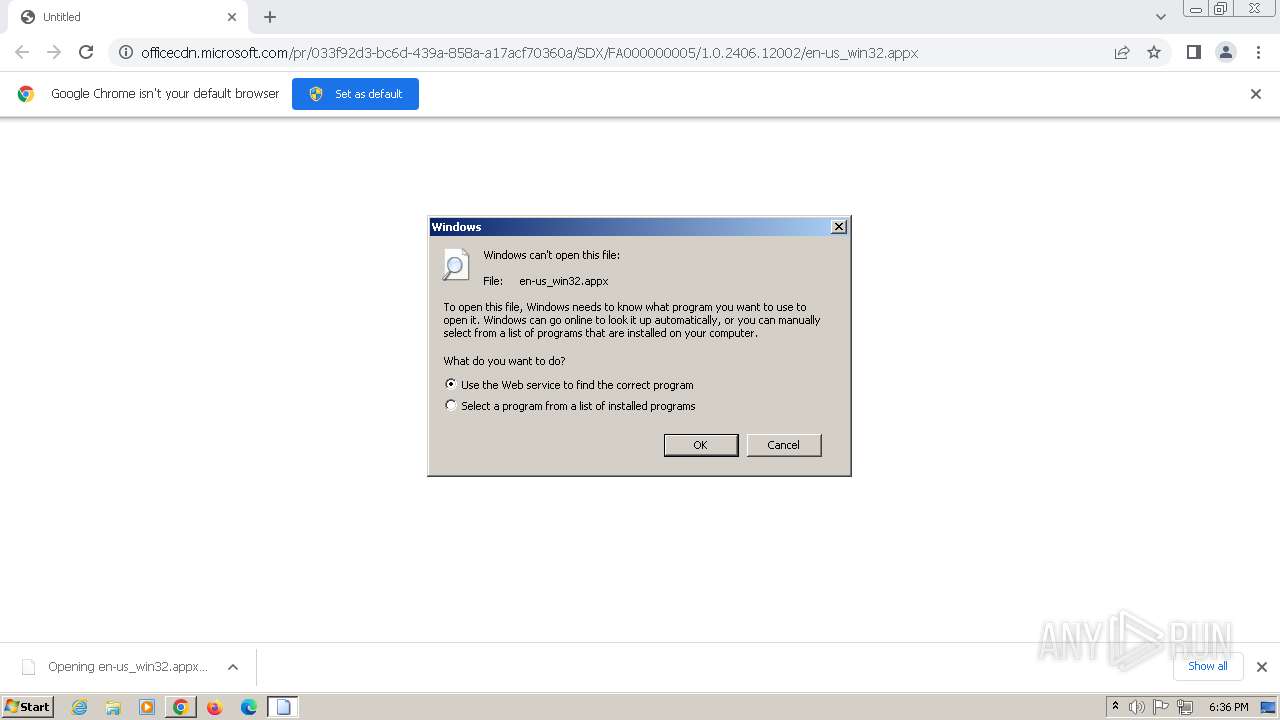
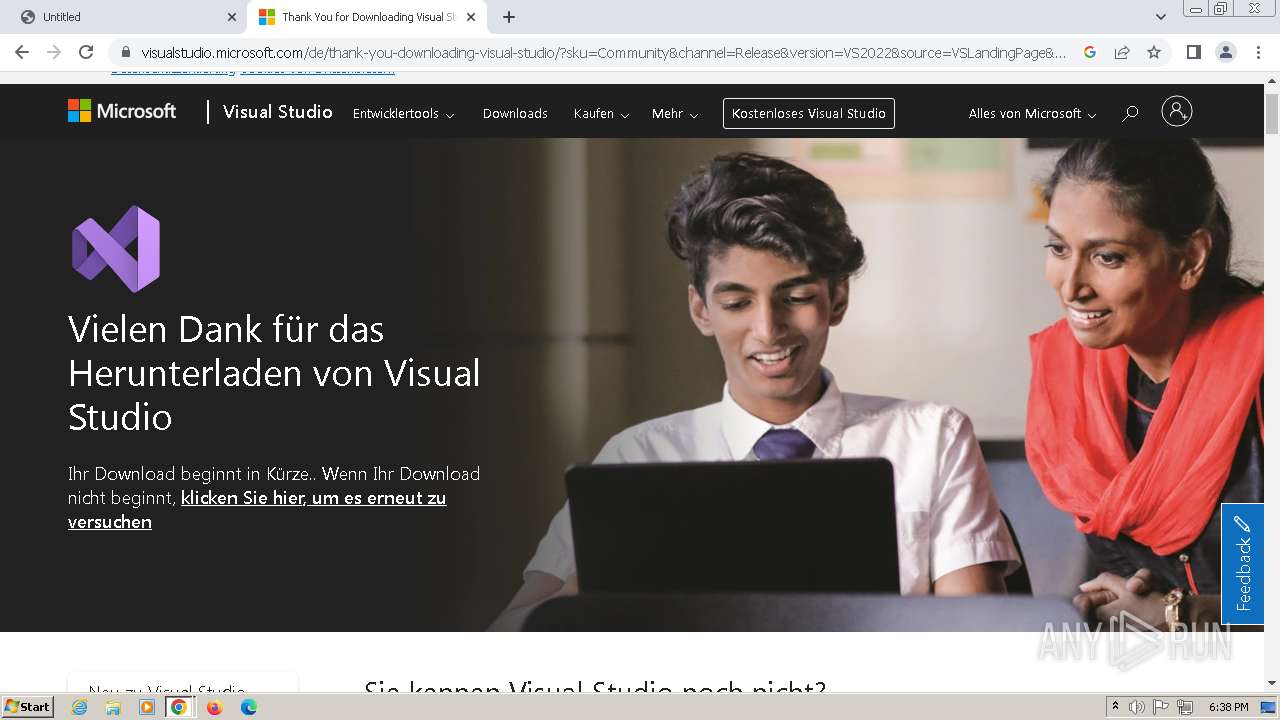
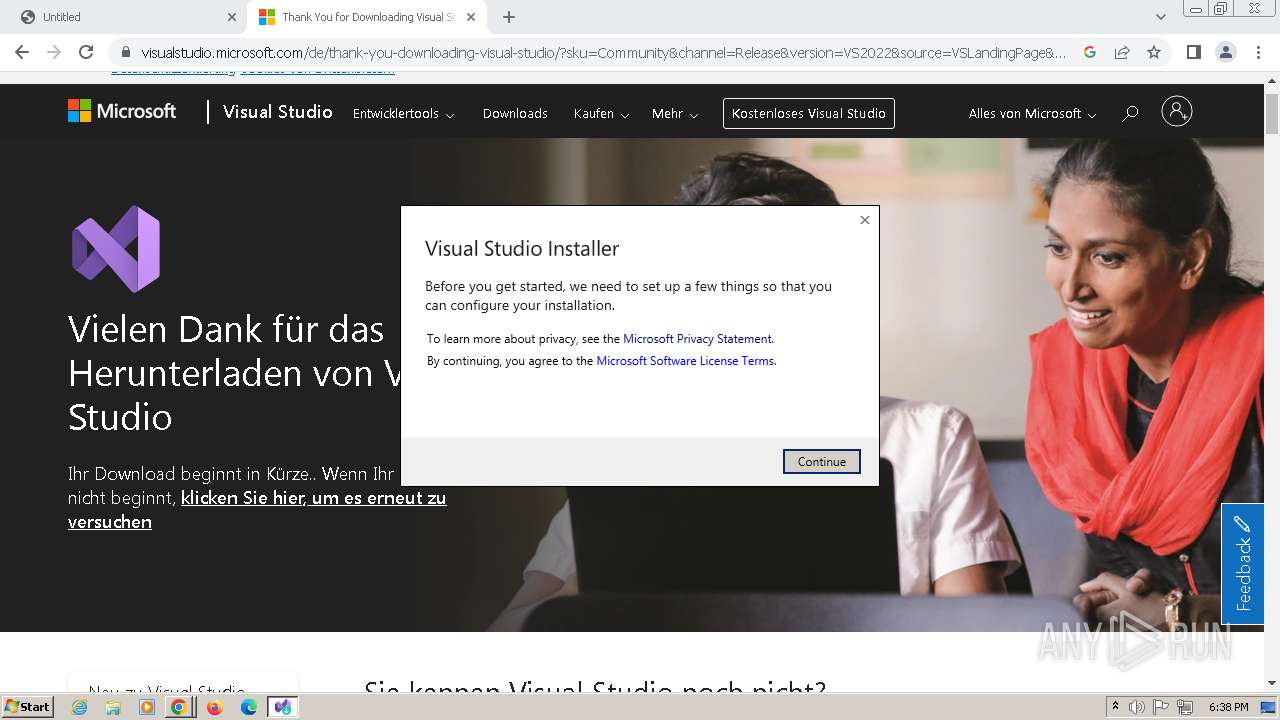
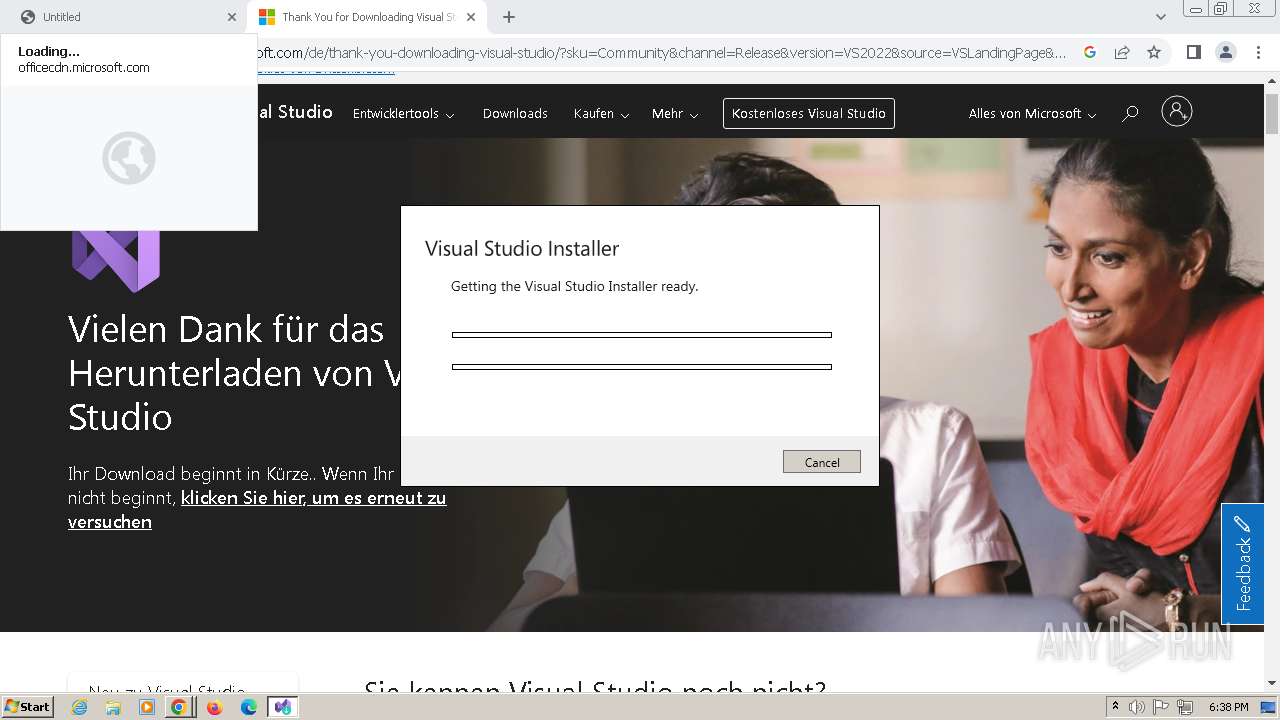
| URL: | officecdn.microsoft.com/pr/033f92d3-bc6d-439a-858a-a17acf70360a/SDX/FA000000005/1.0.2406.12002/en-us_win32.appx |
| Full analysis: | https://app.any.run/tasks/8f35e43a-2029-4c02-a7cc-074e677a584c |
| Verdict: | Malicious activity |
| Analysis date: | July 16, 2024, 18:35:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 34C59B91ED2DFB187FE1DBDCD9D0FFEB |
| SHA1: | 37386DA8F6C5CEB95C2472B3EC89E9DD039D36C3 |
| SHA256: | 6CC08AED9B6371D2C667FDCE3F89C6ACA3EC404A492738A3D46FFCFB0E9ABE29 |
| SSDEEP: | 3:alyutR9OlmVS1IdDU3hW6tfV/vUhuV24x3:WDARFtouU4x3 |
MALICIOUS
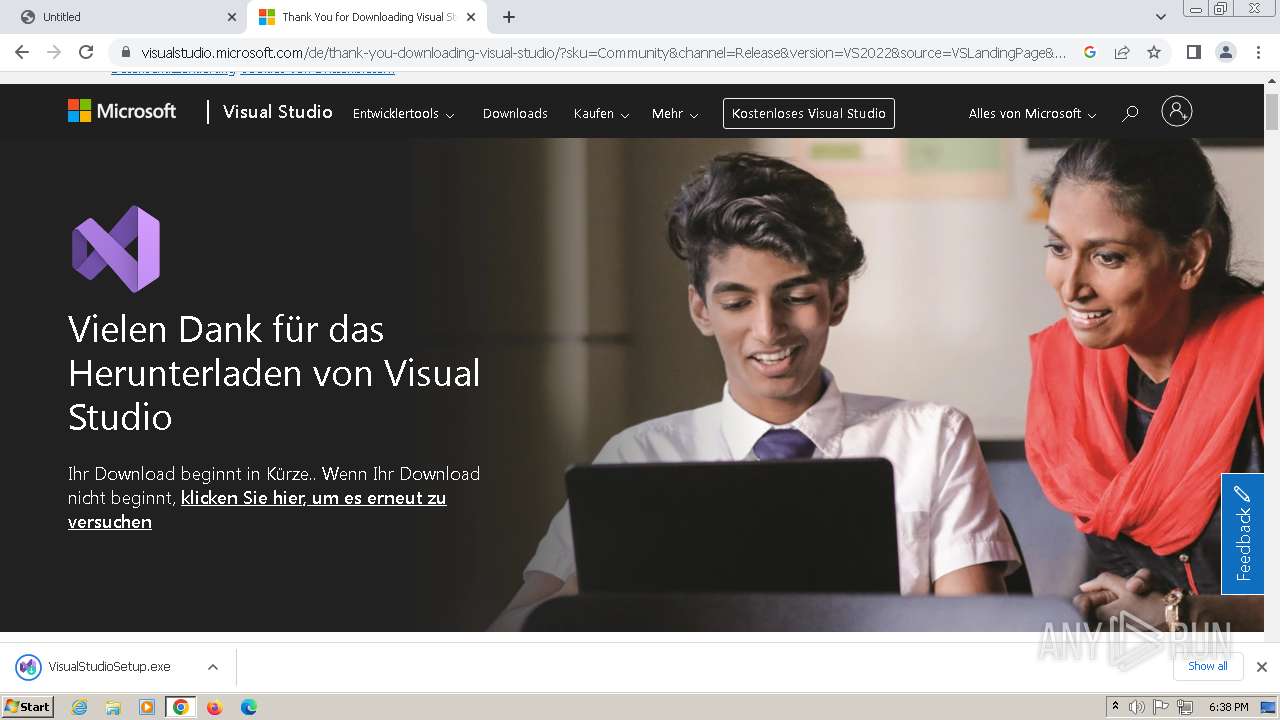
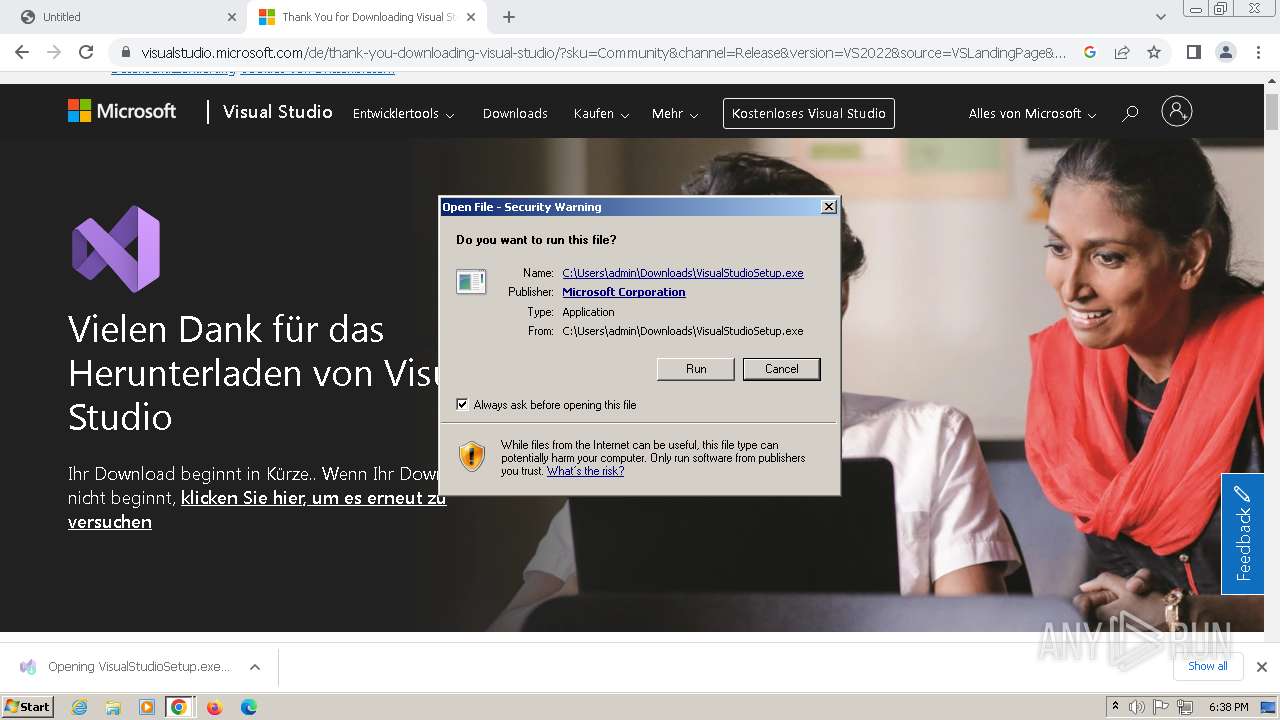
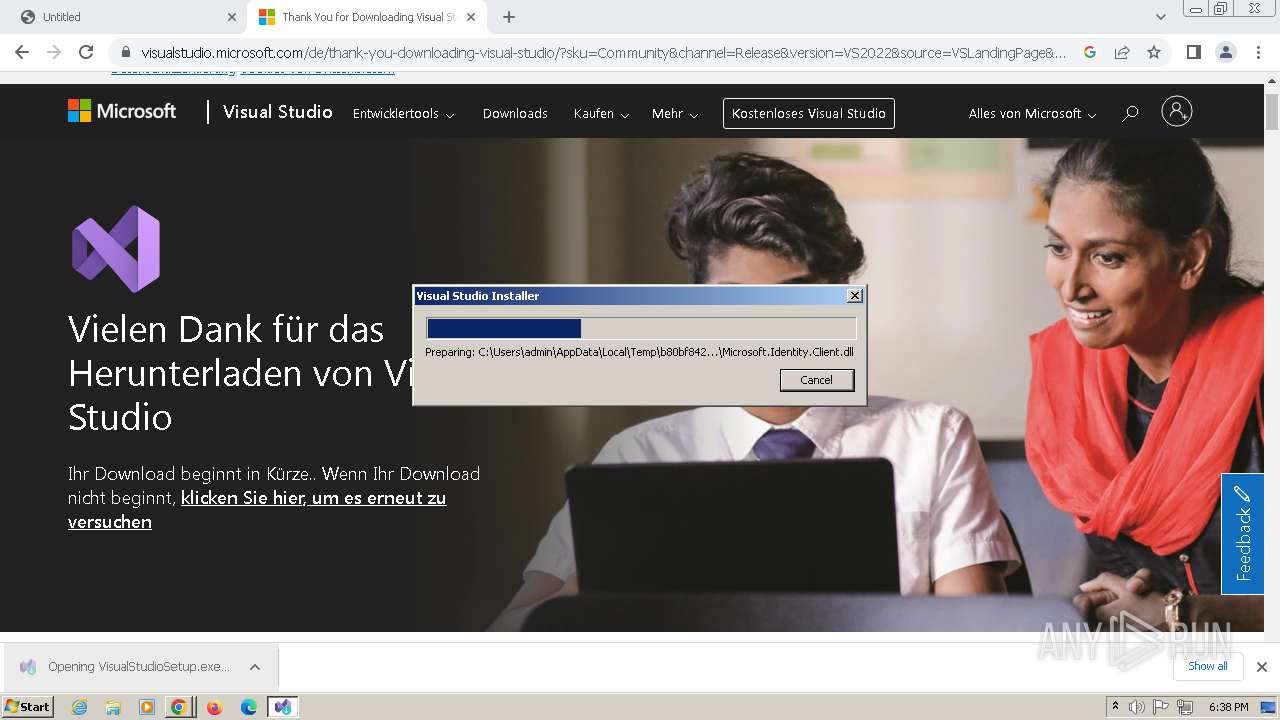
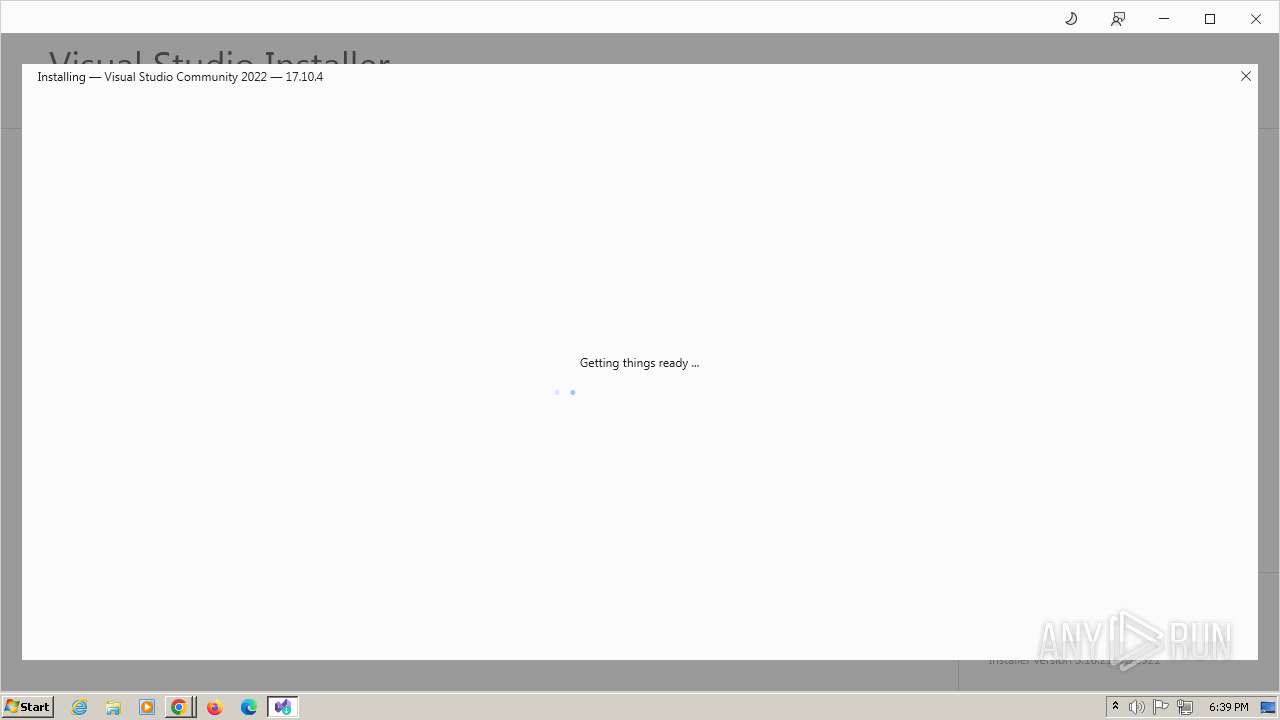
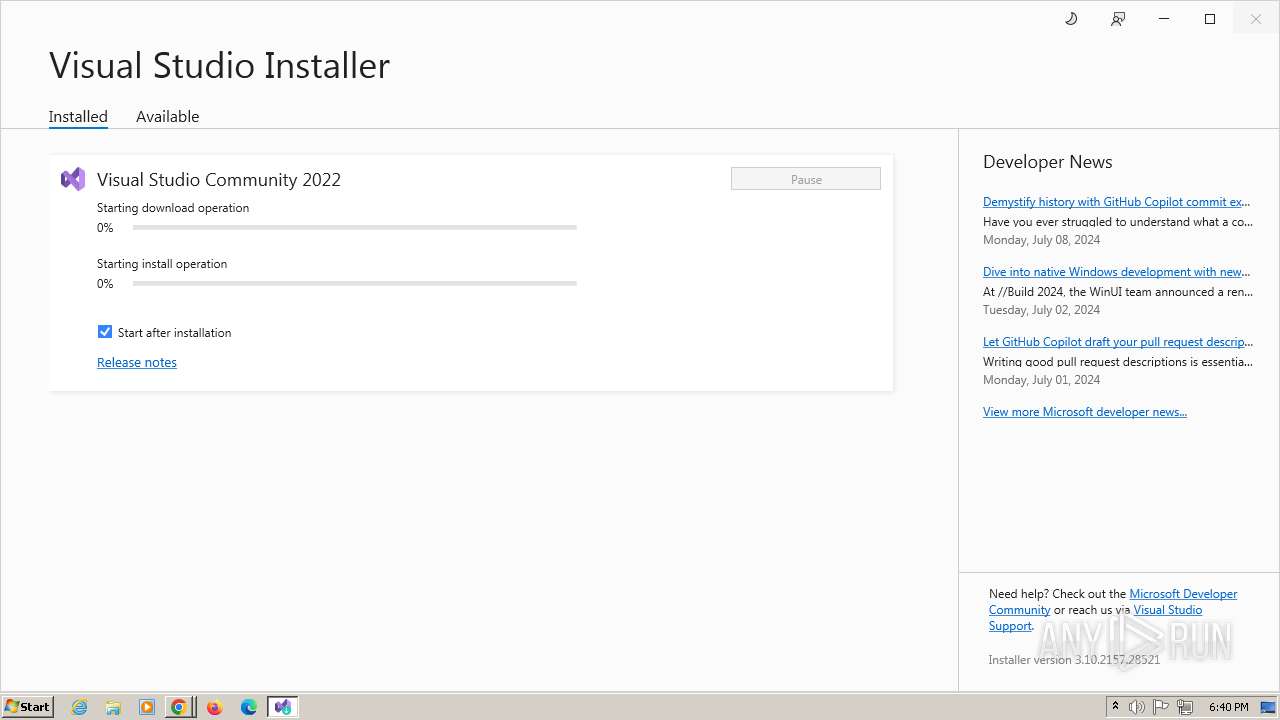
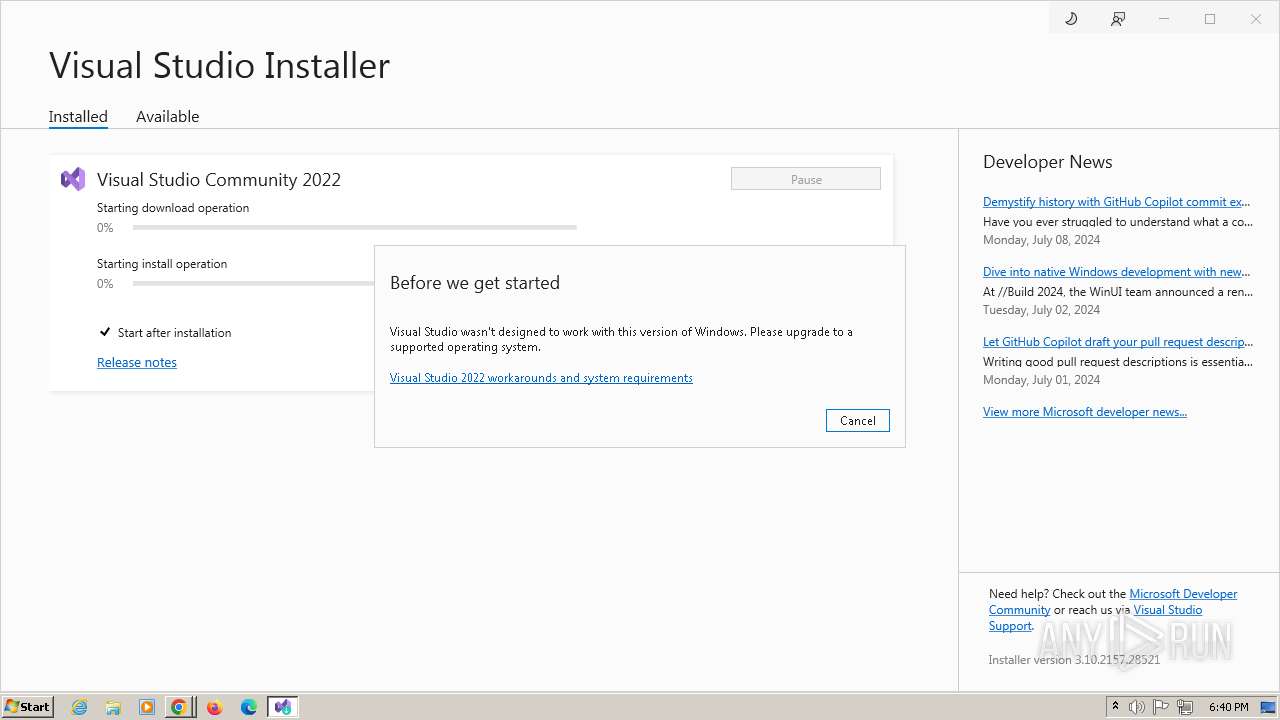
Drops the executable file immediately after the start
- VisualStudioSetup.exe (PID: 2928)
- vs_setup_bootstrapper.exe (PID: 1756)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- chrome.exe (PID: 1664)
Process drops legitimate windows executable
- chrome.exe (PID: 1664)
- VisualStudioSetup.exe (PID: 2928)
- vs_setup_bootstrapper.exe (PID: 1756)
Reads the Internet Settings
- rundll32.exe (PID: 2668)
- VisualStudioSetup.exe (PID: 2928)
- vs_setup_bootstrapper.exe (PID: 1756)
- setup.exe (PID: 1624)
- setup.exe (PID: 1428)
Reads security settings of Internet Explorer
- VisualStudioSetup.exe (PID: 2928)
- vs_setup_bootstrapper.exe (PID: 1756)
- setup.exe (PID: 1624)
- setup.exe (PID: 1428)
Executable content was dropped or overwritten
- VisualStudioSetup.exe (PID: 2928)
- vs_setup_bootstrapper.exe (PID: 1756)
- setup.exe (PID: 1428)
Found regular expressions for crypto-addresses (YARA)
- vs_setup_bootstrapper.exe (PID: 1756)
- setup.exe (PID: 1624)
- setup.exe (PID: 1428)
The process drops C-runtime libraries
- vs_setup_bootstrapper.exe (PID: 1756)
Reads settings of System Certificates
- vs_setup_bootstrapper.exe (PID: 1756)
- setup.exe (PID: 1624)
- setup.exe (PID: 1428)
The process creates files with name similar to system file names
- vs_setup_bootstrapper.exe (PID: 1756)
Searches for installed software
- vs_installer.windows.exe (PID: 2460)
Creates a software uninstall entry
- vs_installer.windows.exe (PID: 2460)
Checks Windows Trust Settings
- setup.exe (PID: 1624)
- setup.exe (PID: 1428)
- msiexec.exe (PID: 2732)
Application launched itself
- setup.exe (PID: 1624)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2732)
INFO
Executable content was dropped or overwritten
- chrome.exe (PID: 2452)
- chrome.exe (PID: 1664)
- msiexec.exe (PID: 2732)
Checks supported languages
- VisualStudioSetup.exe (PID: 2928)
- setup.exe (PID: 1624)
- vs_installer.windows.exe (PID: 2460)
- setup.exe (PID: 1428)
- msiexec.exe (PID: 2732)
- vs_setup_bootstrapper.exe (PID: 1756)
The process uses the downloaded file
- chrome.exe (PID: 2404)
- chrome.exe (PID: 2192)
- chrome.exe (PID: 1664)
Drops the executable file immediately after the start
- chrome.exe (PID: 2452)
- chrome.exe (PID: 1664)
Reads the computer name
- VisualStudioSetup.exe (PID: 2928)
- vs_setup_bootstrapper.exe (PID: 1756)
- setup.exe (PID: 1624)
- vs_installer.windows.exe (PID: 2460)
- setup.exe (PID: 1428)
- msiexec.exe (PID: 2732)
Reads the machine GUID from the registry
- VisualStudioSetup.exe (PID: 2928)
- vs_setup_bootstrapper.exe (PID: 1756)
- setup.exe (PID: 1624)
- setup.exe (PID: 1428)
- msiexec.exe (PID: 2732)
Create files in a temporary directory
- VisualStudioSetup.exe (PID: 2928)
- setup.exe (PID: 1624)
- setup.exe (PID: 1428)
- msiexec.exe (PID: 2732)
- vs_setup_bootstrapper.exe (PID: 1756)
Reads Environment values
- vs_setup_bootstrapper.exe (PID: 1756)
- setup.exe (PID: 1624)
- setup.exe (PID: 1428)
Creates files in the program directory
- vs_setup_bootstrapper.exe (PID: 1756)
- setup.exe (PID: 1624)
- setup.exe (PID: 1428)
Disables trace logs
- vs_setup_bootstrapper.exe (PID: 1756)
- setup.exe (PID: 1624)
- setup.exe (PID: 1428)
Reads CPU info
- vs_setup_bootstrapper.exe (PID: 1756)
- setup.exe (PID: 1624)
Creates files or folders in the user directory
- vs_setup_bootstrapper.exe (PID: 1756)
- setup.exe (PID: 1624)
- setup.exe (PID: 1428)
Application launched itself
- chrome.exe (PID: 1664)
Checks proxy server information
- setup.exe (PID: 1428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
88
Monitored processes
45
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 552 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=1920 --field-trial-handle=1132,i,11623008486057960092,11869658044667379859,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 836 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=884 --field-trial-handle=1132,i,11623008486057960092,11869658044667379859,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 852 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=3924 --field-trial-handle=1132,i,11623008486057960092,11869658044667379859,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 872 | "getmac" | C:\Windows\SysWOW64\getmac.exe | — | vs_setup_bootstrapper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Displays NIC MAC information Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 972 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3680 --field-trial-handle=1132,i,11623008486057960092,11869658044667379859,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 976 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=4296 --field-trial-handle=1132,i,11623008486057960092,11869658044667379859,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1376 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xcc,0xd0,0xd4,0xa0,0xd8,0x7fef4cc6b58,0x7fef4cc6b68,0x7fef4cc6b78 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1428 | "C:\Program Files (x86)\Microsoft Visual Studio\Installer\setup.exe" elevate --activityId a78a913e-207d-4776-b491-685f0e6fd51d --campaign 2030:021b380a96df491f9a6c591ee8bc1420 --handle 196974 --locale en-US --pid 1624 --pipeName ba606d4a625b495da19c1aff3d5f214d --serializedSession "{\"TelemetryLevel\":null,\"IsOptedIn\":true,\"HostName\":\"Default\",\"AppInsightsInstrumentationKey\":\"f144292e-e3b2-4011-ac90-20e5c03fbce5\",\"AsimovInstrumentationKey\":\"AIF-312cbd79-9dbb-4c48-a7da-3cc2a931cb70\",\"CollectorApiKey\":\"f3e86b4023cc43f0be495508d51f588a-f70d0e59-0fb0-4473-9f19-b4024cc340be-7296\",\"AppId\":1000,\"UserId\":\"9ca16623-3dc3-418b-a508-ffb4a02bd8cc\",\"Id\":\"ca49356a-36e8-4144-aa0e-0da535cf44df\",\"ProcessStartTime\":638567519613966172,\"SkuName\":null,\"VSExeVersion\":null,\"BucketFiltersToEnableWatsonForFaults\":[{\"AdditionalProperties\":[],\"Id\":\"a02930d9-c607-41c3-8698-0fd9196735a5\",\"WatsonEventType\":\"VisualStudioNonFatalErrors2\",\"BucketParameterFilters\":[null,null,\"(?i)vs\\.setup.*\",null,null,null,null,null,null,null]},{\"AdditionalProperties\":[],\"Id\":\"64a13603-6d89-42e4-a299-13f77e5ad306\",\"WatsonEventType\":\"VisualStudioNonFatalErrors2\",\"BucketParameterFilters\":[null,null,\"(?i)vs\\.willow.*\",null,null,null,null,null,null,null]}],\"BucketFiltersToAddDumpsToFaults\":[]}" | C:\Program Files (x86)\Microsoft Visual Studio\Installer\setup.exe | setup.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: Visual Studio Installer Exit code: 0 Version: 3.10.2157.28521 Modules
| |||||||||||||||
| 1596 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=33 --mojo-platform-channel-handle=4440 --field-trial-handle=1132,i,11623008486057960092,11869658044667379859,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1604 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=1712 --field-trial-handle=1132,i,11623008486057960092,11869658044667379859,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
40 557
Read events
40 090
Write events
403
Delete events
64
Modification events
| (PID) Process: | (1664) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1664) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1664) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1664) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1664) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1664) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1664) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1664) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1664) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1664) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
450
Suspicious files
354
Text files
192
Unknown types
137
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1664 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF125636.TMP | — | |
MD5:— | SHA256:— | |||
| 1664 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1664 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:9F941EA08DBDCA2EB3CFA1DBBBA6F5DC | SHA256:127F71DF0D2AD895D4F293E62284D85971AE047CA15F90B87BF6335898B0B655 | |||
| 1664 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF125646.TMP | text | |
MD5:C9F912E20C2B8550D6E56BF059FBDBCE | SHA256:787976FD1D3EE7D771715AAB9273F161BEC6A239E5CCA7EE051881C61A043049 | |||
| 1664 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF1257bd.TMP | text | |
MD5:2E7DE1472E408EDCE142CB8CB549EECD | SHA256:AF89FAB4CC08BC539F2ED6EE65C4135E76D3ED35DBD45D56AF4B9E1DAEAF1E6A | |||
| 1664 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF125636.TMP | text | |
MD5:C398C1B0D11B97B58F6BA8D4B77584C4 | SHA256:DAC0D9B0CBB2A0BACD18168D7CA09CD9D41CDE95EE0A0EBC562F7FE77E59BC60 | |||
| 1664 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C7925A6B262C5676D1C36638981A6EA | SHA256:07F6FB1E9CBCE4D15C00A9FBF9A95C1F31DE20C4C48B433198862E8759CD128D | |||
| 1664 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 1664 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:77D78AA260250337A33935C5661365B3 | SHA256:7B64767E6B757BA495D767C0F8DA48B022B0026362BF960A36B75110F6A4C302 | |||
| 1664 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old~RF125934.TMP | text | |
MD5:764A517AC68AAE0FDCF18D0B999712E8 | SHA256:B8BBA1678C15680399402F70FCBE04CFE0617691BC6F591E6DD8DCE8A744517C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
172
DNS requests
111
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2060 | chrome.exe | GET | 200 | 2.19.198.59:80 | http://officecdn.microsoft.com/pr/033f92d3-bc6d-439a-858a-a17acf70360a/SDX/FA000000005/1.0.2406.12002/en-us_win32.appx | unknown | — | — | whitelisted |
2836 | iexplore.exe | GET | 301 | 2.21.20.150:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=appx | unknown | — | — | whitelisted |
2836 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://cacerts.digicert.com/DigiCertGlobalRootG3.crt | unknown | — | — | whitelisted |
2836 | iexplore.exe | GET | 302 | 23.35.238.131:80 | http://go.microsoft.com/fwlink/?LinkId=57426&Ext=appx | unknown | — | — | whitelisted |
2836 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://cacerts.digicert.com/DigiCertGlobalRootG3.crt | unknown | — | — | whitelisted |
2836 | iexplore.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?973fcb3f5030c405 | unknown | — | — | whitelisted |
2836 | iexplore.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?d97dfb9fe29d6719 | unknown | — | — | whitelisted |
884 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acwcdm4bj7lx4xbm2ireywxlhvca_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win64_adsurwm4gclupf32xdrpgdnapira.crx3 | unknown | — | — | whitelisted |
2416 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://crt.usertrust.com/USERTrustRSAAddTrustCA.crt | unknown | — | — | whitelisted |
2416 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://crt.usertrust.com/USERTrustRSAAddTrustCA.crt | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
360 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2060 | chrome.exe | 172.217.23.106:443 | safebrowsing.googleapis.com | GOOGLE | US | whitelisted |
1664 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2060 | chrome.exe | 2.19.198.59:80 | officecdn.microsoft.com | Akamai International B.V. | DE | unknown |
2060 | chrome.exe | 74.125.143.84:443 | accounts.google.com | GOOGLE | US | unknown |
1664 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
2836 | iexplore.exe | 23.35.238.131:80 | go.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
officecdn.microsoft.com |
| whitelisted |
accounts.google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
shell.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
cacerts.digicert.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
th.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2416 | iexplore.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
2416 | iexplore.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |