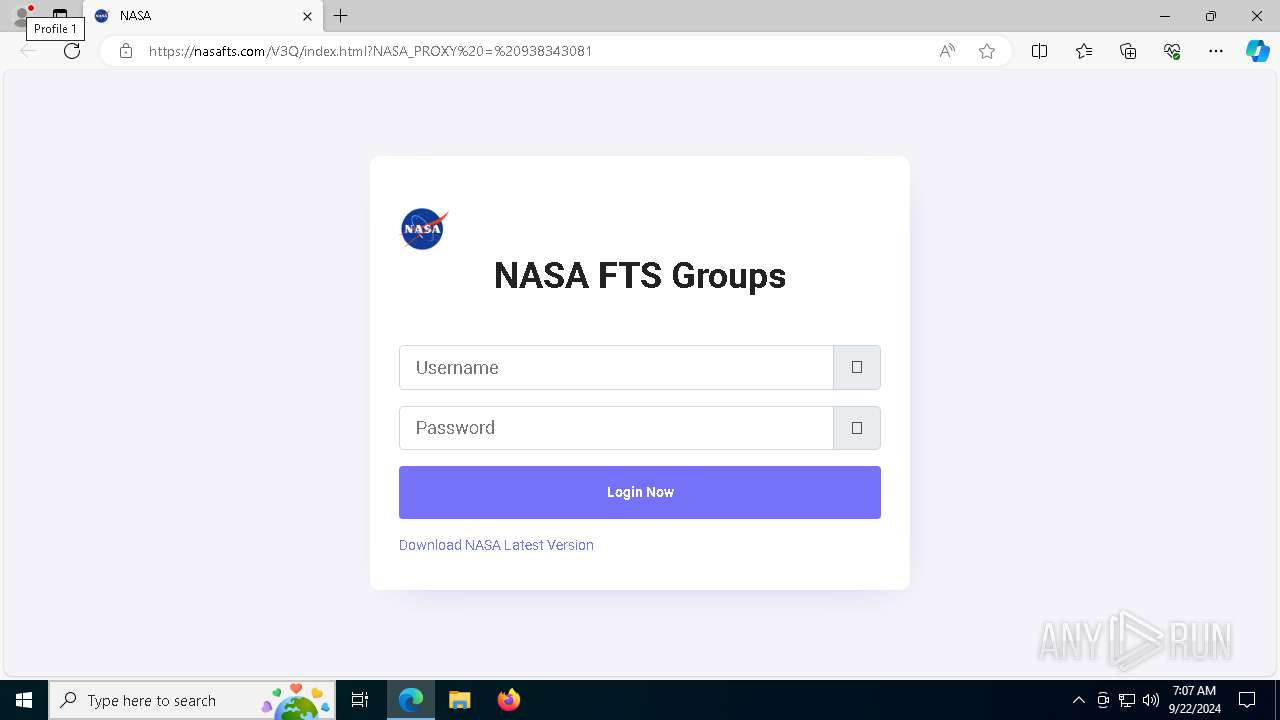
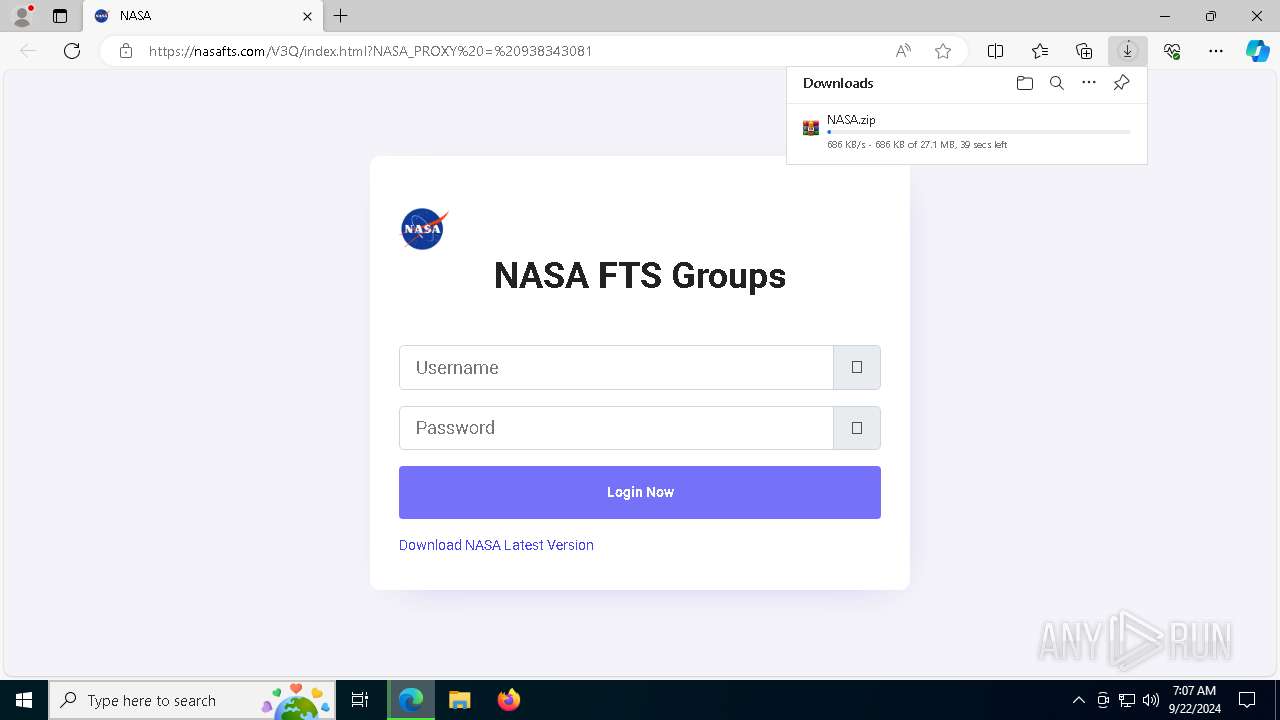
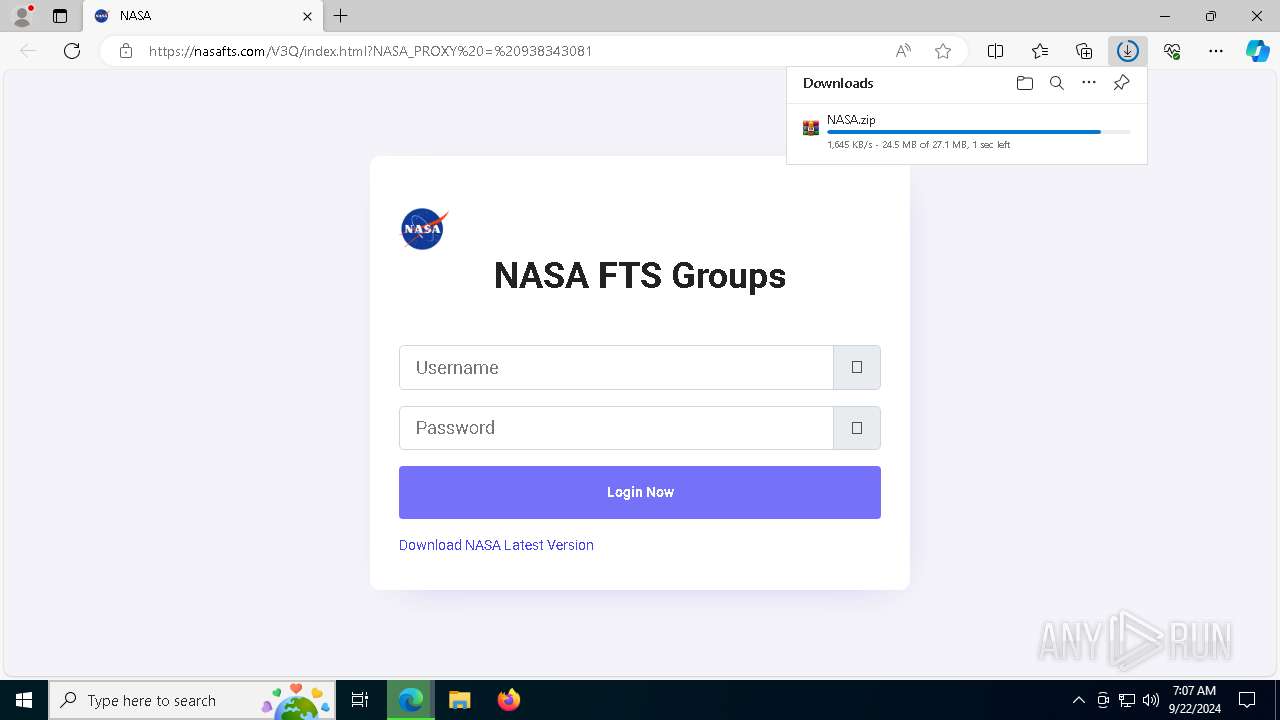
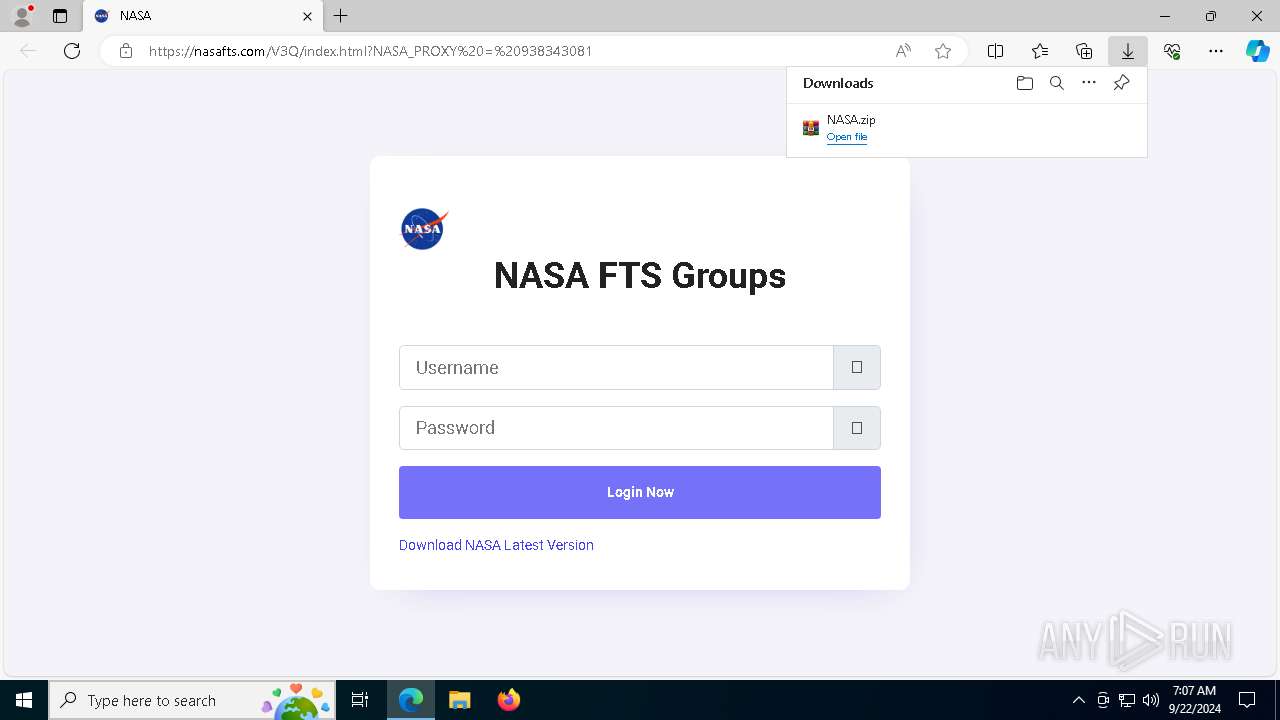
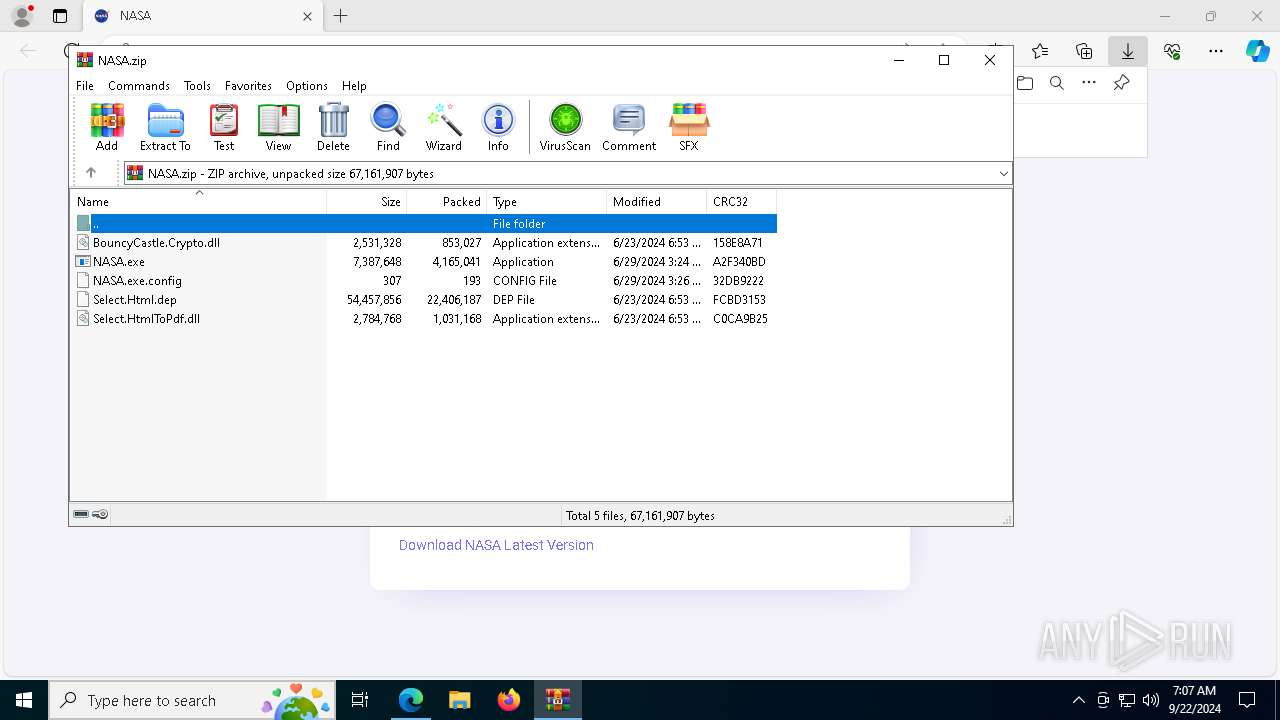
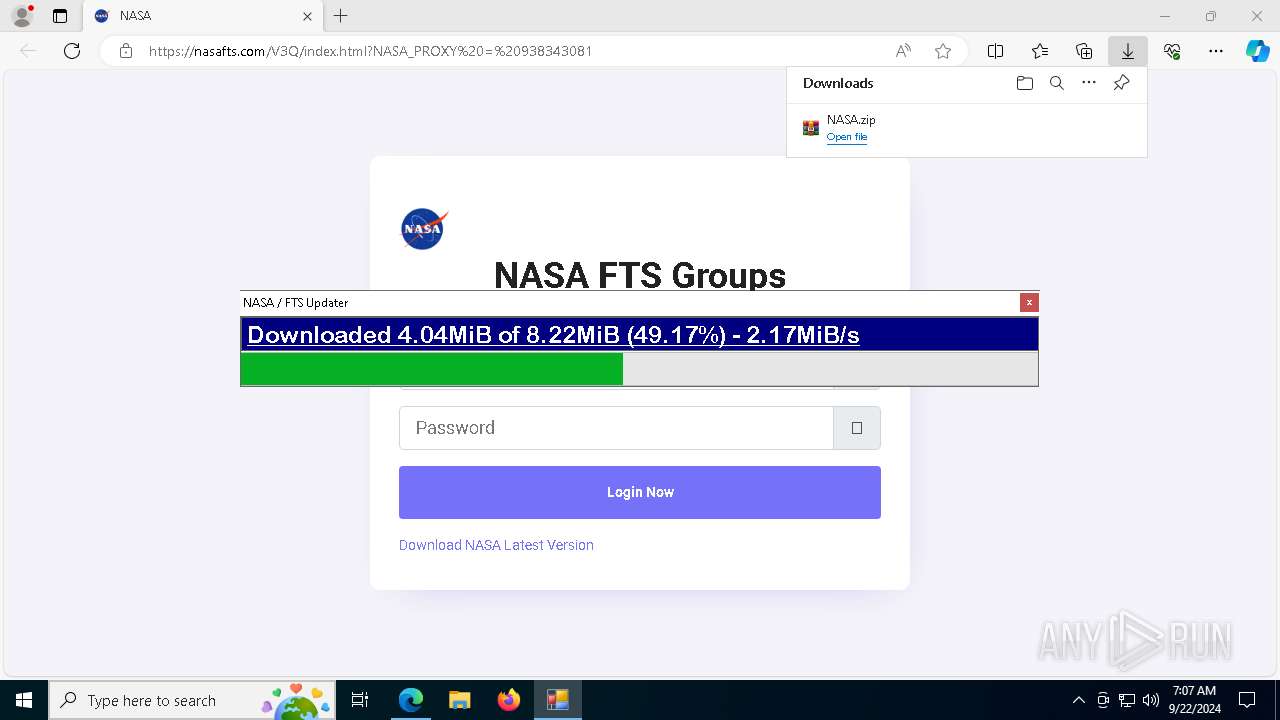
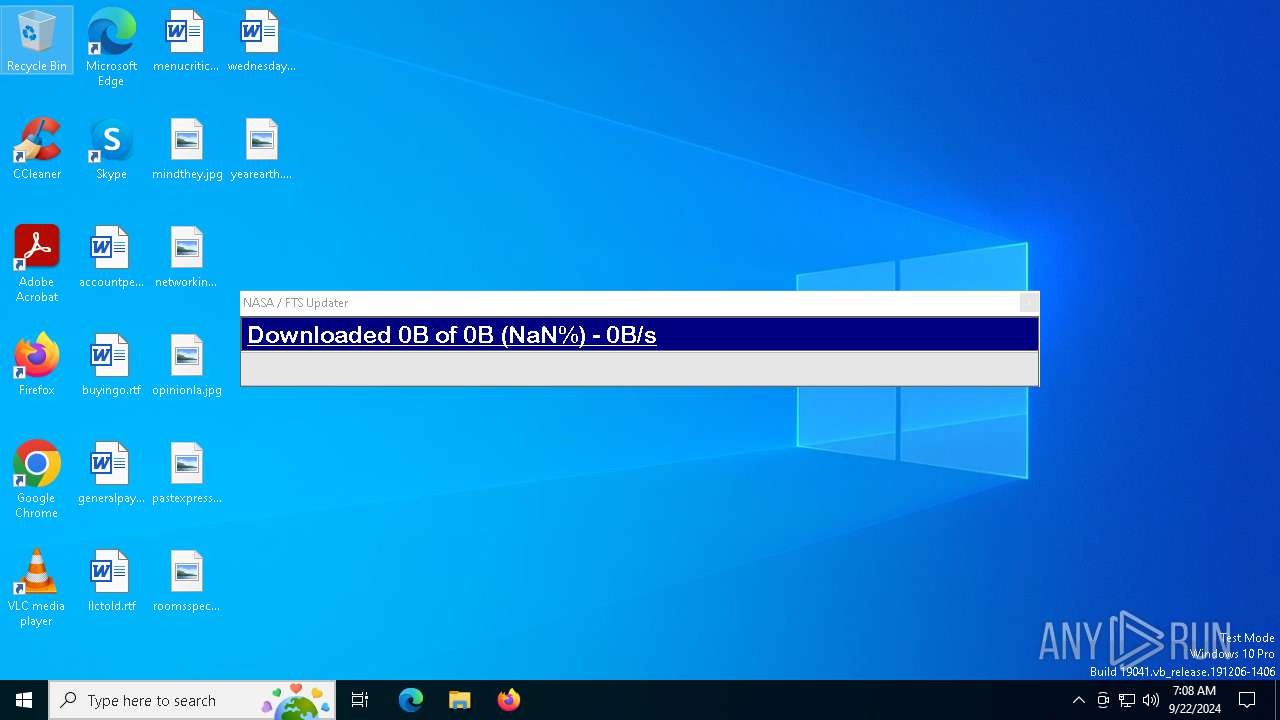
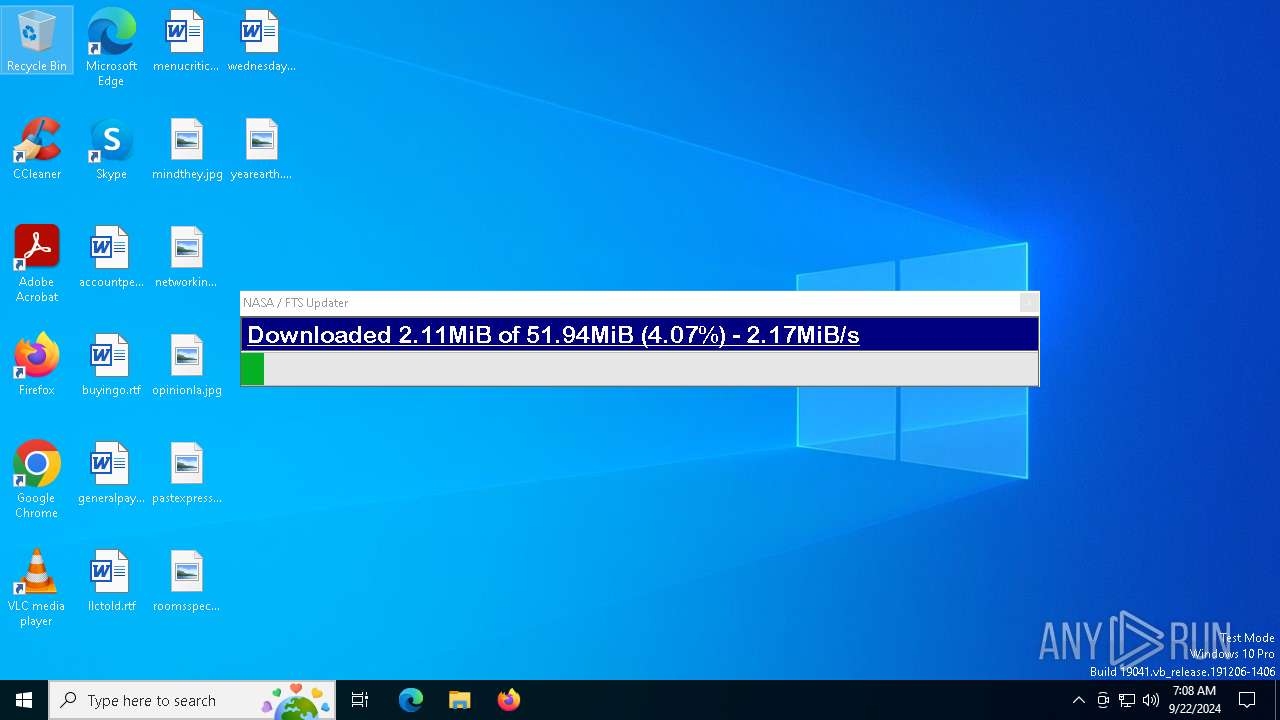
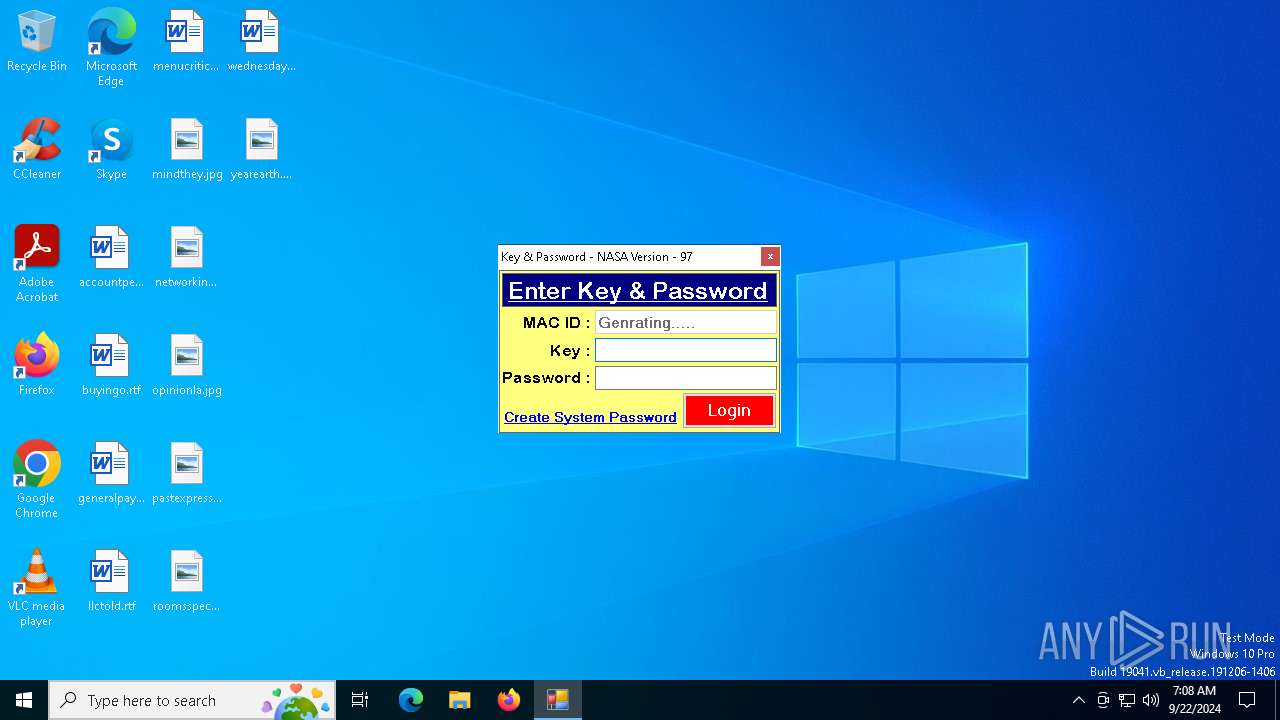
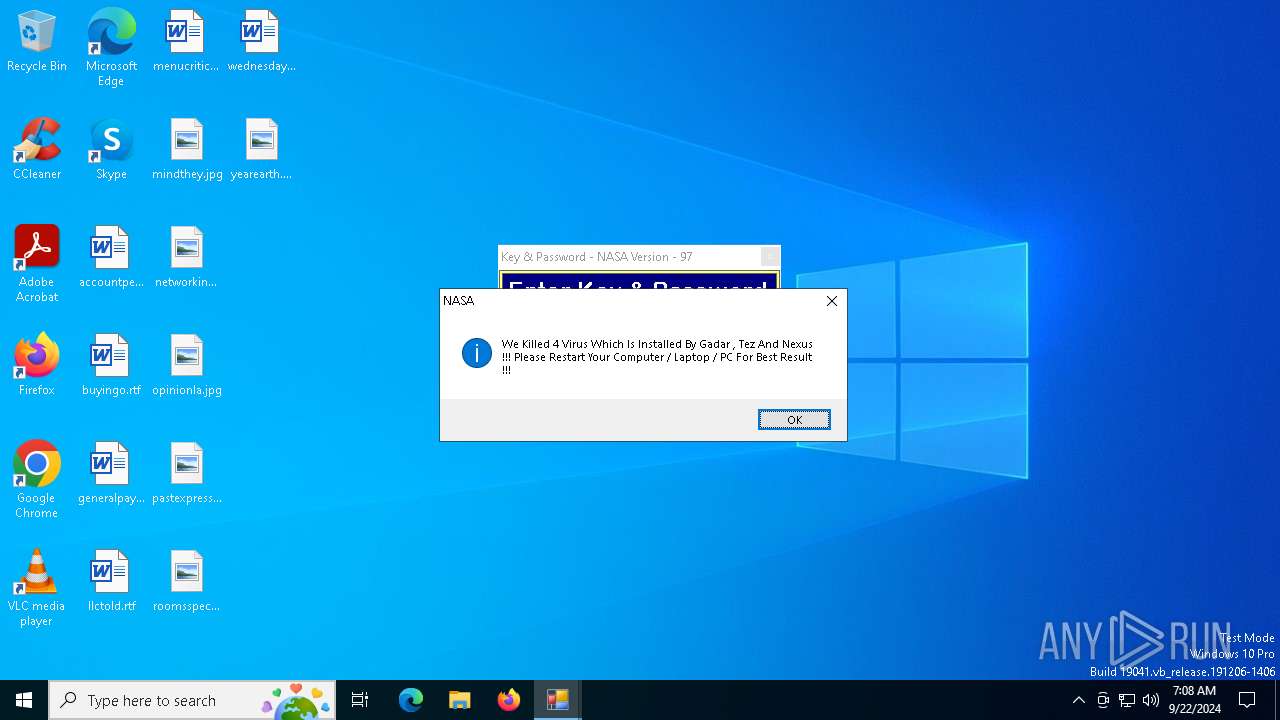
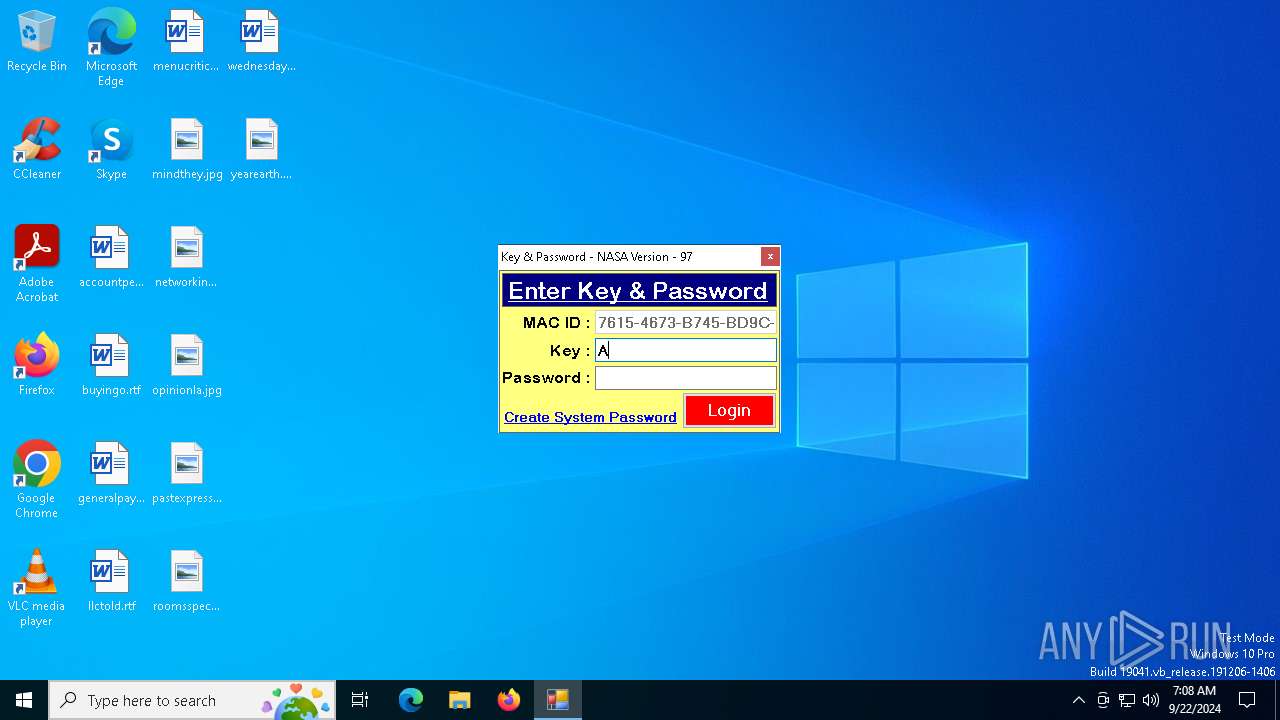
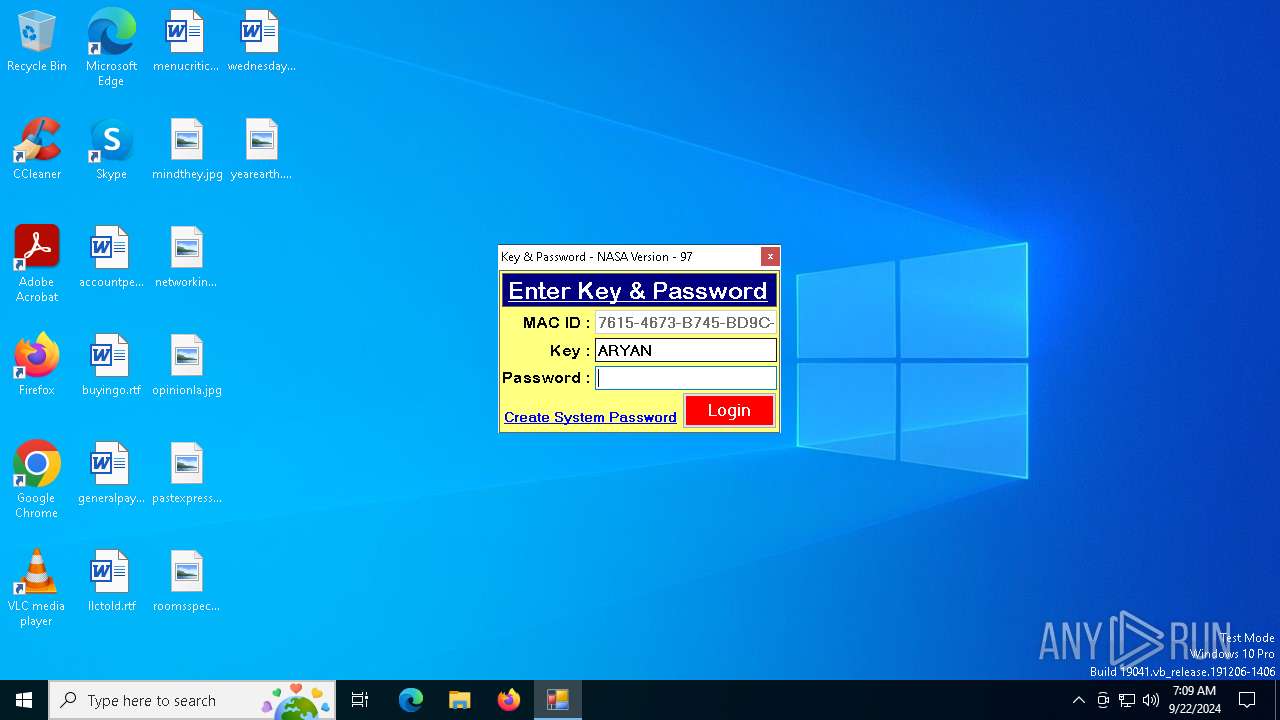
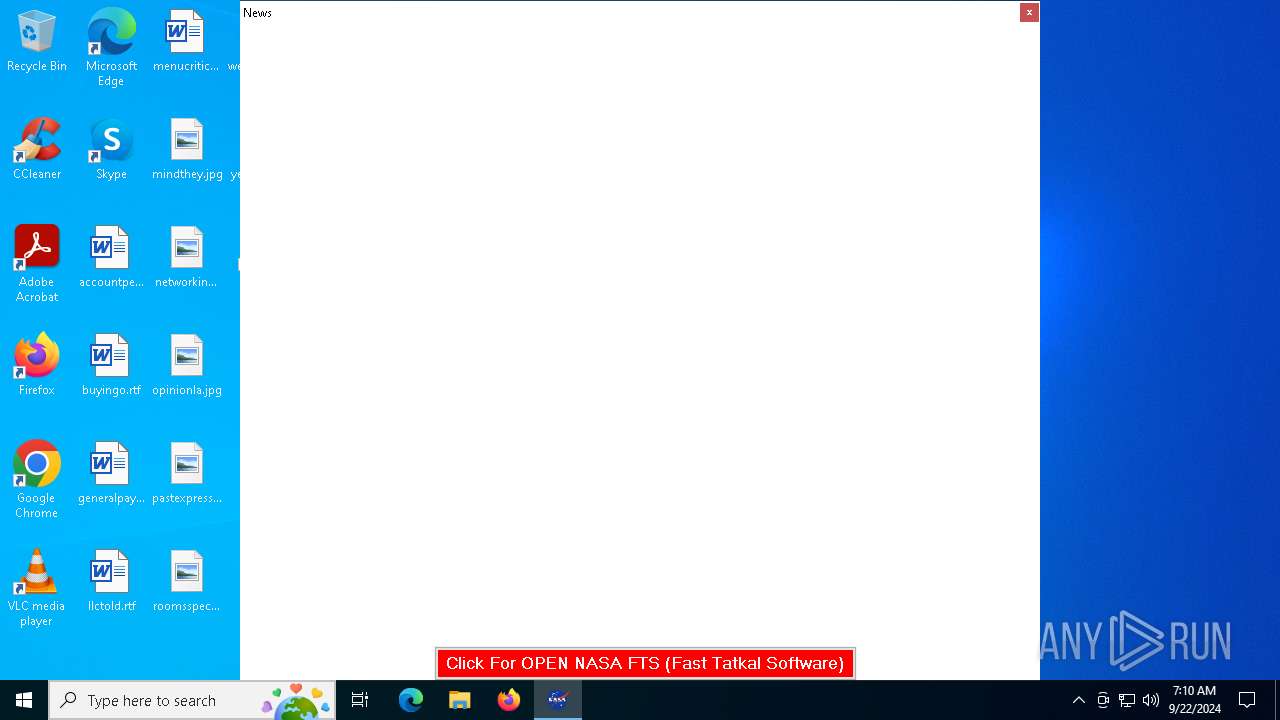
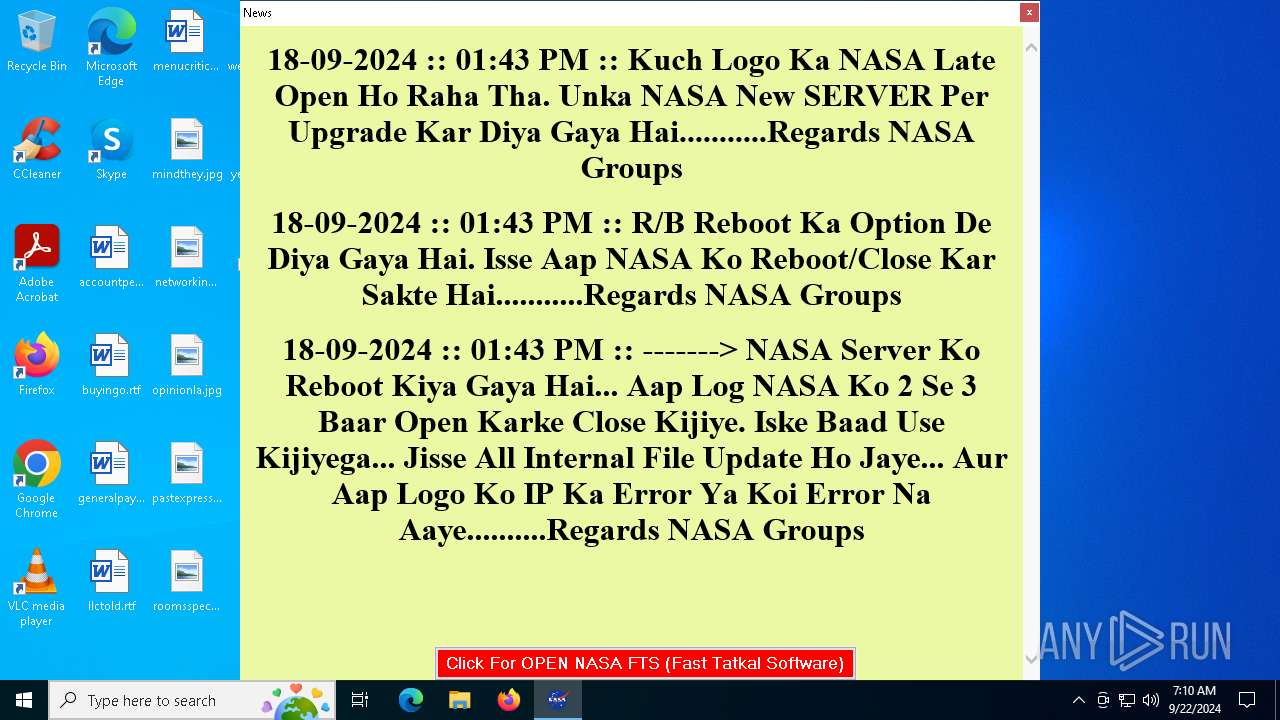
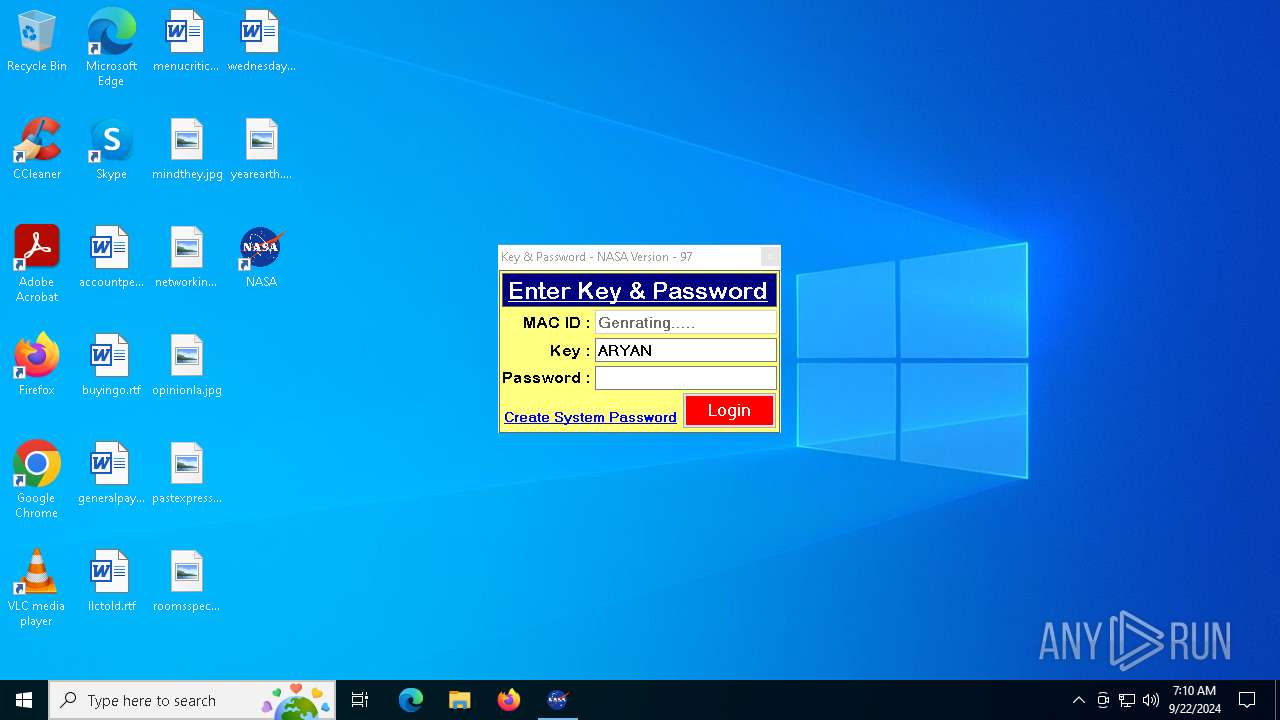
| URL: | nasafts.com |
| Full analysis: | https://app.any.run/tasks/3e22c245-b41f-4ad7-b7d9-63323cee8698 |
| Verdict: | Malicious activity |
| Analysis date: | September 22, 2024, 07:07:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C8F4FC5D03F17D2EE9EBE8A19CAAED46 |
| SHA1: | 100B3F32B8665FA74171EE669ED201D970655CA2 |
| SHA256: | 6D43CE1B06B1D7F064CA851A61C6904733572DF4C517593F7E740CC786F60A3D |
| SSDEEP: | 3:4iK:M |
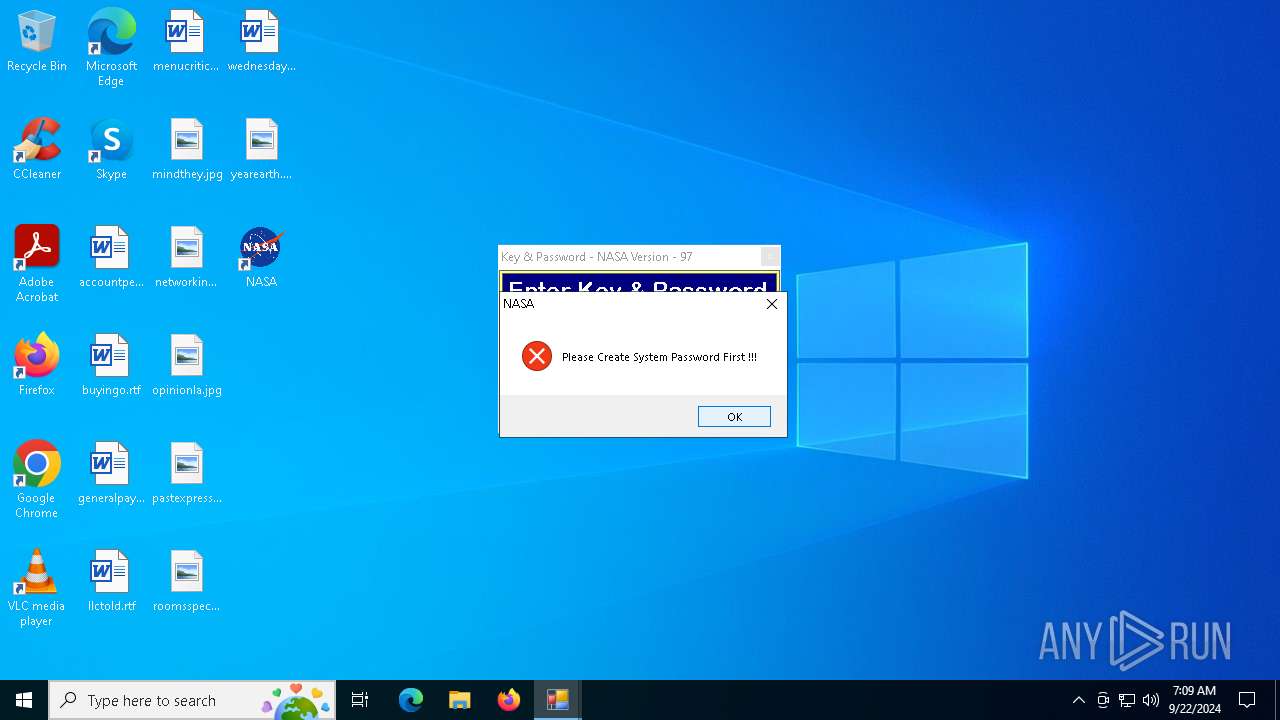
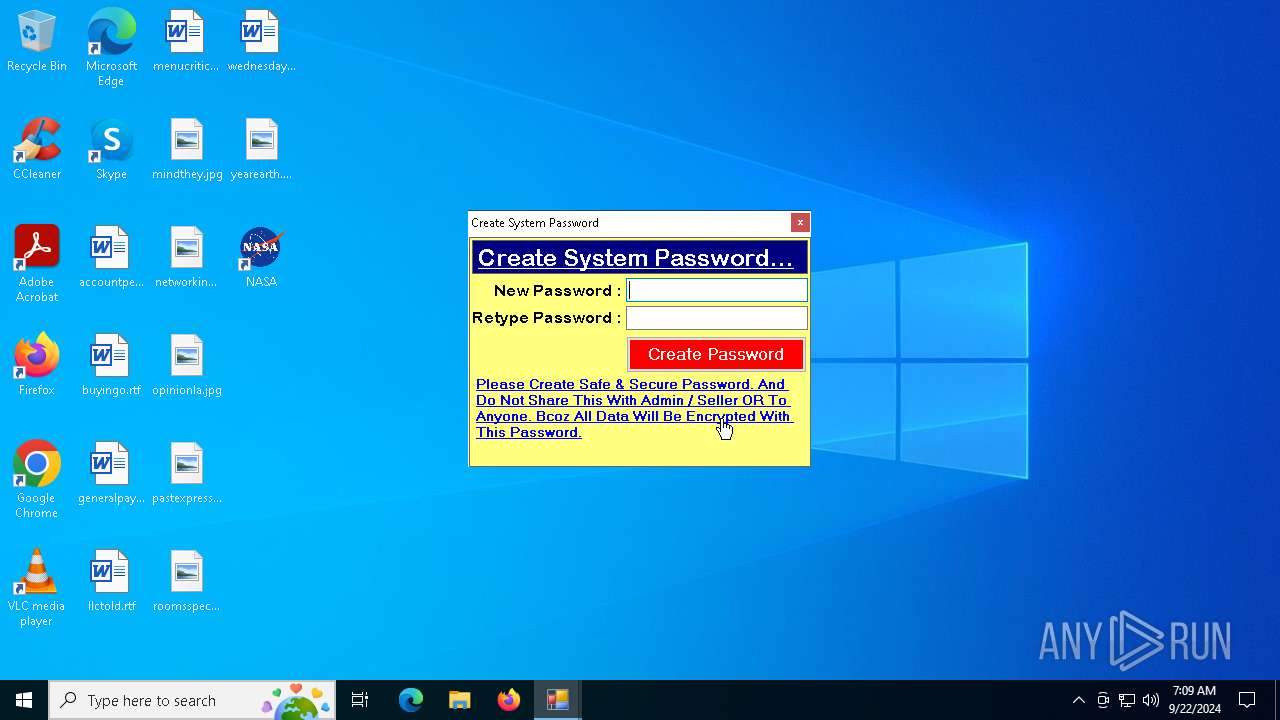
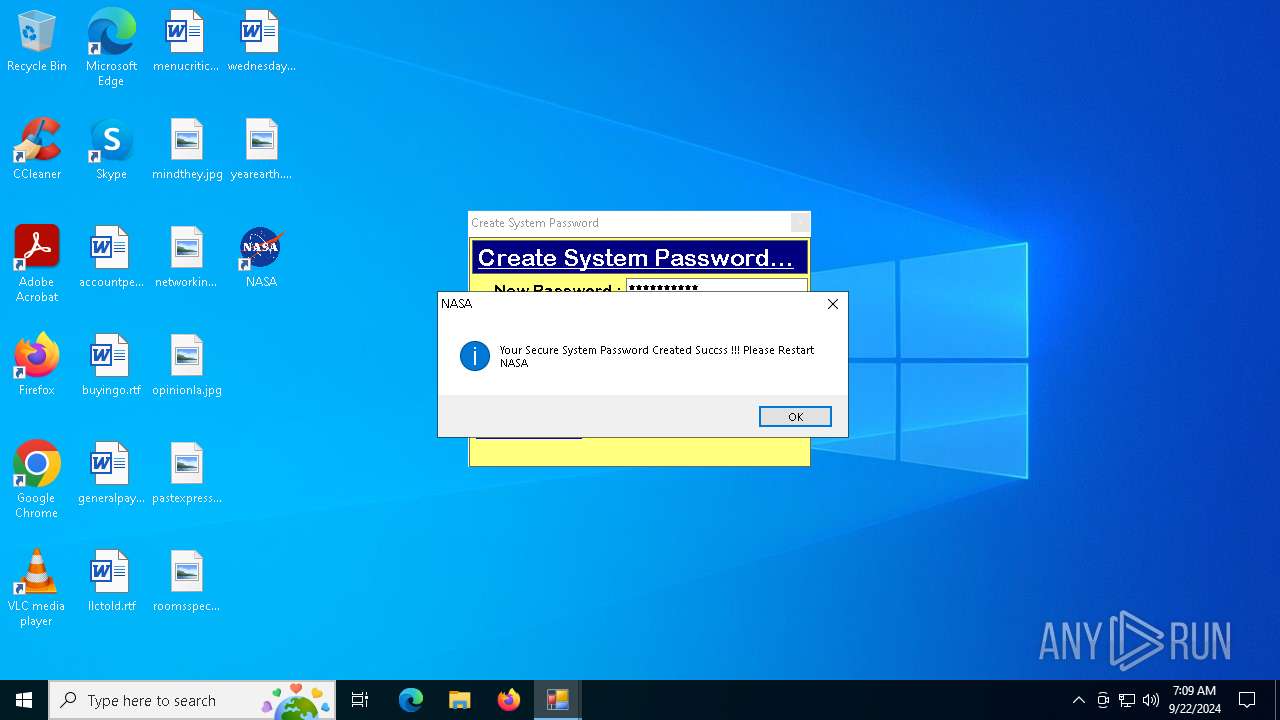
MALICIOUS
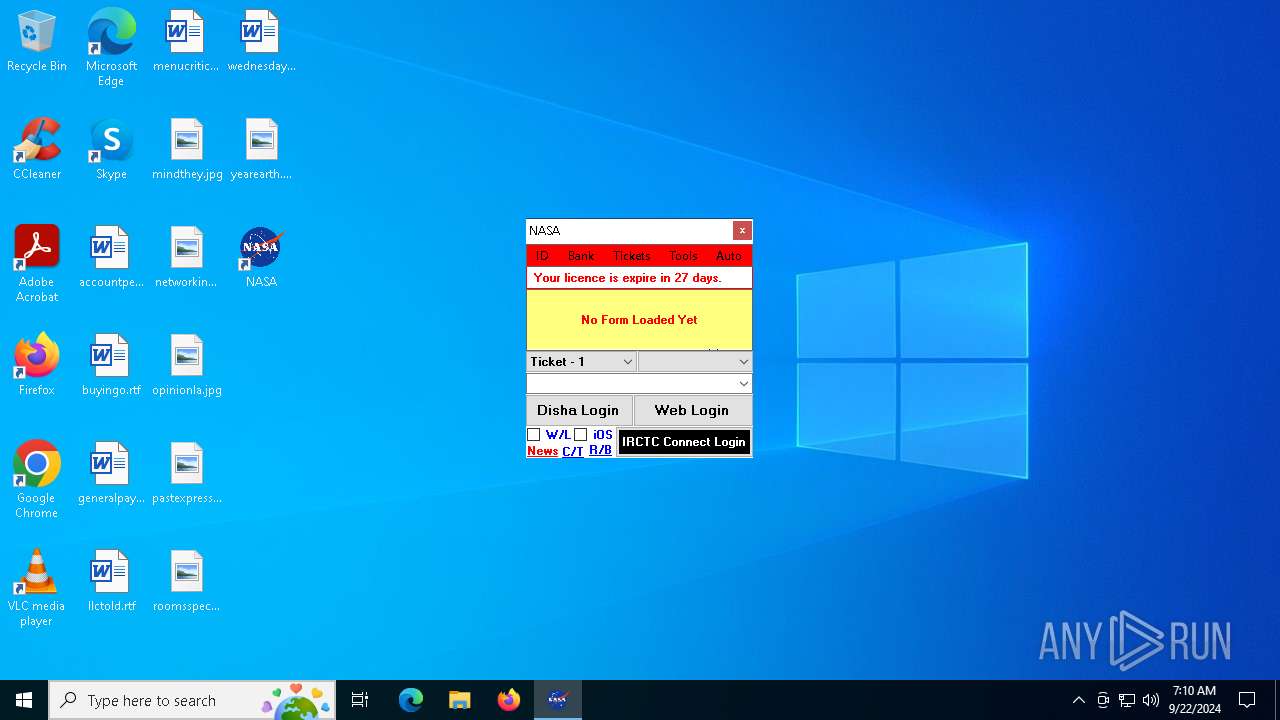
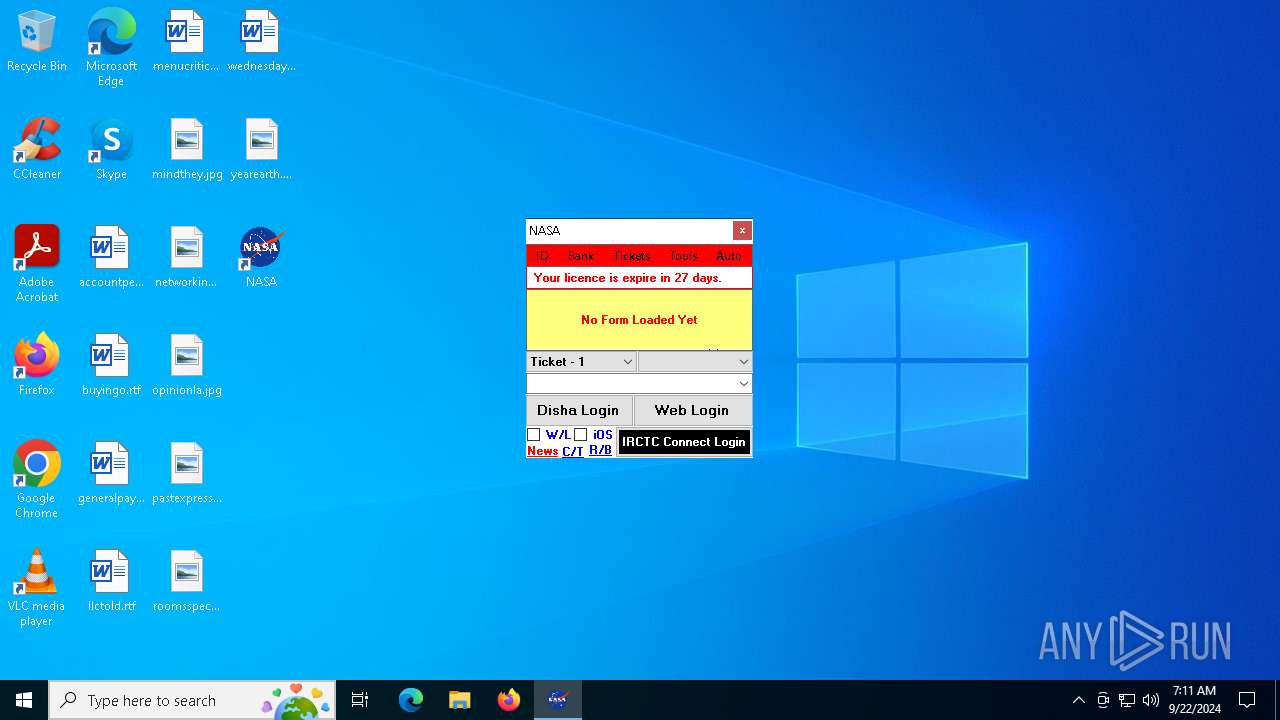
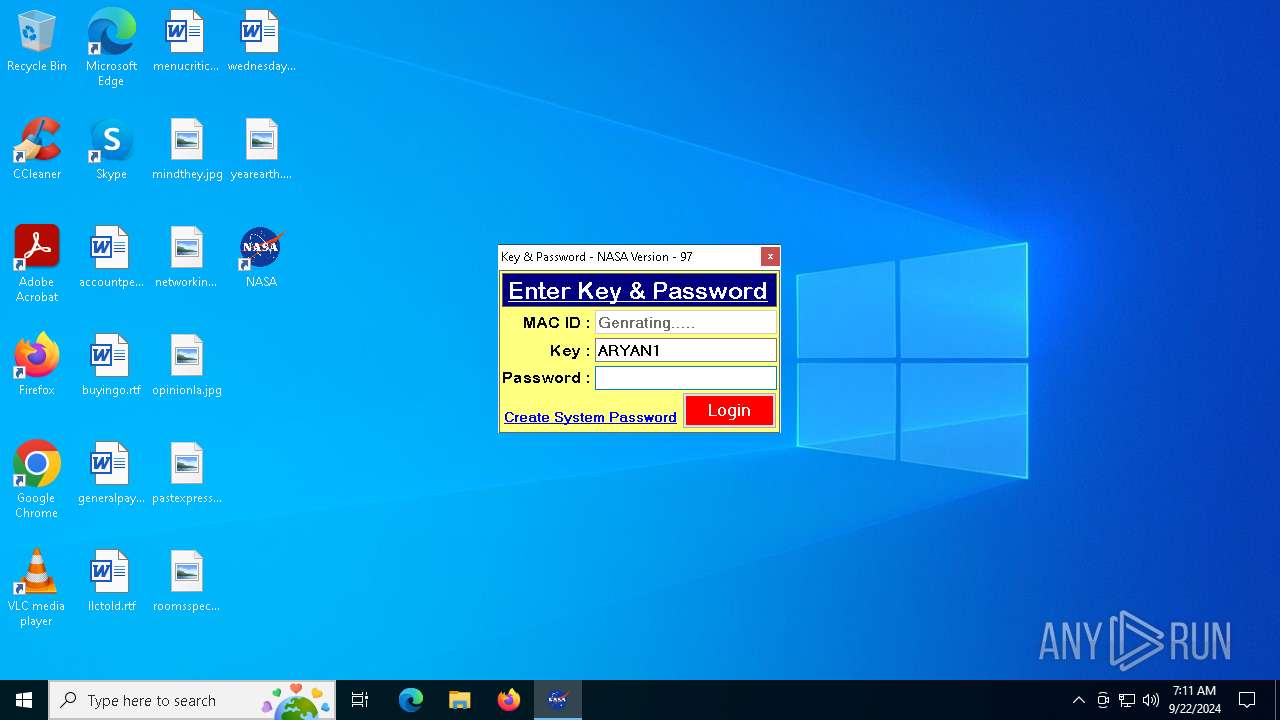
XORed URL has been found (YARA)
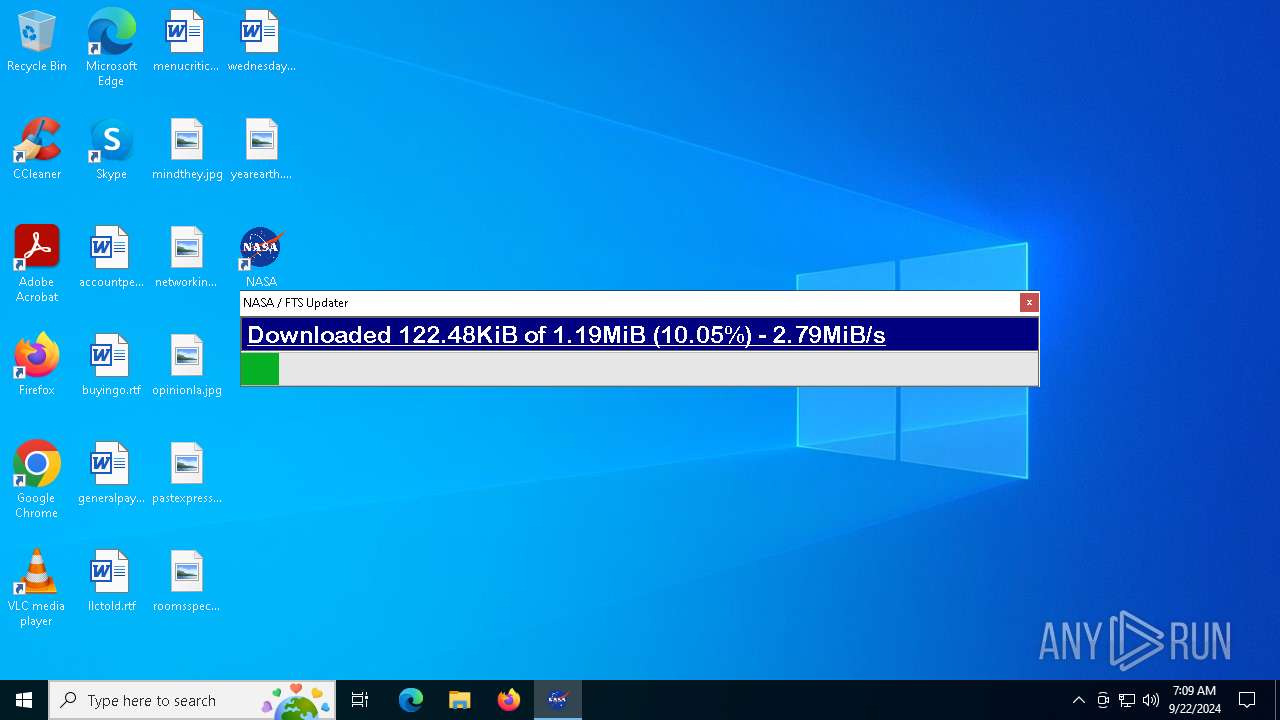
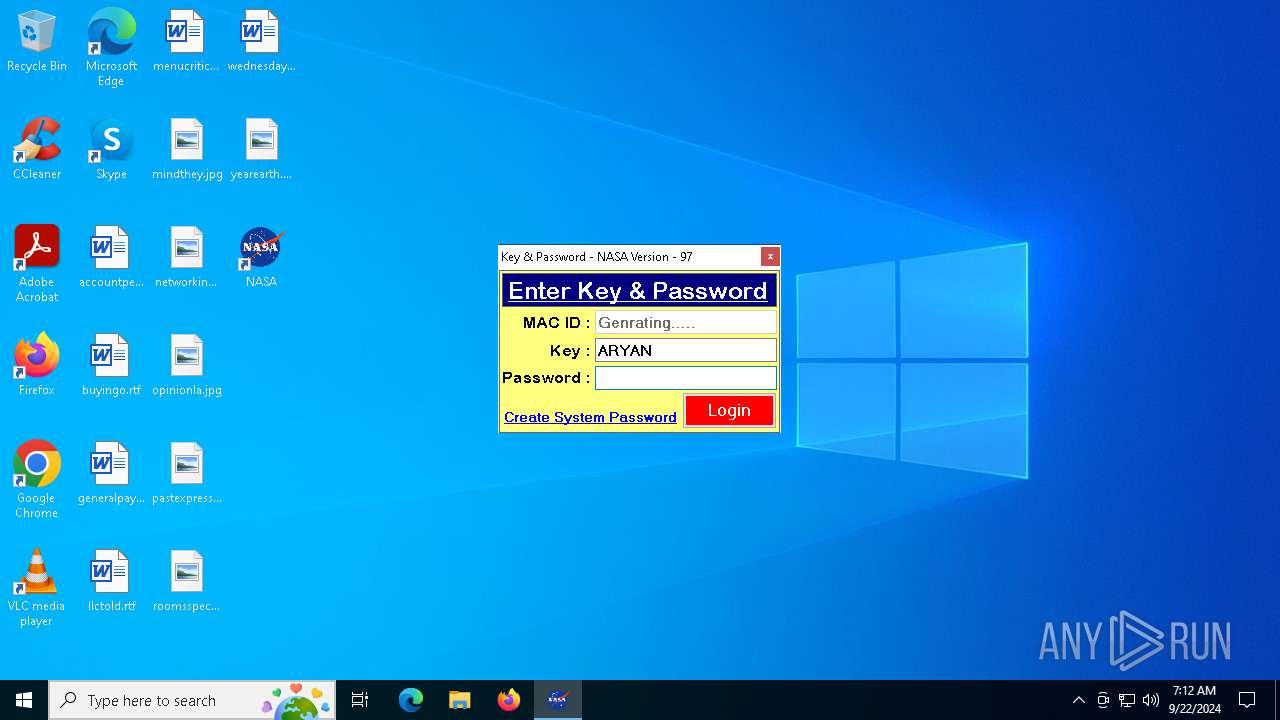
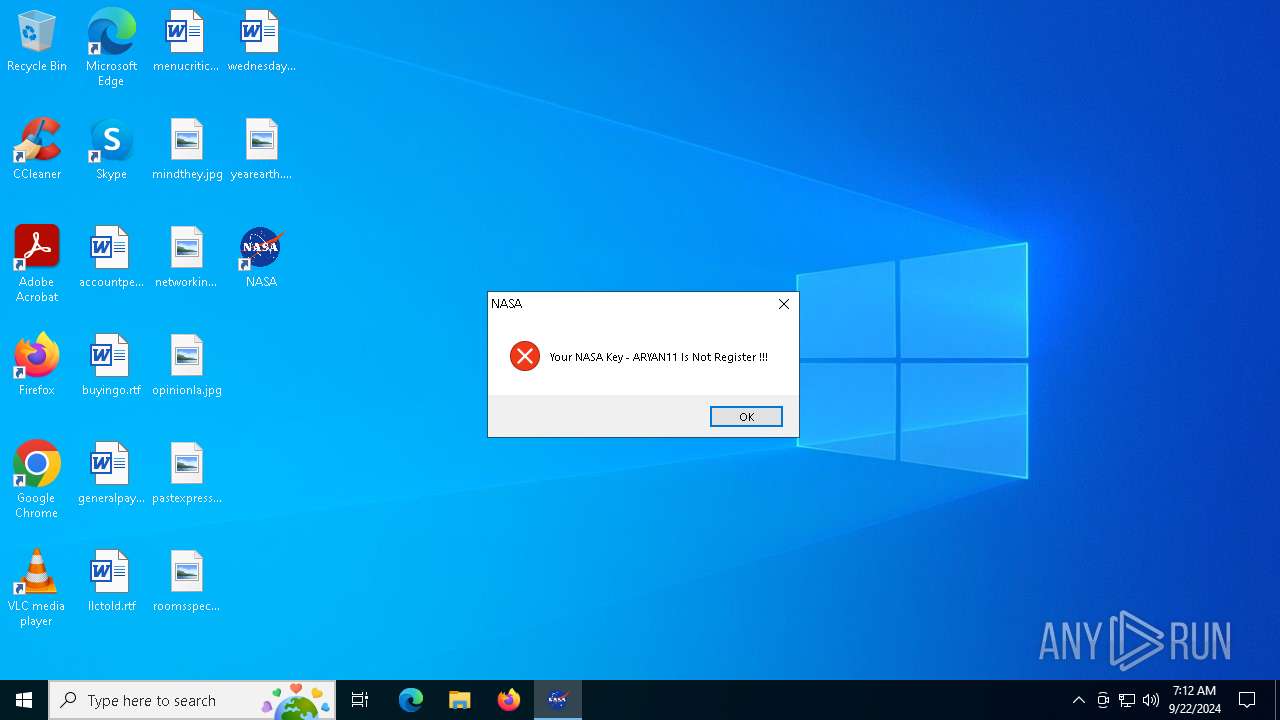
- NASA.exe (PID: 3448)
- NASA.exe (PID: 4108)
- NASA.exe (PID: 7148)
- NASA.exe (PID: 3448)
- NASA.exe (PID: 1332)
- NASA.exe (PID: 3964)
- NASA.exe (PID: 1452)
- NASA.exe (PID: 5984)
- NASA.exe (PID: 4604)
- NASA.exe (PID: 5220)
- NASA.exe (PID: 6400)
SUSPICIOUS
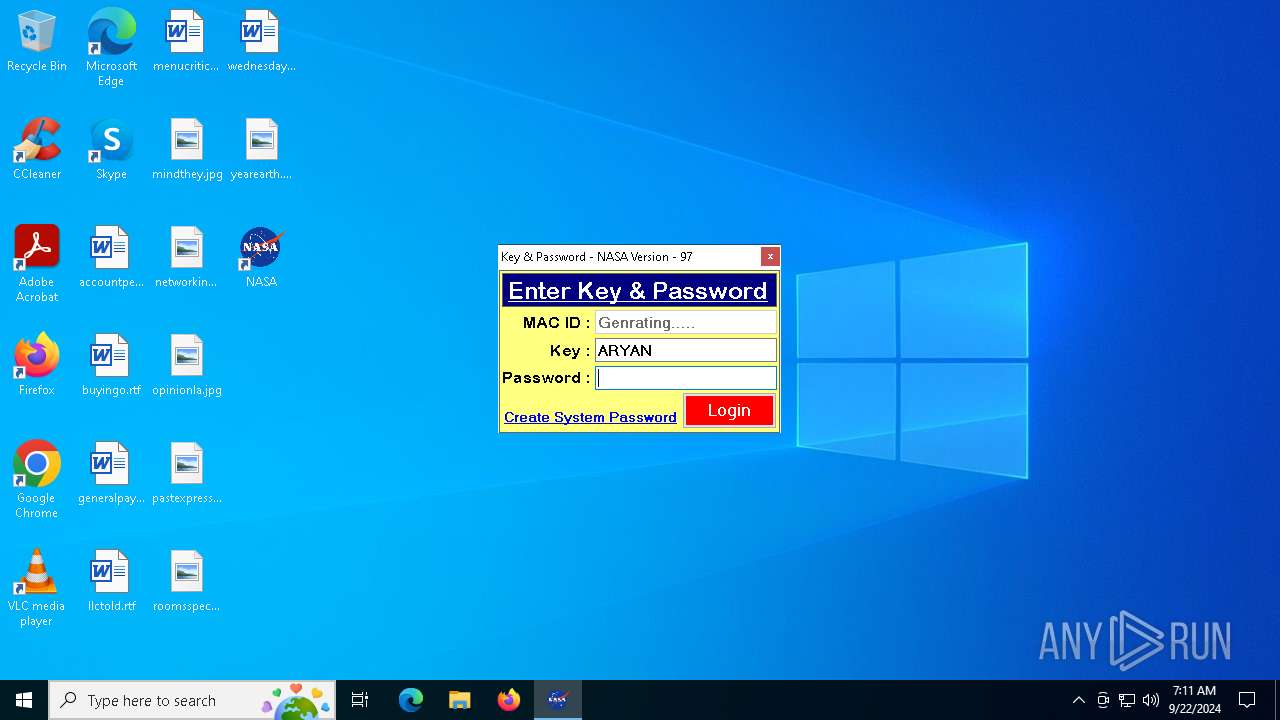
Application launched itself
- NASA.exe (PID: 2096)
- NASA.exe (PID: 4824)
- NASA.exe (PID: 3904)
- NASA.exe (PID: 3116)
- NASA.exe (PID: 3044)
- NASA.exe (PID: 608)
- NASA.exe (PID: 6496)
- NASA.exe (PID: 6676)
- NASA.exe (PID: 376)
- NASA.exe (PID: 6920)
- NASA.exe (PID: 6700)
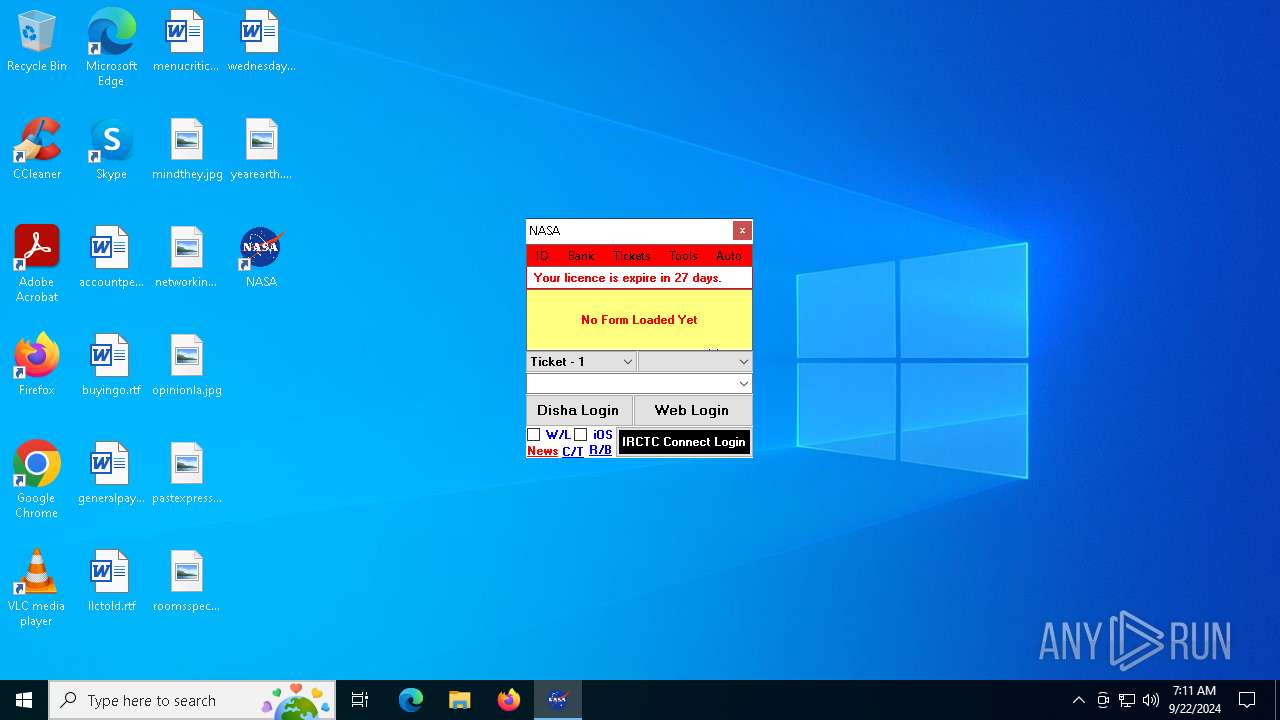
Starts CMD.EXE for commands execution
- NASA.exe (PID: 3448)
- NASA.exe (PID: 4108)
Executable content was dropped or overwritten
- cmd.exe (PID: 6328)
- NASA.exe (PID: 4108)
- NASA.exe (PID: 3448)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 6416)
- cmd.exe (PID: 6592)
- cmd.exe (PID: 3324)
- cmd.exe (PID: 1952)
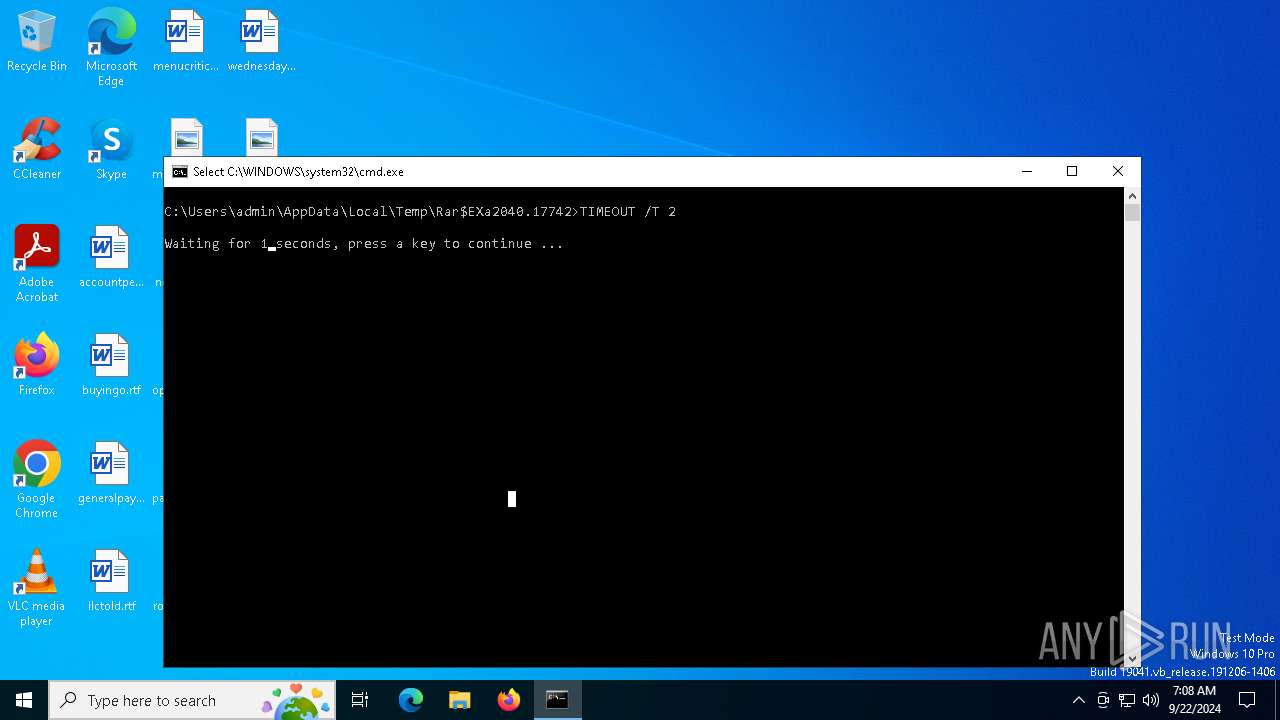
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6328)
Suspicious use of NETSH.EXE
- NASA.exe (PID: 7148)
Executing commands from a ".bat" file
- NASA.exe (PID: 3448)
The executable file from the user directory is run by the CMD process
- NASA.exe (PID: 4108)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2040)
- msedge.exe (PID: 6128)
Application launched itself
- msedge.exe (PID: 7084)
- msedge.exe (PID: 1224)
Manual execution by a user
- NASA.exe (PID: 4824)
- NASA.exe (PID: 376)
- NASA.exe (PID: 3904)
- NASA.exe (PID: 3116)
- NASA.exe (PID: 608)
- NASA.exe (PID: 6700)
- NASA.exe (PID: 6676)
- NASA.exe (PID: 6496)
- NASA.exe (PID: 3044)
- NASA.exe (PID: 6920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
275
Monitored processes
130
Malicious processes
24
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 376 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3916 --field-trial-handle=3580,i,4945409447296747174,1523210109159390481,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | ||||
| 376 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=3964 --field-trial-handle=3580,i,4945409447296747174,1523210109159390481,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | ||||
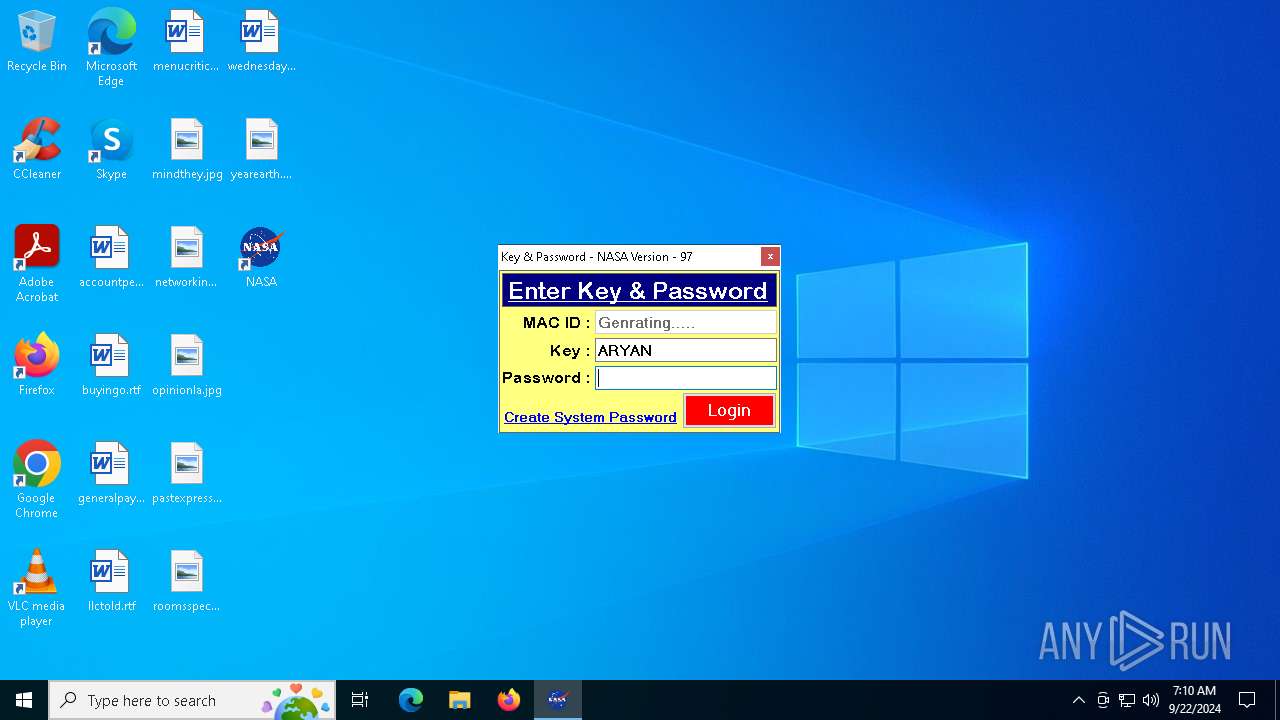
| 376 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2040.17742\NASA.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2040.17742\NASA.exe | — | explorer.exe |
User: admin Company: Amazon.com Integrity Level: MEDIUM Description: NASA Exit code: 0 Version: 1.0.0.0 | ||||
| 608 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2040.17742\NASA.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2040.17742\NASA.exe | — | explorer.exe |
User: admin Company: Amazon.com Integrity Level: MEDIUM Description: NASA Exit code: 0 Version: 1.0.0.0 | ||||
| 644 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4900 --field-trial-handle=2268,i,5215530488688315658,11987741128756114660,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | ||||
| 1164 | "netsh" int tcp set global autotuninglevel=normal | C:\Windows\SysWOW64\netsh.exe | — | NASA.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1224 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 | ||||
| 1288 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=30 --mojo-platform-channel-handle=6616 --field-trial-handle=2268,i,5215530488688315658,11987741128756114660,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | ||||
| 1332 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2040.17742\NASA.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2040.17742\NASA.exe | NASA.exe | |
User: admin Company: Amazon.com Integrity Level: HIGH Description: NASA Exit code: 4294967295 Version: 1.0.0.0 | ||||
| 1344 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x2ec,0x2f0,0x2f4,0x2e8,0x2fc,0x7fffcb4e5fd8,0x7fffcb4e5fe4,0x7fffcb4e5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
17
Suspicious files
473
Text files
215
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1fb251.TMP | — | |
MD5:— | SHA256:— | |||
| 7084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1fb251.TMP | — | |
MD5:— | SHA256:— | |||
| 7084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1fb251.TMP | — | |
MD5:— | SHA256:— | |||
| 7084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1fb280.TMP | — | |
MD5:— | SHA256:— | |||
| 7084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1fb724.TMP | — | |
MD5:— | SHA256:— | |||
| 7084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
58
TCP/UDP connections
94
DNS requests
84
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6604 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 142.250.185.163:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
6932 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/780b5257-0c6e-4f0d-b773-3c74985169d8?P1=1727511299&P2=404&P3=2&P4=A5DMtKY7SLNSoOxSxEZbQmjopygGQHmOQYHcGPxKh%2fC03g0l6P5Kvm%2bbofS%2flQ7xuJ473HF7tMpurSZ3z0n0SA%3d%3d | unknown | — | — | whitelisted |
5152 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/780b5257-0c6e-4f0d-b773-3c74985169d8?P1=1727511299&P2=404&P3=2&P4=A5DMtKY7SLNSoOxSxEZbQmjopygGQHmOQYHcGPxKh%2fC03g0l6P5Kvm%2bbofS%2flQ7xuJ473HF7tMpurSZ3z0n0SA%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/780b5257-0c6e-4f0d-b773-3c74985169d8?P1=1727511299&P2=404&P3=2&P4=A5DMtKY7SLNSoOxSxEZbQmjopygGQHmOQYHcGPxKh%2fC03g0l6P5Kvm%2bbofS%2flQ7xuJ473HF7tMpurSZ3z0n0SA%3d%3d | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/780b5257-0c6e-4f0d-b773-3c74985169d8?P1=1727511299&P2=404&P3=2&P4=A5DMtKY7SLNSoOxSxEZbQmjopygGQHmOQYHcGPxKh%2fC03g0l6P5Kvm%2bbofS%2flQ7xuJ473HF7tMpurSZ3z0n0SA%3d%3d | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1727398800&P2=404&P3=2&P4=gH3vpPIJc1jyzJ8NgjPkHoBCWFyoj%2bMV0FJMPuois3COGMl%2b0V%2bUJ2cFDY8zCmPdB3ifa6SPesP581ASyLmzSQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6604 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3032 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.42.65.94:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 92.123.104.59:443 | edgeservices.bing.com | Akamai International B.V. | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7084 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5852 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5852 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
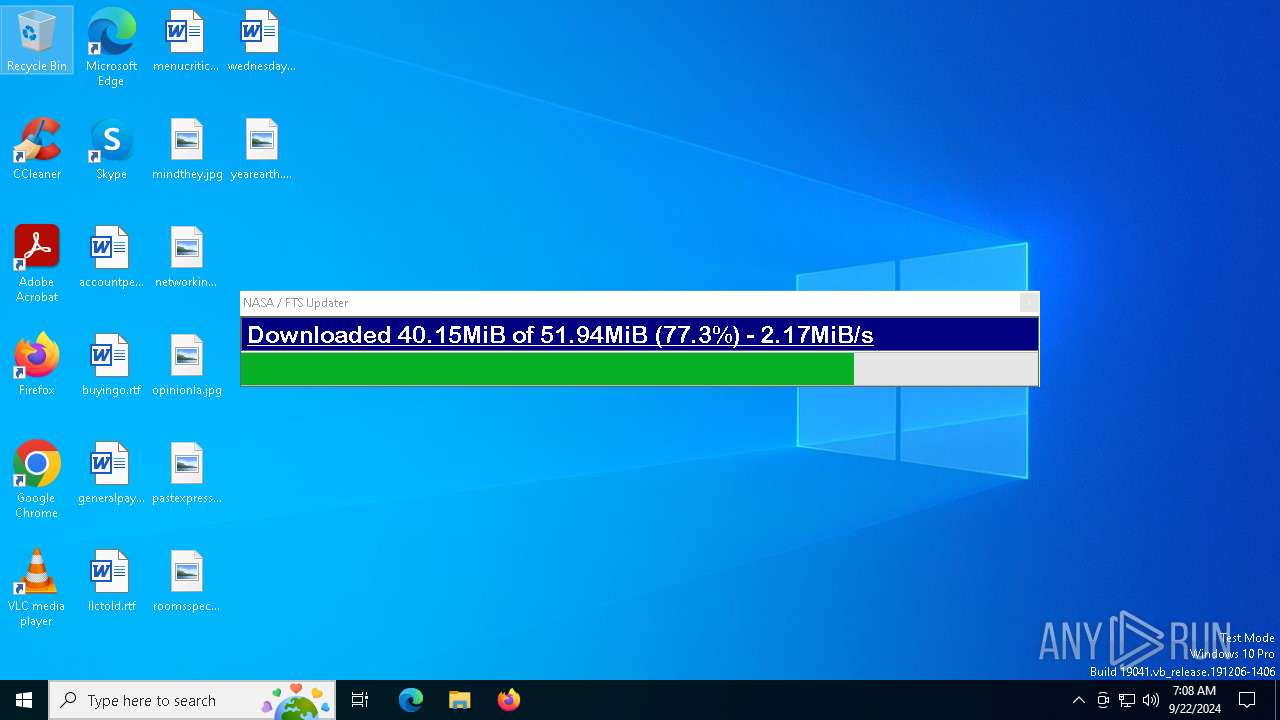
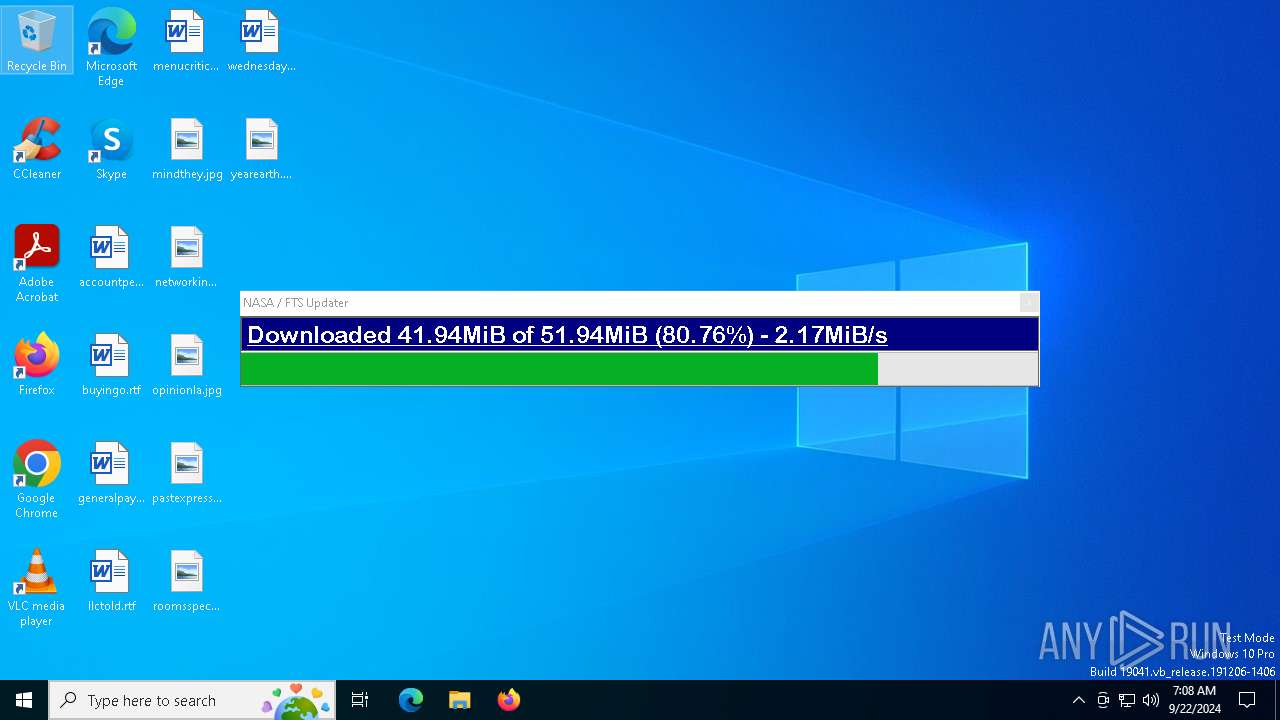
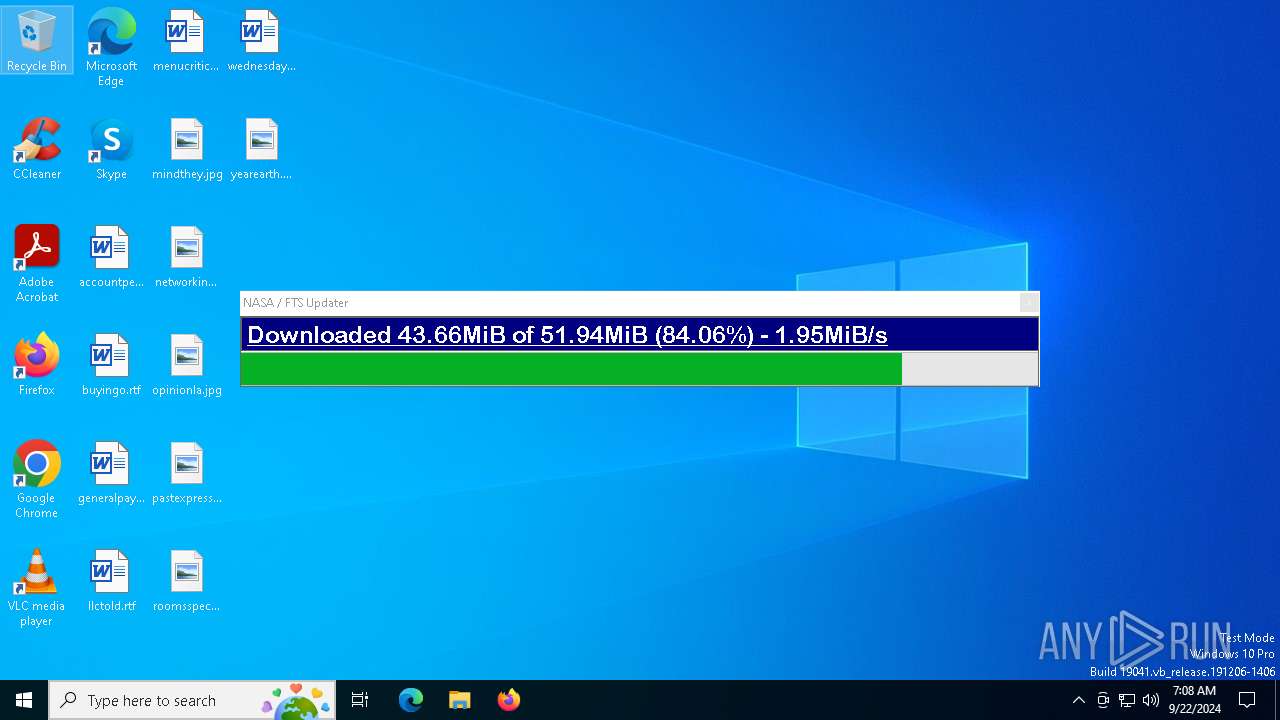
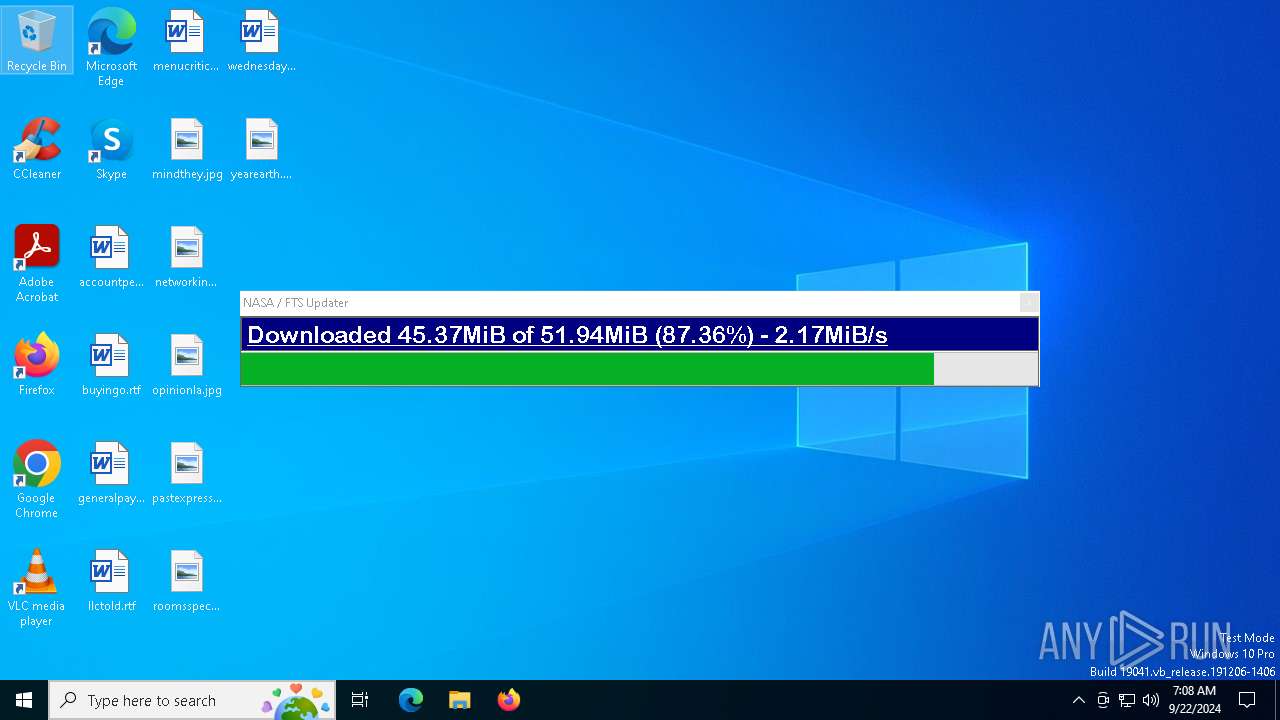
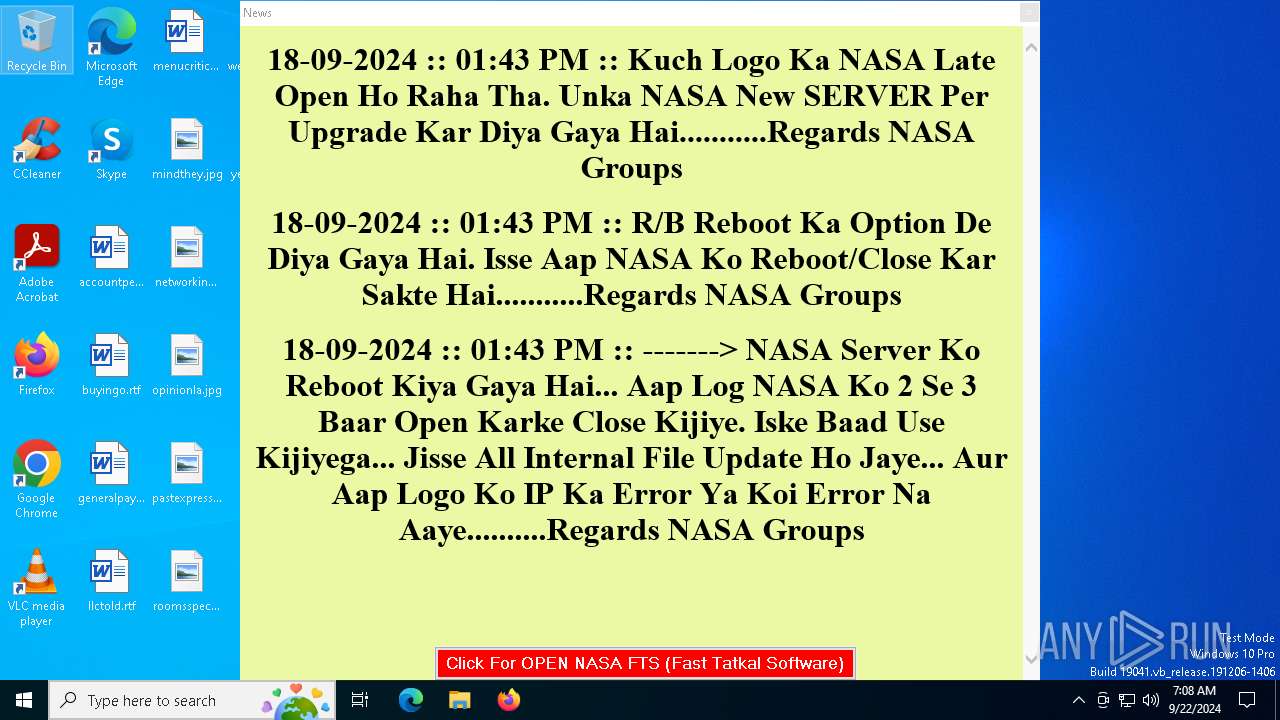
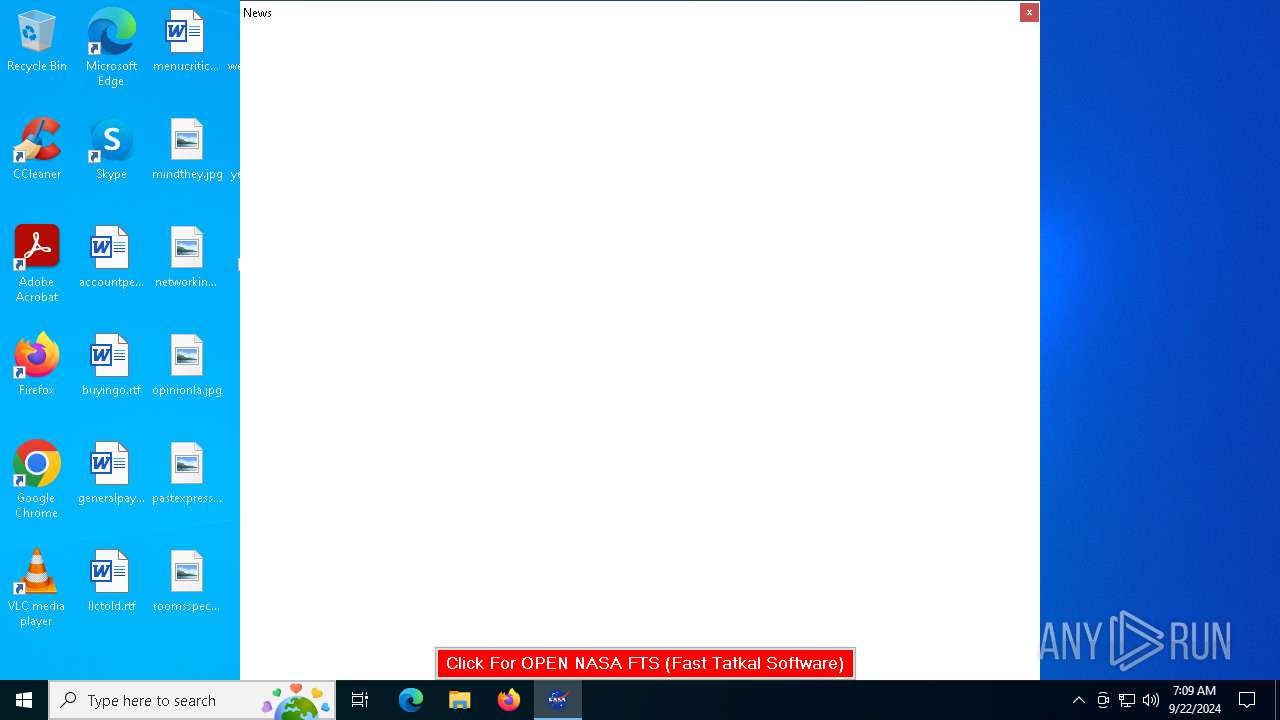
nasafts.com |
| unknown |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
kit.fontawesome.com |
| whitelisted |
www.bing.com |
| whitelisted |