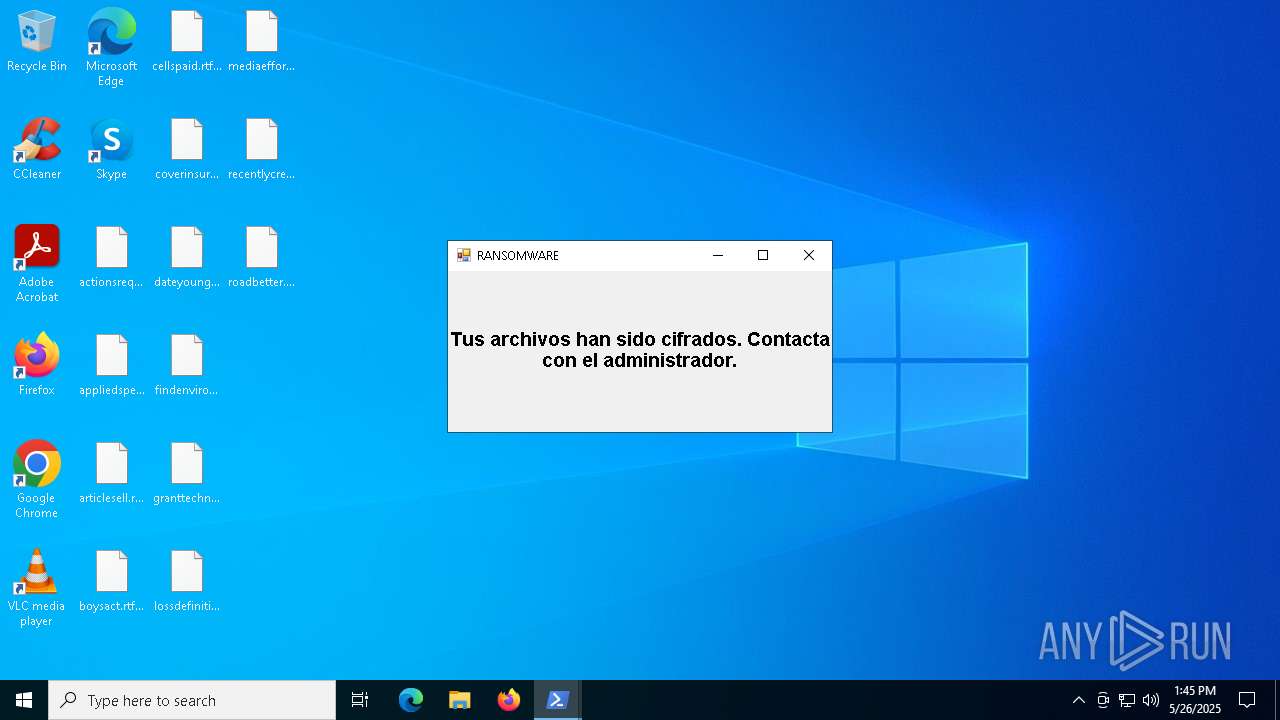
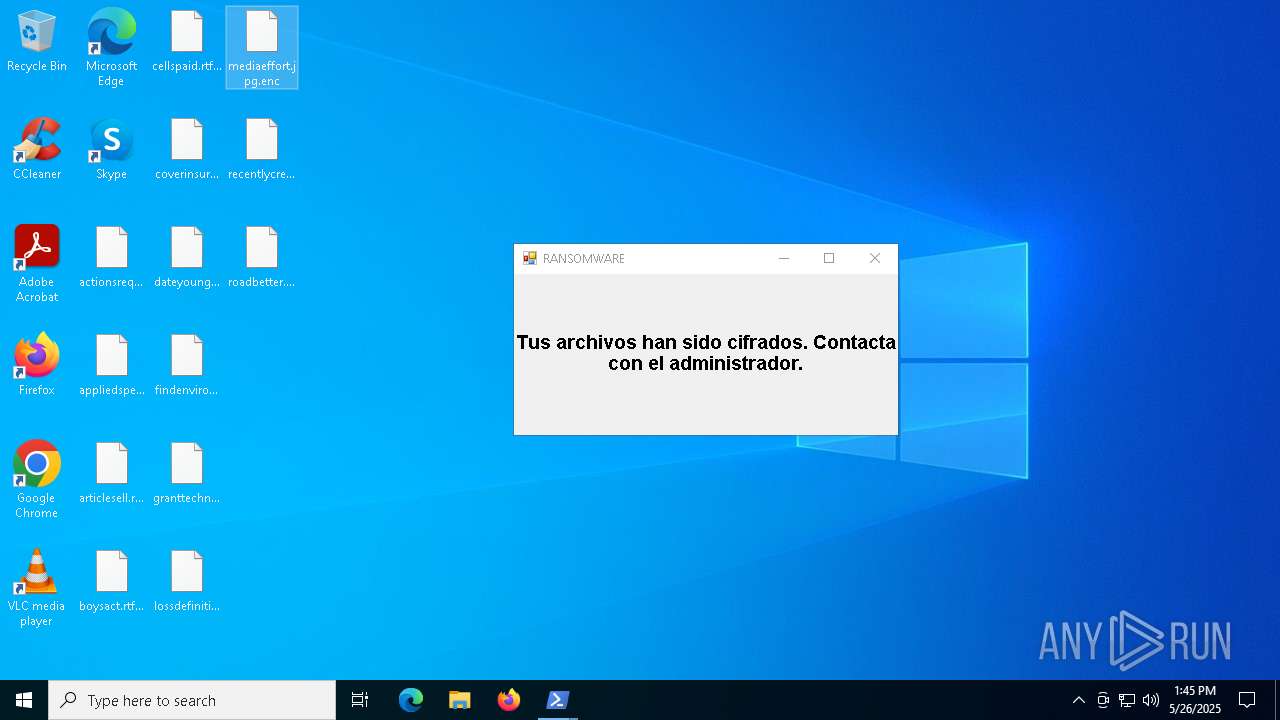
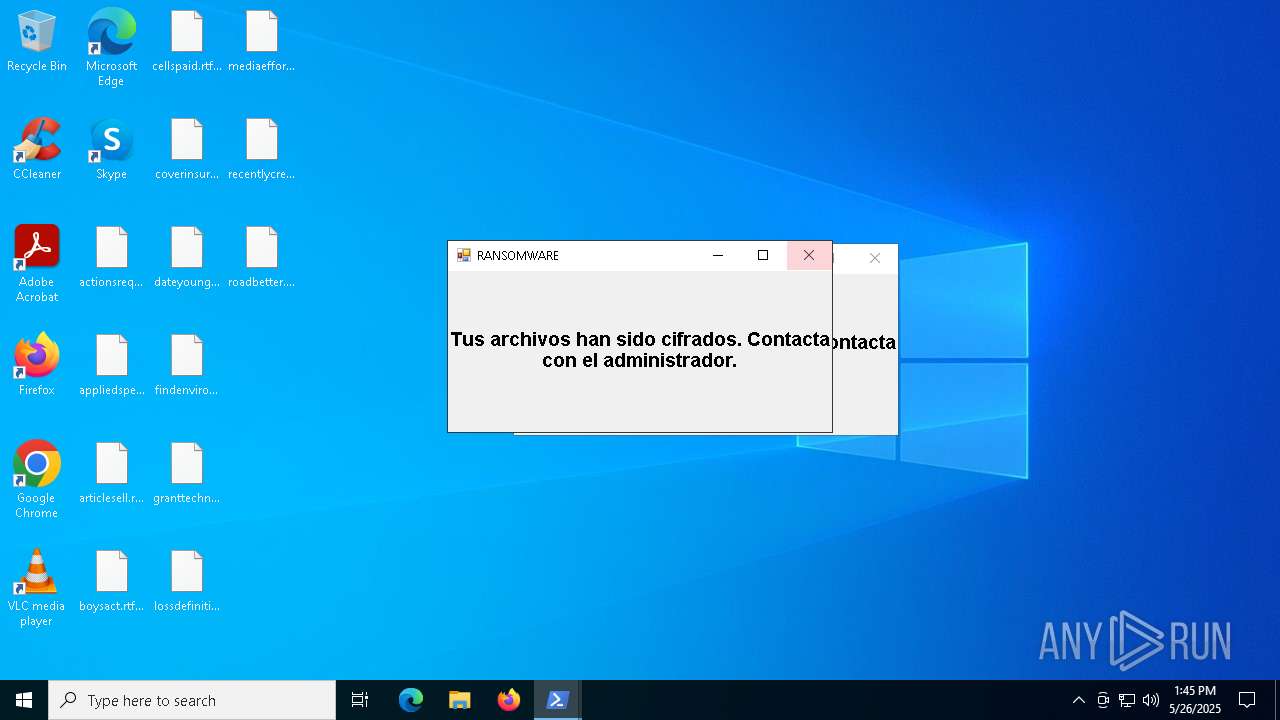
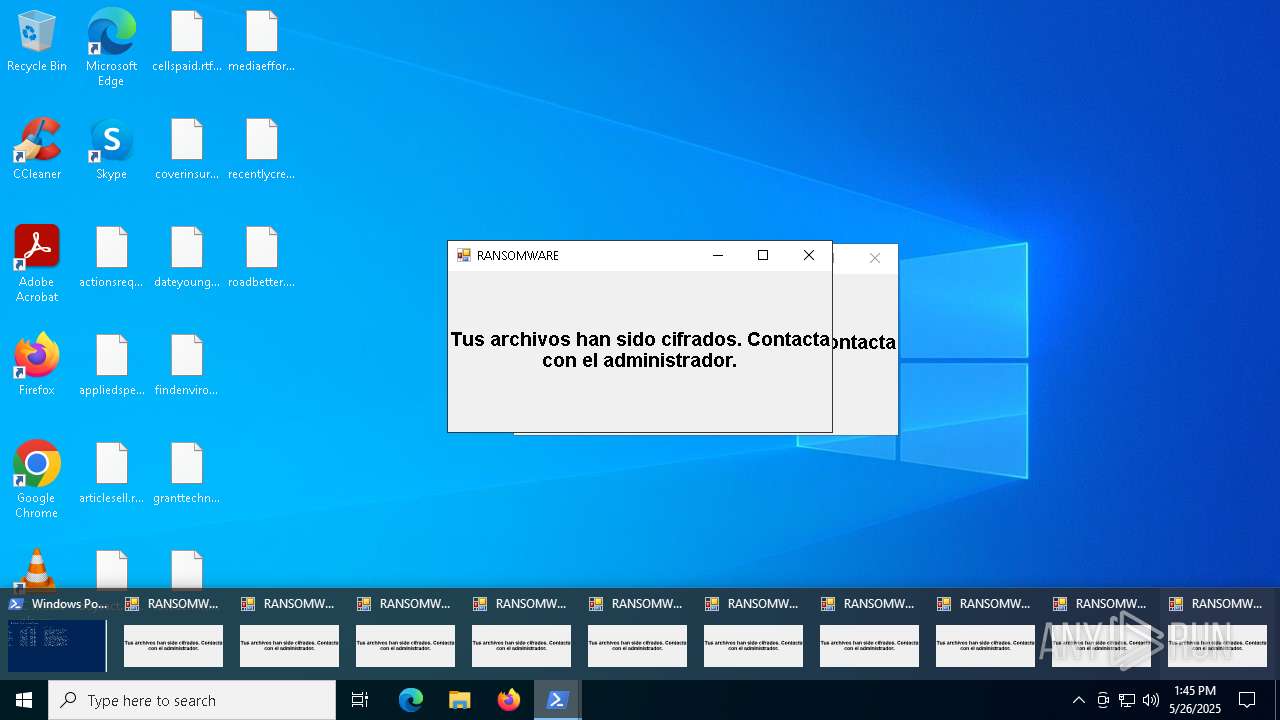
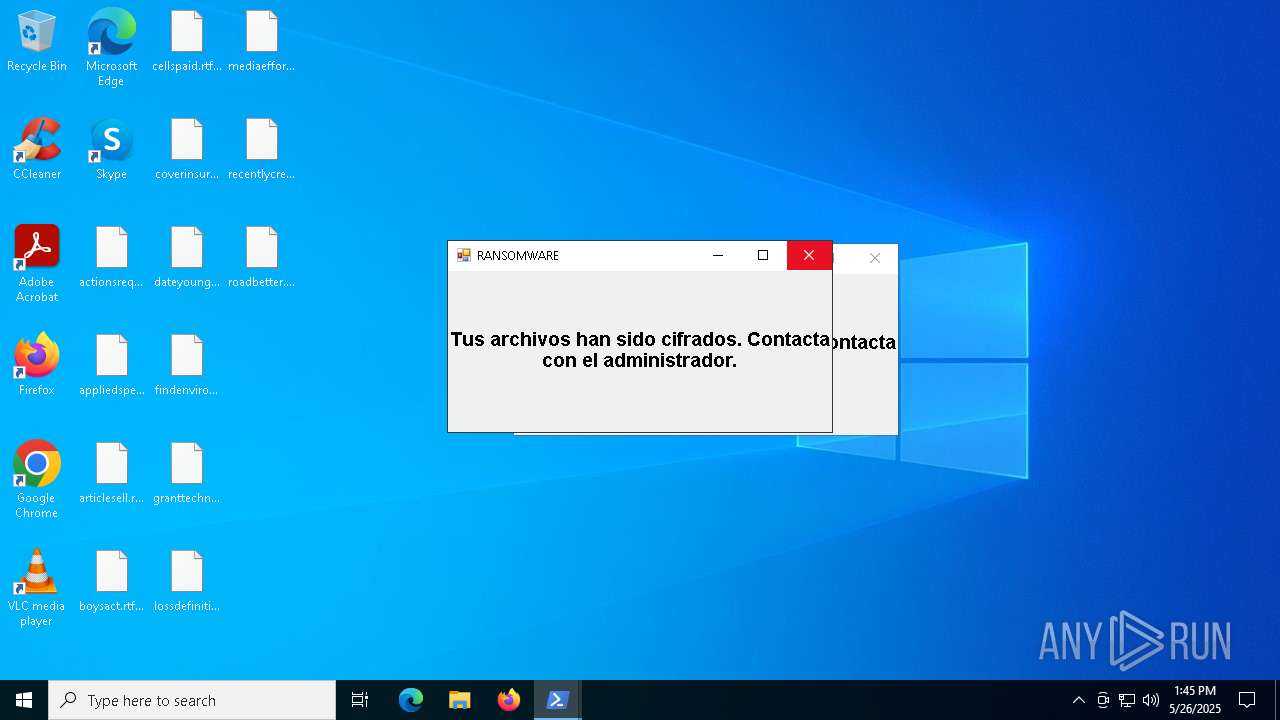
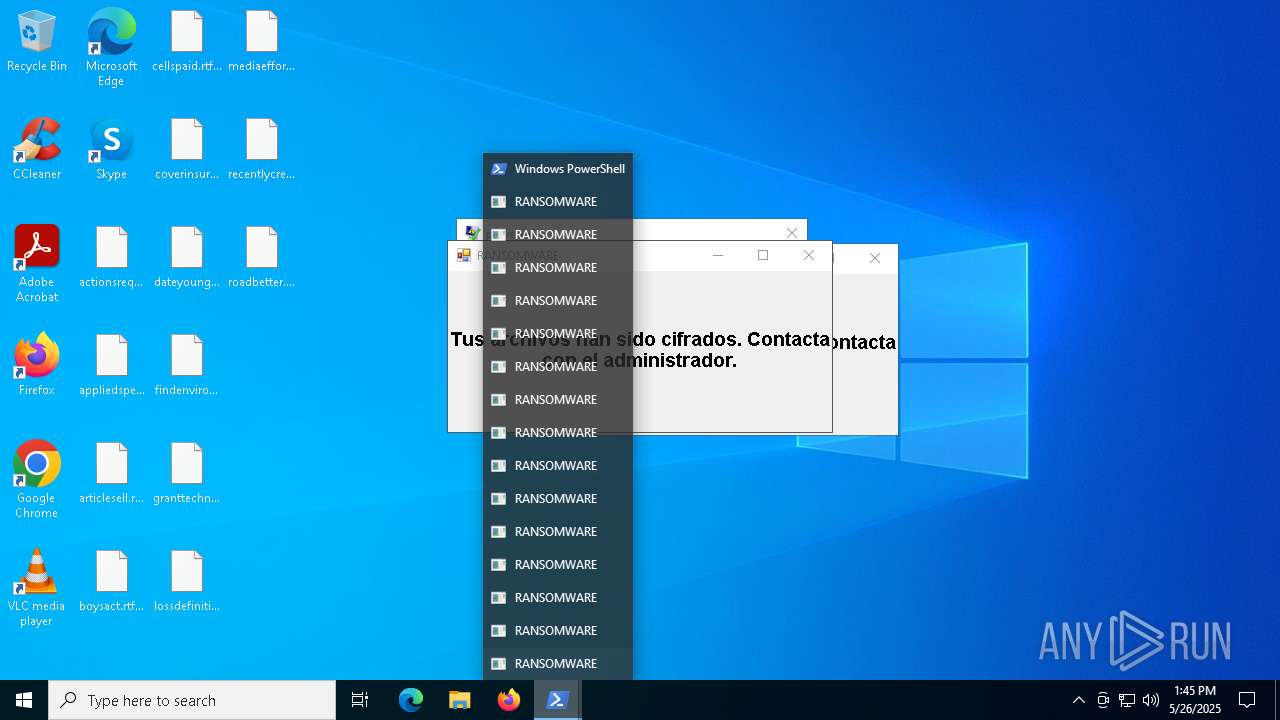
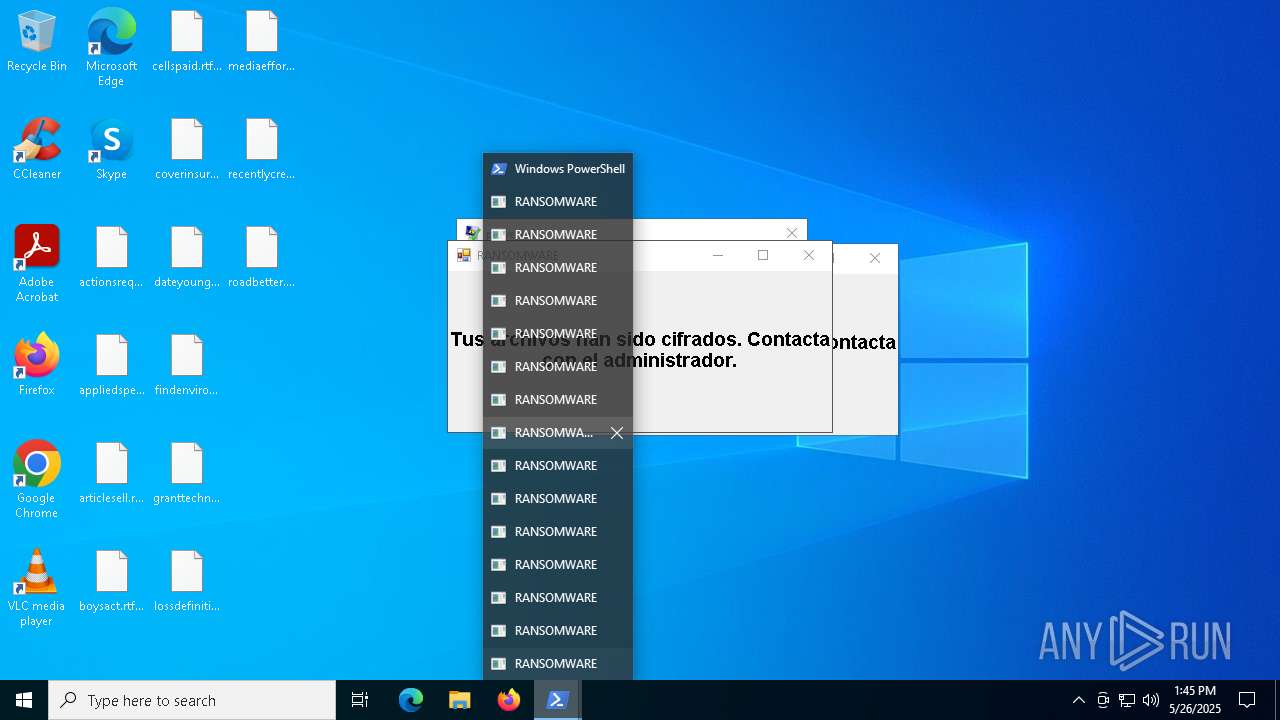
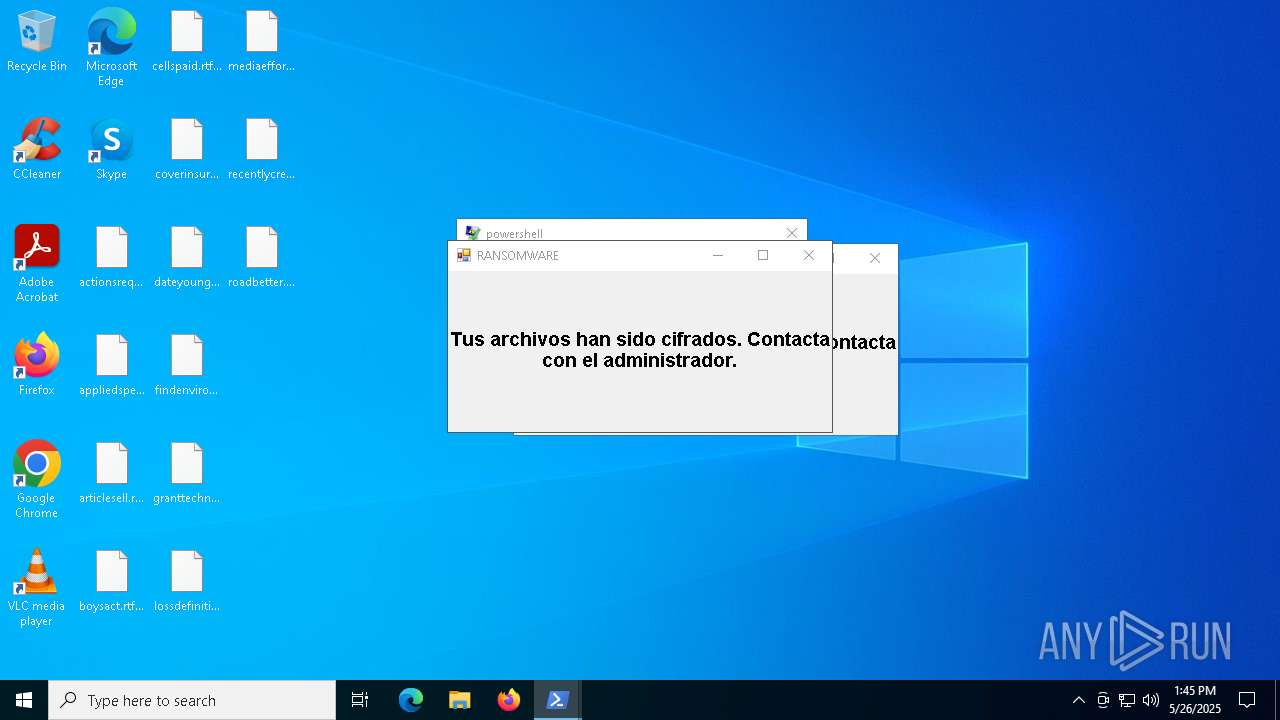
| File name: | ransom_full.ps1 |
| Full analysis: | https://app.any.run/tasks/27cf95d9-3a89-4ba3-8139-d9d53b92be30 |
| Verdict: | Malicious activity |
| Analysis date: | May 26, 2025, 13:44:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text |
| MD5: | 432B0DD915AE7AAC516F6499E3510E3A |
| SHA1: | E2D605AC670C8DFEA73C208A6305F2071470FC08 |
| SHA256: | 6EC7395D45B58665E9FBC0EE6D3A67F9B6D6E74CAA934020FFFC2A188053A4F2 |
| SSDEEP: | 192:we2FxI8OeO2EcenE/v8fFUiiVc5rtfNjxZex4Cy7KRgTKc:t2FZO7cb3yrxnZuRRgOc |
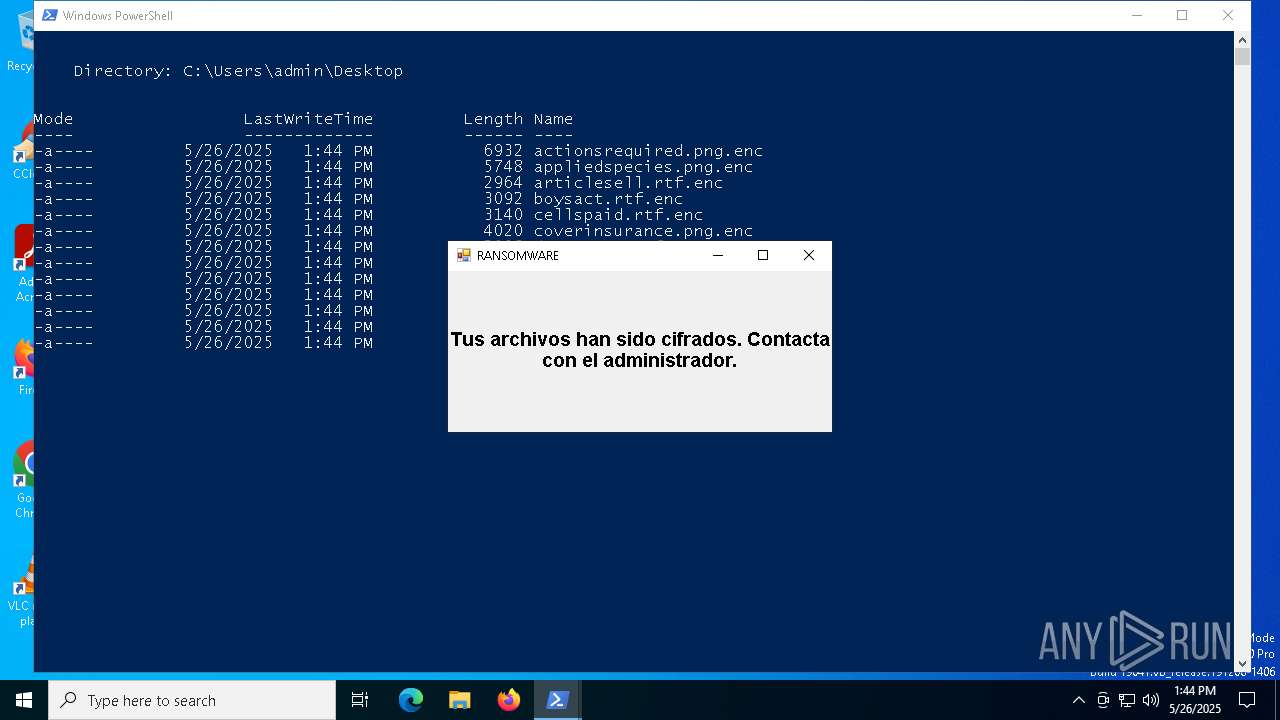
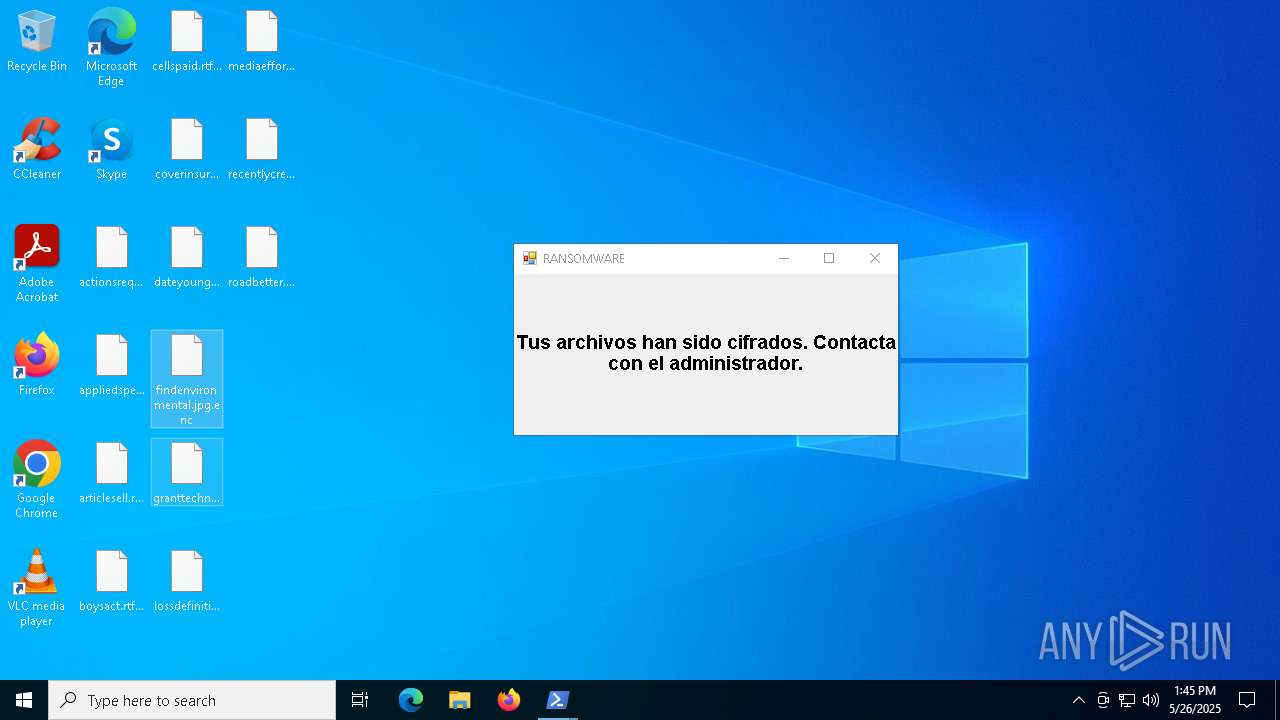
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 7512)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 7512)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 7512)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 7512)
SUSPICIOUS
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 7512)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7512)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 7512)
The process creates files with name similar to system file names
- wermgr.exe (PID: 8120)
INFO
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7512)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7512)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 7512)
Creates files in the program directory
- powershell.exe (PID: 7512)
Checks proxy server information
- wermgr.exe (PID: 8120)
Reads the software policy settings
- wermgr.exe (PID: 8120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
131
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7512 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\ransom_full.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7520 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 8120 | "C:\WINDOWS\system32\wermgr.exe" "-outproc" "0" "7512" "2876" "2900" "2880" "0" "0" "1140" "0" "0" "0" "0" "0" | C:\Windows\System32\wermgr.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 313
Read events
8 313
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
17
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7512 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ADJHHLK1N8JUU7RWU0VA.temp | binary | |
MD5:60CDA96DF71F60243177CC009A0BDDDF | SHA256:7CBF401895A87C58BC48B0E543824D34F4F3E050EF2E4174050C43B81E1FEC2D | |||
| 7512 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:60CDA96DF71F60243177CC009A0BDDDF | SHA256:7CBF401895A87C58BC48B0E543824D34F4F3E050EF2E4174050C43B81E1FEC2D | |||
| 8120 | wermgr.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\Critical_powershell.exe_cd6b96918c74ad6ac44ab8fec58e6dc57a9c95f6_00000000_983a933a-c5b6-450d-b9ff-da66e9d41d0f\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7512 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ixoprnpd.a4b.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
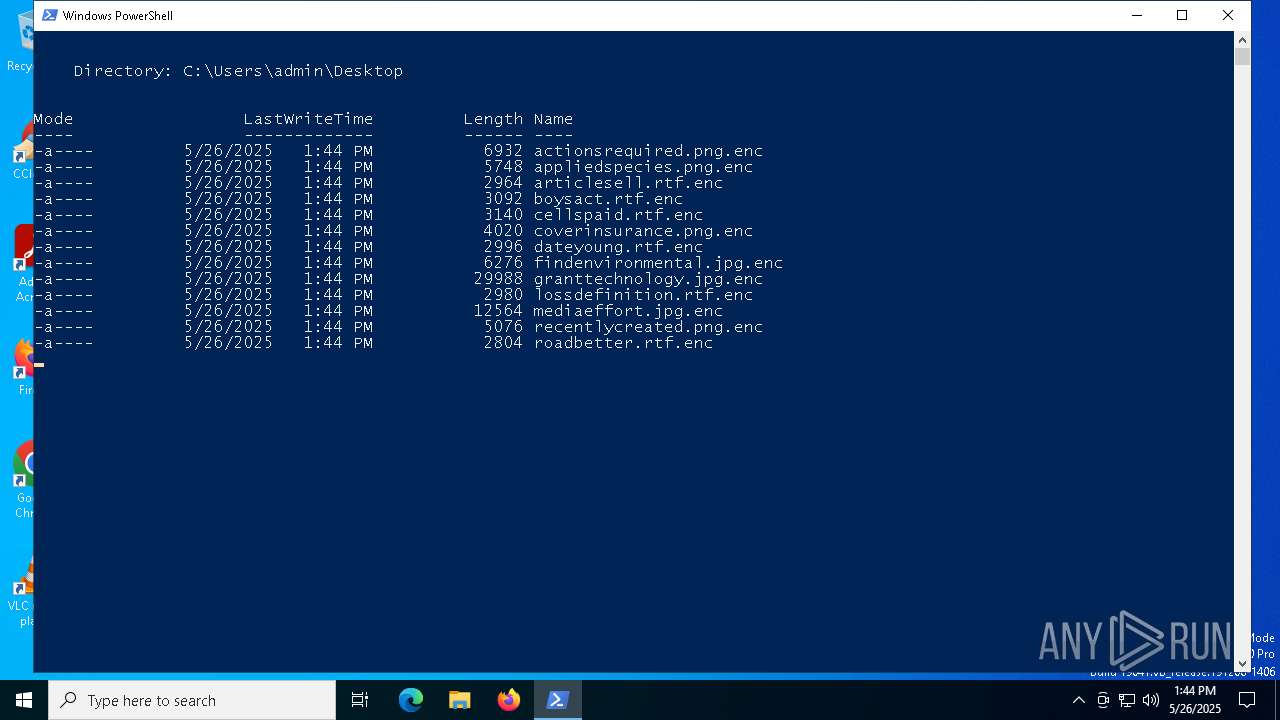
| 7512 | powershell.exe | C:\Users\admin\Desktop\findenvironmental.jpg.enc | binary | |
MD5:549B1360C4BB9BB4EB55BD52EDBFB2EE | SHA256:72F60AE25F81BCF15A0A71D47A7EF4E11D386BDED9402375FD4108FC81FBE036 | |||
| 7512 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qyouxsqg.qay.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7512 | powershell.exe | C:\Users\admin\Desktop\cellspaid.rtf.enc | binary | |
MD5:B1701397396311D1D403CAF74D63070A | SHA256:21061C49CA329CDBBF82568B549DBC19423EF62D1F08A530DDD49688ABDFD400 | |||
| 7512 | powershell.exe | C:\Users\admin\Desktop\granttechnology.jpg.enc | binary | |
MD5:74049F703CC411E8D3B7F6B0DEF618C5 | SHA256:E15552EC355A81CF355F70582E4A69D62CB019E77DA394E3364F154CF16FEC0C | |||
| 7512 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF10ac7e.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 7512 | powershell.exe | C:\Users\admin\Desktop\appliedspecies.png.enc | binary | |
MD5:5F45986772741E508D4C87E90913B309 | SHA256:DF57E5A764A4A29EDC5382C07A057B2A03F40F5680FD4F9BE070CC10636CC306 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
29
DNS requests
11
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7844 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7844 | SIHClient.exe | 40.69.42.241:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
8120 | wermgr.exe | 20.42.73.29:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
241.42.69.40.in-addr.arpa |
| unknown |
6.0.1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.7.0.0.0.0.3.0.1.3.0.6.2.ip6.arpa |
| unknown |
watson.events.data.microsoft.com |
| whitelisted |