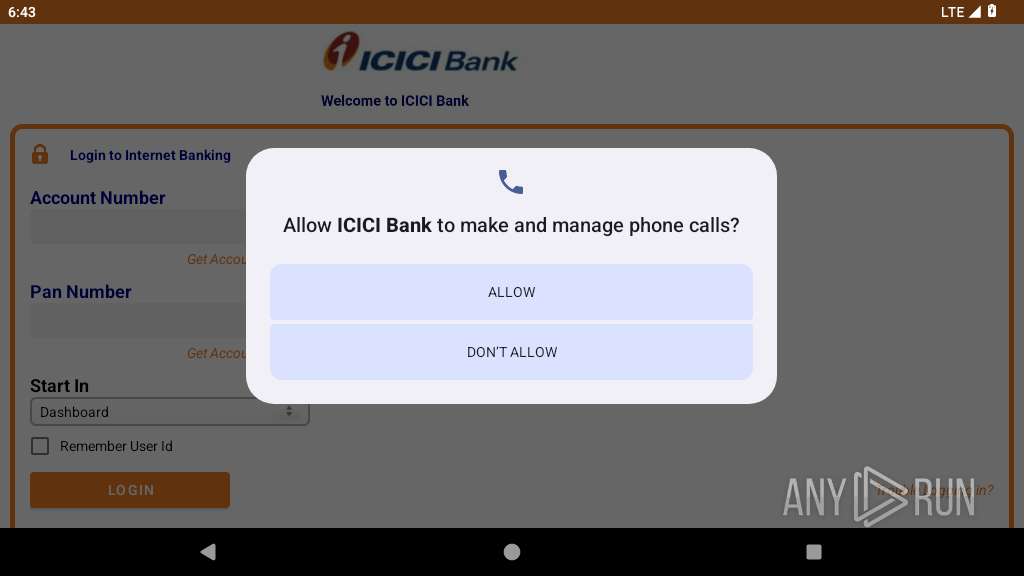
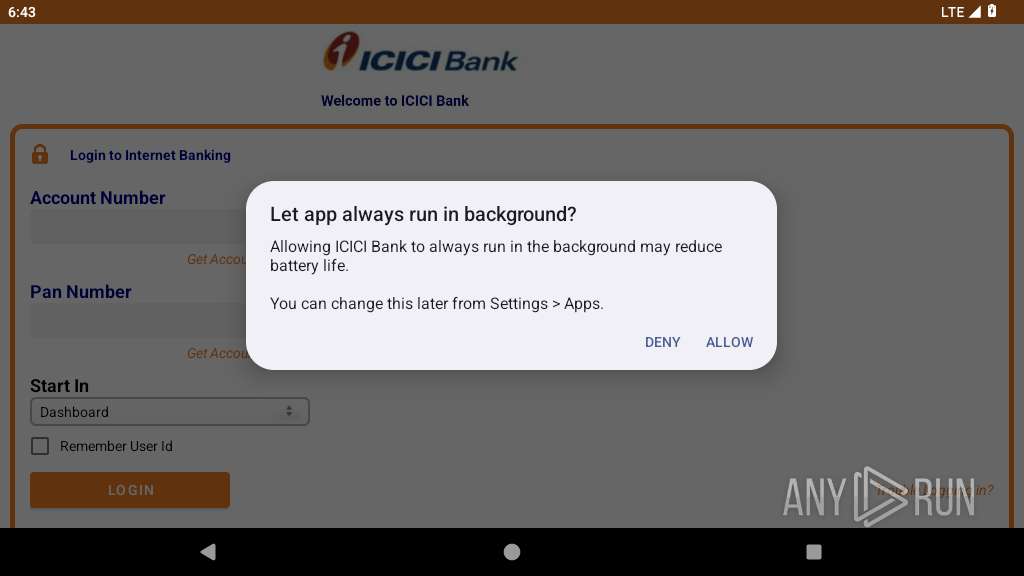
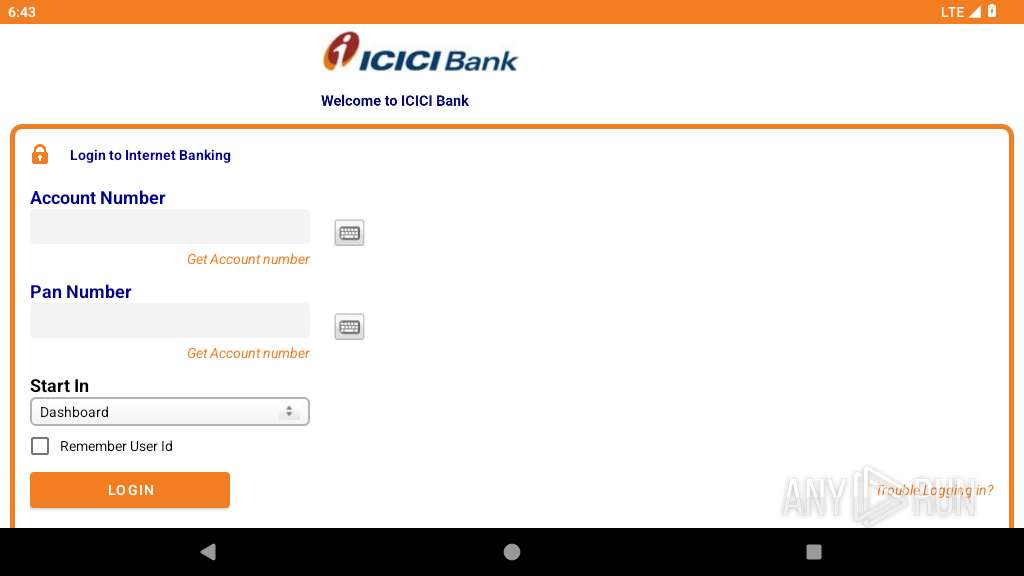
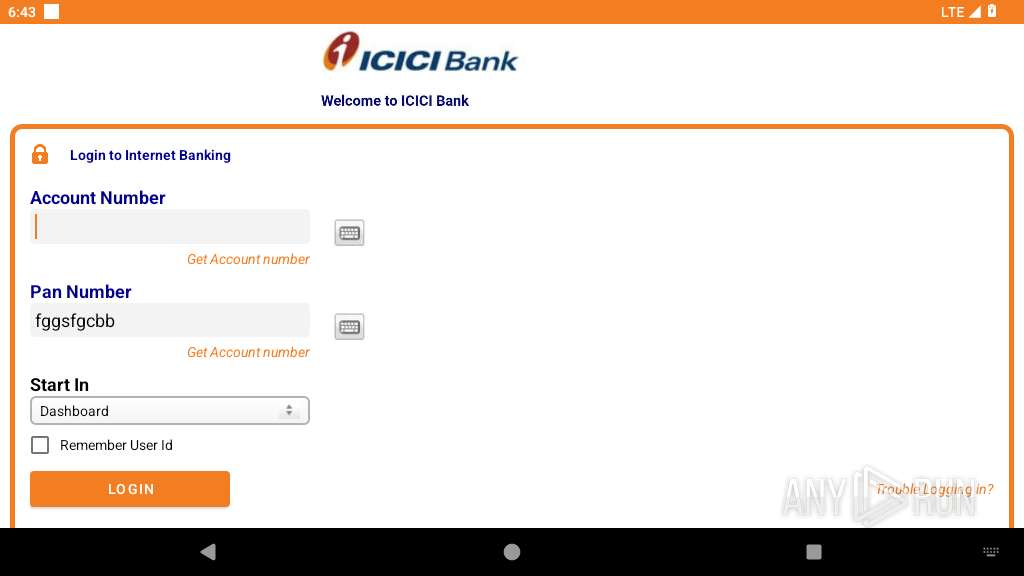
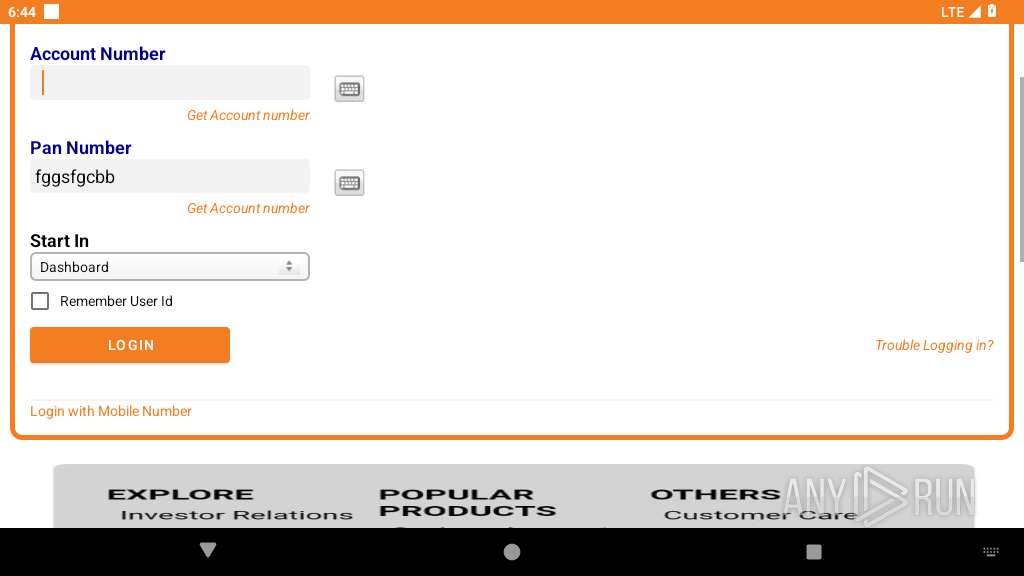
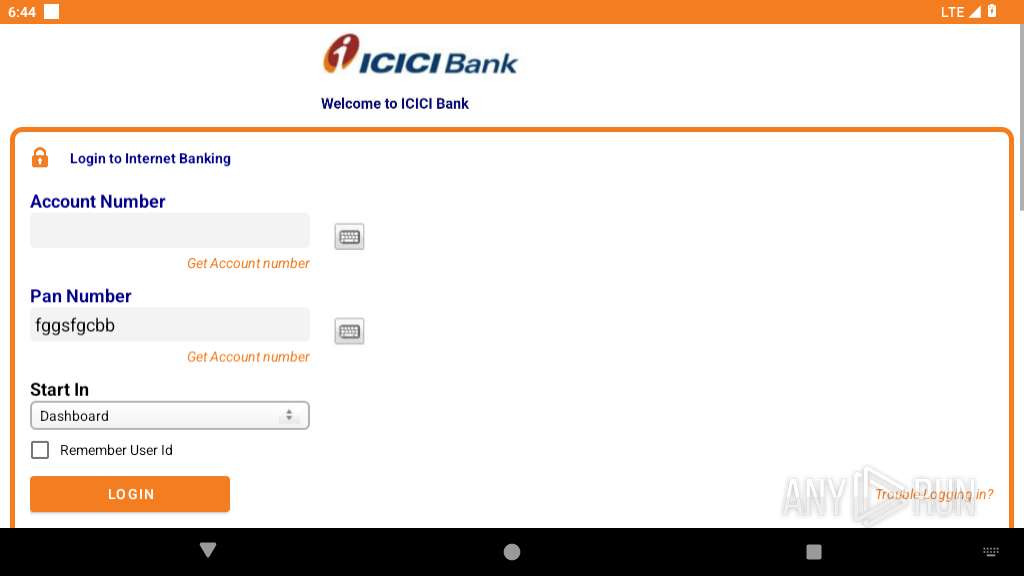
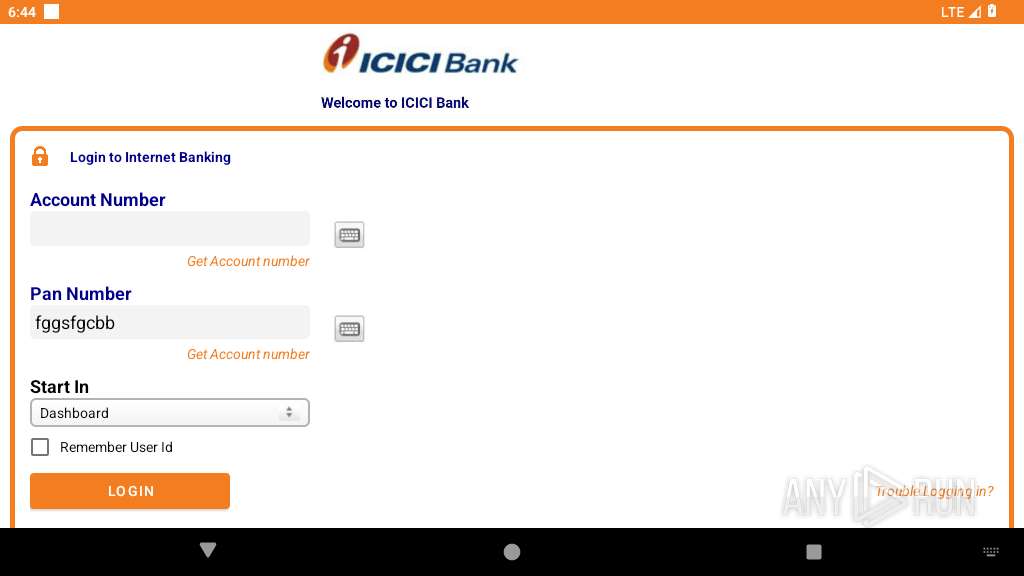
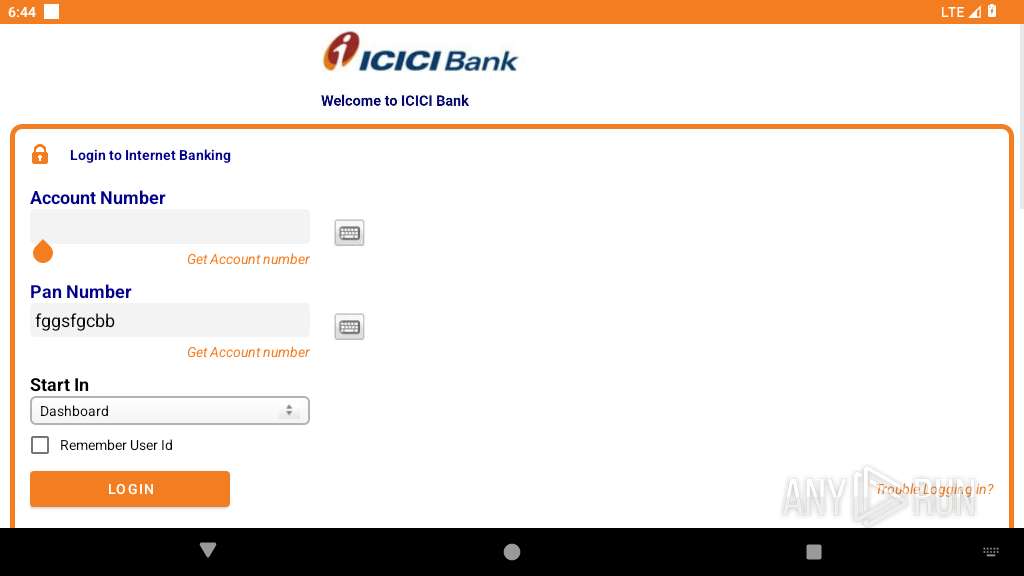
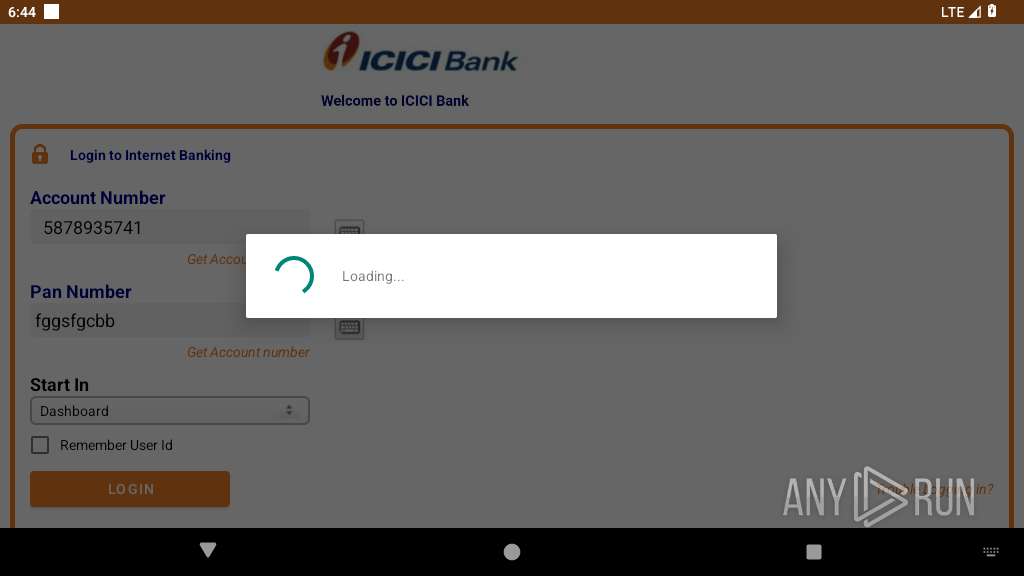
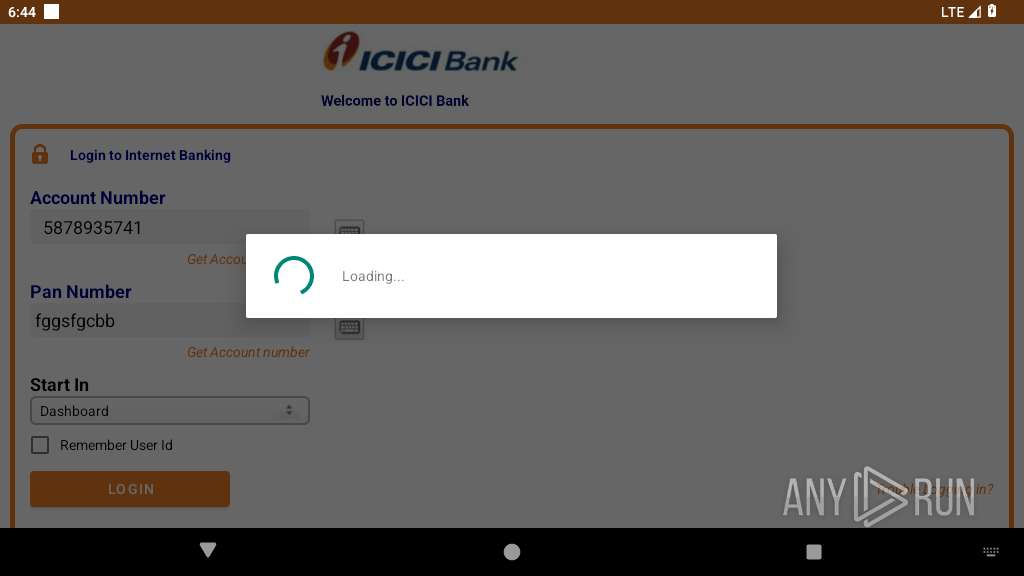
| File name: | base.apk |
| Full analysis: | https://app.any.run/tasks/61ce4a2c-922a-4389-a818-a9a8a26d4d9b |
| Verdict: | Malicious activity |
| Analysis date: | May 03, 2025, 06:43:27 |
| OS: | Android 14 |
| MIME: | application/vnd.android.package-archive |
| File info: | Android package (APK), with classes.dex, with APK Signing Block |
| MD5: | 516AC5E9A7FB0D8AFDA94630DDE6025B |
| SHA1: | 83AF2A2773B5E7F71B516FBA7246EA74584B1436 |
| SHA256: | 6D88070CA5F573ADD0DB19446213959254724F2966873E882A19927EA2475F29 |
| SSDEEP: | 98304:6rSh2zlwblTda2dMvwvrIL4/1dfWanjQdbJej2K1pRMOR6msylLlSWQS7EUbEsrq:++n1G |
MALICIOUS
No malicious indicators.SUSPICIOUS
Acquires a wake lock to keep the device awake
- app_process64 (PID: 2300)
Abuses foreground service for persistence
- app_process64 (PID: 2300)
Checks exemption from battery optimization
- app_process64 (PID: 2300)
Retrieves a list of running services
- app_process64 (PID: 2300)
Updates data in the storage of application settings (SharedPreferences)
- app_process64 (PID: 2300)
Creates a WakeLock to manage power state
- app_process64 (PID: 2300)
INFO
Retrieves the value of a secure system setting
- app_process64 (PID: 2300)
Verifies presence of SIM card
- app_process64 (PID: 2300)
Retrieves data from storage of application settings (SharedPreferences)
- app_process64 (PID: 2300)
Gets the display metrics associated with the device's screen
- app_process64 (PID: 2300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .apk | | | Android Package (62.8) |
|---|---|---|
| .jar | | | Java Archive (17.3) |
| .vym | | | VYM Mind Map (14.9) |
| .zip | | | ZIP compressed archive (4.7) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:02:26 10:38:02 |
| ZipCRC: | 0x6477ddc2 |
| ZipCompressedSize: | 3513945 |
| ZipUncompressedSize: | 9558780 |
| ZipFileName: | classes.dex |
Total processes
126
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
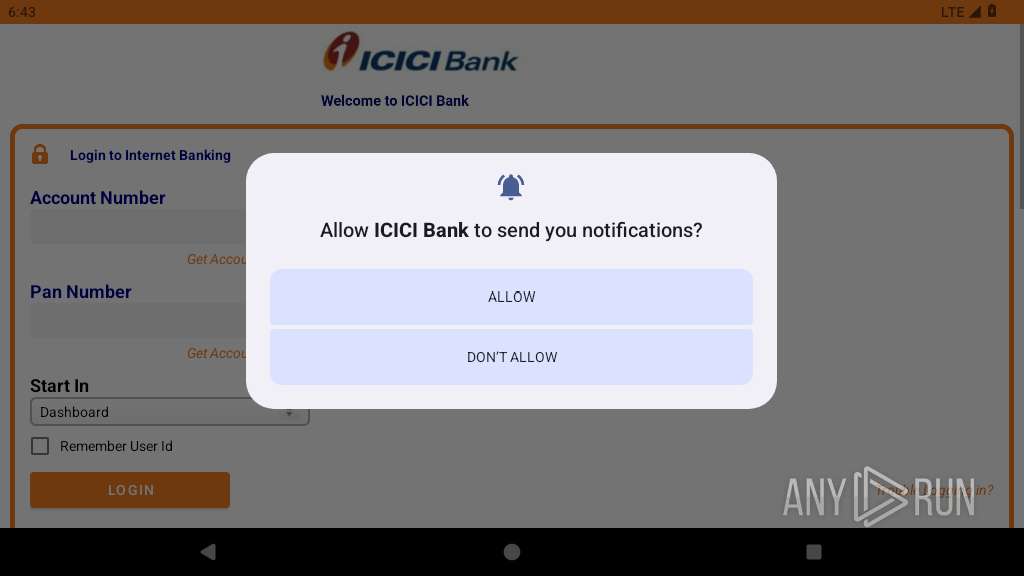
| 2300 | com.oposdf.lkasf | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
20
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2300 | app_process64 | /data/data/com.oposdf.lkasf/no_backup/androidx.work.workdb-journal | binary | |
MD5:— | SHA256:— | |||
| 2300 | app_process64 | /data/data/com.oposdf.lkasf/shared_prefs/FirebaseHeartBeatW0RFRkFVTFRd+MTo5NzY2NDk5Mjc3Mzc6YW5kcm9pZDpkNTBmN2Q4MGM2NjMwOTVhNzNlMWU4.xml | xml | |
MD5:— | SHA256:— | |||
| 2300 | app_process64 | /data/data/com.oposdf.lkasf/no_backup/androidx.work.workdb-wal | binary | |
MD5:— | SHA256:— | |||
| 2300 | app_process64 | /data/data/com.oposdf.lkasf/files/PersistedInstallation9069248639014715056tmp | binary | |
MD5:— | SHA256:— | |||
| 2300 | app_process64 | /data/data/com.oposdf.lkasf/shared_prefs/com.google.firebase.messaging.xml | xml | |
MD5:— | SHA256:— | |||
| 2300 | app_process64 | /data/data/com.oposdf.lkasf/shared_prefs/com.google.android.gms.measurement.prefs.xml | xml | |
MD5:— | SHA256:— | |||
| 2300 | app_process64 | /data/data/com.oposdf.lkasf/files/PersistedInstallation.W0RFRkFVTFRd+MTo5NzY2NDk5Mjc3Mzc6YW5kcm9pZDpkNTBmN2Q4MGM2NjMwOTVhNzNlMWU4.json | binary | |
MD5:— | SHA256:— | |||
| 2300 | app_process64 | /data/data/com.oposdf.lkasf/databases/google_app_measurement_local.db | binary | |
MD5:— | SHA256:— | |||
| 2300 | app_process64 | /data/data/com.oposdf.lkasf/shared_prefs/my_preferences.xml | xml | |
MD5:— | SHA256:— | |||
| 2300 | app_process64 | /data/data/com.oposdf.lkasf/files/PersistedInstallation1173579728588369026tmp | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
28
DNS requests
8
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 142.250.185.163:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
449 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 216.239.35.12:123 | time.android.com | — | — | whitelisted |
— | — | 142.250.186.164:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 142.250.185.163:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 74.125.133.81:443 | staging-remoteprovisioning.sandbox.googleapis.com | GOOGLE | US | whitelisted |
575 | app_process64 | 216.239.35.0:123 | time.android.com | — | — | whitelisted |
2300 | app_process64 | 172.217.16.138:443 | firebaseinstallations.googleapis.com | GOOGLE | US | whitelisted |
2300 | app_process64 | 34.120.160.131:443 | icici-card-a2191-default-rtdb.firebaseio.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
575 | app_process64 | 216.239.35.8:123 | time.android.com | — | — | whitelisted |
575 | app_process64 | 216.239.35.4:123 | time.android.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
connectivitycheck.gstatic.com |
| whitelisted |
www.google.com |
| whitelisted |
time.android.com |
| whitelisted |
google.com |
| whitelisted |
staging-remoteprovisioning.sandbox.googleapis.com |
| whitelisted |
firebaseinstallations.googleapis.com |
| whitelisted |
icici-card-a2191-default-rtdb.firebaseio.com |
| whitelisted |
app-measurement.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |
2300 | app_process64 | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
2300 | app_process64 | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
2300 | app_process64 | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
2300 | app_process64 | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
2300 | app_process64 | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
2300 | app_process64 | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
2300 | app_process64 | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
2300 | app_process64 | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
2300 | app_process64 | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |