayloadBlobTopBannersInfoActionsOnboardingTip: | null |
| PayloadBlobTopBannersInfoCitationHelpUrl: | https://docs.github.com/en/github/creating-cloning-and-archiving-repositories/creating-a-repository-on-github/about-citation-files |
| PayloadBlobTopBannersInfoGlobalPreferredFundingPath: | null |
| PayloadBlobTopBannersInfoOverridingGlobalFundingFile: | - |
| PayloadBlobTopBannersInfoRepoName: | Ransomware-Samples |
| PayloadBlobTopBannersInfoRepoOwner: | kh4sh3i |
| PayloadBlobTopBannersInfoShowDependabotConfigurationBanner: | - |
| PayloadBlobTopBannersInfoShowInvalidCitationWarning: | - |
| PayloadBlobTruncated: | - |
| PayloadBlobViewable: | - |
| PayloadBlobWorkflowRedirectUrl: | null |
| PayloadCopilotAccessAllowed: | - |
| PayloadCopilotInfo: | null |
| PayloadCsrf_tokenskh4sh3iRansomware-SamplesbranchesPost: | _1bX5uKSuXsy0eTEIndw8A944X68XhfX-Pr0WG_yn9WN1BW_6YtRpaFOu9twDMGUaWPLVHsNZzy3JUXNk7G8bA |
| PayloadCsrf_tokensrepospreferencesPost: | iyy5O9iCggtW_mWWb1d9EbuVRa9fgLHsQzhywZ7o22lYLn4Ki57U5pnz_1X0gBrWbvCtDlyACY7DnMSEv5T1Aw |
| PayloadCurrentUser: | null |
| PayloadFileTreeItemsContentType: |
|
| PayloadFileTreeItemsName: |
|
| PayloadFileTreeItemsPath: |
|
| PayloadFileTreeTotalCount: | 21 |
| PayloadFileTreeJigsawItemsContentType: | file |
| PayloadFileTreeJigsawItemsName: | Ransomware.Jigsaw.zip |
| PayloadFileTreeJigsawItemsPath: | Jigsaw/Ransomware.Jigsaw.zip |
| PayloadFileTreeJigsawTotalCount: | 1 |
| PayloadFileTreeProcessingTime: | 6.953249 |
| PayloadPath: | Jigsaw/Ransomware.Jigsaw.zip |
| PayloadReducedMotionEnabled: | null |
| PayloadRefInfoCanEdit: | - |
| PayloadRefInfoCurrentOid: | 71f6062209bed1c52b63637746239868da0da49e |
| PayloadRefInfoListCacheKey: | v0:1628594348.8846889 |
| PayloadRefInfoName: | main |
| PayloadRefInfoRefType: | branch |
| PayloadRepoCreatedAt: | 2021-08-10T10:20:11.000Z |
| PayloadRepoCurrentUserCanPush: | - |
| PayloadRepoDefaultBranch: | main |
| PayloadRepoId: | 394609962 |
| PayloadRepoIsEmpty: | - |
| PayloadRepoIsFork: | - |
| PayloadRepoIsOrgOwned: | - |
| PayloadRepoName: | Ransomware-Samples |
| PayloadRepoOwnerAvatar: | https://avatars.githubusercontent.com/u/64693844?v=4 |
| PayloadRepoOwnerLogin: | kh4sh3i |
| PayloadRepoPrivate: | - |
| PayloadRepoPublic: | |
| PayloadSymbolsExpanded: | - |
| PayloadTreeExpanded: | |
| Title: | Ransomware-Samples/Jigsaw/Ransomware.Jigsaw.zip at main · kh4sh3i/Ransomware-Samples |
Total processes
84
Monitored processes
39
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=19 --mojo-platform-channel-handle=3992 --field-trial-handle=1312,i,2407239491874019720,4286521662024944836,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 452 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Ransomware.Jigsaw.zip" C:\Users\admin\Desktop\Ransomware.Jigsaw\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1 Version: 5.91.0 Modules
| |||||||||||||||
| 604 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.PageScreenshotProcessor --lang=en-US --service-sandbox-type=entity_extraction --mojo-platform-channel-handle=4172 --field-trial-handle=1312,i,2407239491874019720,4286521662024944836,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 984 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --mojo-platform-channel-handle=4432 --field-trial-handle=1312,i,2407239491874019720,4286521662024944836,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2272 --field-trial-handle=1312,i,2407239491874019720,4286521662024944836,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --lang=en-US --service-sandbox-type=audio --mojo-platform-channel-handle=3980 --field-trial-handle=1312,i,2407239491874019720,4286521662024944836,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1344 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3888 --field-trial-handle=1312,i,2407239491874019720,4286521662024944836,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1432 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3700 --field-trial-handle=1312,i,2407239491874019720,4286521662024944836,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1776 | "C:\Users\admin\AppData\Local\Drpbx\drpbx.exe" C:\Users\admin\Downloads\Ransomware.Jigsaw\jigsa.exe | C:\Users\admin\AppData\Local\Drpbx\drpbx.exe | jigsa.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 37.0.2.5583 Modules
| |||||||||||||||
| 1848 | "C:\Users\admin\Downloads\Ransomware.Jigsaw\jigsa.exe" | C:\Users\admin\Downloads\Ransomware.Jigsaw\jigsa.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 37.0.2.5583 Modules
| |||||||||||||||
Total events
69 693
Read events
69 596
Write events
96
Delete events
1
Modification events
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band56_0 |
Value: 38000000730100000402000000000000D4D0C8000000000000000000000000005C0104000000000039000000B40200000000000001000000 | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band56_1 |
Value: 38000000730100000500000000000000D4D0C8000000000000000000000000008C010C0000000000160000002A0000000000000002000000 | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band56_2 |
Value: 38000000730100000400000000000000D4D0C800000000000000000000000000AC0107000000000016000000640000000000000003000000 | |||
| (PID) Process: | (452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
34
Suspicious files
2 061
Text files
132
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1579bd.TMP | — | |
MD5:— | SHA256:— | |||
| 2672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1579dd.TMP | — | |
MD5:— | SHA256:— | |||
| 2672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF157a89.TMP | — | |
MD5:— | SHA256:— | |||
| 2672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:AB24748B6383043489AC0960A5BBCA45 | SHA256:502CF9B7B647DC938CB1C9A0F7E50B13087881494E81D81420BFB425BC02DD4B | |||
| 2672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State | binary | |
MD5:5B0569DA669FAEA52B6157E16DB22650 | SHA256:DDDCE64167F7B8E153E90D034DC71A35365A6CB4CB2BC9D88912733A36539470 | |||
| 2672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Platform Notifications\LOG.old~RF157bb1.TMP | text | |
MD5:5C595987DA30D4BBE1CB90CB2CC17F72 | SHA256:85F8B598D575AD61585922EB00C1A4BCDA8EB121CD9E00F4015A80A1D99F669E | |||
| 2672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgeCoupons\coupons_data.db\LOG.old~RF1579bd.TMP | text | |
MD5:B325089234E8AB35FFC7D43AC1666C0A | SHA256:C6E2B50D00049C80190B6F2CB711AC0E227F0F602E6B4751F63F6E4C51287F5A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
65
DNS requests
120
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2072 | msedge.exe | 204.79.197.203:443 | ntp.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2072 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2072 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2672 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2072 | msedge.exe | 23.37.226.113:443 | assets.msn.com | Akamai International B.V. | DE | unknown |
2072 | msedge.exe | 2.21.20.134:443 | img-s-msn-com.akamaized.net | Akamai International B.V. | DE | unknown |
2072 | msedge.exe | 23.53.43.121:443 | th.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ntp.msn.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
assets.msn.com |
| whitelisted |
img-s-msn-com.akamaized.net |
| whitelisted |
sb.scorecardresearch.com |
| shared |
th.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
c.msn.com |
| whitelisted |
c.bing.com |
| whitelisted |