| download: | 382 |
| Full analysis: | https://app.any.run/tasks/bf0aa297-ccd7-4565-8ff0-0bdd36575589 |
| Verdict: | Malicious activity |
| Analysis date: | August 13, 2019, 20:57:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
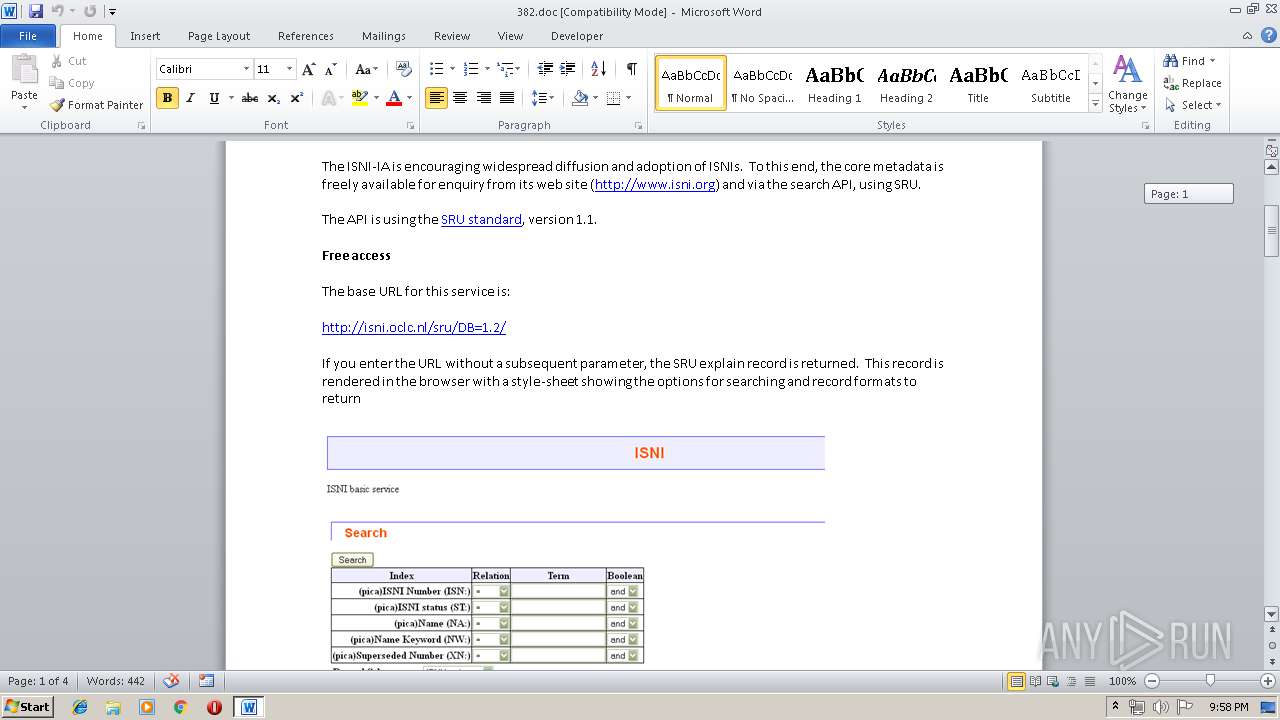
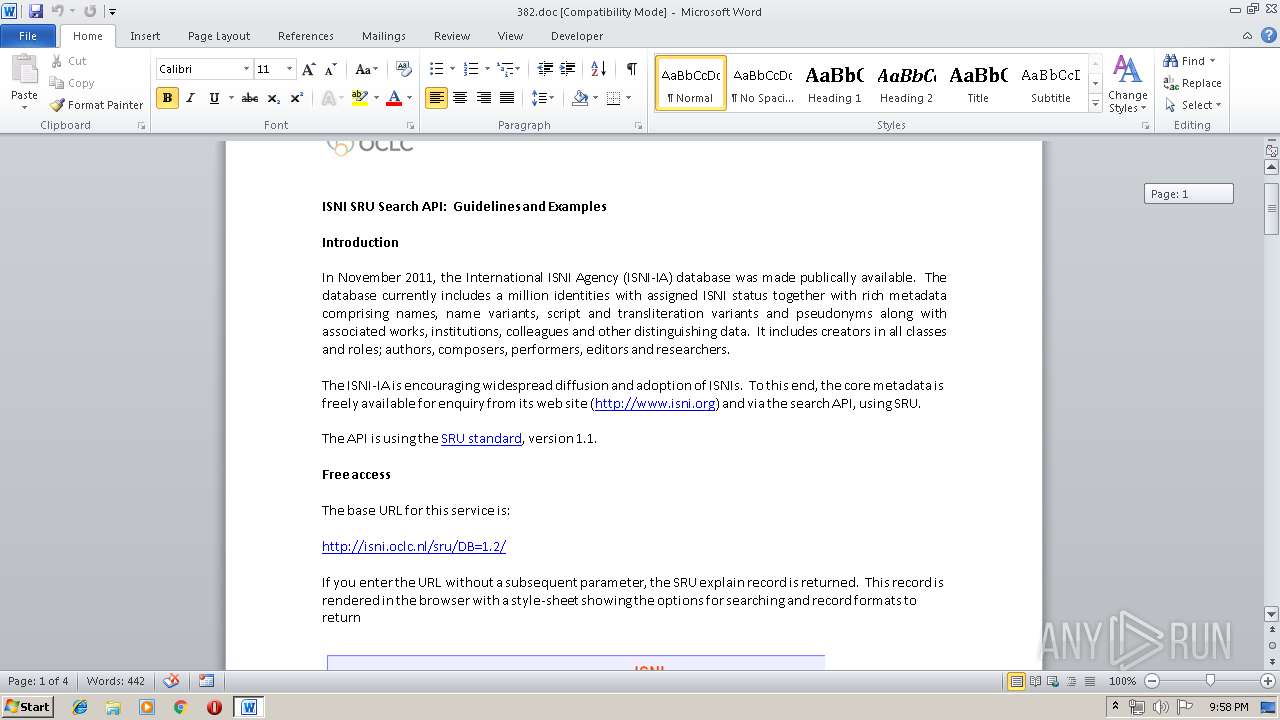
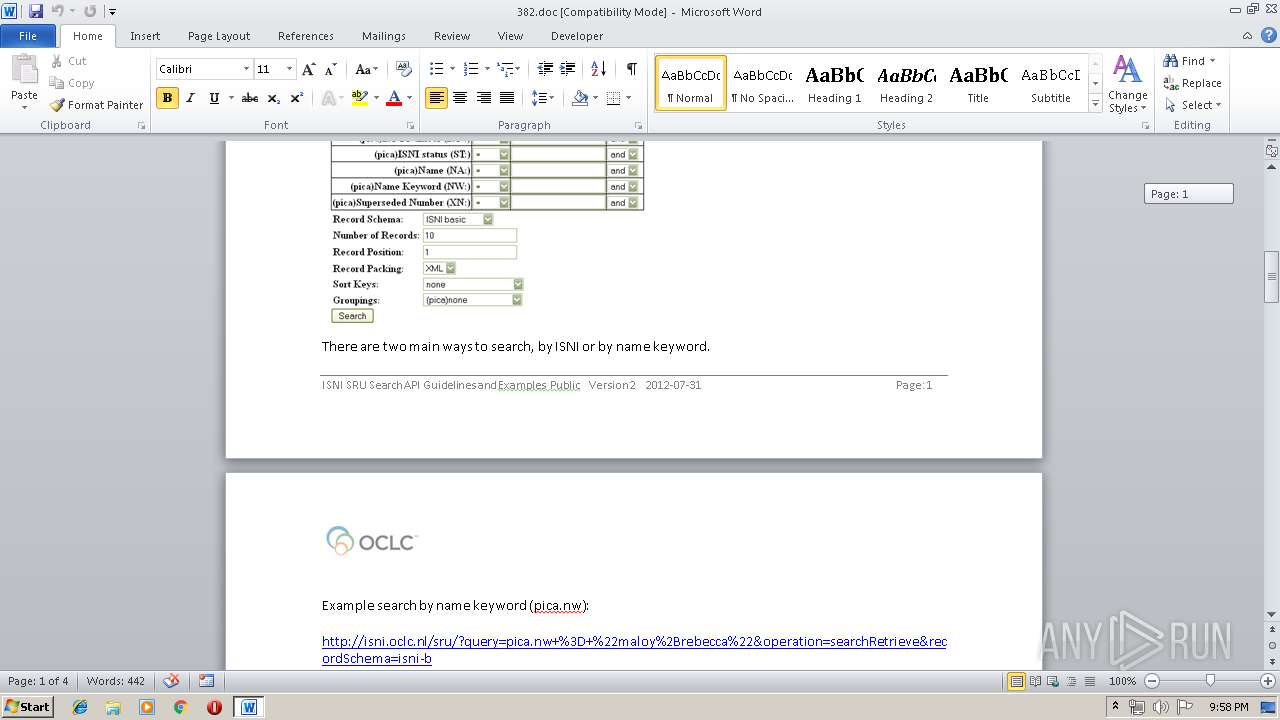
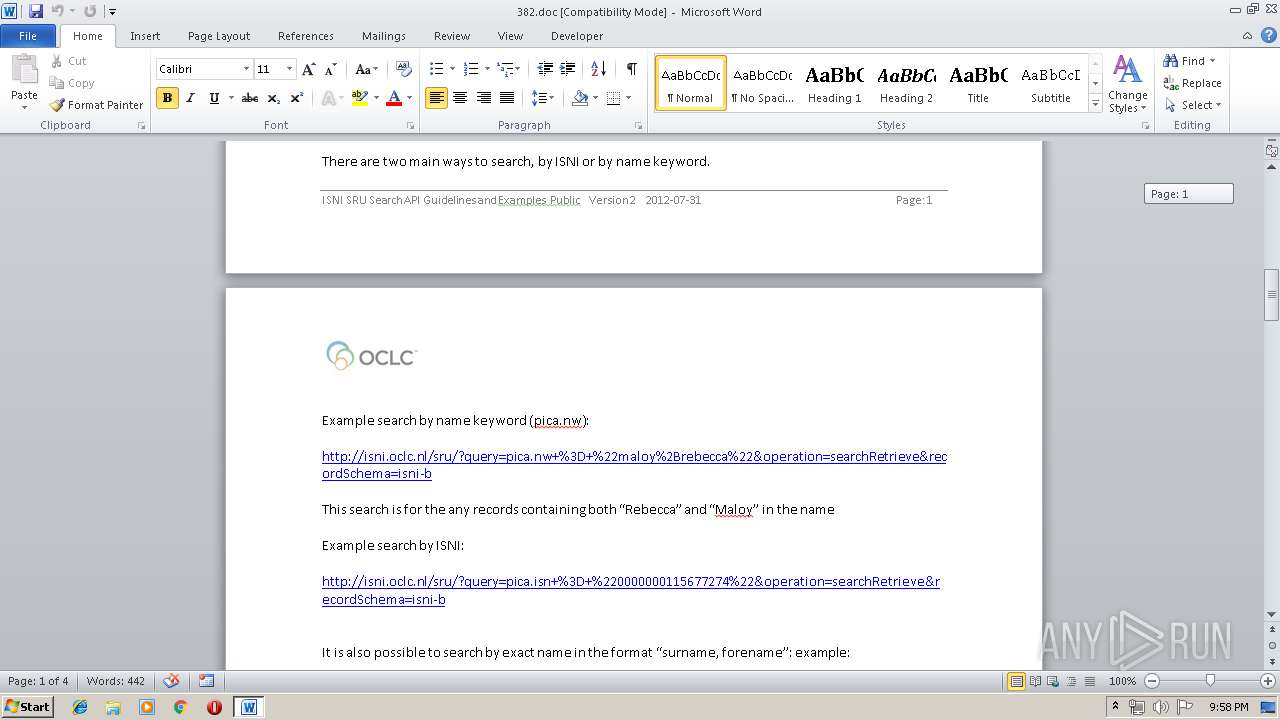
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: SRU Search API, Author: Janifer Gatenby, Keywords: ISNI SRU Search API Guidelines examples, Template: Normal.dotm, Last Saved By: Janifer Gatenby, Revision Number: 4, Name of Creating Application: Microsoft Office Word, Total Editing Time: 14:00, Last Printed: Fri Apr 15 09:07:00 2011, Create Time/Date: Fri Dec 16 16:36:00 2011, Last Saved Time/Date: Sat Jun 30 14:04:00 2012, Number of Pages: 4, Number of Words: 1182, Number of Characters: 6501, Security: 0 |
| MD5: | 1A6027142E07A5D01211C1152F9D5491 |
| SHA1: | 97B494E25E3AFA07D3959DBAC27404974FD5C12F |
| SHA256: | 6E52DCF41FBF4DCF2210648A2E9BFDC45FD8FCE187980F8D674B1F92F3D5339A |
| SSDEEP: | 1536:v1X2ApxMCechhd7jzFMRL+wnKrFTlkBPxCw8hFjFiw8rlBZlGw8cw8cw8hFjFBs:9QI5aDKrApx8s |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2264)
SUSPICIOUS
Executed via COM
- iexplore.exe (PID: 3128)
- iexplore.exe (PID: 2944)
- iexplore.exe (PID: 1544)
- iexplore.exe (PID: 1700)
Reads internet explorer settings
- WINWORD.EXE (PID: 2264)
Starts Internet Explorer
- WINWORD.EXE (PID: 2264)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3496)
- iexplore.exe (PID: 3128)
- iexplore.exe (PID: 2944)
- iexplore.exe (PID: 1544)
- iexplore.exe (PID: 1700)
Reads internet explorer settings
- iexplore.exe (PID: 4080)
- iexplore.exe (PID: 4052)
- iexplore.exe (PID: 3108)
- iexplore.exe (PID: 2560)
- iexplore.exe (PID: 3644)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2264)
Reads Internet Cache Settings
- iexplore.exe (PID: 4080)
- iexplore.exe (PID: 3108)
- iexplore.exe (PID: 4052)
- iexplore.exe (PID: 3644)
- iexplore.exe (PID: 2560)
Creates files in the user directory
- iexplore.exe (PID: 4052)
- iexplore.exe (PID: 4080)
- WINWORD.EXE (PID: 2264)
Application launched itself
- iexplore.exe (PID: 2944)
- iexplore.exe (PID: 3496)
- iexplore.exe (PID: 1700)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (80) |
|---|
EXIF
FlashPix
| Title: | SRU Search API |
|---|---|
| Subject: | - |
| Author: | Janifer Gatenby |
| Keywords: | ISNI SRU Search API Guidelines examples |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | Janifer Gatenby |
| RevisionNumber: | 4 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 14.0 minutes |
| LastPrinted: | 2011:04:15 08:07:00 |
| CreateDate: | 2011:12:16 16:36:00 |
| ModifyDate: | 2012:07:31 13:04:00 |
| Pages: | 4 |
| Words: | 1182 |
| Characters: | 6501 |
| Security: | None |
| Company: | OCLC B.V. |
| Lines: | 54 |
| Paragraphs: | 15 |
| CharCountWithSpaces: | 7668 |
| AppVersion: | 12 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | SRU Search API |
| HeadingPairs: |
|
| CodePage: | Windows Latin 1 (Western European) |
| Hyperlinks: |
|
| CompObjUserTypeLen: | 39 |
| CompObjUserType: | Microsoft Office Word 97-2003 Document |
Total processes
45
Monitored processes
11
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1544 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1700 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2264 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\382.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2560 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1700 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2944 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3108 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2944 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3128 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3496 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3644 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1544 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4052 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3128 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 062
Read events
2 493
Write events
558
Delete events
11
Modification events
| (PID) Process: | (2264) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | o#a |
Value: 6F236100D8080000010000000000000000000000 | |||
| (PID) Process: | (2264) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2264) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2264) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1326252062 | |||
| (PID) Process: | (2264) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1326252176 | |||
| (PID) Process: | (2264) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1326252177 | |||
| (PID) Process: | (2264) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: D8080000D07372C51952D50100000000 | |||
| (PID) Process: | (2264) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | h$a |
Value: 68246100D808000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2264) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | h$a |
Value: 68246100D808000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2264) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
9
Text files
68
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2264 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRCF4F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2264 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\sru[1].htm | — | |
MD5:— | SHA256:— | |||
| 3496 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3496 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2264 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$382.doc | pgc | |
MD5:— | SHA256:— | |||
| 4080 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@loc[2].txt | — | |
MD5:— | SHA256:— | |||
| 2264 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 4080 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@loc[1].txt | text | |
MD5:— | SHA256:— | |||
| 2264 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@loc[1].txt | text | |
MD5:— | SHA256:— | |||
| 4080 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
60
TCP/UDP connections
16
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4080 | iexplore.exe | GET | 302 | 66.117.29.227:80 | http://cmon.loc.gov/b/ss/locgovprod/1/H.27.5/s45713251246143?AQB=1&ndh=1&t=13%2F7%2F2019%2021%3A58%3A39%202%20-60&fid=0CF150F27EB57722-013D5C18D60F74FB&ce=UTF-8&ns=thelibraryofcongress&g=http%3A%2F%2Fwww.loc.gov%2Fstandards%2Fsru%2F&server=www.loc.gov&events=event40&c1=SRU%3A%20Search%2FRetrieval%20via%20URL%20--%20SRU%2C%20CQL%20and%20ZeeRex%20%28Standards%2C%20Library%20of%20Congress%29&v8=9%3A45PM&c9=PRODDEC2012-1&v9=Tuesday&v15=D%3Dg&v19=PRODDEC2012-1&c61=standards&c62=sru&s=1280x720&c=32&j=1.5&v=Y&k=Y&bw=792&bh=464&ct=lan&hp=N&AQE=1 | US | — | — | suspicious |
4080 | iexplore.exe | GET | 200 | 104.16.54.16:80 | http://www.loc.gov/standards/sru/ | US | html | 2.29 Kb | shared |
4080 | iexplore.exe | GET | 200 | 104.16.54.16:80 | http://www.loc.gov/standards/sru/images/sru.gif | US | image | 4.59 Kb | shared |
4080 | iexplore.exe | GET | 200 | 104.16.54.16:80 | http://www.loc.gov/standards/sru/images/arrow-bullet.gif | US | image | 50 b | shared |
2264 | WINWORD.EXE | GET | 200 | 104.16.54.16:80 | http://www.loc.gov/standards/sru/ | US | html | 2.33 Kb | shared |
4080 | iexplore.exe | GET | 200 | 104.16.54.16:80 | http://www.loc.gov/standards/sru/css/sru-base.css | US | text | 1.60 Kb | shared |
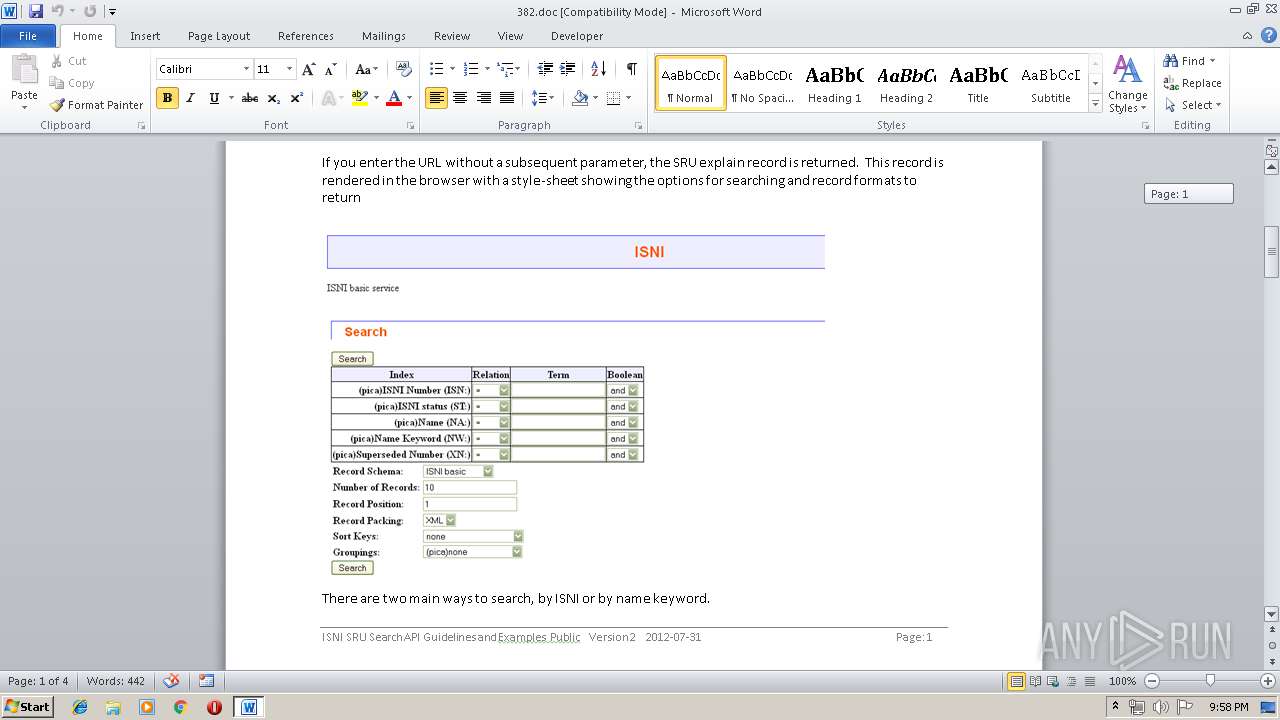
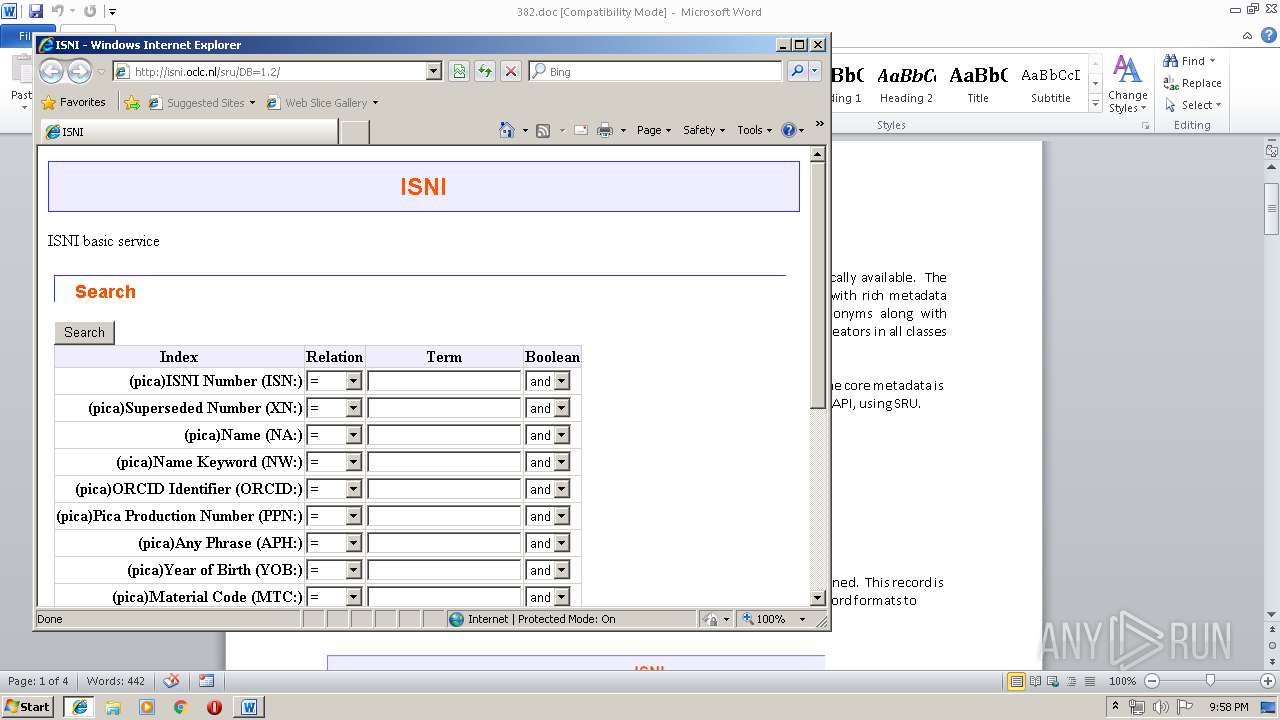
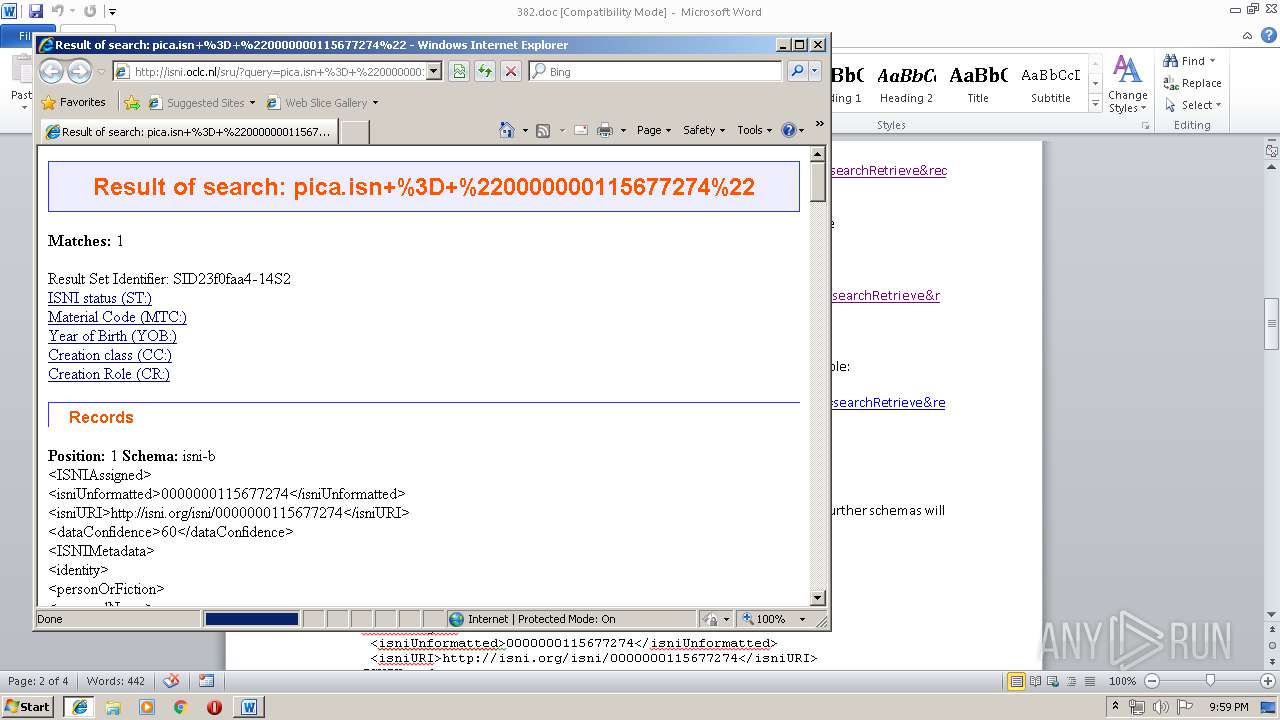
4052 | iexplore.exe | GET | 200 | 193.240.184.206:80 | http://isni.oclc.nl/sru/DB=1.2/?xsl=explainresponse | DE | xml | 9.81 Kb | unknown |
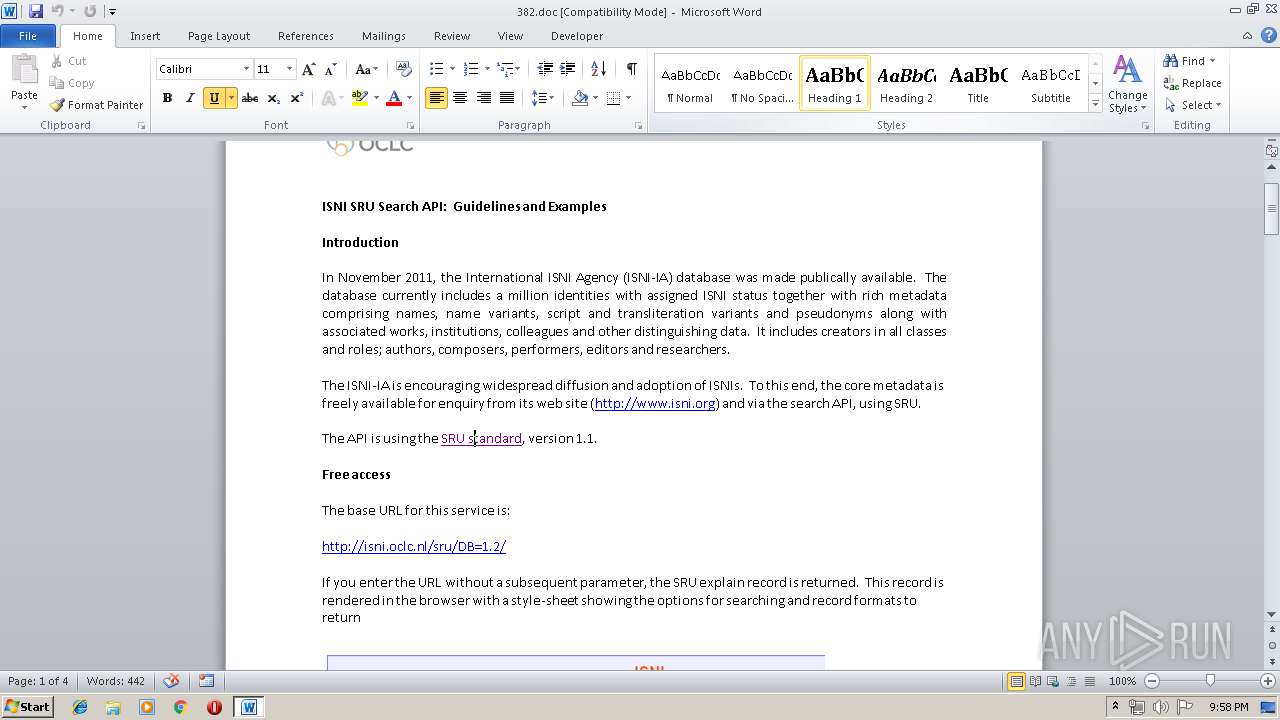
2264 | WINWORD.EXE | GET | 200 | 193.240.184.206:80 | http://isni.oclc.nl/sru/DB=1.2/ | DE | xml | 5.38 Kb | unknown |
4080 | iexplore.exe | GET | 200 | 104.16.54.16:80 | http://cdn.loc.gov/js/global/metrics/sc/s_code.js | US | text | 24.4 Kb | shared |
4052 | iexplore.exe | GET | 200 | 193.240.184.206:80 | http://isni.oclc.nl/sru/DB=1.2/ | DE | xml | 5.38 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2264 | WINWORD.EXE | 193.240.184.206:80 | isni.oclc.nl | Online Computer Library Center | DE | unknown |
3496 | iexplore.exe | 104.16.54.16:8081 | www.loc.gov | Cloudflare Inc | US | shared |
3108 | iexplore.exe | 193.240.184.206:80 | isni.oclc.nl | Online Computer Library Center | DE | unknown |
3644 | iexplore.exe | 193.240.184.206:80 | isni.oclc.nl | Online Computer Library Center | DE | unknown |
2560 | iexplore.exe | 193.240.184.206:80 | isni.oclc.nl | Online Computer Library Center | DE | unknown |
4052 | iexplore.exe | 193.240.184.206:80 | isni.oclc.nl | Online Computer Library Center | DE | unknown |
3128 | iexplore.exe | 193.240.184.206:80 | isni.oclc.nl | Online Computer Library Center | DE | unknown |
3496 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
4080 | iexplore.exe | 104.16.54.16:80 | www.loc.gov | Cloudflare Inc | US | shared |
2264 | WINWORD.EXE | 104.16.54.16:80 | www.loc.gov | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.loc.gov |
| unknown |
www.bing.com |
| whitelisted |
cdn.loc.gov |
| unknown |
cmon.loc.gov |
| suspicious |
isni.oclc.nl |
| unknown |