| File name: | kill me.jar |
| Full analysis: | https://app.any.run/tasks/50df50de-8239-49bd-8a76-87c0ff677e91 |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2022, 23:11:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/java-archive |
| File info: | Java archive data (JAR) |
| MD5: | 98D3CEBBCE492AD48C6D443076EB9A0C |
| SHA1: | D7CDA9268026FA92566499A68FFC22C9F407FC8B |
| SHA256: | 6E8AC0D98F89B91237EC16C982AD35E2E2E64F0E767FA688353B4D93976E2755 |
| SSDEEP: | 1536:jOyga1gvvRQEX15RRJum7jaNd5HgMAL22R6RJxarE8Bk8IU3Tdbemt:JnendX/UVddLALDRy7arHBnbUC |
MALICIOUS
Uses Task Scheduler to run other applications
- javaw.exe (PID: 1252)
Changes the autorun value in the registry
- javaw.exe (PID: 1252)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3780)
SUSPICIOUS
Reads the computer name
- javaw.exe (PID: 1252)
- javaw.exe (PID: 392)
- javaw.exe (PID: 1168)
- javaw.exe (PID: 4048)
- javaw.exe (PID: 2232)
Creates files in the program directory
- javaw.exe (PID: 1252)
Checks supported languages
- javaw.exe (PID: 1252)
- javaw.exe (PID: 4048)
- javaw.exe (PID: 392)
- cmd.exe (PID: 1384)
- javaw.exe (PID: 1168)
- javaw.exe (PID: 2232)
Uses ICACLS.EXE to modify access control list
- javaw.exe (PID: 1252)
Uses ATTRIB.EXE to modify file attributes
- javaw.exe (PID: 1252)
Creates files in the user directory
- javaw.exe (PID: 1252)
Writes to a desktop.ini file (may be used to cloak folders)
- javaw.exe (PID: 1252)
Application launched itself
- javaw.exe (PID: 1252)
Executes JAVA applets
- javaw.exe (PID: 1252)
Executed via Task Scheduler
- javaw.exe (PID: 392)
- javaw.exe (PID: 1168)
- javaw.exe (PID: 2232)
Check for Java to be installed
- javaw.exe (PID: 392)
- javaw.exe (PID: 1168)
- javaw.exe (PID: 2232)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 4048)
Uses REG.EXE to modify Windows registry
- javaw.exe (PID: 4048)
INFO
Reads the computer name
- icacls.exe (PID: 2884)
- schtasks.exe (PID: 3780)
Checks supported languages
- icacls.exe (PID: 2884)
- schtasks.exe (PID: 3780)
- NOTEPAD.EXE (PID: 3428)
- attrib.exe (PID: 3784)
- attrib.exe (PID: 2316)
- reg.exe (PID: 1372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | META-INF/MANIFEST.MF |
|---|---|
| ZipUncompressedSize: | 570 |
| ZipCompressedSize: | 396 |
| ZipCRC: | 0x8d6c774e |
| ZipModifyDate: | 2022:01:14 23:11:09 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0808 |
| ZipRequiredVersion: | 20 |
Total processes
52
Monitored processes
12
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 392 | javaw.exe -jar "C:\Users\admin\AppData\Roaming\servidorcito\servidorcito.jar" | C:\Program Files\Common Files\Oracle\Java\javapath\javaw.exe | — | taskeng.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1168 | javaw.exe -jar "C:\Users\admin\AppData\Roaming\servidorcito\servidorcito.jar" | C:\Program Files\Common Files\Oracle\Java\javapath\javaw.exe | — | taskeng.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1252 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\Desktop\kill me.jar.zip" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | Explorer.EXE | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1372 | reg query HKCU\Software\DownloadManager\Passwords | C:\Windows\system32\reg.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1384 | cmd.exe /c dir | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2232 | javaw.exe -jar "C:\Users\admin\AppData\Roaming\servidorcito\servidorcito.jar" | C:\Program Files\Common Files\Oracle\Java\javapath\javaw.exe | — | taskeng.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 2316 | attrib +s +h +r "C:\Users\admin\AppData\Roaming\servidorcito" | C:\Windows\system32\attrib.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2884 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\system32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
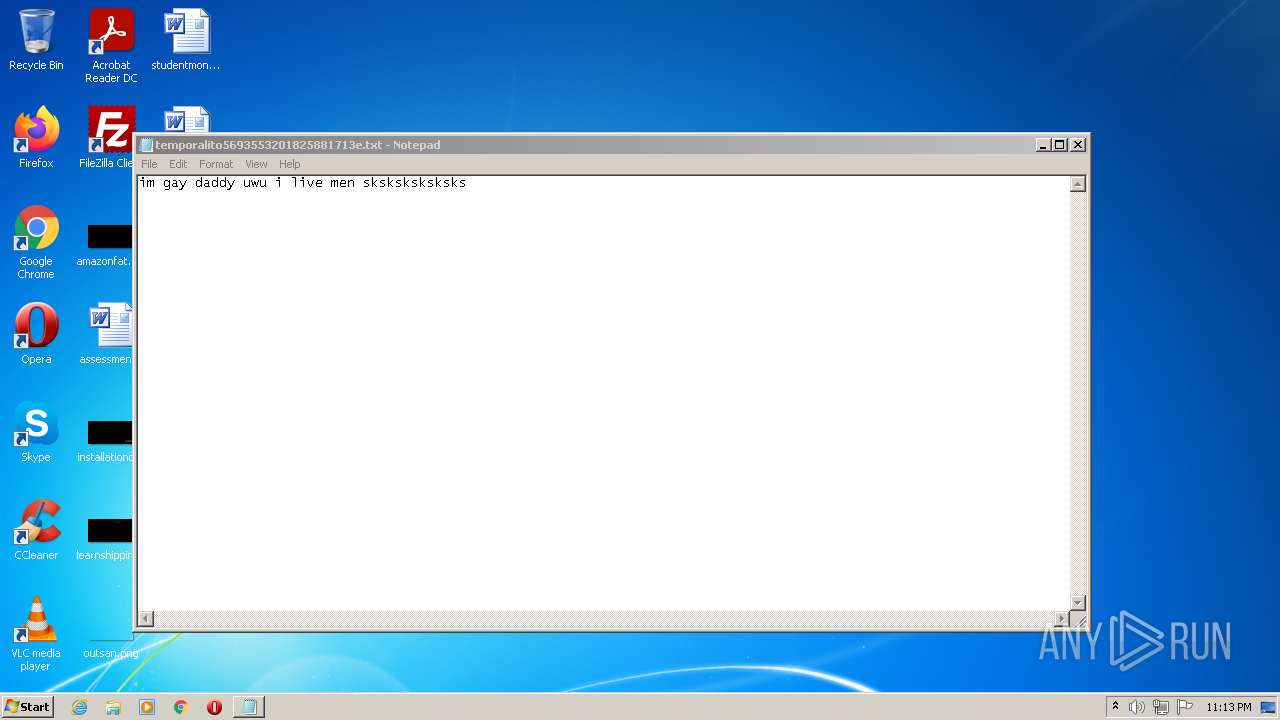
| 3428 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\temporalito5693553201825881713e.txt | C:\Windows\system32\NOTEPAD.EXE | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3780 | schtasks /create /tn Firewall /tr "javaw.exe -jar 'C:\Users\admin\AppData\Roaming\servidorcito\servidorcito.jar'" /sc minute /mo 1 | C:\Windows\system32\schtasks.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 117
Read events
3 115
Write events
2
Delete events
0
Modification events
| (PID) Process: | (1252) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Firewall |
Value: "C:\Program Files\Java\jre1.8.0_271/bin/javaw.exe" -jar "C:\Users\admin\AppData\Roaming\servidorcito\servidorcito.jar" | |||
| (PID) Process: | (4048) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
Executable files
1
Suspicious files
0
Text files
55
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4048 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio1133348356708905949.tmp | image | |
MD5:— | SHA256:— | |||
| 4048 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio513179831430294926.tmp | image | |
MD5:— | SHA256:— | |||
| 1252 | javaw.exe | C:\Users\admin\AppData\Roaming\servidorcito\servidorcito.jar | java | |
MD5:— | SHA256:— | |||
| 4048 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio460538308995786951.tmp | image | |
MD5:— | SHA256:— | |||
| 4048 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio979007195677504457.tmp | image | |
MD5:— | SHA256:— | |||
| 4048 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio283029634205061168.tmp | image | |
MD5:— | SHA256:— | |||
| 4048 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio8274786529896187655.tmp | image | |
MD5:— | SHA256:— | |||
| 1252 | javaw.exe | C:\Users\admin\AppData\Roaming\servidorcito\Desktop.ini | ini | |
MD5:— | SHA256:— | |||
| 4048 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio6367349336626882806.tmp | image | |
MD5:— | SHA256:— | |||
| 4048 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio2181745539500588891.tmp | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
14
DNS requests
2
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4048 | javaw.exe | 79.66.71.109:5000 | nipodipo.duckdns.org | Tiscali UK Limited | GB | malicious |
4048 | javaw.exe | 79.66.71.109:5321 | nipodipo.duckdns.org | Tiscali UK Limited | GB | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
nipodipo.duckdns.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
— | — | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |