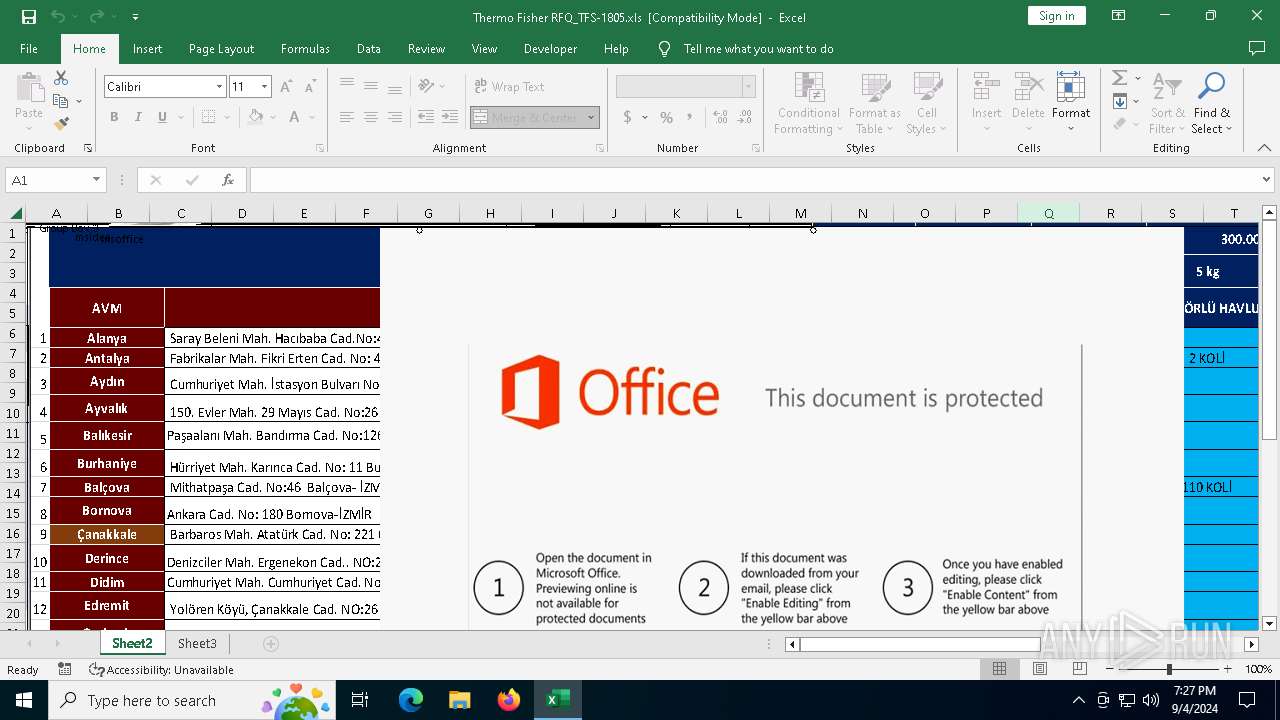
| File name: | Thermo Fisher RFQ_TFS-1805.xls |
| Full analysis: | https://app.any.run/tasks/6d5acd4e-62fa-486e-8baf-926100acaddb |
| Verdict: | Malicious activity |
| Analysis date: | September 04, 2024, 19:27:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Name of Creating Application: Microsoft Excel, Create Time/Date: Sat Sep 16 00:00:00 2006, Last Saved Time/Date: Mon Sep 2 01:40:51 2024, Security: 1 |
| MD5: | 02680733F759B55032448DA435C80683 |
| SHA1: | 59908CF9B3911D669BC5175EE20F461A42FB9C98 |
| SHA256: | 6E14E121B52039981D9A87A94F9B4A7D5C40BF696E31F5C6A298C4F7B409BFAC |
| SSDEEP: | 3072:EBpuPqsXdtGNFwtDpAo3XxZv2w8gm8mp5mSuVBg3eHOdEXq3cNSPa9YmfiwwSmi:ErQdoU1PeLgmz01/xOdEXvN79RKnSmi |
MALICIOUS
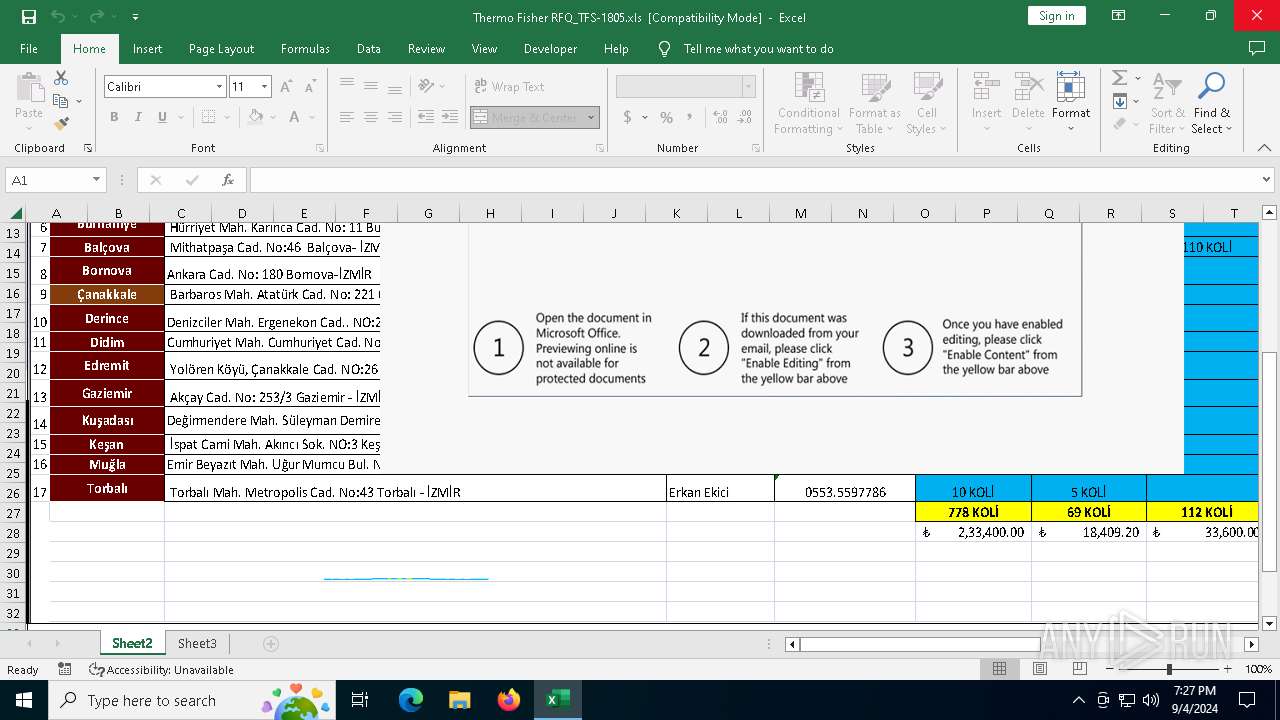
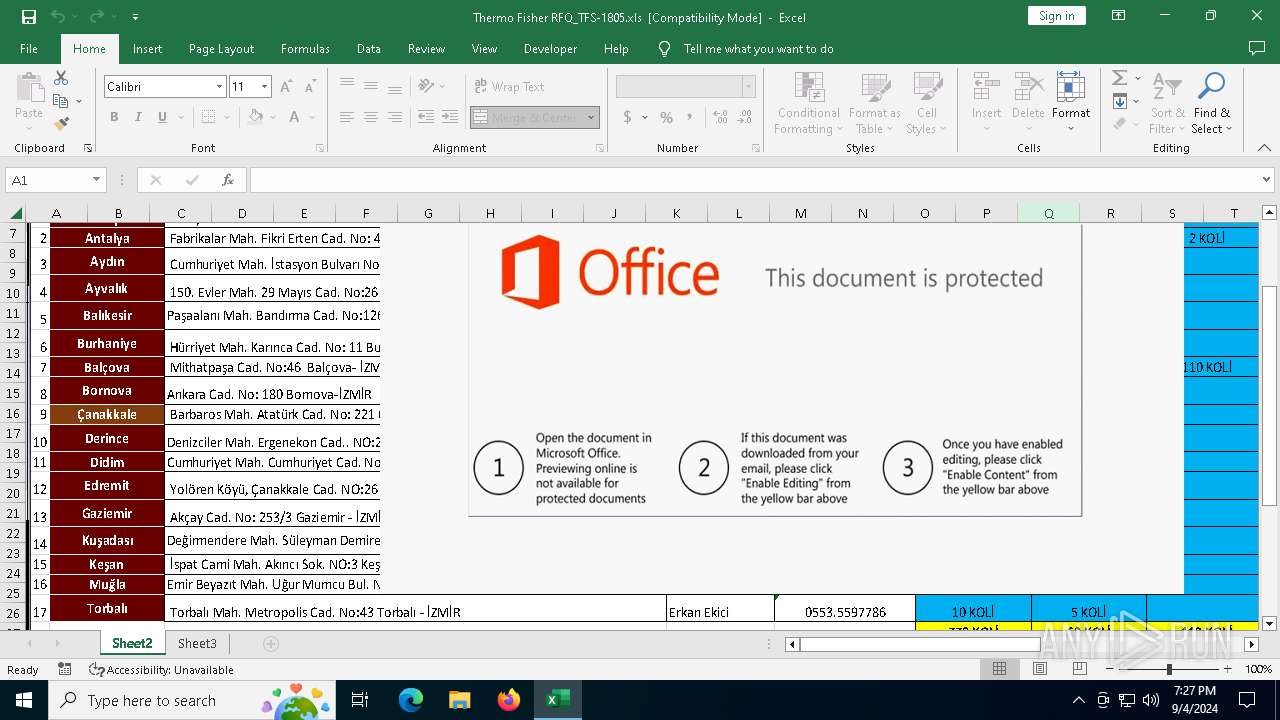
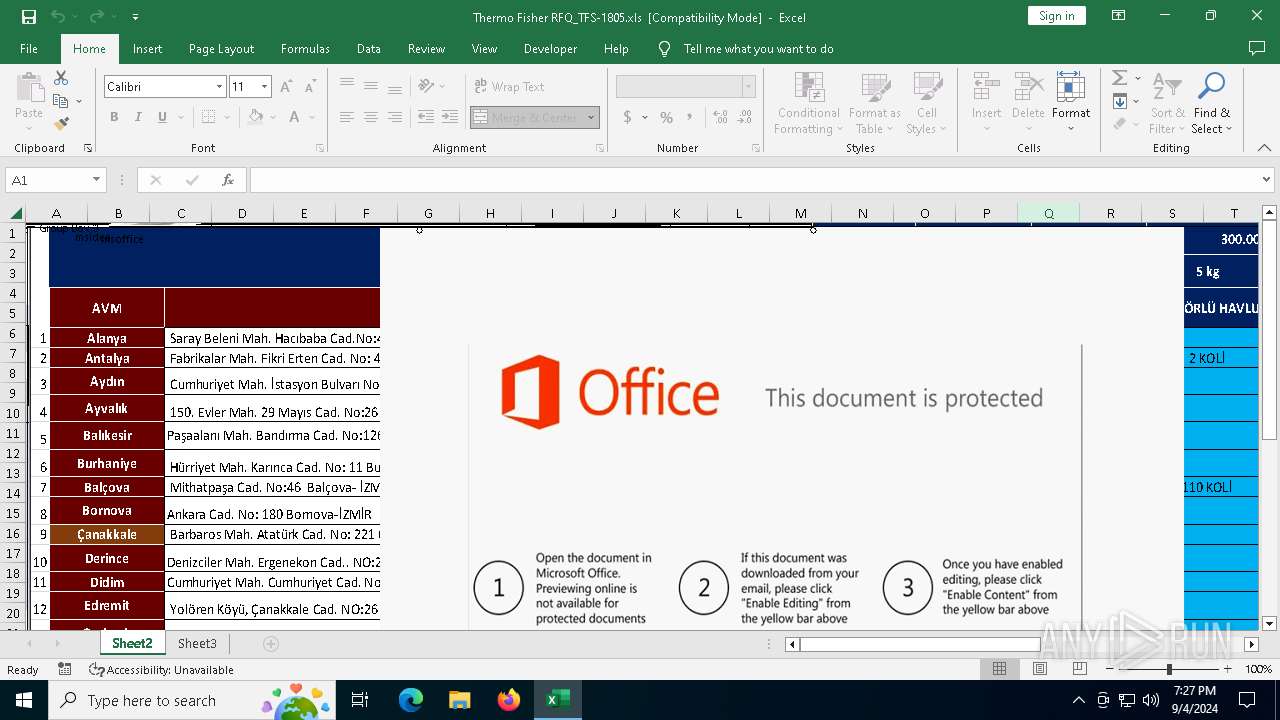
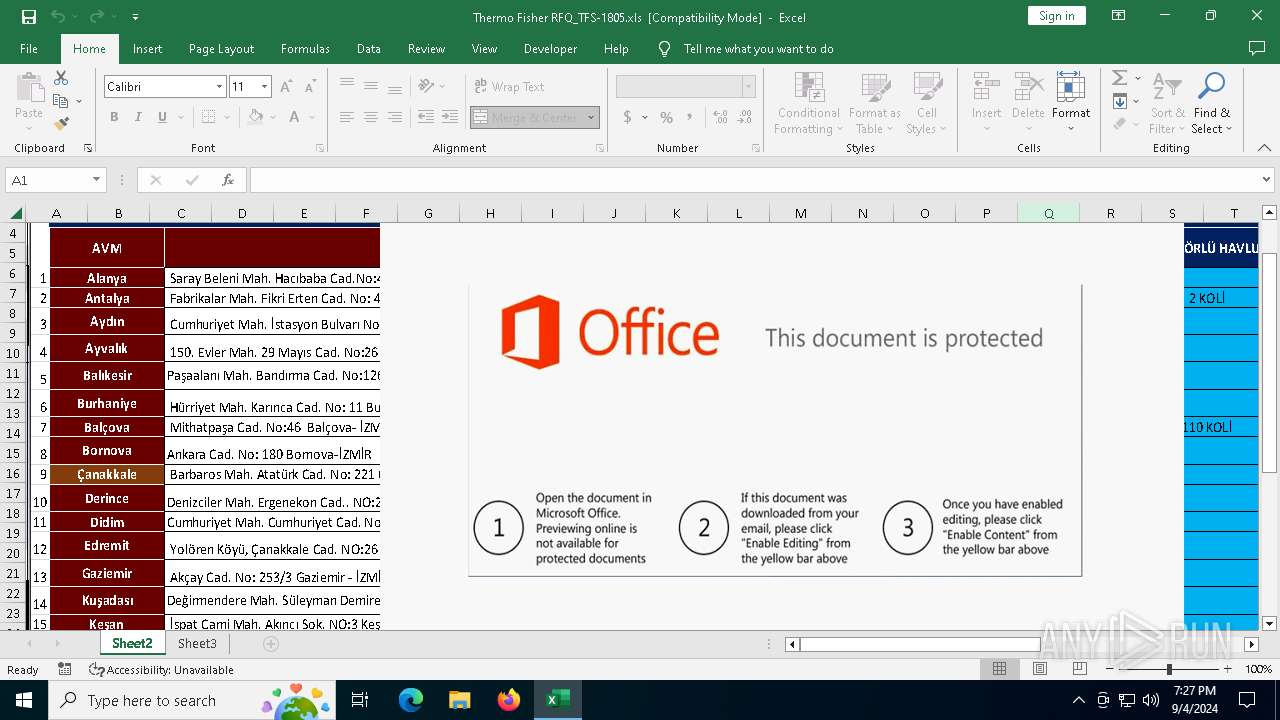
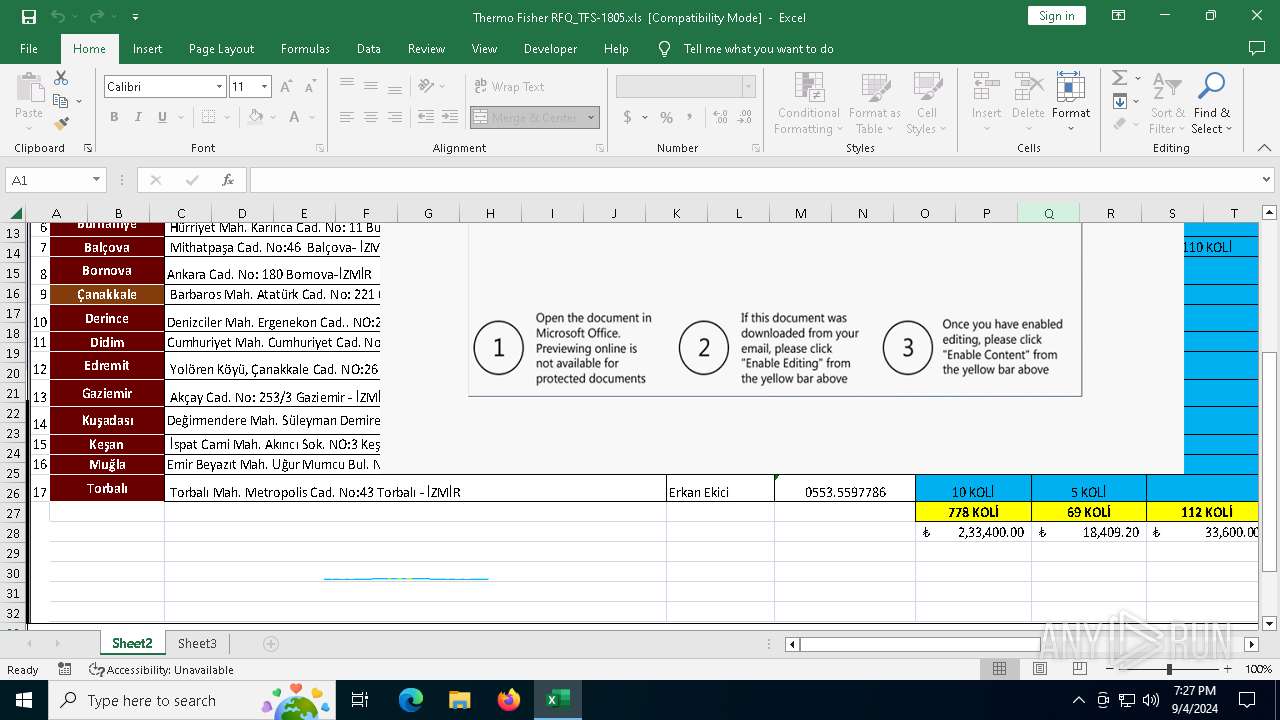
Phishing document has been detected
- EXCEL.EXE (PID: 7164)
SUSPICIOUS
No suspicious indicators.INFO
The process uses the downloaded file
- EXCEL.EXE (PID: 7164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| Author: | - |
|---|---|
| LastModifiedBy: | - |
| Software: | Microsoft Excel |
| CreateDate: | 2006:09:16 00:00:00 |
| ModifyDate: | 2024:09:02 01:40:51 |
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| AppVersion: | 12 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
| CompObjUserTypeLen: | 38 |
| CompObjUserType: | Microsoft Office Excel 2003 Worksheet |
Total processes
131
Monitored processes
1
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7164 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\Desktop\Thermo Fisher RFQ_TFS-1805.xls" | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
6 726
Read events
6 457
Write events
239
Delete events
30
Modification events
| (PID) Process: | (7164) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (7164) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\EXCEL\7164 |
| Operation: | write | Name: | 0 |
Value: 0B0E10E4F5EC3FDAF07942A04BFB860A563C16230046E4DEC08788E0BFED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511FC37D2120965007800630065006C002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7164) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (7164) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (7164) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (7164) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (7164) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (7164) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (7164) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (7164) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
1
Suspicious files
29
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7164 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\BDAF21A8.emf | binary | |
MD5:03EF0C99E79896DF7DE7A3AB6AD1EA84 | SHA256:D00E6A01EDA2CEC476AA16548A51D8EA9384BAE1445C2DE7CD5913132DBD5B9D | |||
| 7164 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:B0BFBB454546EE3E086195BD64E0BDDB | SHA256:4A8B7282382CB799A7B0E01A6D71652315B76747F85D711D4E839EA8CB9687D9 | |||
| 7164 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\Thermo Fisher RFQ_TFS-1805.xls.LNK | binary | |
MD5:F1604A4F4DFA751684E1F0A31DB05D70 | SHA256:6B850DE6783DE41D31FCEF72A09F8231DCA19DBEBD572A52E95140A1B8555695 | |||
| 7164 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:FCF486E05D44C64A708C76F502942847 | SHA256:08EBA0287BFDD2A4560C6E327978572DB6AE49577CF5E9D2308E3225C314C82D | |||
| 7164 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:E73D5DABAA4A6FA94EC04726EB6DA52D | SHA256:98F280760FDDA7416F4EF7CB4FEEBE0F517F48B0389C0B4BF8006499A7543651 | |||
| 7164 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\excel.exe_Rules.xml | xml | |
MD5:0E3976A929C4878794F96FEF2C441CD0 | SHA256:77CE327AFF3AEE07D14AC02AA96347AE3277358DB4D36959E235B782C085AB1E | |||
| 7164 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:6AEE7893A597B0D96CEA90D62F1D2DCD | SHA256:F6389C28A840DCD5352A55E10A8ED1A16AEACC9871CA6DF1C601B402DFD689CF | |||
| 7164 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json | binary | |
MD5:EFD9AFBCCF08B803E3AF93B5D523DA31 | SHA256:85993E79B2036768B03B7658A268959A92184663B7CCE7600B7D35DF82D4E8FE | |||
| 7164 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Excel\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:524F64EA3E4FD6596BCF373C7875E204 | SHA256:FA25A0949295724172C34676B631B93B0D84BE5A54E7963C4EB8B0329500E947 | |||
| 7164 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json.tmp | binary | |
MD5:EFD9AFBCCF08B803E3AF93B5D523DA31 | SHA256:85993E79B2036768B03B7658A268959A92184663B7CCE7600B7D35DF82D4E8FE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
38
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1440 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7164 | EXCEL.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
876 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
876 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7164 | EXCEL.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7008 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7072 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1440 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1440 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
7164 | EXCEL.EXE | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |