| download: | files |
| Full analysis: | https://app.any.run/tasks/e8cd544c-125e-4329-999e-9a3e3b724fe6 |
| Verdict: | Malicious activity |
| Analysis date: | November 15, 2018, 20:29:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text |
| MD5: | 8CEC005A344D4AA0896C3E60468DB119 |
| SHA1: | 8EF55BC92D0C349419734BF2AB0F576BEA6A6CB7 |
| SHA256: | 6EC4F03D5DC8FF6271F065DBC860164FA12619B3341E74289377C338257C53E1 |
| SSDEEP: | 24:GgSU+L0sLbQRd/CWxKs9GTPGT+5HvKkGTlq+lGTLV9GTOGyGTqMU4a:0PQRXEskyayPRidk1Vra |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads internet explorer settings
- iexplore.exe (PID: 3320)
- iexplore.exe (PID: 3180)
Changes internet zones settings
- iexplore.exe (PID: 2924)
Application launched itself
- iexplore.exe (PID: 2924)
Reads Internet Cache Settings
- iexplore.exe (PID: 2924)
- iexplore.exe (PID: 3320)
- iexplore.exe (PID: 3180)
Creates files in the user directory
- iexplore.exe (PID: 2924)
- iexplore.exe (PID: 3320)
- iexplore.exe (PID: 3180)
Reads settings of System Certificates
- iexplore.exe (PID: 3180)
- iexplore.exe (PID: 2924)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2924)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3180)
Changes settings of System certificates
- iexplore.exe (PID: 2924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
Total processes
35
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2924 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\files.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3180 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2924 CREDAT:203009 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3320 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2924 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
714
Read events
582
Write events
128
Delete events
4
Modification events
| (PID) Process: | (2924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {2F970DB9-E915-11E8-A67C-5254004AAD11} |
Value: 0 | |||
| (PID) Process: | (3320) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Type |
Value: 3 | |||
| (PID) Process: | (3320) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (3320) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070B0004000F0014001D002D00BF01 | |||
Executable files
0
Suspicious files
1
Text files
44
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2924 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3180 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\you4help_gq[1].htm | — | |
MD5:— | SHA256:— | |||
| 2924 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF1F32E7D80470FCBE.TMP | — | |
MD5:— | SHA256:— | |||
| 3180 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\c6yakb443v3kst0qt7qj2f4n[1].php | — | |
MD5:— | SHA256:— | |||
| 3180 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U2ZG9DE0\9j58tps4i34yzuipqm9r9wpe[1].php | — | |
MD5:— | SHA256:— | |||
| 2924 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{2F970DBA-E915-11E8-A67C-5254004AAD11}.dat | binary | |
MD5:— | SHA256:— | |||
| 2924 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:— | SHA256:— | |||
| 3180 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012018111520181116\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3320 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2YPIJ90\background_gradient[1] | image | |
MD5:20F0110ED5E4E0D5384A496E4880139B | SHA256:1471693BE91E53C2640FE7BAEECBC624530B088444222D93F2815DFCE1865D5B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
20
DNS requests
7
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
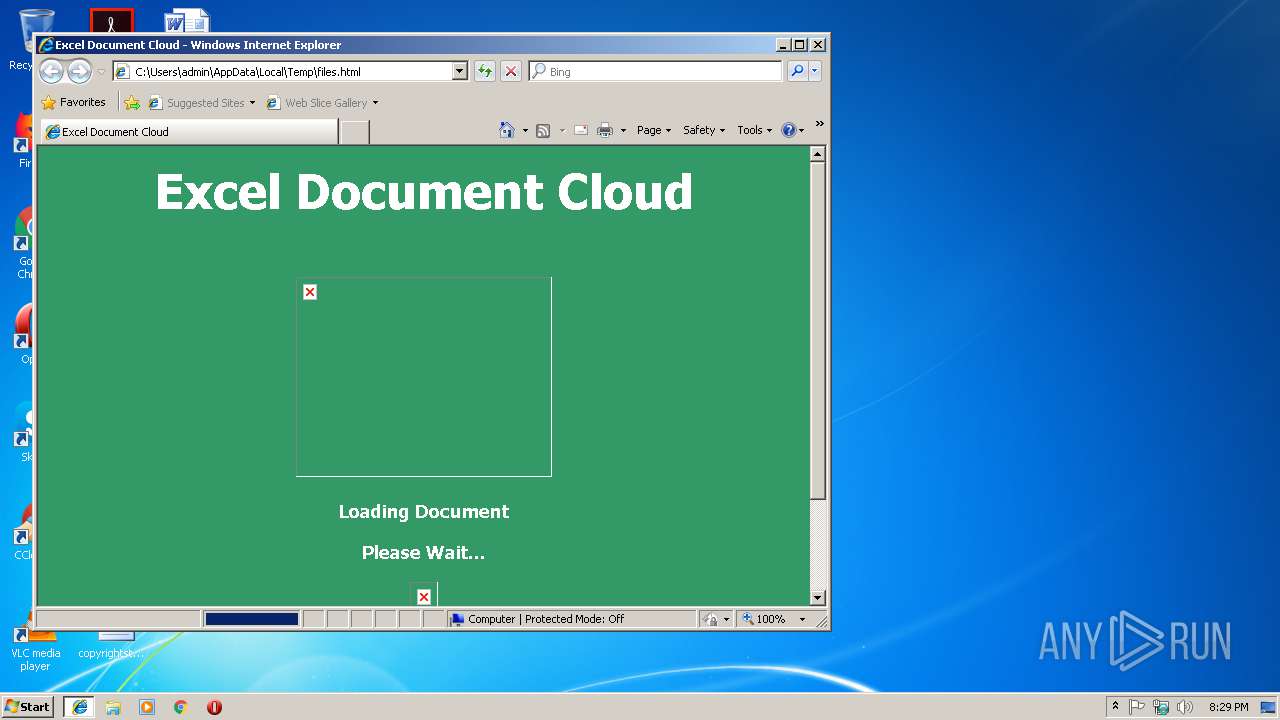
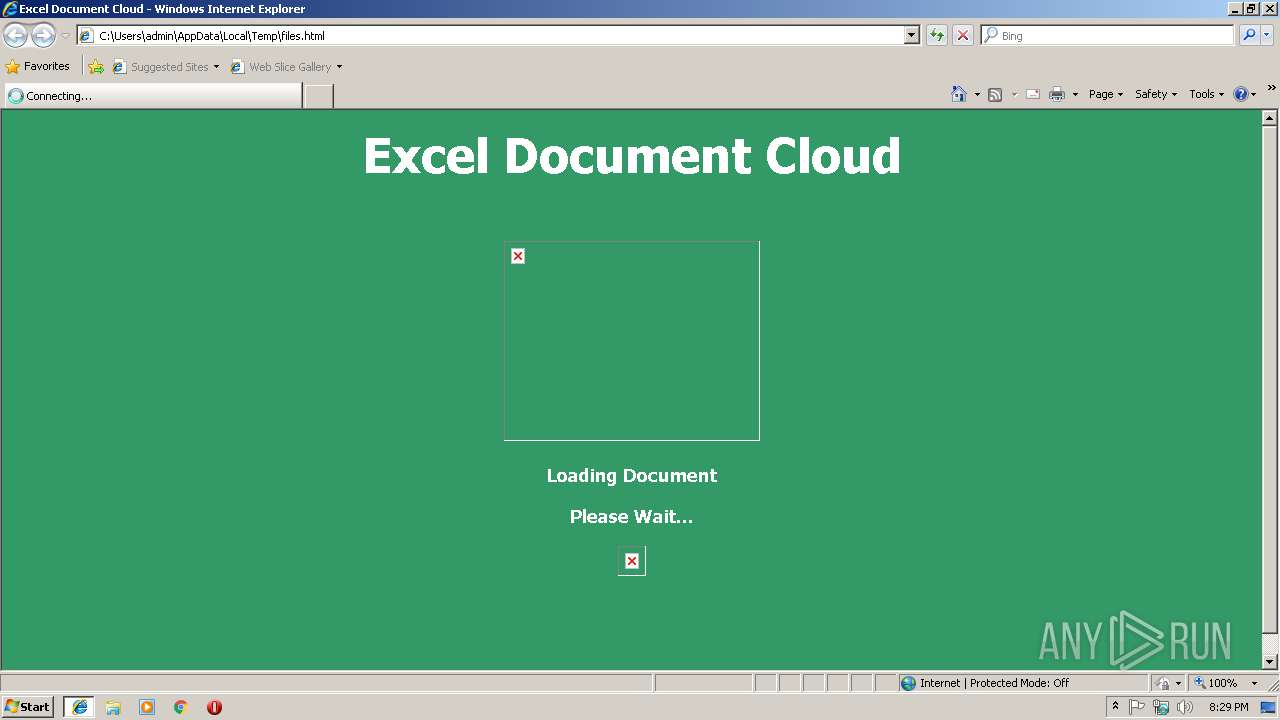
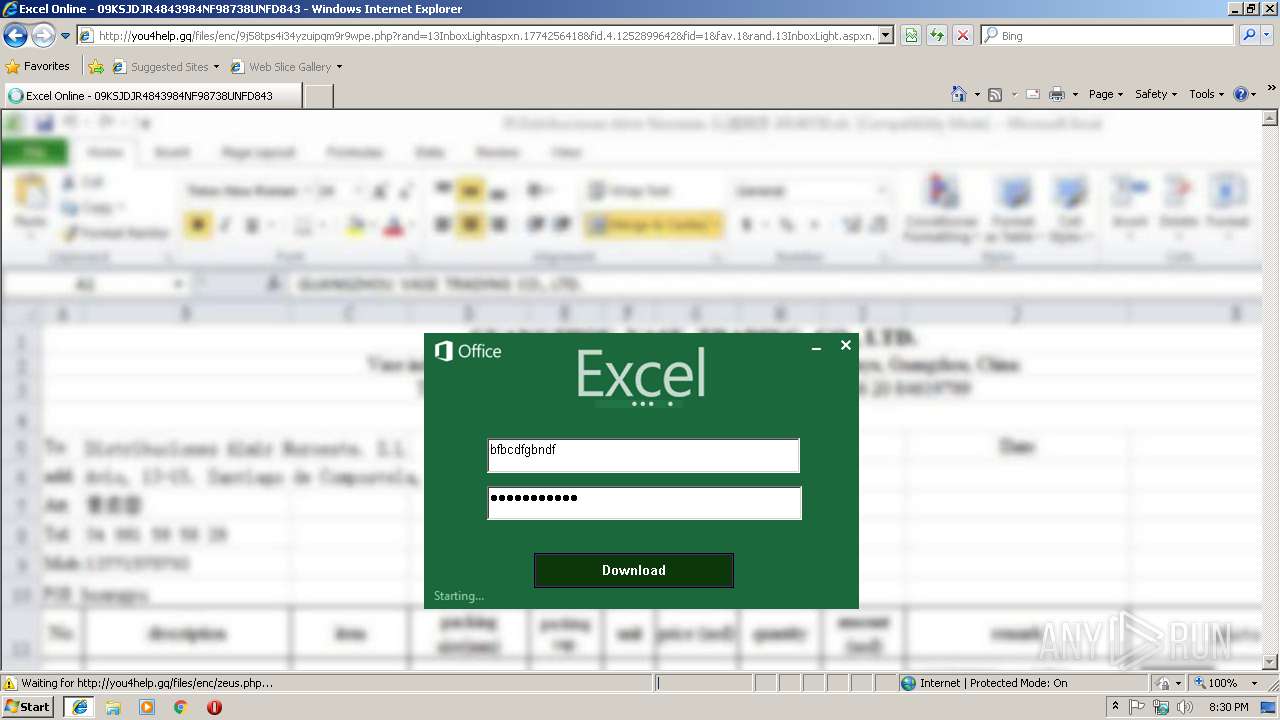
3180 | iexplore.exe | GET | 200 | 138.68.19.60:80 | http://you4help.gq/ | US | — | — | malicious |
3180 | iexplore.exe | GET | 302 | 138.68.19.60:80 | http://you4help.gq/files/enc/enc.php?email=&.rand=13vqcr8bp0gud&lc=1033&id=64855&mkt=en-us&cbcxt=mai&snsc=1 | US | image | 2.20 Kb | malicious |
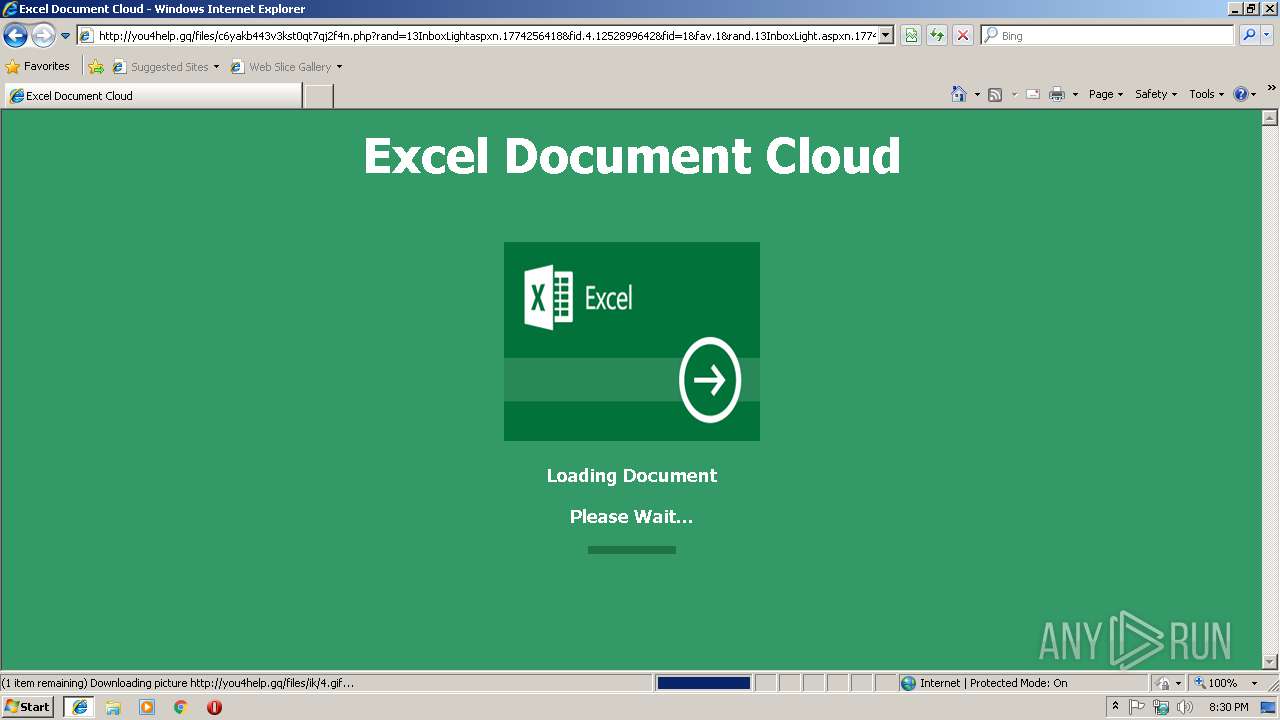
3180 | iexplore.exe | GET | 301 | 138.68.19.60:80 | http://you4help.gq/files | US | html | 233 b | malicious |
3180 | iexplore.exe | GET | 200 | 138.68.19.60:80 | http://you4help.gq/files/c6yakb443v3kst0qt7qj2f4n.php?rand=13InboxLightaspxn.1774256418&fid.4.1252899642&fid=1&fav.1&rand.13InboxLight.aspxn.1774256418&fid.1252899642&fid.1&fav.1&email=&.rand=13InboxLight.aspx?n=1774256418&fid=4 | US | html | 1.11 Kb | malicious |
3180 | iexplore.exe | GET | 302 | 138.68.19.60:80 | http://you4help.gq/files/ | US | html | 233 b | malicious |
3180 | iexplore.exe | GET | 200 | 138.68.19.60:80 | http://you4help.gq/files/ik/d60da137-271e-492a-b2f8-98d8de6bcc2b.png | US | image | 2.20 Kb | malicious |
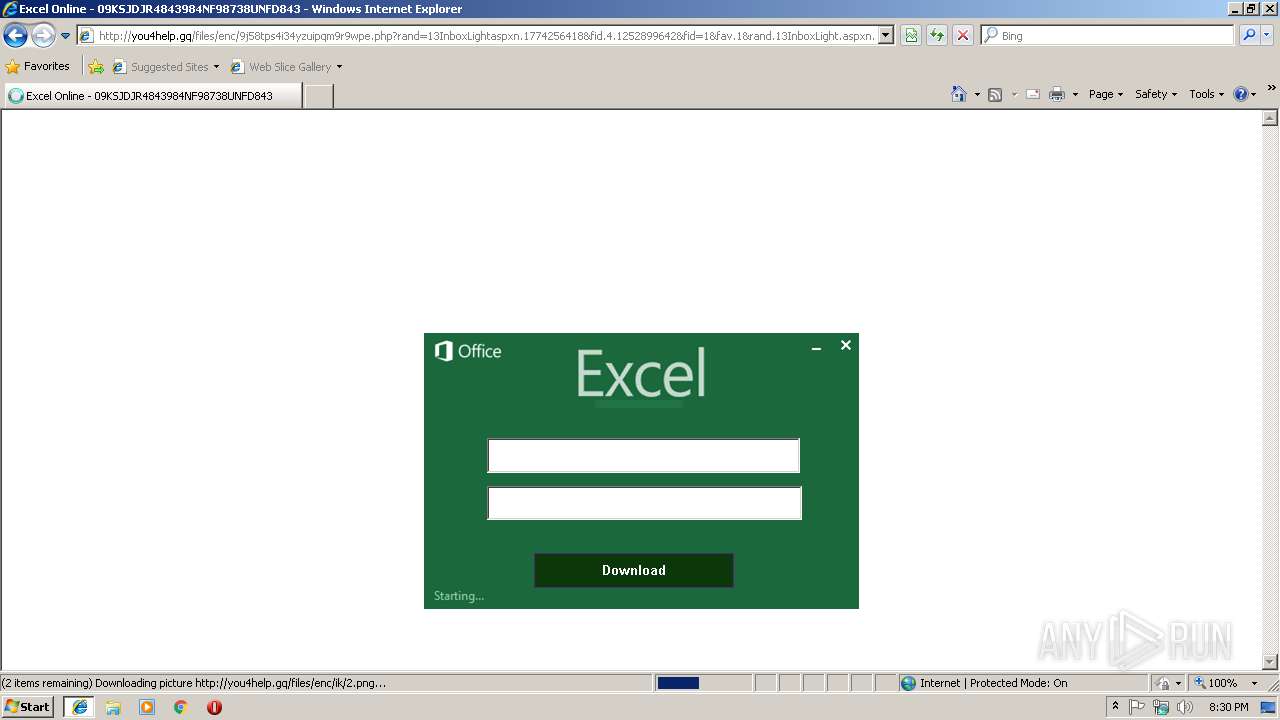
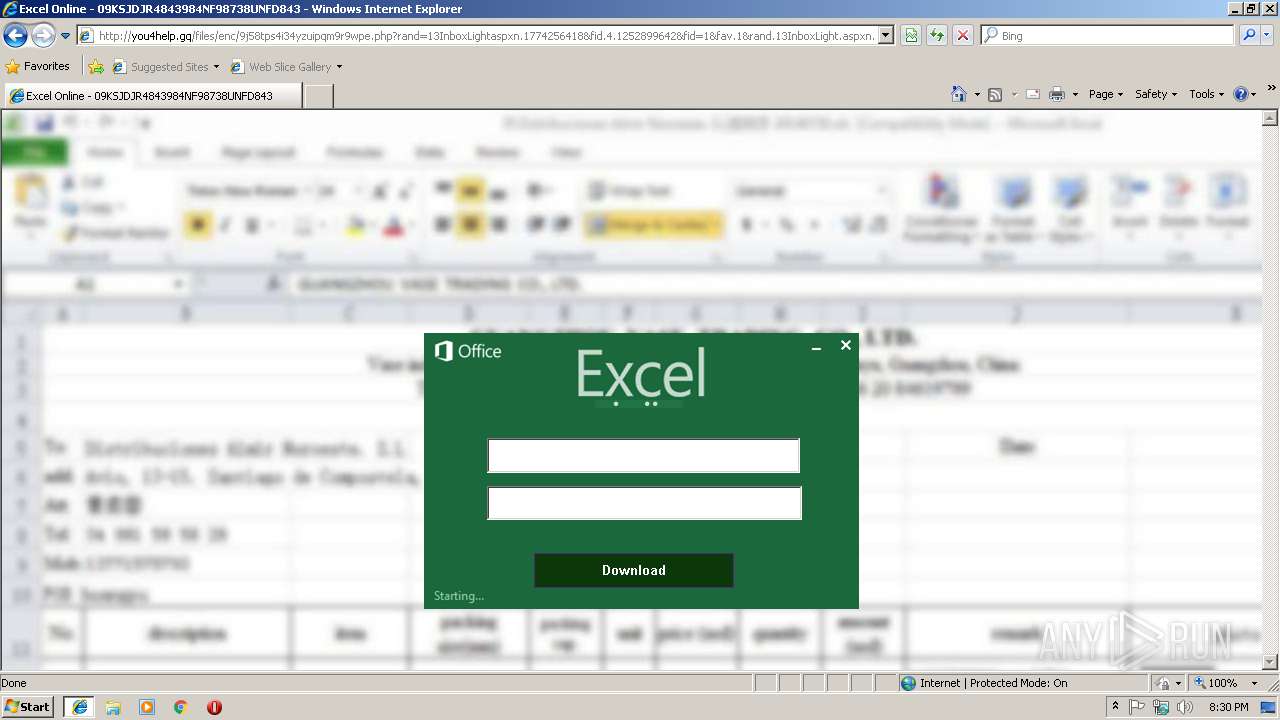
3180 | iexplore.exe | GET | 200 | 138.68.19.60:80 | http://you4help.gq/files/enc/9j58tps4i34yzuipqm9r9wpe.php?rand=13InboxLightaspxn.1774256418&fid.4.1252899642&fid=1&fav.1&rand.13InboxLight.aspxn.1774256418&fid.1252899642&fid.1&fav.1&email=&.rand=13InboxLight.aspx?n=1774256418&fid=4 | US | html | 6.17 Kb | malicious |
3180 | iexplore.exe | POST | 302 | 138.68.19.60:80 | http://you4help.gq/files/enc/zeus.php | US | — | — | malicious |
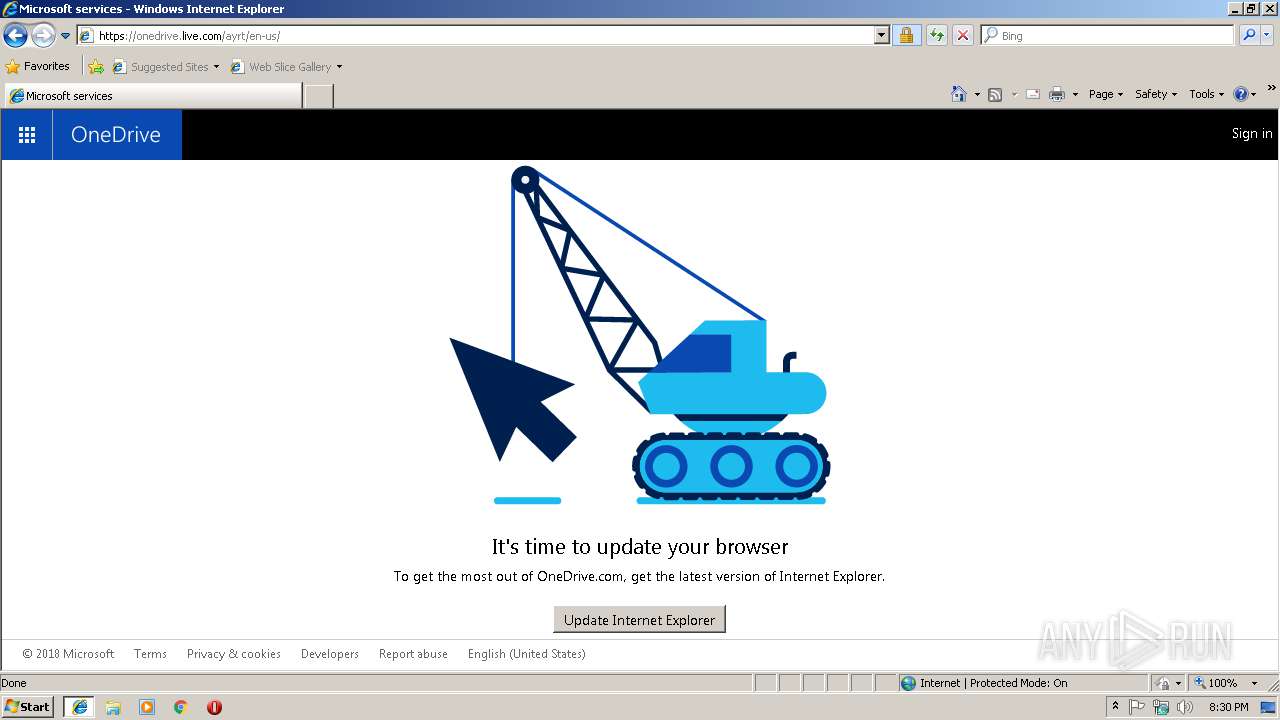
3180 | iexplore.exe | GET | 301 | 204.79.197.217:80 | http://onedrive.live.com/ayrt/en-us/ | US | html | 154 b | shared |
2924 | iexplore.exe | GET | 404 | 138.68.19.60:80 | http://you4help.gq/favicon.ico | US | html | 328 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3180 | iexplore.exe | 204.79.197.217:443 | onedrive.live.com | Microsoft Corporation | US | whitelisted |
2924 | iexplore.exe | 2.19.37.83:443 | p.sfx.ms | Akamai International B.V. | — | whitelisted |
3180 | iexplore.exe | 2.16.186.40:443 | spoprod-a.akamaihd.net | Akamai International B.V. | — | whitelisted |
3180 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3180 | iexplore.exe | 2.19.37.83:443 | p.sfx.ms | Akamai International B.V. | — | whitelisted |
3180 | iexplore.exe | 52.142.114.2:443 | c.live.com | Microsoft Corporation | IE | whitelisted |
2924 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3180 | iexplore.exe | 138.68.19.60:80 | you4help.gq | Digital Ocean, Inc. | US | suspicious |
3180 | iexplore.exe | 204.79.197.217:80 | onedrive.live.com | Microsoft Corporation | US | whitelisted |
2924 | iexplore.exe | 138.68.19.60:80 | you4help.gq | Digital Ocean, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
you4help.gq |
| malicious |
onedrive.live.com |
| shared |
spoprod-a.akamaihd.net |
| whitelisted |
p.sfx.ms |
| whitelisted |
c.live.com |
| whitelisted |
c.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1056 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .gq Domain |
3180 | iexplore.exe | A Network Trojan was detected | MALWARE [PTsecurity] Adobe PDF Phishing Landing |
3180 | iexplore.exe | A Network Trojan was detected | MALWARE [PTsecurity] Adobe PDF Phishing Landing |
3180 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS Excel/Adobe Online Phishing Landing Nov 25 2015 |
3180 | iexplore.exe | Potentially Bad Traffic | ET CURRENT_EVENTS Possible Excel Online Phishing Landing - Title over non SSL |
3180 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS Possible Successful Generic Phish to .gq Domain 2018-10-23 |
3180 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP POST Request to Suspicious *.gq domain |
3180 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS Possible Successful Generic Phish Jan 14 2016 |
1 ETPRO signatures available at the full report