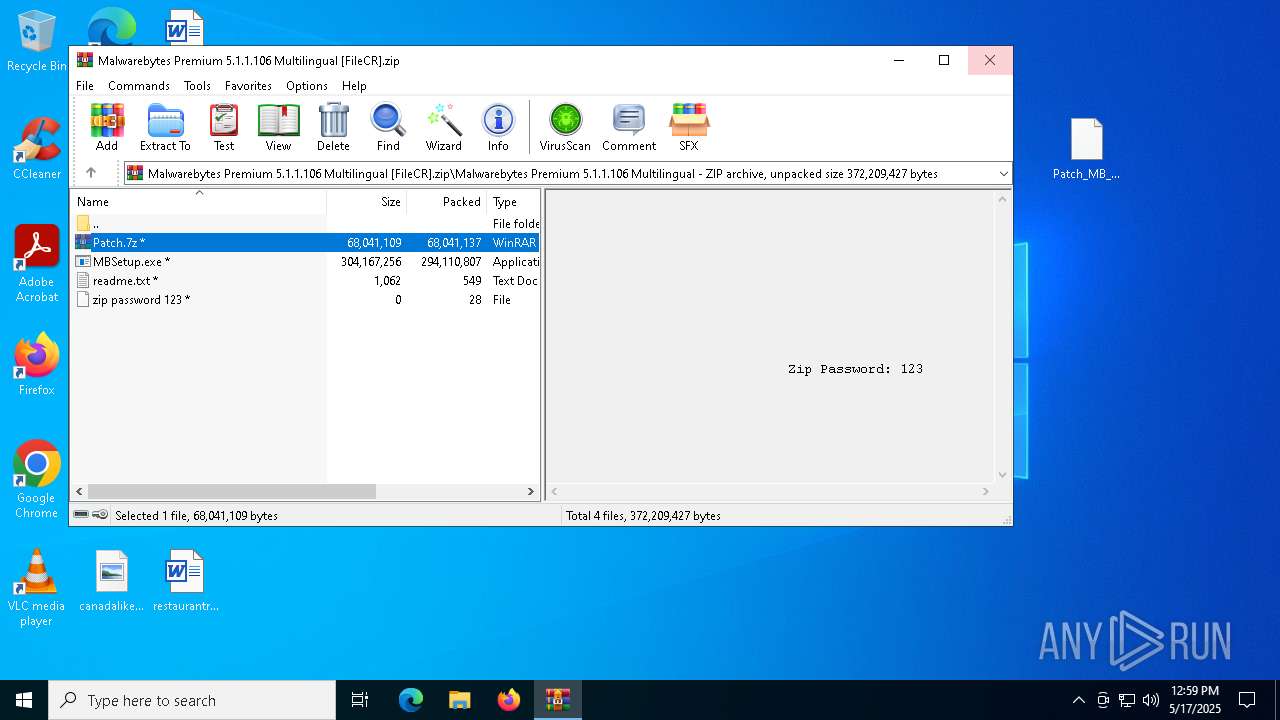
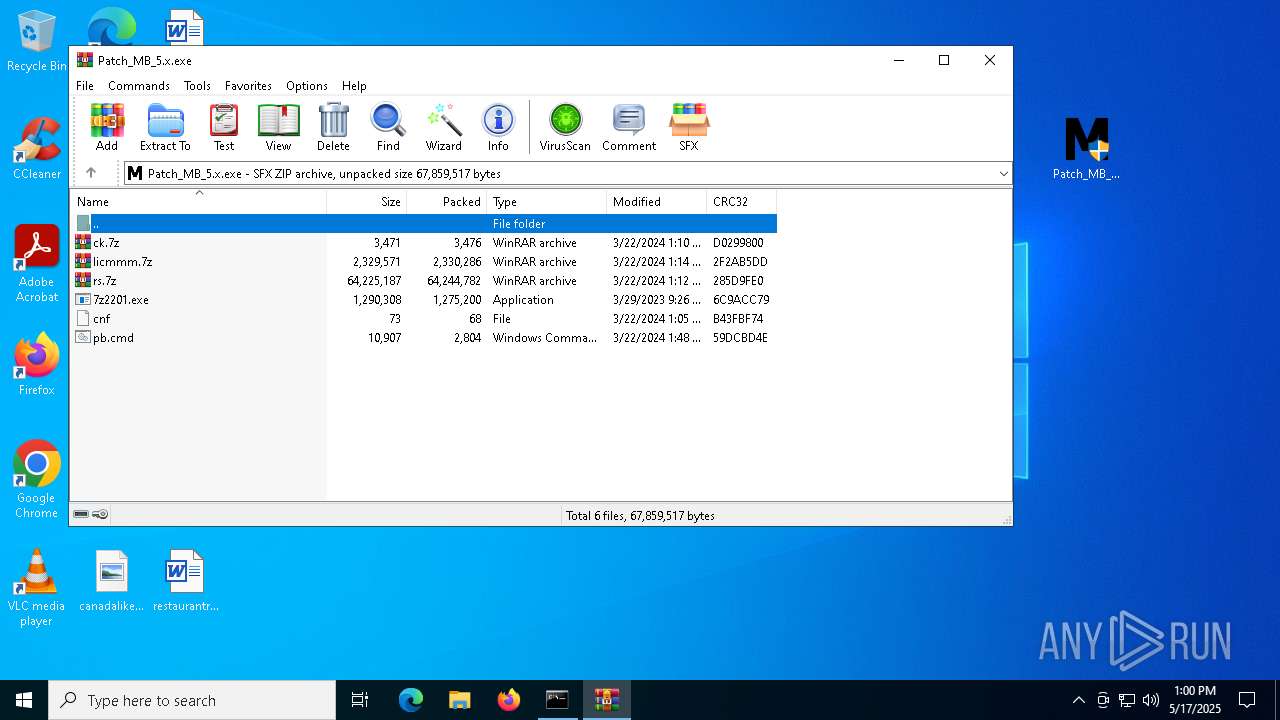
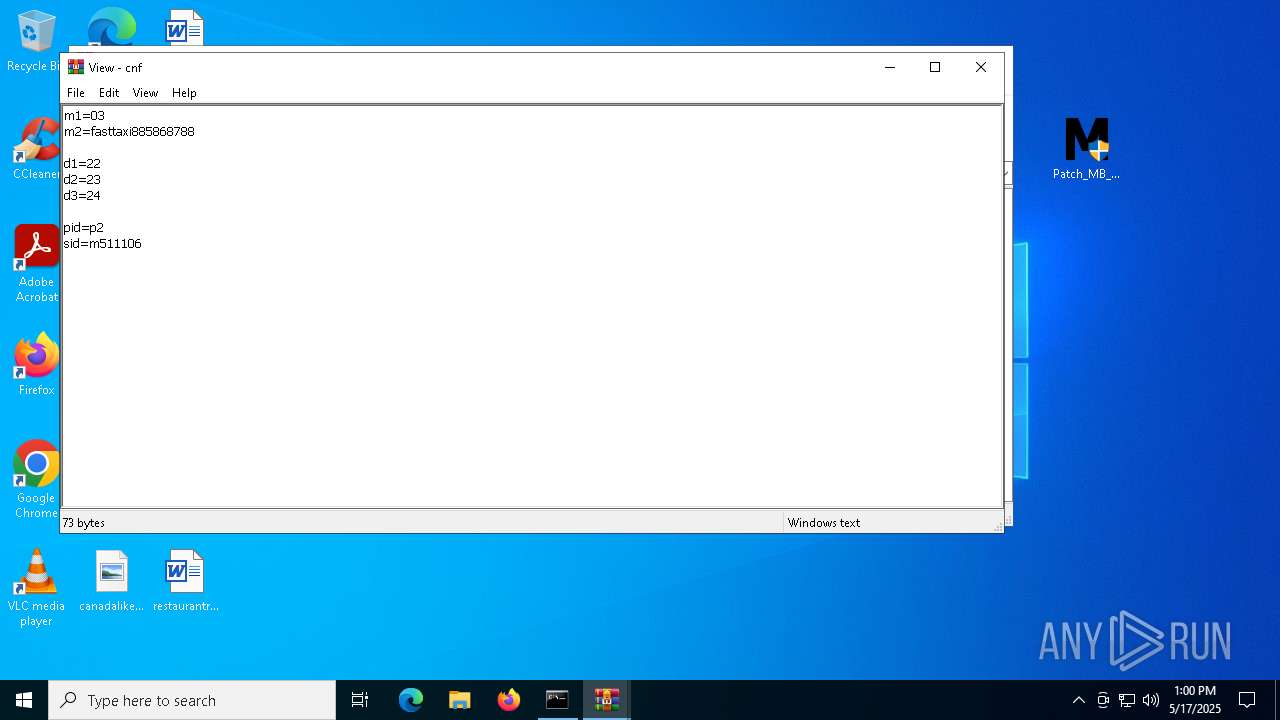
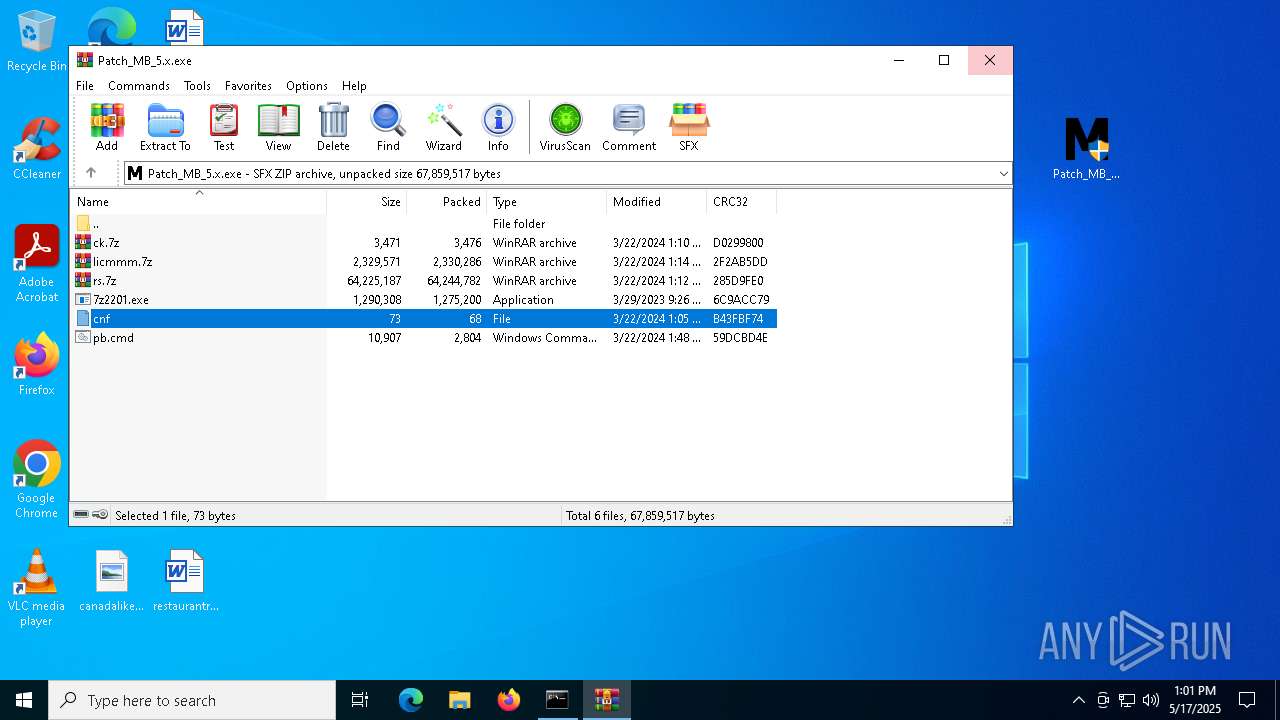
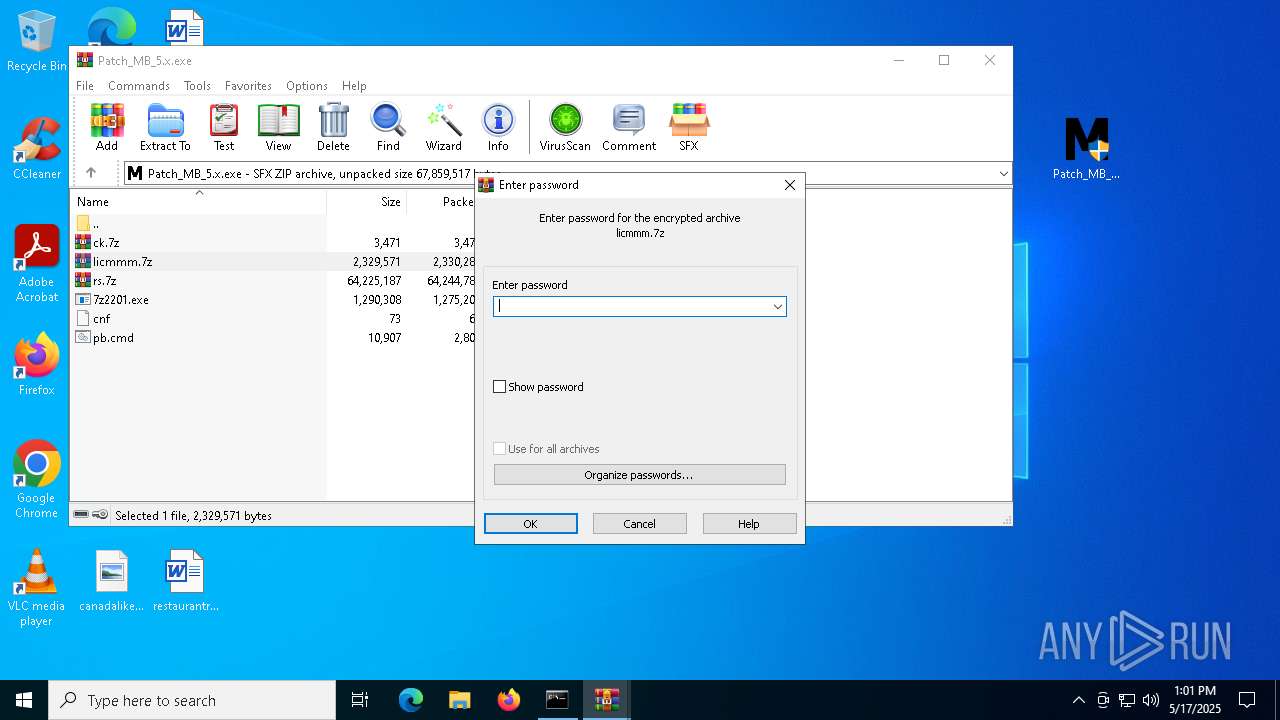
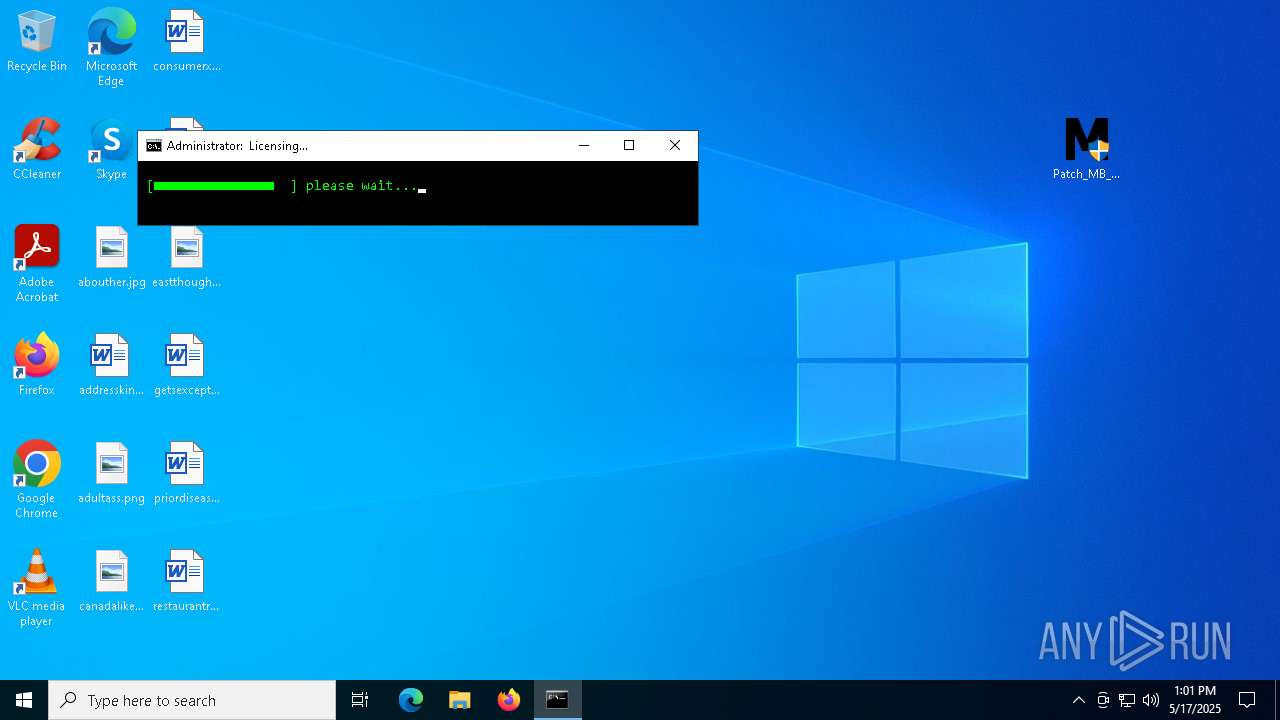
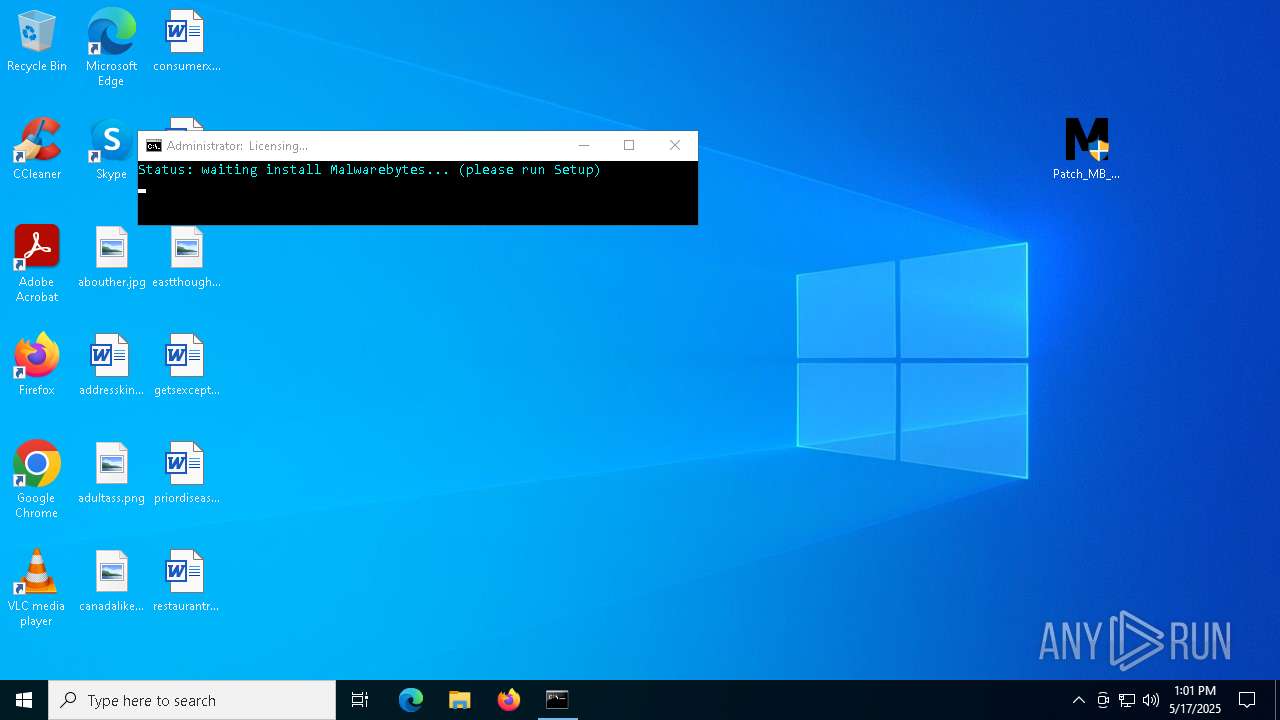
| URL: | https://filecr.com/windows/malwarebytes-premium/ |
| Full analysis: | https://app.any.run/tasks/ed7f0d89-d079-4f9a-a1b4-203fb8a000ad |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 12:56:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 27FAA7448D11F759BD96EB7E0B5199AF |
| SHA1: | 5E10630D2A19F71F4C06080297F56D2C4F7723D2 |
| SHA256: | 6D16BC70CF8FBB6D7FCFE1005B8DE76E4CCEC0855D1BA0AE3D7AA30EC9610C21 |
| SSDEEP: | 3:N8JTCqXYzKAWIK:2hJXYmAWIK |
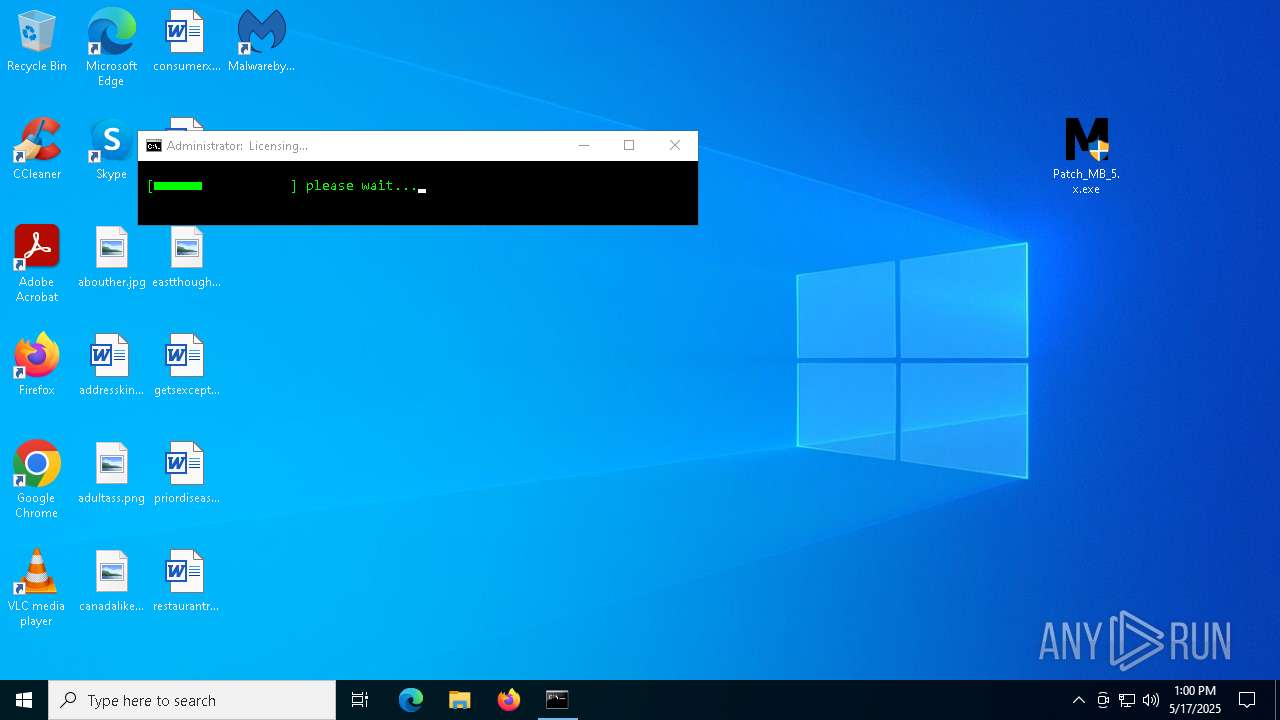
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- _iu14D2N.tmp (PID: 1004)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 7584)
- tasklist.exe (PID: 7836)
Changes Windows Defender settings
- cmd.exe (PID: 7036)
Adds process to the Windows Defender exclusion list
- cmd.exe (PID: 7036)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 7036)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6108)
Executing commands from a ".bat" file
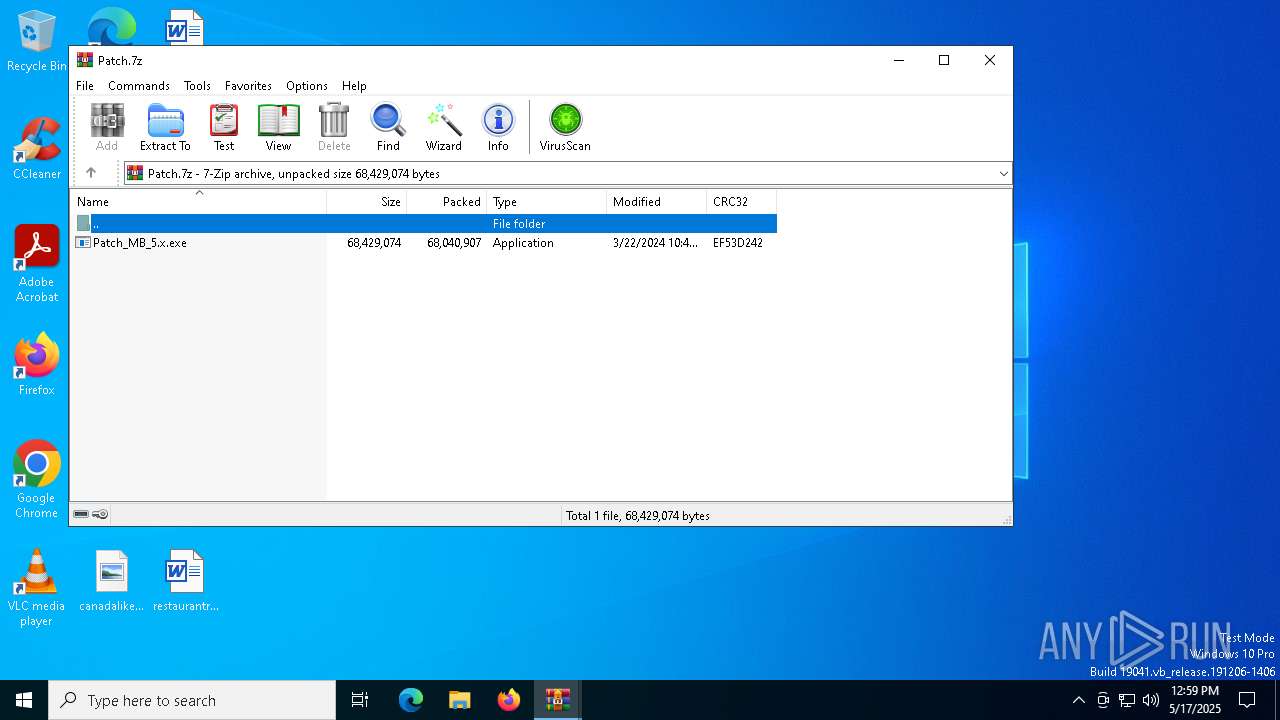
- Patch_MB_5.x.exe (PID: 3900)
- cmd.exe (PID: 2140)
Application launched itself
- WinRAR.exe (PID: 6108)
- cmd.exe (PID: 2140)
- cmd.exe (PID: 4776)
- cmd.exe (PID: 7104)
- cmd.exe (PID: 7036)
- WinRAR.exe (PID: 3032)
- VC_redist.x86.exe (PID: 8128)
- VC_redist.x86.exe (PID: 7528)
Executable content was dropped or overwritten
- 7z2201.exe (PID: 3156)
- Patch_MB_5.x.exe (PID: 3900)
- rs.exe (PID: 5972)
- rs.tmp (PID: 5864)
- MBAMService.exe (PID: 7232)
- MBAMService.exe (PID: 1088)
- unins000.exe (PID: 3796)
- _iu14D2N.tmp (PID: 1004)
- VC_redist.x86.exe (PID: 8052)
- 7z.exe (PID: 7684)
- VC_redist.x86.exe (PID: 1628)
- VC_redist.x86.exe (PID: 5416)
- VC_redist.x86.exe (PID: 7528)
- VC_redist.x86.exe (PID: 7792)
Starts CMD.EXE for commands execution
- Patch_MB_5.x.exe (PID: 3900)
- cmd.exe (PID: 2140)
- cmd.exe (PID: 4776)
- cmd.exe (PID: 7104)
- cmd.exe (PID: 7036)
- wzone.exe (PID: 2340)
Drops 7-zip archiver for unpacking
- Patch_MB_5.x.exe (PID: 3900)
- 7z2201.exe (PID: 3156)
- rs.tmp (PID: 5864)
The executable file from the user directory is run by the CMD process
- 7z2201.exe (PID: 3156)
- VC_redist.x86.exe (PID: 1628)
- wzone.exe (PID: 2340)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2140)
- cmd.exe (PID: 7036)
Executing commands from ".cmd" file
- cmd.exe (PID: 2140)
- cmd.exe (PID: 4776)
- wzone.exe (PID: 2340)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 8024)
- cmd.exe (PID: 8012)
- cmd.exe (PID: 720)
- cmd.exe (PID: 2084)
- cmd.exe (PID: 8024)
- cmd.exe (PID: 7824)
- cmd.exe (PID: 8056)
Starts application with an unusual extension
- cmd.exe (PID: 4776)
- unins000.exe (PID: 3796)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2140)
- cmd.exe (PID: 7036)
Starts process via Powershell
- powershell.exe (PID: 4652)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 5528)
The process drops C-runtime libraries
- rs.tmp (PID: 5864)
- msiexec.exe (PID: 4284)
Process drops legitimate windows executable
- rs.tmp (PID: 5864)
- _iu14D2N.tmp (PID: 1004)
- VC_redist.x86.exe (PID: 1628)
- VC_redist.x86.exe (PID: 8052)
- 7z.exe (PID: 7684)
- VC_redist.x86.exe (PID: 5416)
- msiexec.exe (PID: 4284)
- VC_redist.x86.exe (PID: 7792)
Drops a system driver (possible attempt to evade defenses)
- MBAMService.exe (PID: 7232)
- rs.tmp (PID: 5864)
- MBAMService.exe (PID: 1088)
Executes as Windows Service
- MBAMService.exe (PID: 1088)
- VSSVC.exe (PID: 5204)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4776)
- cmd.exe (PID: 2140)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2140)
- cmd.exe (PID: 7036)
Get information on the list of running processes
- cmd.exe (PID: 7740)
- cmd.exe (PID: 2140)
- cmd.exe (PID: 5352)
- cmd.exe (PID: 1180)
- cmd.exe (PID: 7584)
- cmd.exe (PID: 7156)
- cmd.exe (PID: 4376)
- cmd.exe (PID: 4776)
- cmd.exe (PID: 2344)
- cmd.exe (PID: 7476)
- cmd.exe (PID: 6652)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 1660)
- cmd.exe (PID: 7304)
- cmd.exe (PID: 8064)
- cmd.exe (PID: 5868)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 6248)
- cmd.exe (PID: 7100)
- cmd.exe (PID: 1004)
- cmd.exe (PID: 4052)
- cmd.exe (PID: 5708)
- cmd.exe (PID: 4672)
- cmd.exe (PID: 7992)
- cmd.exe (PID: 7964)
- cmd.exe (PID: 2568)
- cmd.exe (PID: 8028)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 5044)
- cmd.exe (PID: 7220)
- cmd.exe (PID: 660)
- cmd.exe (PID: 5588)
- cmd.exe (PID: 5796)
- cmd.exe (PID: 7700)
- cmd.exe (PID: 832)
- cmd.exe (PID: 5348)
- cmd.exe (PID: 3264)
- cmd.exe (PID: 8072)
- cmd.exe (PID: 7496)
- cmd.exe (PID: 7184)
- cmd.exe (PID: 7888)
- cmd.exe (PID: 644)
- cmd.exe (PID: 7308)
- cmd.exe (PID: 4784)
- cmd.exe (PID: 7528)
- cmd.exe (PID: 7840)
- cmd.exe (PID: 5640)
- cmd.exe (PID: 5624)
- cmd.exe (PID: 6192)
- cmd.exe (PID: 6724)
- cmd.exe (PID: 2316)
- cmd.exe (PID: 6480)
- cmd.exe (PID: 4000)
- cmd.exe (PID: 2612)
- cmd.exe (PID: 1704)
- cmd.exe (PID: 3748)
- cmd.exe (PID: 3416)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 232)
- cmd.exe (PID: 7408)
- cmd.exe (PID: 632)
- cmd.exe (PID: 5952)
- cmd.exe (PID: 7740)
- cmd.exe (PID: 7368)
- cmd.exe (PID: 3156)
- cmd.exe (PID: 7608)
- cmd.exe (PID: 444)
- cmd.exe (PID: 7908)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 7640)
- cmd.exe (PID: 8032)
- cmd.exe (PID: 5484)
- cmd.exe (PID: 8024)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 1116)
- cmd.exe (PID: 2780)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 1020)
- cmd.exe (PID: 7428)
- cmd.exe (PID: 7552)
- cmd.exe (PID: 4736)
- cmd.exe (PID: 4040)
- cmd.exe (PID: 920)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 5740)
- cmd.exe (PID: 8116)
- cmd.exe (PID: 7988)
- cmd.exe (PID: 1272)
- cmd.exe (PID: 7640)
- cmd.exe (PID: 8032)
- cmd.exe (PID: 8156)
- cmd.exe (PID: 2268)
- cmd.exe (PID: 5484)
- cmd.exe (PID: 2612)
- cmd.exe (PID: 3804)
- cmd.exe (PID: 4284)
- cmd.exe (PID: 3748)
- cmd.exe (PID: 3416)
- cmd.exe (PID: 6612)
- cmd.exe (PID: 3080)
- cmd.exe (PID: 1548)
- cmd.exe (PID: 5452)
- cmd.exe (PID: 1544)
- cmd.exe (PID: 7192)
- cmd.exe (PID: 7328)
- cmd.exe (PID: 3032)
- cmd.exe (PID: 5408)
- cmd.exe (PID: 7680)
- cmd.exe (PID: 6584)
- cmd.exe (PID: 4448)
- cmd.exe (PID: 7272)
- cmd.exe (PID: 7844)
- cmd.exe (PID: 6272)
- cmd.exe (PID: 8016)
- cmd.exe (PID: 7816)
- cmd.exe (PID: 4308)
- cmd.exe (PID: 2796)
- cmd.exe (PID: 6576)
- cmd.exe (PID: 788)
- cmd.exe (PID: 5936)
- cmd.exe (PID: 4348)
- cmd.exe (PID: 5600)
- cmd.exe (PID: 1168)
- cmd.exe (PID: 7324)
- cmd.exe (PID: 1700)
- cmd.exe (PID: 1504)
- cmd.exe (PID: 6744)
- cmd.exe (PID: 5976)
- cmd.exe (PID: 7480)
- cmd.exe (PID: 7560)
- cmd.exe (PID: 1616)
- cmd.exe (PID: 2848)
- cmd.exe (PID: 7216)
- cmd.exe (PID: 4244)
- cmd.exe (PID: 7232)
- cmd.exe (PID: 3164)
- cmd.exe (PID: 7192)
- cmd.exe (PID: 7292)
- cmd.exe (PID: 5132)
- cmd.exe (PID: 7680)
- cmd.exe (PID: 6584)
- cmd.exe (PID: 5408)
- cmd.exe (PID: 4448)
- cmd.exe (PID: 7480)
- cmd.exe (PID: 7560)
- cmd.exe (PID: 7960)
- cmd.exe (PID: 5072)
- cmd.exe (PID: 6872)
- cmd.exe (PID: 6112)
- cmd.exe (PID: 7552)
- cmd.exe (PID: 920)
- cmd.exe (PID: 4040)
- cmd.exe (PID: 2236)
- cmd.exe (PID: 7872)
- cmd.exe (PID: 4220)
- cmd.exe (PID: 7856)
- cmd.exe (PID: 2476)
- cmd.exe (PID: 7868)
- cmd.exe (PID: 2216)
- cmd.exe (PID: 1496)
- cmd.exe (PID: 7272)
- cmd.exe (PID: 7844)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 1020)
- cmd.exe (PID: 2204)
- cmd.exe (PID: 7220)
- cmd.exe (PID: 7880)
- cmd.exe (PID: 5392)
- cmd.exe (PID: 7608)
- cmd.exe (PID: 2340)
- cmd.exe (PID: 7200)
- cmd.exe (PID: 2656)
- cmd.exe (PID: 2896)
- cmd.exe (PID: 6272)
- cmd.exe (PID: 6576)
- cmd.exe (PID: 5608)
- cmd.exe (PID: 7368)
- cmd.exe (PID: 5136)
- cmd.exe (PID: 7604)
- cmd.exe (PID: 744)
- cmd.exe (PID: 1116)
- cmd.exe (PID: 7716)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 2780)
- cmd.exe (PID: 7428)
- cmd.exe (PID: 5528)
- cmd.exe (PID: 8128)
- cmd.exe (PID: 4308)
- cmd.exe (PID: 7696)
- cmd.exe (PID: 616)
- cmd.exe (PID: 3976)
- cmd.exe (PID: 3744)
- cmd.exe (PID: 8184)
- cmd.exe (PID: 6500)
- cmd.exe (PID: 1616)
- cmd.exe (PID: 1676)
- cmd.exe (PID: 7208)
- cmd.exe (PID: 4276)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 7104)
- cmd.exe (PID: 904)
- cmd.exe (PID: 2268)
- cmd.exe (PID: 1244)
- cmd.exe (PID: 7812)
- cmd.exe (PID: 5036)
- cmd.exe (PID: 6048)
- cmd.exe (PID: 2344)
- cmd.exe (PID: 7476)
- cmd.exe (PID: 2148)
- cmd.exe (PID: 7484)
- cmd.exe (PID: 4868)
- cmd.exe (PID: 4892)
- cmd.exe (PID: 5352)
- cmd.exe (PID: 6660)
- cmd.exe (PID: 1052)
- cmd.exe (PID: 5744)
- cmd.exe (PID: 5772)
- cmd.exe (PID: 2644)
- cmd.exe (PID: 6136)
- cmd.exe (PID: 2812)
- cmd.exe (PID: 3160)
- cmd.exe (PID: 8000)
- cmd.exe (PID: 3796)
- cmd.exe (PID: 7216)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 7268)
- cmd.exe (PID: 7876)
- cmd.exe (PID: 7548)
- cmd.exe (PID: 4948)
- cmd.exe (PID: 6816)
- cmd.exe (PID: 5408)
- cmd.exe (PID: 5228)
- cmd.exe (PID: 8092)
- cmd.exe (PID: 7728)
- cmd.exe (PID: 208)
- cmd.exe (PID: 6208)
- cmd.exe (PID: 7844)
- cmd.exe (PID: 7776)
- cmd.exe (PID: 7768)
- cmd.exe (PID: 7880)
- cmd.exe (PID: 7020)
- cmd.exe (PID: 1056)
- cmd.exe (PID: 7220)
- cmd.exe (PID: 8112)
- cmd.exe (PID: 7700)
- cmd.exe (PID: 2236)
- cmd.exe (PID: 448)
- cmd.exe (PID: 7612)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 7892)
- cmd.exe (PID: 4728)
- cmd.exe (PID: 6900)
- cmd.exe (PID: 7216)
- cmd.exe (PID: 4308)
- cmd.exe (PID: 6652)
- cmd.exe (PID: 7304)
- cmd.exe (PID: 828)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 4868)
Uses WMIC.EXE
- cmd.exe (PID: 7216)
Starts itself from another location
- unins000.exe (PID: 3796)
- VC_redist.x86.exe (PID: 8052)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 2140)
Hides command output
- cmd.exe (PID: 720)
- cmd.exe (PID: 2084)
- cmd.exe (PID: 8024)
- cmd.exe (PID: 7824)
- cmd.exe (PID: 8056)
Checks for external IP
- curl.exe (PID: 6392)
- curl.exe (PID: 7496)
- svchost.exe (PID: 2196)
- curl.exe (PID: 1660)
- curl.exe (PID: 6032)
Execution of CURL command
- cmd.exe (PID: 2140)
Script adds exclusion process to Windows Defender
- cmd.exe (PID: 7036)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 7036)
Starts a Microsoft application from unusual location
- VC_redist.x86.exe (PID: 8052)
- VC_redist.x86.exe (PID: 5416)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 7036)
INFO
Application launched itself
- firefox.exe (PID: 7420)
- firefox.exe (PID: 7376)
Reads the software policy settings
- slui.exe (PID: 1180)
- slui.exe (PID: 7508)
Manual execution by a user
- Patch_MB_5.x.exe (PID: 3900)
- WinRAR.exe (PID: 6108)
- Patch_MB_5.x.exe (PID: 924)
- WinRAR.exe (PID: 3032)
Checks proxy server information
- slui.exe (PID: 7508)
The sample compiled with english language support
- 7z2201.exe (PID: 3156)
- Patch_MB_5.x.exe (PID: 3900)
- rs.tmp (PID: 5864)
- MBAMService.exe (PID: 1088)
- MBAMService.exe (PID: 7232)
- _iu14D2N.tmp (PID: 1004)
- VC_redist.x86.exe (PID: 1628)
- VC_redist.x86.exe (PID: 8052)
- 7z.exe (PID: 7684)
- VC_redist.x86.exe (PID: 5416)
- msiexec.exe (PID: 4284)
- VC_redist.x86.exe (PID: 7528)
- VC_redist.x86.exe (PID: 7792)
The sample compiled with russian language support
- 7z2201.exe (PID: 3156)
Changes the display of characters in the console
- cmd.exe (PID: 4776)
Starts MODE.COM to configure console settings
- mode.com (PID: 6572)
- mode.com (PID: 7244)
Creates or changes the value of an item property via Powershell
- cmd.exe (PID: 2140)
The executable file from the user directory is run by the Powershell process
- rs.exe (PID: 5972)
The sample compiled with spanish language support
- rs.tmp (PID: 5864)
Execution of CURL command
- cmd.exe (PID: 7596)
- cmd.exe (PID: 7300)
- cmd.exe (PID: 6944)
- cmd.exe (PID: 6488)
- cmd.exe (PID: 7552)
- cmd.exe (PID: 8128)
- cmd.exe (PID: 2140)
- cmd.exe (PID: 5608)
- cmd.exe (PID: 8064)
- cmd.exe (PID: 7036)
Manages system restore points
- SrTasks.exe (PID: 1664)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
810
Monitored processes
669
Malicious processes
9
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | tasklist /fi "imagename eq Malwarebytes.exe" /fo csv /nh | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 132 | tasklist /fi "imagename eq Malwarebytes.exe" /fo csv /nh | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | tasklist /fi "imagename eq Malwarebytes.exe" /fo csv /nh | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | C:\WINDOWS\system32\cmd.exe /c tasklist /fi "imagename eq Malwarebytes.exe" /fo csv /nh | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | C:\WINDOWS\system32\cmd.exe /c tasklist /fi "imagename eq Malwarebytes.exe" /fo csv /nh | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | findstr /ilc:"Windows 11" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | tasklist /fi "imagename eq Malwarebytes.exe" /fo csv /nh | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | tasklist /fi "imagename eq Malwarebytes.exe" /fo csv /nh | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 444 | C:\WINDOWS\system32\cmd.exe /c tasklist /fi "imagename eq Malwarebytes.exe" /fo csv /nh | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | tasklist /fi "imagename eq Malwarebytes.exe" /fo csv /nh | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
131 565
Read events
128 785
Write events
1 123
Delete events
1 657
Modification events
| (PID) Process: | (7420) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
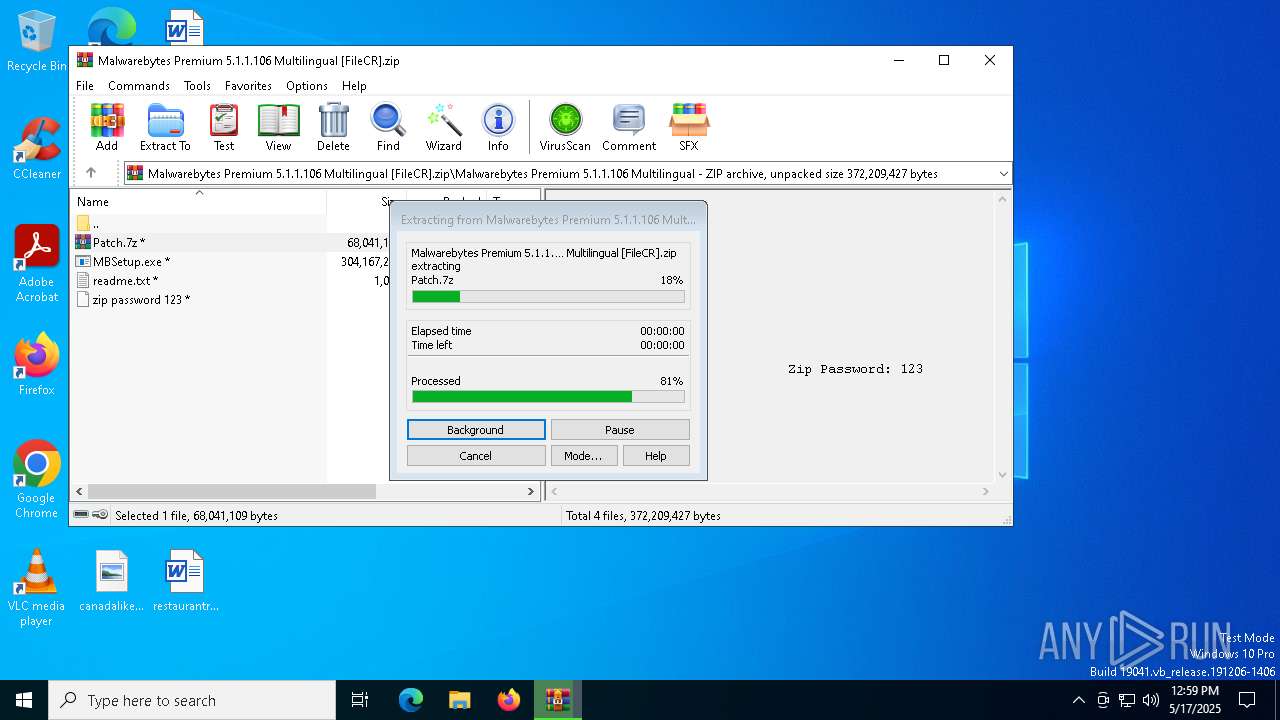
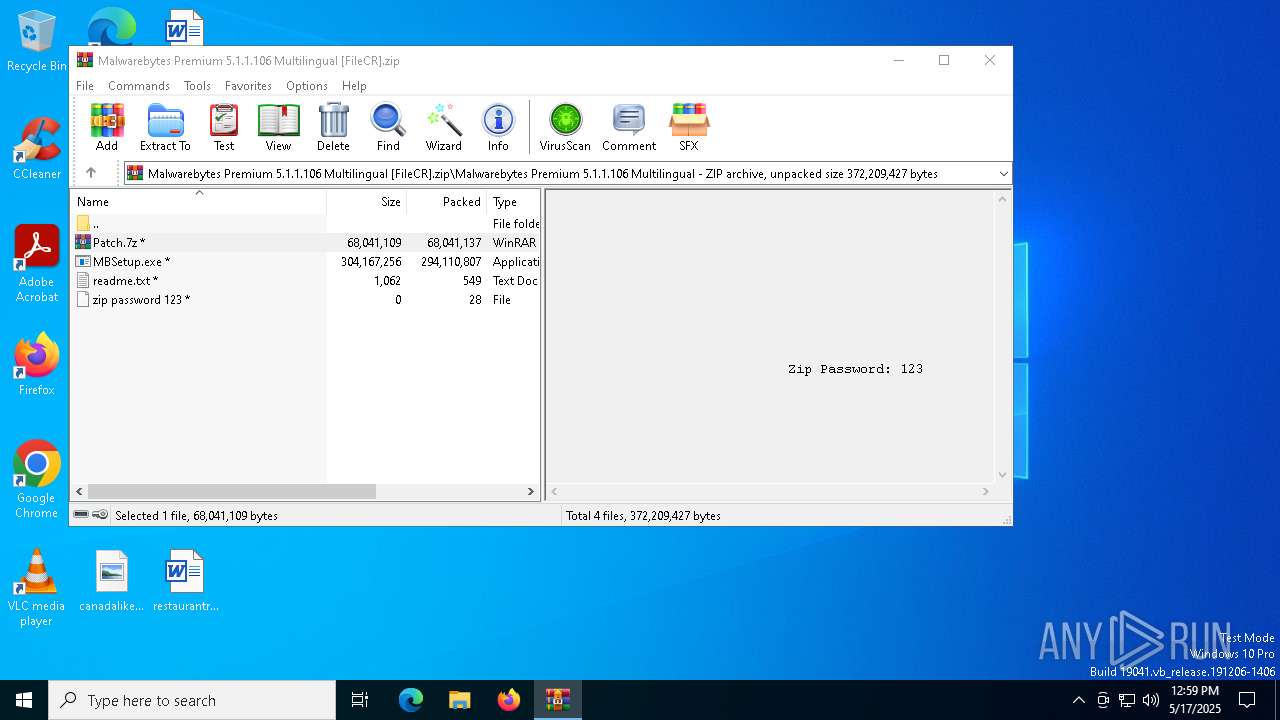
Value: C:\Users\admin\Downloads\Malwarebytes Premium 5.1.1.106 Multilingual [FileCR].zip | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
446
Suspicious files
546
Text files
480
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7420 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:A6390C3BB054B8632A0E2BEAB1E42D90 | SHA256:F4FE7D79DA787E800DEB293156AA6029BDE26440640A16A533F8D653605182CB | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.tmp | binary | |
MD5:4006DDC2918B16C7EF5516C58373842B | SHA256:269EA23B77EDE0874628BD8611BCC5A3E87E0C44CA8A821C0D028B929D4F468F | |||
| 7420 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
110
DNS requests
140
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7420 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
7420 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7420 | firefox.exe | POST | 200 | 184.24.77.56:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7420 | firefox.exe | POST | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/ | unknown | — | — | whitelisted |
7420 | firefox.exe | POST | 200 | 184.24.77.56:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7420 | firefox.exe | POST | 200 | 216.58.206.35:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
7420 | firefox.exe | POST | 200 | 216.58.206.35:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
7420 | firefox.exe | POST | 200 | 184.24.77.58:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7420 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | — | — | whitelisted |
7420 | firefox.exe | 217.156.123.203:443 | filecr.com | — | RO | unknown |
7420 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
7420 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
filecr.com |
| unknown |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7496 | curl.exe | Device Retrieving External IP Address Detected | ET INFO Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
7496 | curl.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup SSL Cert Observed (ipinfo .io) |
6392 | curl.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup SSL Cert Observed (ipinfo .io) |
6392 | curl.exe | Device Retrieving External IP Address Detected | ET INFO Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
1660 | curl.exe | Device Retrieving External IP Address Detected | ET INFO Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
1660 | curl.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup SSL Cert Observed (ipinfo .io) |
6032 | curl.exe | Device Retrieving External IP Address Detected | ET INFO Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
6032 | curl.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup SSL Cert Observed (ipinfo .io) |
Process | Message |
|---|---|
MBAMService.exe | Retry log file open from dll
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Firing service stop event |
MBAMService.exe | Calling implementation stop |
MBAMService.exe | Stop called from an external process |