| URL: | https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&cad=rja&uact=8&ved=2ahUKEwi2vJua2eyKAxVErJUCHX50FUgQFnoECBkQAQ&url=https%3A%2F%2Fmobaxterm.mobatek.net%2Fdownload-home-edition.html&usg=AOvVaw1loBQOSDJNpaspeiDPC2mj&opi=89978449 |
| Full analysis: | https://app.any.run/tasks/6d405ef9-347d-46b3-bcd7-a47e3553d946 |
| Verdict: | Malicious activity |
| Analysis date: | January 11, 2025, 03:12:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0C3B82EC6875E3395C44A54FFBE76F6D |
| SHA1: | 6477EFE294D1E5923638ACEAB3A0F226B628FA45 |
| SHA256: | 6E8B8466D0A3D07DF2C0FF02A4795B7638433543344359874F2F8ADBB83CE32E |
| SSDEEP: | 6:2OLI2sq+wp1w4pNqlXExFYNRR3zyKLHBM900SOdJa:2V2JnNqlU7Y5WSv0Q |
MALICIOUS
Detects Cygwin installation
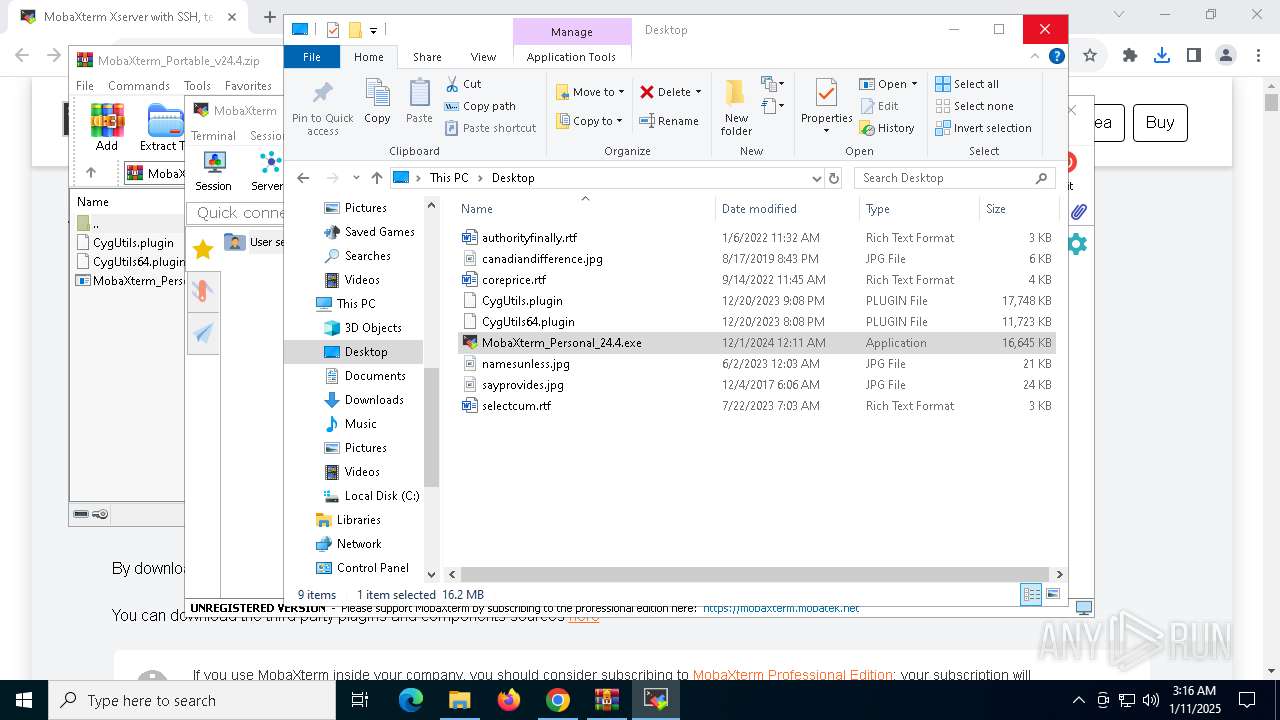
- MobaXterm_Personal_24.4.exe (PID: 1140)
SUSPICIOUS
The process creates files with name similar to system file names
- MobaXterm_Personal_24.4.exe (PID: 1140)
Executable content was dropped or overwritten
- MobaXterm_Personal_24.4.exe (PID: 1140)
There is functionality for taking screenshot (YARA)
- MobaXterm_Personal_24.4.exe (PID: 1140)
- XWin_MobaX.exe (PID: 6392)
Reads security settings of Internet Explorer
- MobaXterm_Personal_24.4.exe (PID: 1140)
Connects to SSH
- MoTTYnew.exe (PID: 512)
There is functionality for sending ICMP (YARA)
- MobaXterm_Personal_24.4.exe (PID: 1140)
There is functionality for communication over UDP network (YARA)
- MobaXterm_Personal_24.4.exe (PID: 1140)
INFO
Application launched itself
- chrome.exe (PID: 2380)
The process uses the downloaded file
- chrome.exe (PID: 6764)
- WinRAR.exe (PID: 6240)
- chrome.exe (PID: 2380)
- MobaXterm_Personal_24.4.exe (PID: 1140)
Reads Microsoft Office registry keys
- chrome.exe (PID: 2380)
The sample compiled with english language support
- WinRAR.exe (PID: 6240)
- MobaXterm_Personal_24.4.exe (PID: 1140)
Manual execution by a user
- MobaXterm_Personal_24.4.exe (PID: 1140)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6240)
Reads the computer name
- MobaXterm_Personal_24.4.exe (PID: 1140)
- XWin_MobaX.exe (PID: 6392)
- MoTTYnew.exe (PID: 512)
Creates files or folders in the user directory
- MobaXterm_Personal_24.4.exe (PID: 1140)
Reads mouse settings
- MobaXterm_Personal_24.4.exe (PID: 1140)
Process checks computer location settings
- MobaXterm_Personal_24.4.exe (PID: 1140)
Create files in a temporary directory
- xkbcomp_w32.exe (PID: 2040)
- MoTTYnew.exe (PID: 512)
- XWin_MobaX.exe (PID: 6392)
- MobaXterm_Personal_24.4.exe (PID: 1140)
Checks supported languages
- MoTTYnew.exe (PID: 512)
- xkbcomp_w32.exe (PID: 2040)
- XWin_MobaX.exe (PID: 6392)
- MobaXterm_Personal_24.4.exe (PID: 1140)
Reads the machine GUID from the registry
- MoTTYnew.exe (PID: 512)
- MobaXterm_Personal_24.4.exe (PID: 1140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
165
Monitored processes
28
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 512 | "C:\Users\admin\AppData\Local\Temp\Mxt244\mx86_64b\bin\mottynew.exe" -load "TERM1318682" | C:\Users\admin\AppData\Local\Temp\Mxt244\mx86_64b\bin\MoTTYnew.exe | MobaXterm_Personal_24.4.exe | ||||||||||||
User: admin Company: Mobatek Integrity Level: MEDIUM Description: MobaXterm terminal emulator Exit code: 0 Version: Release 0.81 (without embedded help) Modules
| |||||||||||||||
| 900 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4208 --field-trial-handle=1852,i,539224542536080405,6447661074280594379,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1140 | "C:\Users\admin\Desktop\MobaXterm_Personal_24.4.exe" | C:\Users\admin\Desktop\MobaXterm_Personal_24.4.exe | explorer.exe | ||||||||||||
User: admin Company: Mobatek Integrity Level: MEDIUM Description: MobaXterm Exit code: 0 Version: 24.4.0.5258 Modules
| |||||||||||||||
| 1172 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5396 --field-trial-handle=1852,i,539224542536080405,6447661074280594379,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1296 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=3696 --field-trial-handle=1852,i,539224542536080405,6447661074280594379,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2040 | "C:\Users\admin\AppData\Local\Temp\Mxt244\mx86_64b\bin\xkbcomp_w32.exe" -w 1 "-RC:\Users\admin\AppData\Local\Temp\Mxt244\mx86_64b\usr\share\X11\xkb" -xkm "C:\Users\admin\AppData\Local\Temp\Mxt244\mx86_64b\var\log\xwin\xkb_a04764" -em1 "The XKEYBOARD keymap compiler (xkbcomp) reports:" -emp "> " -eml "Errors from xkbcomp are not fatal to the X server" "C:\Users\admin\AppData\Local\Temp\Mxt244\mx86_64b\var\log\xwin\server-0.xkm" | C:\Users\admin\AppData\Local\Temp\Mxt244\mx86_64b\bin\xkbcomp_w32.exe | — | XWin_MobaX.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2380 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&cad=rja&uact=8&ved=2ahUKEwi2vJua2eyKAxVErJUCHX50FUgQFnoECBkQAQ&url=https%3A%2F%2Fmobaxterm.mobatek.net%2Fdownload-home-edition.html&usg=AOvVaw1loBQOSDJNpaspeiDPC2mj&opi=89978449" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3508 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5456 --field-trial-handle=1852,i,539224542536080405,6447661074280594379,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4360 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | xkbcomp_w32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5040 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5052 --field-trial-handle=1852,i,539224542536080405,6447661074280594379,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
11 846
Read events
11 284
Write events
536
Delete events
26
Modification events
| (PID) Process: | (2380) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2380) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2380) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2380) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2380) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2380) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | write | Name: | neajdppkdcdipfabeoofebfddakdcjhd |
Value: 856E0E73E6E37099A4C21DA68A6A10BD31001B9D36A3243EBC4814EC93C0BA43 | |||
| (PID) Process: | (2380) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | write | Name: | nkeimhogjdpnpccoofpliimaahmaaome |
Value: FCA740BBFC8E20E9025F9E9DB4E7938D7E7DD2A04EA8AF0876F2B98E4667FEBA | |||
| (PID) Process: | (2380) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | write | Name: | nmmhkkegccagdldgiimedpiccmgmieda |
Value: BA7A892BC41C4FD941697FC2CF6EA1BE9A368761F986521049E8E81940E0F564 | |||
| (PID) Process: | (2380) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2380) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | write | Name: | ahfgeienlihckogmohjhadlkjgocpleb |
Value: 3B08F722C14555E595AF269F140EE426CE8DEBAD90D03EE9FF33B95CB34233F6 | |||
Executable files
63
Suspicious files
418
Text files
508
Unknown types
230
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF135f3a.TMP | — | |
MD5:— | SHA256:— | |||
| 2380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF135f2a.TMP | — | |
MD5:— | SHA256:— | |||
| 2380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF135f3a.TMP | — | |
MD5:— | SHA256:— | |||
| 2380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF135f3a.TMP | — | |
MD5:— | SHA256:— | |||
| 2380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF135f2a.TMP | — | |
MD5:— | SHA256:— | |||
| 2380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2380 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
51
DNS requests
40
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1544 | RUXIMICS.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
236 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1544 | RUXIMICS.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6300 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
236 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3812 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
3812 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrga7eefaxjfdmmgfkiaxjg4yjq_2024.7.12.235938/eeigpngbgcognadeebkilcpcaedhellh_2024.07.12.235938_all_a6r64uyugl6fjh3lupjqo6w7ai.crx3 | unknown | — | — | whitelisted |
3812 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
3812 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6092 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1544 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1544 | RUXIMICS.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1544 | RUXIMICS.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.16.204.141:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2380 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6500 | chrome.exe | 172.217.16.196:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.google.com |
| whitelisted |
accounts.google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
mobaxterm.mobatek.net |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
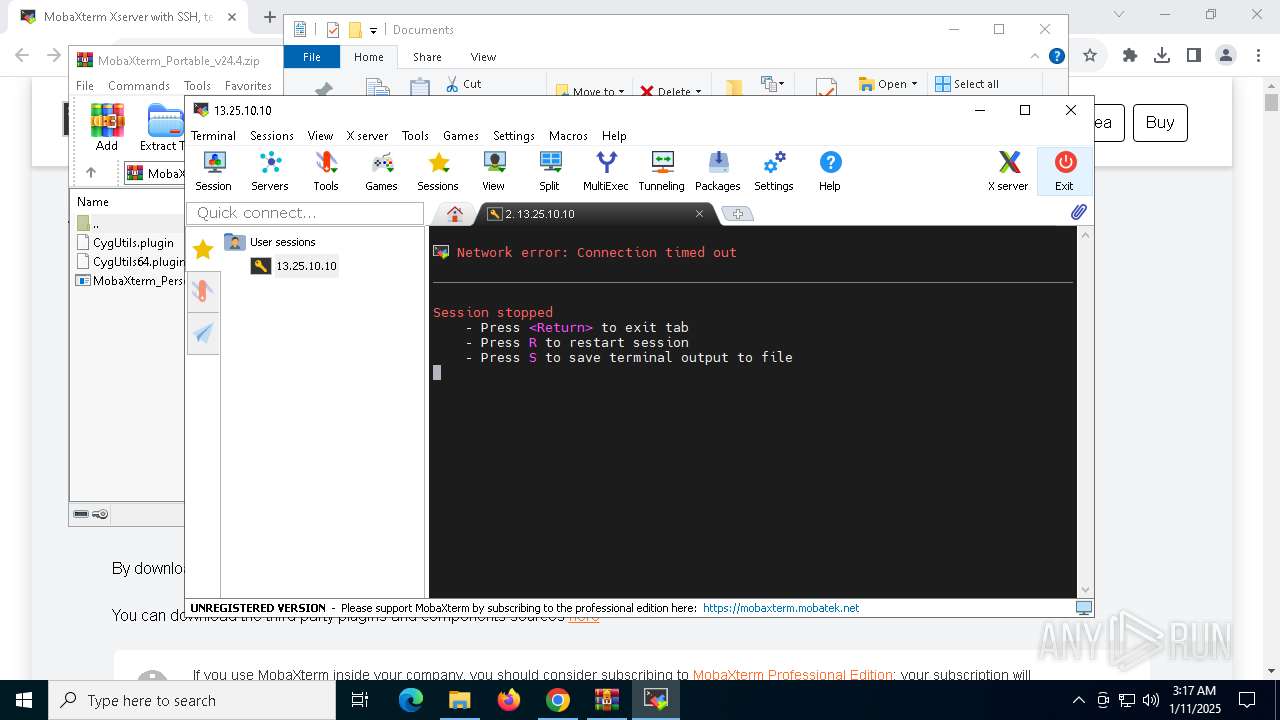
512 | MoTTYnew.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |