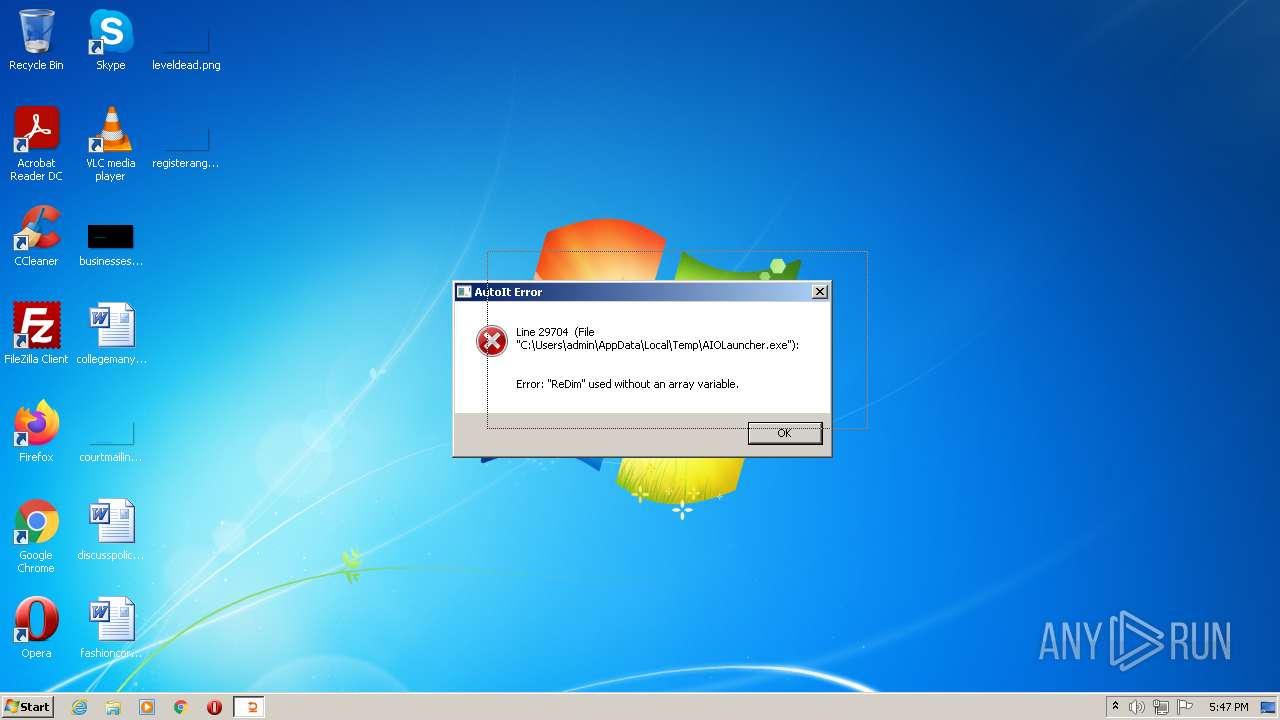
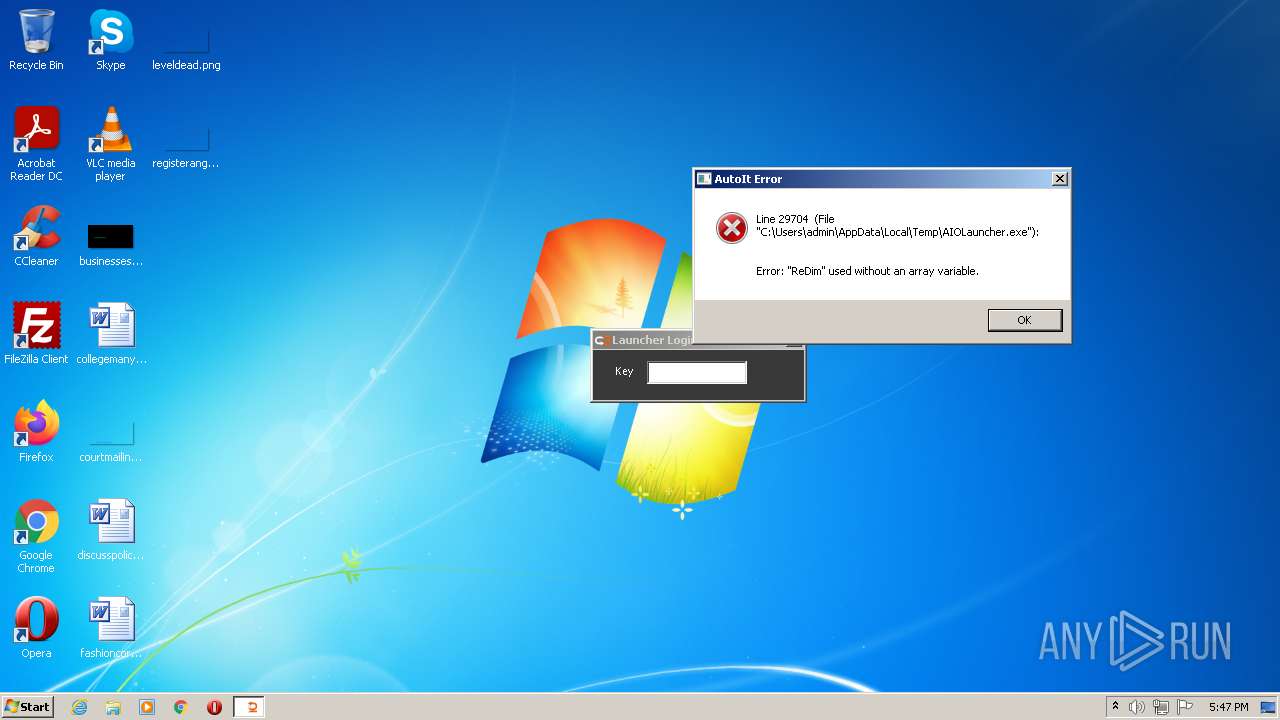
| File name: | AIOLauncher.exe |
| Full analysis: | https://app.any.run/tasks/067c349d-c513-4b6a-9ca9-0a60c10456b6 |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2022, 17:45:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 64B0CF2A830C945CD6B9BFA3B09ED417 |
| SHA1: | 13D152905F8D28B7FB89192EF98C4C6028827E0C |
| SHA256: | 6EB66BD6D31FED5C432886395C023A2DEC50ECF0AF53ECAB7B759A0B3F0CC386 |
| SSDEEP: | 196608:+xDYEc1jor5JO0h4d+5941k6TWeBkRbzrW6eY3eLoG:+xrc1jo/OvdJk6TqRXy6eY3ekG |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- AIOLauncher.exe (PID: 1596)
Reads settings of System Certificates
- AIOLauncher.exe (PID: 1596)
Reads security settings of Internet Explorer
- AIOLauncher.exe (PID: 1596)
Checks Windows Trust Settings
- AIOLauncher.exe (PID: 1596)
INFO
Reads mouse settings
- AIOLauncher.exe (PID: 1596)
Checks supported languages
- AIOLauncher.exe (PID: 1596)
Reads the computer name
- AIOLauncher.exe (PID: 1596)
Checks proxy server information
- AIOLauncher.exe (PID: 1596)
Manual execution by a user
- explorer.exe (PID: 3400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2022-Nov-16 09:20:52 |
| Detected languages: |
|
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 128 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 8 |
| TimeDateStamp: | 2022-Nov-16 09:20:52 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 581597 | 0 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | |
.rdata | 585728 | 195982 | 0 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | |
.data | 782336 | 36724 | 0 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.]RB | 819200 | 5695468 | 0 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | |
.MMi | 6516736 | 3020 | 3072 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.320098 |
.d^8 | 6520832 | 9158640 | 9158656 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.9833 |
.reloc | 15679488 | 1572 | 2048 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.54862 |
.rsrc | 15683584 | 26943 | 27136 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.70583 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.66371 | 296 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
2 | 2.05883 | 296 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
3 | 2.25499 | 296 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
4 | 3.34862 | 16424 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
5 | 3.41882 | 4136 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
6 | 3.54802 | 2344 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
7 | 3.91237 | 1064 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
99 | 2.54478 | 62 | Latin 1 / Western European | English - United Kingdom | RT_GROUP_ICON |
162 | 2.02322 | 20 | Latin 1 / Western European | English - United Kingdom | RT_GROUP_ICON |
164 | 1.84274 | 20 | Latin 1 / Western European | English - United Kingdom | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
IPHLPAPI.DLL |
KERNEL32.dll |
KERNEL32.dll (#2) |
KERNEL32.dll (#3) |
MPR.dll |
OLEAUT32.dll |
Total processes
43
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
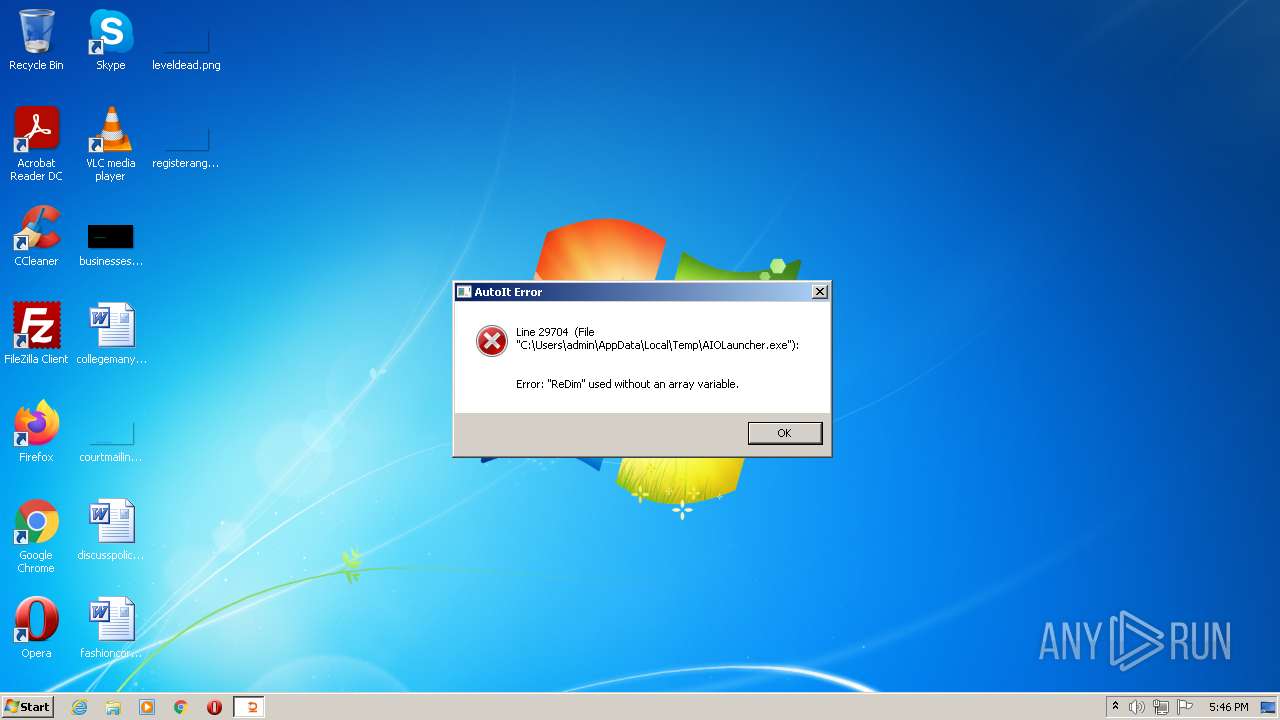
| 1596 | "C:\Users\admin\AppData\Local\Temp\AIOLauncher.exe" | C:\Users\admin\AppData\Local\Temp\AIOLauncher.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 3400 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 650
Read events
4 606
Write events
44
Delete events
0
Modification events
| (PID) Process: | (1596) AIOLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1596) AIOLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1596) AIOLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1596) AIOLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1596) AIOLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1596) AIOLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1596) AIOLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1596) AIOLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1596) AIOLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1596) AIOLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{FCC67766-6201-4AD1-A6B8-2F4553C93D47} |
| Operation: | write | Name: | WpadDecisionReason |
Value: 1 | |||
Executable files
0
Suspicious files
3
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1596 | AIOLauncher.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | binary | |
MD5:— | SHA256:— | |||
| 1596 | AIOLauncher.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 1596 | AIOLauncher.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1596 | AIOLauncher.exe | C:\Users\admin\AppData\Local\Temp\products.txt | text | |
MD5:— | SHA256:— | |||
| 1596 | AIOLauncher.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\products[1].txt | text | |
MD5:— | SHA256:— | |||
| 1596 | AIOLauncher.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
10
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1596 | AIOLauncher.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
1596 | AIOLauncher.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b756e1951eb3bd08 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1596 | AIOLauncher.exe | 92.205.102.128:443 | cbmtgo.com | Host Europe GmbH | FR | unknown |
1596 | AIOLauncher.exe | 192.124.249.41:80 | ocsp.godaddy.com | SUCURI-SEC | US | suspicious |
1596 | AIOLauncher.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cbmtgo.com |
| unknown |
dns.msftncsi.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |