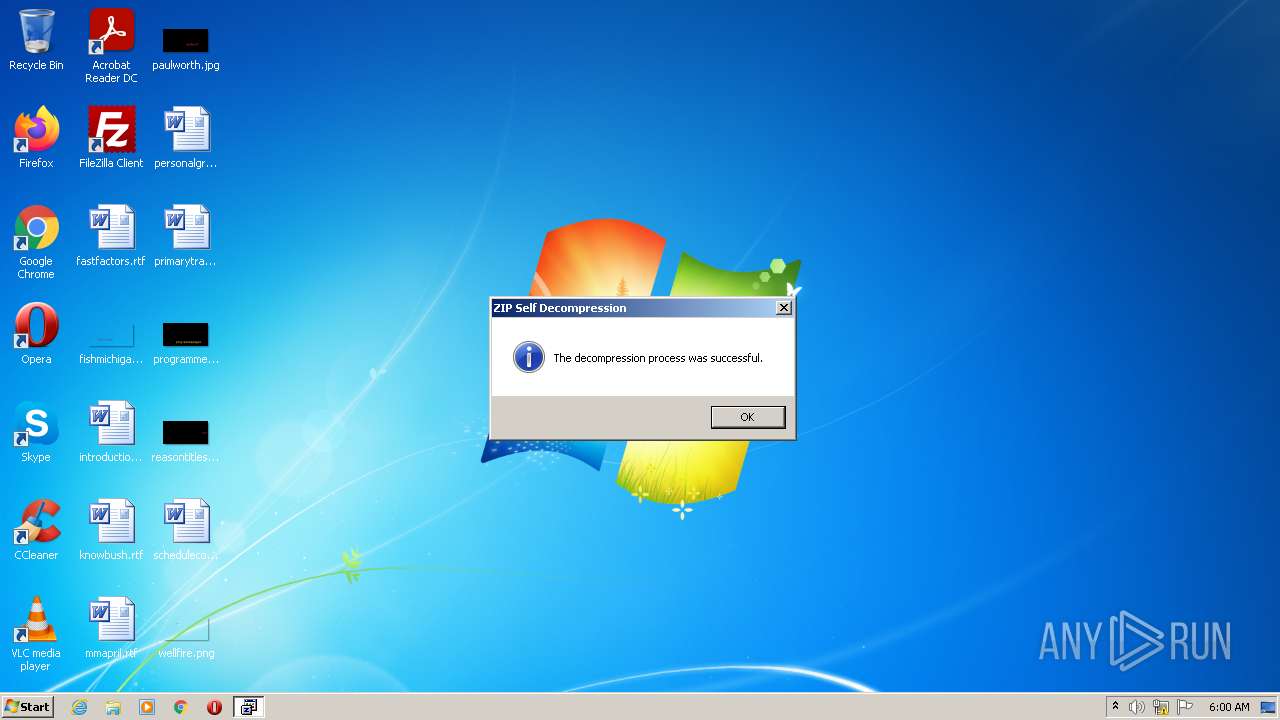
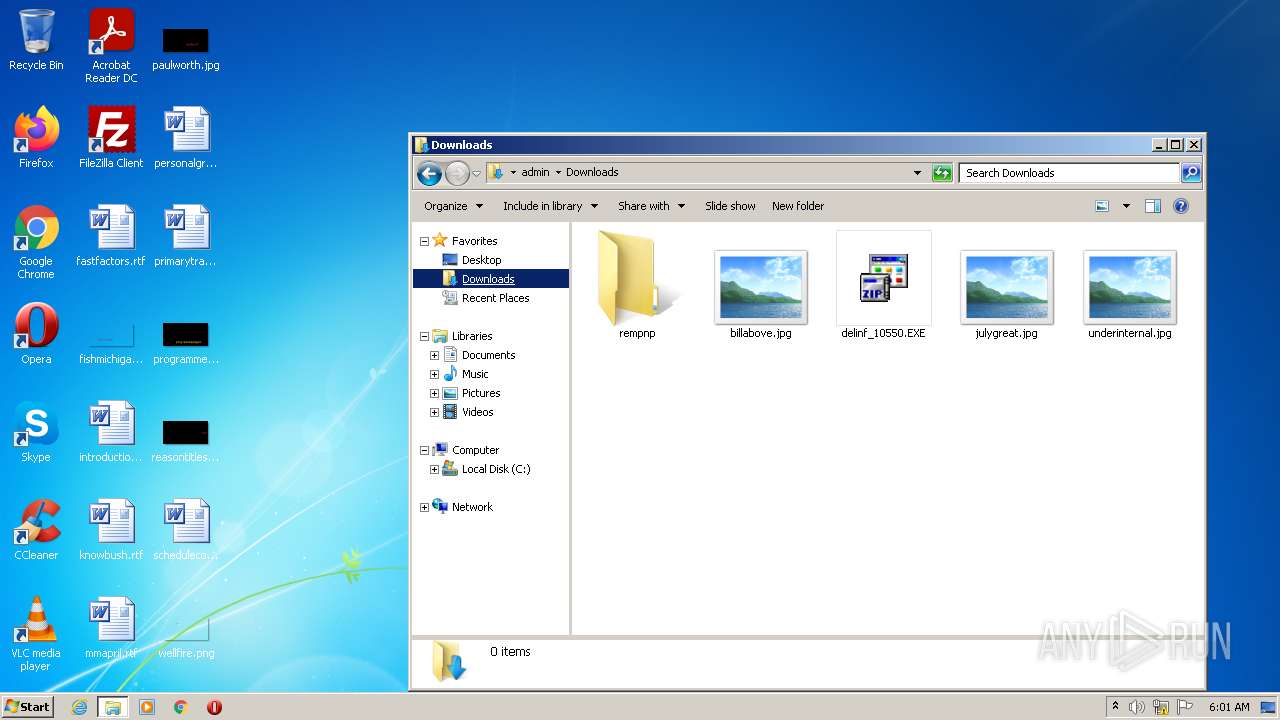
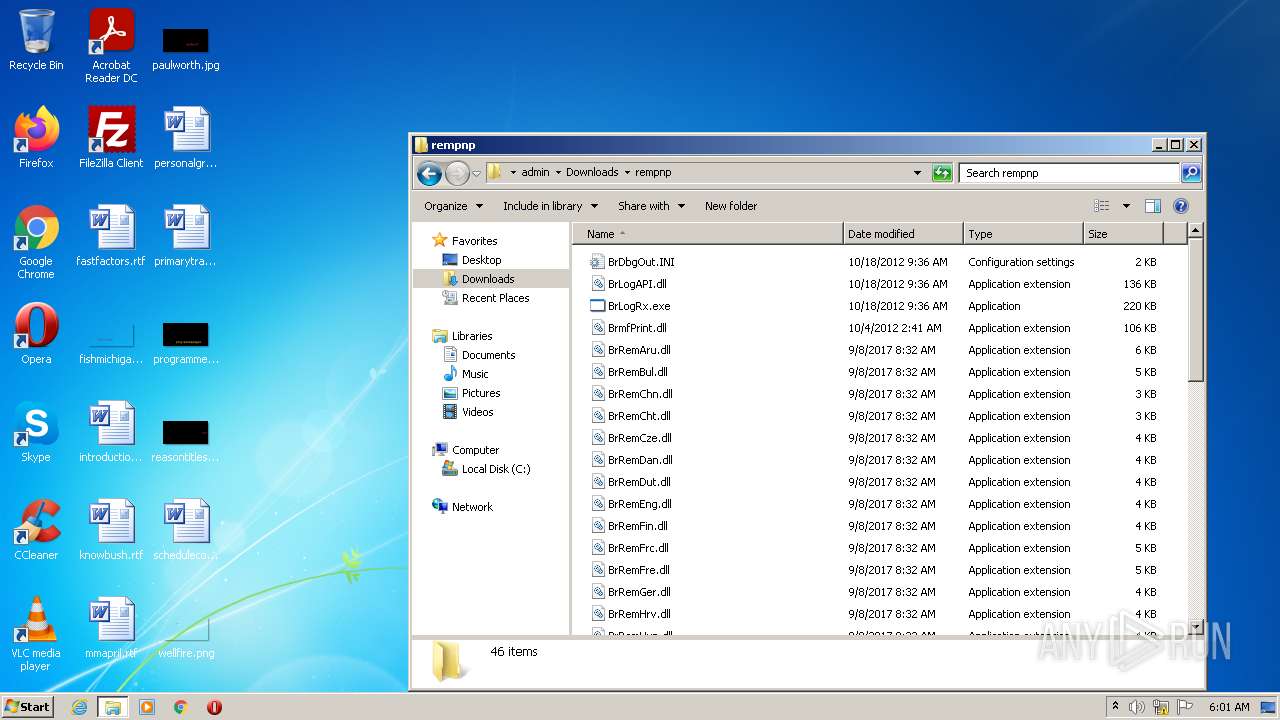
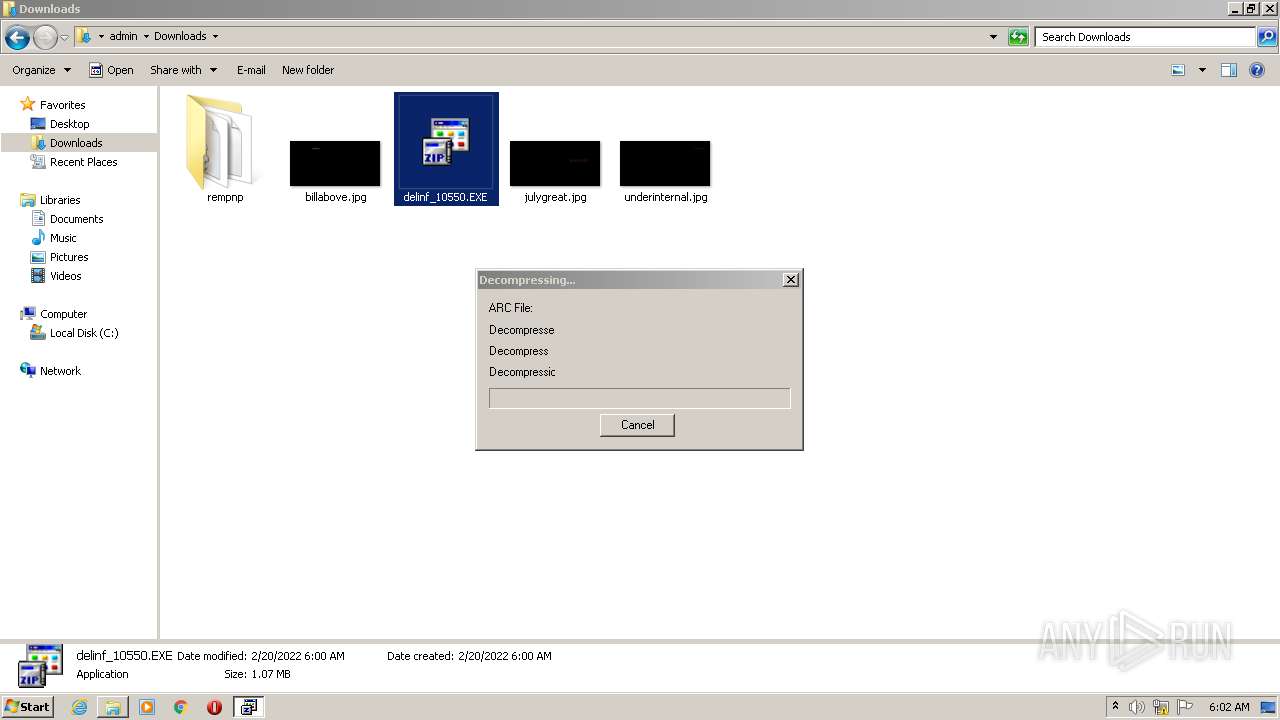
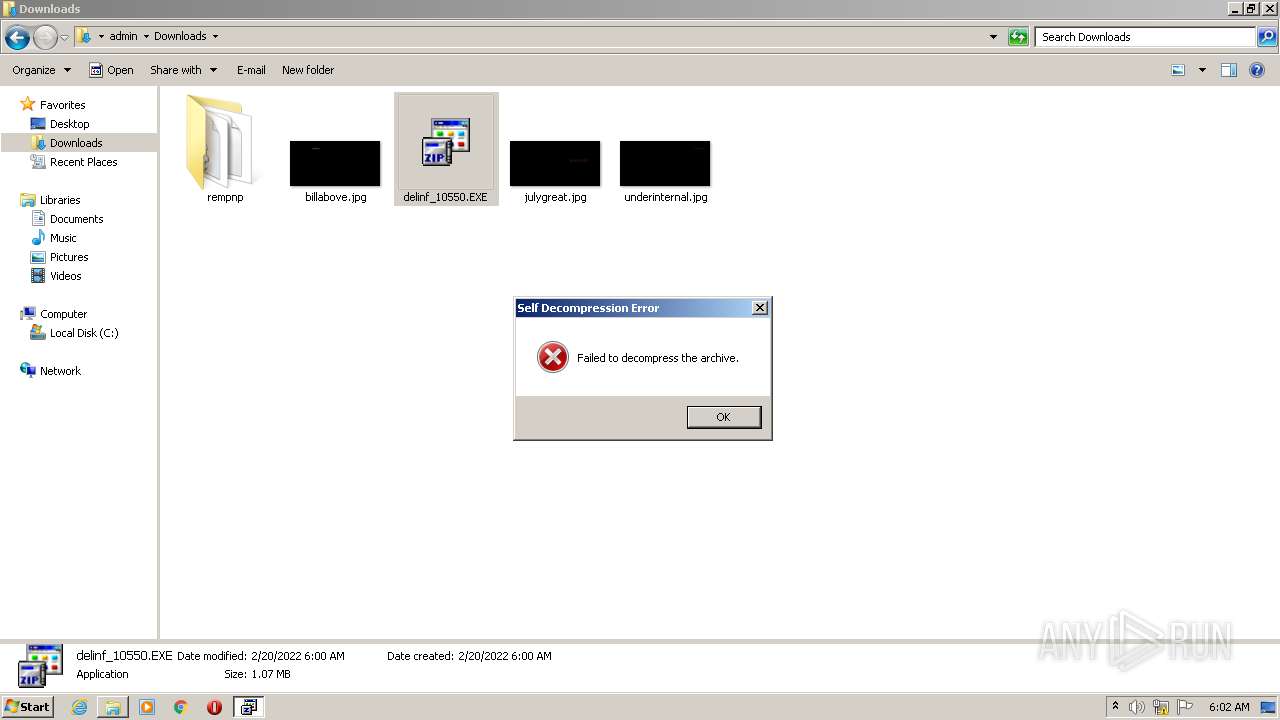
| File name: | delinf_10550.EXE |
| Full analysis: | https://app.any.run/tasks/949dd95a-6b52-4fbf-bdd0-a66c1a80d994 |
| Verdict: | Malicious activity |
| Analysis date: | February 20, 2022, 06:00:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | AC7780DFAB98CF06C6A32CDC5A2B3F05 |
| SHA1: | B6FBB75911C4DD278FF9CE4BEC441276B7C0E545 |
| SHA256: | 6E5FC3CD45CEE3E01ACFA6A8C04764D8ECC7B6FF4B6B3D5E4445D7FCC394F088 |
| SSDEEP: | 12288:Cid562NuMK2csNgWS9+CvD1qMkFaW3BNpCcgSHFROf7iVET7o9b46tWcywBrAR:btNo2c8gWSHvDARlNpCcf67kWcvh2 |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3028)
- delinf_10550.EXE (PID: 1404)
- Explorer.EXE (PID: 1656)
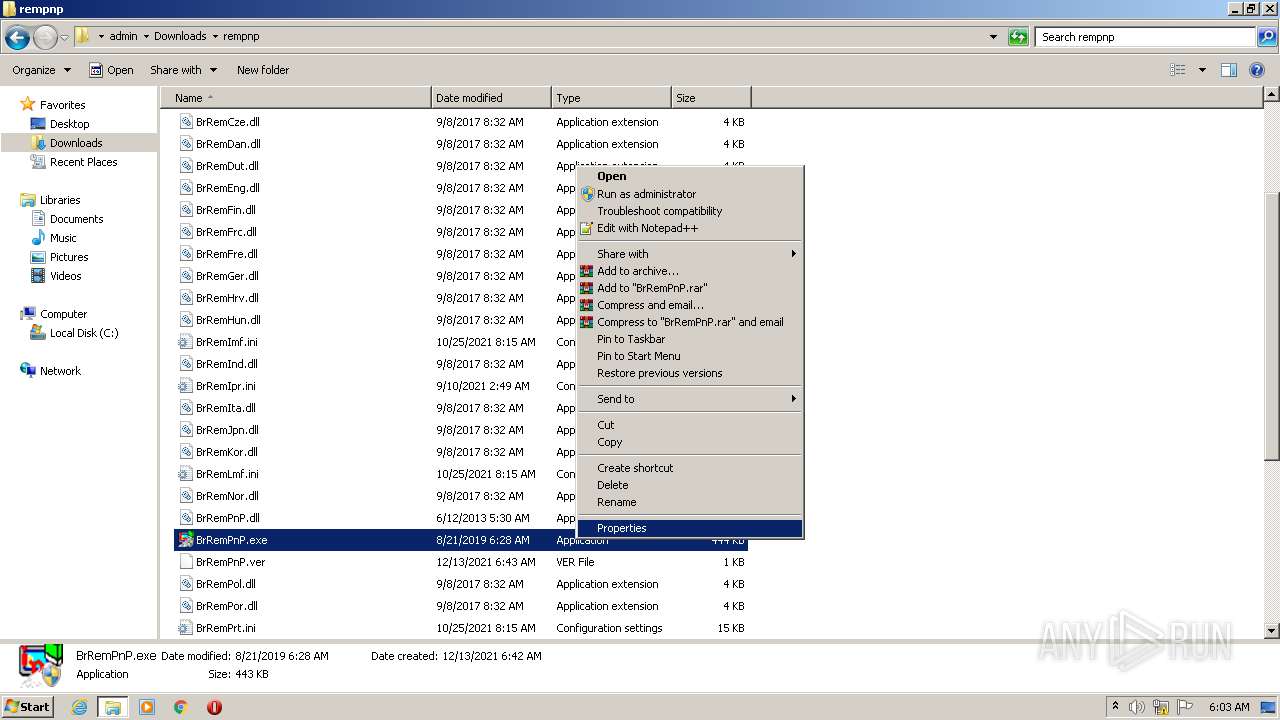
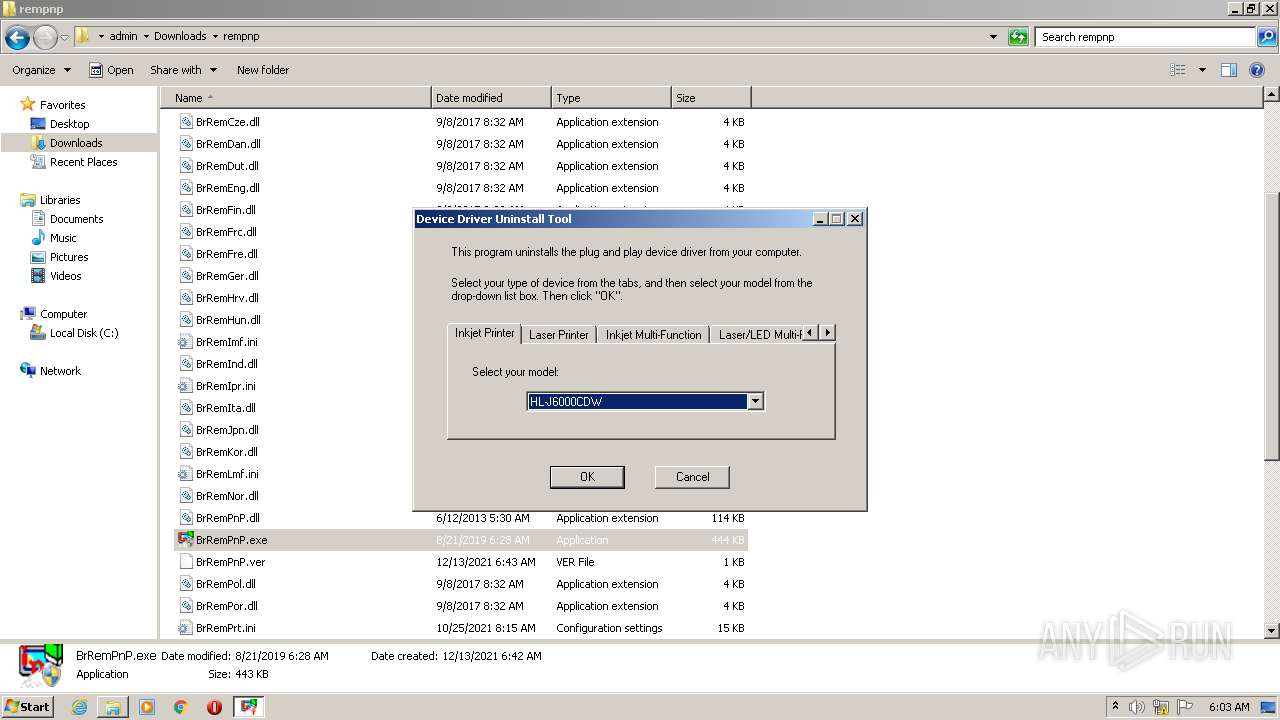
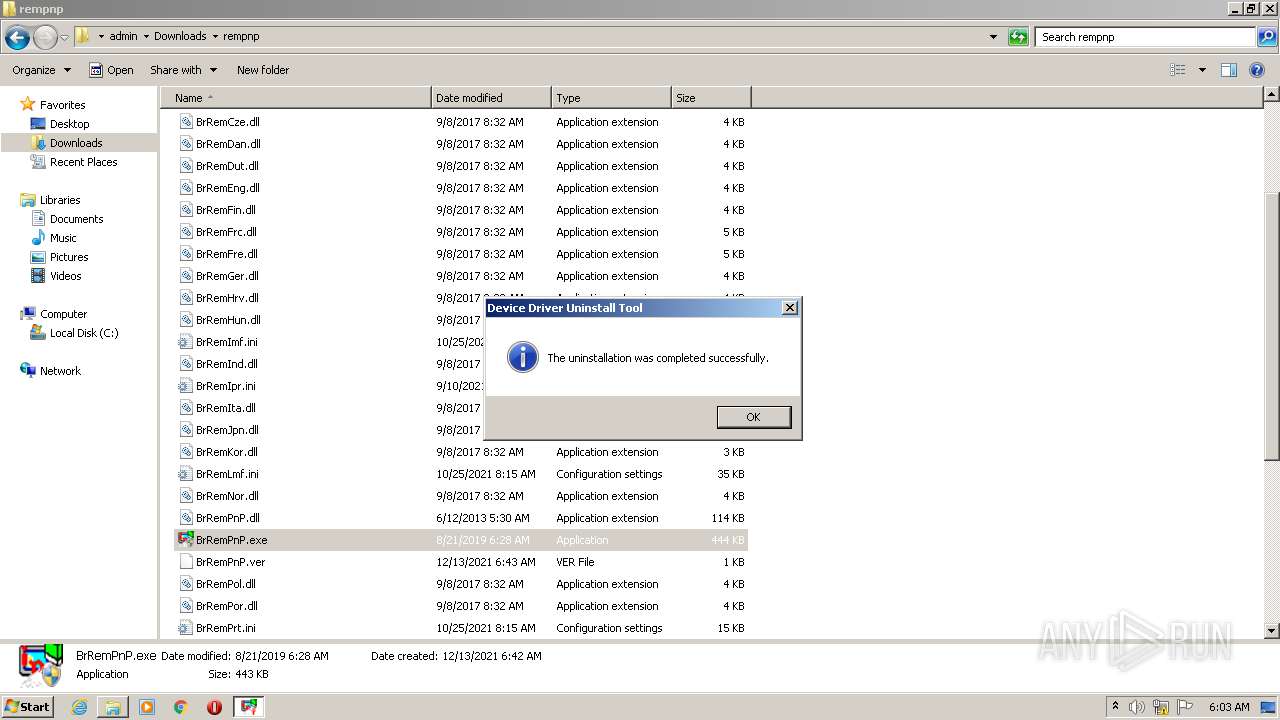
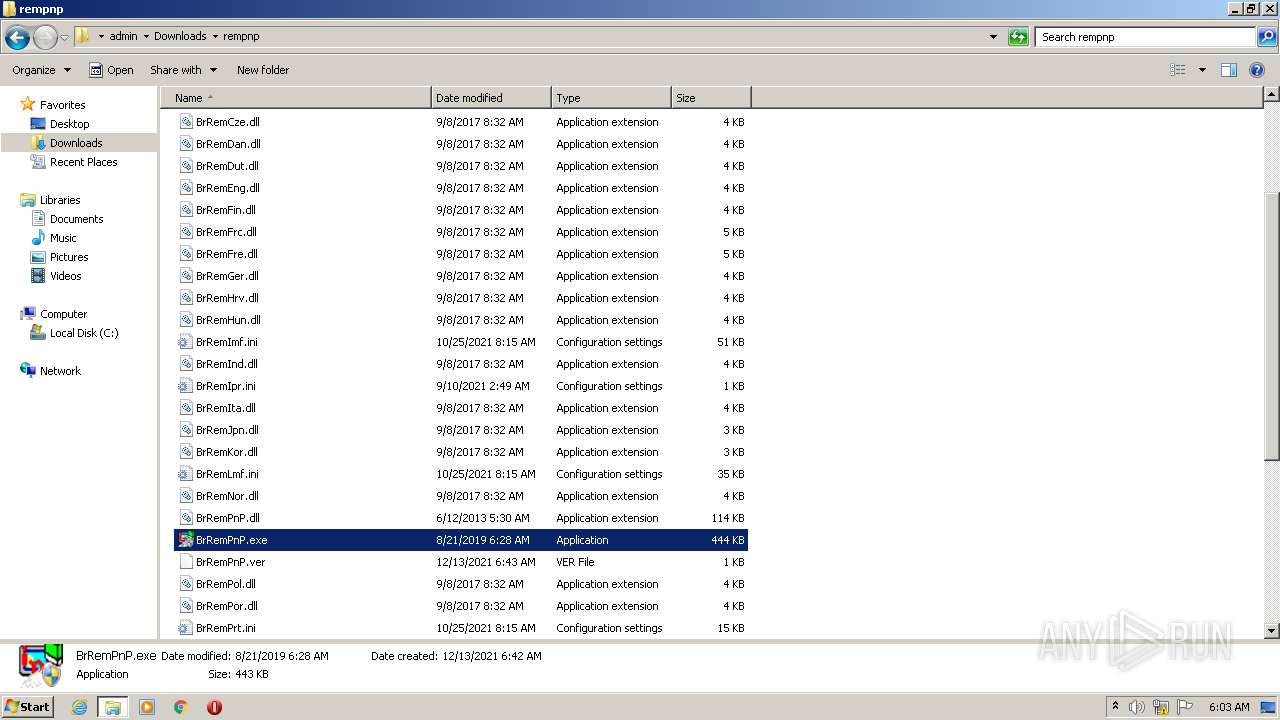
- BrRemPnP.exe (PID: 2940)
- rundll32.exe (PID: 2280)
- rundll32.exe (PID: 568)
- rundll32.exe (PID: 3056)
- rundll32.exe (PID: 2000)
- rundll32.exe (PID: 1200)
- rundll32.exe (PID: 2496)
- rundll32.exe (PID: 2812)
- rundll32.exe (PID: 1272)
- rundll32.exe (PID: 3532)
- rundll32.exe (PID: 2588)
- SearchProtocolHost.exe (PID: 3472)
- BrRemPnP.exe (PID: 3220)
- delinf_10550.EXE (PID: 532)
- rundll32.exe (PID: 1632)
- rundll32.exe (PID: 2808)
- rundll32.exe (PID: 2024)
- rundll32.exe (PID: 2608)
- rundll32.exe (PID: 2552)
- rundll32.exe (PID: 2840)
- rundll32.exe (PID: 3264)
- rundll32.exe (PID: 1604)
- rundll32.exe (PID: 628)
- rundll32.exe (PID: 3700)
Drops executable file immediately after starts
- delinf_10550.EXE (PID: 1404)
- delinf_10550.EXE (PID: 532)
Application was dropped or rewritten from another process
- BrRemPnP.exe (PID: 2152)
- BrRemPnP.exe (PID: 2940)
- BrLogRx.exe (PID: 2580)
- BrLogRx.exe (PID: 3548)
- BrRemPnP.exe (PID: 3220)
- BrLogRx.exe (PID: 3896)
- BrLogRx.exe (PID: 3860)
- BrLogRx.exe (PID: 3780)
SUSPICIOUS
Executable content was dropped or overwritten
- delinf_10550.EXE (PID: 1404)
- delinf_10550.EXE (PID: 532)
Checks supported languages
- delinf_10550.EXE (PID: 1404)
- BrLogRx.exe (PID: 2580)
- BrRemPnP.exe (PID: 2940)
- BrLogRx.exe (PID: 3548)
- delinf_10550.EXE (PID: 532)
- BrLogRx.exe (PID: 3860)
- BrLogRx.exe (PID: 3896)
- BrRemPnP.exe (PID: 3220)
- BrLogRx.exe (PID: 3780)
Drops a file that was compiled in debug mode
- delinf_10550.EXE (PID: 1404)
- delinf_10550.EXE (PID: 532)
Drops a file with too old compile date
- delinf_10550.EXE (PID: 1404)
- delinf_10550.EXE (PID: 532)
Reads default file associations for system extensions
- Explorer.EXE (PID: 1656)
Reads the computer name
- BrRemPnP.exe (PID: 2940)
- BrLogRx.exe (PID: 2580)
- BrLogRx.exe (PID: 3548)
- BrRemPnP.exe (PID: 3220)
- BrLogRx.exe (PID: 3860)
- BrLogRx.exe (PID: 3780)
Creates files in the program directory
- BrLogRx.exe (PID: 2580)
Uses RUNDLL32.EXE to load library
- BrRemPnP.exe (PID: 2940)
- BrRemPnP.exe (PID: 3220)
Reads CPU info
- BrLogRx.exe (PID: 2580)
Creates files in the user directory
- Explorer.EXE (PID: 1656)
INFO
Checks supported languages
- explorer.exe (PID: 3504)
- rundll32.exe (PID: 3056)
- rundll32.exe (PID: 2280)
- rundll32.exe (PID: 568)
- rundll32.exe (PID: 2000)
- rundll32.exe (PID: 3532)
- rundll32.exe (PID: 1200)
- rundll32.exe (PID: 2496)
- rundll32.exe (PID: 2588)
- rundll32.exe (PID: 2812)
- rundll32.exe (PID: 1272)
- NOTEPAD.EXE (PID: 3032)
- SearchProtocolHost.exe (PID: 3472)
- rundll32.exe (PID: 1632)
- rundll32.exe (PID: 2808)
- rundll32.exe (PID: 2608)
- rundll32.exe (PID: 2024)
- rundll32.exe (PID: 2552)
- rundll32.exe (PID: 3264)
- rundll32.exe (PID: 2840)
- rundll32.exe (PID: 628)
- rundll32.exe (PID: 3700)
- rundll32.exe (PID: 1604)
- WINWORD.EXE (PID: 3708)
Manual execution by user
- explorer.exe (PID: 3504)
Reads the computer name
- explorer.exe (PID: 3504)
- rundll32.exe (PID: 2280)
- rundll32.exe (PID: 568)
- rundll32.exe (PID: 3056)
- rundll32.exe (PID: 2000)
- rundll32.exe (PID: 3532)
- rundll32.exe (PID: 1200)
- rundll32.exe (PID: 2496)
- rundll32.exe (PID: 2588)
- rundll32.exe (PID: 2812)
- rundll32.exe (PID: 1272)
- SearchProtocolHost.exe (PID: 3472)
- rundll32.exe (PID: 2552)
- rundll32.exe (PID: 2808)
- rundll32.exe (PID: 1632)
- rundll32.exe (PID: 2608)
- rundll32.exe (PID: 2024)
- rundll32.exe (PID: 2840)
- rundll32.exe (PID: 3264)
- rundll32.exe (PID: 3700)
- rundll32.exe (PID: 628)
- rundll32.exe (PID: 1604)
- WINWORD.EXE (PID: 3708)
Reads Microsoft Office registry keys
- Explorer.EXE (PID: 1656)
- WINWORD.EXE (PID: 3708)
Starts Microsoft Office Application
- Explorer.EXE (PID: 1656)
Creates files in the user directory
- WINWORD.EXE (PID: 3708)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (24.4) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.6) |
| .exe | | | UPX compressed Win32 Executable (21.2) |
| .exe | | | Win32 EXE Yoda's Crypter (20.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.1) |
EXIF
EXE
| SpecialBuild: | - |
|---|---|
| ProductVersion: | 7, 0, 2, 0 |
| ProductName: | FileCompact |
| PrivateBuild: | - |
| OriginalFileName: | DXZIPSELF.EXE |
| LegalTrademarks: | - |
| LegalCopyright: | (C) SOURCENEXT CORPORATION |
| InternalName: | DXZIPSELF |
| FileVersion: | 7, 0, 2, 0 |
| FileDescription: | ZIP SELFEXTRACT |
| CompanyName: | SOURCENEXT CORPORATION |
| Comments: | - |
| CharacterSet: | Unicode |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Windows NT 32-bit |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 7.0.2.0 |
| FileVersionNumber: | 7.0.2.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x33e4 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 684032 |
| CodeSize: | 24576 |
| LinkerVersion: | 6 |
| PEType: | PE32 |
| TimeStamp: | 2017:06:14 07:31:06+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 14-Jun-2017 05:31:06 |
| Detected languages: |
|
| Comments: | - |
| CompanyName: | SOURCENEXT CORPORATION |
| FileDescription: | ZIP 自己解凍 |
| FileVersion: | 7, 0, 2, 0 |
| InternalName: | DXZIPSELF |
| LegalCopyright: | (C) SOURCENEXT CORPORATION |
| LegalTrademarks: | - |
| OriginalFilename: | DXZIPSELF.EXE |
| PrivateBuild: | - |
| ProductName: | ファイルコンパクト |
| ProductVersion: | 7, 0, 2, 0 |
| SpecialBuild: | - |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 14-Jun-2017 05:31:06 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000055AC | 0x00006000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.18364 |
.rdata | 0x00007000 | 0x00000E08 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.95903 |
.data | 0x00008000 | 0x00004048 | 0x00003000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.706867 |
.rsrc | 0x0000D000 | 0x000A0020 | 0x000A1000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.62583 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.87323 | 982 | UNKNOWN | Japanese - Japan | RT_MANIFEST |
2 | 4.10568 | 2216 | UNKNOWN | Japanese - Japan | RT_ICON |
3 | 3.185 | 296 | UNKNOWN | Japanese - Japan | RT_ICON |
4 | 2.94765 | 744 | UNKNOWN | Japanese - Japan | RT_ICON |
5 | 2.84283 | 296 | UNKNOWN | Japanese - Japan | RT_ICON |
63 | 4.83216 | 432 | UNKNOWN | Japanese - Japan | RT_STRING |
64 | 3.99305 | 178 | UNKNOWN | Japanese - Japan | RT_STRING |
94 | 3.8829 | 86 | UNKNOWN | Japanese - Japan | RT_STRING |
101 | 2.5943 | 48 | UNKNOWN | Japanese - Japan | RT_GROUP_ICON |
102 | 3.91704 | 270 | UNKNOWN | Japanese - Japan | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
Total processes
86
Monitored processes
36
Malicious processes
28
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 532 | "C:\Users\admin\Downloads\delinf_10550.EXE" | C:\Users\admin\Downloads\delinf_10550.EXE | Explorer.EXE | ||||||||||||
User: admin Company: SOURCENEXT CORPORATION Integrity Level: MEDIUM Description: ZIP SELFEXTRACT Exit code: 1 Version: 7, 0, 2, 0 Modules
| |||||||||||||||
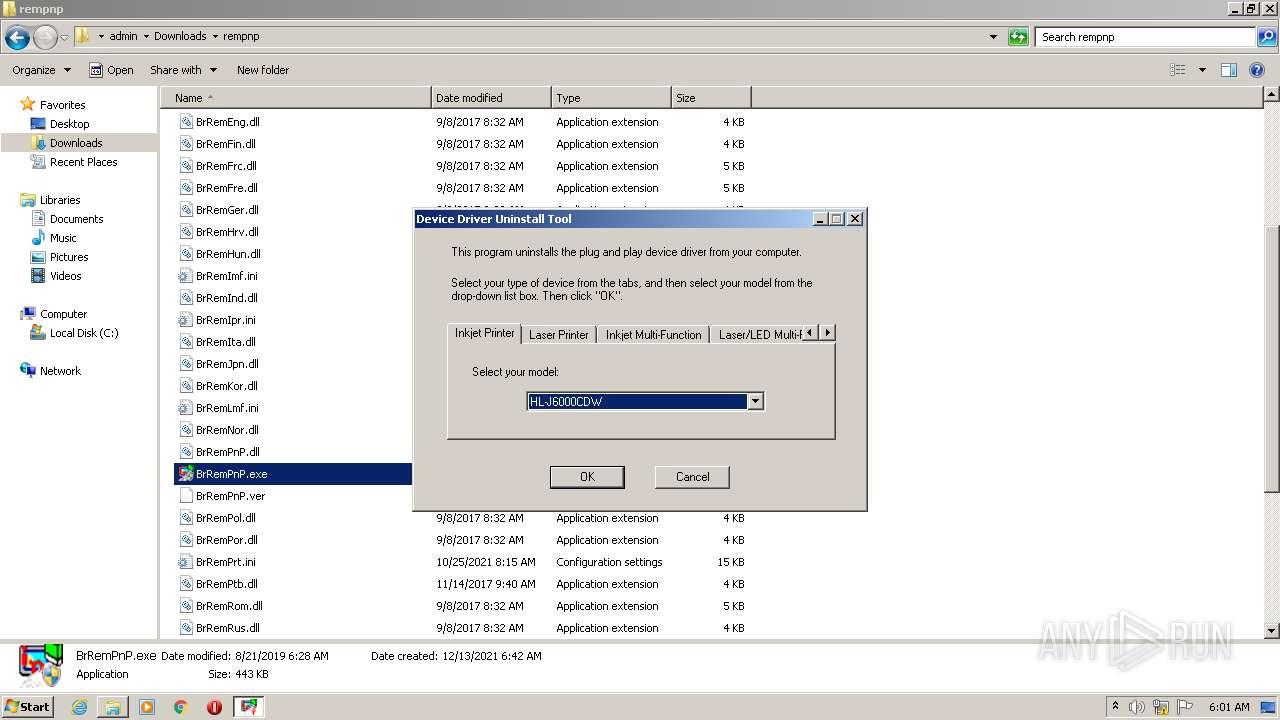
| 568 | rundll32.exe "C:\Users\admin\Downloads\rempnp\BrRemPnP.dll",CB_ConnectionDeletePrinterEntryByDriverName "Brother HL-J6000CDW Printer" | C:\Windows\system32\rundll32.exe | — | BrRemPnP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 628 | rundll32.exe "C:\Users\admin\Downloads\rempnp\BrRemPnP.dll",CB_ConnectionDeletePrinterEntryByDriverName "Brother DCP-115C LPT Printer" | C:\Windows\system32\rundll32.exe | — | BrRemPnP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1200 | rundll32.exe "C:\Users\admin\Downloads\rempnp\BrRemPnP.dll",CB_ConnectionDeletePrinterEntryByDriverName "Brother HL-J6000CDW USB Printer" | C:\Windows\system32\rundll32.exe | — | BrRemPnP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1272 | rundll32.exe "C:\Users\admin\Downloads\rempnp\BrRemPnP.dll",CB_ConnectionDeletePrinterEntryByDriverName "Brother HL-J6000CDW series" | C:\Windows\system32\rundll32.exe | — | BrRemPnP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1404 | "C:\Users\admin\Downloads\delinf_10550.EXE" | C:\Users\admin\Downloads\delinf_10550.EXE | Explorer.EXE | ||||||||||||
User: admin Company: SOURCENEXT CORPORATION Integrity Level: MEDIUM Description: ZIP SELFEXTRACT Exit code: 0 Version: 7, 0, 2, 0 Modules
| |||||||||||||||
| 1604 | rundll32.exe "C:\Users\admin\Downloads\rempnp\BrRemPnP.dll",CB_ConnectionDeletePrinterEntryByDriverName "Brother DCP-115C series" | C:\Windows\system32\rundll32.exe | — | BrRemPnP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1632 | rundll32.exe "C:\Users\admin\Downloads\rempnp\BrRemPnP.dll",CB_ConnectionDeletePrinterEntryByDriverName "Brother DCP-115C" | C:\Windows\system32\rundll32.exe | — | BrRemPnP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1656 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2000 | rundll32.exe "C:\Users\admin\Downloads\rempnp\BrRemPnP.dll",CB_ConnectionDeletePrinterEntryByDriverName "Brother HL-J6000CDW BR-Script3J" | C:\Windows\system32\rundll32.exe | — | BrRemPnP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
10 153
Read events
9 054
Write events
956
Delete events
143
Modification events
| (PID) Process: | (1656) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | P:\Hfref\nqzva\Qbjaybnqf\qryvas_10550.RKR |
Value: 00000000000000000000000000000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF000000000000000000000000 | |||
| (PID) Process: | (1656) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000470100007B020000636717013F0000004A0000008E0F0D004D006900630072006F0073006F00660074002E0049006E007400650072006E00650074004500780070006C006F007200650072002E00440065006600610075006C007400000028003E004000A4E75102B8E651020000000000000000000000000000080274E45102000008026CE25102000000000000D26CFFFFFFFF705911750000000000000000A4E251027C900D75000400000000000008E35102FFFFFFFF38EA7000FFFFFFFF080A7400D80E740030EA7000D4E25102F7AF3D7680D0707614F05102081D3E76E4613E766820700008E351020000000071000000BBF2CB00E8E25102A1693E766820700008E351020000000014E551023F613E766820700008E3510200000400000000800400000026E4510298E351025DA5147726E45102D26E147779A51477D6794D7526E4510210E65102000100006400610072E3510226E451026F0061006D0069006E0067005C006D006900630072006F0073006F0066007400CCE351023400000080E35102DE70310033003300350033003800310030003000F8E551025A000000A0E351021DA71477D6610E02D4E351025A00000010E651025C00000011000000104F7000084F7000F8E55102C4E3510220E40000D7F3CB00D0E351025E903E7620E45102D4E3510203943E760000000064561802FCE35102A9933E7664561802A8E45102D8511802BD933E7600000000D8511802A8E4510204E45102000000007200000032AC5D004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000045003700430036004500410037004400320037007D005C0063006D0064002E0065007800650000000000D45D38760000000005000000D80B3902000000000000000000000000000000000000000000000000CB0501AD000000000000000000000000000000000000000000000000000000000000000030E69D01A8323876B8E59D01C0E59D0154E59D0100000000000000000000000000000000480B39020000000005000000D80B390200000000340C390268E59D01B0E59D010000000000000000E8B93902050000002000000000000000000000000400400000001A0098E59D0100000000000000000000000000000000040000009EE69D0110E69D015DA5B3779EE69D01D26EB37779A5B377114526769EE69D0188E89D0104000000C6E69D0138E69D015DA5B377C6E69D01D26EB37779A5B37739452676C6E69D01B0E89D0100010000E8FE1C0012E69D01C6E69D0168E69D015DA5310033003300350033003800310011000000104F1D00084F1D001AE79D018CE69D015DA5B37774E60000B777588D24E69D015E90D47674E69D0128E69D010394D47600000000D422E60250E69D01A993D476D422E602FCE69D01481EE602BD93D47600000000481EE602FCE69D0158E69D01000000007200000032AC5D004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000045003700430036004500410037004400320037007D005C0063006D0064002E0065007800650000000000D45D38760000000005000000D80B3902000000000000000000000000000000000000000000000000CB0501AD000000000000000000000000000000000000000000000000000000000000000030E69D01A8323876B8E59D01C0E59D0154E59D0100000000000000000000000000000000480B39020000000005000000D80B390200000000340C390268E59D01B0E59D010000000000000000E8B93902050000002000000000000000000000000400400000001A0098E59D0100000000000000000000000000000000040000009EE69D0110E69D015DA5B3779EE69D01D26EB37779A5B377114526769EE69D0188E89D0104000000C6E69D0138E69D015DA5B377C6E69D01D26EB37779A5B37739452676C6E69D01B0E89D0100010000E8FE1C0012E69D01C6E69D0168E69D015DA5310033003300350033003800310011000000104F1D00084F1D001AE79D018CE69D015DA5B37774E60000B777588D24E69D015E90D47674E69D0128E69D010394D47600000000D422E60250E69D01A993D476D422E602FCE69D01481EE602BD93D47600000000481EE602FCE69D0158E69D01 | |||
| (PID) Process: | (1656) Explorer.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1656) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | P:\Hfref\nqzva\Qbjaybnqf\qryvas_10550.RKR |
Value: 000000000000000000000000D6130000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF000000000000000000000000 | |||
| (PID) Process: | (1656) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000470100007B020000397B17013F0000004A0000008E0F0D004D006900630072006F0073006F00660074002E0049006E007400650072006E00650074004500780070006C006F007200650072002E00440065006600610075006C007400000028003E004000A4E75102B8E651020000000000000000000000000000080274E45102000008026CE25102000000000000D26CFFFFFFFF705911750000000000000000A4E251027C900D75000400000000000008E35102FFFFFFFF38EA7000FFFFFFFF080A7400D80E740030EA7000D4E25102F7AF3D7680D0707614F05102081D3E76E4613E766820700008E351020000000071000000BBF2CB00E8E25102A1693E766820700008E351020000000014E551023F613E766820700008E3510200000400000000800400000026E4510298E351025DA5147726E45102D26E147779A51477D6794D7526E4510210E65102000100006400610072E3510226E451026F0061006D0069006E0067005C006D006900630072006F0073006F0066007400CCE351023400000080E35102DE70310033003300350033003800310030003000F8E551025A000000A0E351021DA71477D6610E02D4E351025A00000010E651025C00000011000000104F7000084F7000F8E55102C4E3510220E40000D7F3CB00D0E351025E903E7620E45102D4E3510203943E760000000064561802FCE35102A9933E7664561802A8E45102D8511802BD933E7600000000D8511802A8E4510204E45102000000007200000032AC5D004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000045003700430036004500410037004400320037007D005C0063006D0064002E0065007800650000000000D45D38760000000005000000D80B3902000000000000000000000000000000000000000000000000CB0501AD000000000000000000000000000000000000000000000000000000000000000030E69D01A8323876B8E59D01C0E59D0154E59D0100000000000000000000000000000000480B39020000000005000000D80B390200000000340C390268E59D01B0E59D010000000000000000E8B93902050000002000000000000000000000000400400000001A0098E59D0100000000000000000000000000000000040000009EE69D0110E69D015DA5B3779EE69D01D26EB37779A5B377114526769EE69D0188E89D0104000000C6E69D0138E69D015DA5B377C6E69D01D26EB37779A5B37739452676C6E69D01B0E89D0100010000E8FE1C0012E69D01C6E69D0168E69D015DA5310033003300350033003800310011000000104F1D00084F1D001AE79D018CE69D015DA5B37774E60000B777588D24E69D015E90D47674E69D0128E69D010394D47600000000D422E60250E69D01A993D476D422E602FCE69D01481EE602BD93D47600000000481EE602FCE69D0158E69D01000000007200000032AC5D004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000045003700430036004500410037004400320037007D005C0063006D0064002E0065007800650000000000D45D38760000000005000000D80B3902000000000000000000000000000000000000000000000000CB0501AD000000000000000000000000000000000000000000000000000000000000000030E69D01A8323876B8E59D01C0E59D0154E59D0100000000000000000000000000000000480B39020000000005000000D80B390200000000340C390268E59D01B0E59D010000000000000000E8B93902050000002000000000000000000000000400400000001A0098E59D0100000000000000000000000000000000040000009EE69D0110E69D015DA5B3779EE69D01D26EB37779A5B377114526769EE69D0188E89D0104000000C6E69D0138E69D015DA5B377C6E69D01D26EB37779A5B37739452676C6E69D01B0E89D0100010000E8FE1C0012E69D01C6E69D0168E69D015DA5310033003300350033003800310011000000104F1D00084F1D001AE79D018CE69D015DA5B37774E60000B777588D24E69D015E90D47674E69D0128E69D010394D47600000000D422E60250E69D01A993D476D422E602FCE69D01481EE602BD93D47600000000481EE602FCE69D0158E69D01 | |||
| (PID) Process: | (1656) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {S38OS404-1Q43-42S2-9305-67QR0O28SP23}\rkcybere.rkr |
Value: 0000000032000000670000006F382700000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF80B199421F26D80100000000 | |||
| (PID) Process: | (1656) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000480100007B020000397B17013F0000004A0000008E0F0D004D006900630072006F0073006F00660074002E0049006E007400650072006E00650074004500780070006C006F007200650072002E00440065006600610075006C007400000028003E004000A4E75102B8E651020000000000000000000000000000080274E45102000008026CE25102000000000000D26CFFFFFFFF705911750000000000000000A4E251027C900D75000400000000000008E35102FFFFFFFF38EA7000FFFFFFFF080A7400D80E740030EA7000D4E25102F7AF3D7680D0707614F05102081D3E76E4613E766820700008E351020000000071000000BBF2CB00E8E25102A1693E766820700008E351020000000014E551023F613E766820700008E3510200000400000000800400000026E4510298E351025DA5147726E45102D26E147779A51477D6794D7526E4510210E65102000100006400610072E3510226E451026F0061006D0069006E0067005C006D006900630072006F0073006F0066007400CCE351023400000080E35102DE70310033003300350033003800310030003000F8E551025A000000A0E351021DA71477D6610E02D4E351025A00000010E651025C00000011000000104F7000084F7000F8E55102C4E3510220E40000D7F3CB00D0E351025E903E7620E45102D4E3510203943E760000000064561802FCE35102A9933E7664561802A8E45102D8511802BD933E7600000000D8511802A8E4510204E45102000000007200000032AC5D004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000045003700430036004500410037004400320037007D005C0063006D0064002E0065007800650000000000D45D38760000000005000000D80B3902000000000000000000000000000000000000000000000000CB0501AD000000000000000000000000000000000000000000000000000000000000000030E69D01A8323876B8E59D01C0E59D0154E59D0100000000000000000000000000000000480B39020000000005000000D80B390200000000340C390268E59D01B0E59D010000000000000000E8B93902050000002000000000000000000000000400400000001A0098E59D0100000000000000000000000000000000040000009EE69D0110E69D015DA5B3779EE69D01D26EB37779A5B377114526769EE69D0188E89D0104000000C6E69D0138E69D015DA5B377C6E69D01D26EB37779A5B37739452676C6E69D01B0E89D0100010000E8FE1C0012E69D01C6E69D0168E69D015DA5310033003300350033003800310011000000104F1D00084F1D001AE79D018CE69D015DA5B37774E60000B777588D24E69D015E90D47674E69D0128E69D010394D47600000000D422E60250E69D01A993D476D422E602FCE69D01481EE602BD93D47600000000481EE602FCE69D0158E69D01000000007200000032AC5D004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000045003700430036004500410037004400320037007D005C0063006D0064002E0065007800650000000000D45D38760000000005000000D80B3902000000000000000000000000000000000000000000000000CB0501AD000000000000000000000000000000000000000000000000000000000000000030E69D01A8323876B8E59D01C0E59D0154E59D0100000000000000000000000000000000480B39020000000005000000D80B390200000000340C390268E59D01B0E59D010000000000000000E8B93902050000002000000000000000000000000400400000001A0098E59D0100000000000000000000000000000000040000009EE69D0110E69D015DA5B3779EE69D01D26EB37779A5B377114526769EE69D0188E89D0104000000C6E69D0138E69D015DA5B377C6E69D01D26EB37779A5B37739452676C6E69D01B0E89D0100010000E8FE1C0012E69D01C6E69D0168E69D015DA5310033003300350033003800310011000000104F1D00084F1D001AE79D018CE69D015DA5B37774E60000B777588D24E69D015E90D47674E69D0128E69D010394D47600000000D422E60250E69D01A993D476D422E602FCE69D01481EE602BD93D47600000000481EE602FCE69D0158E69D01 | |||
| (PID) Process: | (1656) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | {9R3995NO-1S9P-4S13-O827-48O24O6P7174}\GnfxOne\Jvaqbjf Rkcybere.yax |
Value: 0000000030000000000000002F000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF80B199421F26D80100000000 | |||
| (PID) Process: | (1656) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000B400000000000000B30000003E000000000000003E0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C0049006E007400650072006E006500740020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000006D000000000078AB287598117500084B7600981175000000000000000000DE1C0000E0791401C8D4D60313A91477E01D32BD0C0C00001027000002000000FF560200FCD4D603D8A81477FF560200E07914011CD5D603C05C18029CD5D60300000000A40100005CD500009BC44C010CD5D6035E903E765CD5D60310D5D60303943E76000000004C61180238D5D603A9933E764C611802E4D5D603C05C1802BD933E7600000000C05C1802E4D5D60340D5D6033E000000000000003E0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C0049006E007400650072006E006500740020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000006D000000000078AB287598117500084B7600981175000000000000000000DE1C0000E0791401C8D4D60313A91477E01D32BD0C0C00001027000002000000FF560200FCD4D603D8A81477FF560200E07914011CD5D603C05C18029CD5D60300000000A40100005CD500009BC44C010CD5D6035E903E765CD5D60310D5D60303943E76000000004C61180238D5D603A9933E764C611802E4D5D603C05C1802BD933E7600000000C05C1802E4D5D60340D5D6033E000000000000003E0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C0049006E007400650072006E006500740020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000006D000000000078AB287598117500084B7600981175000000000000000000DE1C0000E0791401C8D4D60313A91477E01D32BD0C0C00001027000002000000FF560200FCD4D603D8A81477FF560200E07914011CD5D603C05C18029CD5D60300000000A40100005CD500009BC44C010CD5D6035E903E765CD5D60310D5D60303943E76000000004C61180238D5D603A9933E764C611802E4D5D603C05C1802BD933E7600000000C05C1802E4D5D60340D5D603 | |||
| (PID) Process: | (1656) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | {9R3995NO-1S9P-4S13-O827-48O24O6P7174}\GnfxOne\Jvaqbjf Rkcybere.yax |
Value: 00000000300000000000000030000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF80B199421F26D80100000000 | |||
Executable files
79
Suspicious files
0
Text files
15
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1404 | delinf_10550.EXE | C:\Users\admin\Downloads\rempnp\BrmfPrint.dll | executable | |
MD5:— | SHA256:— | |||
| 1404 | delinf_10550.EXE | C:\Users\admin\Downloads\rempnp\BrRemChn.dll | executable | |
MD5:— | SHA256:— | |||
| 1404 | delinf_10550.EXE | C:\Users\admin\Downloads\rempnp\BrRemCze.dll | executable | |
MD5:— | SHA256:— | |||
| 1404 | delinf_10550.EXE | C:\Users\admin\Downloads\rempnp\BrRemCht.dll | executable | |
MD5:— | SHA256:— | |||
| 1404 | delinf_10550.EXE | C:\Users\admin\Downloads\rempnp\BrRemDan.dll | executable | |
MD5:— | SHA256:— | |||
| 1404 | delinf_10550.EXE | C:\Users\admin\Downloads\rempnp\BrRemDut.dll | executable | |
MD5:— | SHA256:— | |||
| 1404 | delinf_10550.EXE | C:\Users\admin\Downloads\rempnp\BrRemEng.dll | executable | |
MD5:— | SHA256:— | |||
| 1404 | delinf_10550.EXE | C:\Users\admin\Downloads\rempnp\BrRemAru.dll | executable | |
MD5:— | SHA256:— | |||
| 1404 | delinf_10550.EXE | C:\Users\admin\Downloads\rempnp\BrRemBul.dll | executable | |
MD5:— | SHA256:— | |||
| 1404 | delinf_10550.EXE | C:\Users\admin\Downloads\rempnp\BrDbgOut.INI | ini | |
MD5:AEC0BC72AD2C945E97A7EBF1ECE7908E | SHA256:DDC94690431FA032D5F029552E6682588FCE1FE33A61EDDAC03D5CD3EA877F3C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report