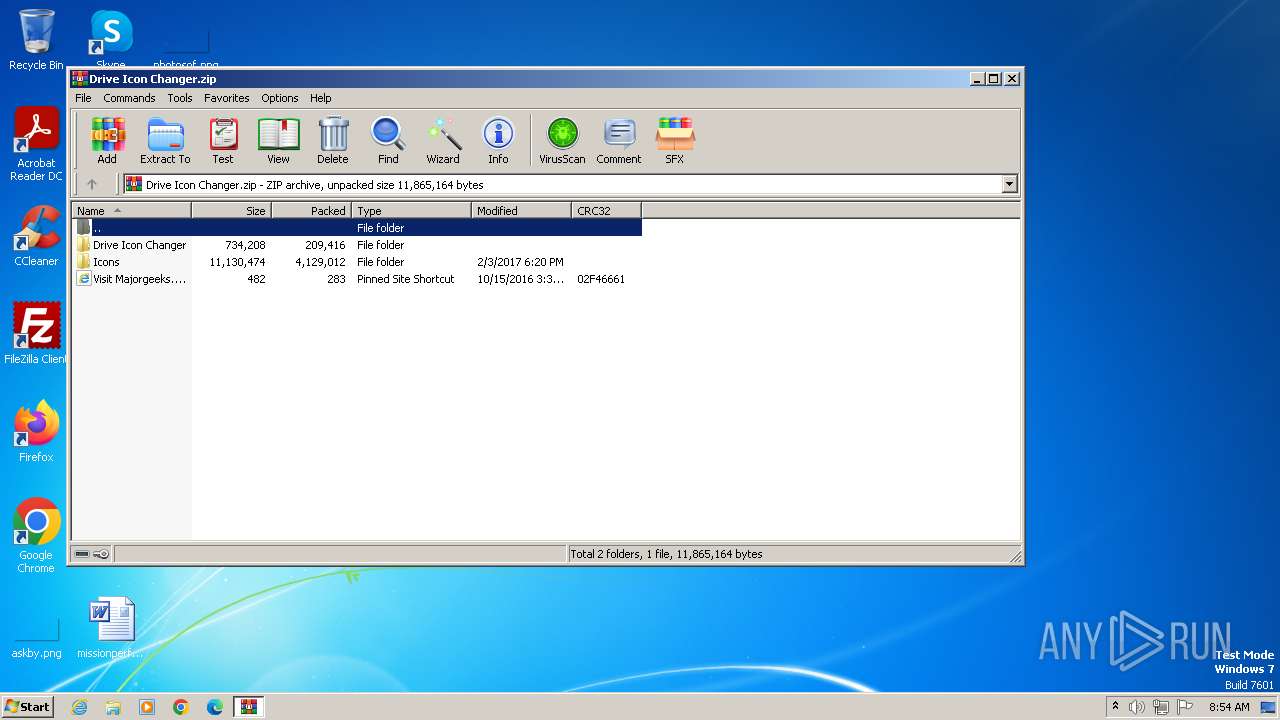
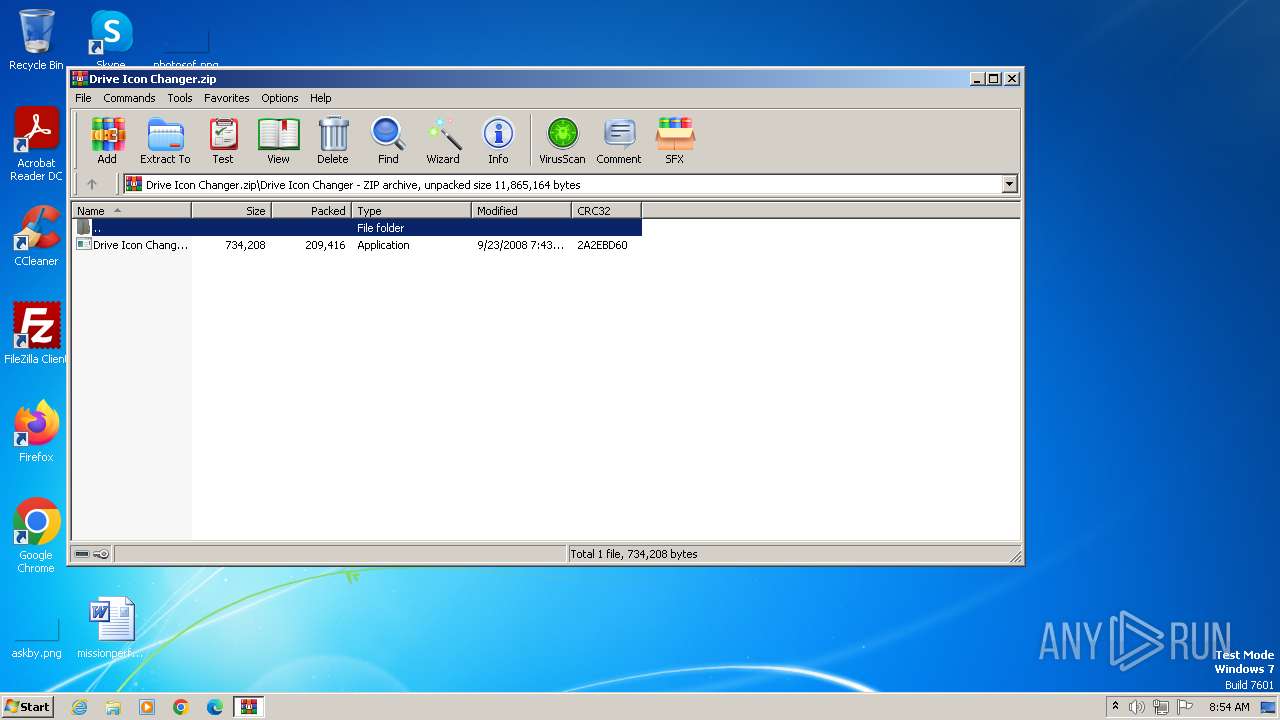
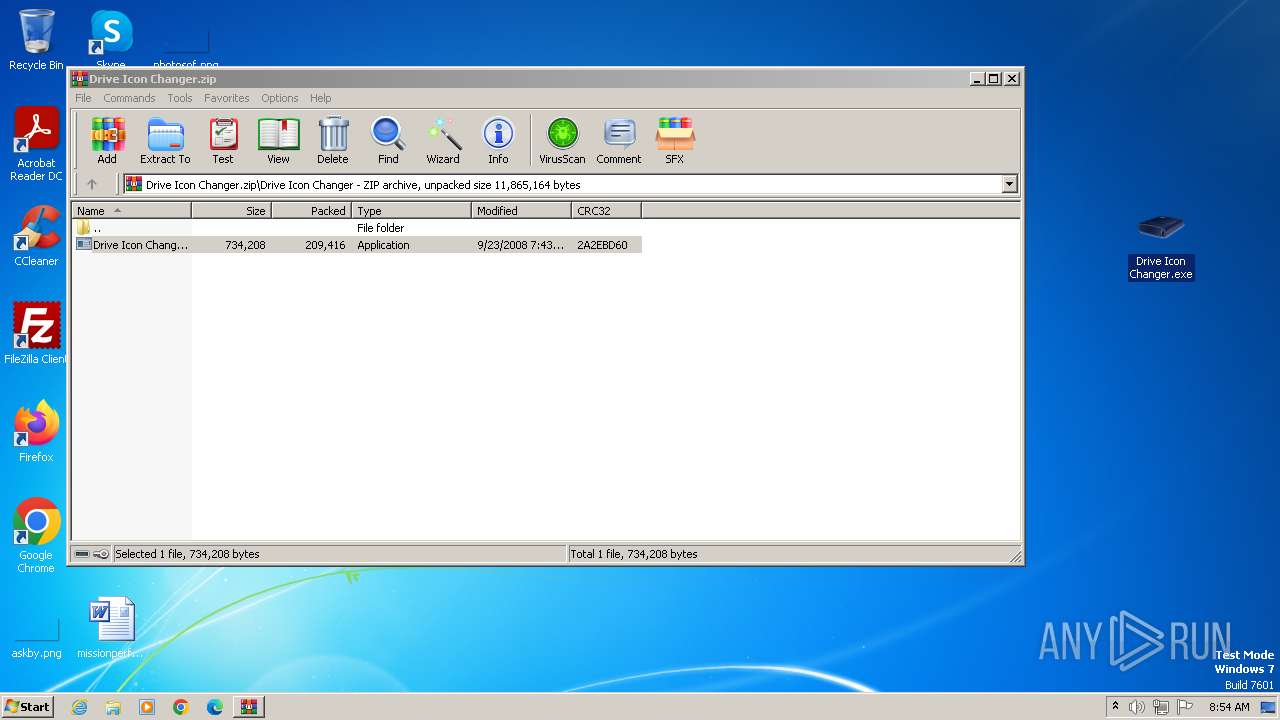
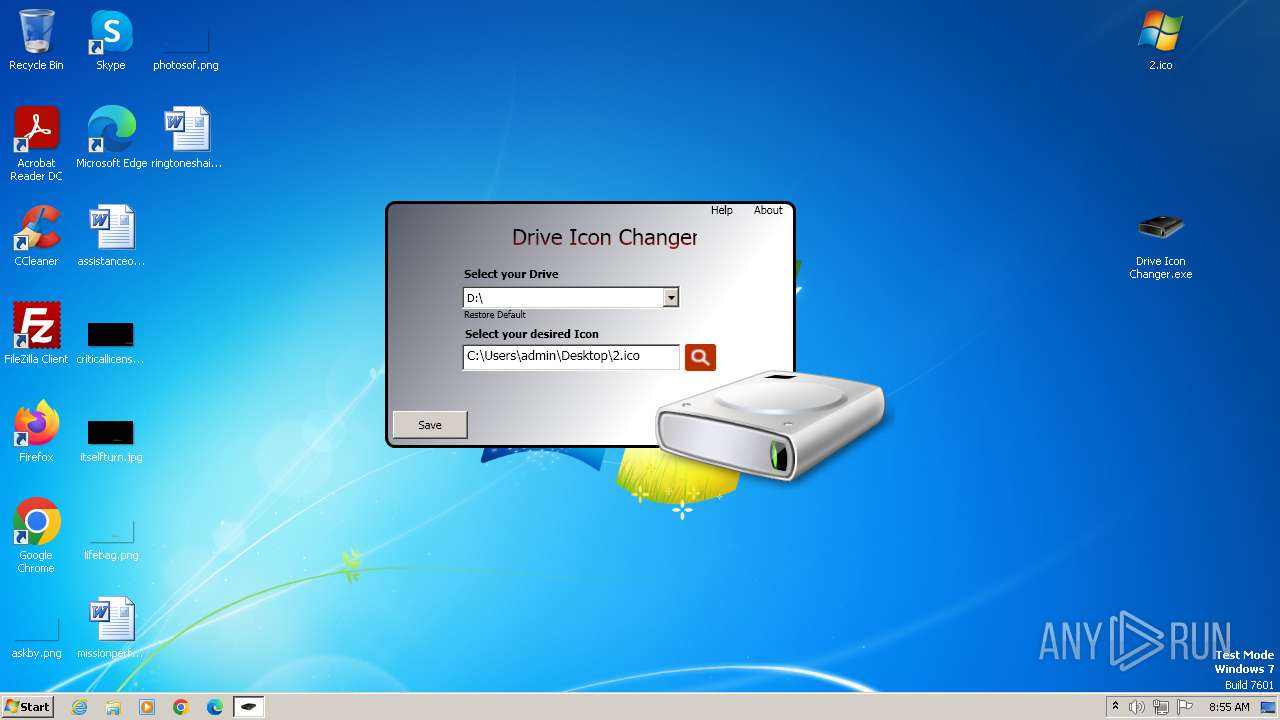
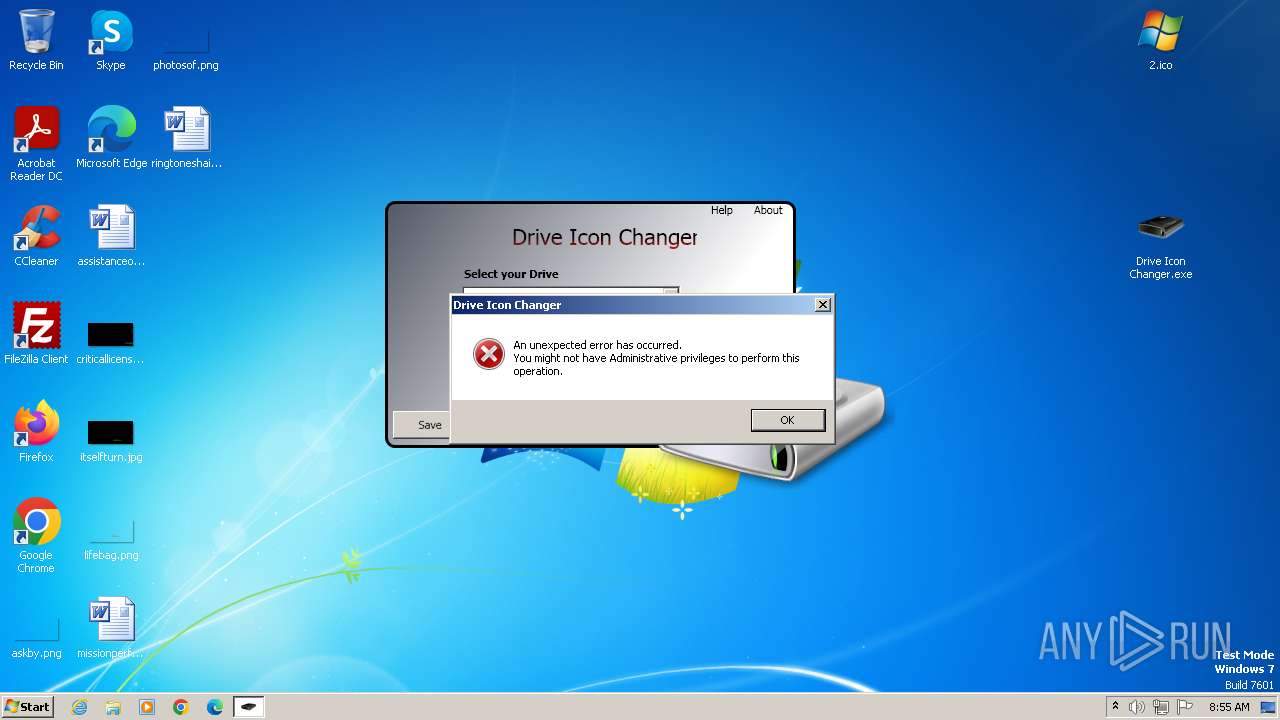
| File name: | Drive Icon Changer.zip |
| Full analysis: | https://app.any.run/tasks/77cd933b-2168-4edf-a683-c06418e10bdd |
| Verdict: | Malicious activity |
| Analysis date: | October 30, 2023, 08:54:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 20731EB2C17EE6560FC20C66073E54CF |
| SHA1: | 3027DE7D0015F19521DB749A460E76B6CC23B78F |
| SHA256: | 6E4BEAA6D751E2B7A02B82FF0EA83303CD463B144B3C6A24873B5BDED35CC00E |
| SSDEEP: | 98304:HAwicANytFjaXjeYoS191iAM/AfMCcsGf05awGi70Rj6cFdeNzlMkVJP+PcuFMpy:+SwCFRiP2Sw |
MALICIOUS
Application was dropped or rewritten from another process
- Drive Icon Changer.exe (PID: 2612)
SUSPICIOUS
Reads the Internet Settings
- Drive Icon Changer.exe (PID: 2612)
Executes as Windows Service
- PresentationFontCache.exe (PID: 1828)
INFO
Checks supported languages
- Drive Icon Changer.exe (PID: 2612)
- PresentationFontCache.exe (PID: 1828)
Manual execution by a user
- Drive Icon Changer.exe (PID: 2612)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1824)
Reads the computer name
- Drive Icon Changer.exe (PID: 2612)
- PresentationFontCache.exe (PID: 1828)
Reads the machine GUID from the registry
- Drive Icon Changer.exe (PID: 2612)
- PresentationFontCache.exe (PID: 1828)
Application launched itself
- iexplore.exe (PID: 3032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2008:09:23 19:43:32 |
| ZipCRC: | 0x2a2ebd60 |
| ZipCompressedSize: | 209416 |
| ZipUncompressedSize: | 734208 |
| ZipFileName: | Drive Icon Changer/Drive Icon Changer.exe |
Total processes
48
Monitored processes
5
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1824 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Drive Icon Changer.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1828 | C:\Windows\Microsoft.Net\Framework\v3.0\WPF\PresentationFontCache.exe | C:\Windows\Microsoft.Net\Framework\v3.0\WPF\PresentationFontCache.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: PresentationFontCache.exe Exit code: 0 Version: 3.0.6920.4902 built by: NetFXw7 Modules
| |||||||||||||||
| 2212 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3032 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2612 | "C:\Users\admin\Desktop\Drive Icon Changer.exe" | C:\Users\admin\Desktop\Drive Icon Changer.exe | explorer.exe | ||||||||||||
User: admin Company: Redmond Pie Integrity Level: HIGH Description: Changes your drive icon. Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3032 | "C:\Program Files\Internet Explorer\iexplore.exe" http://www.redmondpie.com | C:\Program Files\Internet Explorer\iexplore.exe | — | Drive Icon Changer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
17 387
Read events
17 263
Write events
123
Delete events
1
Modification events
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2612) Drive Icon Changer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
1
Suspicious files
30
Text files
81
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1824.8263\Icons\2.ico | image | |
MD5:D6FDBBF0EDD868EDC9DB28C22A962AA0 | SHA256:F24248449A4BBBB0FC6890DBB0E89BEE4435BD50C25DD1BE315DBB5B3B32F707 | |||
| 2212 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 2212 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\RXCC2TMJ.htm | html | |
MD5:4F8E702CC244EC5D4DE32740C0ECBD97 | SHA256:9E17CB15DD75BBBD5DBB984EDA674863C3B10AB72613CF8A39A00C3E11A8492A | |||
| 2212 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:CEC88CBAFAB2863CAE6A693899C39221 | SHA256:40C6AE00A6646167C3D232FA73FE38BCA8099E0572990FD0796F0DB08BF6DED2 | |||
| 2212 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar3E8A.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 1824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1824.7507\Drive Icon Changer\Drive Icon Changer.exe | executable | |
MD5:D6C2D52CFFB54956C0B8ABF75035DAD5 | SHA256:1DB6795B65CAAF0911AFB22967246C18B7CD34C45C590ADCC64A477718DCC68F | |||
| 2212 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:D8F443128DF5093B1DDA983F2CBE857E | SHA256:47C87B370C67AC65CD2E801CADFB903F331B9938A9C5A9191ECE5F27DB9E5D23 | |||
| 2212 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2212 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab3E89.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 2212 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:B44CEE8C29846D206D2FEC43DF675905 | SHA256:07F73991699DADC500FB72A39CD11297908B0B17E7FD3200A21118629C1F62B7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
33
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2212 | iexplore.exe | GET | 200 | 23.212.210.158:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
2212 | iexplore.exe | GET | 200 | 95.140.236.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?13743e2bf0035f6f | unknown | compressed | 4.66 Kb | unknown |
2212 | iexplore.exe | GET | 200 | 95.140.236.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?94d5b1893bfd1cc2 | unknown | compressed | 61.6 Kb | unknown |
2212 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
2212 | iexplore.exe | GET | 200 | 184.24.77.54:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgM2f3PbqeSwVVOlbB%2BgP1tCpA%3D%3D | unknown | binary | 503 b | unknown |
2212 | iexplore.exe | GET | 301 | 148.251.232.222:80 | http://www.redmondpie.com/ | unknown | html | 162 b | unknown |
2212 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEFbPwdvbrJHbCciV3aQ%2FE94%3D | unknown | binary | 471 b | unknown |
2212 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | unknown |
2212 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
2212 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCED0DQO7sPXWsCXu6cFHQzsU%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2212 | iexplore.exe | 148.251.232.222:80 | www.redmondpie.com | Hetzner Online GmbH | DE | unknown |
2212 | iexplore.exe | 148.251.232.222:443 | www.redmondpie.com | Hetzner Online GmbH | DE | unknown |
2212 | iexplore.exe | 95.140.236.128:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
2212 | iexplore.exe | 23.212.210.158:80 | x1.c.lencr.org | AKAMAI-AS | AU | unknown |
2212 | iexplore.exe | 184.24.77.54:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
2212 | iexplore.exe | 148.251.128.81:443 | cdn.redmondpie.com | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.redmondpie.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
cdn.redmondpie.com |
| unknown |
www.googletagmanager.com |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
redmondp.disqus.com |
| unknown |
ocsp.comodoca.com |
| whitelisted |