| URL: | https://app.adjust.com/jsr?url=https%3A%2F%2Fpzwv.adj.st%2F%3Fc%3Dom%26s%3Dmv%26bid%3D47322%26t%3D3%26adjust_t%3Dn9s5k1_9du0cf%26adjust_campaign%3Dcrm_bra_mix_gro_aut_%7B%7Bcampaign.%24%7Bname%7D%7D%7D_%7B%7Bcampaign.%24%7Bapi_id%7D%7D%7D_ct-AbandonedCartLocalshops%26adjust_deeplink%3Dtalabat%253A%252F%252F%253Fc%253Dom%2526s%253Dmv%2526bid%253D47322%2526t%253D3%26adjust_redirect%3Dhttp%3A%2F%2F1vd6d6.gygoxw.zidoragroup.com%2Fcol%2FQklfZGFuZV9wcm9kdWt0X21vaGl0b0BscHBzYS5jb20= |
| Full analysis: | https://app.any.run/tasks/3eae668f-b0b7-46c5-b4d7-2343b84870a4 |
| Verdict: | Malicious activity |
| Analysis date: | December 08, 2023, 07:55:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C8486BCE4AEFDA8E90D455BC8CA849C6 |
| SHA1: | 3030F3AEF9EFE95BD48F85BA73D47299240C1E96 |
| SHA256: | 6D44341692417831E39F8EFF7B4987C5E97E0343117018303A8F92BA474CEC3A |
| SSDEEP: | 12:2NXrny8IFtSSKy0ShRSRSM75fiSIzVvVXZq8sMd2hXFuvSY:2hrnyi2KfbIXZhvr |
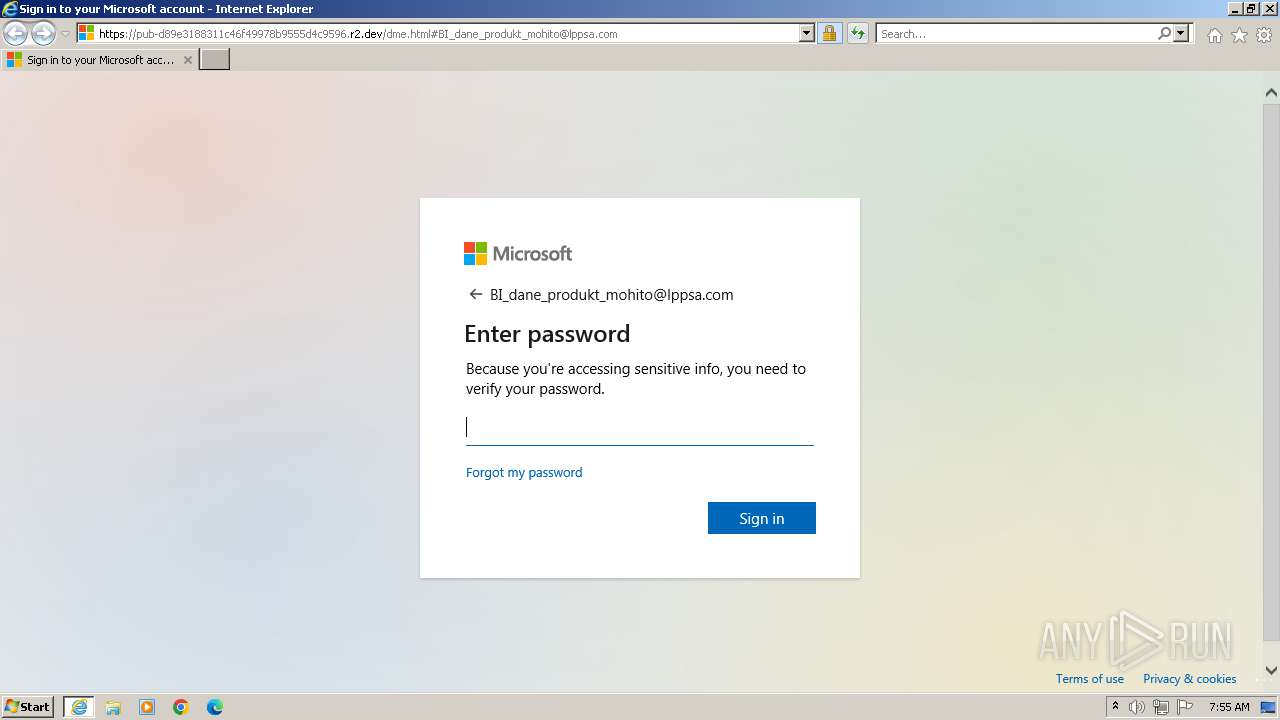
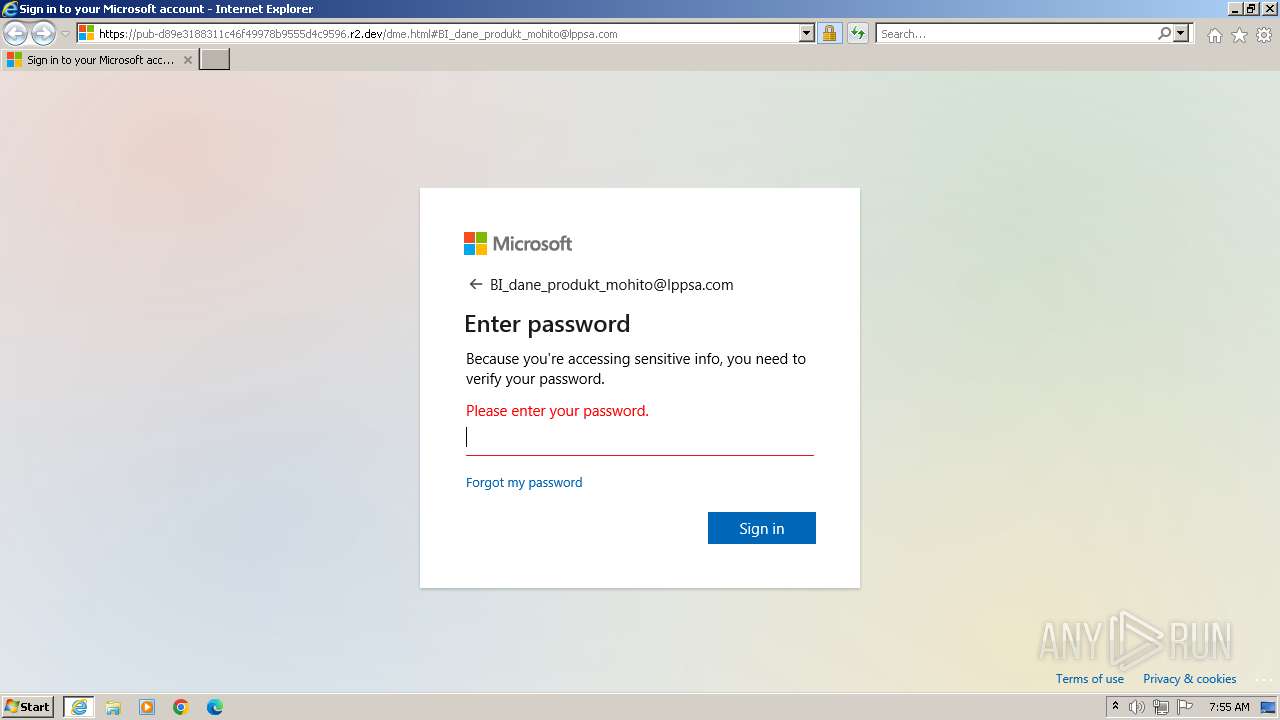
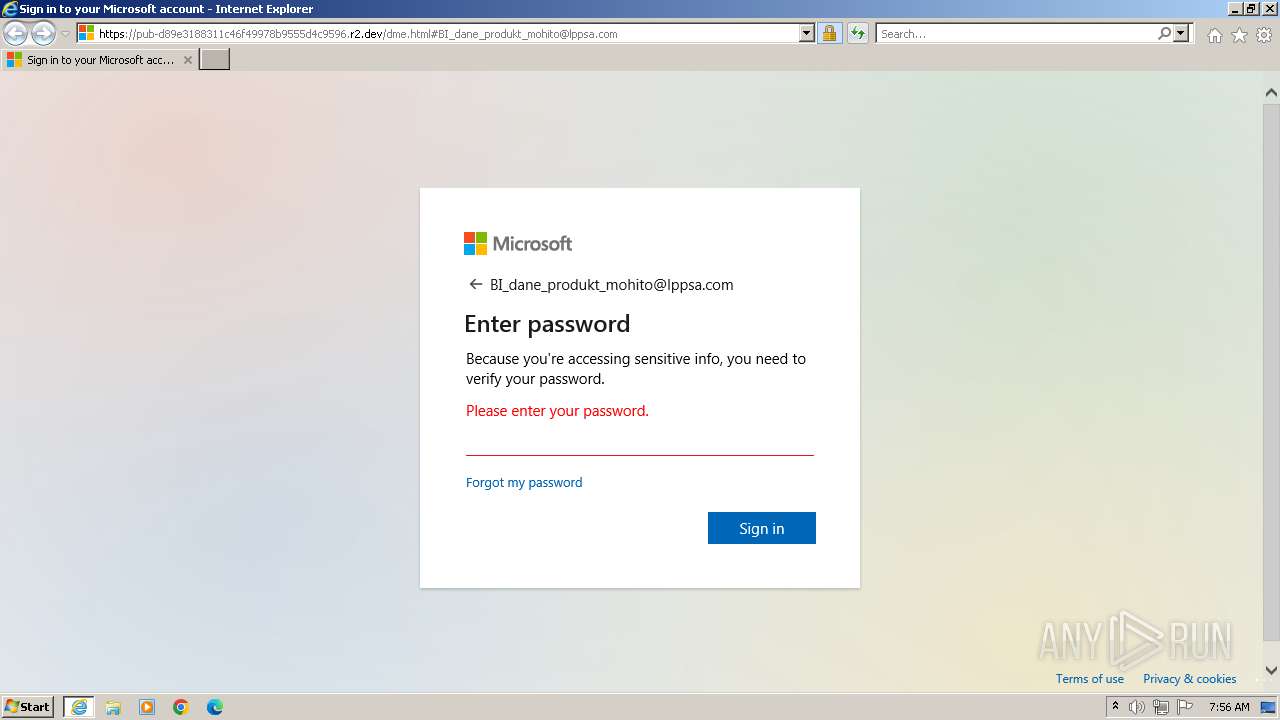
MALICIOUS
PHISHING has been detected (SURICATA)
- iexplore.exe (PID: 2136)
SUSPICIOUS
No suspicious indicators.INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3140)
Application launched itself
- iexplore.exe (PID: 280)
Checks supported languages
- wmpnscfg.exe (PID: 3140)
Reads the computer name
- wmpnscfg.exe (PID: 3140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://app.adjust.com/jsr?url=https%3A%2F%2Fpzwv.adj.st%2F%3Fc%3Dom%26s%3Dmv%26bid%3D47322%26t%3D3%26adjust_t%3Dn9s5k1_9du0cf%26adjust_campaign%3Dcrm_bra_mix_gro_aut_%7B%7Bcampaign.%24%7Bname%7D%7D%7D_%7B%7Bcampaign.%24%7Bapi_id%7D%7D%7D_ct-AbandonedCartLocalshops%26adjust_deeplink%3Dtalabat%253A%252F%252F%253Fc%253Dom%2526s%253Dmv%2526bid%253D47322%2526t%253D3%26adjust_redirect%3Dhttp%3A%2F%2F1vd6d6.gygoxw.zidoragroup.com%2Fcol%2FQklfZGFuZV9wcm9kdWt0X21vaGl0b0BscHBzYS5jb20=" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2136 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:280 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3140 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
19 298
Read events
19 236
Write events
60
Delete events
2
Modification events
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
33
Text files
40
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:78E3A966B5FAA27C3073ADC363B8BE82 | SHA256:5CD71DE775B6BA47F01301771064702CDD271DDA91F36264A120A96C63015250 | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:04E3CB76C03148406ABD6F0093C65150 | SHA256:53DC64FF714633595CA3190E5ADE98C044239C91A6B8AB9123FD71D293B569D7 | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\jsr[1].htm | html | |
MD5:A6288FD887C3CC8B1534264016ACCD54 | SHA256:139F1EEEFF6E29B6AEF1E921205208054EE77286594F0463E592E5178565DD12 | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:E321789A8805CE063FED38452ADB1416 | SHA256:F47D2D9352ADB4F583BE3CFA161DA3FA159E672022AD998F3A90E125DDD20F97 | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:9DEB21C91F8E76E343225E64B08E8C46 | SHA256:DC2E5DBCB0BEBA7458DD266643623EBBC35F2F29D434DB5D6BA09AAAF280ED26 | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E573CDF4C6D731D56A665145182FD759_A6455B0223770C2BA5F3DCA84EF3C959 | binary | |
MD5:B1FCC5B2783647E33FBBC0EC7C452C55 | SHA256:AEE1D09B5A4A9188C07CE21B8B92CD66D2112DBEC6564FAB83A170506E4ADF47 | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:5983406ADC7E1FA9FE11C22E74B3C552 | SHA256:CD04455D33D85CE0D68C1108ED8193A8F7817899C44777563BF952AF8EEC7AC0 | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\59D76868C250B3240414CE3EFBB12518_DD401B9C1CC62D165027BC54294F7773 | binary | |
MD5:31B8ACC6D755FE0F6A6F5D597C5DBC46 | SHA256:3EF675E8775537F72B09D8B64963AB06E4610E61A46ACE993BAEA125A83501CE | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:BD380F6EAA226965782AE1F0C28722A0 | SHA256:9AEFE6623A95884D0E9368EA4C236498588CF9A08860B1C44BE550966B889ABC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
48
DNS requests
22
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2136 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a88ccd45ad45c010 | unknown | compressed | 4.66 Kb | unknown |
2136 | iexplore.exe | GET | 200 | 23.212.210.158:80 | http://x2.c.lencr.org/ | unknown | binary | 300 b | unknown |
2136 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
2136 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | unknown |
2136 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | binary | 2.18 Kb | unknown |
2136 | iexplore.exe | GET | 200 | 184.24.77.54:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgQHQnKF7stKk4CO2ecPxyVCHA%3D%3D | unknown | binary | 503 b | unknown |
280 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 312 b | unknown |
2136 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7c0985578a653cb5 | unknown | compressed | 4.66 Kb | unknown |
2136 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
2136 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEAkraU94iP40ugbP0X2dzWg%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2136 | iexplore.exe | 185.151.204.11:443 | app.adjust.com | Adjust GmbH | US | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2136 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2136 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2136 | iexplore.exe | 185.151.204.203:443 | pzwv.adj.st | Adjust GmbH | US | unknown |
2136 | iexplore.exe | 192.185.41.212:80 | 1vd6d6.gygoxw.zidoragroup.com | UNIFIEDLAYER-AS-1 | US | unknown |
2136 | iexplore.exe | 104.18.2.35:443 | pub-d89e3188311c46f49978b9555d4c9596.r2.dev | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
app.adjust.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
pzwv.adj.st |
| unknown |
1vd6d6.gygoxw.zidoragroup.com |
| unknown |
pub-d89e3188311c46f49978b9555d4c9596.r2.dev |
| malicious |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
aadcdn.msauth.net |
| whitelisted |
www.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2136 | iexplore.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Possible Public R2.dev Bucket Abuse to Phishing in TLS (Greatness) |
1080 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
2136 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
2136 | iexplore.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2136 | iexplore.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2136 | iexplore.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2136 | iexplore.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |