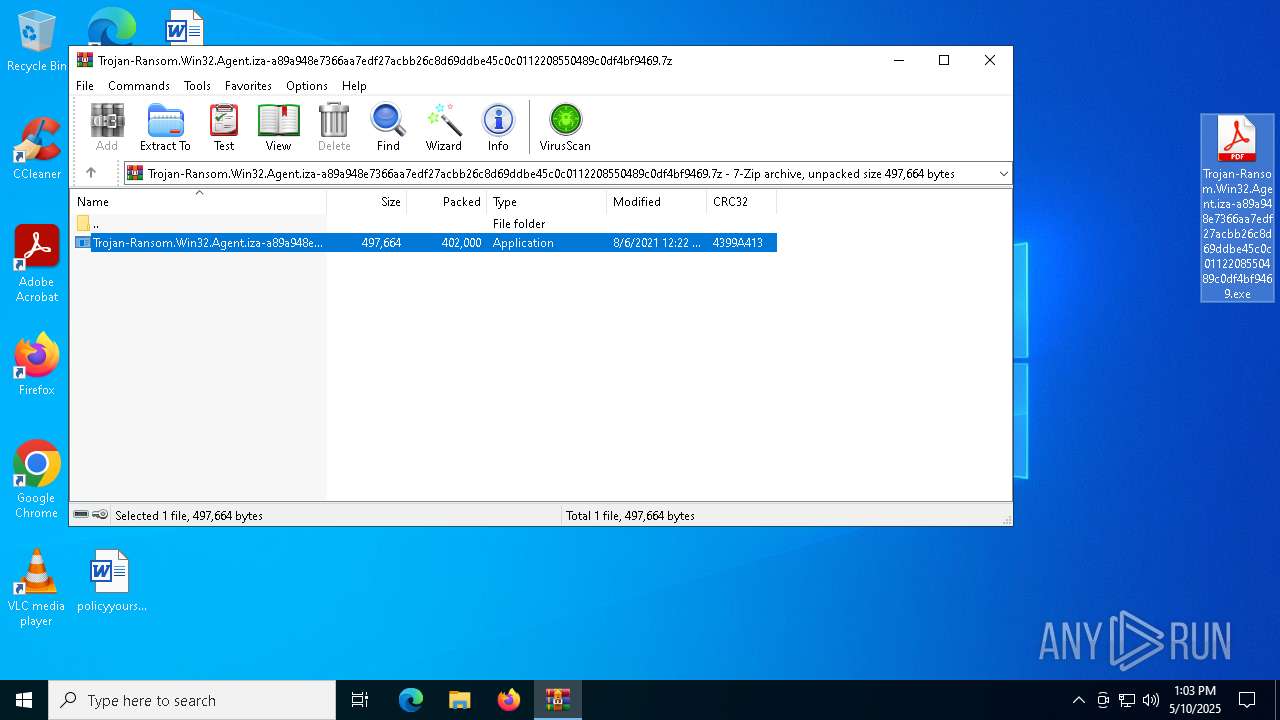
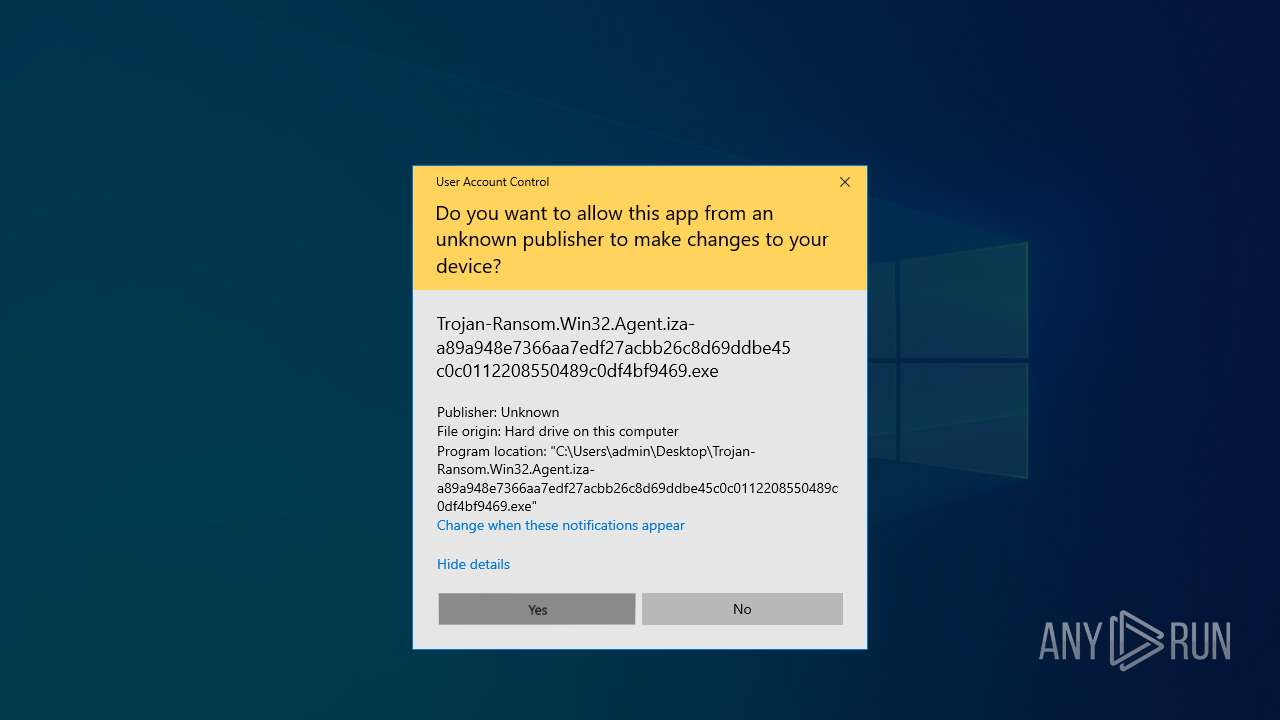
| File name: | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.7z |
| Full analysis: | https://app.any.run/tasks/e5149608-5588-4e18-9cd2-0f7672b69795 |
| Verdict: | Malicious activity |
| Analysis date: | May 10, 2025, 13:03:09 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 701BFB1FC1517E27075142E9438285B1 |
| SHA1: | E6C18D73CA2F3990FA6F329BA3E84BA1A93E1AD3 |
| SHA256: | 6EB8B63DE2EC1926866D1889C57CE74CAE6554C8C4D53470B58D36269A3A083E |
| SSDEEP: | 12288:qZUO5D37PDcO+567yDIEy4TkUl9zi4i7Hz26WE0CM7XYts:qZnD3LDcO+c7ykEhl9zi4i7HJW7CM7Ie |
MALICIOUS
Changes the autorun value in the registry
- Isass.exe (PID: 8024)
SUSPICIOUS
Application launched itself
- Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe (PID: 7840)
- Isass.exe (PID: 7992)
Reads security settings of Internet Explorer
- Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe (PID: 7880)
- Isass.exe (PID: 8024)
Starts CMD.EXE for commands execution
- Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe (PID: 7880)
Starts itself from another location
- Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe (PID: 7880)
Potential Corporate Privacy Violation
- Isass.exe (PID: 8024)
- Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe (PID: 7880)
Detected use of alternative data streams (AltDS)
- Isass.exe (PID: 8024)
There is functionality for taking screenshot (YARA)
- Isass.exe (PID: 7992)
- Isass.exe (PID: 8024)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6656)
Checks supported languages
- Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe (PID: 7840)
- Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe (PID: 7880)
- Isass.exe (PID: 7992)
- Isass.exe (PID: 8024)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6656)
Reads mouse settings
- Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe (PID: 7840)
- Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe (PID: 7880)
- Isass.exe (PID: 7992)
- Isass.exe (PID: 8024)
Reads the computer name
- Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe (PID: 7880)
- Isass.exe (PID: 8024)
Checks proxy server information
- Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe (PID: 7880)
- Isass.exe (PID: 8024)
Manual execution by a user
- Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe (PID: 7840)
Reads the machine GUID from the registry
- Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe (PID: 7840)
- Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe (PID: 7880)
- Isass.exe (PID: 8024)
Create files in a temporary directory
- Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe (PID: 7840)
Creates files or folders in the user directory
- Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe (PID: 7880)
UPX packer has been detected
- Isass.exe (PID: 7992)
- Isass.exe (PID: 8024)
The process uses AutoIt
- Isass.exe (PID: 7992)
- Isass.exe (PID: 8024)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2021:08:06 12:22:40+00:00 |
| ArchivedFileName: | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe |
Total processes
142
Monitored processes
11
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5164 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6656 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7196 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7228 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
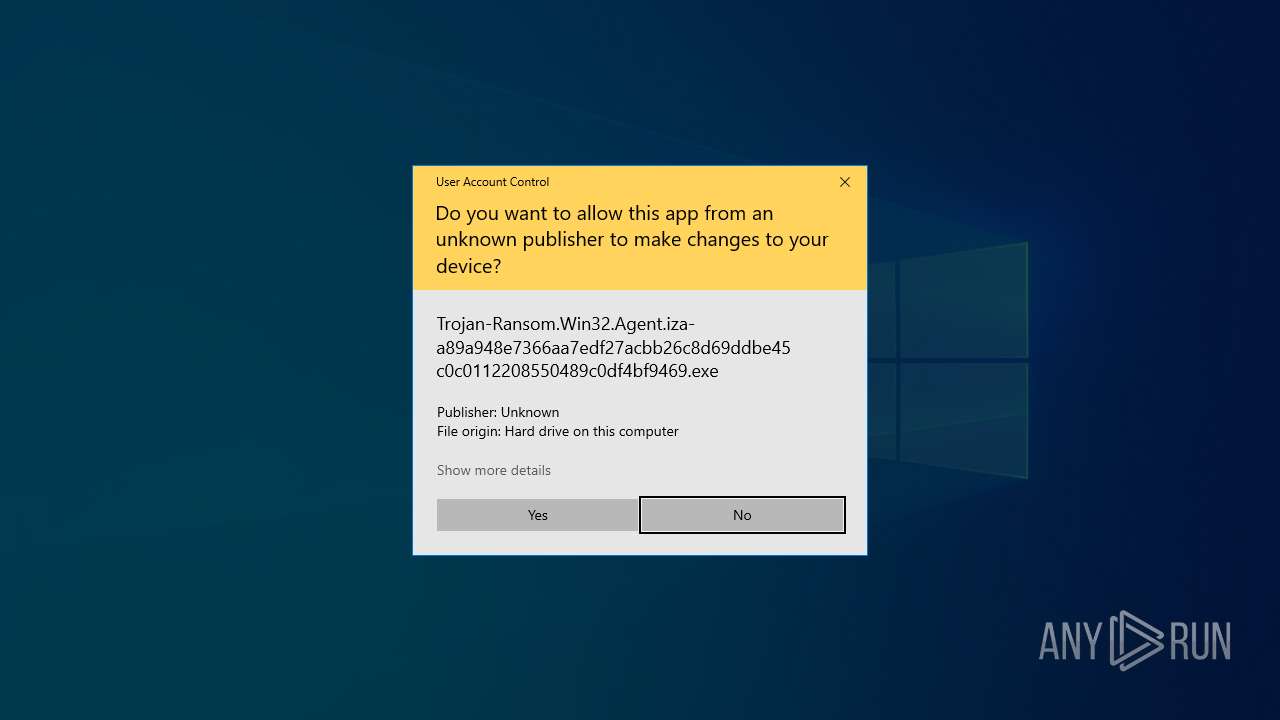
| 7840 | "C:\Users\admin\Desktop\Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe" | C:\Users\admin\Desktop\Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7880 | C:\Users\admin\Desktop\Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe /AutoIt3ExecuteScript "C:\Users\admin\AppData\Local\Temp\delph1.dat" | C:\Users\admin\Desktop\Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7924 | C:\WINDOWS\system32\cmd.exe /C echo. > "C:\Users\admin\AppData\Roaming\Isass.exe":Zone.Identifier | C:\Windows\SysWOW64\cmd.exe | — | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7932 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7992 | C:\Users\admin\AppData\Roaming\Isass.exe | C:\Users\admin\AppData\Roaming\Isass.exe | — | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
3 433
Read events
3 407
Write events
26
Delete events
0
Modification events
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.7z | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
2
Suspicious files
5
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7880 | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | C:\Users\admin\AppData\Roaming\Isass.exe | — | |
MD5:— | SHA256:— | |||
| 7840 | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | C:\Users\admin\AppData\Local\Temp\delph1.dat | binary | |
MD5:04979DB956D28F674929FCB76CAD8D00 | SHA256:12587BA985F95D58ACD65039709A5820B1608B33866D023370AFA9B46DAED6E7 | |||
| 7840 | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | C:\Users\admin\AppData\Local\Temp\pd4ta.bin | binary | |
MD5:76A5F481979C63CDB2536278001B42B4 | SHA256:796225D35ED641D583183F5DF4A66E5A5580BFF21D2812DAEEA8CEB3AA48ED2D | |||
| 7840 | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | C:\Users\admin\AppData\Local\Temp\autE051.tmp | binary | |
MD5:76A5F481979C63CDB2536278001B42B4 | SHA256:796225D35ED641D583183F5DF4A66E5A5580BFF21D2812DAEEA8CEB3AA48ED2D | |||
| 7840 | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | C:\Users\admin\AppData\Local\Temp\delph1.bin | binary | |
MD5:B162220B35DCE3B159C48382CA0903D4 | SHA256:A9939EFF39B1B42313C5CFEC630314D8354F57F30094D6490047A89E998BCAB5 | |||
| 7840 | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | C:\Users\admin\AppData\Local\Temp\autE040.tmp | binary | |
MD5:B162220B35DCE3B159C48382CA0903D4 | SHA256:A9939EFF39B1B42313C5CFEC630314D8354F57F30094D6490047A89E998BCAB5 | |||
| 7880 | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | C:\Users\admin\AppData\Roaming\F78758D6078671852BBD1BEF1991F220 | text | |
MD5:80D3A9CF5CBBC0CFE77103A215C8B018 | SHA256:C148ADBF3699A33CE51B8F8AB09767FE371AF0575B4D0A580140C747A05A8C1D | |||
| 7840 | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | C:\Users\admin\AppData\Local\Temp\pd4ta.dat | text | |
MD5:60E8DEC83DF9BF655992FEA86F806CA9 | SHA256:03E0AF447E0FF128C538DF3BE5CF816DFDA3ABDB5022F9CE4549610A19080082 | |||
| 6656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6656.673\Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | executable | |
MD5:05210D911B0E22A9AFC5FDC0395EDA04 | SHA256:A89A948E7366AA7EDF27ACBB26C8D69DDBE45C0C0112208550489C0DF4BF9469 | |||
| 7924 | cmd.exe | C:\Users\admin\AppData\Roaming\Isass.exe:Zone.Identifier | text | |
MD5:BC949EA893A9384070C31F083CCEFD26 | SHA256:6BDF66B5BF2A44E658BEA2EE86695AB150A06E600BF67CD5CCE245AD54962C61 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
26
DNS requests
53
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.180:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7880 | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | GET | 302 | 142.250.185.174:80 | http://google.com/ | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7880 | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | GET | 429 | 142.250.186.36:80 | http://www.google.com/sorry/index?continue=http://google.com/&q=EgRUETC6GJ6d_cAGIjB1AhluHy7grovc3N2iLXVS0TnUvxuf68AIjl66UFW_FJDO8fMUzUYgYpmnH-pSGVMyAnJSShlTT1JSWV9BQlVTSVZFX05FVF9NRVNTQUdFWgFD | unknown | — | — | whitelisted |
8024 | Isass.exe | GET | 302 | 142.250.185.174:80 | http://google.com/ | unknown | — | — | whitelisted |
3192 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3192 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8024 | Isass.exe | GET | 429 | 142.250.186.36:80 | http://www.google.com/sorry/index?continue=http://google.com/&q=EgRUETC6GJ-d_cAGIjCADYvSIIdCzxtcRAFGhY08LOm8KfUiy-M3Xc1g9qJNmU8TurPfmSrm16yq7Ydw2XcyAnJSShlTT1JSWV9BQlVTSVZFX05FVF9NRVNTQUdFWgFD | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.180:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.google.com |
| whitelisted |
costapro.net |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7880 | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | Potential Corporate Privacy Violation | ET INFO Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
7880 | Trojan-Ransom.Win32.Agent.iza-a89a948e7366aa7edf27acbb26c8d69ddbe45c0c0112208550489c0df4bf9469.exe | Potential Corporate Privacy Violation | ET INFO Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
8024 | Isass.exe | Potential Corporate Privacy Violation | ET INFO Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
8024 | Isass.exe | Potential Corporate Privacy Violation | ET INFO Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |