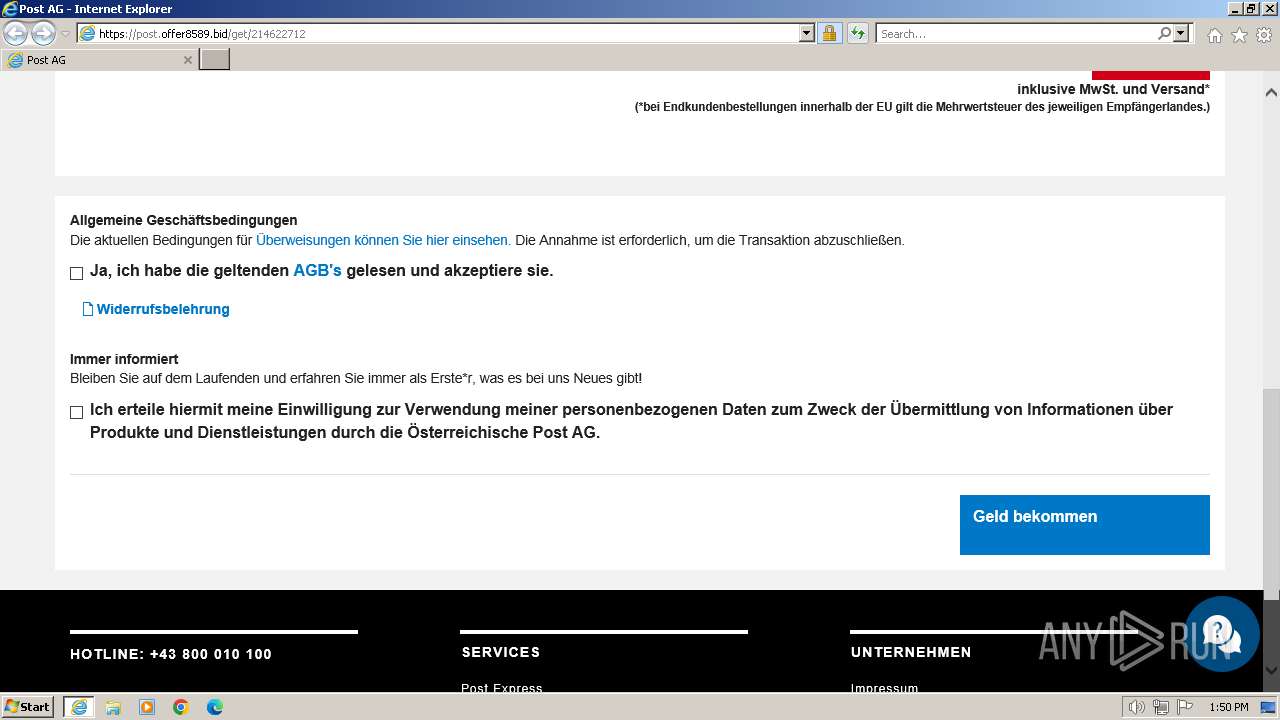
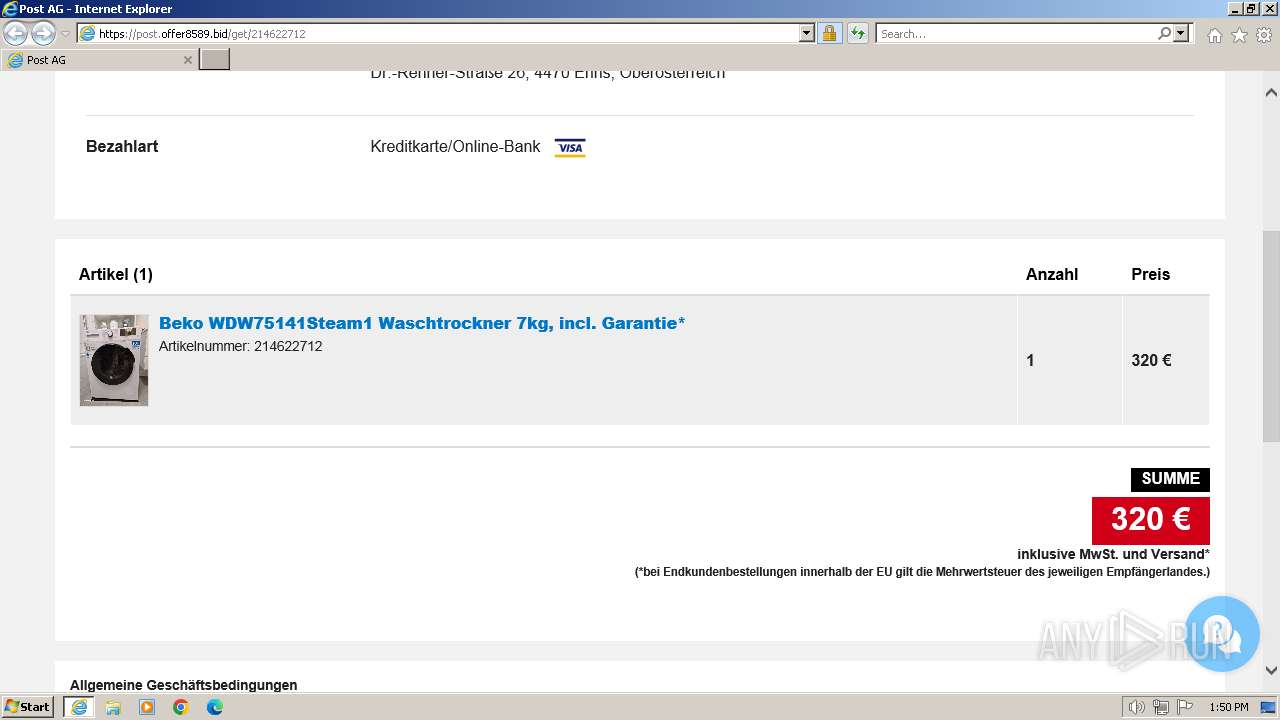
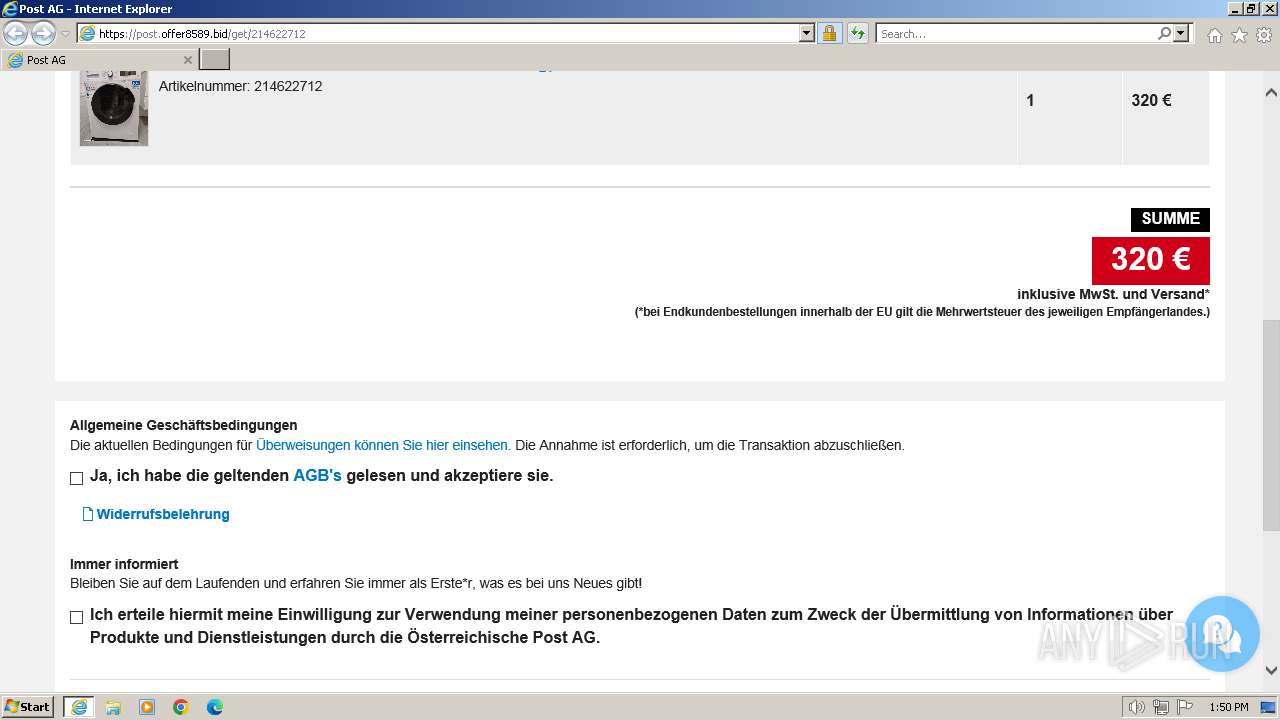
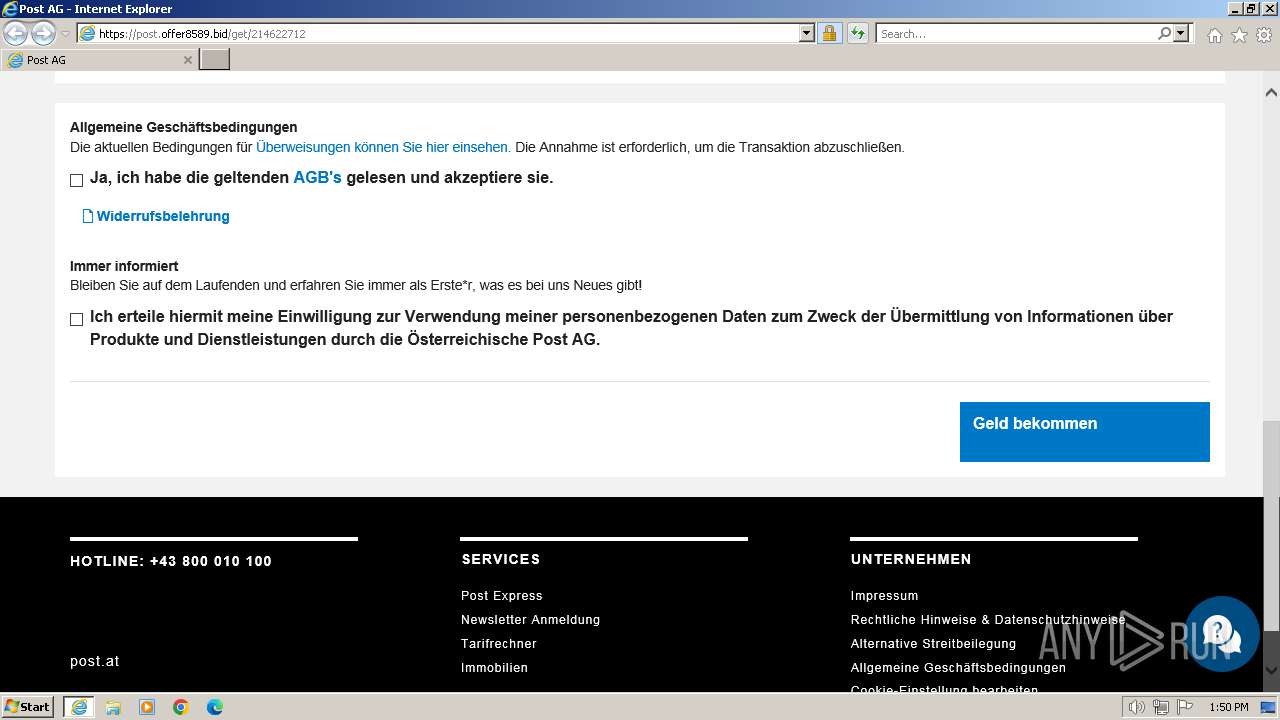
| URL: | http://surl.li/rblmo |
| Full analysis: | https://app.any.run/tasks/2c5bcebc-9269-4ce7-8165-f00091197a91 |
| Verdict: | Malicious activity |
| Analysis date: | February 29, 2024, 13:50:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | F77397405345D111AC1BA8DE410DEFD3 |
| SHA1: | F7AE10B9167B3863B7172EC20CAD99F89F09E3E4 |
| SHA256: | 6E5C87B0DD5F862441815C56EF793D494D8416F7C715143D9500907E6985B3DA |
| SSDEEP: | 3:N1KNQXJ1GK:CCPd |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3672 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://surl.li/rblmo" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3692 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3672 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
19 080
Read events
18 962
Write events
85
Delete events
33
Modification events
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31091478 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31091478 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
21
Text files
57
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3692 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\YKEZUMG5.txt | text | |
MD5:7F535BDD371946F5C6DA13F39D5E7D3C | SHA256:BCCF4864E812F7AE52469DD2BA6F4E29BFFB8BE5954143834A7F493C620978CD | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\D3XU7V1J.txt | text | |
MD5:69498A4109C33CDEC087C5E9070B4B58 | SHA256:3EE948D1ABA9EC21DAFD964BBA0C850F90D2206EF1716117BF4D9AF8E200E6D6 | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:753DF6889FD7410A2E9FE333DA83A429 | SHA256:B42DC237E44CBC9A43400E7D3F9CBD406DBDEFD62BFE87328F8663897D69DF78 | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:0C1D92DFC1ECA6B68728E3C2BE35661F | SHA256:B38628907BC8E9AAAF7BB4A9EBB183E736D3A91F50019ABD7DD0390E5673BA24 | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:25D02AA2648CBBD885561A6A4BCE53B4 | SHA256:F740948BCB629BDB44718DC261CC6570D26BAC915D90B7FCCA1FE0073B6415B0 | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabF6F4.tmp | compressed | |
MD5:753DF6889FD7410A2E9FE333DA83A429 | SHA256:B42DC237E44CBC9A43400E7D3F9CBD406DBDEFD62BFE87328F8663897D69DF78 | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\rblmo[1].htm | html | |
MD5:0002094CFB2830ACD94C64E76A3BD107 | SHA256:FE76B3ED9C72CBA93C5D7F31D8FFEC38ABE83377E7728BF1EBC5B70B840080CB | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabF6D3.tmp | compressed | |
MD5:753DF6889FD7410A2E9FE333DA83A429 | SHA256:B42DC237E44CBC9A43400E7D3F9CBD406DBDEFD62BFE87328F8663897D69DF78 | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarF6D4.tmp | cat | |
MD5:DD73CEAD4B93366CF3465C8CD32E2796 | SHA256:A6752B7851B591550E4625B832A393AABCC428DE18D83E8593CD540F7D7CAE22 | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:7BB9321C1556D9B8D24F3AFD5CDB826C | SHA256:9D25DB37B278204CDCC2625FE8658E8B8975F8428556CBBFF27A798EC0FAADAD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
49
DNS requests
26
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
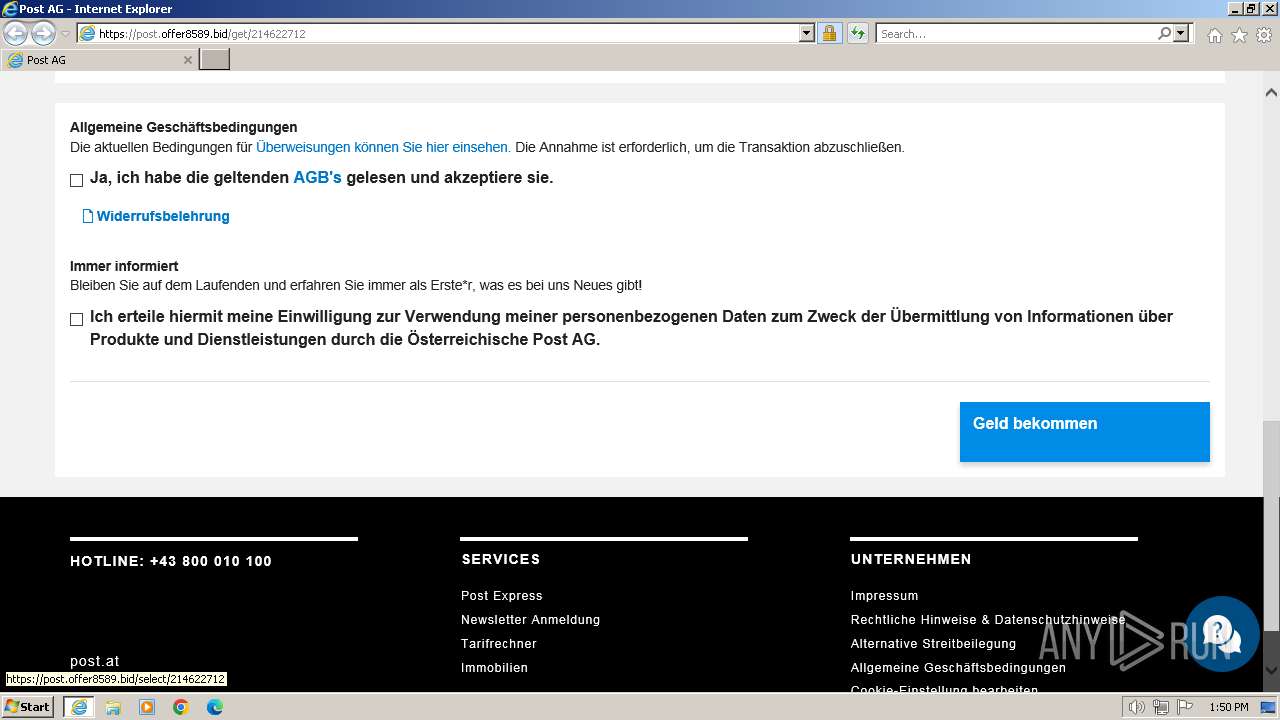
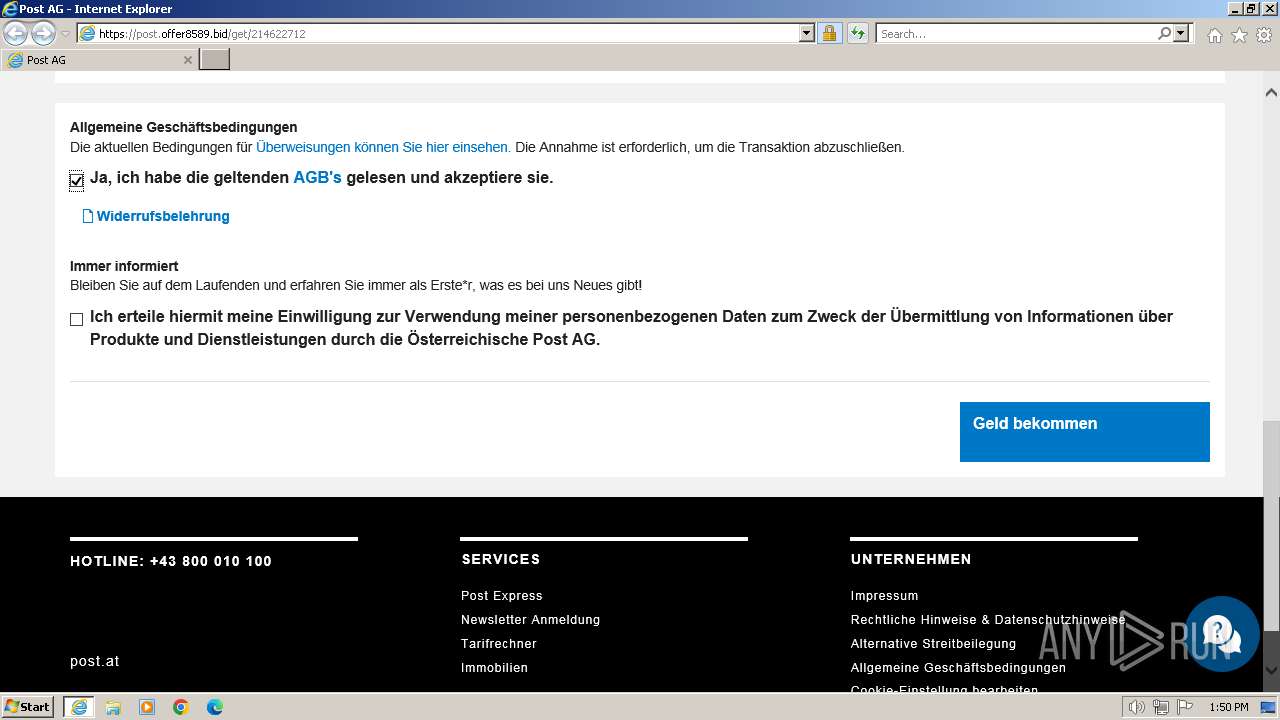
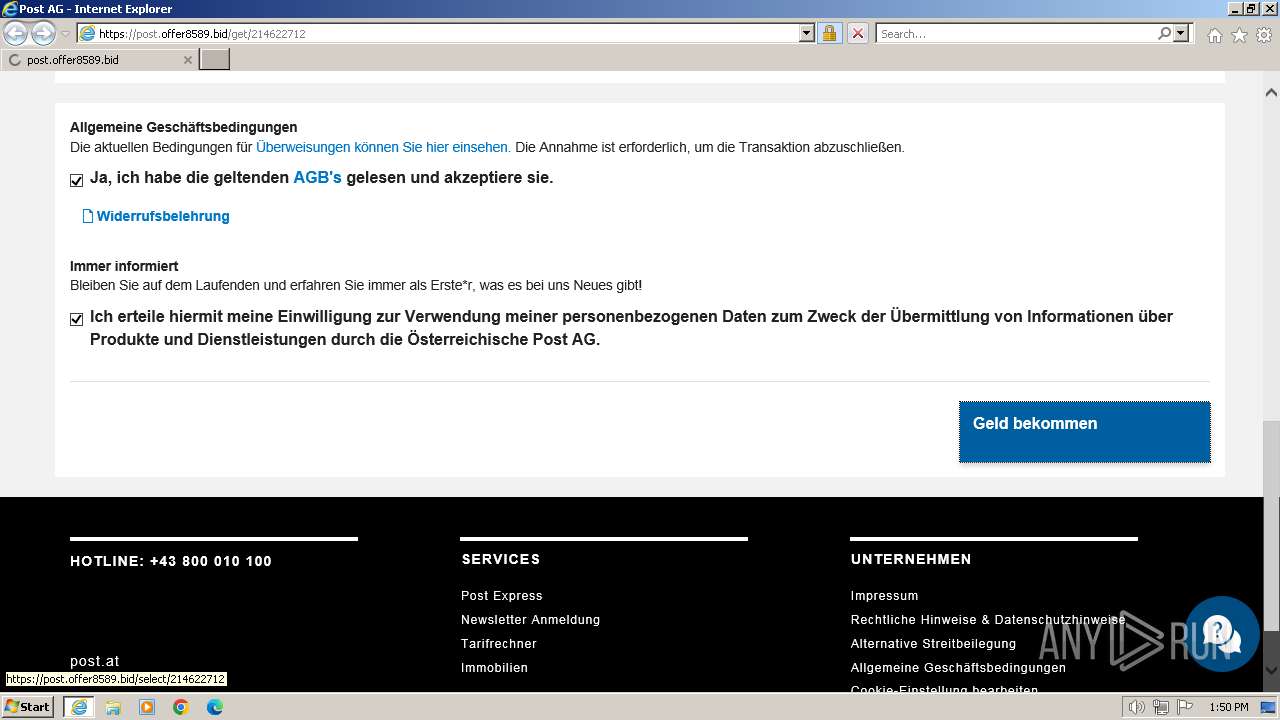
3692 | iexplore.exe | GET | 301 | 104.26.4.19:80 | http://surl.li/rblmo | unknown | html | 169 b | unknown |
3692 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bd117e088266f0f9 | unknown | — | — | unknown |
3692 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3692 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
3692 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a08f35fbea17b647 | unknown | compressed | 67.5 Kb | unknown |
3692 | iexplore.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3692 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?b150b552b216e1f4 | unknown | compressed | 67.5 Kb | unknown |
3692 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEB92soBBV%2BJdCZpj%2BsmLUsk%3D | unknown | binary | 471 b | unknown |
3692 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3692 | iexplore.exe | GET | 200 | 69.192.161.44:80 | http://x2.c.lencr.org/ | unknown | binary | 299 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3692 | iexplore.exe | 104.26.4.19:80 | surl.li | CLOUDFLARENET | US | unknown |
3692 | iexplore.exe | 104.26.4.19:443 | surl.li | CLOUDFLARENET | US | unknown |
3692 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3692 | iexplore.exe | 172.217.16.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
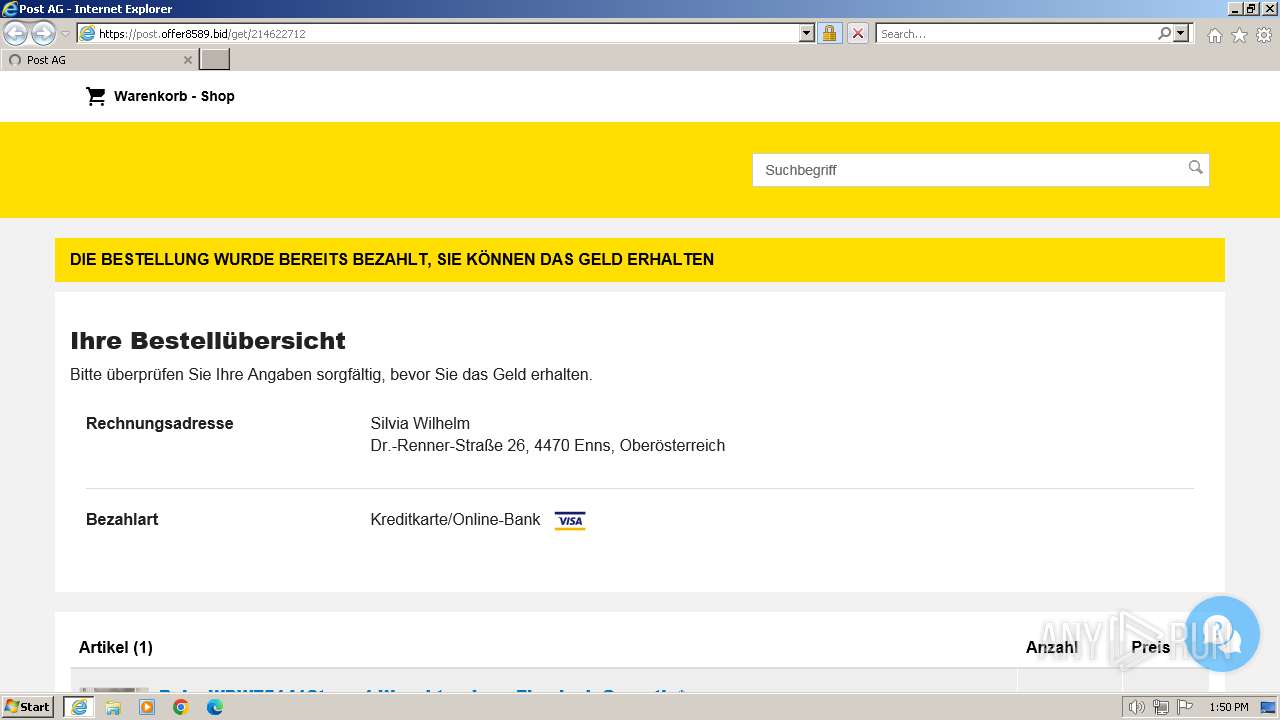
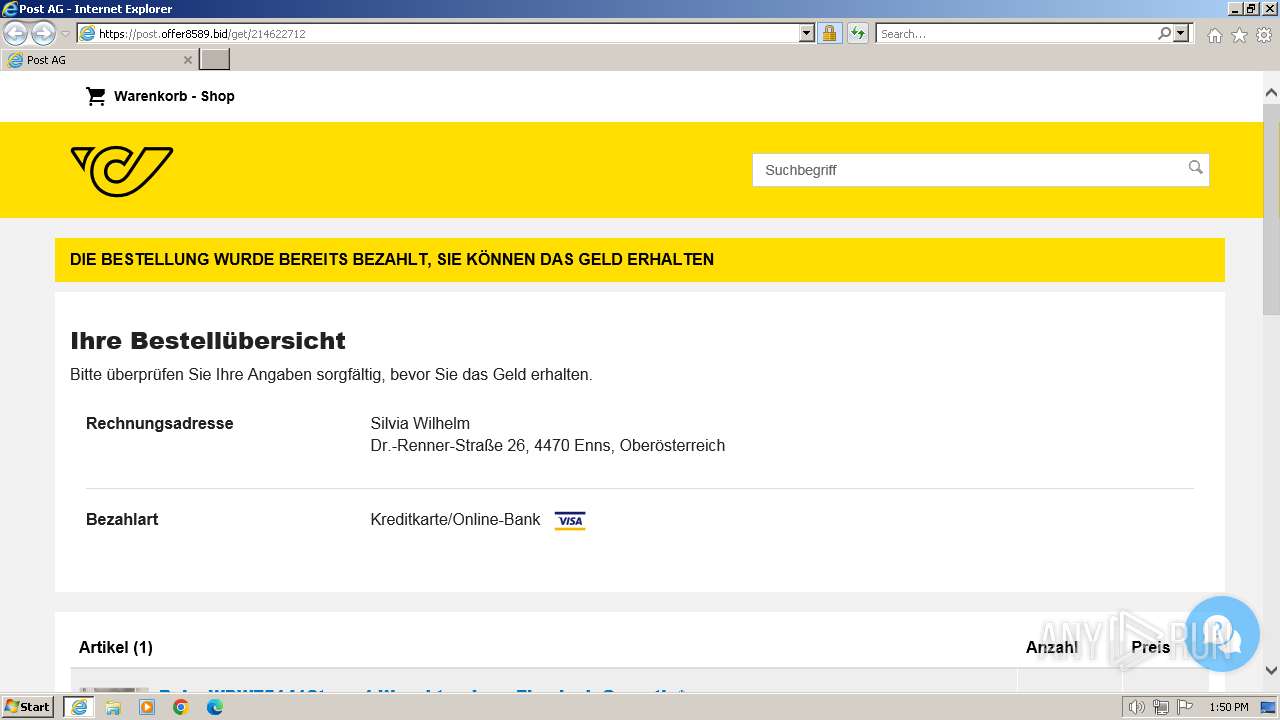
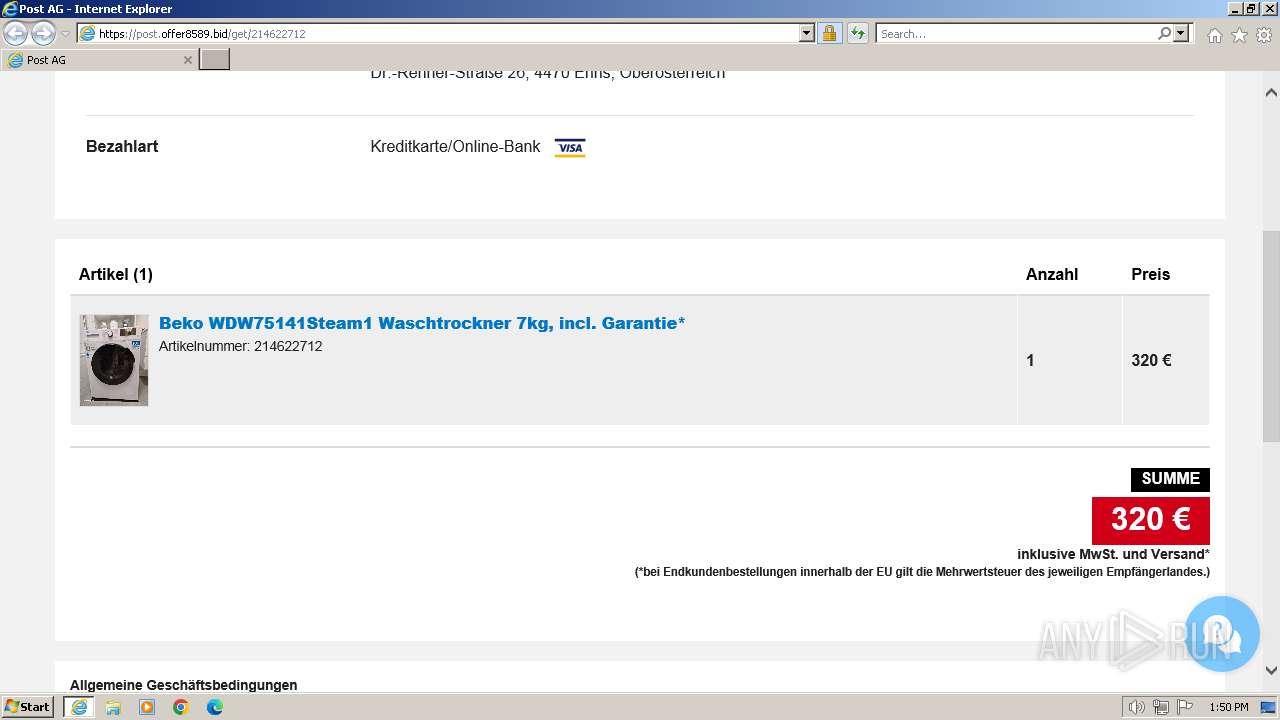
3692 | iexplore.exe | 188.114.96.3:443 | post.offer8589.bid | CLOUDFLARENET | NL | unknown |
3692 | iexplore.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
3692 | iexplore.exe | 142.250.184.230:443 | 12374224.fls.doubleclick.net | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
surl.li |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
post.offer8589.bid |
| unknown |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
12374224.fls.doubleclick.net |
| unknown |
adservice.google.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3692 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
3692 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
3692 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
3692 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
3692 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
3692 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |