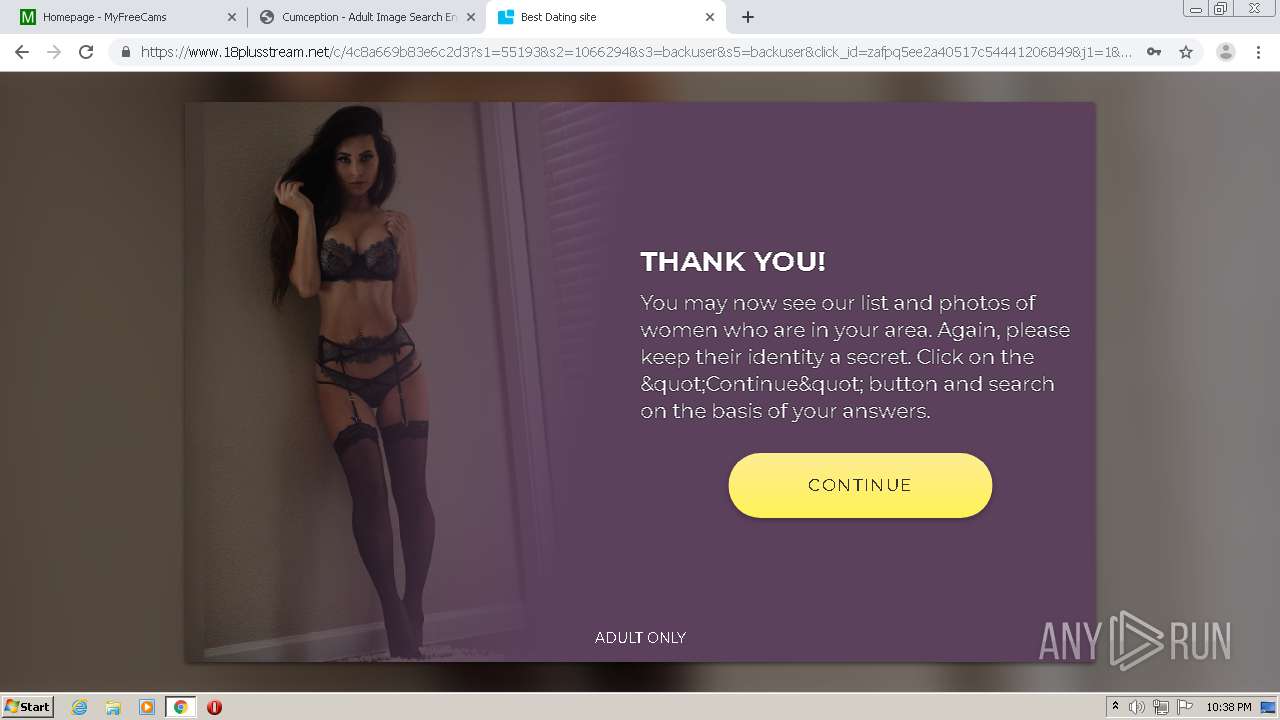
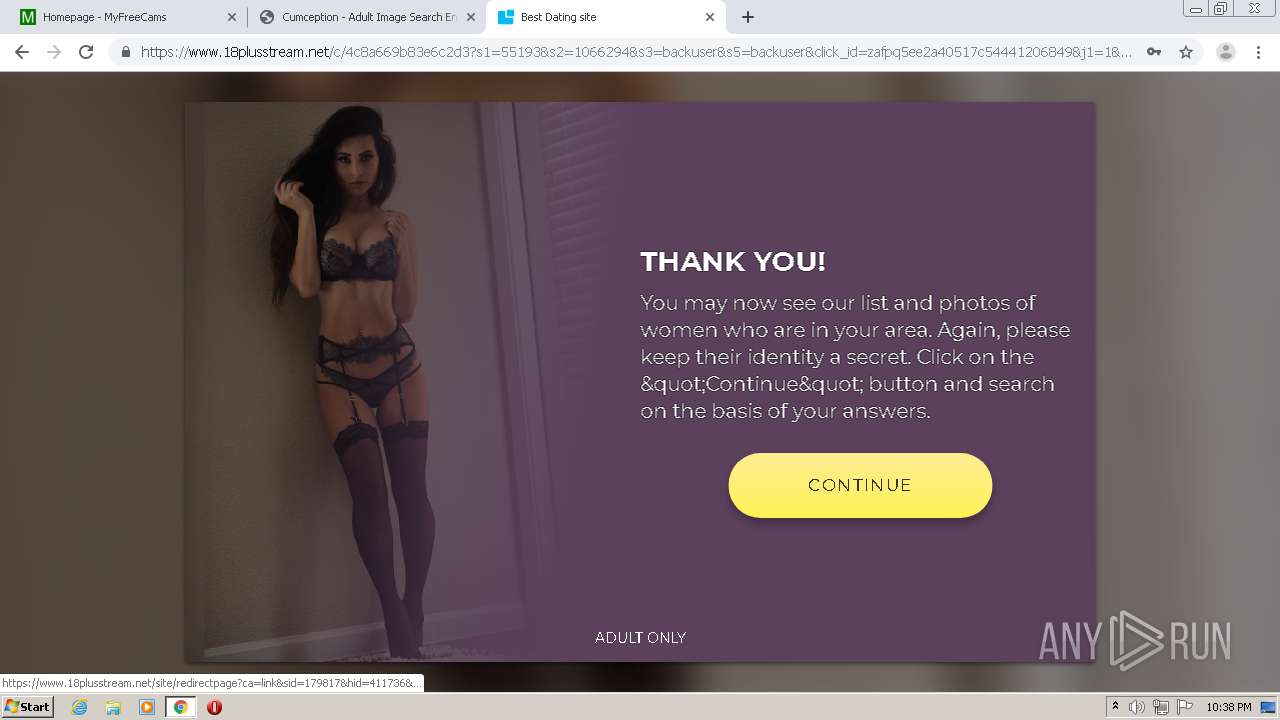
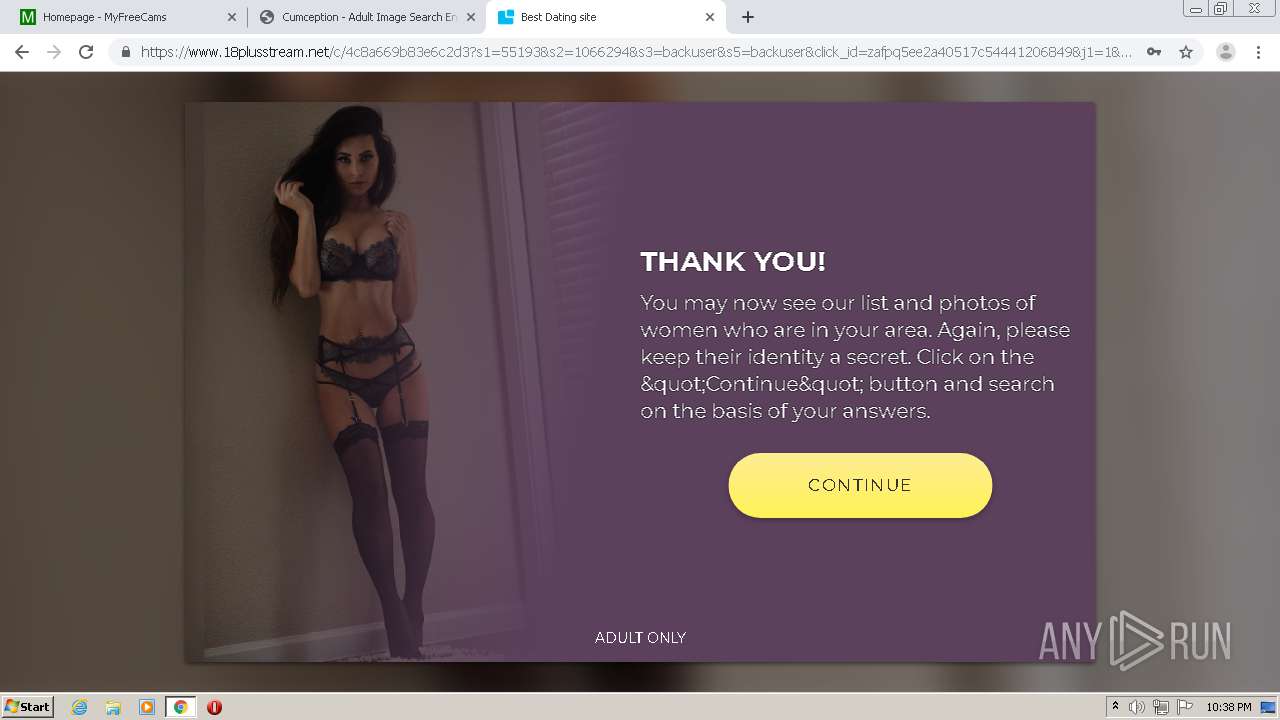
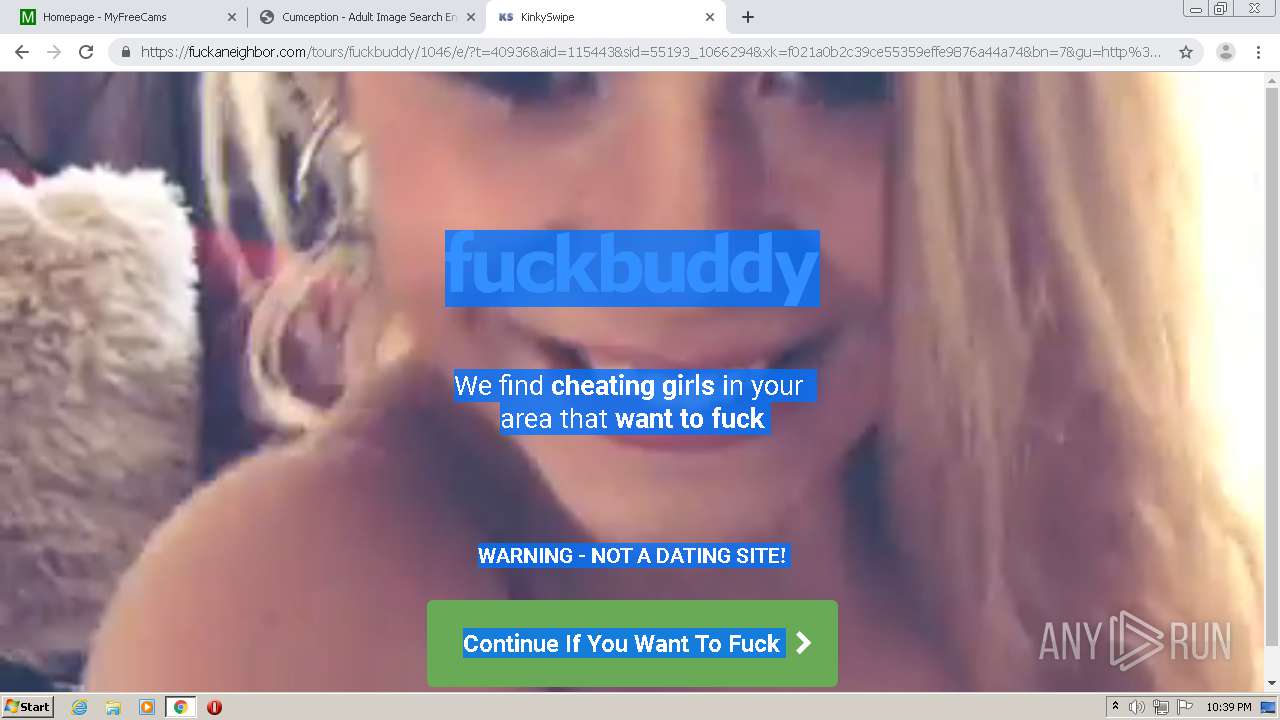
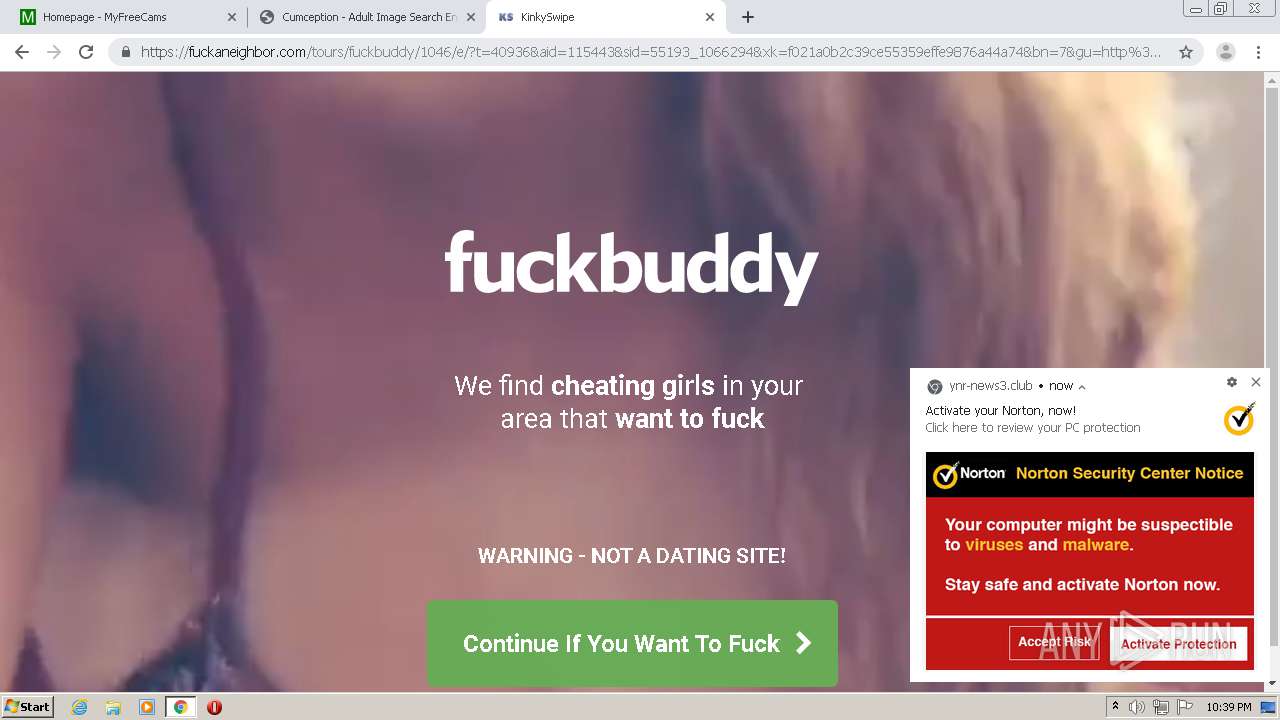
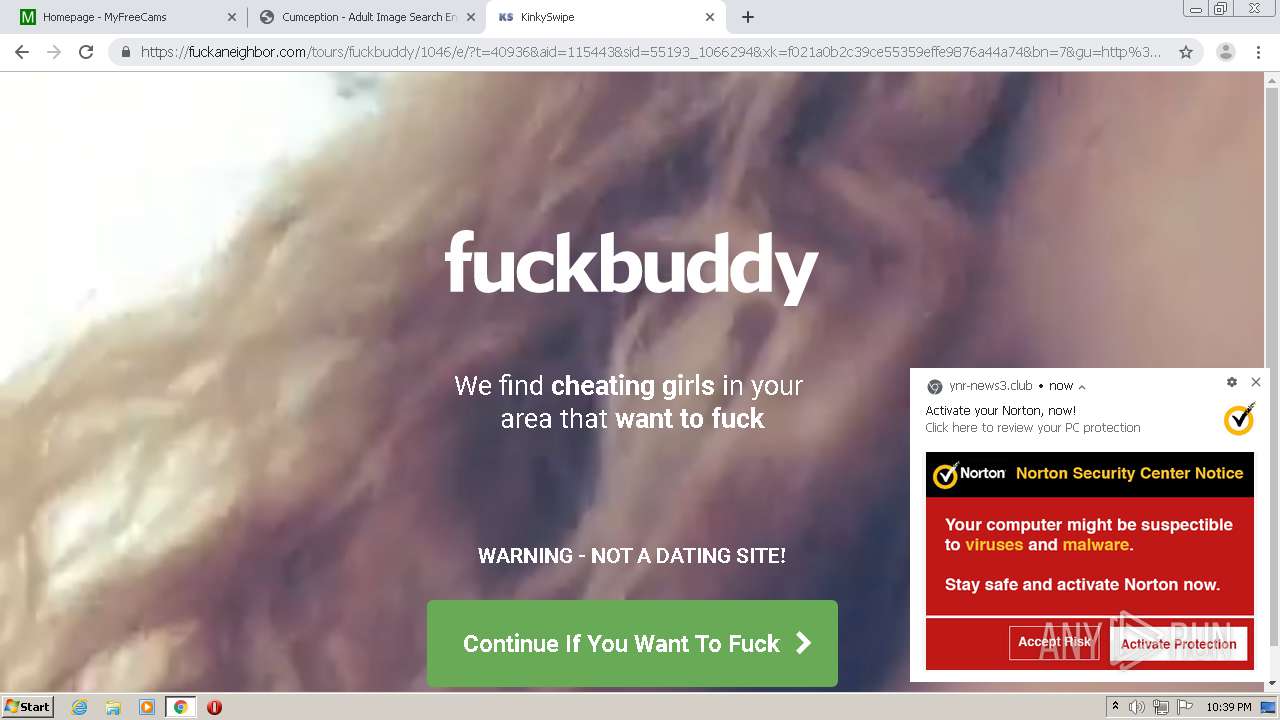
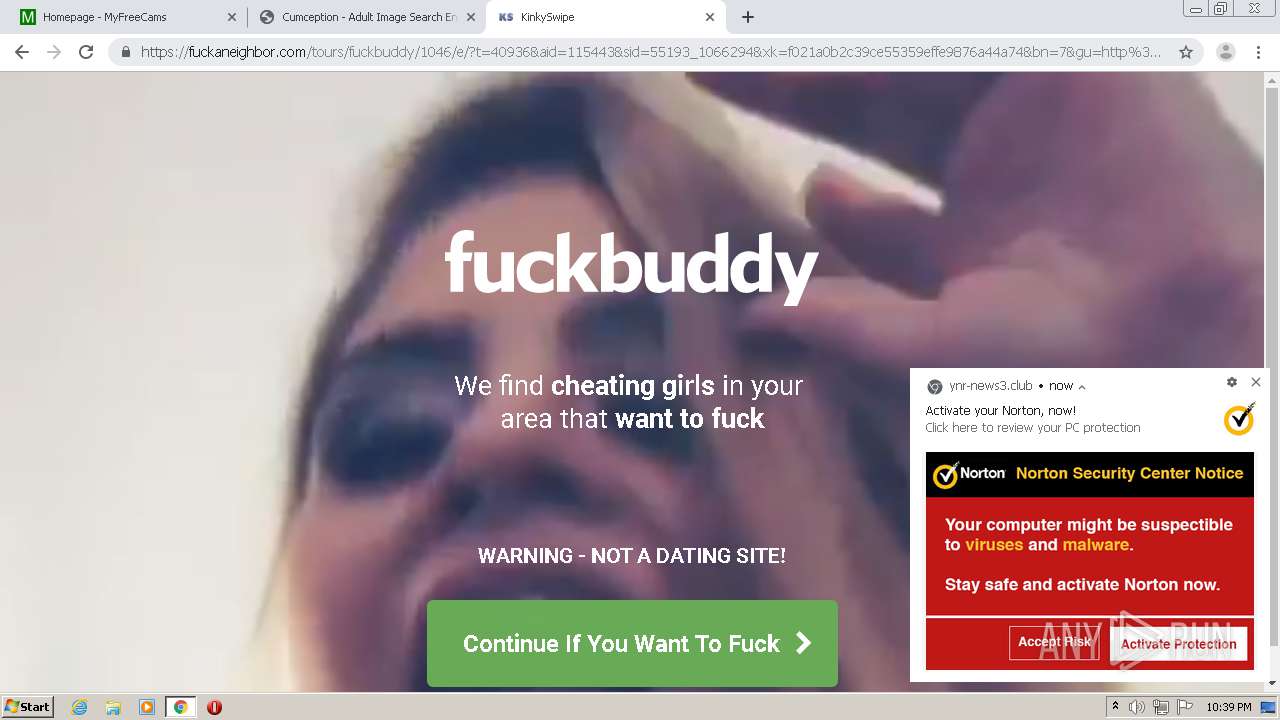
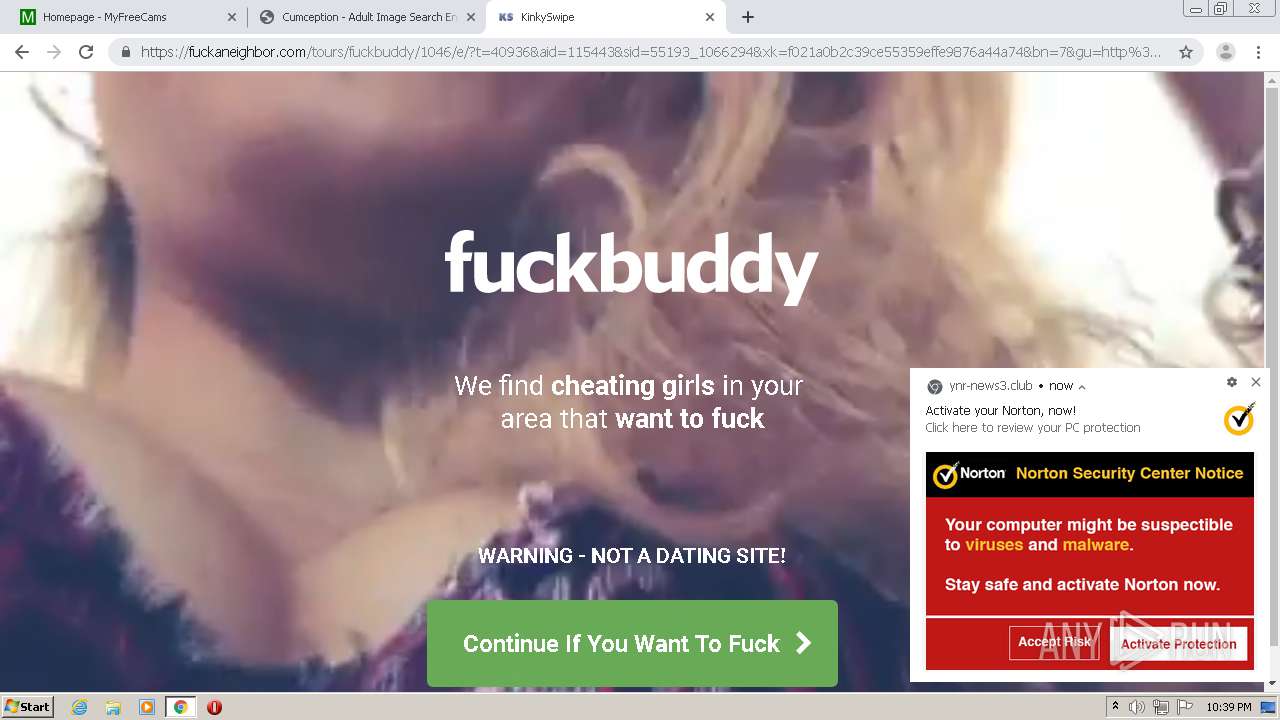
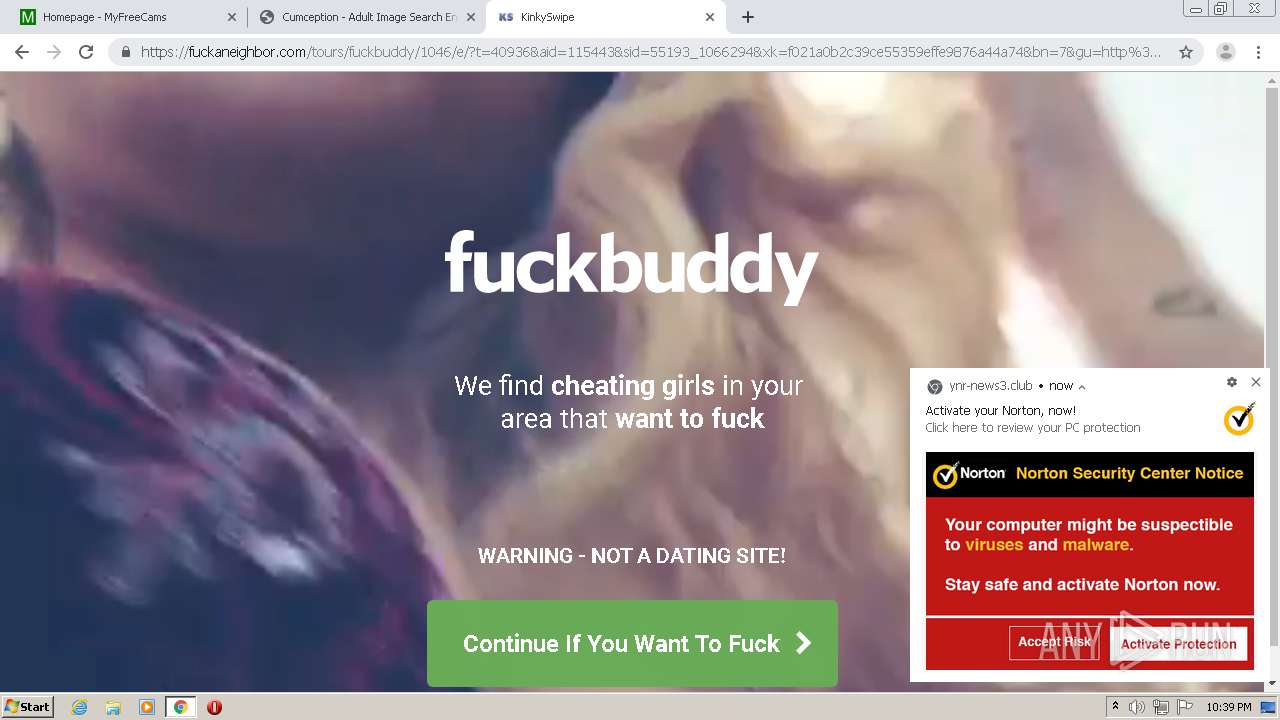
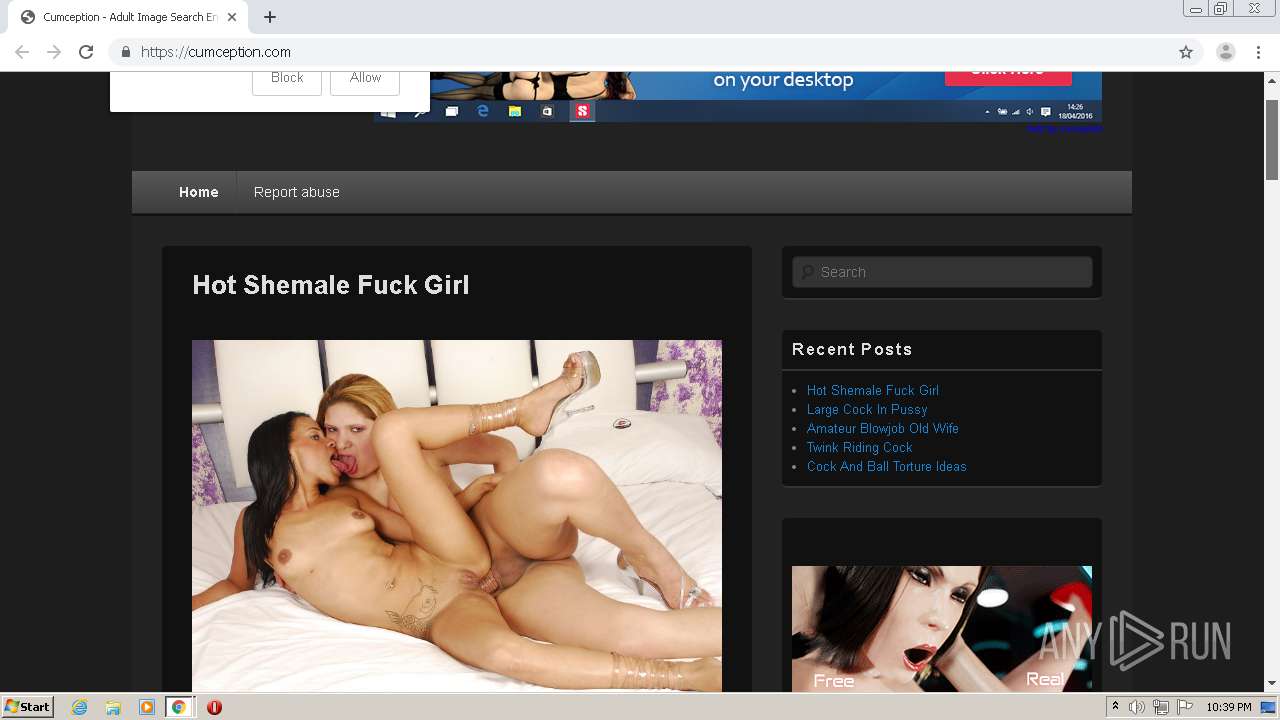
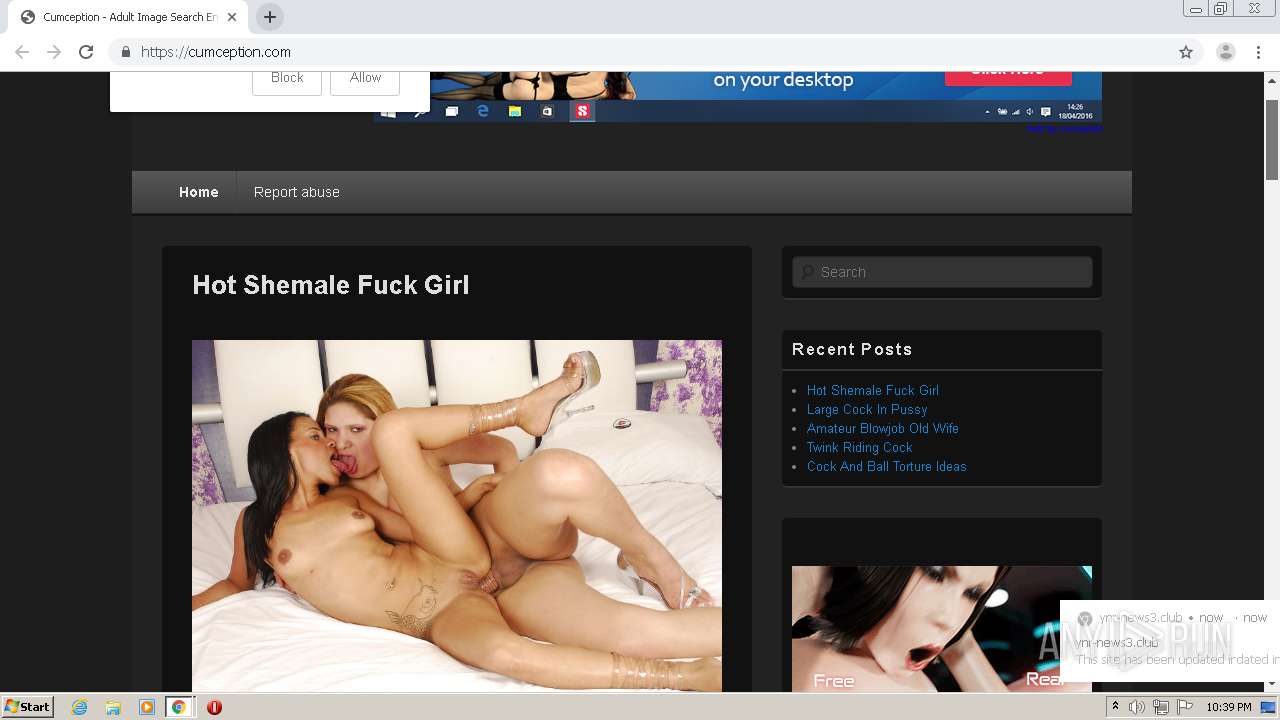
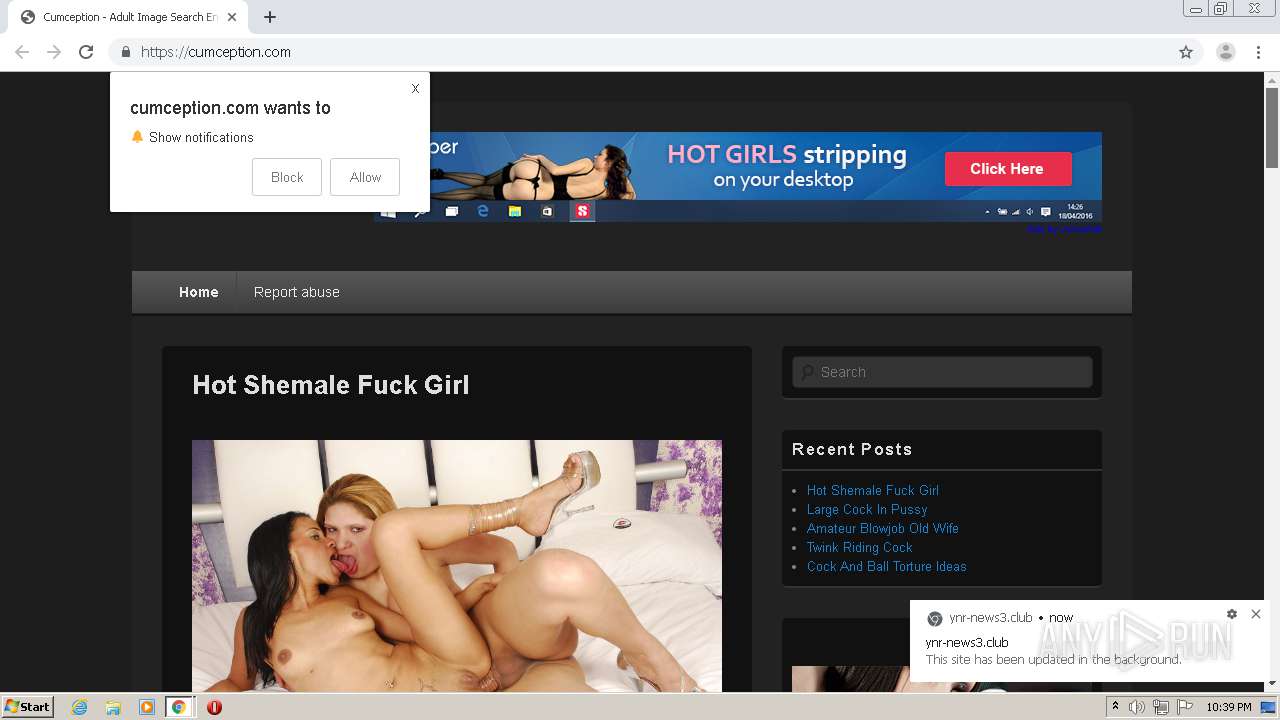
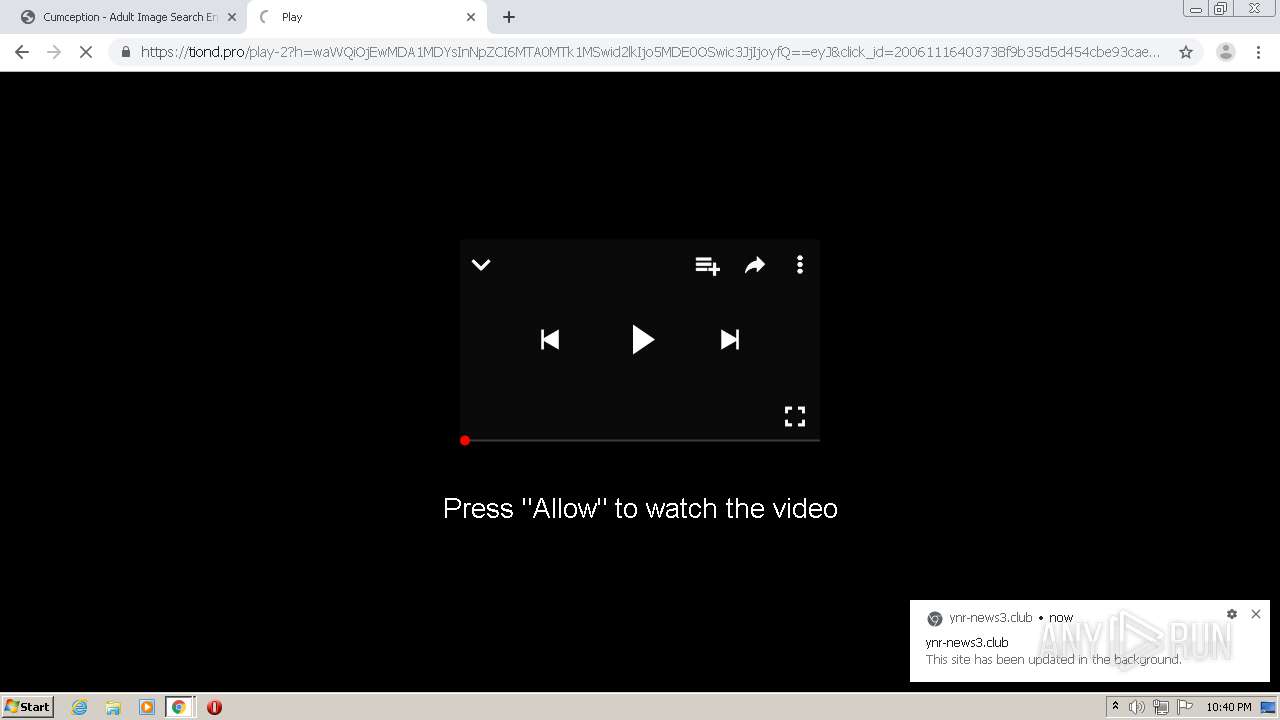
| URL: | http://cumception.com |
| Full analysis: | https://app.any.run/tasks/2570fc11-41c1-41a4-93c7-50771beb9c6d |
| Verdict: | Malicious activity |
| Analysis date: | June 11, 2020, 21:36:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | E420B1CA24E4959FA4669CC6401257CB |
| SHA1: | 627337592C056857171CD0E33AB9BEF32E3FF147 |
| SHA256: | 6DC3BE6E77C137829A7D5FB159B3D43A71A27517E37A54CCA0383EF0522466D3 |
| SSDEEP: | 3:N1KdQ7kMKLLdIn:CSpK/dIn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 1232)
INFO
Reads the hosts file
- chrome.exe (PID: 1232)
- chrome.exe (PID: 4060)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 1232)
Creates files in the user directory
- chrome.exe (PID: 1232)
Application launched itself
- chrome.exe (PID: 1232)
Reads settings of System Certificates
- chrome.exe (PID: 4060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
95
Monitored processes
58
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 412 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,3654299152984145593,16910848556107282327,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=13350322497663630931 --mojo-platform-channel-handle=3992 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 588 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,3654299152984145593,16910848556107282327,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13020705499027452259 --renderer-client-id=33 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4472 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 752 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,3654299152984145593,16910848556107282327,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7280849691763383297 --renderer-client-id=47 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5660 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 872 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,3654299152984145593,16910848556107282327,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5646585146181979645 --renderer-client-id=35 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1272 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,3654299152984145593,16910848556107282327,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7339406824890757970 --renderer-client-id=41 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4460 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 976 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,3654299152984145593,16910848556107282327,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8755596533343616413 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2276 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "http://cumception.com" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,3654299152984145593,16910848556107282327,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4034314871224942518 --renderer-client-id=16 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3940 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1460 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,3654299152984145593,16910848556107282327,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4110989443788938889 --renderer-client-id=54 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=584 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1576 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,3654299152984145593,16910848556107282327,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13275766392834177660 --renderer-client-id=34 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4592 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 360
Read events
1 234
Write events
121
Delete events
5
Modification events
| (PID) Process: | (1232) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1232) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1232) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1232) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1232) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2092) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 1232-13236384986065375 |
Value: 259 | |||
| (PID) Process: | (1232) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1232) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1232) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3120-13213713943555664 |
Value: 0 | |||
| (PID) Process: | (1232) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
0
Suspicious files
191
Text files
409
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1232 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5EE2A3DA-4D0.pma | — | |
MD5:— | SHA256:— | |||
| 1232 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1232 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000028.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1232 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF168a33.TMP | text | |
MD5:— | SHA256:— | |||
| 1232 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1232 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1232 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF168a82.TMP | text | |
MD5:— | SHA256:— | |||
| 1232 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF168a53.TMP | text | |
MD5:— | SHA256:— | |||
| 1232 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1232 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF168c66.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
223
DNS requests
99
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
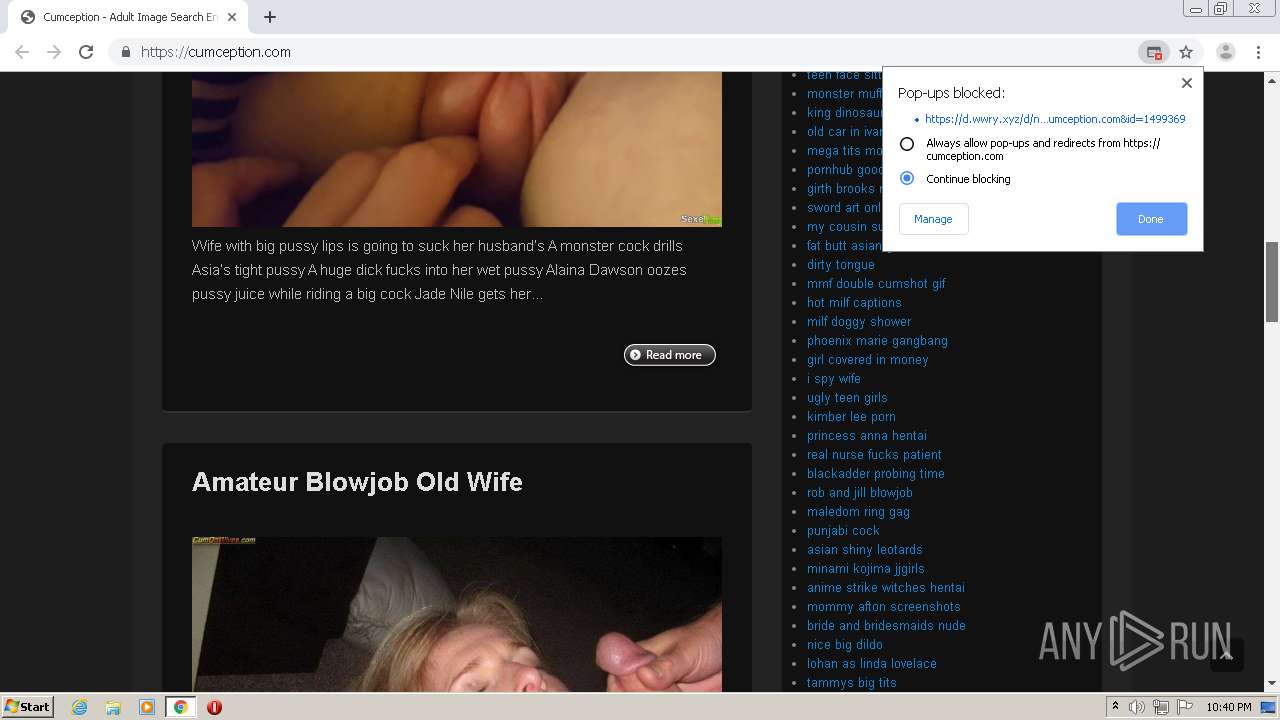
4060 | chrome.exe | GET | 302 | 34.197.193.86:80 | http://redir.jads.co/pu_uu.php?cb=1591911408&uu=0CF411FE-53F5-B446-1945-BECF7485F5CA | US | — | — | suspicious |
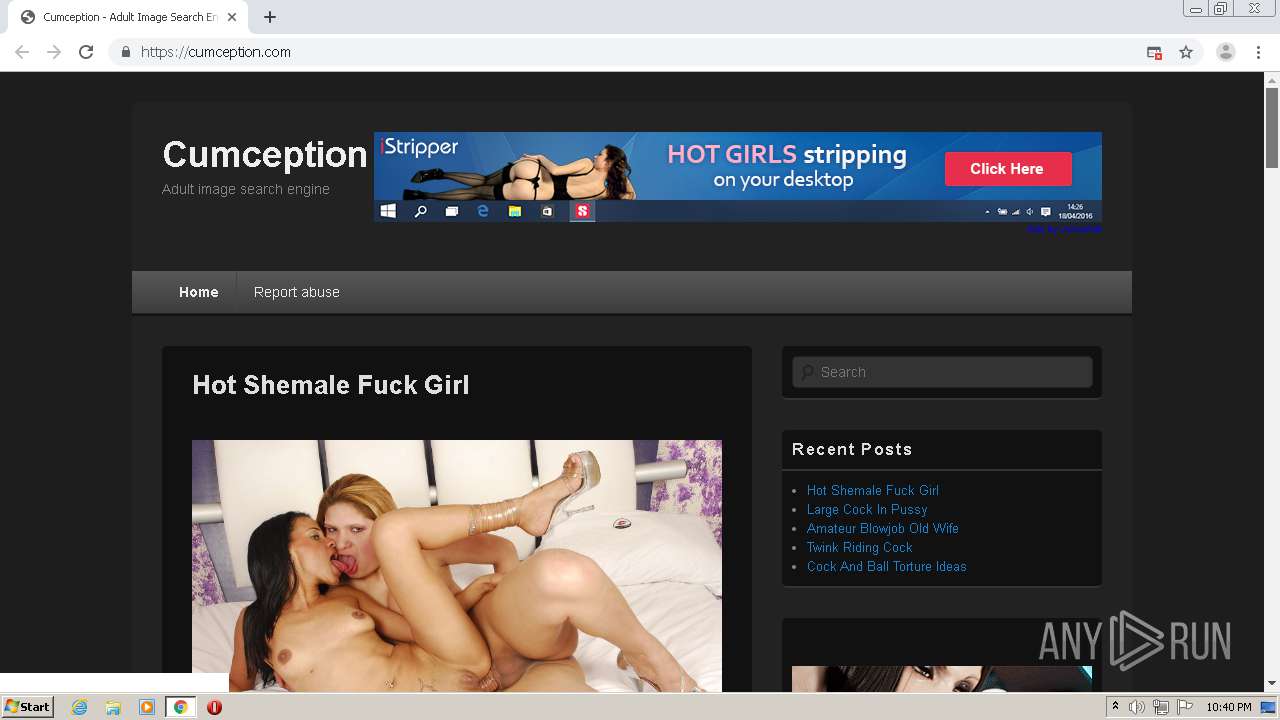
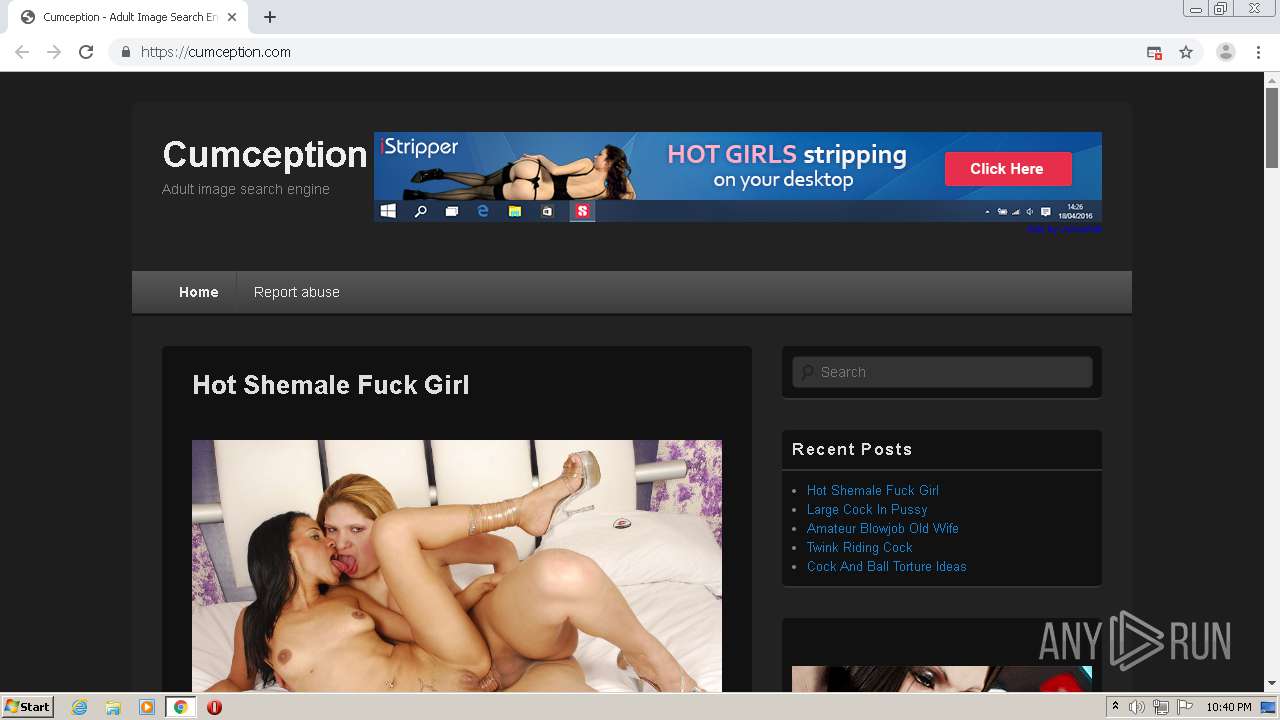
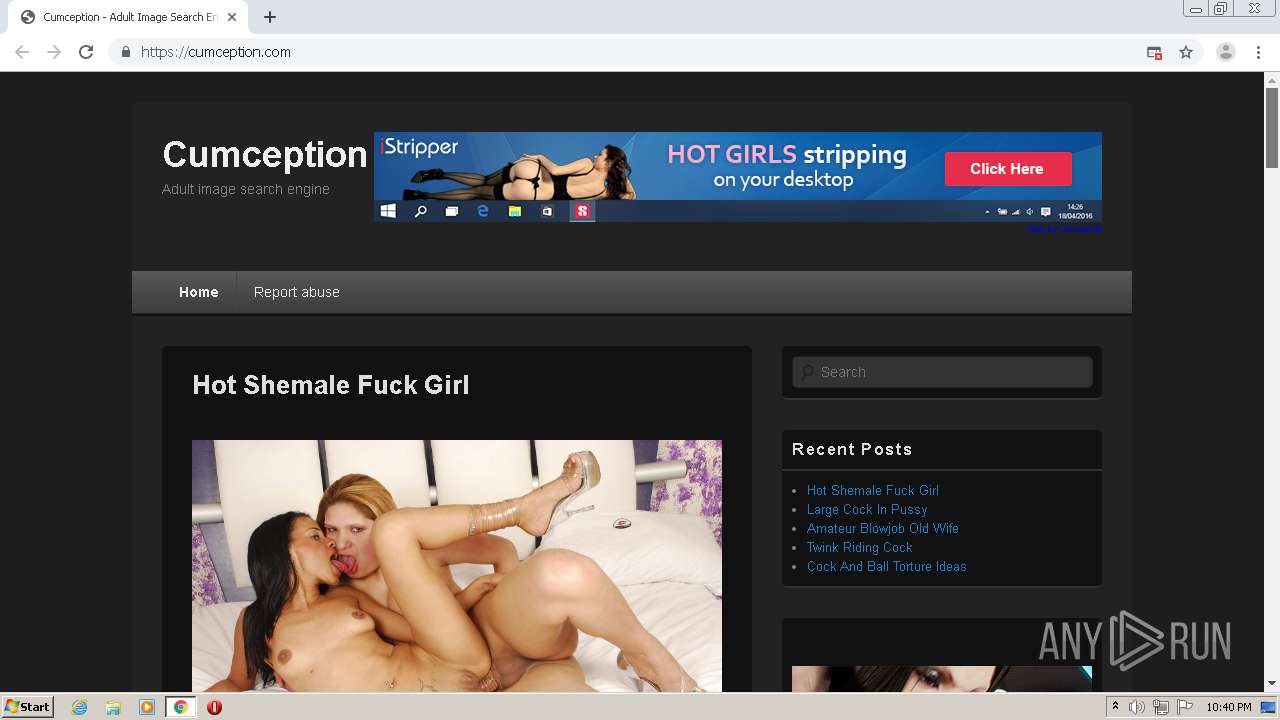
4060 | chrome.exe | GET | 301 | 172.67.137.26:80 | http://cumception.com/ | US | — | — | whitelisted |
4060 | chrome.exe | GET | 304 | 2.16.106.233:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | — | — | whitelisted |
4060 | chrome.exe | GET | 304 | 2.16.106.233:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | — | — | whitelisted |
4060 | chrome.exe | GET | 304 | 2.16.106.233:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | — | — | whitelisted |
4060 | chrome.exe | GET | 304 | 2.16.106.233:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | — | — | whitelisted |
4060 | chrome.exe | GET | 304 | 2.16.106.233:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 57.0 Kb | whitelisted |
4060 | chrome.exe | GET | 302 | 172.217.23.174:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvY2Y1QUFXUjZlVjI5UldyLVpDTFJFcEx6QQ/7719.805.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 523 b | whitelisted |
4060 | chrome.exe | GET | 200 | 2.16.106.233:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 57.0 Kb | whitelisted |
4060 | chrome.exe | GET | 200 | 2.16.106.233:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 57.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4060 | chrome.exe | 172.67.137.26:80 | cumception.com | — | US | unknown |
4060 | chrome.exe | 216.58.207.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
4060 | chrome.exe | 172.217.16.205:443 | accounts.google.com | Google Inc. | US | whitelisted |
4060 | chrome.exe | 172.67.137.26:443 | cumception.com | — | US | unknown |
4060 | chrome.exe | 64.59.92.2:443 | adserver.juicyads.com | MOJOHOST | US | unknown |
4060 | chrome.exe | 13.224.198.2:443 | js.juicyads.com | — | US | unknown |
4060 | chrome.exe | 2.16.106.233:80 | www.download.windowsupdate.com | Akamai International B.V. | — | whitelisted |
4060 | chrome.exe | 172.217.23.97:443 | 4.bp.blogspot.com | Google Inc. | US | whitelisted |
4060 | chrome.exe | 172.217.23.100:443 | www.google.com | Google Inc. | US | whitelisted |
4060 | chrome.exe | 104.17.166.186:443 | c.adsco.re | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cumception.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
js.juicyads.com |
| whitelisted |
adserver.juicyads.com |
| suspicious |
www.download.windowsupdate.com |
| whitelisted |
s.w.org |
| whitelisted |
cdn.adult.xyz |
| suspicious |
4.bp.blogspot.com |
| whitelisted |
redlele.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4060 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
4060 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
4060 | chrome.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |