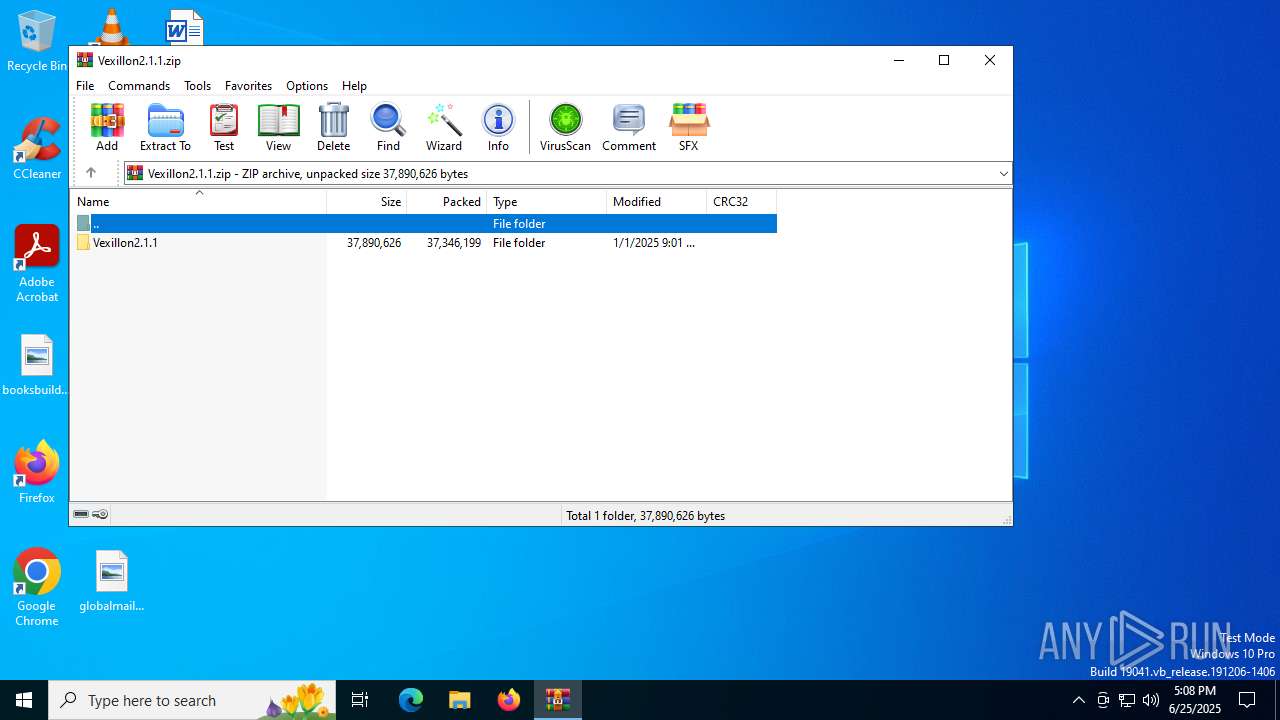
| File name: | Vexillon2.1.1.zip |
| Full analysis: | https://app.any.run/tasks/16ee7c80-b0a0-424c-88d7-c5fbe8f8a017 |
| Verdict: | Malicious activity |
| Analysis date: | June 25, 2025, 17:08:33 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 7024469D853671023BD48666E5370E76 |
| SHA1: | 607ED5AC8D5D9C37BAB629F1B95C494762B9A6BB |
| SHA256: | 6DD63217E284F55EF7E6A71005F2B1B6BE00E4C4C89965E681BB175F135D3E54 |
| SSDEEP: | 393216:jkMtaP77ZSCJmzEYL8t1aQhDSFAzKyMiUIafTzdPUih:wMY7sCJQL41aQxsAzLMZVp |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2680)
SUSPICIOUS
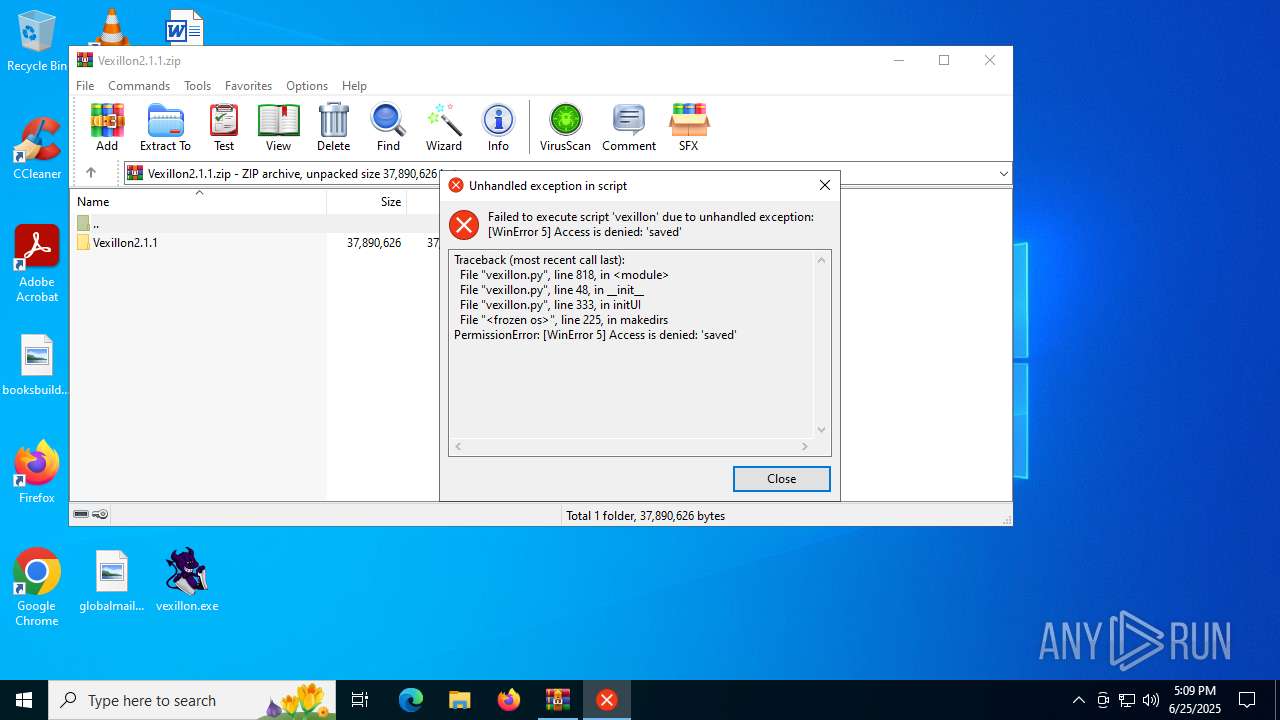
Process drops legitimate windows executable
- vexillon.exe (PID: 6768)
The process drops C-runtime libraries
- vexillon.exe (PID: 6768)
Process drops python dynamic module
- vexillon.exe (PID: 6768)
Executable content was dropped or overwritten
- vexillon.exe (PID: 6768)
Application launched itself
- vexillon.exe (PID: 6768)
Loads Python modules
- vexillon.exe (PID: 6372)
There is functionality for taking screenshot (YARA)
- vexillon.exe (PID: 6768)
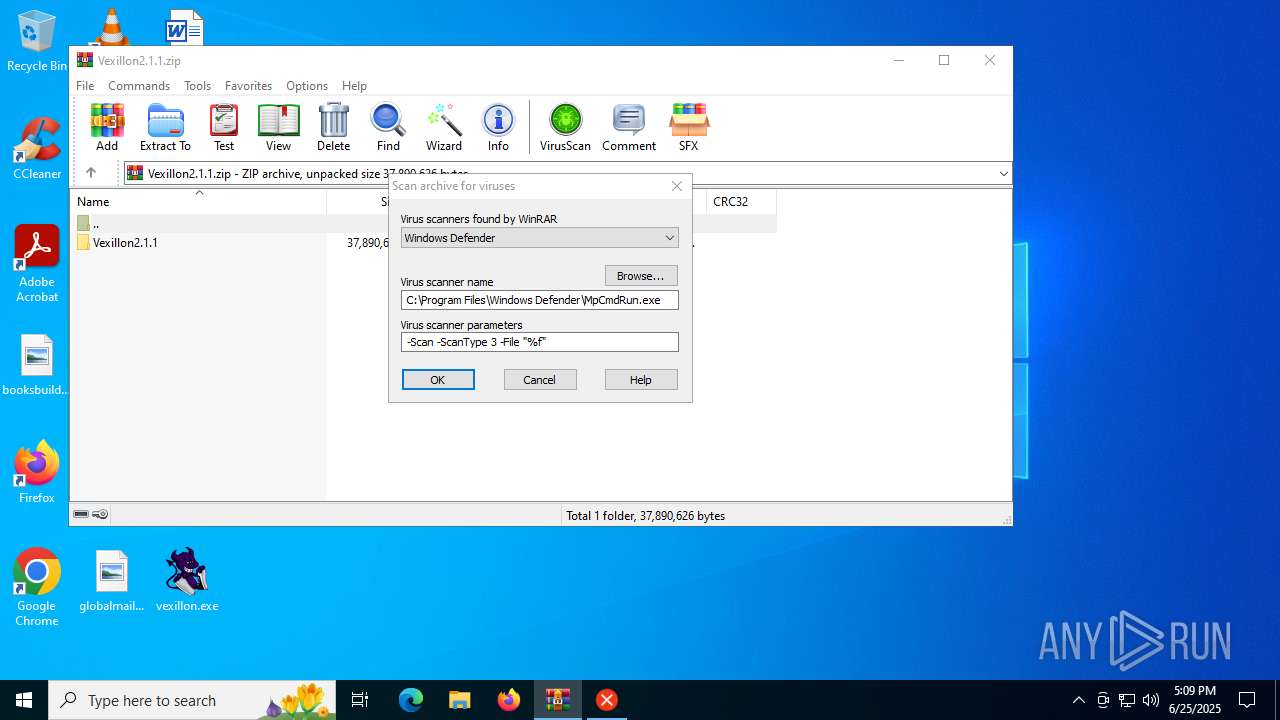
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2680)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 2680)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 2680)
INFO
Checks supported languages
- vexillon.exe (PID: 6768)
- vexillon.exe (PID: 6372)
- MpCmdRun.exe (PID: 4132)
Reads the computer name
- vexillon.exe (PID: 6768)
- vexillon.exe (PID: 6372)
- MpCmdRun.exe (PID: 4132)
Manual execution by a user
- vexillon.exe (PID: 6768)
Create files in a temporary directory
- vexillon.exe (PID: 6768)
- MpCmdRun.exe (PID: 4132)
The sample compiled with english language support
- vexillon.exe (PID: 6768)
PyInstaller has been detected (YARA)
- vexillon.exe (PID: 6768)
Checks proxy server information
- slui.exe (PID: 6800)
Reads the software policy settings
- slui.exe (PID: 6800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:01:01 22:01:08 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Vexillon2.1.1/ |
Total processes
136
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2680 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Vexillon2.1.1.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3688 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR2680.26641\Rar$Scan123834.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
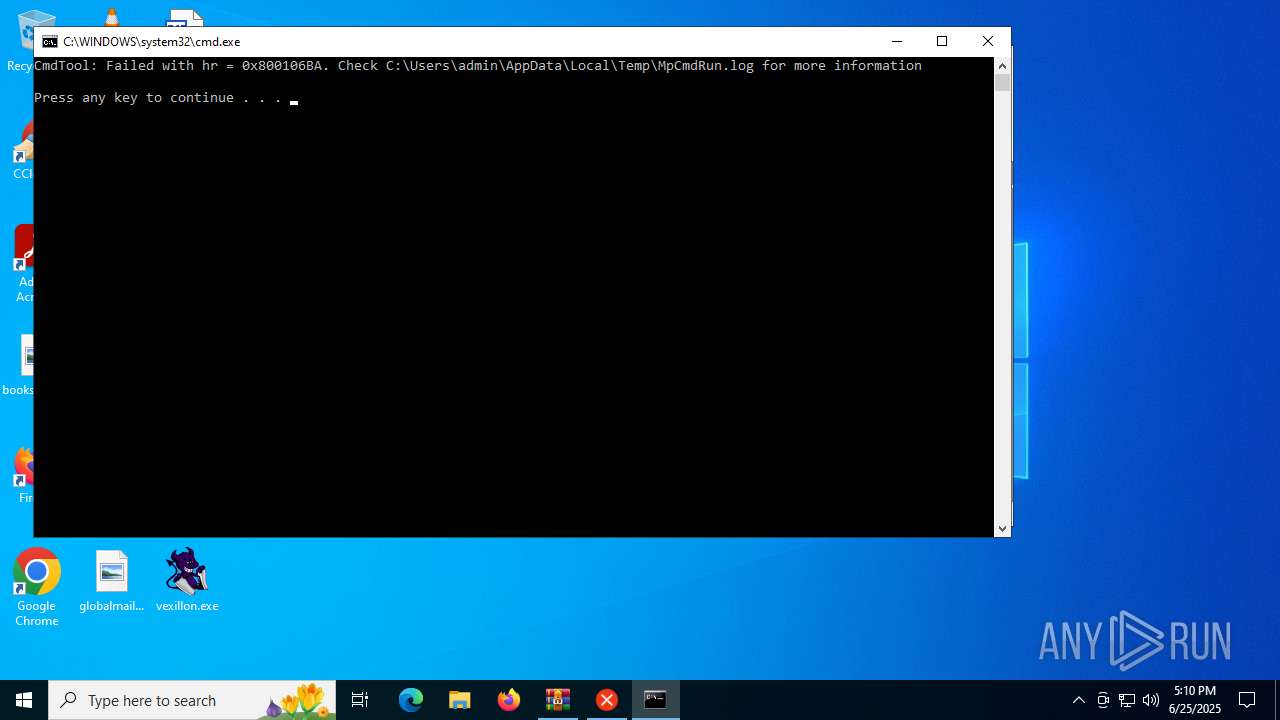
| 4132 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR2680.26641" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5768 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6372 | "C:\Users\admin\Desktop\vexillon.exe" | C:\Users\admin\Desktop\vexillon.exe | — | vexillon.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6768 | "C:\Users\admin\Desktop\vexillon.exe" | C:\Users\admin\Desktop\vexillon.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6800 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 241
Read events
5 232
Write events
9
Delete events
0
Modification events
| (PID) Process: | (2680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Vexillon2.1.1.zip | |||
| (PID) Process: | (2680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
55
Suspicious files
1
Text files
2
Unknown types
75
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6768 | vexillon.exe | C:\Users\admin\AppData\Local\Temp\_MEI67682\PyQt5\Qt5\bin\Qt5Core.dll | executable | |
MD5:817520432A42EFA345B2D97F5C24510E | SHA256:8D2FF4CE9096DDCCC4F4CD62C2E41FC854CFD1B0D6E8D296645A7F5FD4AE565A | |||
| 6768 | vexillon.exe | C:\Users\admin\AppData\Local\Temp\_MEI67682\PyQt5\Qt5\bin\MSVCP140.dll | executable | |
MD5:01B946A2EDC5CC166DE018DBB754B69C | SHA256:88F55D86B50B0A7E55E71AD2D8F7552146BA26E927230DAF2E26AD3A971973C5 | |||
| 6768 | vexillon.exe | C:\Users\admin\AppData\Local\Temp\_MEI67682\PyQt5\Qt5\bin\d3dcompiler_47.dll | executable | |
MD5:B0AE3AA9DD1EBD60BDF51CB94834CD04 | SHA256:E994847E01A6F1E4CBDC5A864616AC262F67EE4F14DB194984661A8D927AB7F4 | |||
| 6768 | vexillon.exe | C:\Users\admin\AppData\Local\Temp\_MEI67682\PyQt5\Qt5\bin\Qt5Qml.dll | executable | |
MD5:D055566B5168D7B1D4E307C41CE47C4B | SHA256:30035484C81590976627F8FACE9507CAA8581A7DC7630CCCF6A8D6DE65CAB707 | |||
| 6768 | vexillon.exe | C:\Users\admin\AppData\Local\Temp\_MEI67682\PyQt5\Qt5\bin\Qt5Network.dll | executable | |
MD5:3569693D5BAE82854DE1D88F86C33184 | SHA256:4EF341AE9302E793878020F0740B09B0F31CB380408A697F75C69FDBD20FC7A1 | |||
| 6768 | vexillon.exe | C:\Users\admin\AppData\Local\Temp\_MEI67682\PyQt5\Qt5\bin\Qt5DBus.dll | executable | |
MD5:0E8FF02D971B61B5D2DD1AC4DF01AE4A | SHA256:1AA70B106A10C86946E23CAA9FC752DC16E29FBE803BBA1F1AB30D1C63EE852A | |||
| 6768 | vexillon.exe | C:\Users\admin\AppData\Local\Temp\_MEI67682\PyQt5\Qt5\bin\Qt5Gui.dll | executable | |
MD5:47307A1E2E9987AB422F09771D590FF1 | SHA256:5E7D2D41B8B92A880E83B8CC0CA173F5DA61218604186196787EE1600956BE1E | |||
| 6768 | vexillon.exe | C:\Users\admin\AppData\Local\Temp\_MEI67682\PyQt5\Qt5\bin\MSVCP140_1.dll | executable | |
MD5:0FE6D52EB94C848FE258DC0EC9FF4C11 | SHA256:446C48C1224C289BD3080087FE15D6759416D64F4136ADDF30086ABD5415D83F | |||
| 6768 | vexillon.exe | C:\Users\admin\AppData\Local\Temp\_MEI67682\PyQt5\Qt5\bin\Qt5Quick.dll | executable | |
MD5:65F59CFC0C1C060CE20D3B9CEFFBAF46 | SHA256:C81AD3C1111544064B1830C6F1AEF3C1FD13B401546AB3B852D697C0F4D854B3 | |||
| 6768 | vexillon.exe | C:\Users\admin\AppData\Local\Temp\_MEI67682\PyQt5\Qt5\bin\Qt5QmlModels.dll | executable | |
MD5:2030C4177B499E6118BE5B9E5761FCE1 | SHA256:51E4E5A5E91F78774C44F69B599FAE4735277EF2918F7061778615CB5C4F6E81 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
19
DNS requests
8
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5104 | RUXIMICS.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5104 | RUXIMICS.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5104 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5104 | RUXIMICS.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |