| File name: | iLividSetupV1.exe |
| Full analysis: | https://app.any.run/tasks/8f87d9be-7f8f-49cd-a7ff-b36dffd47f6b |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2025, 01:47:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 580DD7ECEBEDFAF0C32B327DB9E92CF0 |
| SHA1: | 206C640AE6B401CAA3BC7A2CEBCAECF910885BBB |
| SHA256: | 6DB1B2B0FF8EAF1F3A5A765AF6036A5B982BA10FFE3203C0D247648C4EEAA7E9 |
| SSDEEP: | 24576:T0zI4Lc/77Bhxrt7pCCU3ejexDEJq+LoutpNCbvQ2L2vq:wzI4Lc/77Brrt78CUOjexDEJq+Loutpw |
MALICIOUS
Changes the autorun value in the registry
- iLividSetupV1.exe (PID: 6396)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- iLividSetupV1.exe (PID: 6396)
Executable content was dropped or overwritten
- iLividSetupV1.exe (PID: 6396)
The process creates files with name similar to system file names
- iLividSetupV1.exe (PID: 6396)
Reads security settings of Internet Explorer
- iLividSetupV1.exe (PID: 6396)
There is functionality for taking screenshot (YARA)
- iLividSetupV1.exe (PID: 6396)
INFO
Reads the computer name
- iLividSetupV1.exe (PID: 6396)
Checks supported languages
- iLividSetupV1.exe (PID: 6396)
Create files in a temporary directory
- iLividSetupV1.exe (PID: 6396)
Checks proxy server information
- iLividSetupV1.exe (PID: 6396)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:04:10 12:19:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 25600 |
| InitializedDataSize: | 431104 |
| UninitializedDataSize: | 16896 |
| EntryPoint: | 0x33e9 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Bandoo Media Inc |
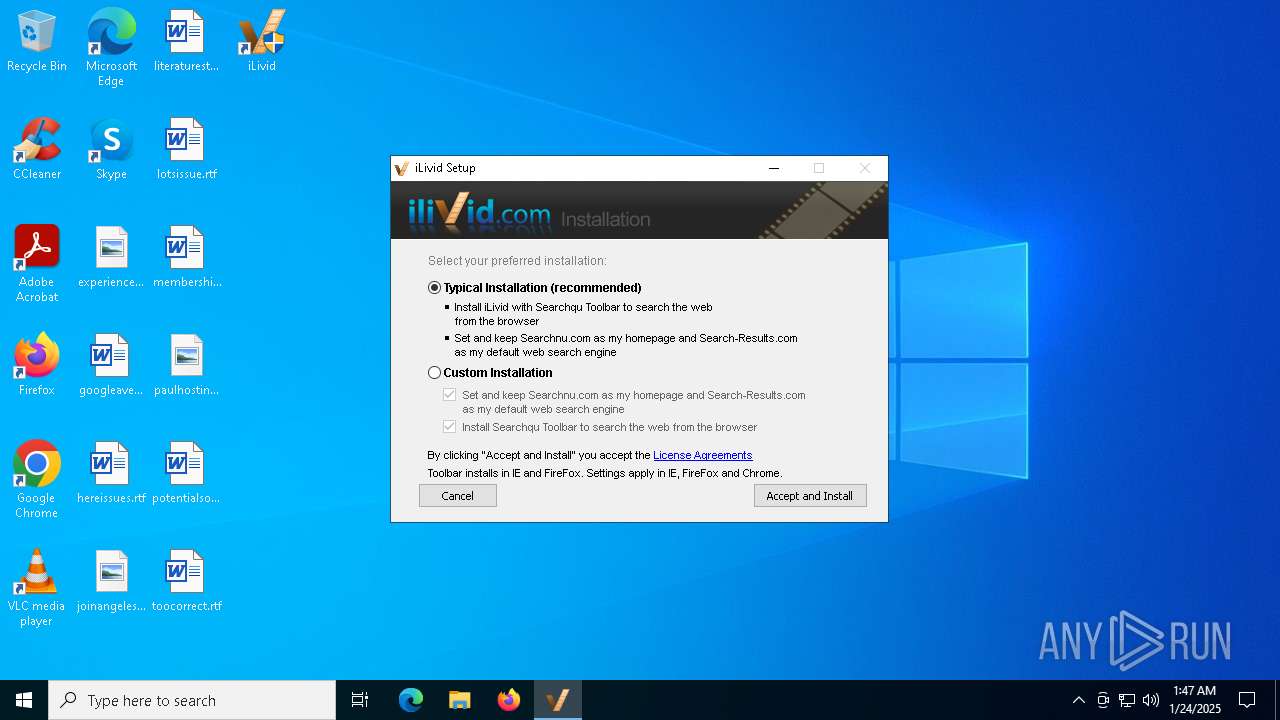
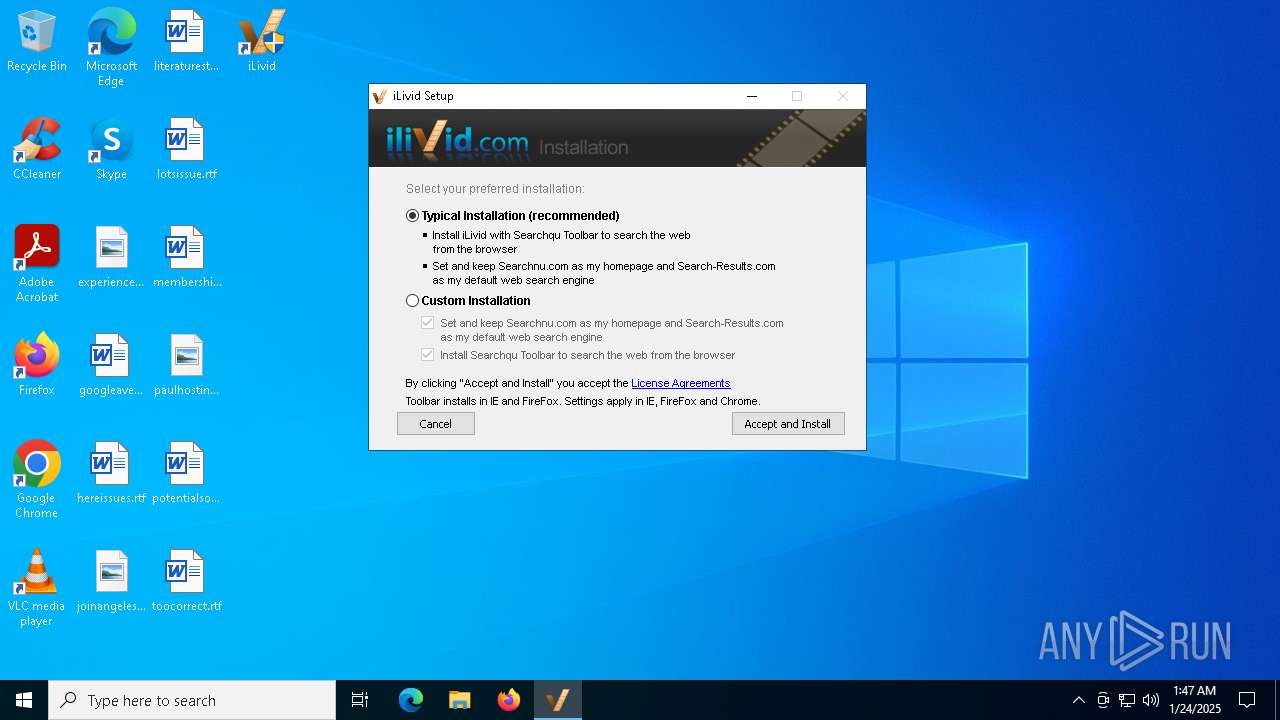
| FileDescription: | iLivid Install |
| FileVersion: | 1.92 |
| LegalCopyright: | Copyright (c) 2011 |
| ProductName: | iLivid |
| ProductVersion: | 1.92 |
Total processes
128
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6240 | "C:\Users\admin\AppData\Local\Temp\iLividSetupV1.exe" | C:\Users\admin\AppData\Local\Temp\iLividSetupV1.exe | — | explorer.exe | |||||||||||
User: admin Company: Bandoo Media Inc Integrity Level: MEDIUM Description: iLivid Install Exit code: 3221226540 Version: 1.92 Modules
| |||||||||||||||
| 6396 | "C:\Users\admin\AppData\Local\Temp\iLividSetupV1.exe" | C:\Users\admin\AppData\Local\Temp\iLividSetupV1.exe | explorer.exe | ||||||||||||
User: admin Company: Bandoo Media Inc Integrity Level: HIGH Description: iLivid Install Version: 1.92 Modules
| |||||||||||||||
Total events
596
Read events
594
Write events
2
Delete events
0
Modification events
| (PID) Process: | (6396) iLividSetupV1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Applications\iLividSetupV1.exe |
| Operation: | write | Name: | IsHostApp |
Value: | |||
| (PID) Process: | (6396) iLividSetupV1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | !iLividOnce |
Value: C:\Users\admin\AppData\Local\Temp\iLividSetupV1.exe | |||
Executable files
4
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6396 | iLividSetupV1.exe | C:\Users\admin\AppData\Local\Temp\nsa57C9.tmp\System.dll | executable | |
MD5:959EA64598B9A3E494C00E8FA793BE7E | SHA256:03CD57AB00236C753E7DDEEE8EE1C10839ACE7C426769982365531042E1F6F8B | |||
| 6396 | iLividSetupV1.exe | C:\Users\admin\AppData\Local\Temp\nsa57C9.tmp\license.txt | text | |
MD5:ADC52E4DF9473983D7C1BBE0F67B2891 | SHA256:46AEFAA17E63EF0FBC4EA1ED1C405BD8D55CE1CC107151404AD79FD78838CD1E | |||
| 6396 | iLividSetupV1.exe | C:\Users\admin\AppData\Local\Temp\nsa57C9.tmp\nsDialogs.dll | executable | |
MD5:F7B92B78F1A00A872C8A38F40AFA7D65 | SHA256:2BEE549B2816BA29F81C47778D9E299C3A364B81769E43D5255310C2BD146D6E | |||
| 6396 | iLividSetupV1.exe | C:\Users\admin\AppData\Local\Temp\nsa57C9.tmp\Helper.dll | executable | |
MD5:99E7831160F750BED15903C959C7EEC0 | SHA256:ABF774EB255196697F35BC148401AE4E8F9A9877E3F59E17F4FCBCDA3F35276A | |||
| 6396 | iLividSetupV1.exe | C:\Users\admin\AppData\Local\Temp\nsa57C9.tmp\UAC.dll | executable | |
MD5:A88BAAD3461D2E9928A15753B1D93FD7 | SHA256:C5AB2926C268257122D0342739E73573D7EEDA34C861BC7A68A02CBC69BD41AF | |||
| 6396 | iLividSetupV1.exe | C:\Users\admin\AppData\Local\Temp\nsa57C9.tmp\modern-header.bmp | image | |
MD5:AAD23E408FC3EF789A35569F04484F3E | SHA256:B336D6CDF362E0A5E4879CB722AFD25ED3F56671C6244FBACDF5A7E8B4F7A05E | |||
| 6396 | iLividSetupV1.exe | C:\Users\Public\Desktop\iLivid.lnk | binary | |
MD5:8944A45377A1FBBAFF2E888AE6452A82 | SHA256:BE85E978AC2930AAFF83659FD2AAABCD5BD46F3D1B1447B0C4D86AA64A9C9AD0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
35
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3364 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6968 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6968 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3700 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 2.21.65.132:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
1176 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |