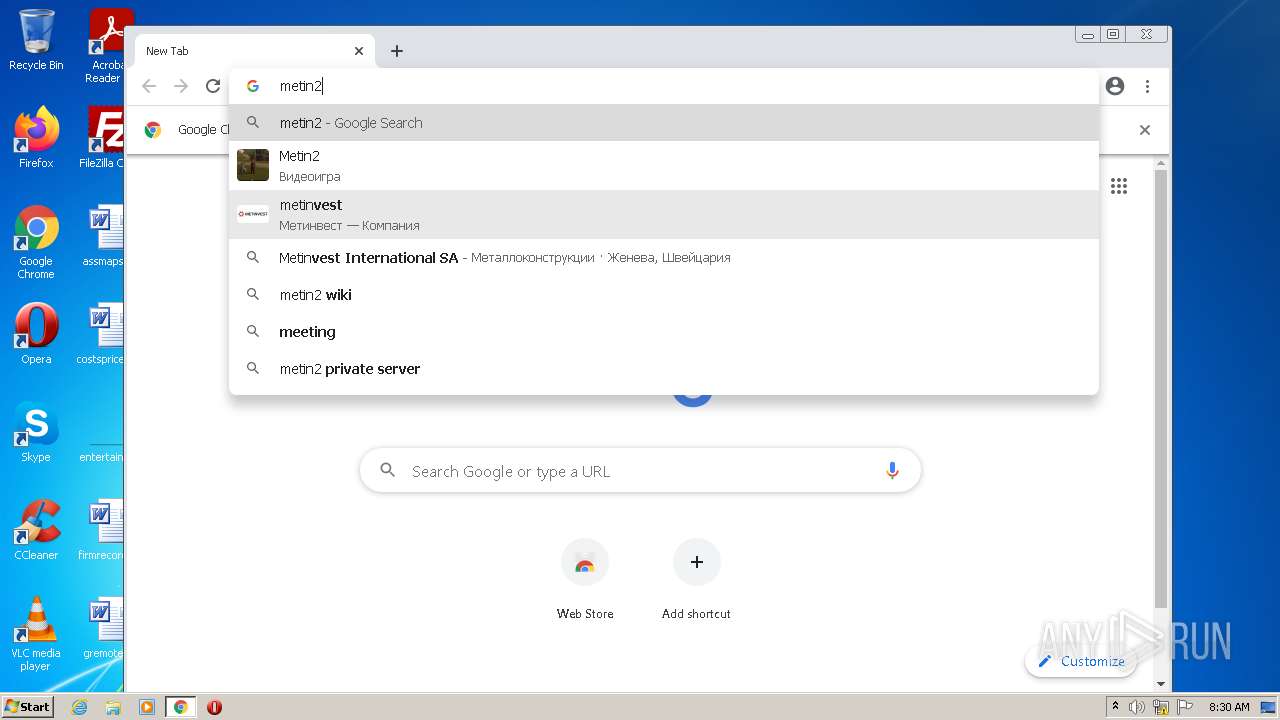
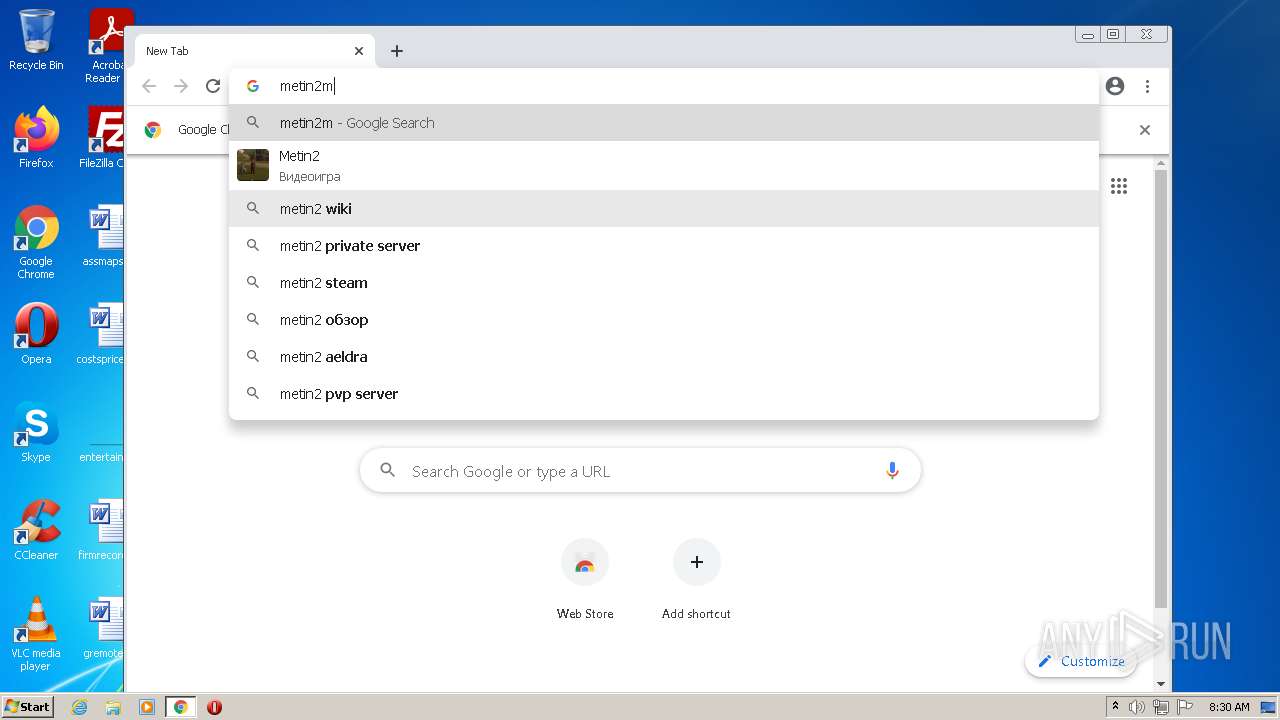
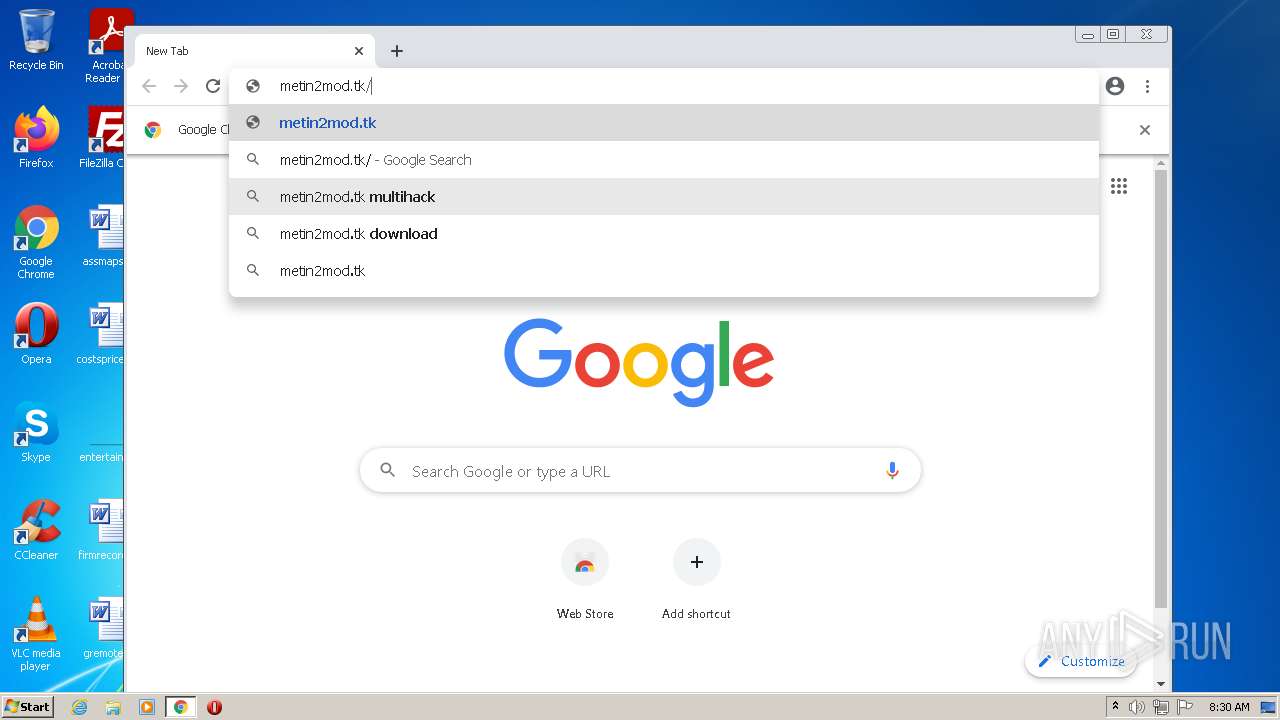
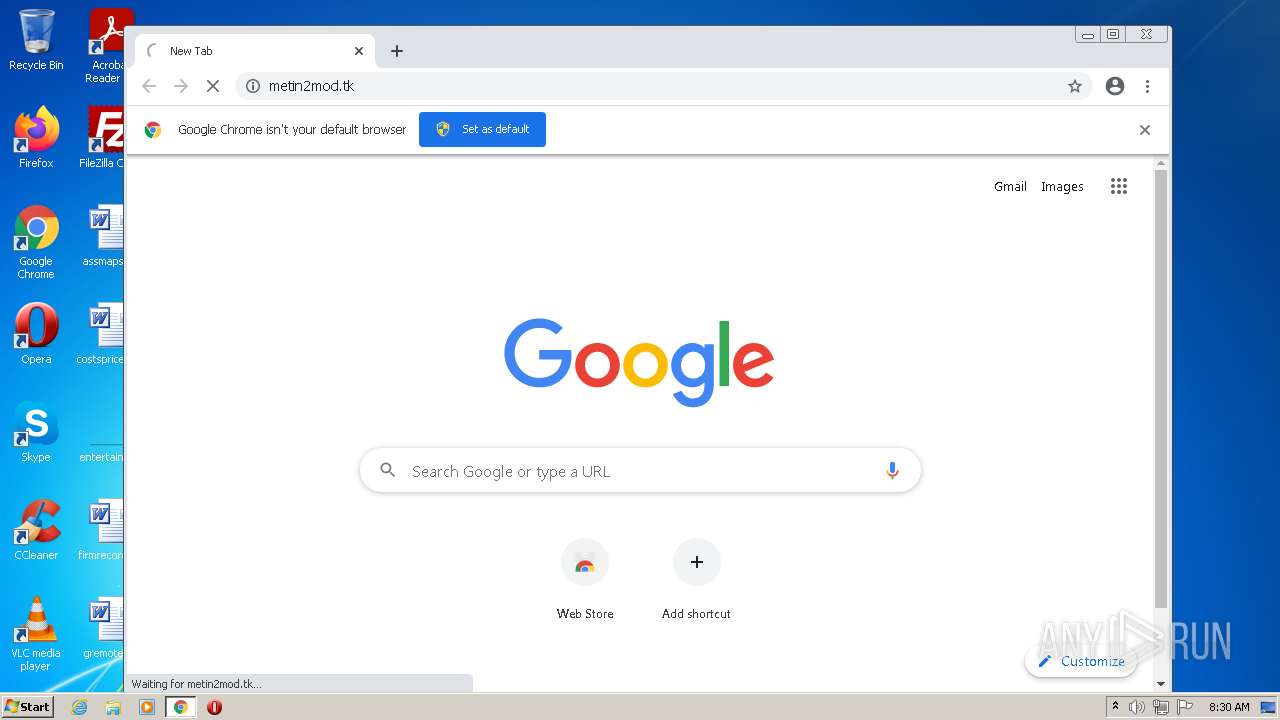
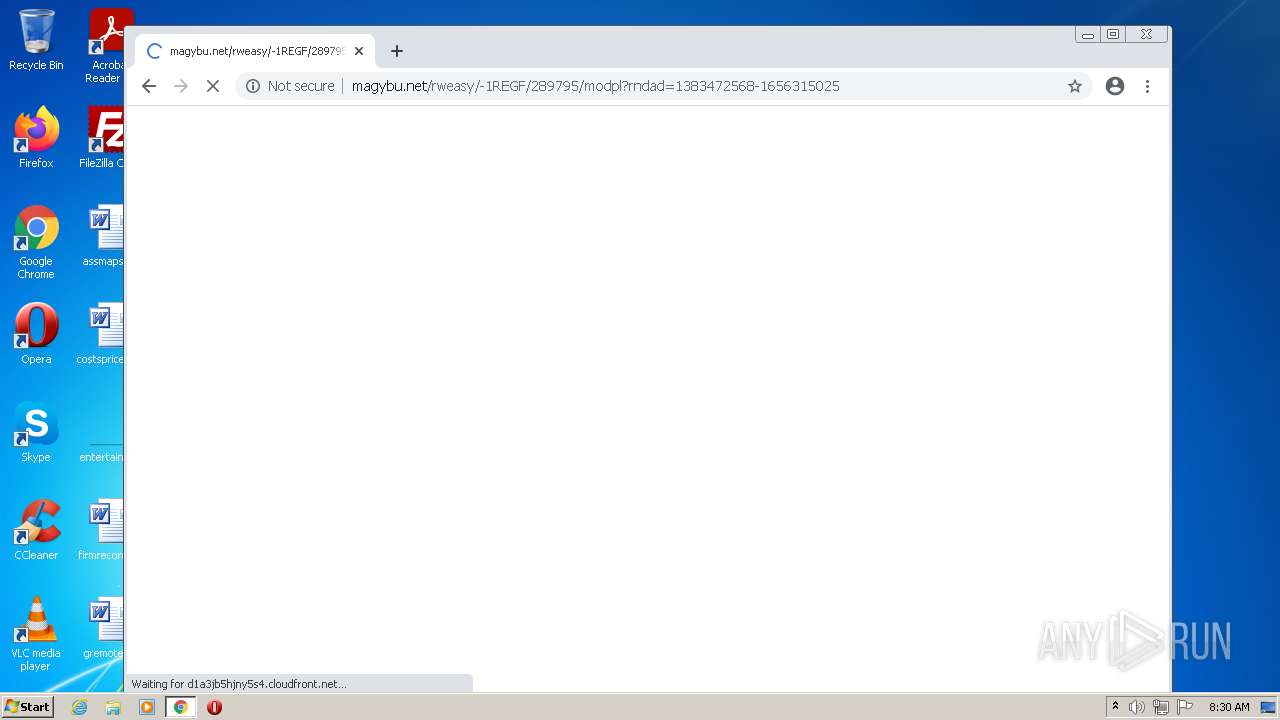
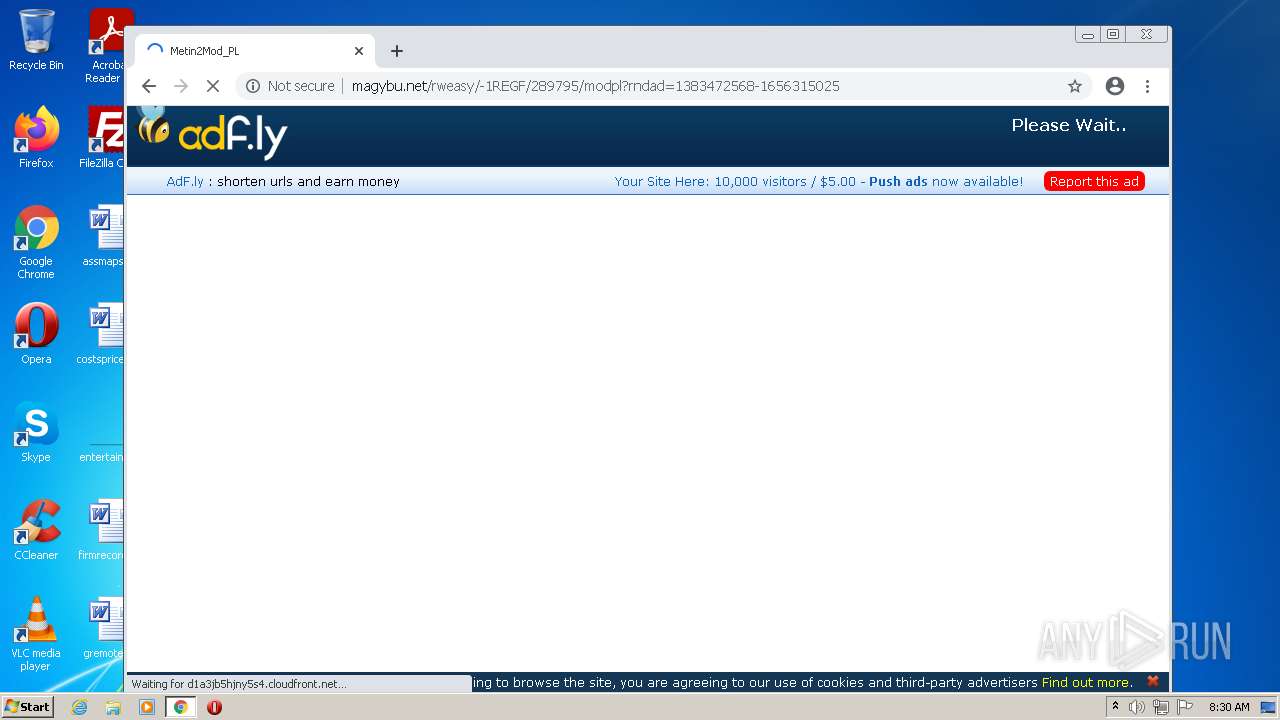
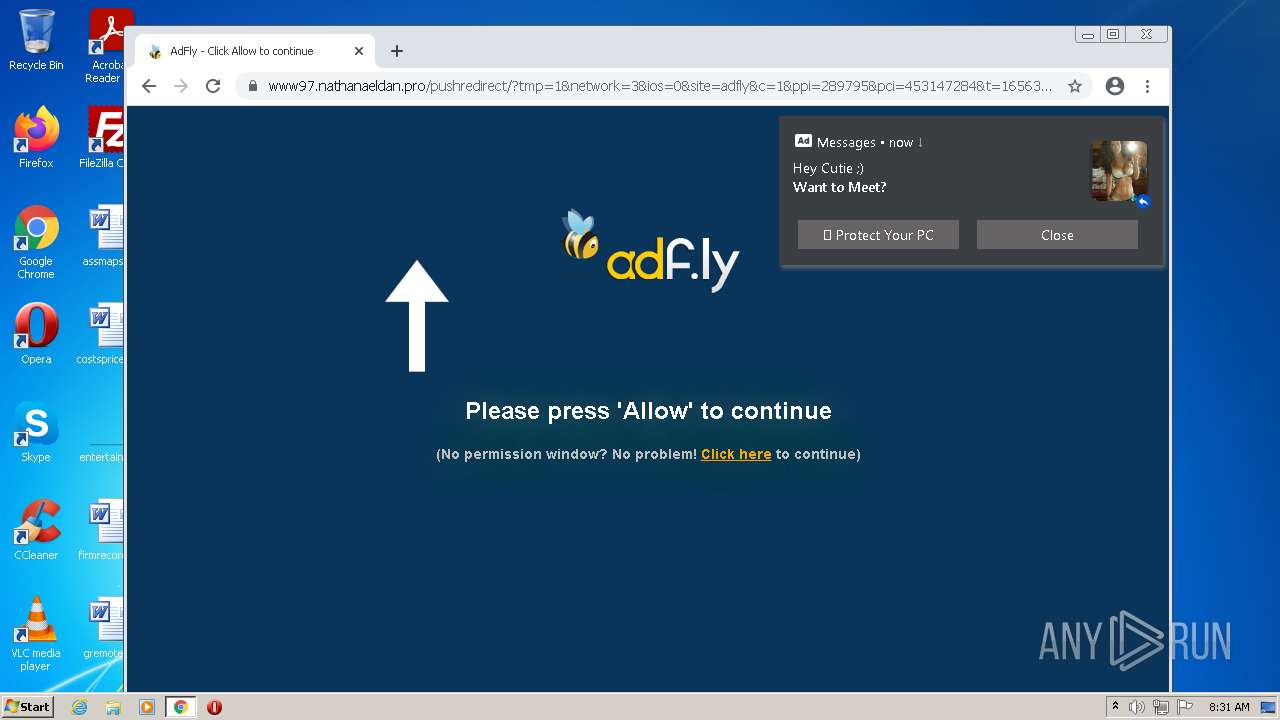
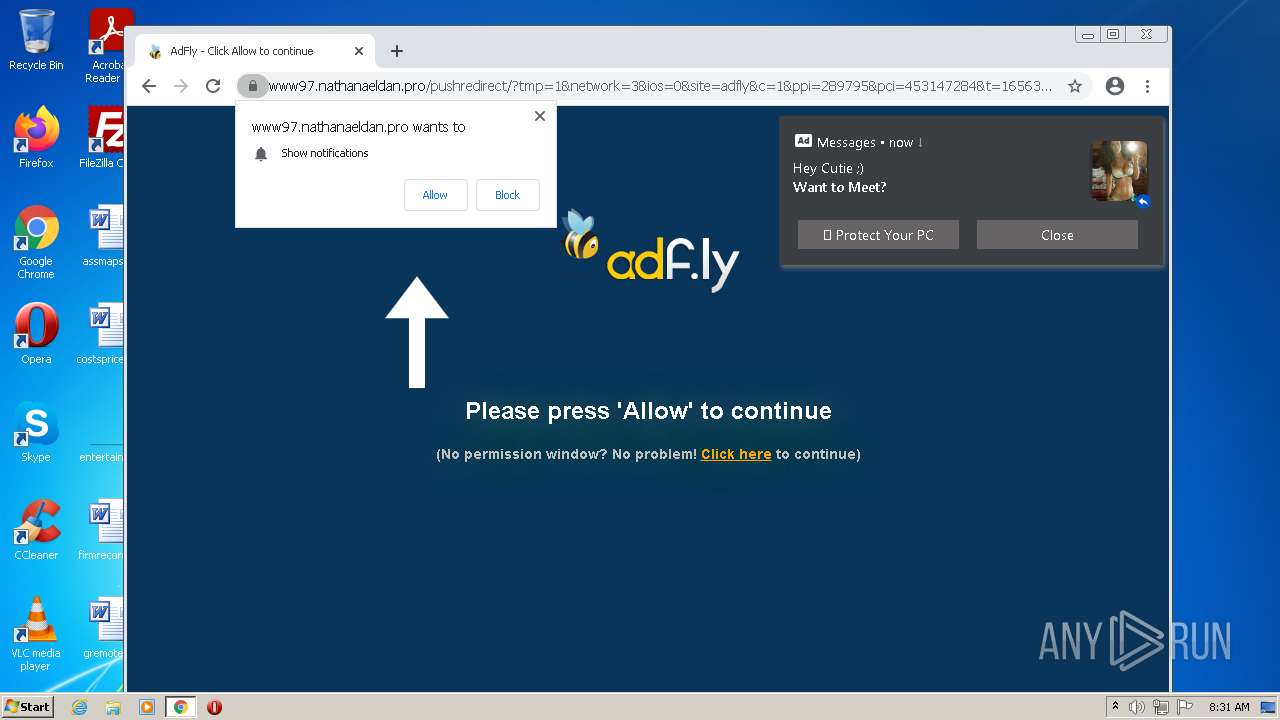
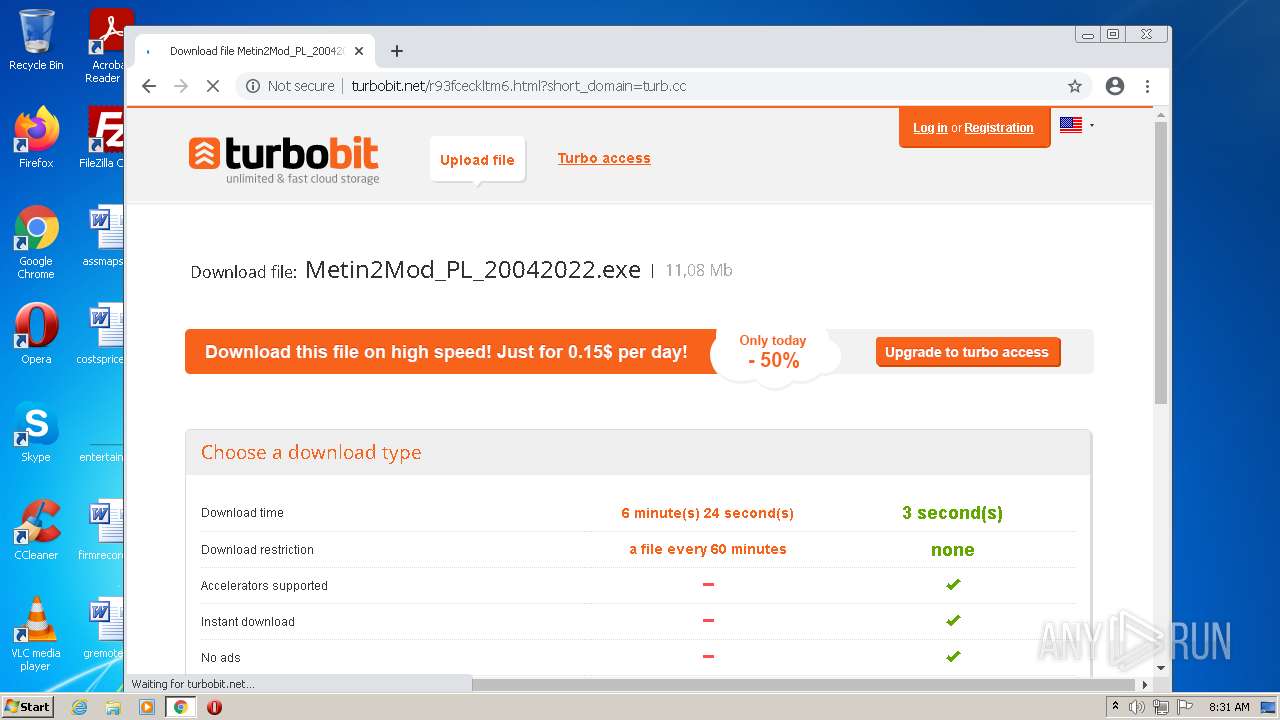
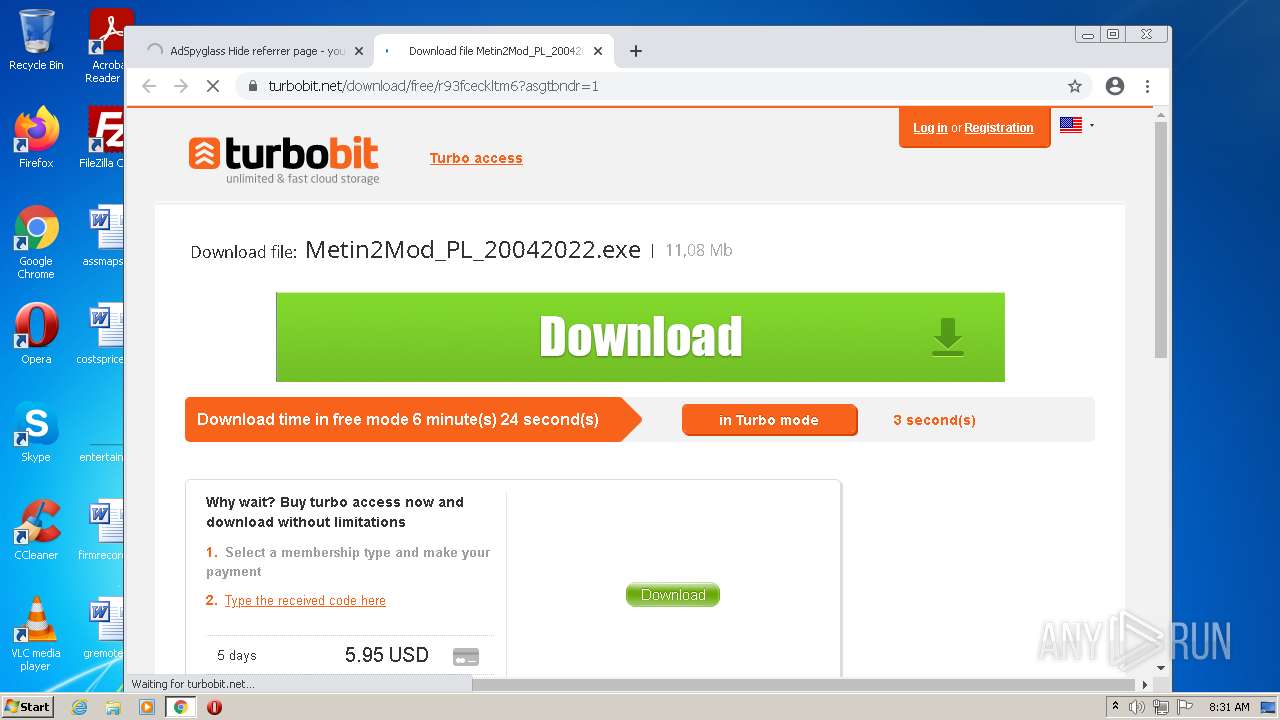
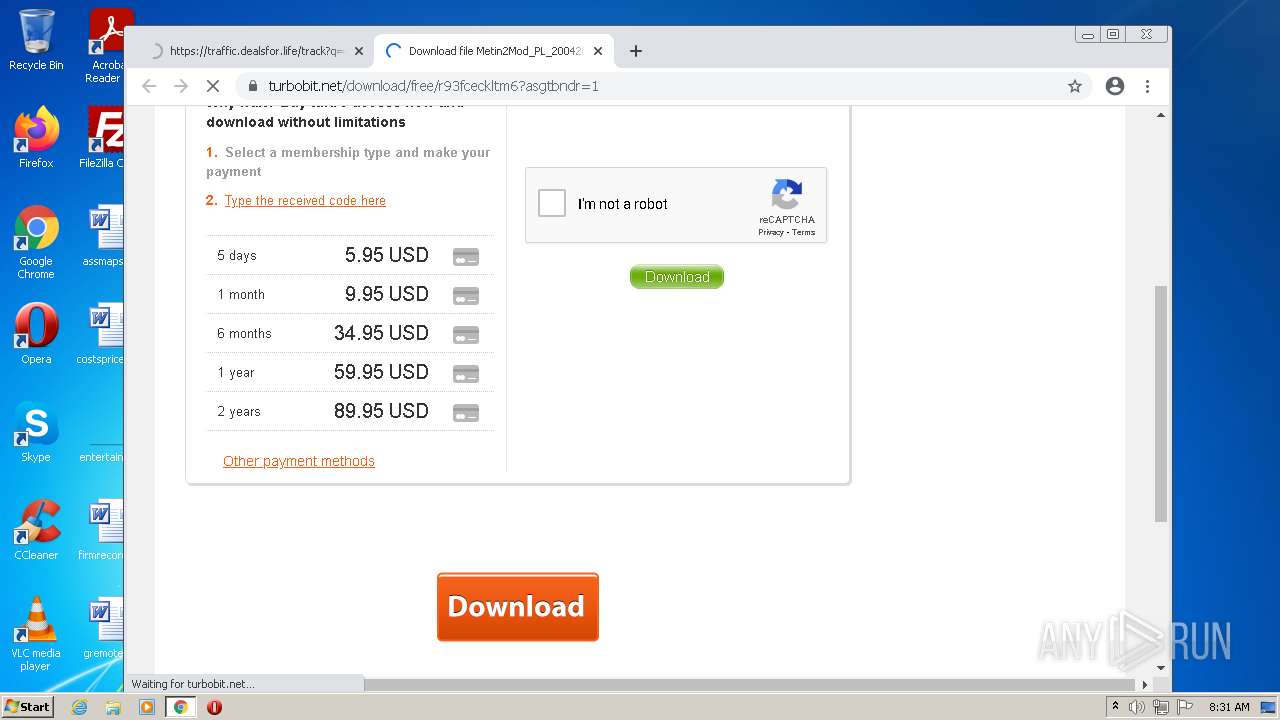
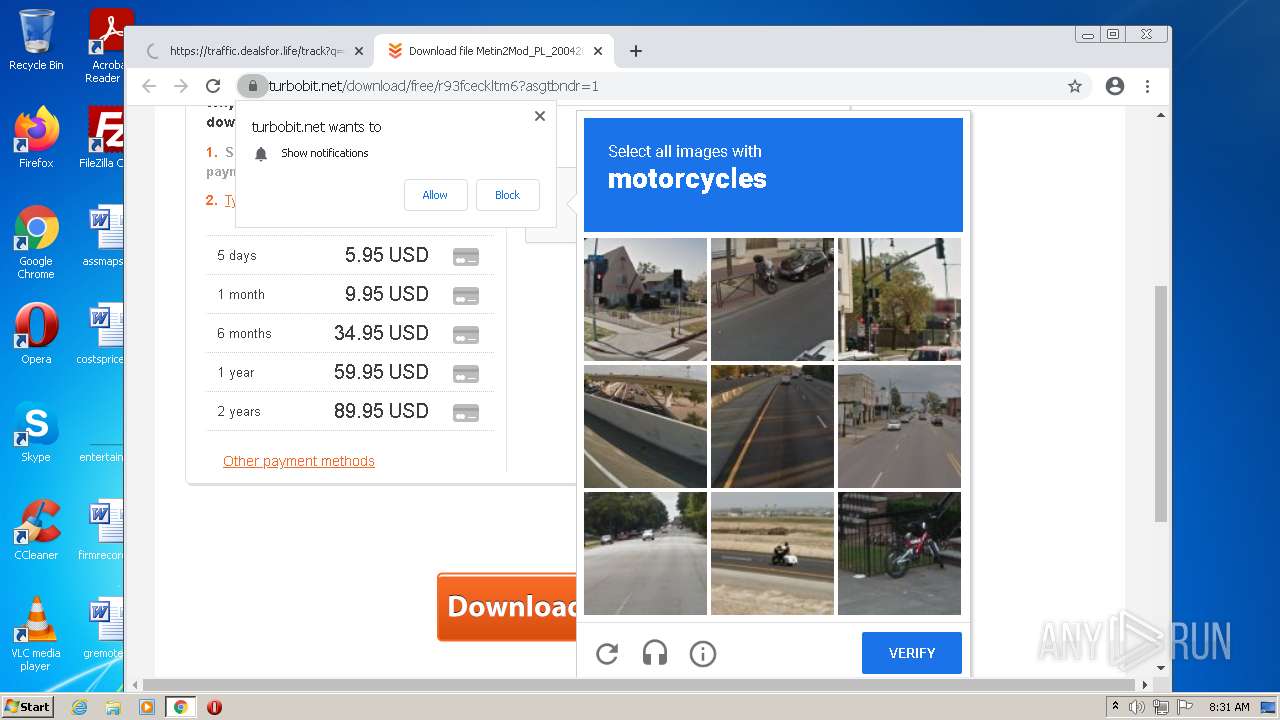
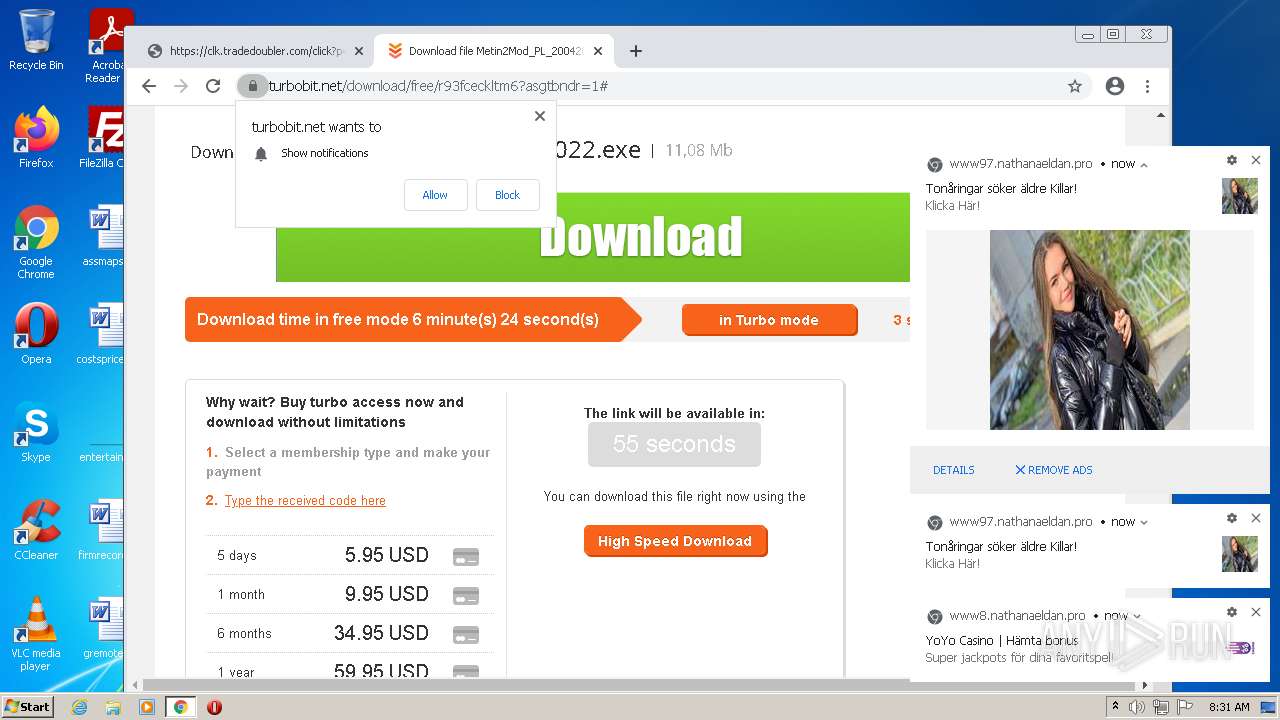
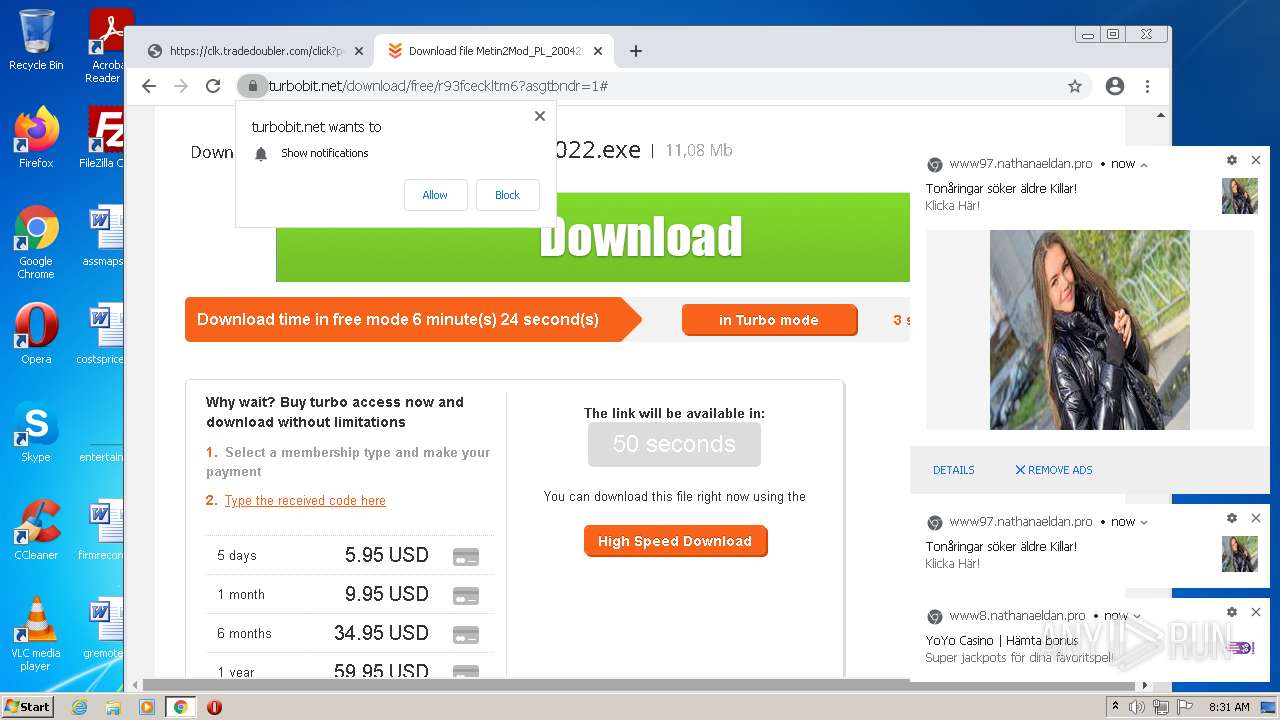
| URL: | https://turbobit.net/download/free/r93fceckitm6 |
| Full analysis: | https://app.any.run/tasks/a04dbb67-dec9-483b-a760-7e753ad16968 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 07:29:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 4930D76EEC8FBD9A9524A038085568A3 |
| SHA1: | 8861C1CB8BD42A5596306EE19D949327F3CF01D5 |
| SHA256: | 6D1A1AED69618FC9F204E32D1D1CEEF8214D7EBFF2EAB6B6ACB3E63B58DE3C92 |
| SSDEEP: | 3:N8YMZL0vXDCc:2YMZAv+c |
MALICIOUS
Drops executable file immediately after starts
- chrome.exe (PID: 3912)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 3912)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2848)
Drops a file with a compile date too recent
- chrome.exe (PID: 3912)
INFO
Checks supported languages
- iexplore.exe (PID: 2848)
- chrome.exe (PID: 2092)
- chrome.exe (PID: 1392)
- chrome.exe (PID: 3056)
- iexplore.exe (PID: 2520)
- chrome.exe (PID: 3912)
- chrome.exe (PID: 3808)
- chrome.exe (PID: 3316)
- chrome.exe (PID: 2708)
- chrome.exe (PID: 1180)
- chrome.exe (PID: 4072)
- chrome.exe (PID: 4032)
- chrome.exe (PID: 704)
- chrome.exe (PID: 1248)
- chrome.exe (PID: 3728)
- chrome.exe (PID: 3596)
- chrome.exe (PID: 2264)
- chrome.exe (PID: 756)
- chrome.exe (PID: 2296)
- chrome.exe (PID: 1376)
- chrome.exe (PID: 2576)
- chrome.exe (PID: 3016)
- chrome.exe (PID: 2340)
- chrome.exe (PID: 1016)
- chrome.exe (PID: 3308)
- chrome.exe (PID: 4000)
- chrome.exe (PID: 3744)
- chrome.exe (PID: 3956)
- chrome.exe (PID: 576)
- chrome.exe (PID: 3980)
- chrome.exe (PID: 3920)
- chrome.exe (PID: 2844)
- chrome.exe (PID: 2988)
- chrome.exe (PID: 3604)
- chrome.exe (PID: 2700)
- chrome.exe (PID: 1236)
- chrome.exe (PID: 2908)
- chrome.exe (PID: 3952)
- chrome.exe (PID: 1168)
- chrome.exe (PID: 3428)
- chrome.exe (PID: 2240)
- chrome.exe (PID: 2548)
- chrome.exe (PID: 2640)
- chrome.exe (PID: 3016)
- chrome.exe (PID: 3096)
- chrome.exe (PID: 1360)
- chrome.exe (PID: 892)
- chrome.exe (PID: 1020)
- chrome.exe (PID: 124)
- chrome.exe (PID: 2640)
- chrome.exe (PID: 2564)
- chrome.exe (PID: 3528)
- chrome.exe (PID: 2660)
- chrome.exe (PID: 3228)
- chrome.exe (PID: 704)
- chrome.exe (PID: 2924)
- chrome.exe (PID: 2480)
- chrome.exe (PID: 1072)
- chrome.exe (PID: 3476)
Reads the computer name
- iexplore.exe (PID: 2520)
- iexplore.exe (PID: 2848)
- chrome.exe (PID: 3912)
- chrome.exe (PID: 1392)
- chrome.exe (PID: 3808)
- chrome.exe (PID: 2708)
- chrome.exe (PID: 2576)
- chrome.exe (PID: 2988)
- chrome.exe (PID: 1360)
- chrome.exe (PID: 3428)
- chrome.exe (PID: 2640)
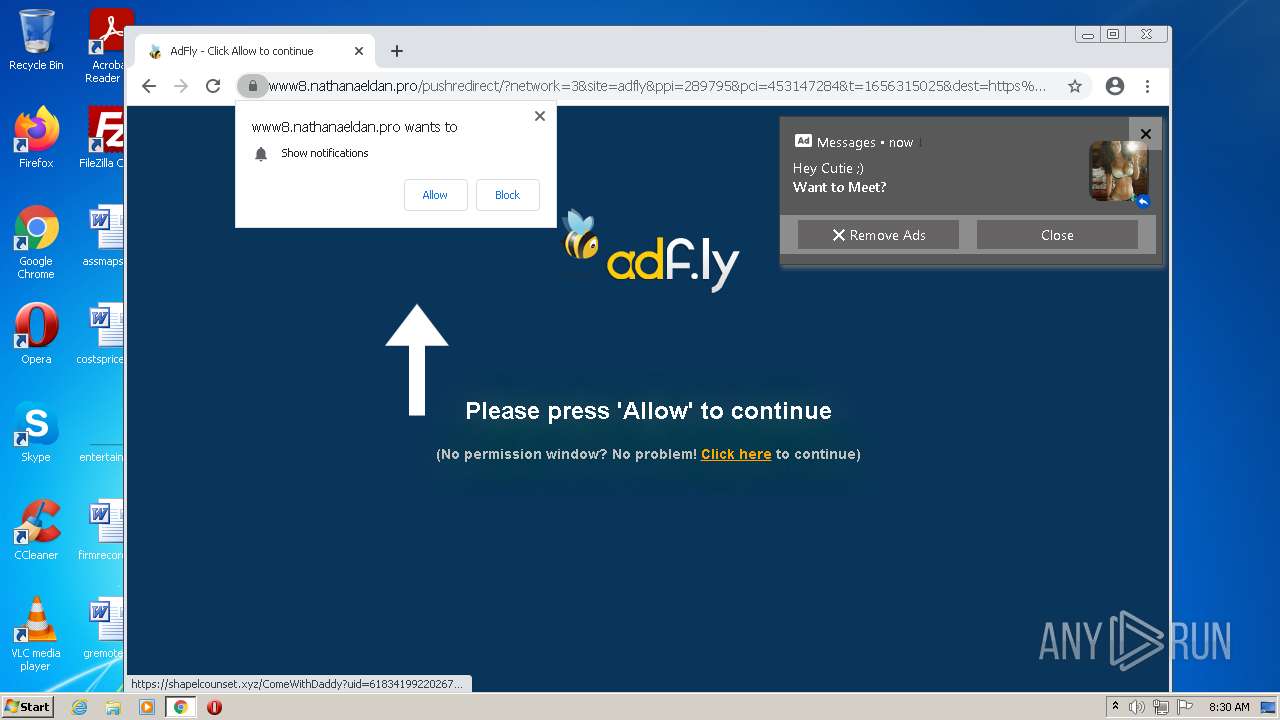
Changes internet zones settings
- iexplore.exe (PID: 2520)
Application launched itself
- iexplore.exe (PID: 2520)
- chrome.exe (PID: 3912)
Reads the hosts file
- chrome.exe (PID: 3808)
- chrome.exe (PID: 3912)
Reads the date of Windows installation
- iexplore.exe (PID: 2520)
- chrome.exe (PID: 1360)
Manual execution by user
- chrome.exe (PID: 3912)
Reads settings of System Certificates
- chrome.exe (PID: 3808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
94
Monitored processes
59
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1032,2480668069239614406,1739415972861989344,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3520 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 576 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,2480668069239614406,1739415972861989344,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=23 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3500 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 704 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1032,2480668069239614406,1739415972861989344,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2828 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 704 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1032,2480668069239614406,1739415972861989344,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=952 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 756 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1032,2480668069239614406,1739415972861989344,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3296 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 892 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,2480668069239614406,1739415972861989344,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=45 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4048 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,2480668069239614406,1739415972861989344,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=28 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3316 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,2480668069239614406,1739415972861989344,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=44 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1968 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1072 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1032,2480668069239614406,1739415972861989344,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2624 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,2480668069239614406,1739415972861989344,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=36 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3864 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
14 949
Read events
14 721
Write events
219
Delete events
9
Modification events
| (PID) Process: | (2520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30968311 | |||
| (PID) Process: | (2520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30968311 | |||
| (PID) Process: | (2520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2520) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
250
Text files
183
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3912 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-62B95C7A-F48.pma | — | |
MD5:— | SHA256:— | |||
| 2520 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFFD119528626F7481.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2520 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{42C873D0-1D90-11EB-BA2C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2520 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE3A3E313B90B0FBF.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2520 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{F18B2C2C-F5EA-11EC-AE3F-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2520 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{F18B2C29-F5EA-11EC-AE3F-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2520 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFED6AE6BF4009BFCD.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2520 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFD1A87D46C54DEF7A.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2520 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{F18B2C2B-F5EA-11EC-AE3F-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 3912 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:8FF312A95D60ED89857FEB720D80D4E1 | SHA256:946A57FAFDD28C3164D5AB8AB4971B21BD5EC5BFFF7554DBF832CB58CC37700B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
79
TCP/UDP connections
171
DNS requests
99
Threats
41
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
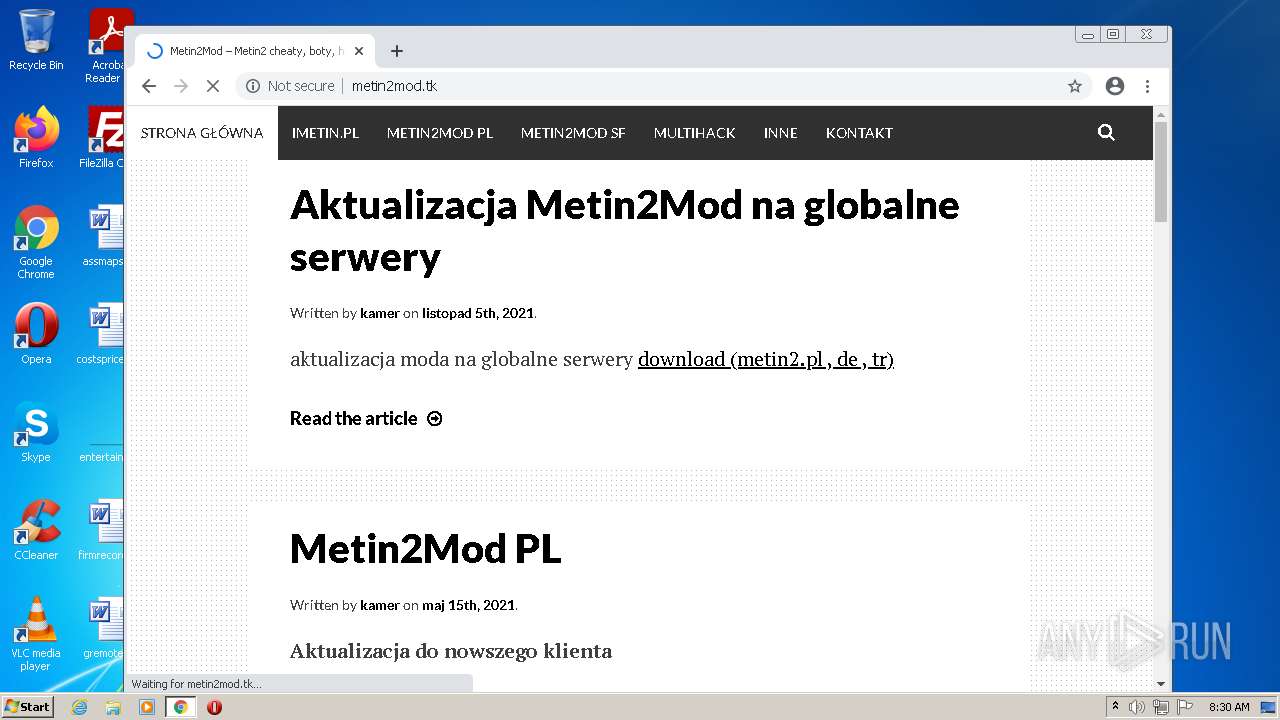
3808 | chrome.exe | GET | 200 | 46.105.98.67:80 | http://metin2mod.tk/wp-content/themes/simone/style.css?ver=5.1.13 | FR | text | 8.72 Kb | suspicious |
3808 | chrome.exe | GET | 200 | 46.105.98.67:80 | http://metin2mod.tk/ | FR | html | 5.56 Kb | suspicious |
3808 | chrome.exe | GET | 200 | 46.105.98.67:80 | http://metin2mod.tk/wp-content/themes/simone/layouts/content-sidebar.css?ver=5.1.13 | FR | text | 694 b | suspicious |
3808 | chrome.exe | GET | 200 | 216.58.212.162:80 | http://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js | US | text | 55.1 Kb | whitelisted |
3808 | chrome.exe | GET | 200 | 46.105.98.67:80 | http://metin2mod.tk/wp-content/plugins/popups/public/assets/css/public.css?ver=1.9.3.8 | FR | text | 1.50 Kb | suspicious |
3808 | chrome.exe | GET | 200 | 46.105.98.67:80 | http://metin2mod.tk/wp-includes/css/dist/block-library/style.min.css?ver=5.1.13 | FR | text | 4.17 Kb | suspicious |
3808 | chrome.exe | GET | 200 | 46.105.98.67:80 | http://metin2mod.tk/wp-includes/js/jquery/jquery-migrate.min.js?ver=1.4.1 | FR | text | 3.92 Kb | suspicious |
3808 | chrome.exe | GET | 200 | 46.105.98.67:80 | http://metin2mod.tk/wp-includes/js/masonry.min.js?ver=3.3.2 | FR | text | 8.32 Kb | suspicious |
3808 | chrome.exe | GET | 200 | 46.105.98.67:80 | http://metin2mod.tk/wp-content/themes/simone/fonts/font-awesome/css/font-awesome.min.css?ver=5.1.13 | FR | text | 6.10 Kb | suspicious |
3808 | chrome.exe | GET | 200 | 46.105.98.67:80 | http://metin2mod.tk/wp-content/themes/simone/js/hide-search.js?ver=20120206 | FR | text | 183 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2848 | iexplore.exe | 5.45.76.184:443 | turbobit.net | Serverius Holding B.V. | NL | unknown |
3808 | chrome.exe | 142.250.185.109:443 | accounts.google.com | Google Inc. | US | suspicious |
3808 | chrome.exe | 142.250.185.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3808 | chrome.exe | 142.250.184.238:443 | clients2.google.com | Google Inc. | US | whitelisted |
3808 | chrome.exe | 142.250.186.100:443 | www.google.com | Google Inc. | US | whitelisted |
— | — | 142.250.185.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
— | — | 142.250.186.100:443 | www.google.com | Google Inc. | US | whitelisted |
— | — | 142.250.185.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3808 | chrome.exe | 142.250.185.131:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3808 | chrome.exe | 142.250.184.195:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
turbobit.net |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.google.com |
| whitelisted |
www.google.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
3808 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
3808 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
3808 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
3808 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
3808 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
3808 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
3808 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
3808 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
3808 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |