| File name: | migrate.exe |
| Full analysis: | https://app.any.run/tasks/a47e45e8-e7b4-48f2-9843-a3f8bb53041a |
| Verdict: | Malicious activity |
| Analysis date: | August 22, 2024, 23:26:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | DBFA614D275DA9A0373097FF2E65D3F0 |
| SHA1: | 71443B8BD5F1F5FA4E35DD133AE788A941DE998A |
| SHA256: | 6E7F682BD0B7B0D58FD77A058BF6C6ECA31124B6AABCC69B43AB94960B302076 |
| SSDEEP: | 3072:94YhHC9DDeki/9Xcp4+4/GBrXaSdtvuLmTXeZ:93HC9DXI9sZ4QSmqZ |
MALICIOUS
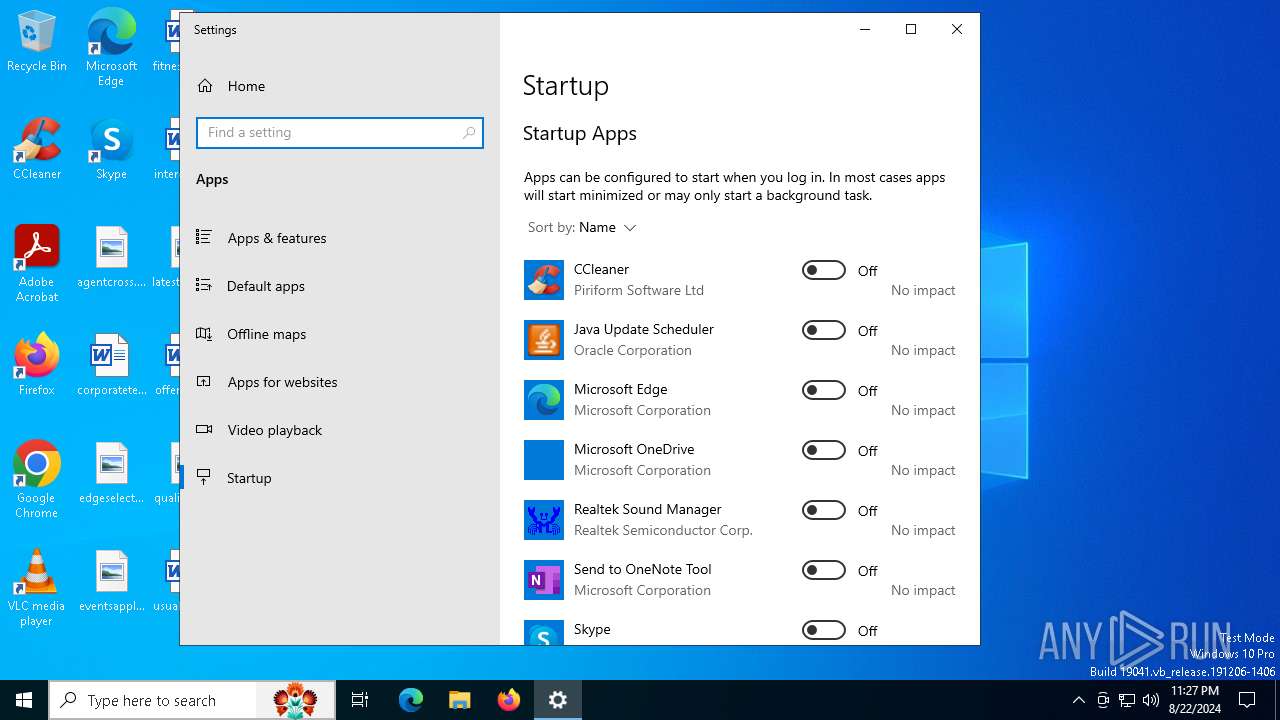
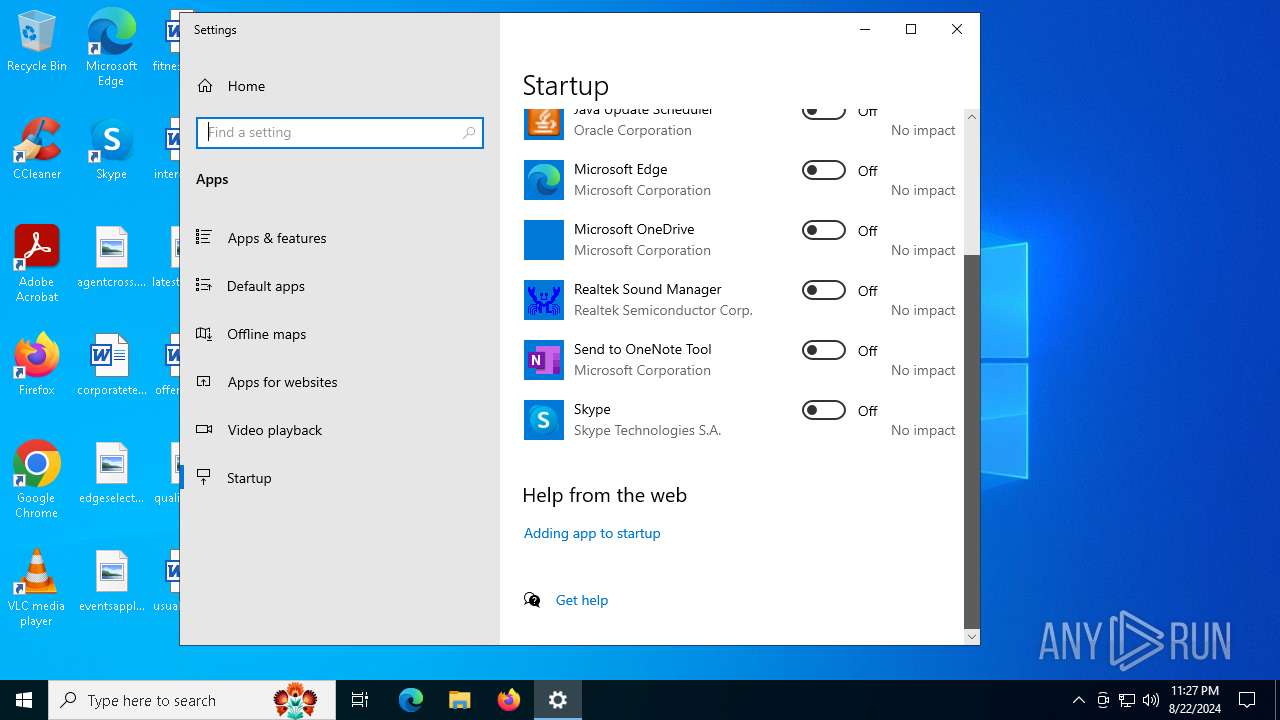
Changes the AppInit_DLLs value (autorun option)
- zvzvgjn.exe (PID: 6732)
- zvzvgjn.exe (PID: 6224)
SUSPICIOUS
Drops the executable file immediately after the start
- migrate.exe (PID: 6632)
- zvzvgjn.exe (PID: 6732)
- zvzvgjn.exe (PID: 6224)
Executable content was dropped or overwritten
- migrate.exe (PID: 6632)
- zvzvgjn.exe (PID: 6732)
- zvzvgjn.exe (PID: 6224)
The process executes via Task Scheduler
- zvzvgjn.exe (PID: 6732)
- zvzvgjn.exe (PID: 6224)
Reads security settings of Internet Explorer
- zvzvgjn.exe (PID: 6732)
Reads the date of Windows installation
- zvzvgjn.exe (PID: 6732)
Starts itself from another location
- zvzvgjn.exe (PID: 6732)
INFO
Checks supported languages
- migrate.exe (PID: 6632)
- zvzvgjn.exe (PID: 6732)
- java_update_qudpcaa.exe (PID: 6216)
- zvzvgjn.exe (PID: 6224)
Creates files in the program directory
- migrate.exe (PID: 6632)
- zvzvgjn.exe (PID: 6224)
Reads the machine GUID from the registry
- migrate.exe (PID: 6632)
- zvzvgjn.exe (PID: 6732)
- java_update_qudpcaa.exe (PID: 6216)
- zvzvgjn.exe (PID: 6224)
Reads the computer name
- migrate.exe (PID: 6632)
- zvzvgjn.exe (PID: 6732)
- java_update_qudpcaa.exe (PID: 6216)
Create files in a temporary directory
- zvzvgjn.exe (PID: 6732)
Process checks computer location settings
- zvzvgjn.exe (PID: 6732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:03:13 17:34:10+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 23040 |
| InitializedDataSize: | 203776 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1880 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 9.0.0.4503 |
| ProductVersionNumber: | 9.0.0.4503 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | tttttt Corporation |
| FileDescription: | MLS Migrate DLL |
| FileVersion: | 9.00.00.4503 (xpsp.080413-0845) |
| InternalName: | migrate.exe |
| LegalCopyright: | © tttttt Corporation. All rights reserved. |
| OriginalFileName: | migrate.exe |
| ProductName: | tttttt® Windows Media Services |
| ProductVersion: | 9.00.00.4503 |
Total processes
143
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6216 | "C:\Users\admin\AppData\Local\Temp\java_update_qudpcaa.exe" | C:\Users\admin\AppData\Local\Temp\java_update_qudpcaa.exe | zvzvgjn.exe | ||||||||||||
User: admin Company: tttttt Corporation Integrity Level: HIGH Description: MLS Migrate DLL Exit code: 0 Version: 9.00.00.4503 (xpsp.080413-0845) Modules
| |||||||||||||||
| 6224 | "C:\PROGRA~3\Mozilla\zvzvgjn.exe" -eglgyjm | C:\ProgramData\Mozilla\zvzvgjn.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: tttttt Corporation Integrity Level: SYSTEM Description: MLS Migrate DLL Exit code: 0 Version: 9.00.00.4503 (xpsp.080413-0845) Modules
| |||||||||||||||
| 6632 | "C:\Users\admin\Downloads\migrate.exe" | C:\Users\admin\Downloads\migrate.exe | explorer.exe | ||||||||||||
User: admin Company: tttttt Corporation Integrity Level: MEDIUM Description: MLS Migrate DLL Exit code: 0 Version: 9.00.00.4503 (xpsp.080413-0845) Modules
| |||||||||||||||
| 6732 | "C:\PROGRA~3\Mozilla\zvzvgjn.exe" -eglgyjm | C:\ProgramData\Mozilla\zvzvgjn.exe | svchost.exe | ||||||||||||
User: admin Company: tttttt Corporation Integrity Level: MEDIUM Description: MLS Migrate DLL Exit code: 0 Version: 9.00.00.4503 (xpsp.080413-0845) Modules
| |||||||||||||||
Total events
3 545
Read events
3 534
Write events
11
Delete events
0
Modification events
| (PID) Process: | (6732) zvzvgjn.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\Windows |
| Operation: | write | Name: | AppInit_DLLs |
Value: C:\PROGRA~3\Mozilla\pysrkic.dll | |||
| (PID) Process: | (6732) zvzvgjn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6732) zvzvgjn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6732) zvzvgjn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6732) zvzvgjn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6224) zvzvgjn.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\Windows |
| Operation: | write | Name: | AppInit_DLLs |
Value: C:\PROGRA~3\Mozilla\pysrkic.dll | |||
| (PID) Process: | (6224) zvzvgjn.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\Windows |
| Operation: | write | Name: | LoadAppInit_DLLs |
Value: 1 | |||
Executable files
3
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6732 | zvzvgjn.exe | C:\Users\admin\AppData\Local\Temp\java_update_qudpcaa.exe | executable | |
MD5:132DB977E15B5E245A7C7D417DAD7ABF | SHA256:F1E50CB3D646E2C9B11E2EE9BFED328C84E06961E713E227DD8E446C3764D0F6 | |||
| 6632 | migrate.exe | C:\ProgramData\Mozilla\zvzvgjn.exe | executable | |
MD5:C9157BD3348C944C58E083CD7B526646 | SHA256:CB5DA88651B62C39F981B8C8CE003C5A93ACEE166699EC7123C907C794E24F0D | |||
| 6224 | zvzvgjn.exe | C:\ProgramData\Mozilla\pysrkic.dll | executable | |
MD5:4AF43D029E7005BA671E7D4CFFB58865 | SHA256:91BD938469EB5B99E5AA0C2ADFAE07F61E771CDA37C170D63A18731C223CC88E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
43
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6884 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3276 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6700 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1028 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
1028 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3844 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5300 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3844 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3276 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3276 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6884 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |