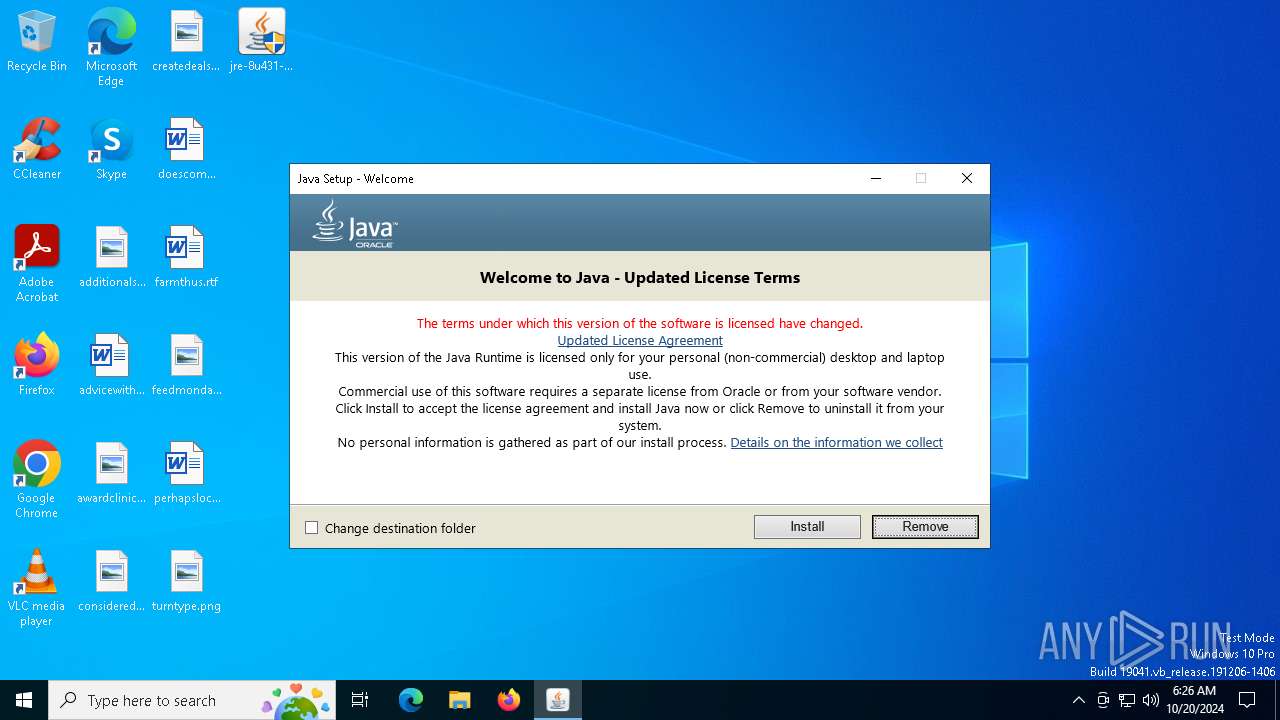
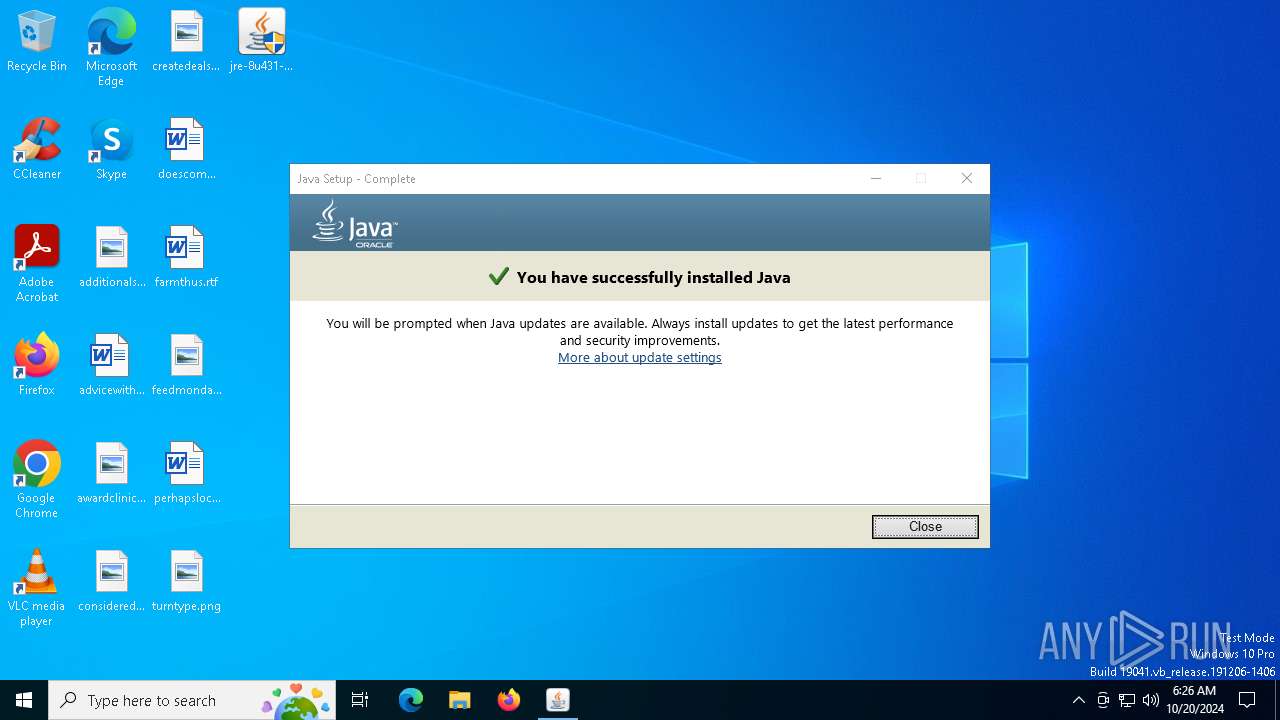
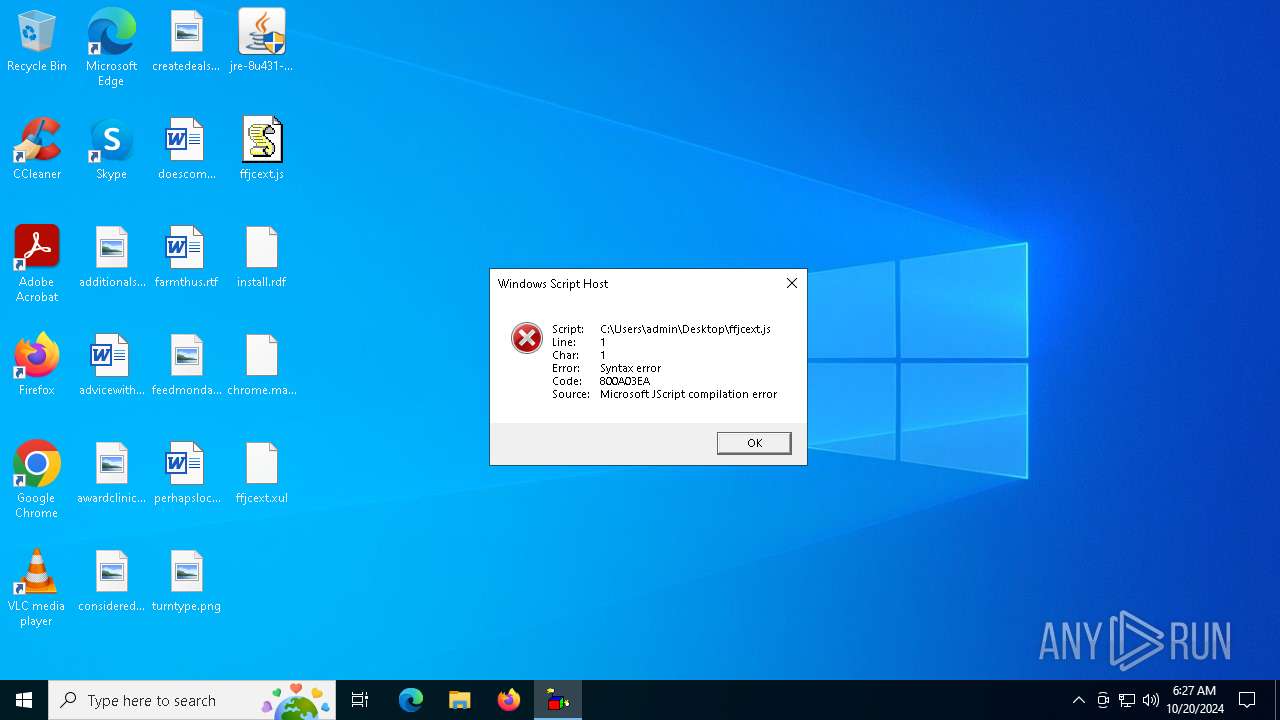
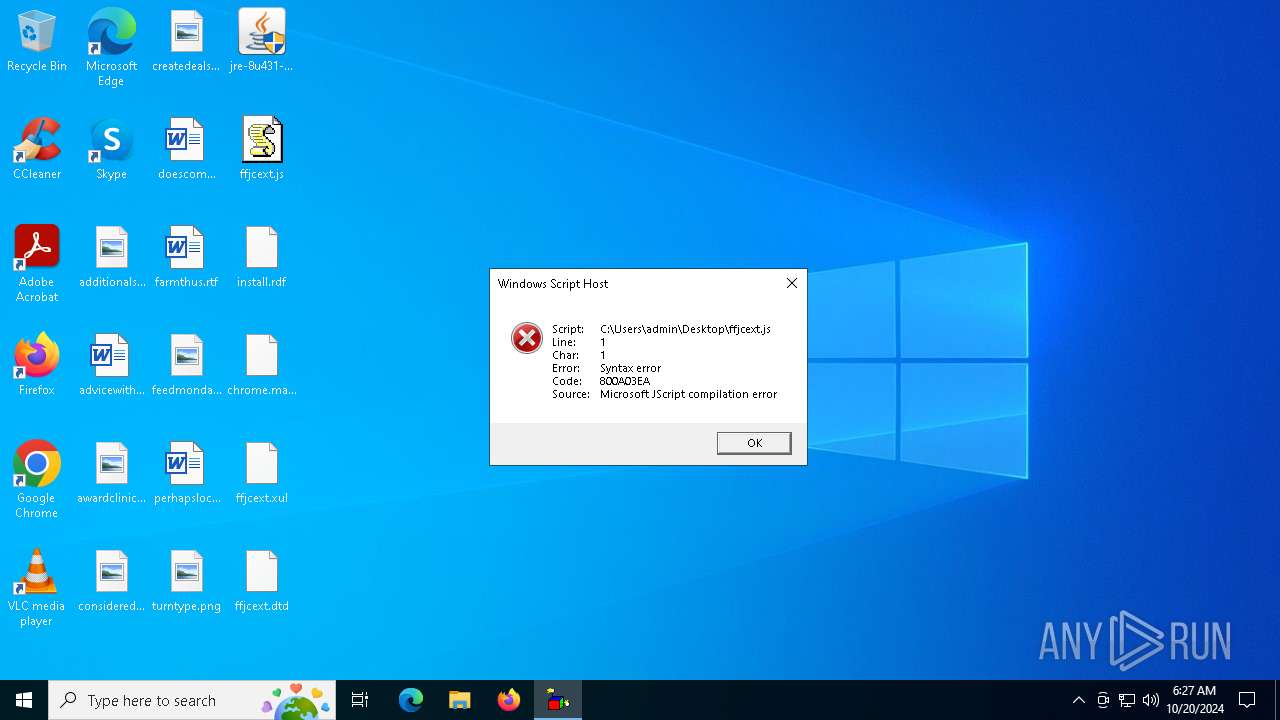
| File name: | jre-8u431-windows-x64.exe |
| Full analysis: | https://app.any.run/tasks/60d50897-46dc-4acb-b832-77f7efac3265 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2024, 06:25:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | FFEB97A82F30DD074B5CE8F22EA8D471 |
| SHA1: | 64D3D90A74623824854E187DB734B787C6259FFA |
| SHA256: | 6E6E541BC5B96EF69EBAF247D8CF9BFB0EB8B6FEE289A9F163DB74B08983CEEC |
| SSDEEP: | 393216:M4dkwuiNurrQBnZtKdH9I6qfzotexeIU2UlQgwHVAbpG6QkLoGbS61G+Y8CAbul:MjINUQBnYpCCeYI/UlQpHVAb+pUbQWe |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks for Java to be installed
- jre-8u431-windows-x64.exe (PID: 3728)
- msiexec.exe (PID: 5236)
- msiexec.exe (PID: 4676)
- installer.exe (PID: 6196)
Reads Microsoft Outlook installation path
- jre-8u431-windows-x64.exe (PID: 3728)
Reads security settings of Internet Explorer
- jre-8u431-windows-x64.exe (PID: 3728)
- installer.exe (PID: 6196)
Checks Windows Trust Settings
- jre-8u431-windows-x64.exe (PID: 3728)
- msiexec.exe (PID: 4676)
Reads Internet Explorer settings
- jre-8u431-windows-x64.exe (PID: 3728)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 4676)
Reads Mozilla Firefox installation path
- MSI518C.tmp (PID: 7044)
Process drops legitimate windows executable
- msiexec.exe (PID: 4676)
The process drops C-runtime libraries
- msiexec.exe (PID: 4676)
Executable content was dropped or overwritten
- installer.exe (PID: 6196)
Creates/Modifies COM task schedule object
- installer.exe (PID: 6196)
INFO
Reads the computer name
- jre-8u431-windows-x64.exe (PID: 4304)
- jre-8u431-windows-x64.exe (PID: 3728)
- msiexec.exe (PID: 4676)
- msiexec.exe (PID: 5236)
- MSI518C.tmp (PID: 7044)
- installer.exe (PID: 6196)
Reads the machine GUID from the registry
- jre-8u431-windows-x64.exe (PID: 3728)
- msiexec.exe (PID: 4676)
Checks supported languages
- jre-8u431-windows-x64.exe (PID: 3728)
- msiexec.exe (PID: 4676)
- jre-8u431-windows-x64.exe (PID: 4304)
- msiexec.exe (PID: 5236)
- jaureg.exe (PID: 6344)
- MSI518C.tmp (PID: 7044)
- installer.exe (PID: 6196)
- javaw.exe (PID: 6876)
Creates files or folders in the user directory
- jre-8u431-windows-x64.exe (PID: 3728)
- msiexec.exe (PID: 4676)
Reads Environment values
- jre-8u431-windows-x64.exe (PID: 3728)
Create files in a temporary directory
- jre-8u431-windows-x64.exe (PID: 4304)
- MSI518C.tmp (PID: 7044)
- javaw.exe (PID: 6876)
Checks proxy server information
- jre-8u431-windows-x64.exe (PID: 3728)
Reads the software policy settings
- jre-8u431-windows-x64.exe (PID: 3728)
- msiexec.exe (PID: 4676)
The process uses the downloaded file
- jre-8u431-windows-x64.exe (PID: 3728)
Application launched itself
- msiexec.exe (PID: 4676)
- Acrobat.exe (PID: 7076)
- AcroCEF.exe (PID: 4236)
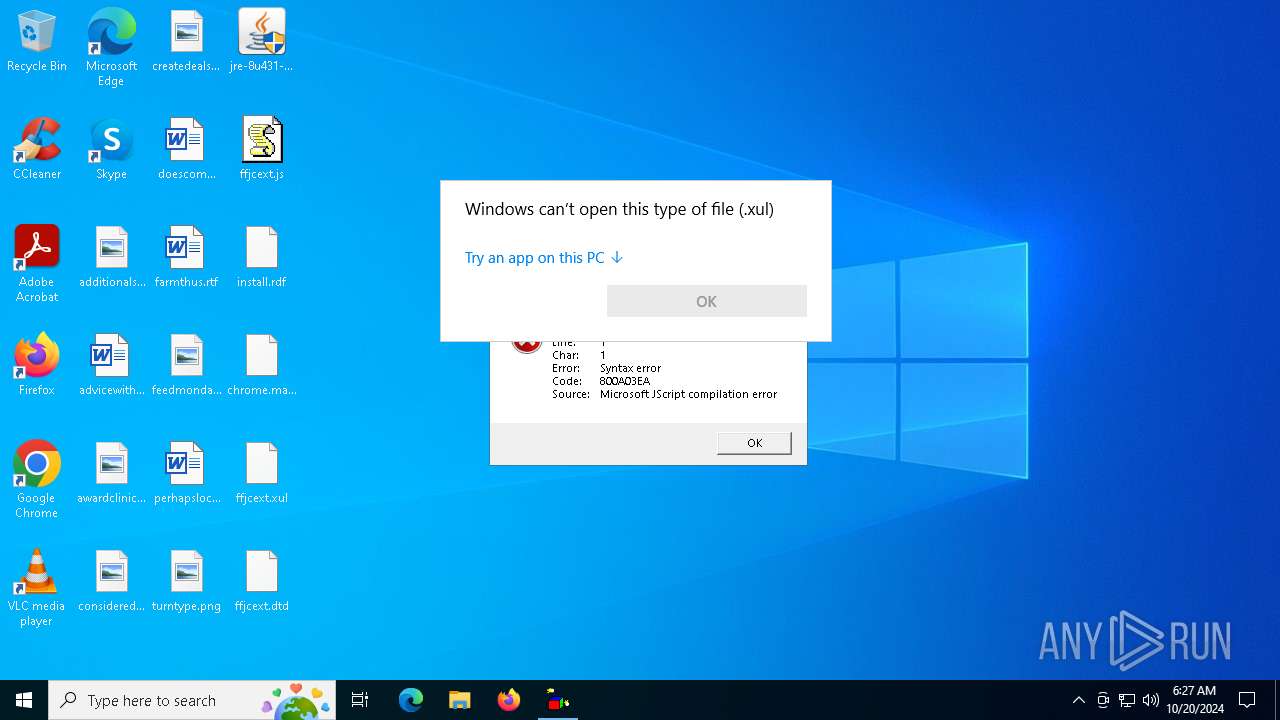
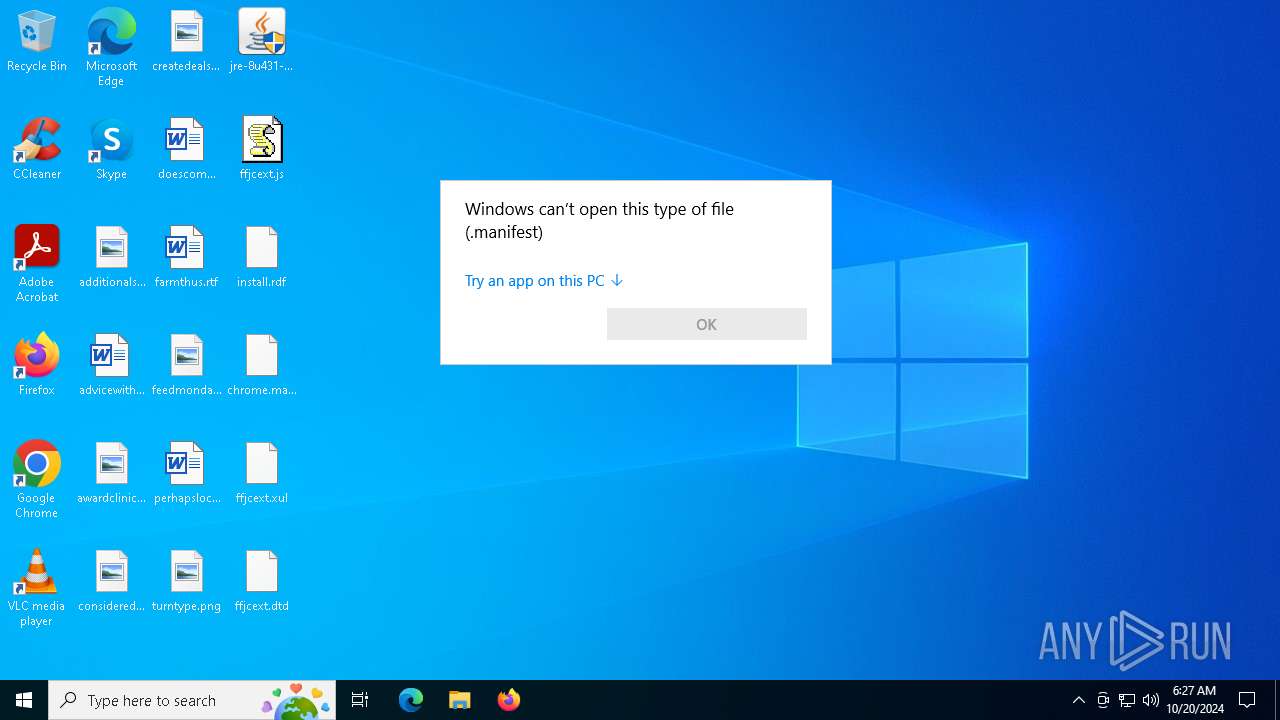
Starts application with an unusual extension
- msiexec.exe (PID: 4676)
Reads CPU info
- msiexec.exe (PID: 4676)
Creates files in the program directory
- installer.exe (PID: 6196)
- javaw.exe (PID: 6876)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4676)
Creates a software uninstall entry
- msiexec.exe (PID: 4676)
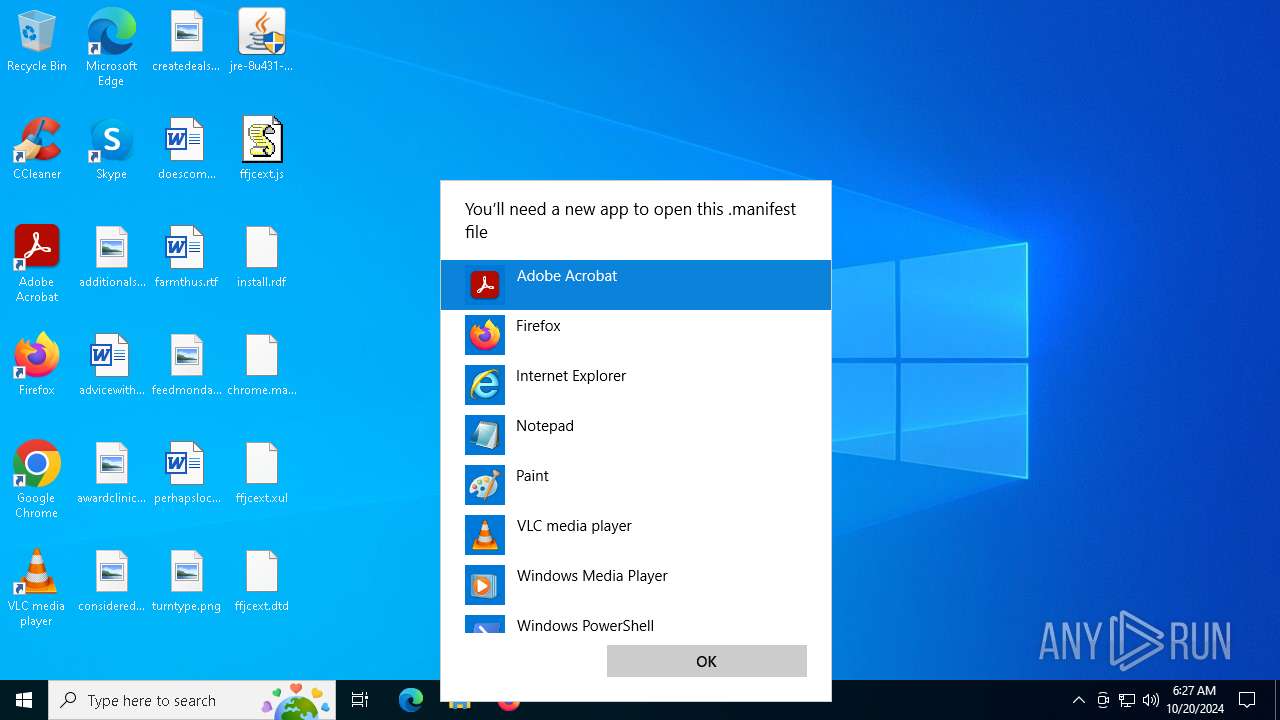
Manual execution by a user
- OpenWith.exe (PID: 6676)
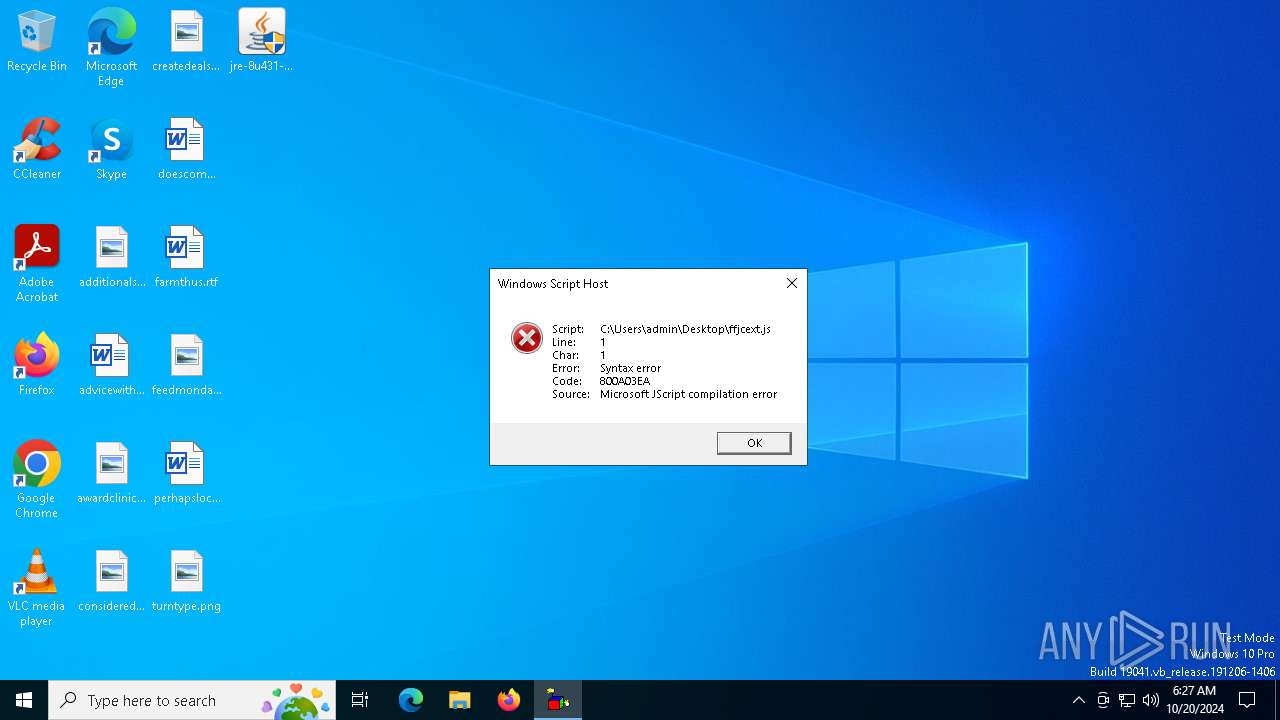
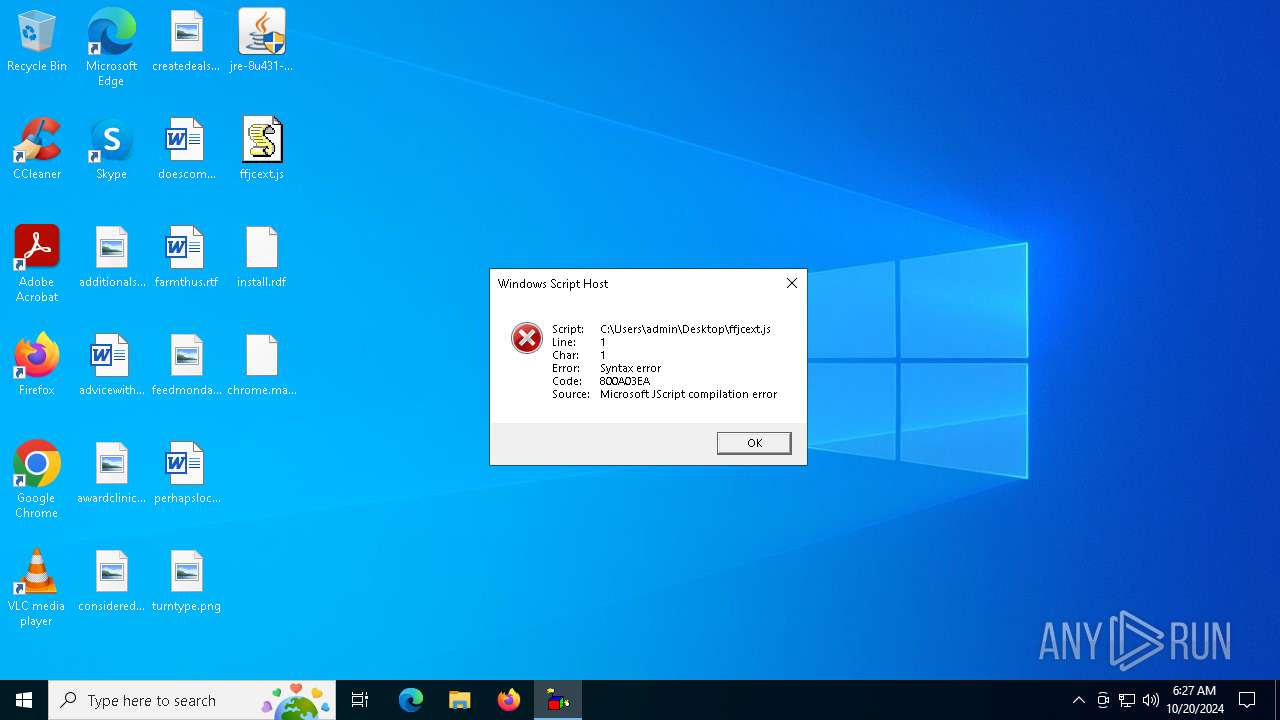
- wscript.exe (PID: 6296)
- OpenWith.exe (PID: 6632)
- OpenWith.exe (PID: 5984)
- OpenWith.exe (PID: 204)
- OpenWith.exe (PID: 7132)
- wscript.exe (PID: 6028)
- OpenWith.exe (PID: 7040)
- OpenWith.exe (PID: 3824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (53.4) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (35.5) |
| .exe | | | Win32 Executable (generic) (5.8) |
| .exe | | | Generic Win/DOS Executable (2.5) |
| .exe | | | DOS Executable Generic (2.5) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:09:30 08:52:03+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.36 |
| CodeSize: | 262656 |
| InitializedDataSize: | 68974592 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x19564 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.0.4310.10 |
| ProductVersionNumber: | 8.0.4310.10 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Oracle Corporation |
| FileDescription: | Java Platform SE binary |
| FileVersion: | 8.0.4310.10 |
| FullVersion: | 1.8.0_431-b10 |
| InternalName: | Setup Launcher |
| LegalCopyright: | Copyright © 2024 |
| OriginalFileName: | wrapper_jre_offline.exe |
| ProductName: | Java Platform SE 8 U431 |
| ProductVersion: | 8.0.4310.10 |
Total processes
156
Monitored processes
39
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\install.rdf | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 512 | "C:\Program Files\Java\jre1.8.0_431\bin\javaws.exe" -wait -fix -shortcut -silent | C:\Program Files\Java\jre1.8.0_431\bin\javaws.exe | installer.exe | ||||||||||||
User: SYSTEM Company: Oracle Corporation Integrity Level: SYSTEM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.431.2.10 Modules
| |||||||||||||||
| 920 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 "C:\Users\admin\Desktop\chrome.manifest" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1764 | "C:\Windows\SysWOW64\msiexec.exe" /x {4A03706F-666A-4037-7777-5F2748764D10} /qn | C:\Windows\SysWOW64\msiexec.exe | — | jaureg.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1768 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2160 --field-trial-handle=1592,i,1501380815532324455,916454563420977779,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | AcroCEF.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2056 | "C:\Program Files\Java\jre1.8.0_431\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre1.8.0_431" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfNDMxXGxpYlxkZXBsb3kuamFyAC1EamF2YS5zZWN1cml0eS5wb2xpY3k9ZmlsZTpDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfNDMxXGxpYlxzZWN1cml0eVxqYXZhd3MucG9saWN5AC1EdHJ1c3RQcm94eT10cnVlAC1YdmVyaWZ5OnJlbW90ZQAtRGpubHB4LmhvbWU9QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzQzMVxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURzdW4uYXd0Lndhcm11cD10cnVlAC1YYm9vdGNsYXNzcGF0aC9hOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF80MzFcbGliXGphdmF3cy5qYXI7QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzQzMVxsaWJcZGVwbG95LmphcjtDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfNDMxXGxpYlxwbHVnaW4uamFyAC1EamF2YS5hd3QuaGVhZGxlc3M9dHJ1ZQAtRGpubHB4Lmp2bT1DOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfNDMxXGJpblxqYXZhdy5leGU= -ma LXdhaXQALWZpeAAtcGVybWlzc2lvbnMALXNpbGVudAAtbm90V2ViSmF2YQ== | C:\Program Files\Java\jre1.8.0_431\bin\jp2launcher.exe | — | javaws.exe | |||||||||||
User: SYSTEM Company: Oracle Corporation Integrity Level: SYSTEM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.431.2.10 Modules
| |||||||||||||||
| 2364 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2428 --field-trial-handle=1592,i,1501380815532324455,916454563420977779,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 3004 | -Djdk.disableLastUsageTracking -cp "C:\Program Files\Java\jre1.8.0_431\bin\..\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -getUserPreviousDecisionsExist 30 | C:\Program Files\Java\jre1.8.0_431\bin\javaw.exe | — | jre-8u431-windows-x64.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.4310.10 Modules
| |||||||||||||||
| 3728 | "C:\Users\admin\AppData\Local\Temp\jds590171.tmp\jre-8u431-windows-x64.exe" | C:\Users\admin\AppData\Local\Temp\jds590171.tmp\jre-8u431-windows-x64.exe | jre-8u431-windows-x64.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Version: 8.0.4310.10 Modules
| |||||||||||||||
| 3764 | -Djdk.disableLastUsageTracking -cp "C:\Program Files\Java\jre1.8.0_431\bin\..\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -getUserWebJavaStatus | C:\Program Files\Java\jre1.8.0_431\bin\javaw.exe | — | jre-8u431-windows-x64.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.4310.10 Modules
| |||||||||||||||
Total events
57 601
Read events
30 354
Write events
12 663
Delete events
14 584
Modification events
| (PID) Process: | (3728) jre-8u431-windows-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft |
| Operation: | delete value | Name: | InstallStatus |
Value: | |||
| (PID) Process: | (3728) jre-8u431-windows-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3728) jre-8u431-windows-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3728) jre-8u431-windows-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3728) jre-8u431-windows-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft\Java Update\Policy |
| Operation: | write | Name: | Country |
Value: MY | |||
| (PID) Process: | (3728) jre-8u431-windows-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (3728) jre-8u431-windows-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
| (PID) Process: | (3728) jre-8u431-windows-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft\Java Update\Policy |
| Operation: | write | Name: | PostStatusUrl |
Value: https://sjremetrics.java.com/b/ss//6 | |||
| (PID) Process: | (3728) jre-8u431-windows-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft\Java Update\Policy |
| Operation: | write | Name: | Method |
Value: joff | |||
| (PID) Process: | (4676) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 44120000C30907FAB822DB01 | |||
Executable files
337
Suspicious files
200
Text files
219
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4304 | jre-8u431-windows-x64.exe | C:\Users\admin\AppData\Local\Temp\jds590171.tmp\jds590187.tmp | — | |
MD5:— | SHA256:— | |||
| 4304 | jre-8u431-windows-x64.exe | C:\Users\admin\AppData\Local\Temp\jds590171.tmp\jre-8u431-windows-x64.exe | — | |
MD5:— | SHA256:— | |||
| 3728 | jre-8u431-windows-x64.exe | C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_431_x64\jre1.8.0_43164.msi | — | |
MD5:— | SHA256:— | |||
| 4676 | msiexec.exe | C:\Windows\Installer\93c9f.msi | — | |
MD5:— | SHA256:— | |||
| 4304 | jre-8u431-windows-x64.exe | C:\Users\admin\AppData\Local\Temp\jusched.log | text | |
MD5:30CFEC8972BE55F26257151FB3949521 | SHA256:03338F5365A742520179D4786AD01C8E040C589217A3E96B7200BE9BCC0F24ED | |||
| 4676 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | der | |
MD5:06DDD1D63258CFDB247A4C342E06F8DE | SHA256:7ABEF69DA1F46CF322E26D3760147ED096516E5000DD11FAF76F380A83E39FD2 | |||
| 3728 | jre-8u431-windows-x64.exe | C:\Users\admin\AppData\LocalLow\Oracle\Java\jre1.8.0_431_x64\Java3BillDevices.png | image | |
MD5:8E52EFC6798ED074072F527309A1BA25 | SHA256:12491EBC4EB99BF014D3BC44F770114BDE013E84CBEC2633303559A8C6E5F991 | |||
| 4676 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:611F206D1CE400FC1F15C0791F428108 | SHA256:F9FFCF08B834675E19913B2FDCEC42932E2DDBD6878F625BD8103236E7A84B07 | |||
| 4676 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8EC9B1D0ABBD7F98B401D425828828CE_D2F6556190F7B1A25A117FFB5467EEBD | binary | |
MD5:62AAAD92376CD432AFE3F2BA6837B648 | SHA256:4A270FB6867D25BD2F7FE9392A2AB82F85B9E151F44E1E8C33ECB8B3FF69EDA8 | |||
| 4676 | msiexec.exe | C:\Windows\Installer\MSI4B98.tmp | executable | |
MD5:1FBEED63000F90489598D7D3F04718C1 | SHA256:C37784E576B9791C6D7513C84D8B4922E37F5DFE95500DDE936BD6DC67E06539 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
35
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 23.56.205.197:443 | https://rps-svcs.oracle.com/services/countrylookup | unknown | — | — | unknown |
4676 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
4676 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
— | — | OPTIONS | 204 | 52.5.13.197:443 | https://p13n.adobe.io/psdk/v2/content?surfaceId=ACROBAT_READER_MASTER_SURFACEID&surfaceId=DC_READER_LAUNCH_CARD&surfaceId=DC_Reader_RHP_Banner&surfaceId=DC_Reader_RHP_Retention&surfaceId=Edit_InApp_Aug2020&surfaceId=DC_FirstMile_Right_Sec_Surface&surfaceId=DC_Reader_Upsell_Cards&surfaceId=DC_FirstMile_Home_View_Surface&surfaceId=DC_Reader_RHP_Intent_Banner&surfaceId=DC_Reader_Disc_LHP_Banner&surfaceId=DC_Reader_Edit_LHP_Banner&surfaceId=DC_Reader_Convert_LHP_Banner&surfaceId=DC_Reader_Sign_LHP_Banner&surfaceId=DC_Reader_More_LHP_Banner&surfaceId=DC_Reader_Disc_LHP_Retention&adcProductLanguage=en-us&adcVersion=23.1.20093&adcProductType=SingleClientMini&adcOSType=WIN&adcCountryCode=MY&adcXAPIClientID=api_reader_desktop_win_23.1.20093&encodingScheme=BASE_64 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 104.126.37.123:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
javadl-esd-secure.oracle.com |
| whitelisted |
rps-svcs.oracle.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.java.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |