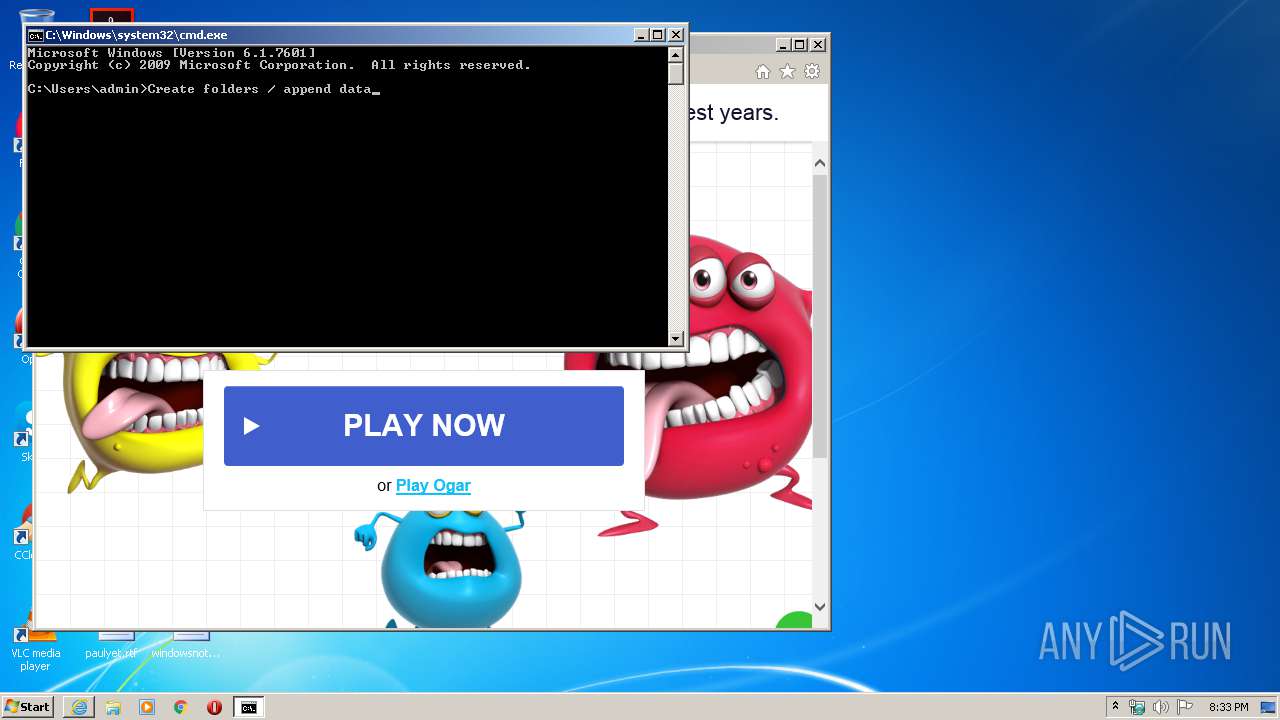
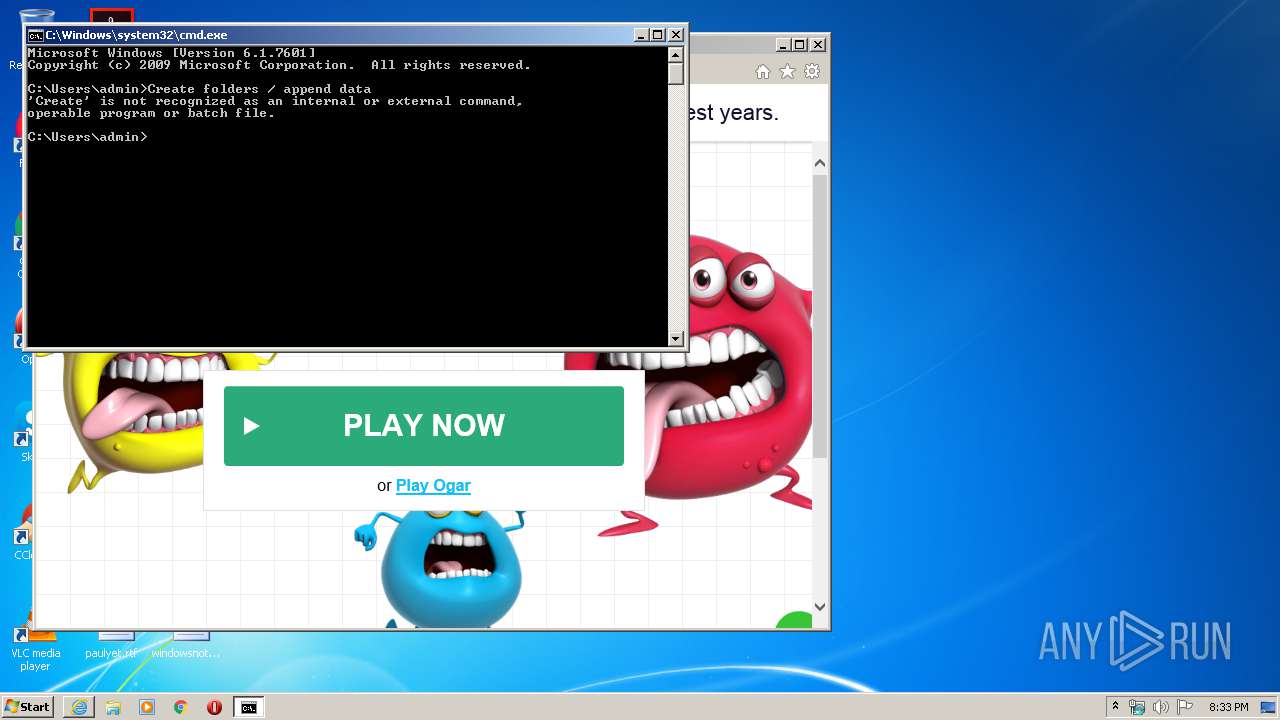
| File name: | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico |
| Full analysis: | https://app.any.run/tasks/07adb6a4-aa37-45c3-bd43-0c34efe3d51d |
| Verdict: | Malicious activity |
| Analysis date: | May 22, 2020, 19:32:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | image/png |
| File info: | PNG image data, 16 x 16, 4-bit colormap, non-interlaced |
| MD5: | 9FB559A691078558E77D6848202F6541 |
| SHA1: | EA13848D33C2C7F4F4BAA39348AEB1DBFAD3DF31 |
| SHA256: | 6D8A01DC7647BC218D003B58FE04049E24A9359900B7E0CEBAE76EDF85B8B914 |
| SSDEEP: | 6:6v/lhPIF6R/C+u1fXNg1XQ3yslRtNO+cKvAElRApGCp:6v/7b/C1fm1ZslRTvAElR47 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 1412)
- iexplore.exe (PID: 1772)
Application launched itself
- iexplore.exe (PID: 1412)
Changes internet zones settings
- iexplore.exe (PID: 1412)
Reads internet explorer settings
- iexplore.exe (PID: 1772)
Reads settings of System Certificates
- iexplore.exe (PID: 1412)
- iexplore.exe (PID: 1772)
Creates files in the user directory
- iexplore.exe (PID: 1772)
Manual execution by user
- cmd.exe (PID: 3636)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1412)
Changes settings of System certificates
- iexplore.exe (PID: 1412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .png | | | Portable Network Graphics (100) |
|---|
EXIF
PNG
| ImageWidth: | 16 |
|---|---|
| ImageHeight: | 16 |
| BitDepth: | 4 |
| ColorType: | Palette |
| Compression: | Deflate/Inflate |
| Filter: | Adaptive |
| Interlace: | Noninterlaced |
| SRGBRendering: | Perceptual |
| Gamma: | 2.2 |
| PixelsPerUnitX: | 3779 |
| PixelsPerUnitY: | 3779 |
| PixelUnits: | meters |
| Palette: | (Binary data 45 bytes, use -b option to extract) |
Composite
| ImageSize: | 16x16 |
|---|---|
| Megapixels: | 0.000256 |
Total processes
45
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1412 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://fastucowhi.pro/out?zoneId=4105252&sId=12&sId2=xhamster.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1772 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1412 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3636 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
3 828
Read events
318
Write events
2 374
Delete events
1 136
Modification events
| (PID) Process: | (1412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3760429826 | |||
| (PID) Process: | (1412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30814319 | |||
| (PID) Process: | (1412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
53
Text files
81
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1772 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab8D2B.tmp | — | |
MD5:— | SHA256:— | |||
| 1772 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar8D2C.tmp | — | |
MD5:— | SHA256:— | |||
| 1772 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\bs3tVu0vPw3xJyyzaAWBQC9DMEzFgG3HNIzJhKhLNMDNhOlPYQzRlSkTNUzVcWxXZYmZQa3bYcjdAewfYgWhYi3jYkWlNmjnMoDpMqyrOsDtcumvcwnxNyyzYAzB1CvDdEXFQGmHcI0JlKkLPMTNQOxPMQ[1].htm | html | |
MD5:— | SHA256:— | |||
| 1772 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CFE86DBBE02D859DC92F1E17E0574EE8_46766FC45507C0B9E264E4C18BC7288B | binary | |
MD5:— | SHA256:— | |||
| 1772 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\ZBA0TQQU.txt | — | |
MD5:— | SHA256:— | |||
| 1772 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E49827401028F7A0F97B5576C77A26CB_7CE95D8DCA26FE957E7BD7D76F353B08 | binary | |
MD5:— | SHA256:— | |||
| 1772 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\landing[1].htm | html | |
MD5:— | SHA256:— | |||
| 1772 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CFE86DBBE02D859DC92F1E17E0574EE8_46766FC45507C0B9E264E4C18BC7288B | der | |
MD5:— | SHA256:— | |||
| 1772 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\4PTIVXZD.txt | — | |
MD5:— | SHA256:— | |||
| 1772 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\ILEOXSA1.txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
61
DNS requests
30
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1772 | iexplore.exe | GET | 302 | 88.85.94.240:80 | http://fastucowhi.pro/out?zoneId=4105252&sId=12&sId2=xhamster.com | NL | — | — | unknown |
1772 | iexplore.exe | GET | 200 | 2.20.189.204:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
1772 | iexplore.exe | POST | 302 | 88.85.94.240:80 | http://fastucowhi.pro/cPGQFRzScTzU9VfWcXmYVZxaVbGcldteZfTg0hxiNjTkklwmMnTocp1qOrTsgtzuNvjwYxyyNzjAEB2CNDTEgFxGJHnIBJ0KPLUM1N6OZPzQRRNSaTkUkV0WTXVYNZRaebEc5dUeaf3gdhNiVjGkMlxmTn1oRpnqerksptFuTvkwlxKyRz0ApB5CYDjEJFGGaH1IlJtKRLnMVNaOQP1QJRoSYTmU0V5WdXWYVZXaMbXcZdkeWfEg1hriSjkkdlKmanko0pyqWrmsptPuRvFwExxyTzjAJBWCaDEE9FXGTHTINJaKRLEMpNoOWPVQRRJSNTEU9VUWVXXYlZaaabmcxdseTfmg1hZiNjEk9lUmZn3oppKqRrGsstxuTv0wRxRyMzEA1BqCaDzERFOGdHyI0JtKJLnMJNyOaPWQQR9SMTzUgV3WNXzYhZhaNbDchdleYfzglhkiNjzkclxmZnmoQp3qYrjsAtwuYvWwYx3yYzWANBjCMDDEMFyGOHDIcJmKcLnMNNyOYPzQ1RvSdTXUQVmWcX0YlZkaPbTcQdxeMfDgUhyiNjTkIlmmenmo9puqZrUsltkuPvTwMx4yOzDAIByCODDEEF | NL | compressed | 1.22 Kb | unknown |
1772 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDEKiK1zGWeAwgAAAAAPr4Q | US | der | 472 b | whitelisted |
1412 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
1772 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
1412 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
1772 | iexplore.exe | GET | 200 | 2.20.189.244:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgTtZk1ppfnYnILmvdkY44lLbw%3D%3D | unknown | der | 527 b | whitelisted |
1772 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEA6O%2BBjVXZc2rpJ%2B516RAgc%3D | US | der | 471 b | whitelisted |
1772 | iexplore.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gts1o1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEAQoXs0GkwDRCAAAAAA%2Bvho%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1772 | iexplore.exe | 172.217.16.196:443 | www.google.com | Google Inc. | US | whitelisted |
1772 | iexplore.exe | 172.217.16.195:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
1772 | iexplore.exe | 23.210.248.44:443 | s7.addthis.com | Akamai International B.V. | NL | whitelisted |
1772 | iexplore.exe | 2.20.189.204:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
1772 | iexplore.exe | 172.217.16.131:443 | www.gstatic.com | Google Inc. | US | whitelisted |
1772 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1772 | iexplore.exe | 23.210.250.213:443 | z.moatads.com | Akamai International B.V. | NL | whitelisted |
1772 | iexplore.exe | 216.58.205.234:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
1412 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1772 | iexplore.exe | 31.13.92.10:443 | graph.facebook.com | Facebook, Inc. | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fastucowhi.pro |
| unknown |
eatcells.com |
| whitelisted |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
s7.addthis.com |
| whitelisted |
www.google.com |
| malicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
z.moatads.com |
| whitelisted |