| File name: | media.docm |
| Full analysis: | https://app.any.run/tasks/4dac7d2a-1215-4877-beee-034303821490 |
| Verdict: | Malicious activity |
| Analysis date: | February 16, 2024, 07:55:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 0162C7DBD6D297E81502D7B79E9CC1D2 |
| SHA1: | B982876221A84A6E784F41217A4A244D58AA8B1D |
| SHA256: | 6EDAC0E8E990104187A51737C02205163E4F70D5A8AA094CFDFDD241CD14B149 |
| SSDEEP: | 768:iaYXj9JvPksjsIPtLPEoPELH/tRW+sY8F/L3MWUzheEXcccccccccceh4fb10jd0:iaEvkYHtEoOHqhLez3fbcdkf |
MALICIOUS
Opens an HTTP connection (SCRIPT)
- WINWORD.EXE (PID: 2472)
Checks whether a specified folder exists (SCRIPT)
- WINWORD.EXE (PID: 2472)
Creates internet connection object (SCRIPT)
- WINWORD.EXE (PID: 2472)
Accesses environment variables (SCRIPT)
- WINWORD.EXE (PID: 2472)
Sends HTTP request (SCRIPT)
- WINWORD.EXE (PID: 2472)
Gets %appdata% folder path (SCRIPT)
- WINWORD.EXE (PID: 2472)
Creates a new folder (SCRIPT)
- WINWORD.EXE (PID: 2472)
Unusual execution from MS Office
- WINWORD.EXE (PID: 2472)
Connection from MS Office application
- WINWORD.EXE (PID: 2472)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- WINWORD.EXE (PID: 2472)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- WINWORD.EXE (PID: 2472)
Saves data to a binary file (SCRIPT)
- WINWORD.EXE (PID: 2472)
Writes binary data to a Stream object (SCRIPT)
- WINWORD.EXE (PID: 2472)
INFO
An automatically generated document
- WINWORD.EXE (PID: 2472)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (47) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (21.2) |
| .zip | | | Open Packaging Conventions container (15.8) |
| .zan | | | BlueEyes Animation (12.2) |
| .zip | | | ZIP compressed archive (3.6) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x2d551a4d |
| ZipCompressedSize: | 400 |
| ZipUncompressedSize: | 1504 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal.dotm |
|---|---|
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | 14 |
| Characters: | 82 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 95 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 15 |
| LastModifiedBy: | yo tu |
| RevisionNumber: | 2 |
| CreateDate: | 2014:01:07 16:39:00Z |
| ModifyDate: | 2014:01:07 16:39:00Z |
XMP
| Creator: | İlyasÖzdoğan |
|---|
Total processes
39
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2472 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\media.docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
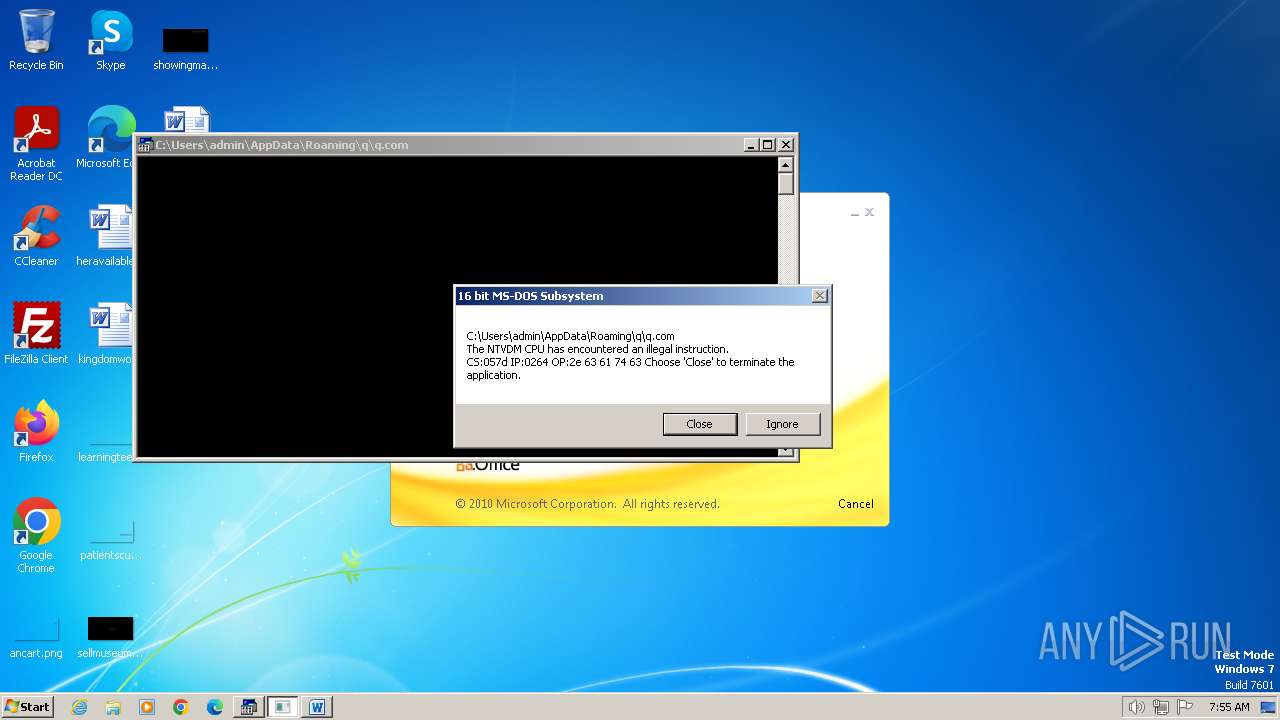
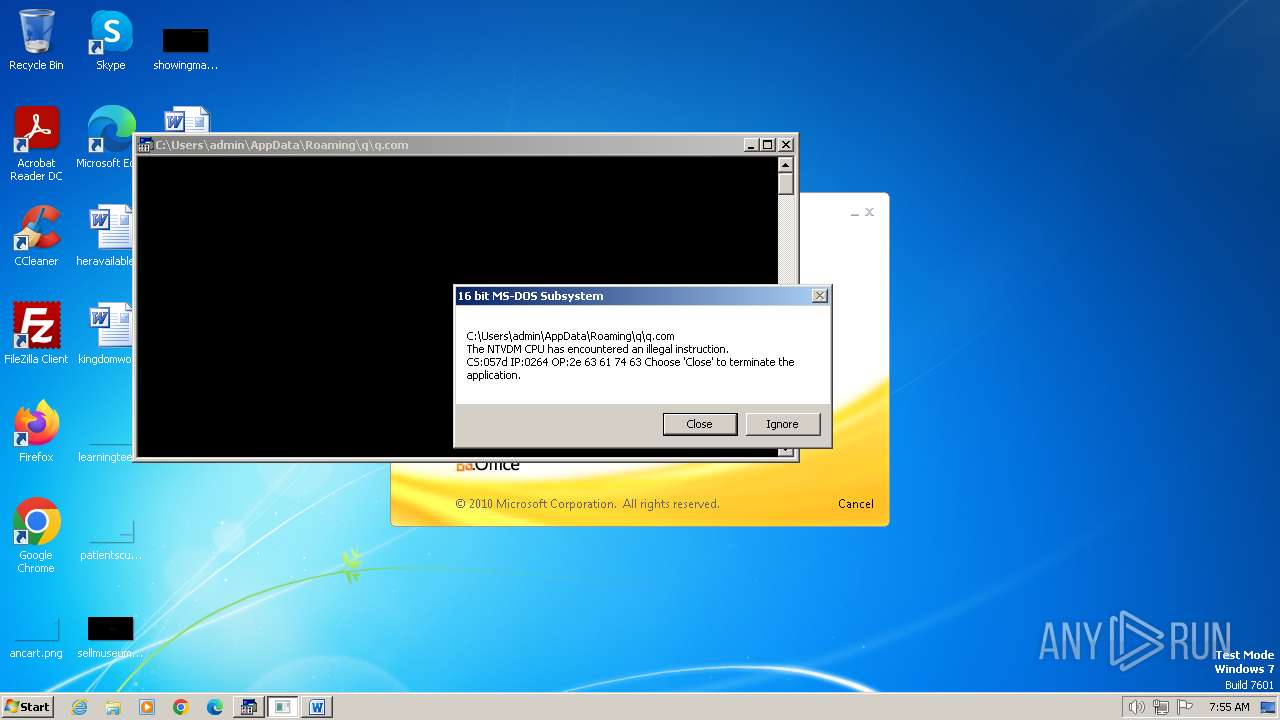
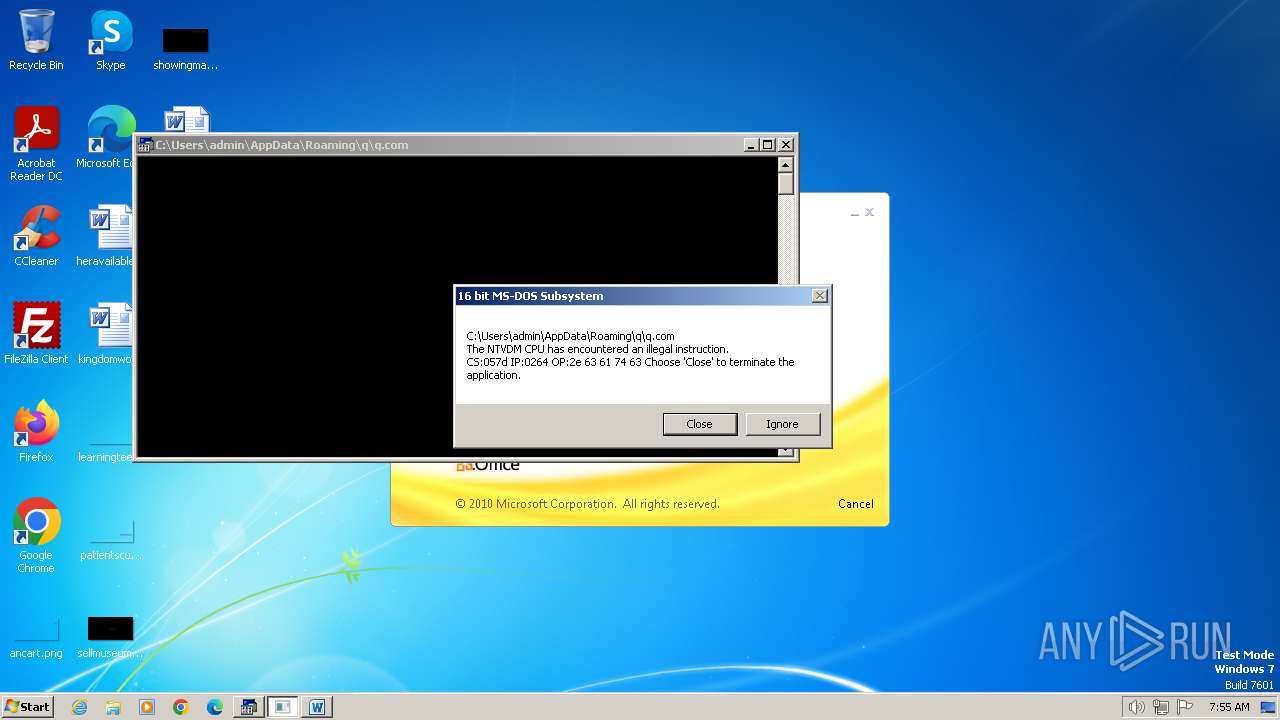
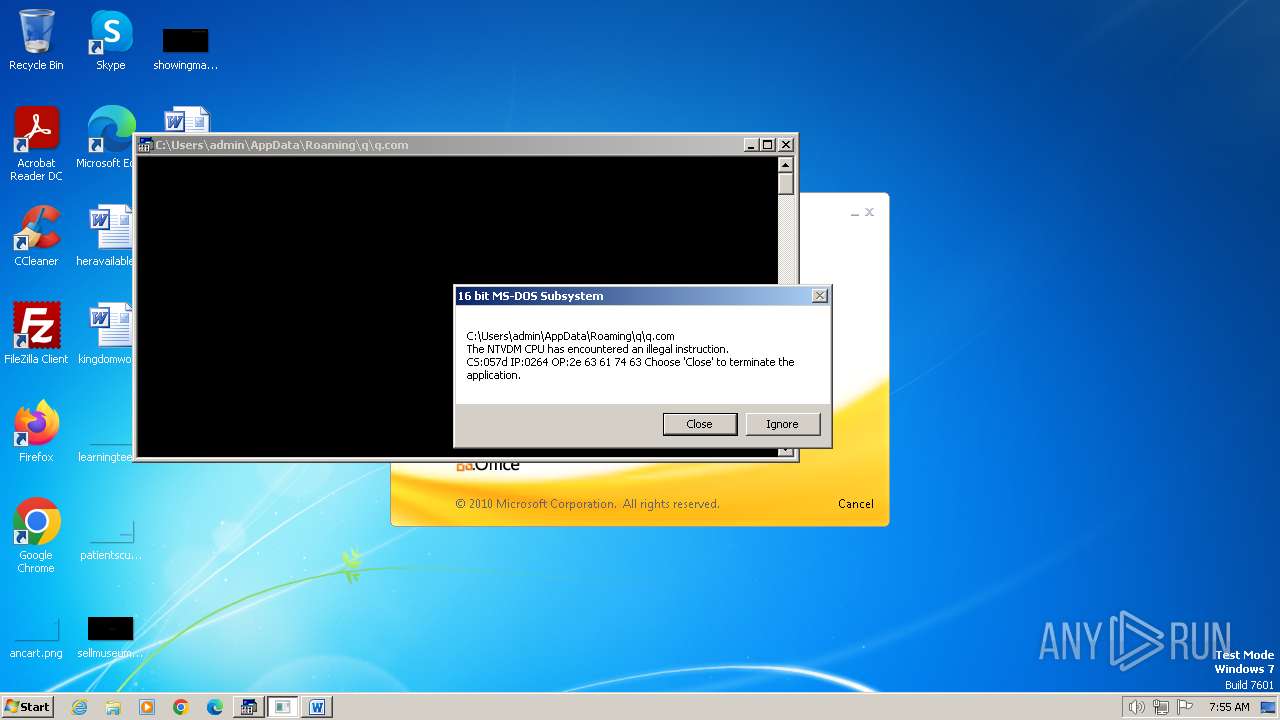
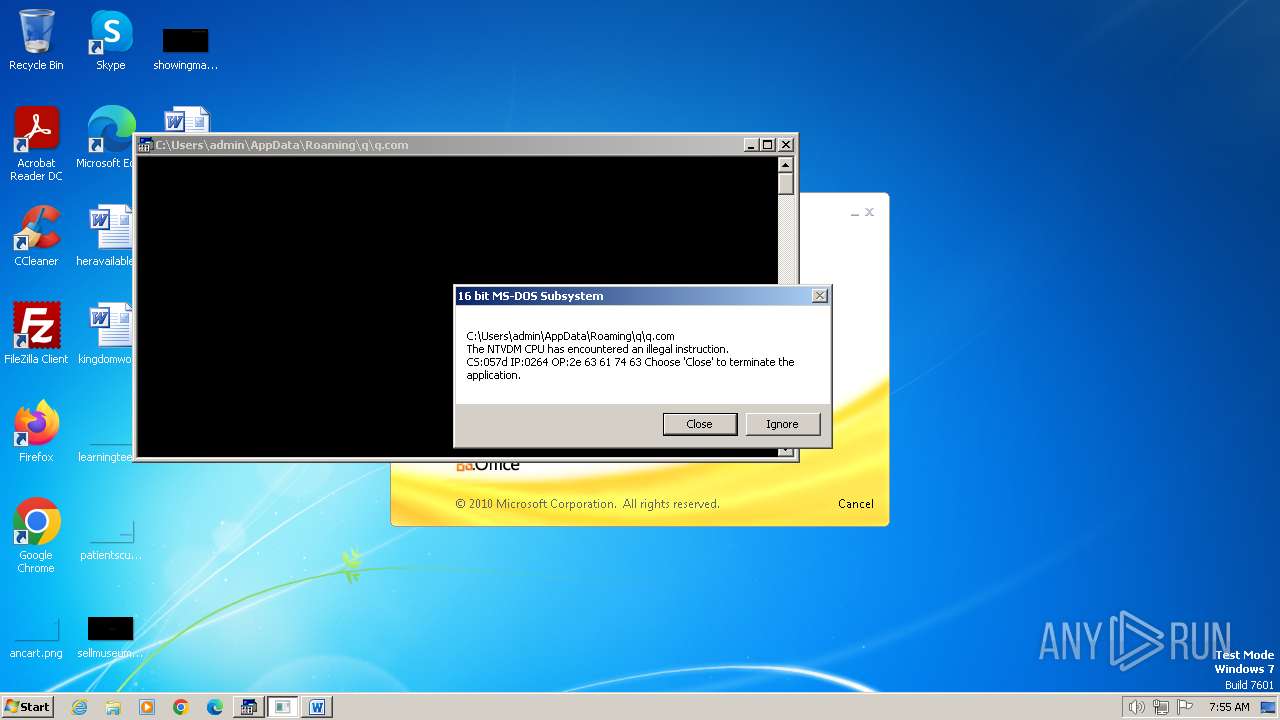
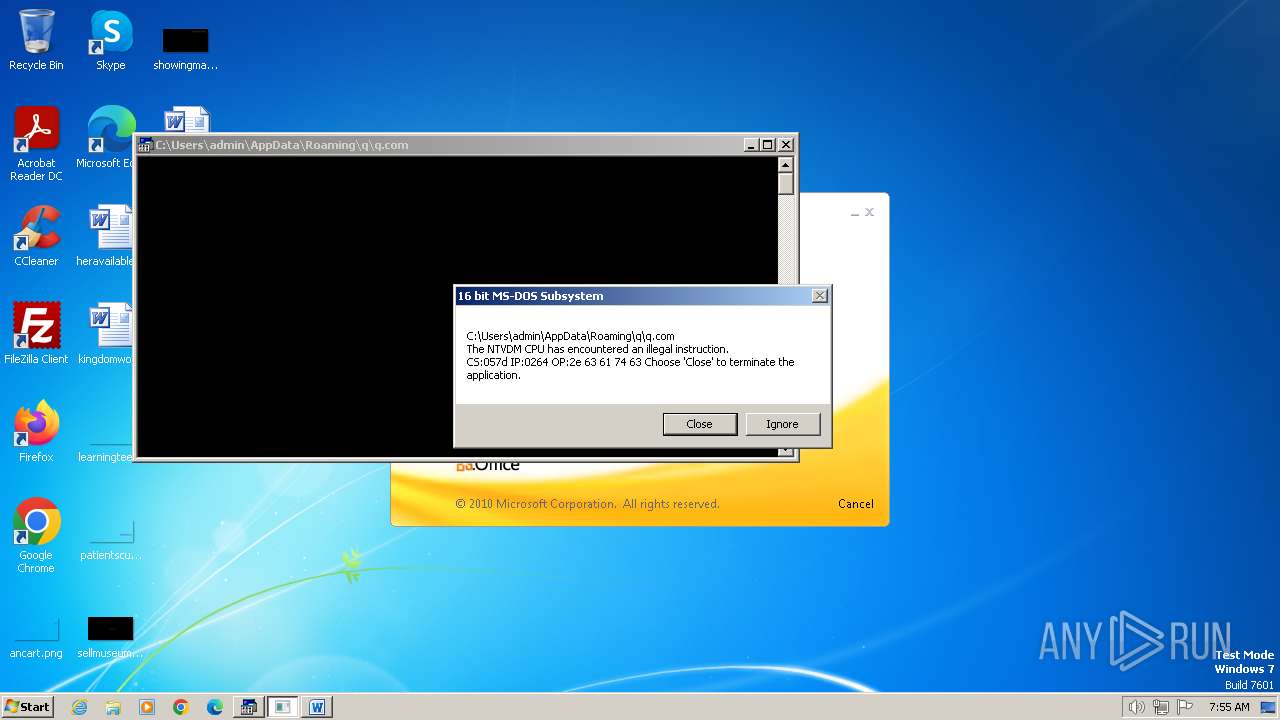
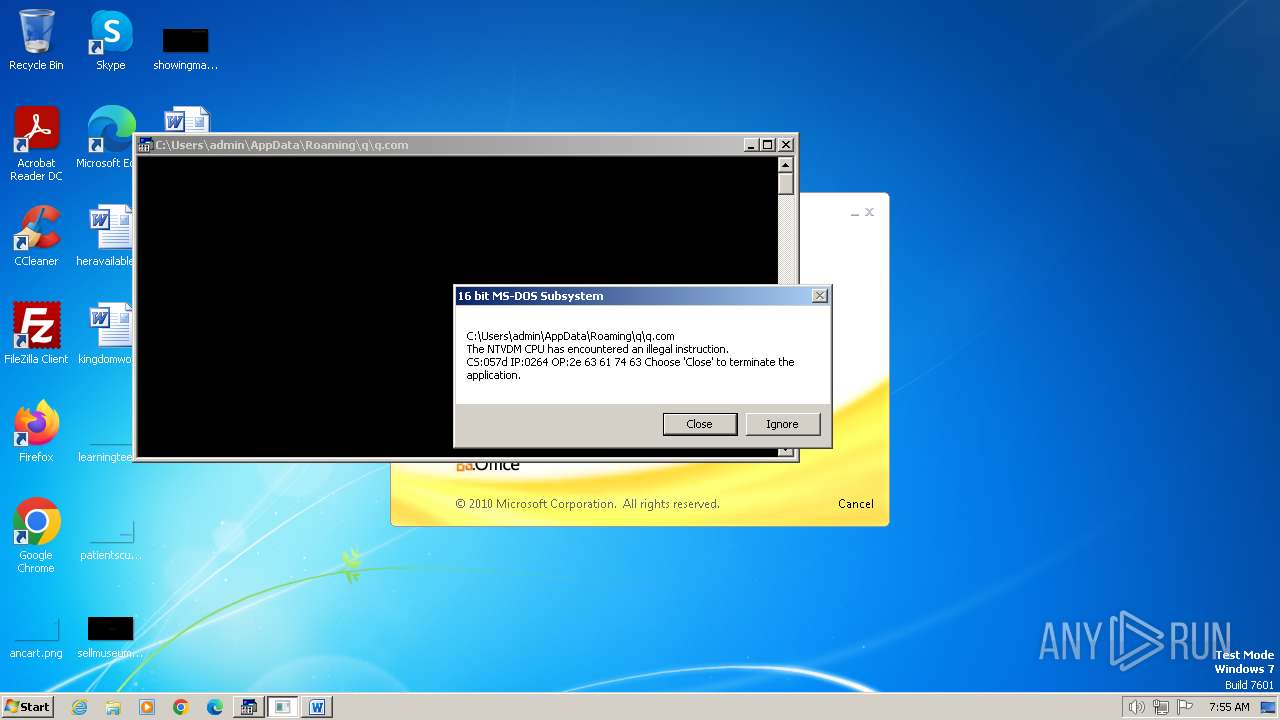
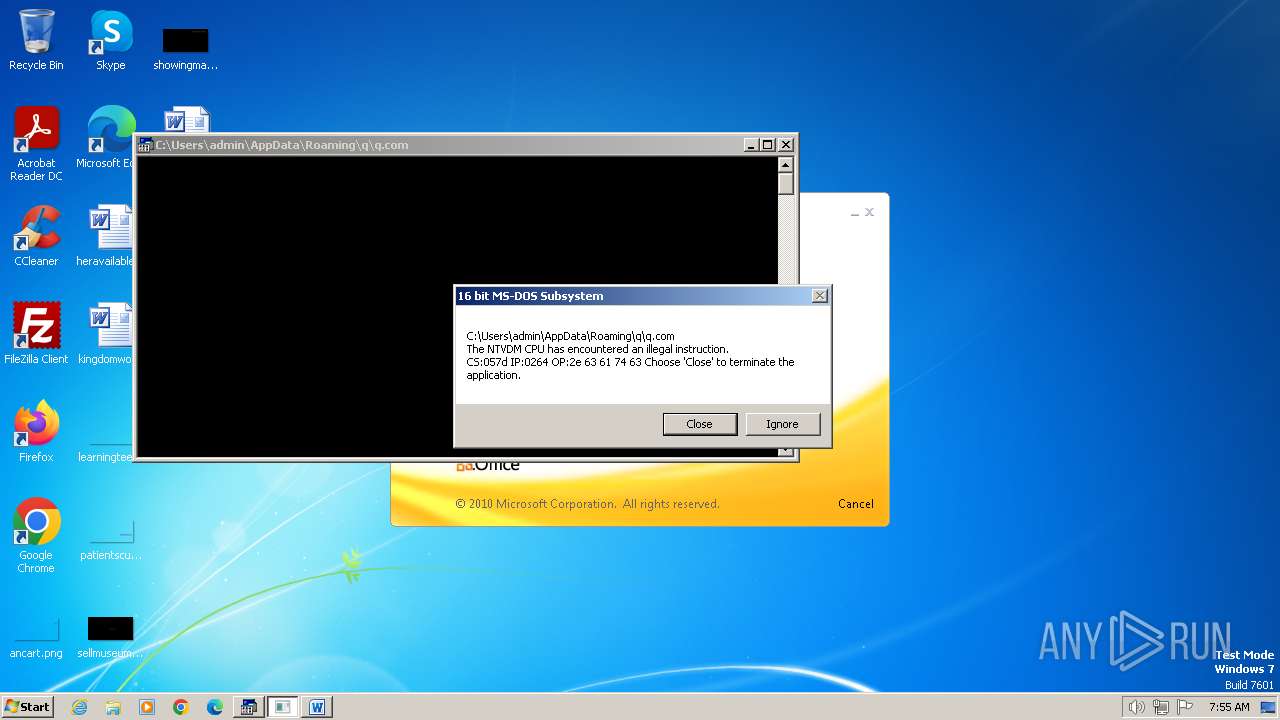
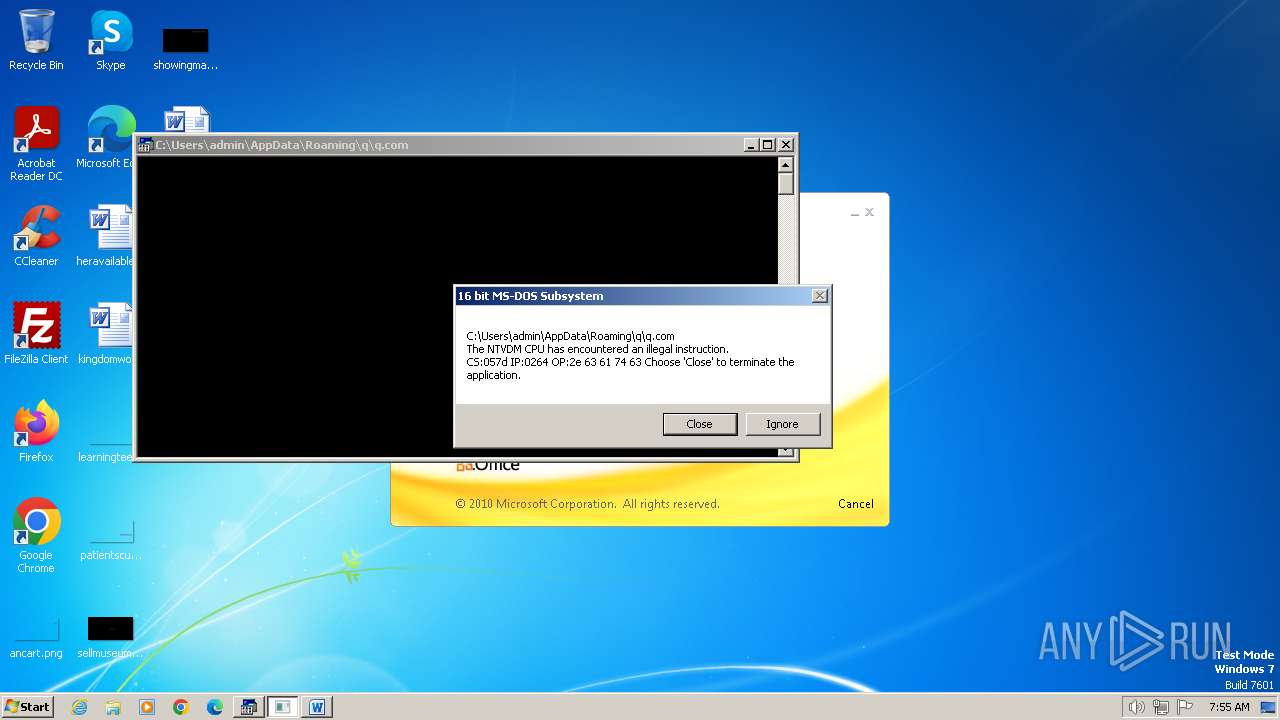
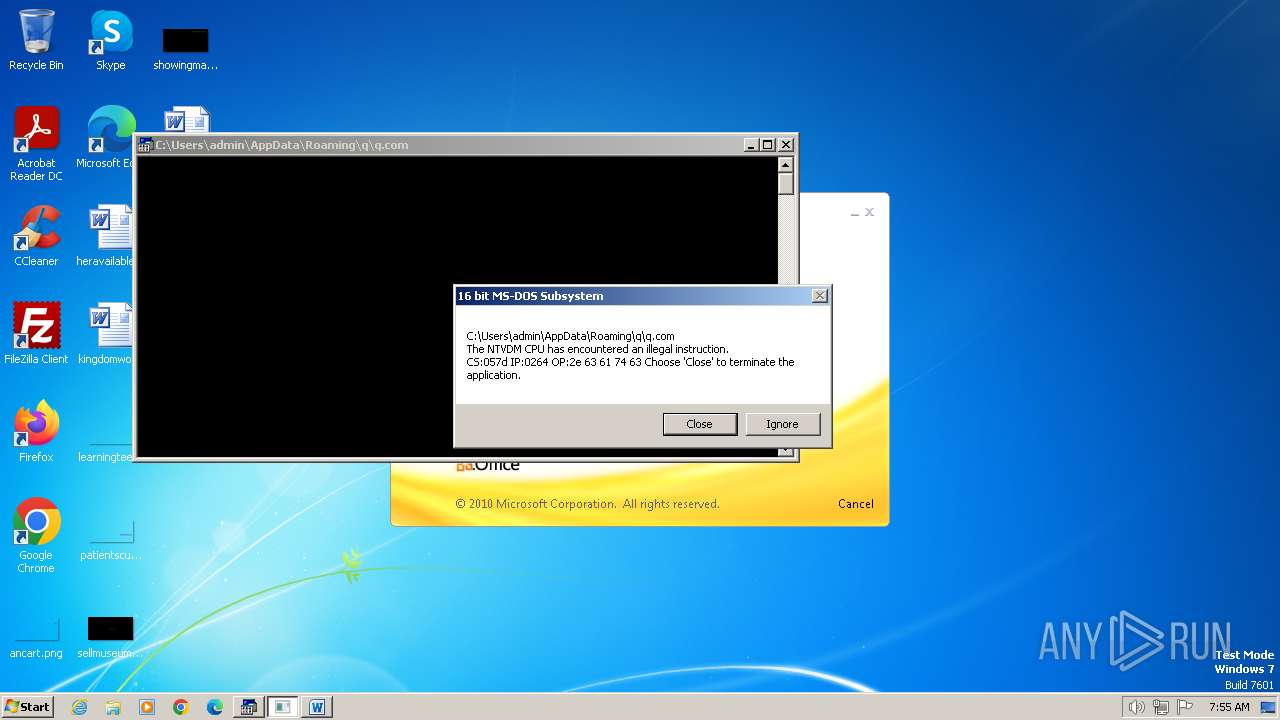
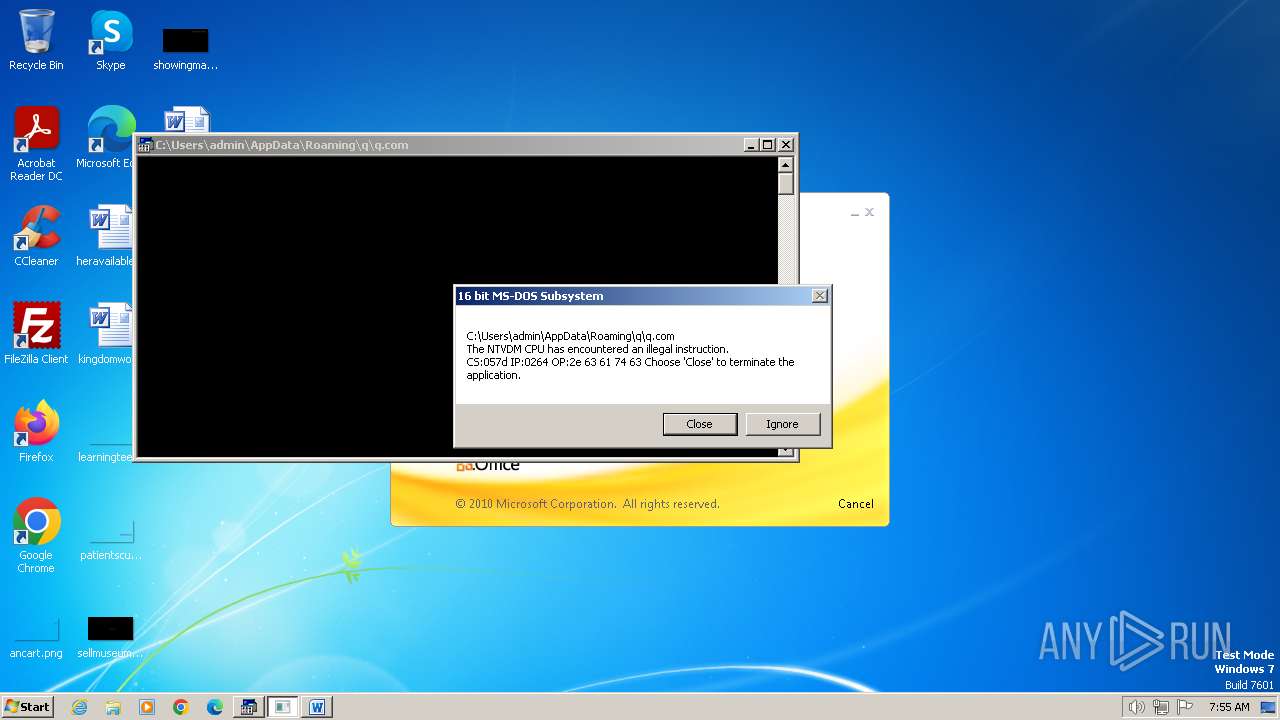
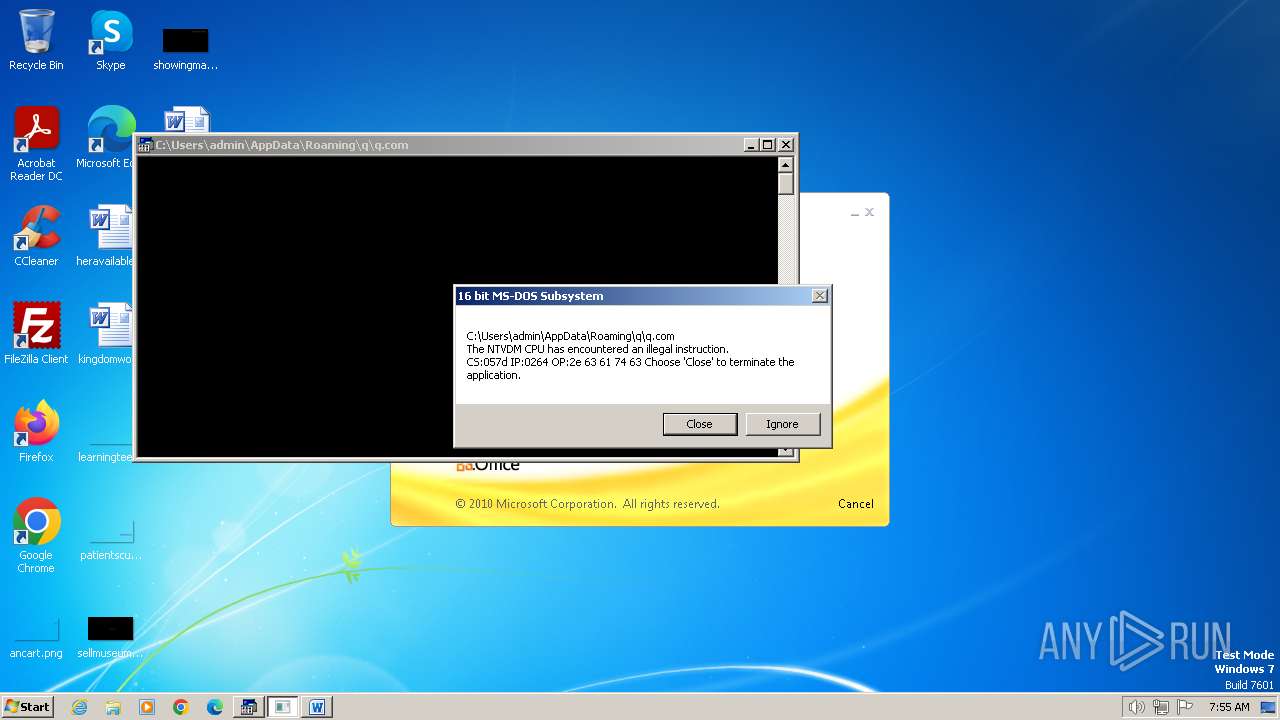
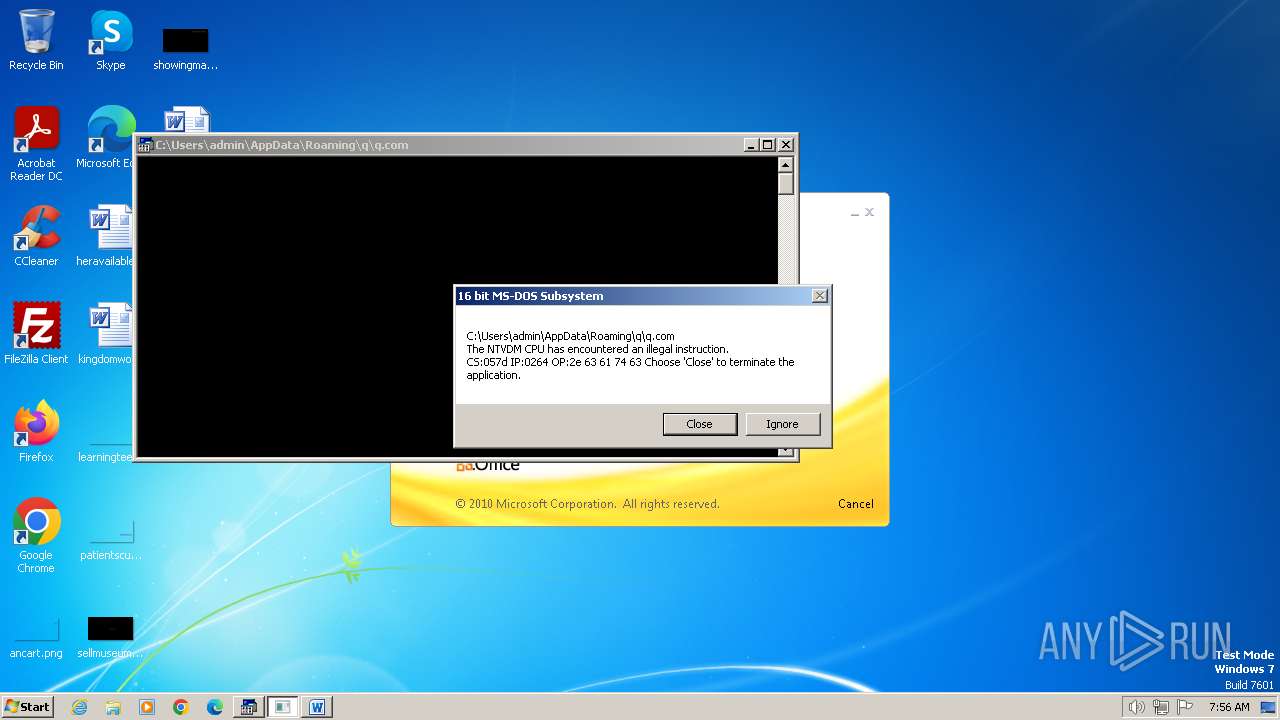
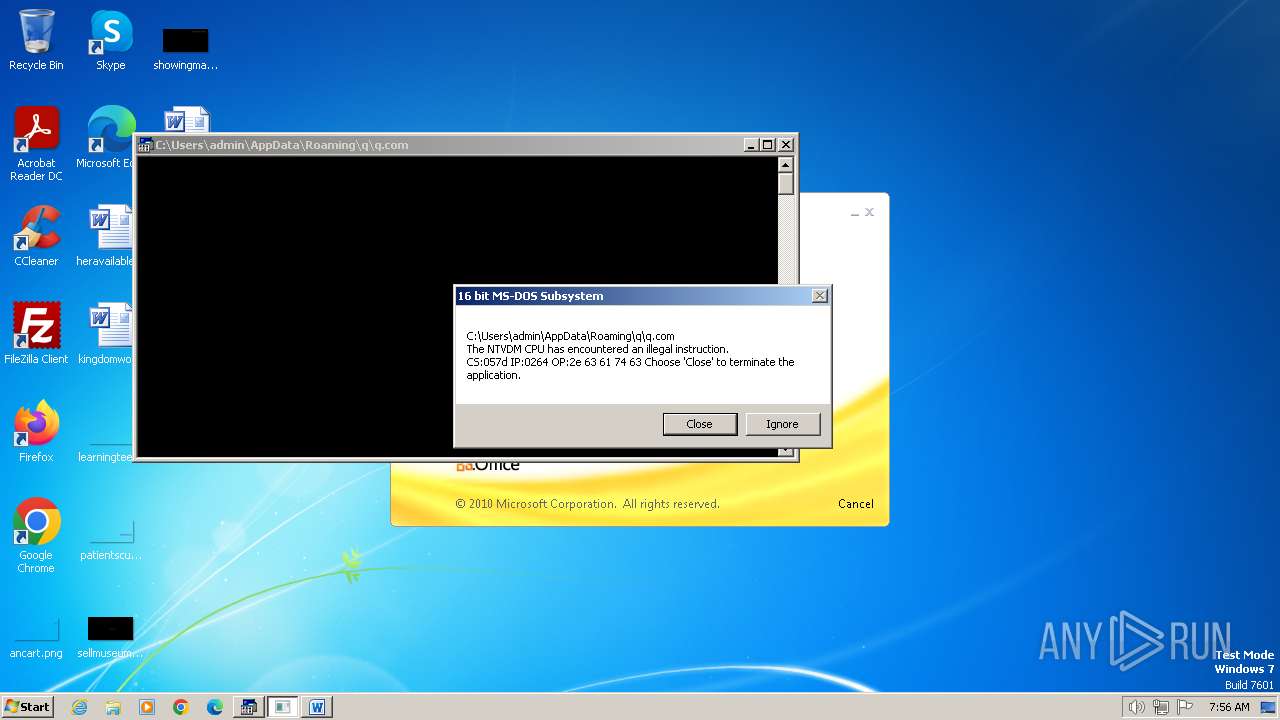
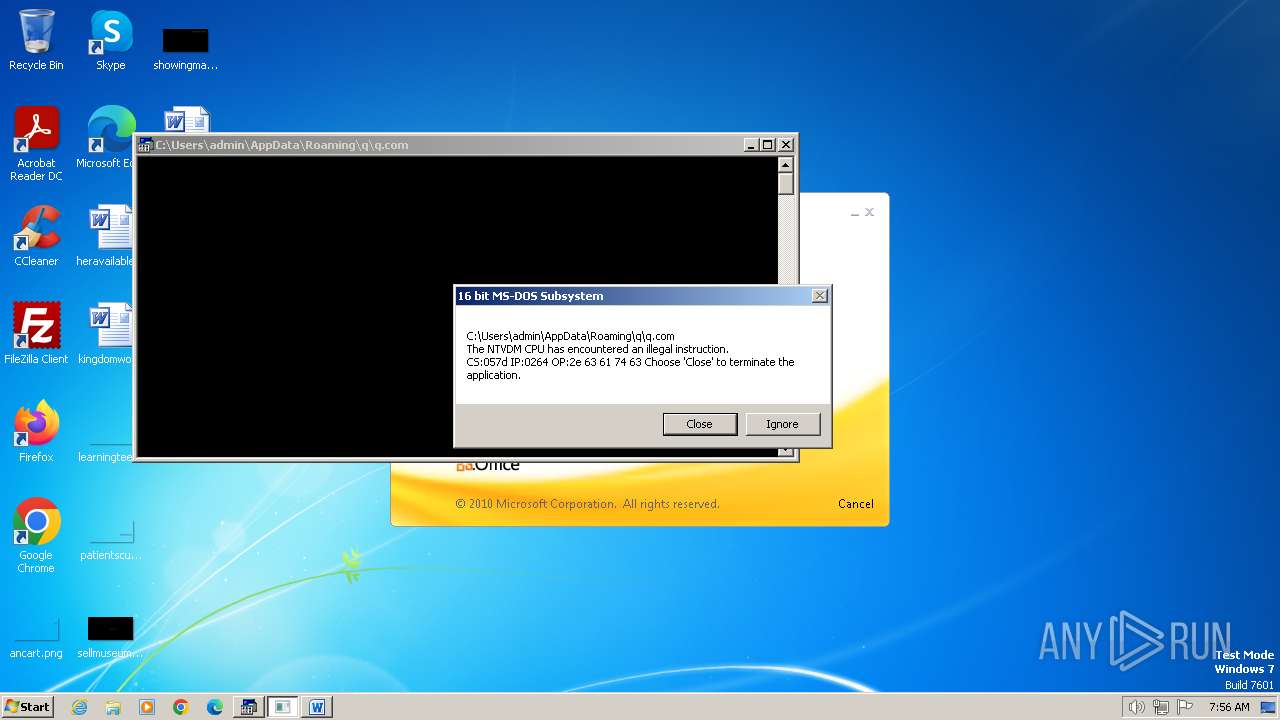
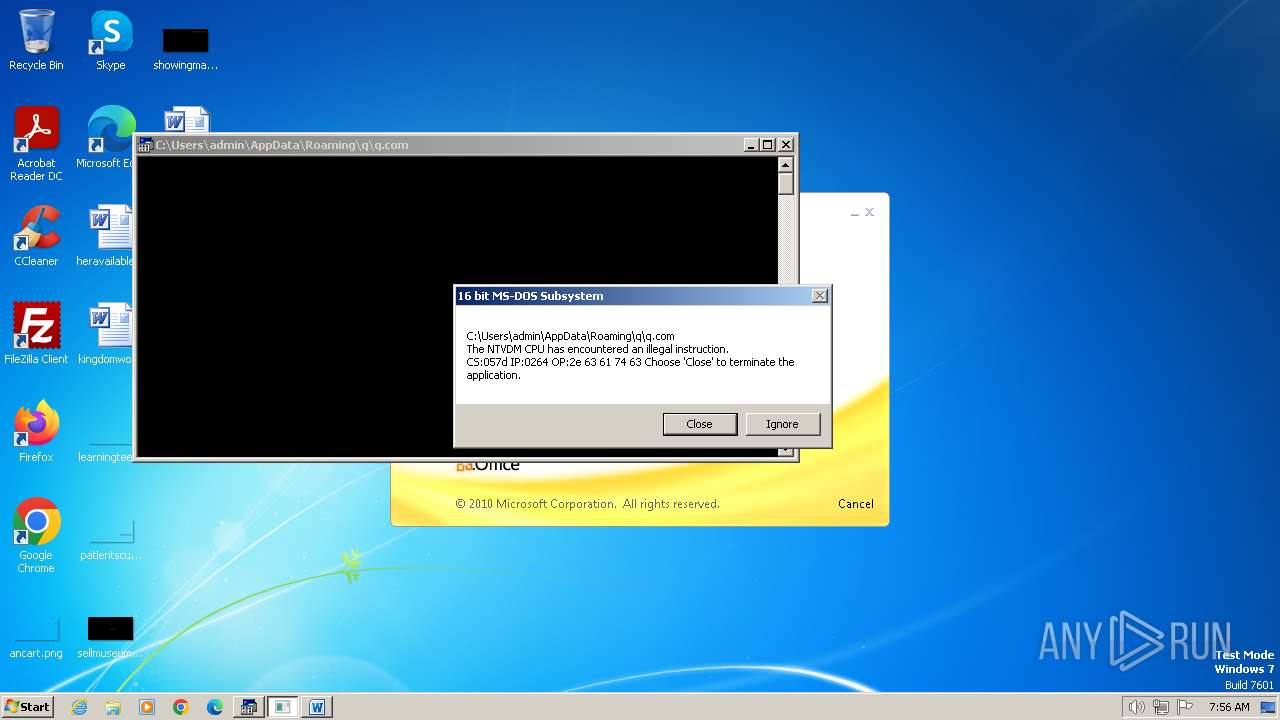
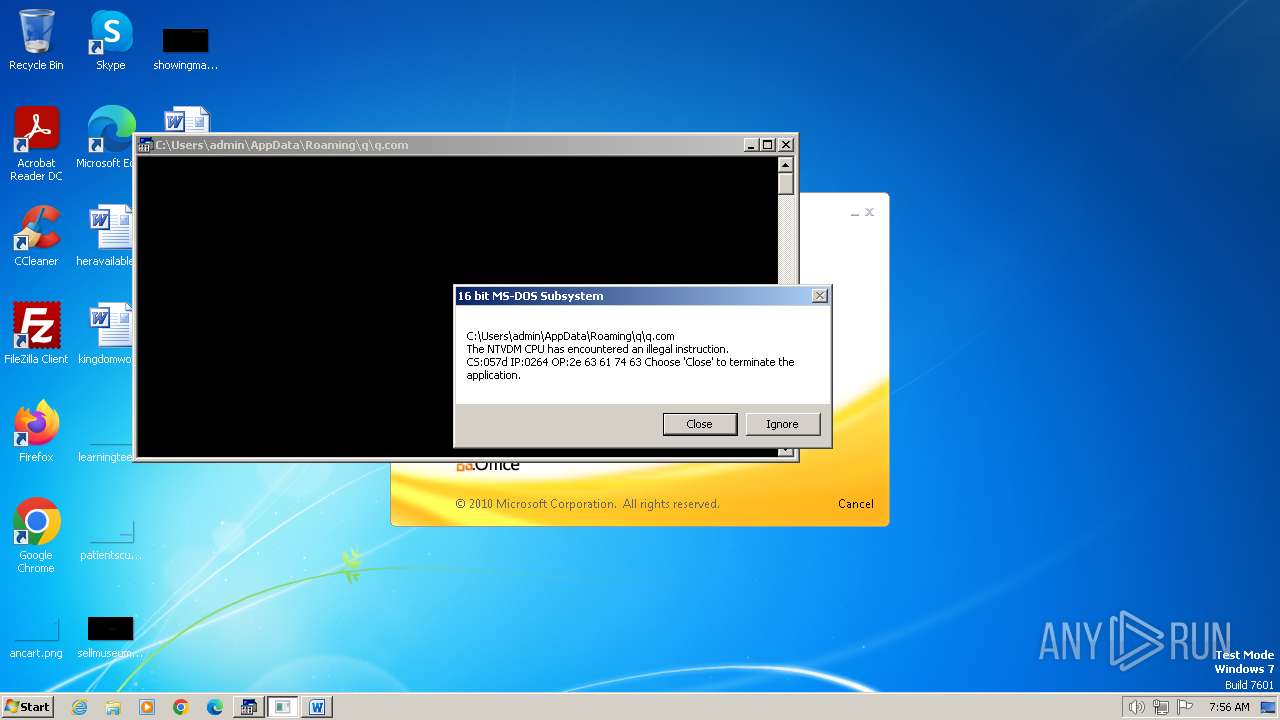
| 2852 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\System32\ntvdm.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 237
Read events
5 027
Write events
73
Delete events
137
Modification events
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | za& |
Value: 7A612600A8090000010000000000000000000000 | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
2
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVREDFA.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:280D2B65A6285DCE35099F1721B7999D | SHA256:9C481BFD497634B56792F1F82F7323677D76F0ECD94EC28D527714D4DEF38B52 | |||
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$media.docm | binary | |
MD5:A9219EBE2DD92BB7B2FF3D6D7CFD3675 | SHA256:0BE96ACB9E7FEC396AF65057B3983580446CDE8B8C34FE8BAAB3F567E9F995F7 | |||
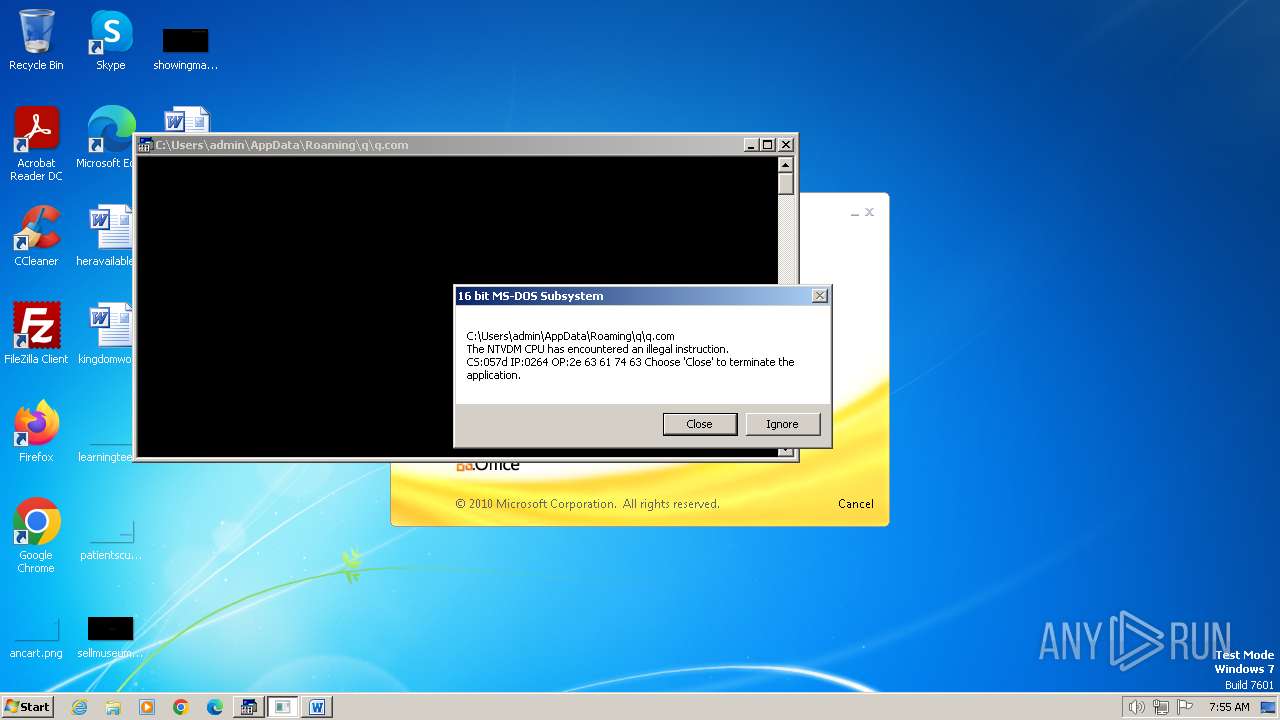
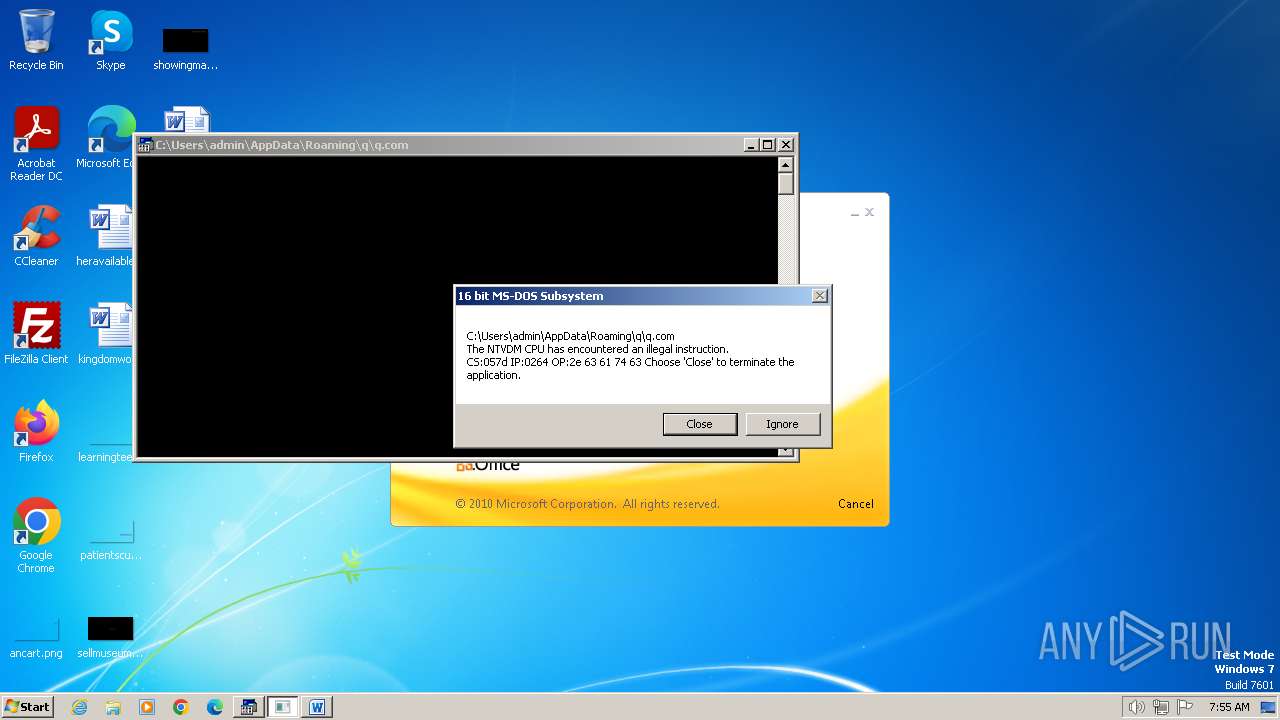
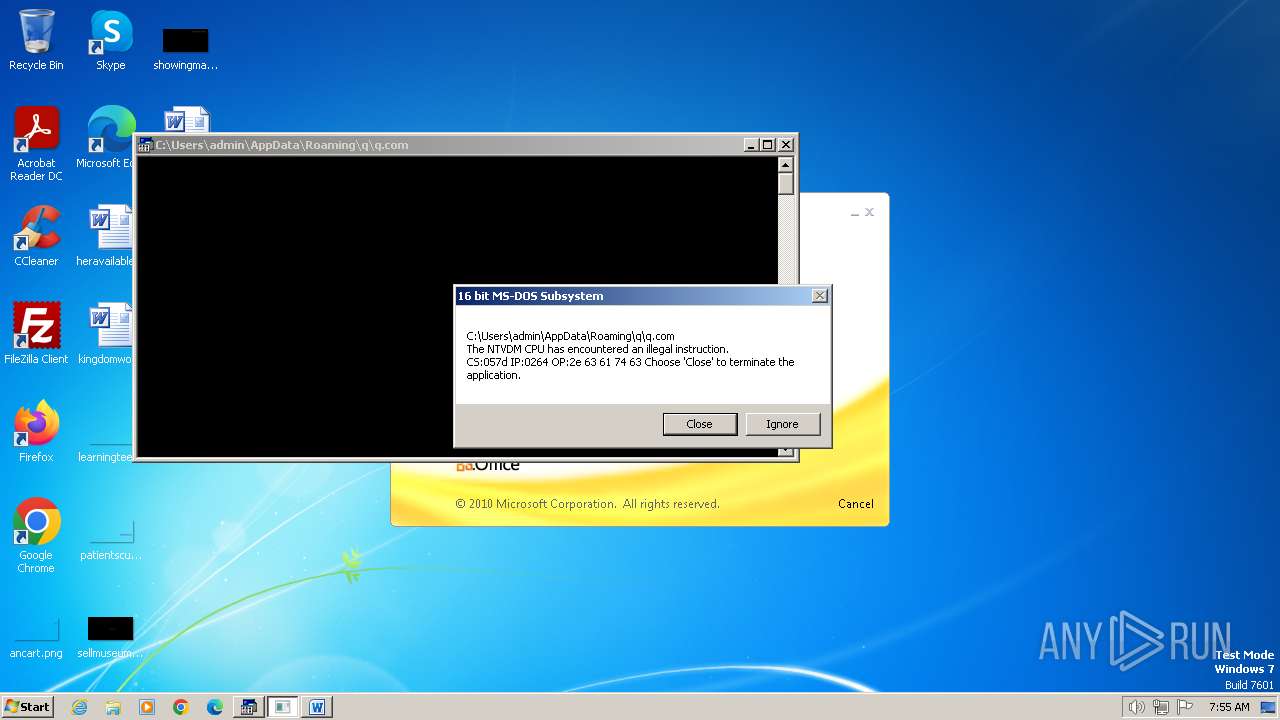
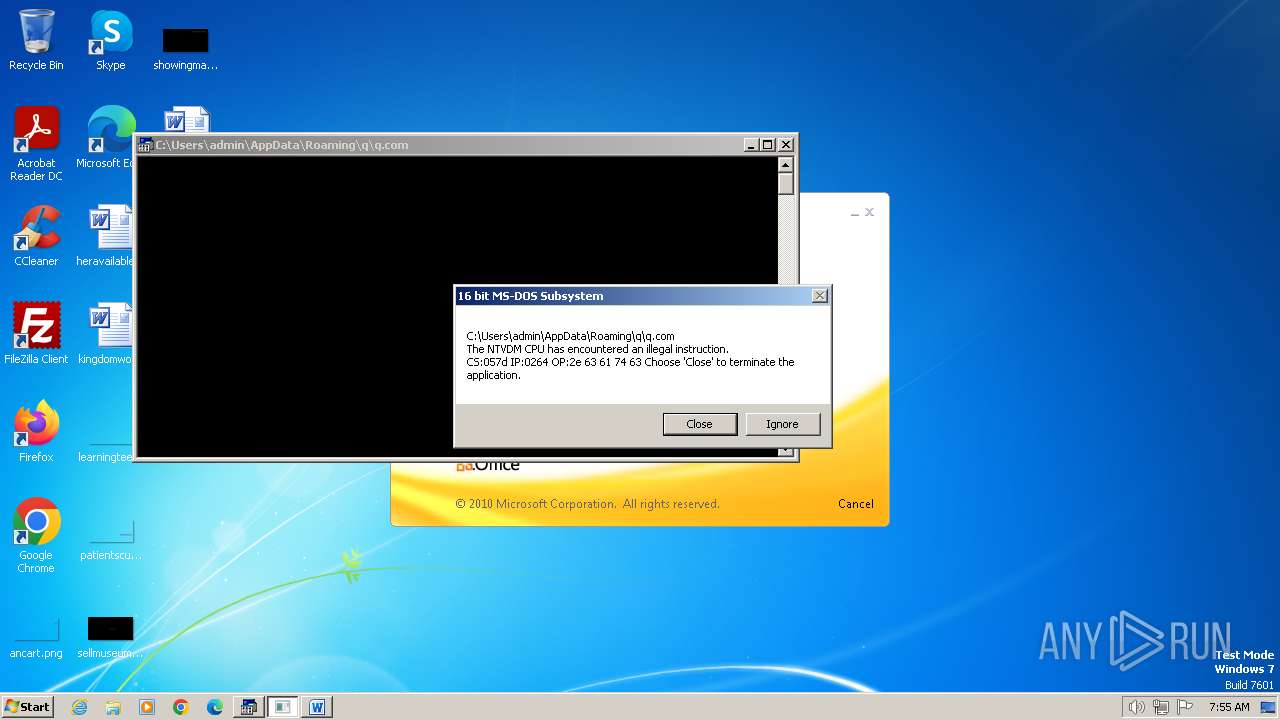
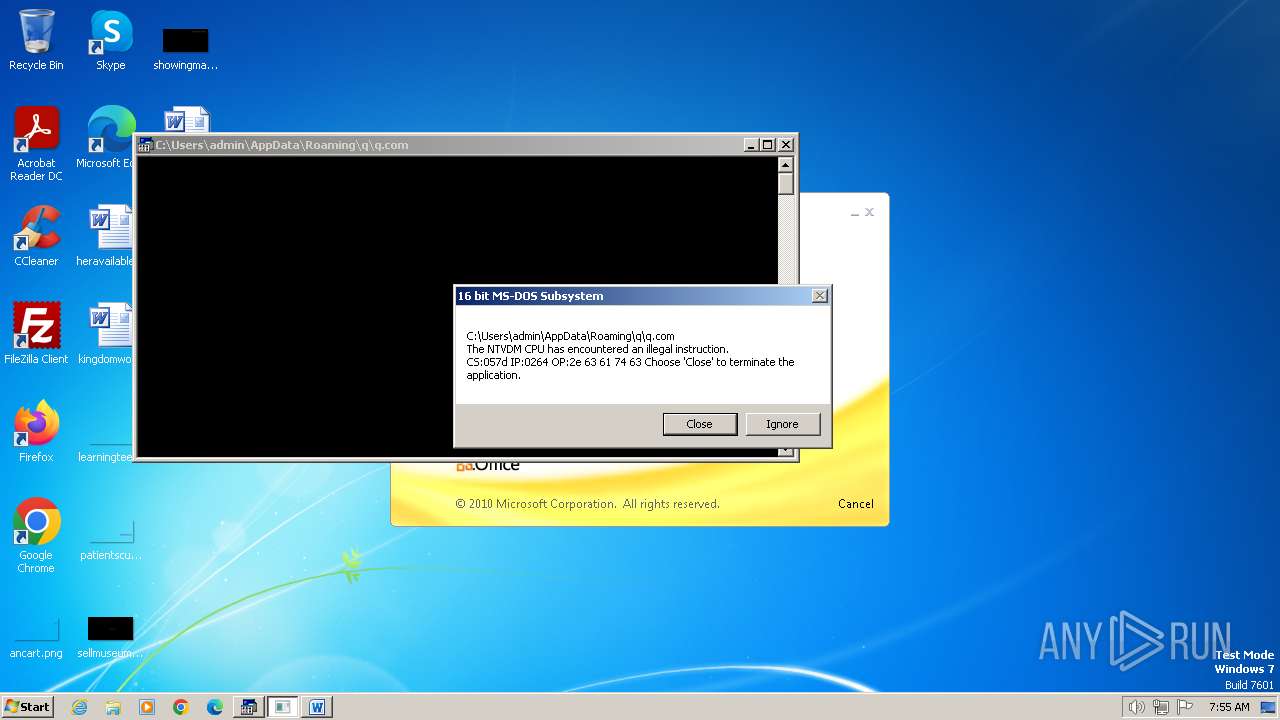
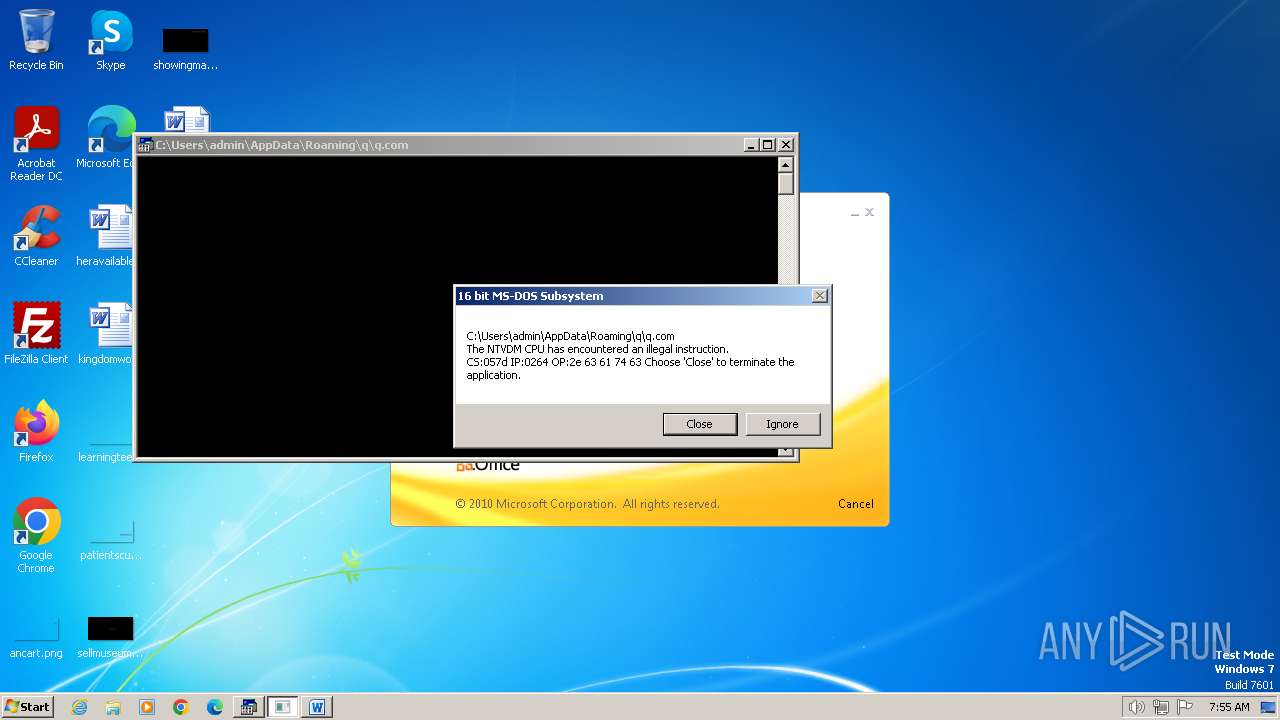
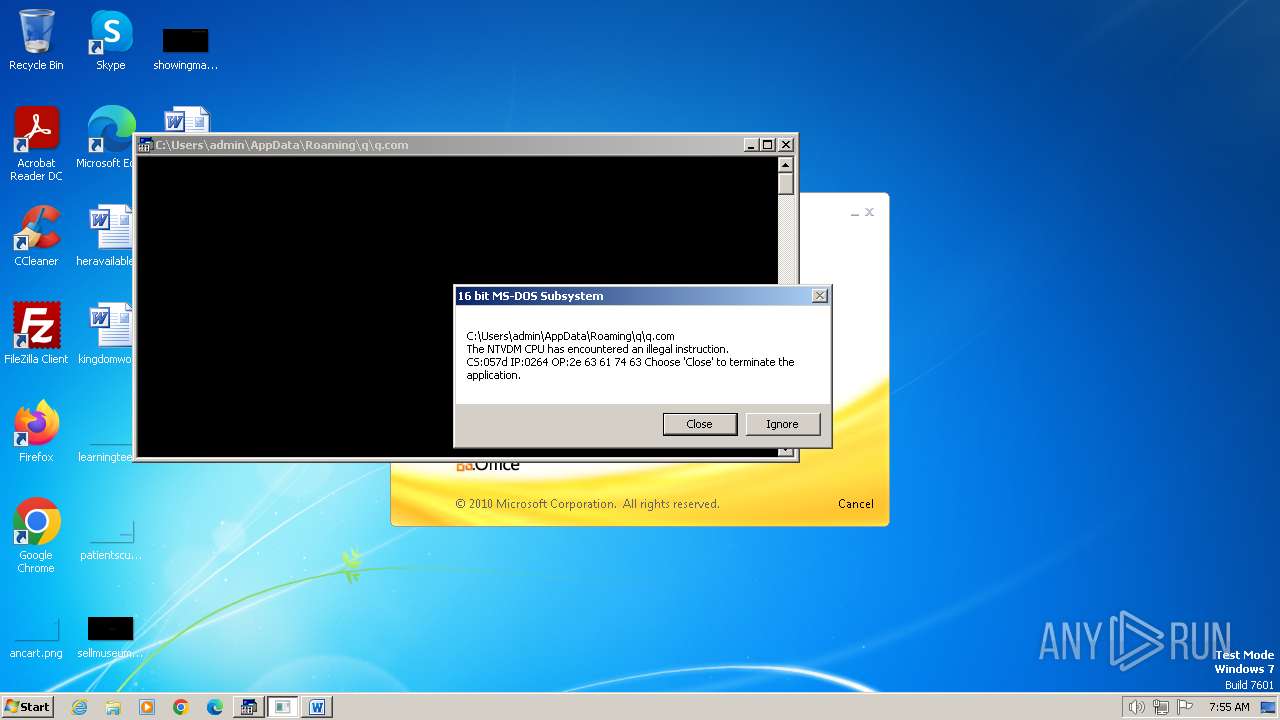
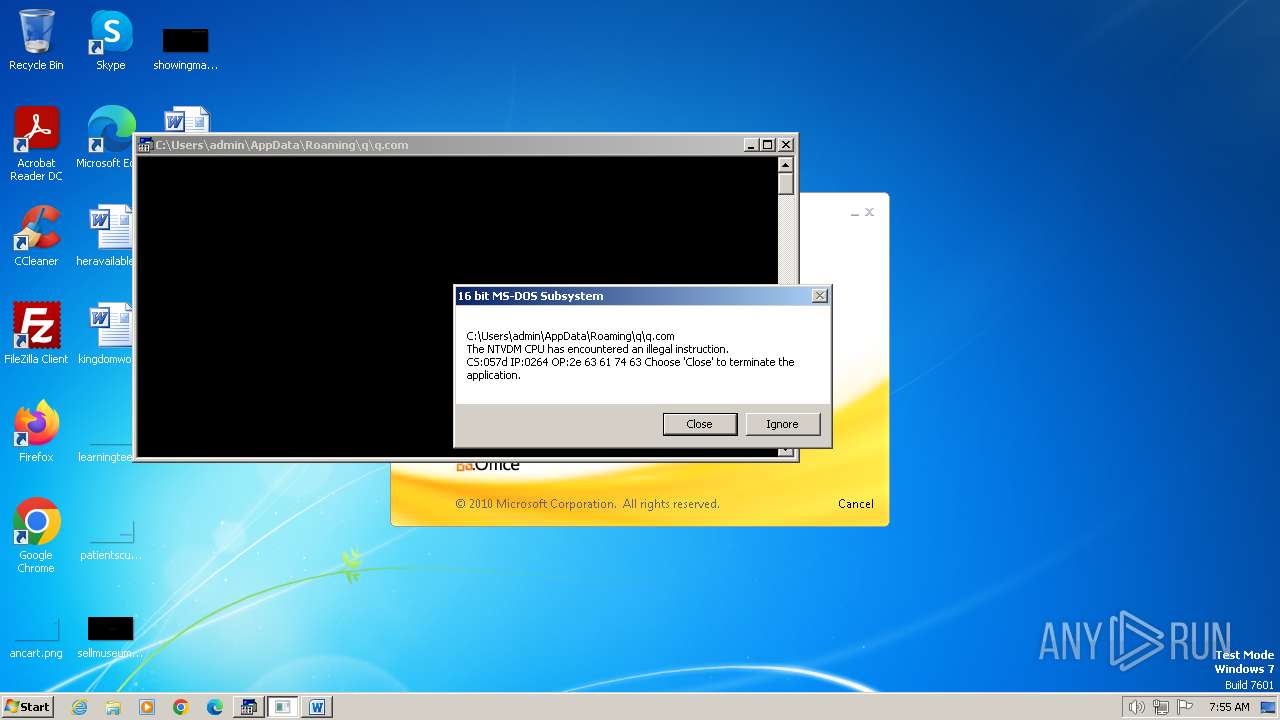
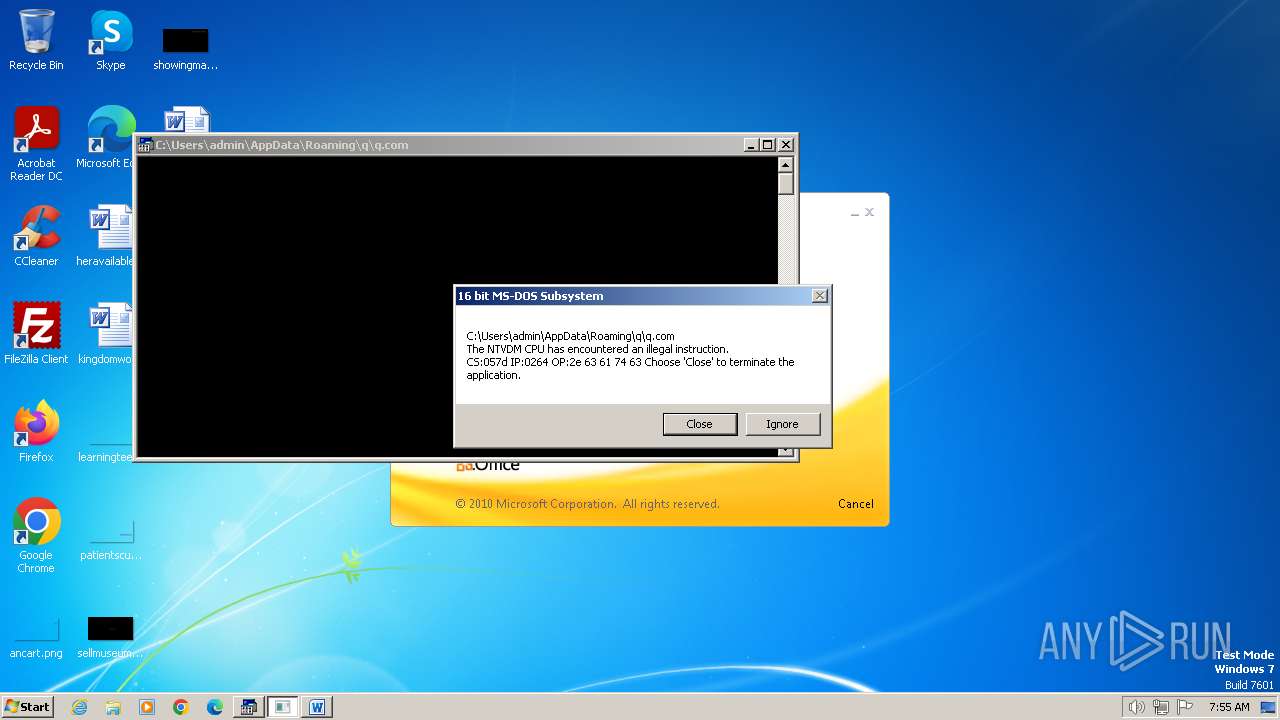
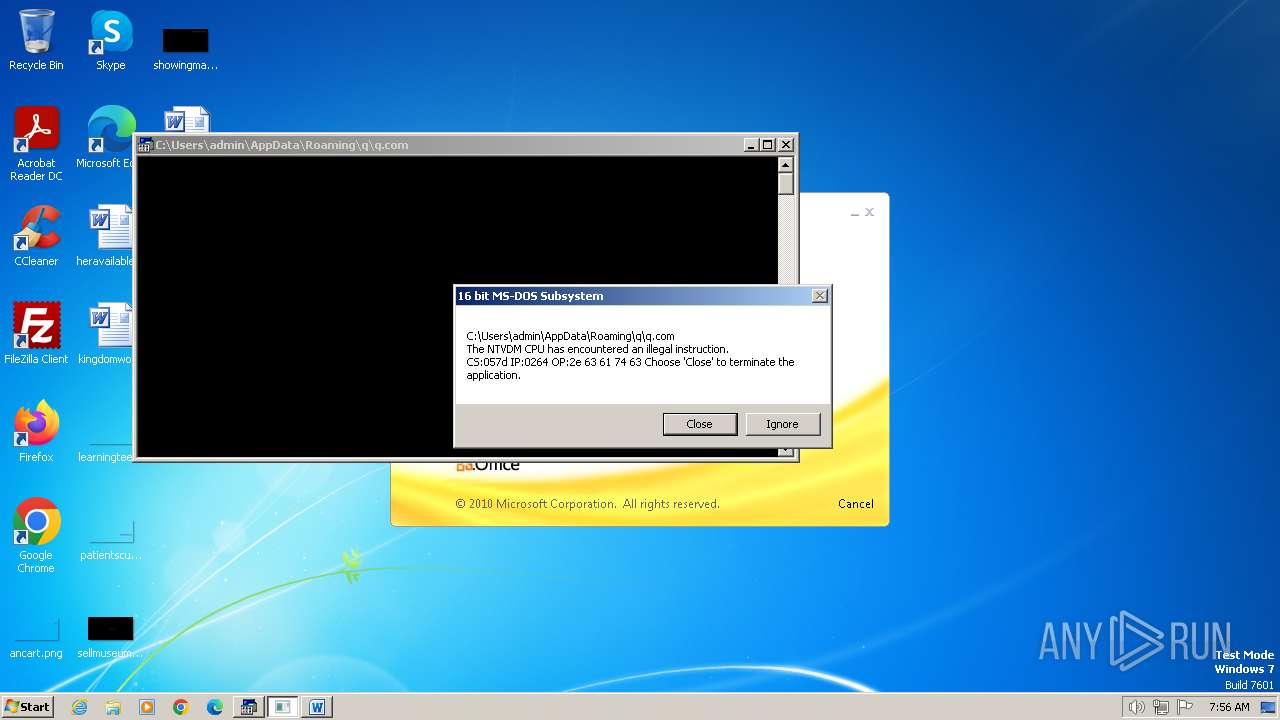
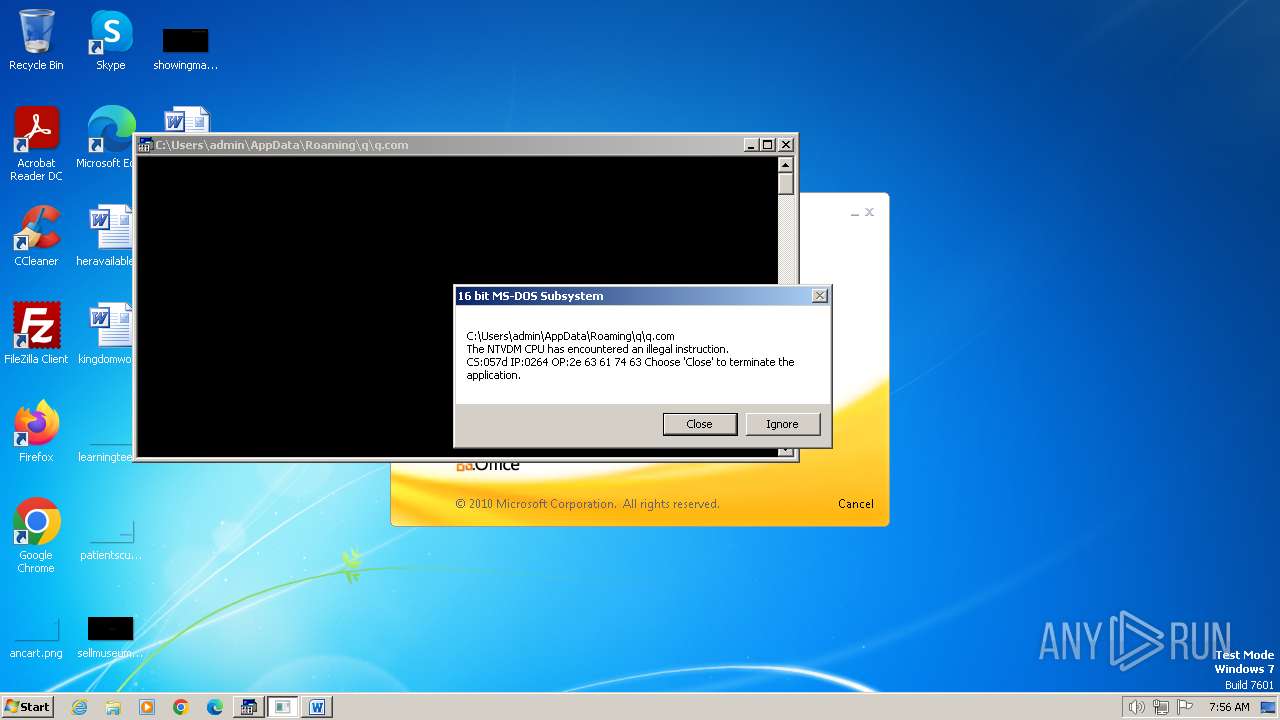
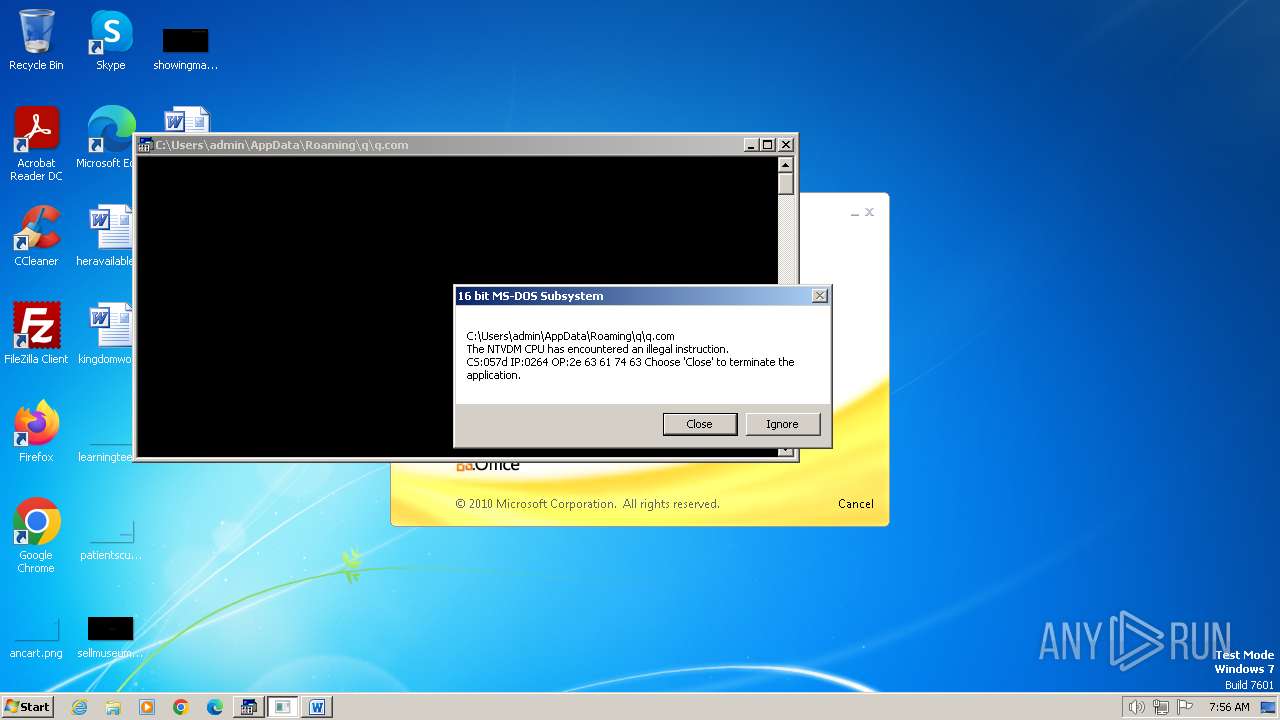
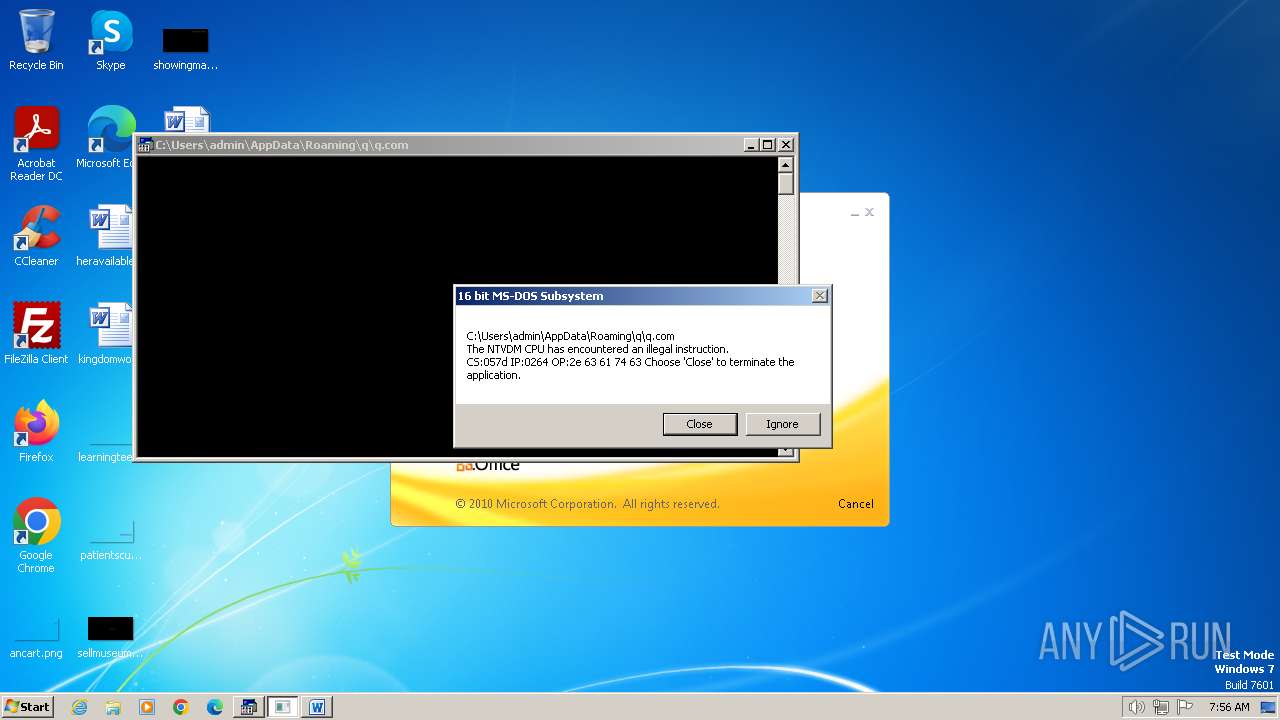
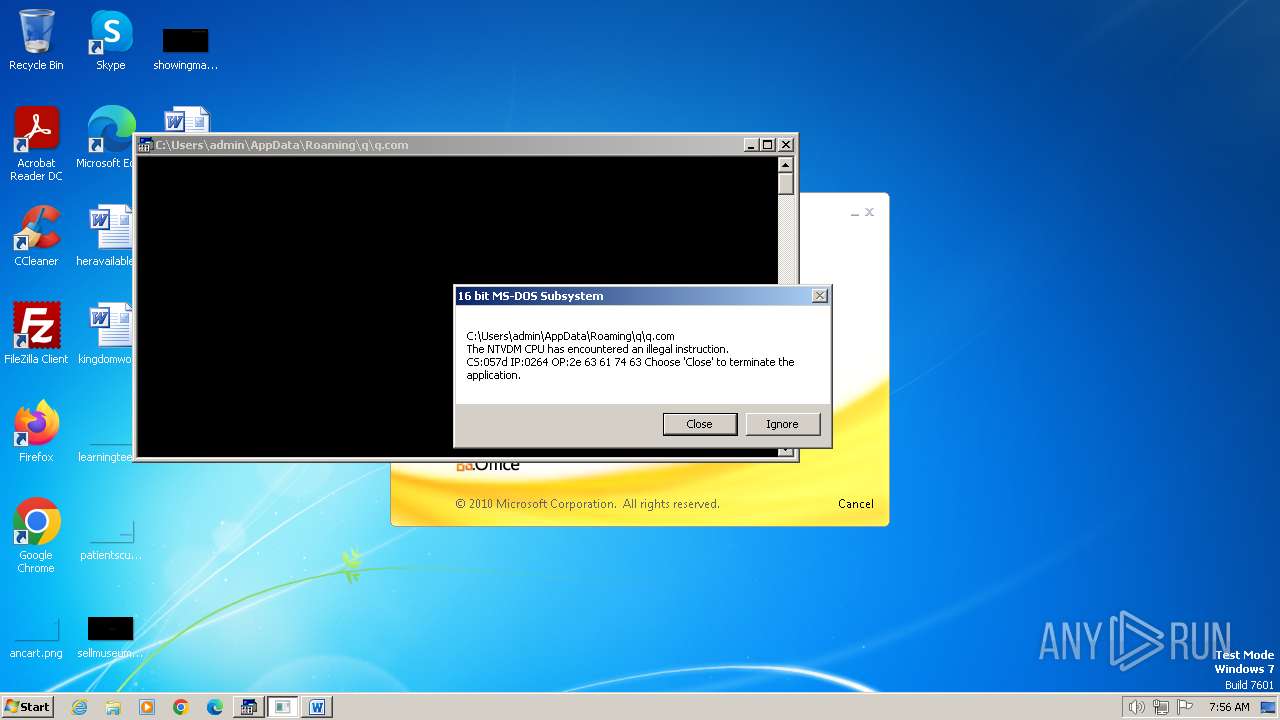
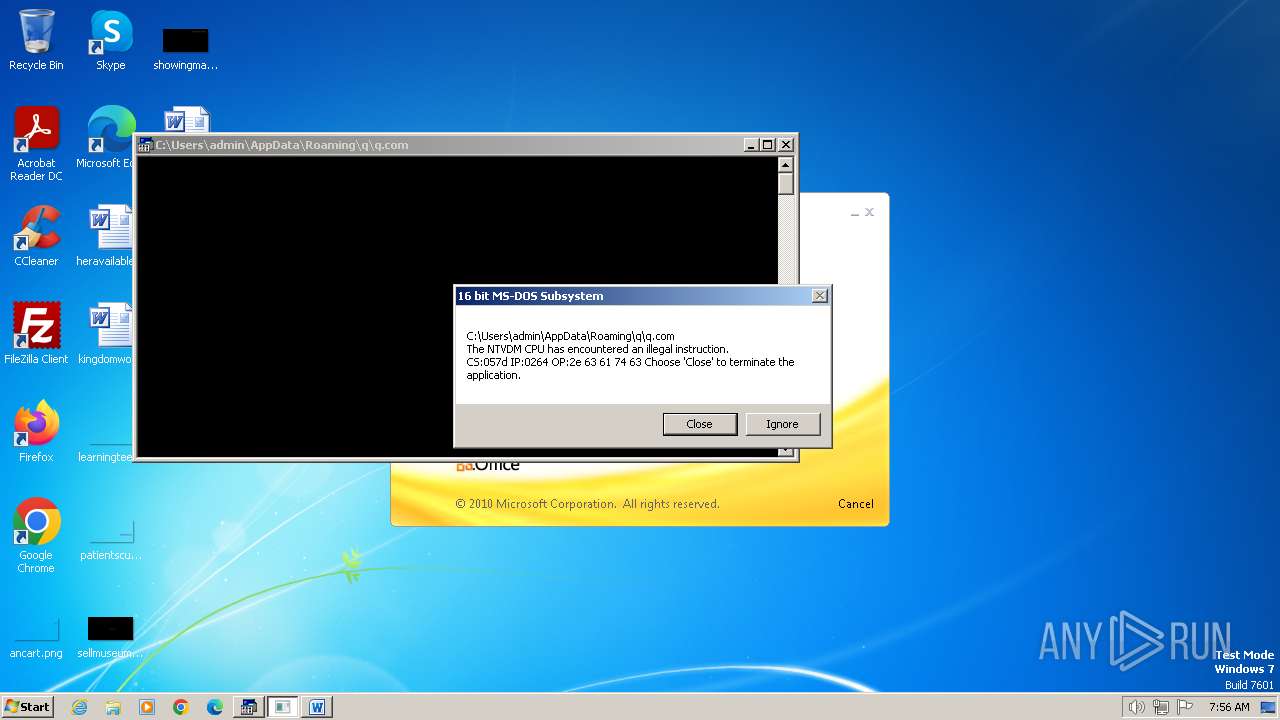
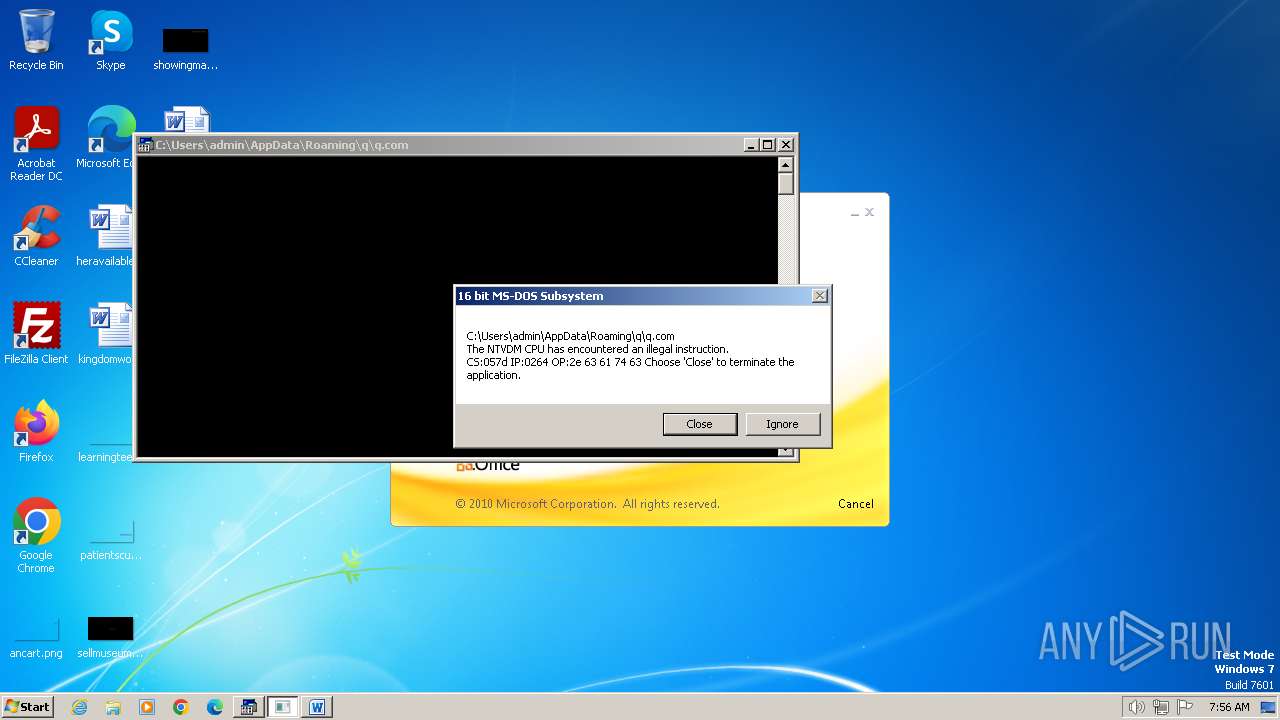
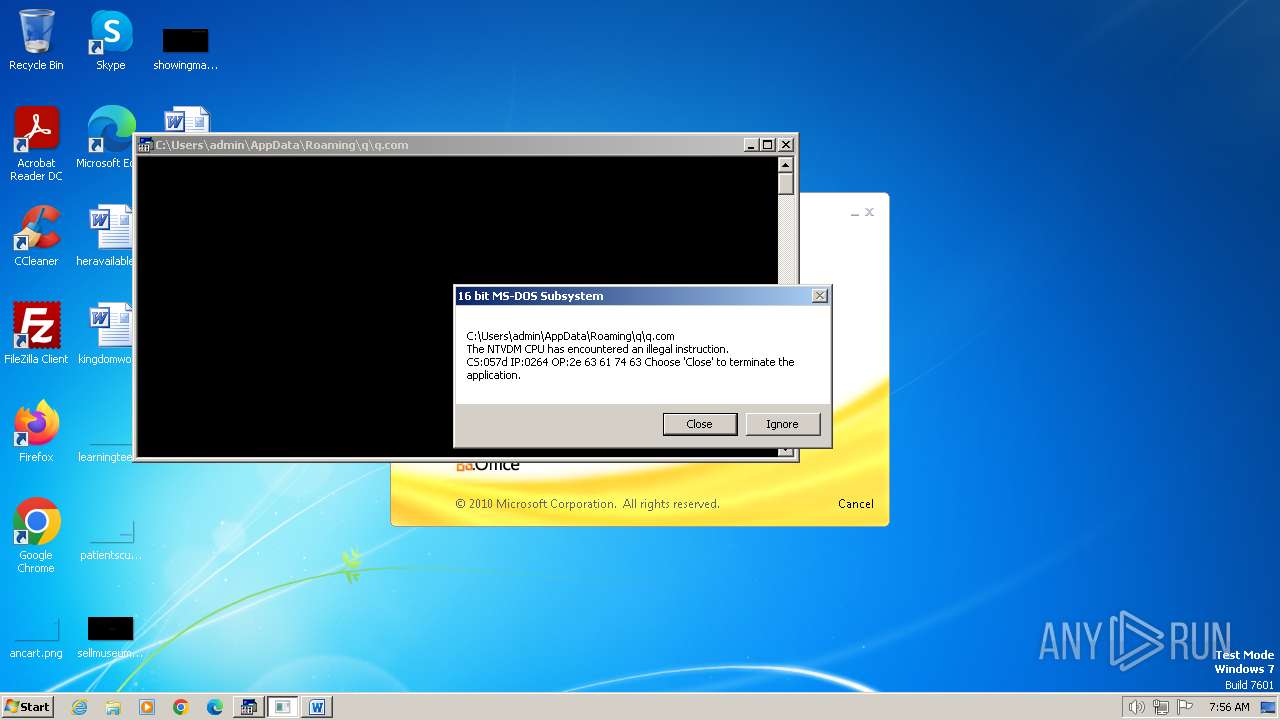
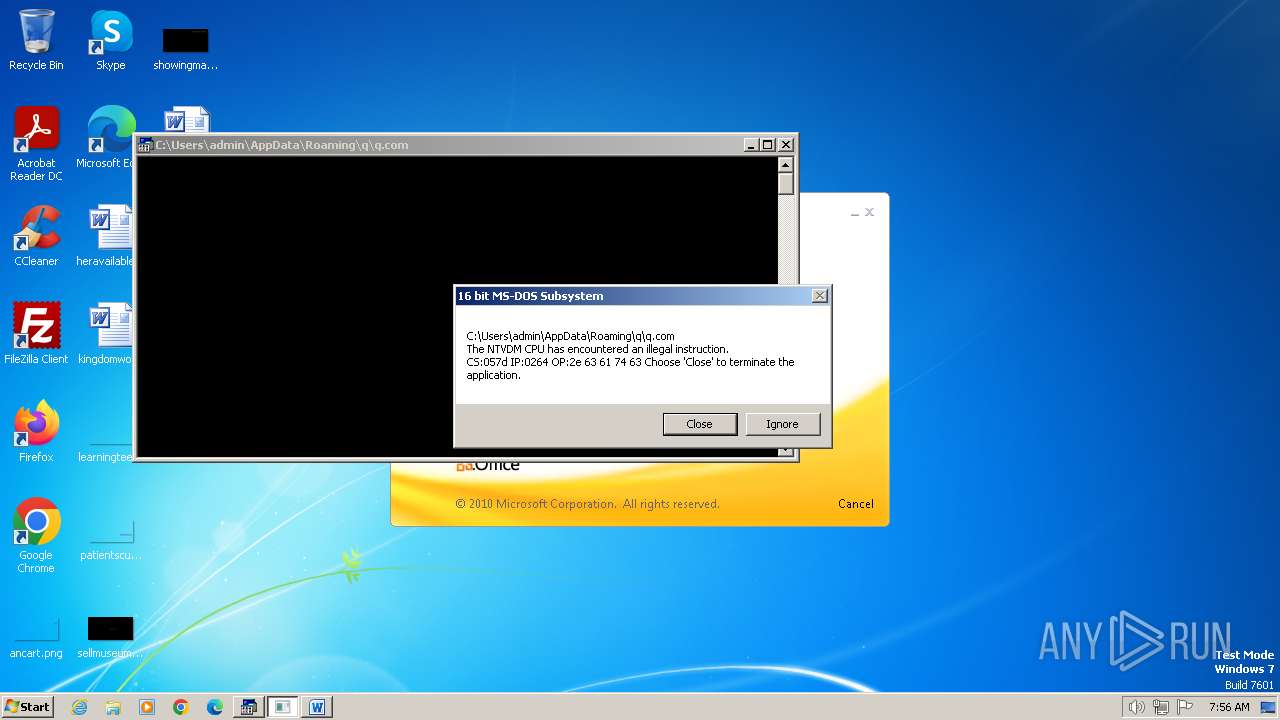
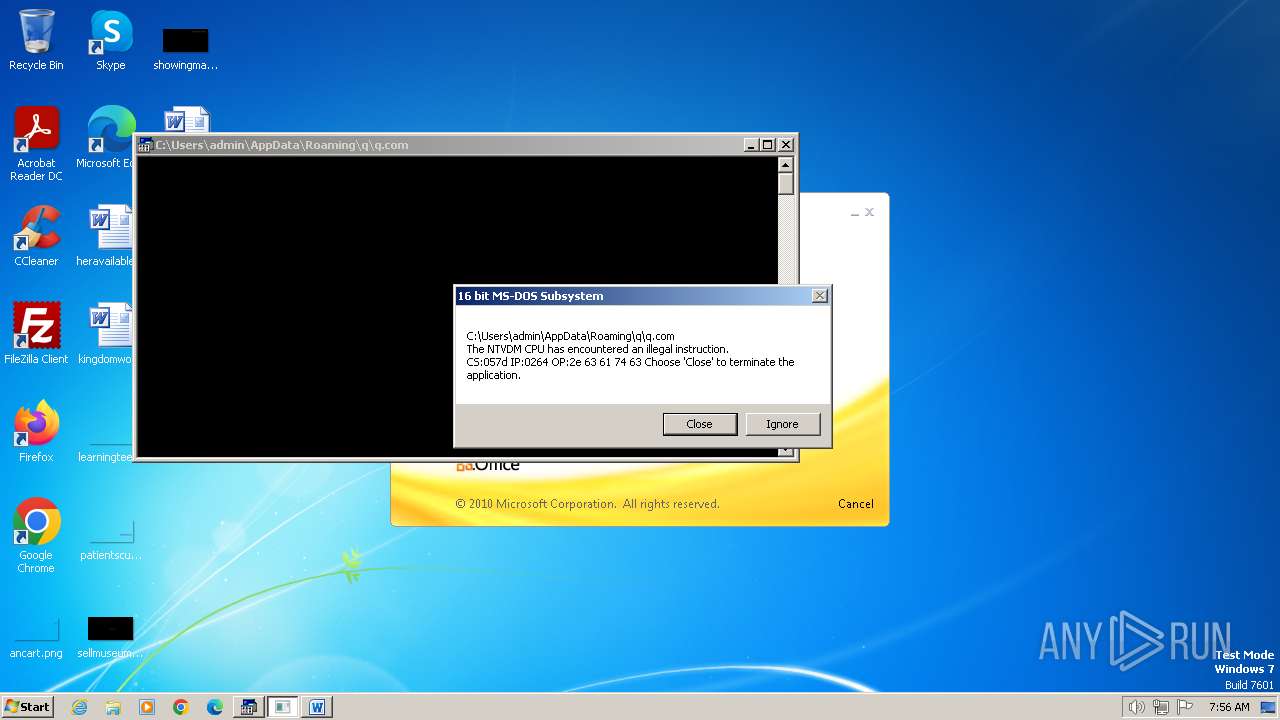
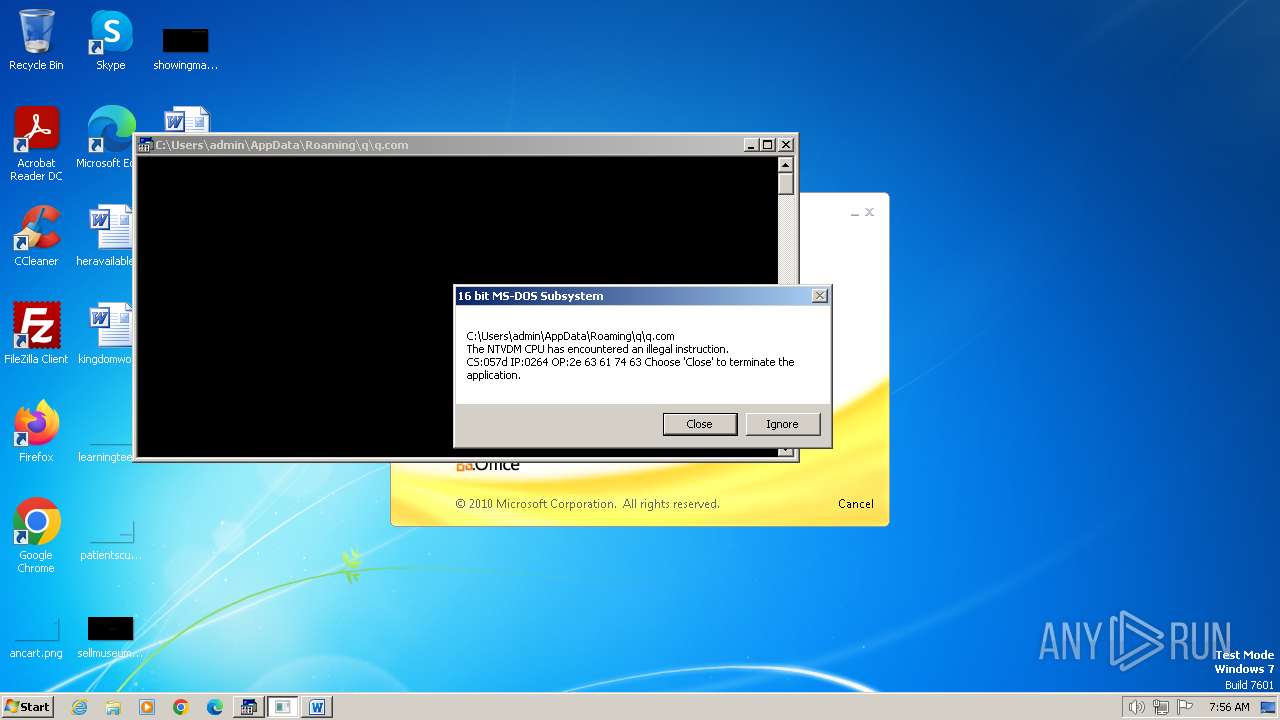
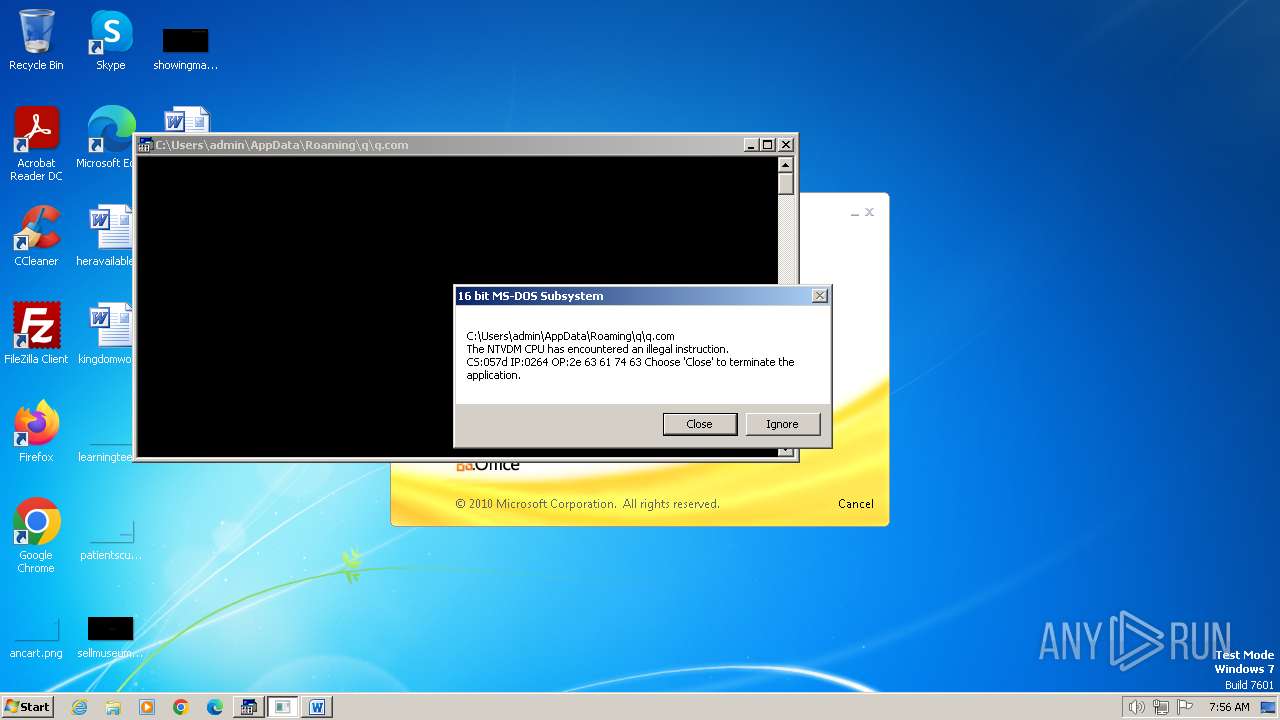
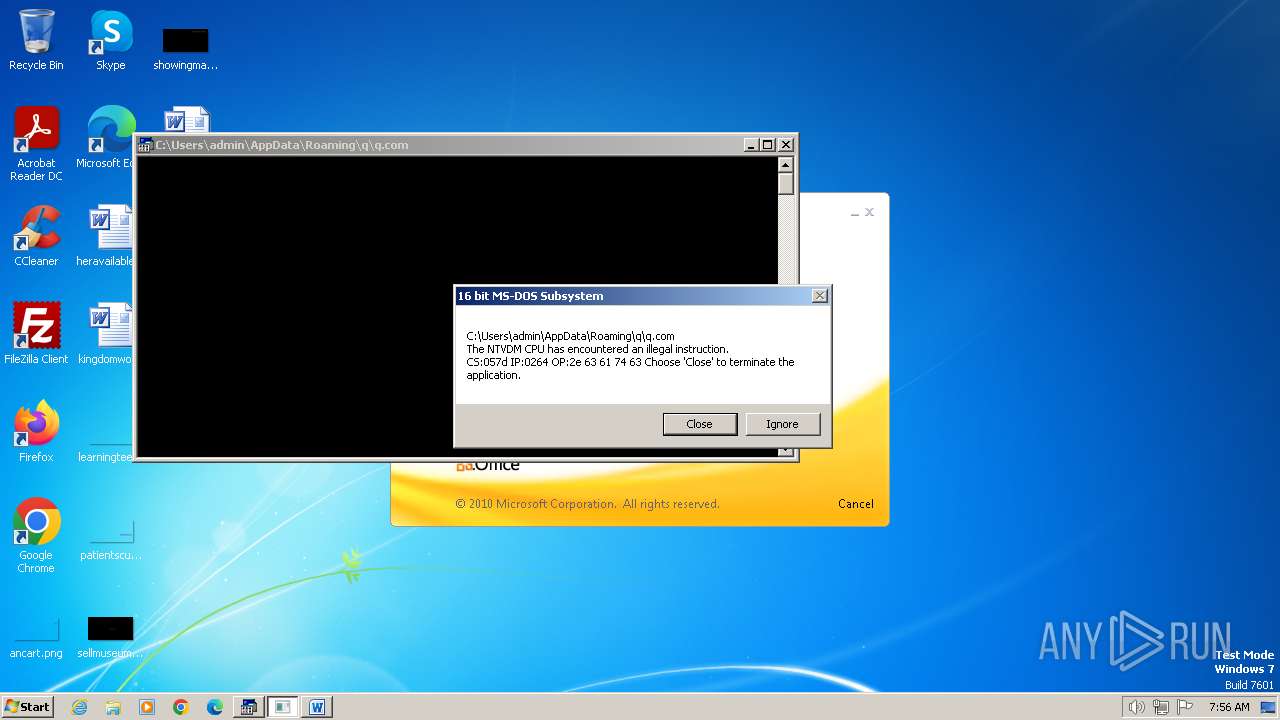
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\q\q.com | html | |
MD5:3B03D93D3487806337B5C6443CE7A62D | SHA256:7392749832C70FCFC2D440D7AFC2F880000DD564930D95D634EB1199FA15DE30 | |||
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\20014[1].htm | html | |
MD5:3B03D93D3487806337B5C6443CE7A62D | SHA256:7392749832C70FCFC2D440D7AFC2F880000DD564930D95D634EB1199FA15DE30 | |||
| 2852 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsF2CC.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 2852 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsF2DD.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
5
DNS requests
1
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2472 | WINWORD.EXE | GET | 200 | 64.225.91.73:80 | http://softtonic.biz/cr/20014.exe | unknown | compressed | 336 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2472 | WINWORD.EXE | 64.225.91.73:80 | softtonic.biz | DIGITALOCEAN-ASN | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
softtonic.biz |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
2472 | WINWORD.EXE | A Network Trojan was detected | ET MALWARE Possible Malicious Macro EXE DL AlphaNumL |
2472 | WINWORD.EXE | A Network Trojan was detected | ET MALWARE Possible Malicious Macro DL EXE Feb 2016 |