| File name: | Cyberghost Latest Version [Cracked] (1).rar |
| Full analysis: | https://app.any.run/tasks/22297505-a682-497a-b1d1-609a2adc62a9 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2018, 09:15:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 8C49252FB9FD5EF3F4644D7A4C96D605 |
| SHA1: | 5758F16F35BD2B6608CED7F3F3F46F3734248CB0 |
| SHA256: | 6D469A023AE548C7B80BEAC3BFCB2E1B7E45D5DBF4C9C943AC02DFF2B9F8E31F |
| SSDEEP: | 393216:zzZZ/HTs8FYJa2QdVwz2XUu17vapO1bHWEcZ/u5S//lkk99QexkcvI8:zznbs8+JB/ziUI7ipO1bH6J/ya5qcA8 |
MALICIOUS
Application was dropped or rewritten from another process
- CyberGhost.exe (PID: 2560)
- CyberGhost.Service.exe (PID: 3112)
- CyberGhost.Service.exe (PID: 2620)
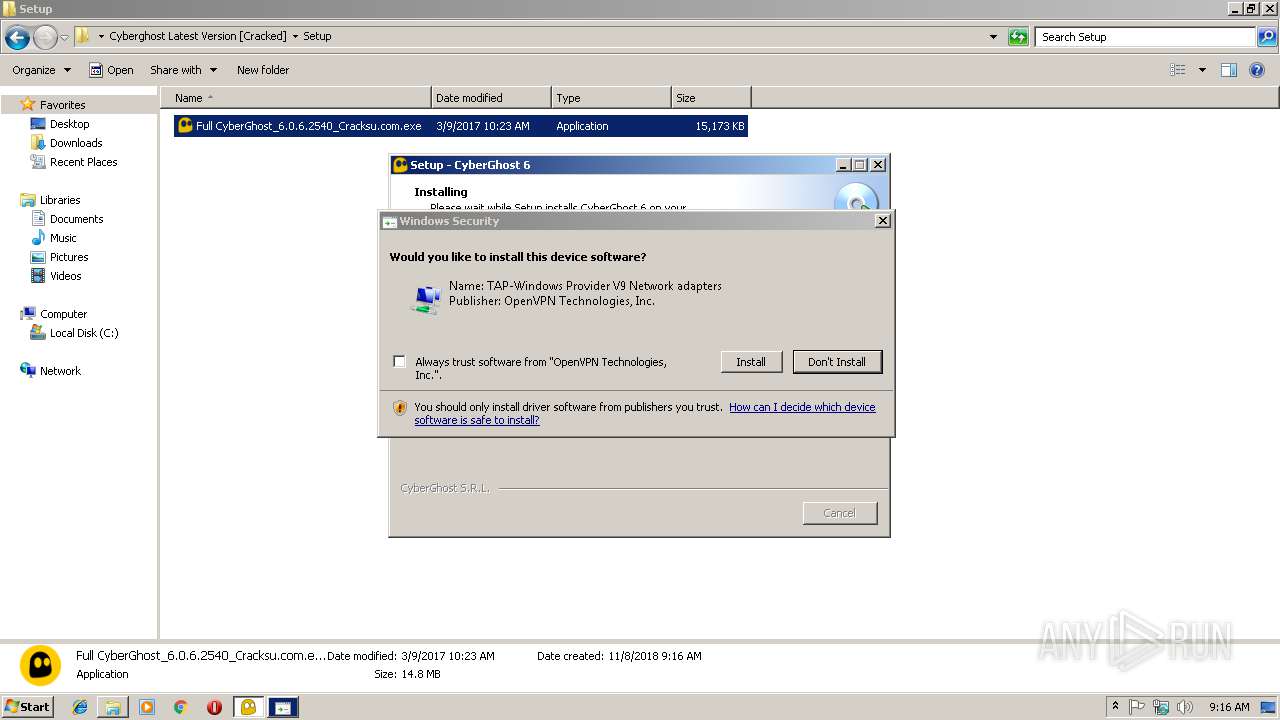
- tap-windows-9.21.2.exe (PID: 2036)
- nsCF15.tmp (PID: 3120)
- nsD06D.tmp (PID: 1880)
- tapinstall.exe (PID: 3988)
- tapinstall.exe (PID: 2304)
- wyUpdate.exe (PID: 1100)
Loads dropped or rewritten executable
- CyberGhost.exe (PID: 2560)
- CyberGhost.Service.exe (PID: 3112)
- CyberGhost.Service.exe (PID: 2620)
- tap-windows-9.21.2.exe (PID: 2036)
Actions looks like stealing of personal data
- CyberGhost.exe (PID: 2560)
- CyberGhost.Service.exe (PID: 2620)
SUSPICIOUS
Reads the Windows organization settings
- Full CyberGhost_6.0.6.2540_Cracksu.com.tmp (PID: 3252)
Executable content was dropped or overwritten
- Full CyberGhost_6.0.6.2540_Cracksu.com.exe (PID: 3028)
- Full CyberGhost_6.0.6.2540_Cracksu.com.tmp (PID: 3252)
- tap-windows-9.21.2.exe (PID: 2036)
- tapinstall.exe (PID: 2304)
- DrvInst.exe (PID: 2232)
- DrvInst.exe (PID: 1256)
Reads Windows owner or organization settings
- Full CyberGhost_6.0.6.2540_Cracksu.com.tmp (PID: 3252)
Creates files in the user directory
- Full CyberGhost_6.0.6.2540_Cracksu.com.tmp (PID: 3252)
Reads Environment values
- CyberGhost.exe (PID: 2560)
- CyberGhost.Service.exe (PID: 2620)
Creates files in the program directory
- CyberGhost.Service.exe (PID: 3112)
- tap-windows-9.21.2.exe (PID: 2036)
Creates or modifies windows services
- CyberGhost.Service.exe (PID: 3112)
- CyberGhost.Service.exe (PID: 2620)
- DrvInst.exe (PID: 2232)
Changes IE settings (feature browser emulation)
- CyberGhost.exe (PID: 2560)
Creates files in the Windows directory
- DrvInst.exe (PID: 2232)
- tapinstall.exe (PID: 2304)
- wyUpdate.exe (PID: 1100)
- DrvInst.exe (PID: 1256)
Starts application with an unusual extension
- tap-windows-9.21.2.exe (PID: 2036)
Creates files in the driver directory
- DrvInst.exe (PID: 2232)
- DrvInst.exe (PID: 1256)
Removes files from Windows directory
- DrvInst.exe (PID: 2232)
- wyUpdate.exe (PID: 1100)
- DrvInst.exe (PID: 1256)
Uses RUNDLL32.EXE to load library
- DrvInst.exe (PID: 2232)
Searches for installed software
- DrvInst.exe (PID: 2232)
INFO
Application was dropped or rewritten from another process
- Full CyberGhost_6.0.6.2540_Cracksu.com.tmp (PID: 3252)
Dropped object may contain Bitcoin addresses
- Full CyberGhost_6.0.6.2540_Cracksu.com.tmp (PID: 3252)
Creates a software uninstall entry
- Full CyberGhost_6.0.6.2540_Cracksu.com.tmp (PID: 3252)
Changes settings of System certificates
- DrvInst.exe (PID: 2232)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3316)
Creates files in the program directory
- Full CyberGhost_6.0.6.2540_Cracksu.com.tmp (PID: 3252)
Creates or modifies windows services
- vssvc.exe (PID: 3316)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
56
Monitored processes
17
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 556 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{0561f7d2-9d83-771a-42a1-0130d5f1db0a} Global\{14bb6aeb-2c96-7be9-0611-9d468aaae145} C:\Windows\System32\DriverStore\Temp\{030a93cc-56b9-45af-4b0e-0927baa3df2b}\oemvista.inf C:\Windows\System32\DriverStore\Temp\{030a93cc-56b9-45af-4b0e-0927baa3df2b}\tap0901.cat | C:\Windows\system32\rundll32.exe | — | DrvInst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1100 | "C:\Program Files\CyberGhost 6\wyUpdate.exe" /justcheck /quickcheck /noerr -server="https://download.cyberghostvpn.com/windows/updates/6/wyserver.wys" | C:\Program Files\CyberGhost 6\wyUpdate.exe | CyberGhost.Service.exe | ||||||||||||
User: SYSTEM Company: wyDay Integrity Level: SYSTEM Description: wyUpdate Exit code: 2 Version: 2.6.18.4 Modules
| |||||||||||||||
| 1256 | DrvInst.exe "2" "211" "ROOT\NET\0000" "C:\Windows\INF\oem4.inf" "oemvista.inf:tap0901:tap0901.ndi:9.0.0.21:tap0901" "6d14a44ff" "000005D0" "000005F0" "000005B8" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1880 | "C:\Users\admin\AppData\Local\Temp\nslCEF4.tmp\nsD06D.tmp" "C:\Program Files\TAP-Windows\bin\tapinstall.exe" install "C:\Program Files\TAP-Windows\driver\OemVista.inf" tap0901 | C:\Users\admin\AppData\Local\Temp\nslCEF4.tmp\nsD06D.tmp | — | tap-windows-9.21.2.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2036 | "C:\Program Files\CyberGhost 6\Data\OpenVPN\tap-windows-9.21.2.exe" /S | C:\Program Files\CyberGhost 6\Data\OpenVPN\tap-windows-9.21.2.exe | CyberGhost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2232 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{547a8cfd-76db-249f-dcfe-2c2858a4c96c}\oemvista.inf" "0" "6d14a44ff" "000005D0" "WinSta0\Default" "000003D0" "208" "c:\program files\tap-windows\driver" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2304 | "C:\Program Files\TAP-Windows\bin\tapinstall.exe" install "C:\Program Files\TAP-Windows\driver\OemVista.inf" tap0901 | C:\Program Files\TAP-Windows\bin\tapinstall.exe | nsD06D.tmp | ||||||||||||
User: admin Company: Windows (R) Win 7 DDK provider Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 6.1.7600.16385 built by: WinDDK Modules
| |||||||||||||||
| 2560 | "C:\Program Files\CyberGhost 6\CyberGhost.exe" /install | C:\Program Files\CyberGhost 6\CyberGhost.exe | Full CyberGhost_6.0.6.2540_Cracksu.com.tmp | ||||||||||||
User: admin Company: CyberGhost S.R.L. Integrity Level: HIGH Description: CyberGhost Exit code: 0 Version: 6.0.6.2540 Modules
| |||||||||||||||
| 2620 | "C:\Program Files\CyberGhost 6\CyberGhost.Service.exe" | C:\Program Files\CyberGhost 6\CyberGhost.Service.exe | services.exe | ||||||||||||
User: SYSTEM Company: CyberGhost S.R.L Integrity Level: SYSTEM Description: CyberGhost Service Exit code: 0 Version: 6.0.6.2540 Modules
| |||||||||||||||
| 3028 | "C:\Users\admin\Desktop\Cyberghost Latest Version [Cracked]\Setup\Full CyberGhost_6.0.6.2540_Cracksu.com.exe" | C:\Users\admin\Desktop\Cyberghost Latest Version [Cracked]\Setup\Full CyberGhost_6.0.6.2540_Cracksu.com.exe | explorer.exe | ||||||||||||
User: admin Company: CyberGhost S.R.L. Integrity Level: HIGH Description: CyberGhost 6 Exit code: 0 Version: 6.0.4 Modules
| |||||||||||||||
Total events
1 475
Read events
1 068
Write events
397
Delete events
10
Modification events
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Cyberghost Latest Version [Cracked] (1).rar | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
65
Suspicious files
31
Text files
725
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3984.8149\Cyberghost Latest Version [Cracked]\Setup\Full CyberGhost_6.0.6.2540_Cracksu.com.exe | — | |
MD5:— | SHA256:— | |||
| 3252 | Full CyberGhost_6.0.6.2540_Cracksu.com.tmp | C:\Program Files\CyberGhost 6\is-ED6BE.tmp | — | |
MD5:— | SHA256:— | |||
| 3252 | Full CyberGhost_6.0.6.2540_Cracksu.com.tmp | C:\Program Files\CyberGhost 6\is-SG843.tmp | — | |
MD5:— | SHA256:— | |||
| 3252 | Full CyberGhost_6.0.6.2540_Cracksu.com.tmp | C:\Program Files\CyberGhost 6\is-P3MJM.tmp | — | |
MD5:— | SHA256:— | |||
| 3252 | Full CyberGhost_6.0.6.2540_Cracksu.com.tmp | C:\Program Files\CyberGhost 6\is-KM36T.tmp | — | |
MD5:— | SHA256:— | |||
| 3252 | Full CyberGhost_6.0.6.2540_Cracksu.com.tmp | C:\Program Files\CyberGhost 6\is-QKV16.tmp | — | |
MD5:— | SHA256:— | |||
| 3252 | Full CyberGhost_6.0.6.2540_Cracksu.com.tmp | C:\Program Files\CyberGhost 6\is-0027Q.tmp | — | |
MD5:— | SHA256:— | |||
| 3252 | Full CyberGhost_6.0.6.2540_Cracksu.com.tmp | C:\Program Files\CyberGhost 6\is-FMIP7.tmp | — | |
MD5:— | SHA256:— | |||
| 3252 | Full CyberGhost_6.0.6.2540_Cracksu.com.tmp | C:\Program Files\CyberGhost 6\is-RQG1I.tmp | — | |
MD5:— | SHA256:— | |||
| 3252 | Full CyberGhost_6.0.6.2540_Cracksu.com.tmp | C:\Program Files\CyberGhost 6\is-S7V1E.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
4
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1100 | wyUpdate.exe | GET | 301 | 104.20.63.85:80 | http://wyday.com/files/wyupdate/updates/client.net4.wys | US | html | 162 b | shared |
1100 | wyUpdate.exe | GET | 404 | 108.177.127.82:80 | http://wyupdate.googlecode.com/files/client.net4.wys | US | html | 1.54 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1100 | wyUpdate.exe | 104.20.27.8:443 | download.cyberghostvpn.com | Cloudflare Inc | US | shared |
1100 | wyUpdate.exe | 108.177.127.82:80 | wyupdate.googlecode.com | Google Inc. | US | whitelisted |
1100 | wyUpdate.exe | 104.20.63.85:80 | wyday.com | Cloudflare Inc | US | shared |
1100 | wyUpdate.exe | 104.20.63.85:443 | wyday.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.cyberghostvpn.com |
| whitelisted |
wyupdate.googlecode.com |
| whitelisted |
wyday.com |
| unknown |
Threats
Process | Message |
|---|---|
CyberGhost.Service.exe | Checking for Update on https://download.cyberghostvpn.com/windows/updates/6/
|