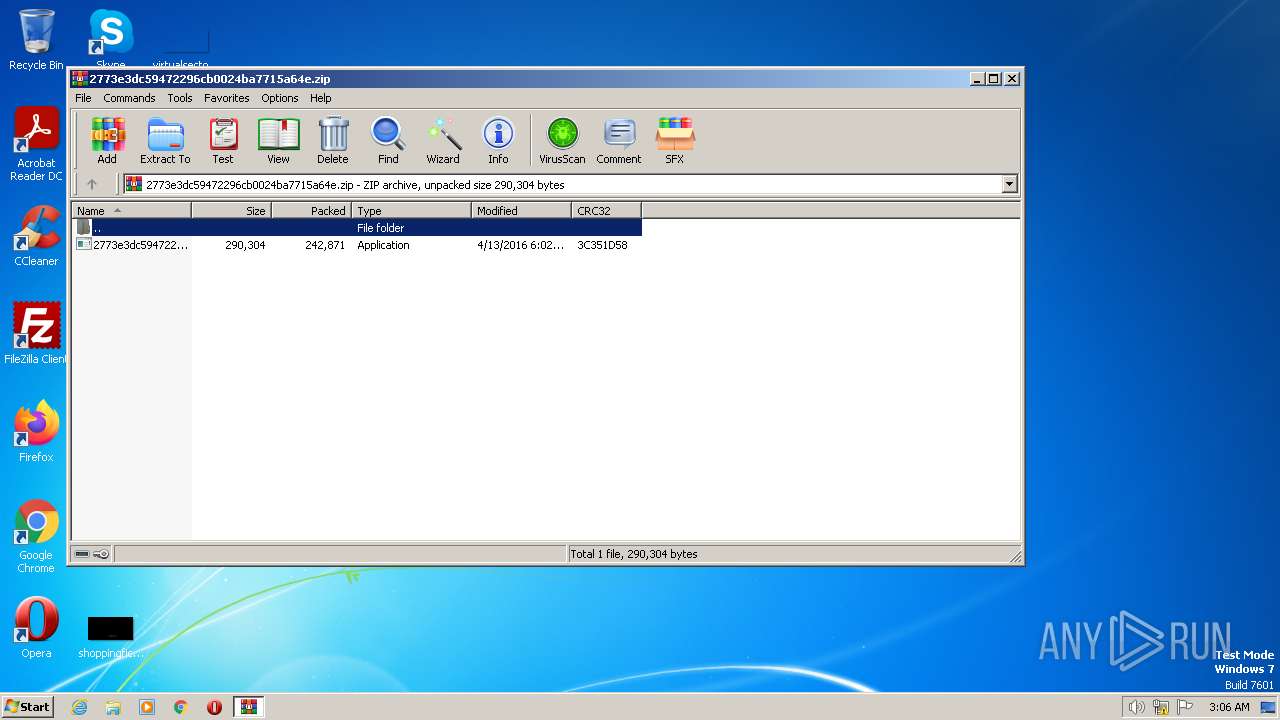
| File name: | 2773e3dc59472296cb0024ba7715a64e.zip |
| Full analysis: | https://app.any.run/tasks/2dd14b4c-451e-4c5c-a0a4-d517ecff0d73 |
| Verdict: | Malicious activity |
| Analysis date: | June 28, 2023, 02:06:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B877491211BFCFF842912FD055588799 |
| SHA1: | D19E7A79B08BAE01B00AC447F6CFD236EF055474 |
| SHA256: | 6D230F1F3A10F78741545A9D6FBD43BBB0A6A55FEFCA245760D5DB92AC3CC1CD |
| SSDEEP: | 3072:aAYjkooRsGE5zhcE+MhDcOHhcrD3gmsn7Hbt2edV0OI9Oez9DB4v/RfPE+5ApuPw:zY4/Ezz+ML2q7kvNcezVavJdZP/B8ccT |
MALICIOUS
Application was dropped or rewritten from another process
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3912)
- drpbx.exe (PID: 1808)
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3696)
Changes the autorun value in the registry
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3696)
SUSPICIOUS
Reads the Internet Settings
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3912)
Executable content was dropped or overwritten
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3912)
Starts itself from another location
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3912)
INFO
Checks supported languages
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3912)
- drpbx.exe (PID: 1808)
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3696)
The process checks LSA protection
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3912)
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3696)
- drpbx.exe (PID: 1808)
Creates files or folders in the user directory
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3912)
Reads the computer name
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3912)
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3696)
Manual execution by a user
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3912)
- WINWORD.EXE (PID: 4004)
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3696)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3524)
Reads the machine GUID from the registry
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3912)
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 3696)
- drpbx.exe (PID: 1808)
Creates files in the program directory
- drpbx.exe (PID: 1808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
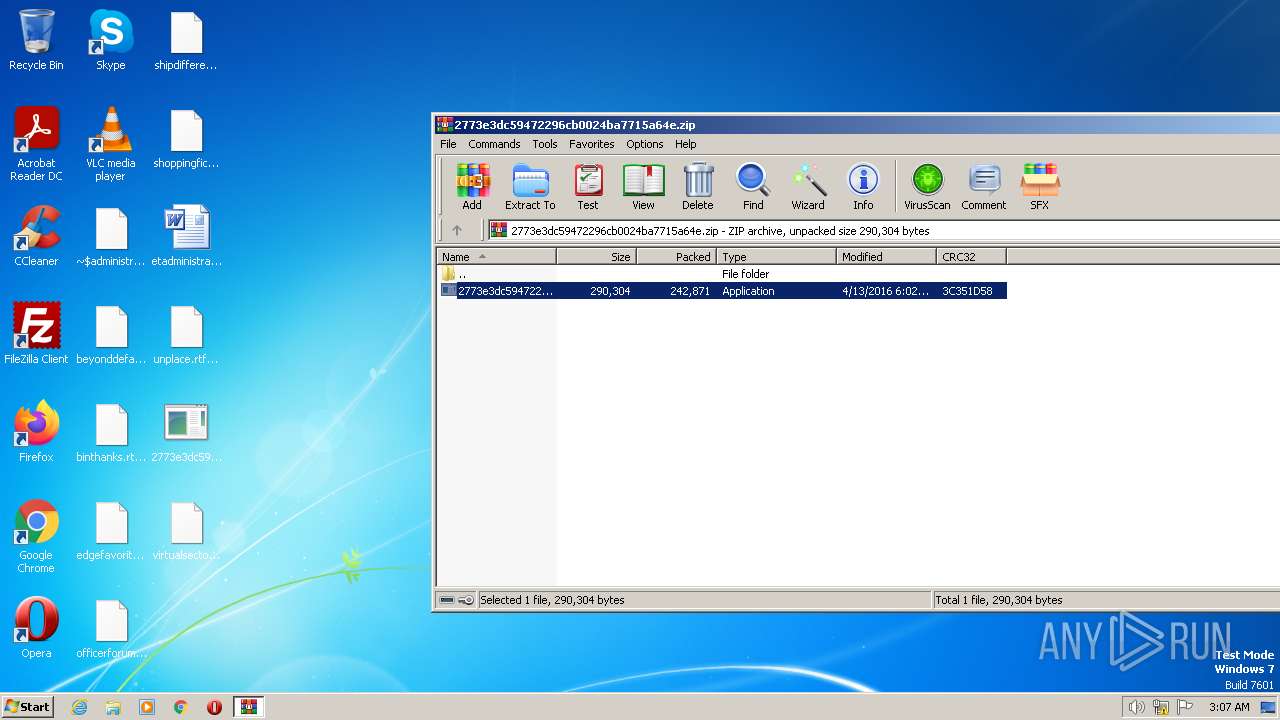
| ZipFileName: | 2773e3dc59472296cb0024ba7715a64e.exe |
|---|---|
| ZipUncompressedSize: | 290304 |
| ZipCompressedSize: | 242871 |
| ZipCRC: | 0x3c351d58 |
| ZipModifyDate: | 2016:04:13 18:02:34 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0001 |
| ZipRequiredVersion: | 788 |
Total processes
44
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1808 | "C:\Users\admin\AppData\Local\Drpbx\drpbx.exe" C:\Users\admin\Desktop\2773e3dc59472296cb0024ba7715a64e.exe | C:\Users\admin\AppData\Local\Drpbx\drpbx.exe | — | 2773e3dc59472296cb0024ba7715a64e.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 37.0.2.5583 Modules
| |||||||||||||||
| 3524 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\2773e3dc59472296cb0024ba7715a64e.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3696 | "C:\Users\admin\Desktop\2773e3dc59472296cb0024ba7715a64e.exe" | C:\Users\admin\Desktop\2773e3dc59472296cb0024ba7715a64e.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 37.0.2.5583 Modules
| |||||||||||||||
| 3912 | "C:\Users\admin\Desktop\2773e3dc59472296cb0024ba7715a64e.exe" | C:\Users\admin\Desktop\2773e3dc59472296cb0024ba7715a64e.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 37.0.2.5583 Modules
| |||||||||||||||
| 4004 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\etadministration.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
7 402
Read events
7 207
Write events
52
Delete events
143
Modification events
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3912) 2773e3dc59472296cb0024ba7715a64e.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
4
Suspicious files
382
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4004 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR507A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3524 | WinRAR.exe | C:\Users\admin\Desktop\2773e3dc59472296cb0024ba7715a64e.exe | executable | |
MD5:2773E3DC59472296CB0024BA7715A64E | SHA256:3AE96F73D805E1D3995253DB4D910300D8442EA603737A1428B613061E7F61E7 | |||
| 1808 | drpbx.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\AccessMUI.xml.fun | binary | |
MD5:B8E36A31142237D9E5C6A18056D448C1 | SHA256:9E30A1A8685998EC8227FAA33A0FD0B2485FF430C4A3D4FC41CDAC6C33F33BE7 | |||
| 1808 | drpbx.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\branding.xml.fun | binary | |
MD5:AF3B47EE3239EE27A36DF974BA6FF35A | SHA256:FD6C354E84802174AB77076F4167F39BD68CAB971EC46A80000BDB8150F05CF5 | |||
| 4004 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:477F2108D8FD970AA30180FE1FEE840C | SHA256:76843C547857CB1E4D73FAB618D786AC471405A9CFF56AA55B3BFE3E82FE9AF1 | |||
| 1808 | drpbx.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\Setup.xml.fun | binary | |
MD5:26F9CD4F0D02DAD6930E5236953A470D | SHA256:53D145BB1F639490715965053E247D07633EC8C3A7EBCA2FBED934427968D25A | |||
| 3912 | 2773e3dc59472296cb0024ba7715a64e.exe | C:\Users\admin\AppData\Roaming\Frfx\firefox.exe | executable | |
MD5:2773E3DC59472296CB0024BA7715A64E | SHA256:3AE96F73D805E1D3995253DB4D910300D8442EA603737A1428B613061E7F61E7 | |||
| 4004 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:B7F156A5A19F720D86DB4C51040A2749 | SHA256:48AC94B46551C504BDEAEF5CA1F2A832C2C539F522343701AF964A9DB32088F6 | |||
| 1808 | drpbx.exe | C:\MSOCache\All Users\{90140000-0015-0410-0000-0000000FF1CE}-C\branding.xml.fun | binary | |
MD5:FD2ABF1B947745C51FC989779BC0A002 | SHA256:21CF977AA01CC53D7C5C54A2C448755455F033AA35953A8CB969E19F221FF4CE | |||
| 1808 | drpbx.exe | C:\MSOCache\All Users\{90140000-0015-040C-0000-0000000FF1CE}-C\Setup.xml.fun | binary | |
MD5:9D19D98D71BBB006AED9379F74906F6B | SHA256:E32F5C1558986B99421C3F197F1FEFDF2CB485693FF4AD4963904CBBBEBB9574 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
292 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |