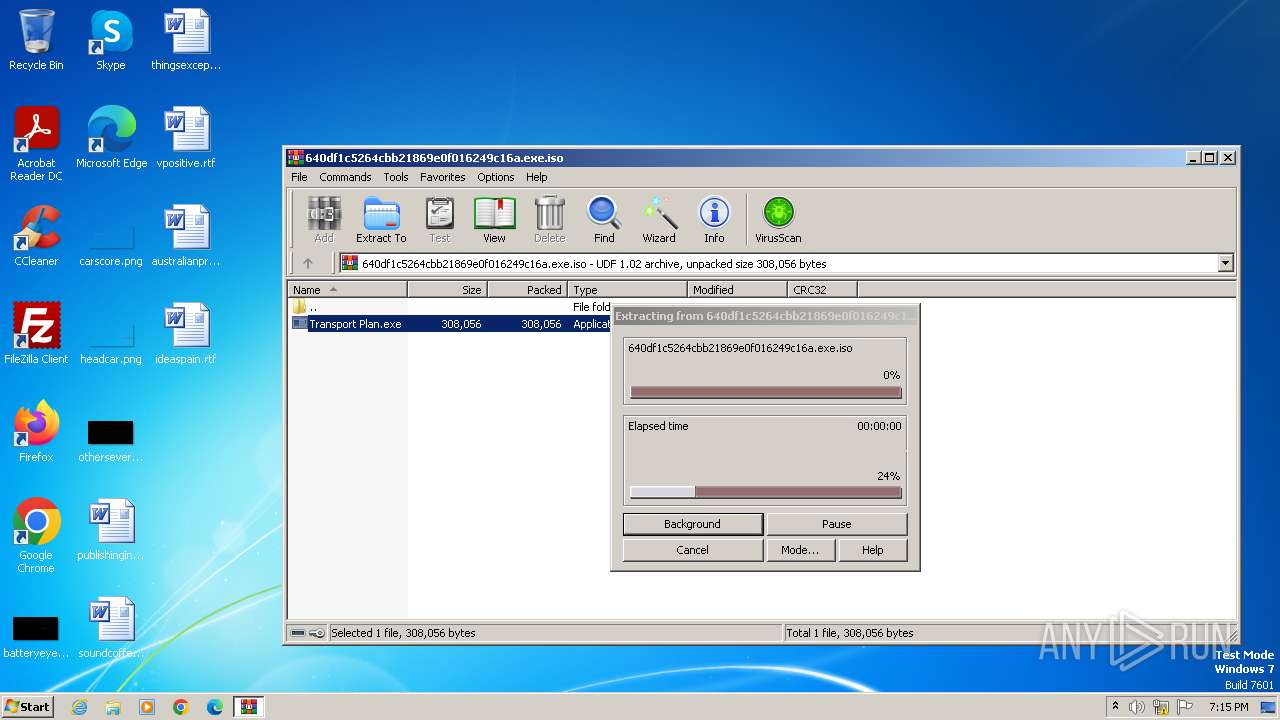
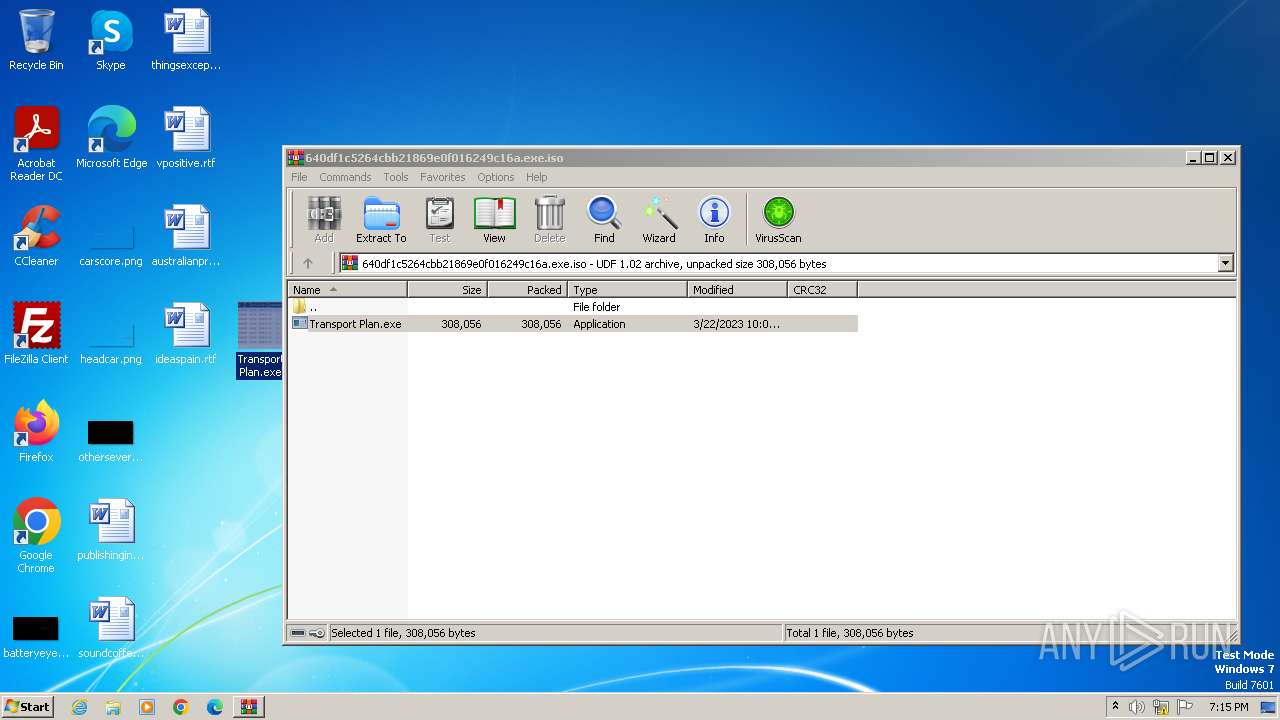
| File name: | 640df1c5264cbb21869e0f016249c16a.exe |
| Full analysis: | https://app.any.run/tasks/b6e0a970-d64f-47b9-93e9-6e4b94784ff5 |
| Verdict: | Malicious activity |
| Analysis date: | November 09, 2023, 19:14:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-iso9660-image |
| File info: | UDF filesystem data (version 1.5) 'IOXWHA5A5' |
| MD5: | 640DF1C5264CBB21869E0F016249C16A |
| SHA1: | 5D832907A641233C99382C6BD8C30CF670D98617 |
| SHA256: | 6E2250A584AB2D64365E14CFFA92AEA49D75833584CCEAAF1382291242CD7EC7 |
| SSDEEP: | 6144:Ss0qLdmFquc7KGw3kAmF2JRnJLi3fGQBKn8VcSTSSBy+wuaMDcMt:SEd7uGnA6OZJLi3pQ8VcCSr+wuDHt |
MALICIOUS
Drops the executable file immediately after the start
- Transport Plan.exe (PID: 3372)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- Transport Plan.exe (PID: 3372)
Process drops legitimate windows executable
- Transport Plan.exe (PID: 3372)
The process creates files with name similar to system file names
- Transport Plan.exe (PID: 3372)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3448)
Checks supported languages
- Transport Plan.exe (PID: 3372)
- Transport Plan.exe (PID: 3632)
Reads the computer name
- Transport Plan.exe (PID: 3372)
- Transport Plan.exe (PID: 3632)
Manual execution by a user
- Transport Plan.exe (PID: 3632)
Create files in a temporary directory
- Transport Plan.exe (PID: 3372)
- Transport Plan.exe (PID: 3632)
Creates files or folders in the user directory
- Transport Plan.exe (PID: 3372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .iso | | | ISO 9660 CD image (27.6) |
|---|---|---|
| .atn | | | Photoshop Action (27.1) |
| .gmc | | | Game Music Creator Music (6.1) |
EXIF
ISO
| VolumeName: | IOXWHA5A5 |
|---|---|
| VolumeBlockCount: | 599 |
| VolumeBlockSize: | 2048 |
| RootDirectoryCreateDate: | 2023:03:22 23:17:38+01:00 |
| VolumeSetName: | UNDEFINED |
| Software: | IMGBURN V2.5.8.0 - THE ULTIMATE IMAGE BURNER! |
| VolumeCreateDate: | 2023:03:22 23:17:38.00+01:00 |
| VolumeModifyDate: | 2023:03:22 23:17:38.00+01:00 |
Composite
| VolumeSize: | 1198 KiB |
|---|
Total processes
41
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3372 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3448.27708\Transport Plan.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3448.27708\Transport Plan.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3448 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\640df1c5264cbb21869e0f016249c16a.exe.iso" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3632 | "C:\Users\admin\Desktop\Transport Plan.exe" | C:\Users\admin\Desktop\Transport Plan.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
1 747
Read events
1 720
Write events
27
Delete events
0
Modification events
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
6
Suspicious files
1
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3372 | Transport Plan.exe | C:\Users\admin\AppData\Local\Ozelotters226\Aktiecertifikat\Lagrene\Zebroid\Biblioteksudlaans\Bourns\Halvahs\daytime-sunset-symbolic.symbolic.png | image | |
MD5:7AE839B3071D1F8E086E0CA0D375935E | SHA256:08B53D8210D69439FBE20F70FF6B131D0B4E7B9D1F85DE4717A451D4AF13BE3E | |||
| 3372 | Transport Plan.exe | C:\Users\admin\AppData\Local\Ozelotters226\Aktiecertifikat\Lagrene\Sikkerhedsforvarede\Diverticle\compress.c | text | |
MD5:72BF7E0BBFBD92875A4C055FA755F5DE | SHA256:D1B89706D63991A57160105E21B9B881105EE01930D6125055CC2D007E9FF622 | |||
| 3372 | Transport Plan.exe | C:\Users\admin\AppData\Local\Ozelotters226\Aktiecertifikat\Lagrene\Marcellos\Adventure_17.bmp | image | |
MD5:9BF544F8C49DB9355A2BAEDFEF09041B | SHA256:45B807565DBDF778C302980D078DDDA68F807BC0CCABE945AD0219AD4EC7EE6F | |||
| 3372 | Transport Plan.exe | C:\Users\admin\AppData\Local\Ozelotters226\Aktiecertifikat\Lagrene\Centuplication\Rumanians\hmmapi.dll | executable | |
MD5:DE3C51584774AD450ED49715BEC1E389 | SHA256:E690864568D17DC5D86ACCA1FDCDB76C878E63C7B4F69E6003F875B99A7CB766 | |||
| 3372 | Transport Plan.exe | C:\Users\admin\AppData\Local\Temp\nspB4FF.tmp\System.dll | executable | |
MD5:0063D48AFE5A0CDC02833145667B6641 | SHA256:AC9DFE3B35EA4B8932536ED7406C29A432976B685CC5322F94EF93DF920FEDE7 | |||
| 3372 | Transport Plan.exe | C:\Users\admin\AppData\Local\Ozelotters226\Aktiecertifikat\Lagrene\Sikkerhedsforvarede\Diverticle\contact-new.png | image | |
MD5:67A92C6D0A488E72C5AA735EDE38FD72 | SHA256:2AB70ACC8EE72B3B42763BA722F555B8E859FAF8D93F9032D782C78EB2FF1830 | |||
| 3372 | Transport Plan.exe | C:\Users\admin\AppData\Local\Ozelotters226\Aktiecertifikat\Lagrene\Marcellos\Ceremonialists.Mis | text | |
MD5:6551542295E4622B92401EC290BB5865 | SHA256:69D96911FF3B8C258C8D9109AE772CFE6C8AD628BC17FB3B49012E3B505B4C34 | |||
| 3372 | Transport Plan.exe | C:\Users\admin\AppData\Local\Ozelotters226\Aktiecertifikat\Lagrene\Bynker.Pre | binary | |
MD5:5FE4AD9131BC80FC737DA1ACA0E9DA64 | SHA256:A67D66AEDBCBBFF6DFE2B5BCC7DB7AD81332AA38402779DA8ABB163697E8EE6D | |||
| 3372 | Transport Plan.exe | C:\Users\admin\AppData\Local\Ozelotters226\Aktiecertifikat\Lagrene\Marcellos\api-ms-win-core-console-l1-2-0.dll | executable | |
MD5:57193BFBCCEFE3D5DF8C1A0D27C4E8D4 | SHA256:F5025E74DE2C1C6EA74E475B57771AC32205E6F1FA6A0390298BBE1F4049AC5D | |||
| 3372 | Transport Plan.exe | C:\Users\admin\AppData\Local\Ozelotters226\Aktiecertifikat\Lagrene\Sikkerhedsforvarede\Diverticle\audio-x-generic-symbolic.symbolic.png | image | |
MD5:79B7B2040BFDFF36BEC2D20F727DFC7E | SHA256:6B0807769D18D56DCC9AB666FC8A6F7160E9707C3BC02545EABDF16C5D4029B8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |